
Description
Exploit a Windows machine in this beginner level challenge.
Deploy the machine and quickly scan the ports with rustscan,
1
rustscan -a 10.10.235.249
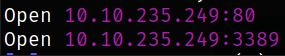
we get 2 open port. Lets scan this using nmap,
1
nmap -sV -sC -p80,3389 10.10.235.249 -oN nmap.txt
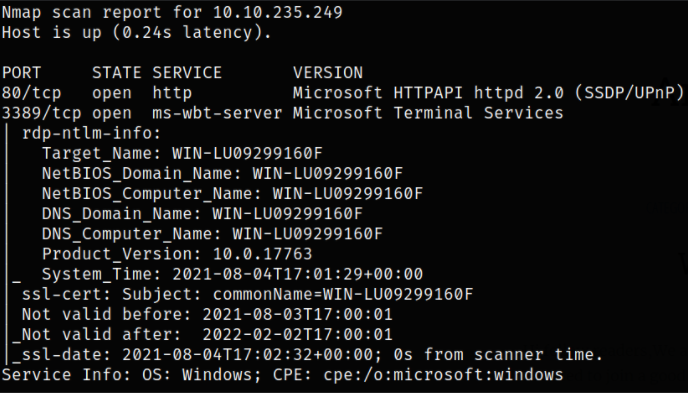
Result scan reveals that port 80 is running Microsoft IIS Server and port 3389 is running rdp service. From results, we can conclude that this is a windows box. Let’s enumerate port 80.
Visit http://10.10.235.249,
we got a blog website. Seems like this is the hiring platform.
Enumerating it a bit, I found a poem which was posted by administrator but we can not find their name. So copy the poem and paste this on google to find out the name of the Administrator,
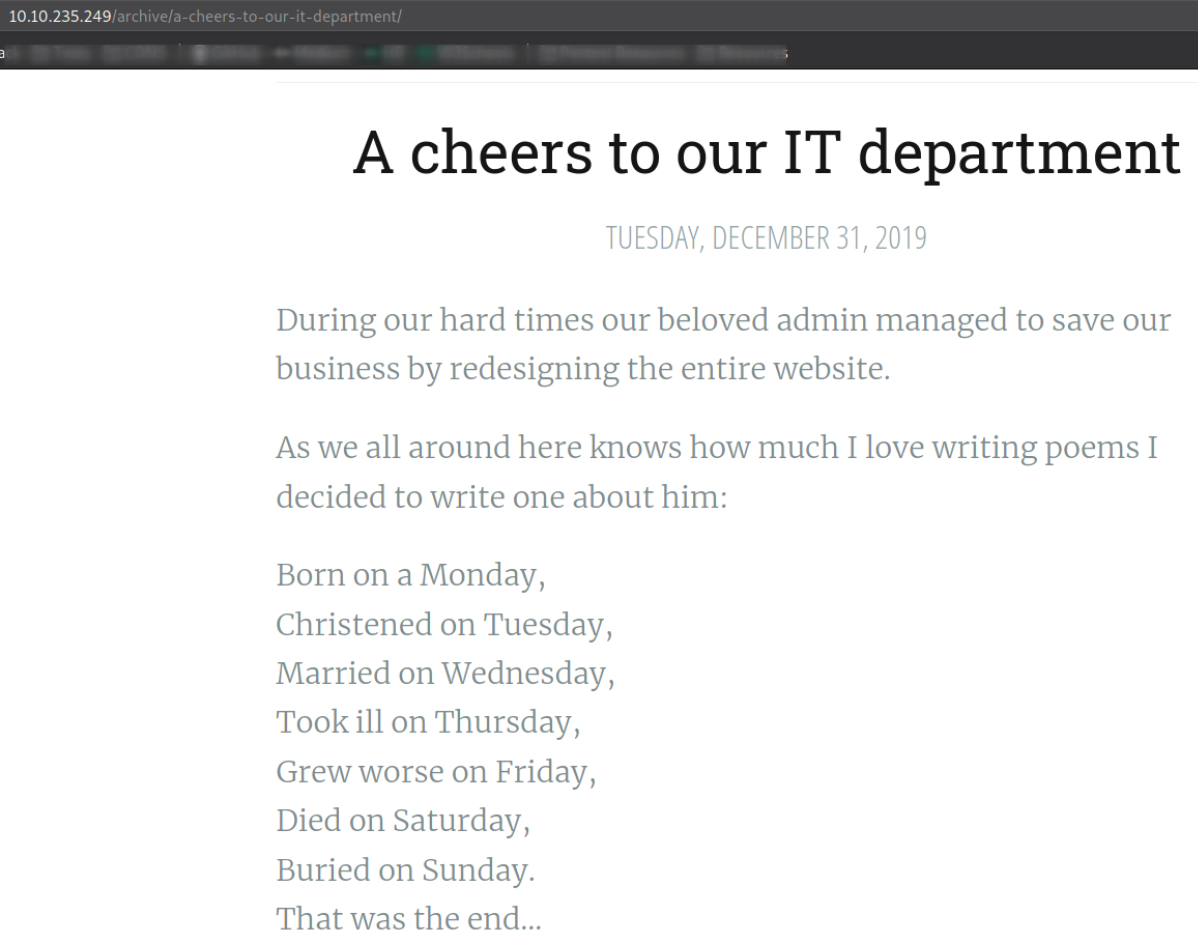
Solomon Grundy and email is sg@anthem.com.
Now, we have find out the username and email of administrator, maybe we can find out the login page where we can utilize these credentials to get into website.
We will use dirsearch to find hidden directories,
1
dirsearch -u http://10.10.235.249 -w /usr/share/seclists/Discovery/Web-Content/common.txt -i 200,301 2>/dev/null
and we get a file name robots.txt which is super interesting to look for. Visit http://10.10.235.249/robots.txt,

we can many hidden directories here, and also maybe the password!
Visiting http://10.10.235.249/umbraco, we are directed to its login page,
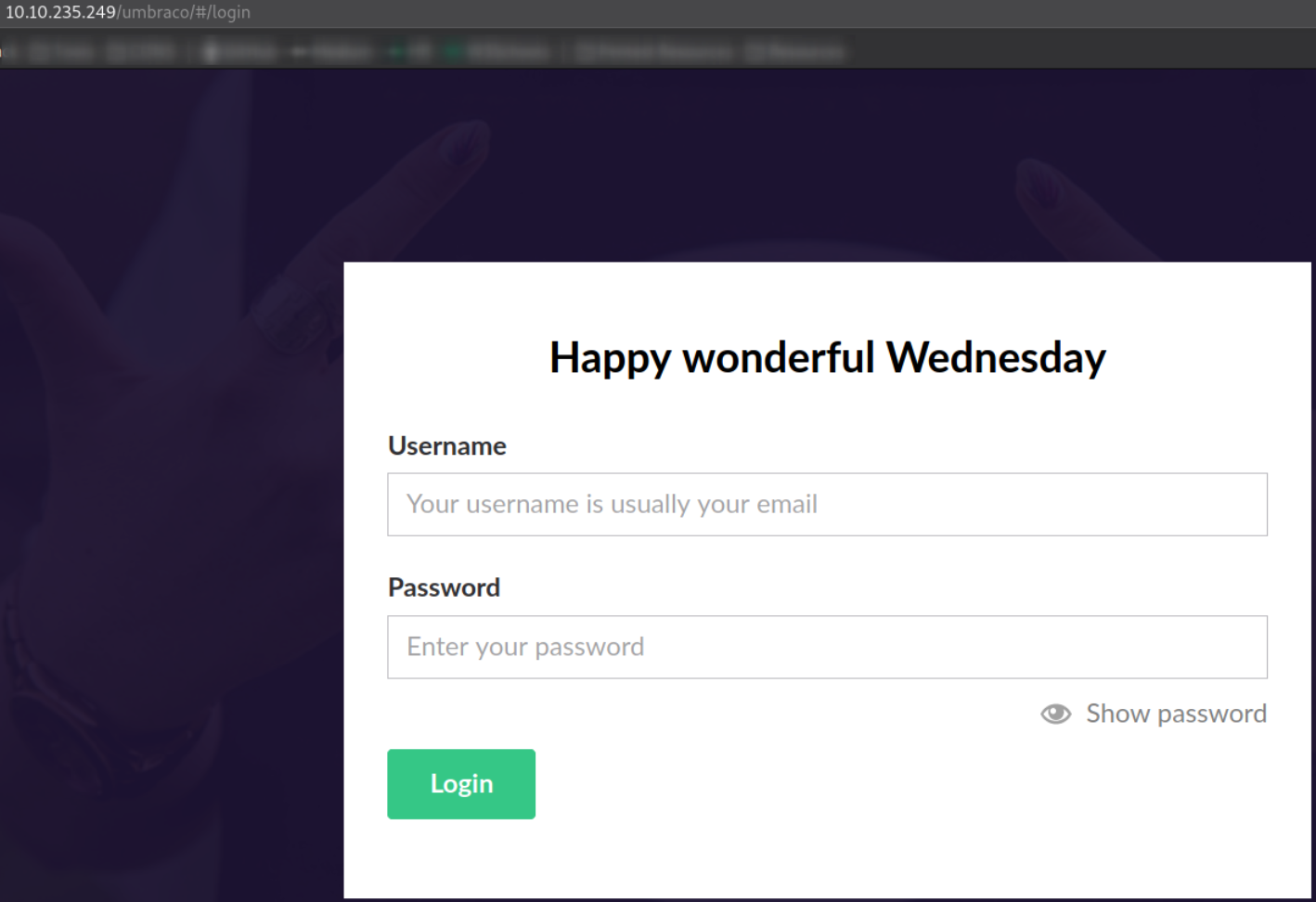
we can use administrator credentials to login,

This is a website which is monitored by administrator.
Now, since we have to find the flags (which are part of task), we can download the whole website using wget command with –recursive switch,
1
2
3
wget --recursive http://10.10.235.249
cd 10.10.235.249
grep -R "THM" #(finding string which contains THM substring in whole directory)
and there we got our flags,
1
2
3
4
./authors/jane-doe/index.html: <input type="text" name="term" placeholder="Search... THM{********}" />
./authors/jane-doe/index.html: <p>Website: <a href="THM{***********}">THM{L0L_WH0_D15}</a>
./archive/a-cheers-to-our-it-department/index.html:<meta content="THM{************}" property="og:description" />
./archive/we-are-hiring/index.html:<meta content="THM{*****************}" property="og:description" />
We can use credentials, SG:***************** to rdp into machine,
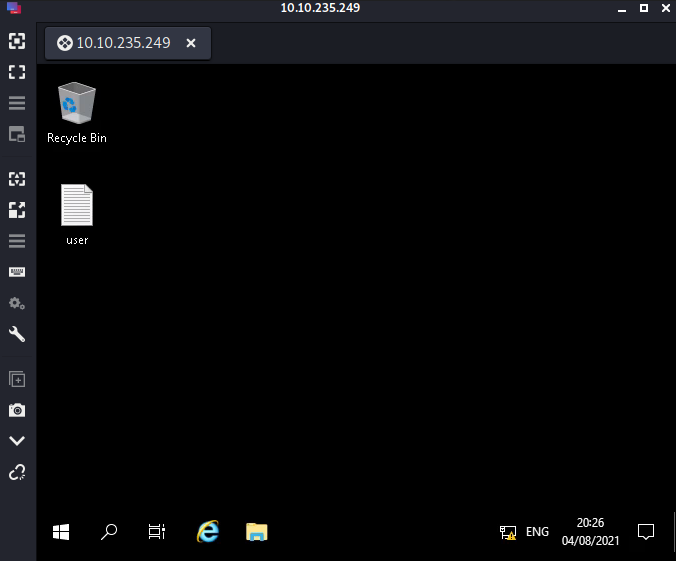
on the desktop, we find our user flag.
Now, it is the time for privilege escalation.
Now, after enumerating, I found that we have to find a way to get hands on administrator password. So after navigating to C drive, there is a directory named backup which is hidden, contain sensitive file,
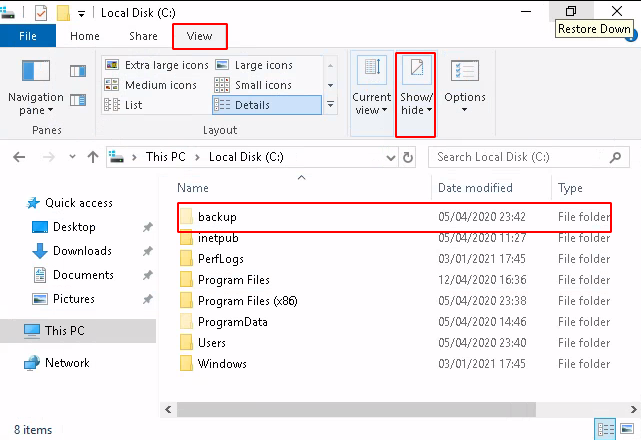
Getting inside of this directory, we can see a text file,
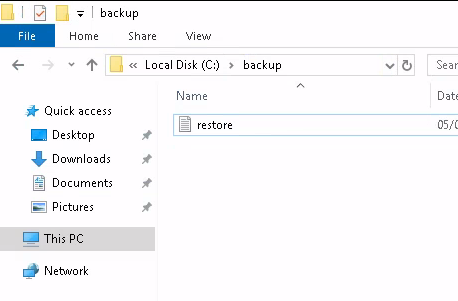
We can open this file,
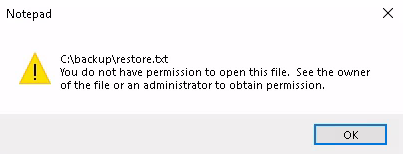
but we got permission error because we are not administrator user.
But, we can do one thing, change this file security permission by adding SG user in administrators group,
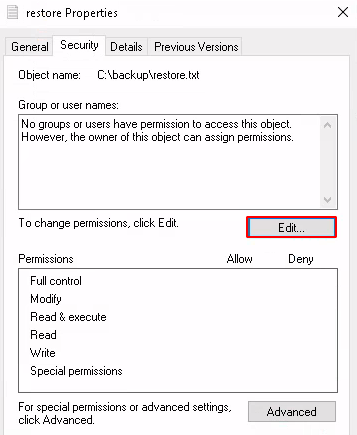
After editing the file permission, we can see our user has been added,
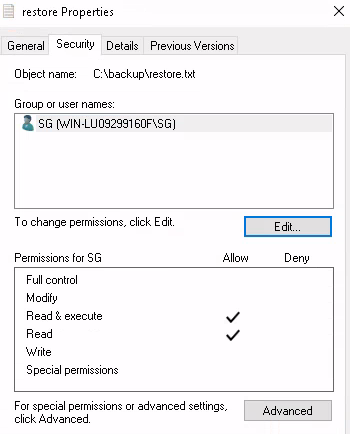
Now, open the file and we can now read the content,

we got the password.
Now, open up the powershell as administrator user and it will prompt us the password,
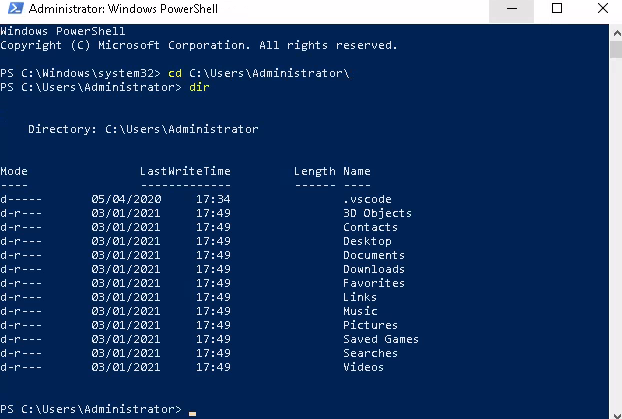
after providing password, we get the administrator access.
Navigating to root directory and listing directory content,
we got our root flag.
