Description
A windows machine has been hacked, its your job to go investigate this windows machine and find clues to what the hacker might have done.
| Room | Investigating Windows |
|---|---|
| OS | Windows |
| Difficulty | Easy |
| Creator | tryhackme |
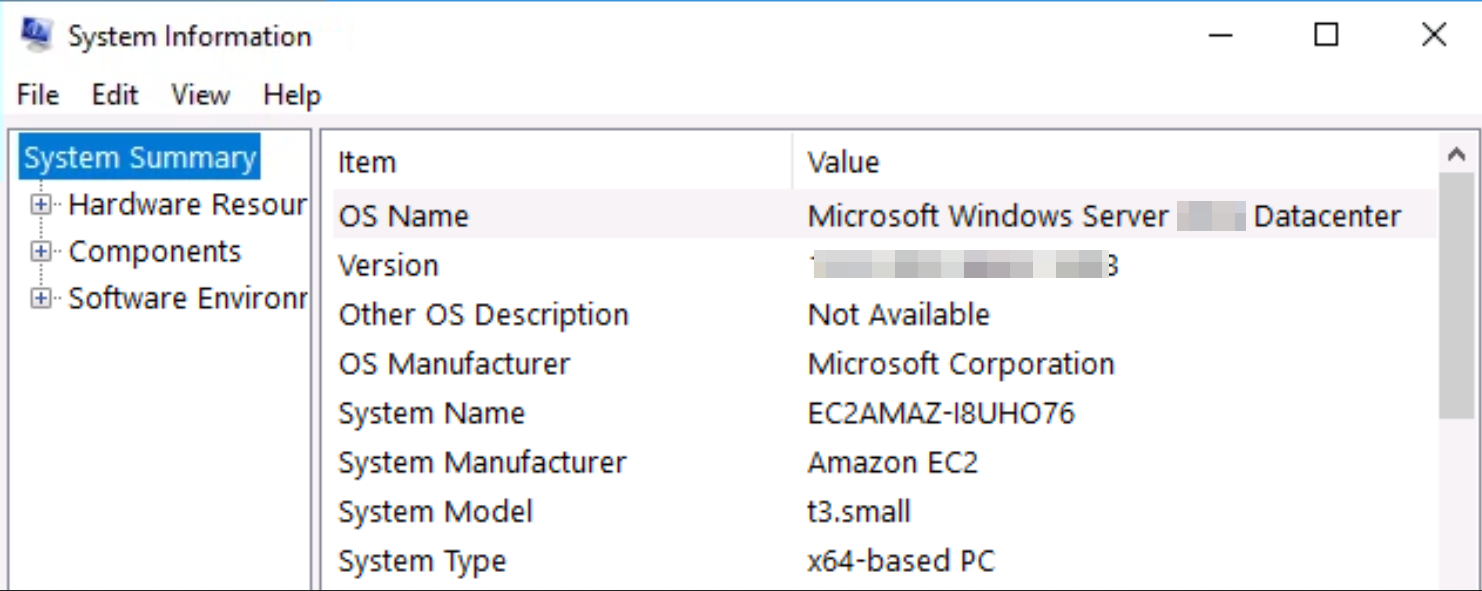
Q. Whats the version and year of the windows machine?
For this, I opened “System Information” with the “Server Manager”,
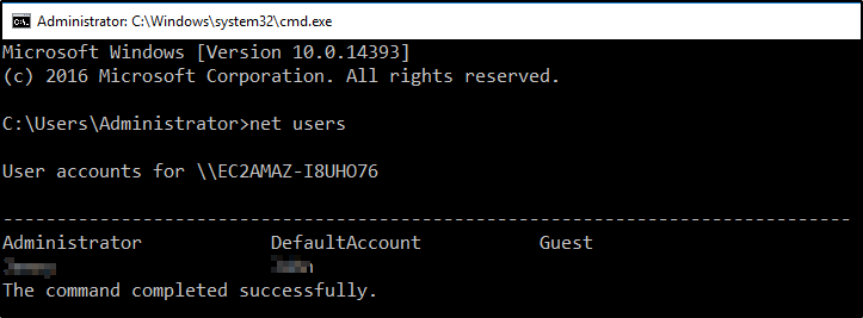
Q. Which user logged in last?
To list all users I entered,
net users
Because I just logged in, I entered the “Administrator” user to inspect the logon time and to get some additional informations.
Q. When did John log onto the system last? Answer format: MM/DD/YYYY H:MM:SS AM/PM
net user ****
Q. What IP does the system connect to when it first starts?
When machine was booting up, we are shown the IP address and this was the IP address that machine first connects to when get’s booted up,
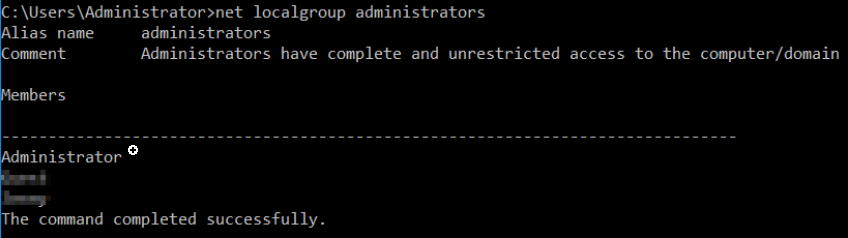
Q. What two accounts had administrative privileges (other than the Administrator user)? Answer format: username1, username2
We can take a look at localgroup of administrator and check the members,
net localgroup administrators
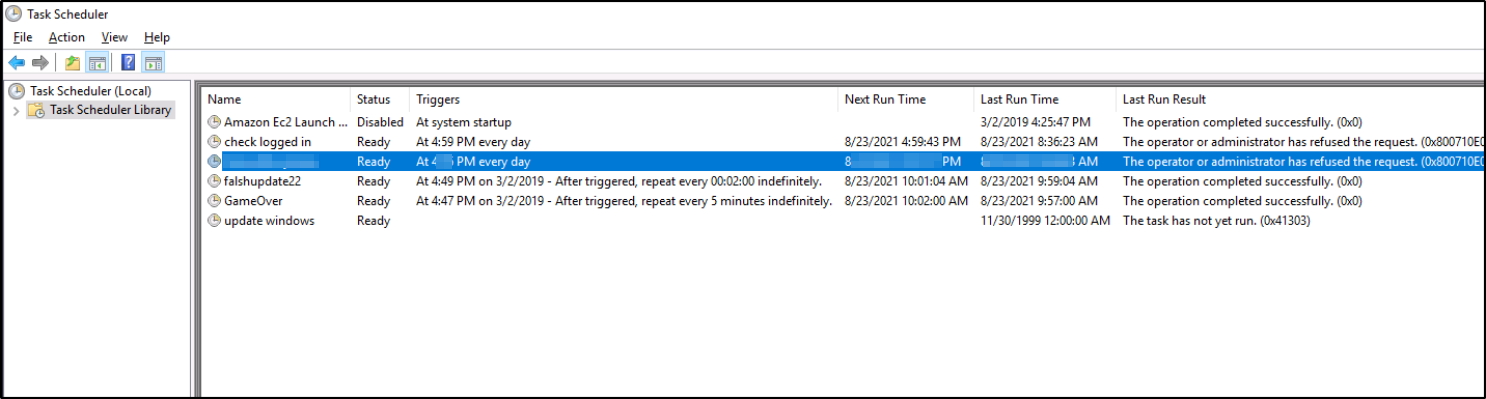
Q. Whats the name of the scheduled task that is malicious?
Open up the “Task Scheduler” and found the malicious scheduled task,
Q. What file was the task trying to run daily?
With the task above under “Actions” I got this answer,
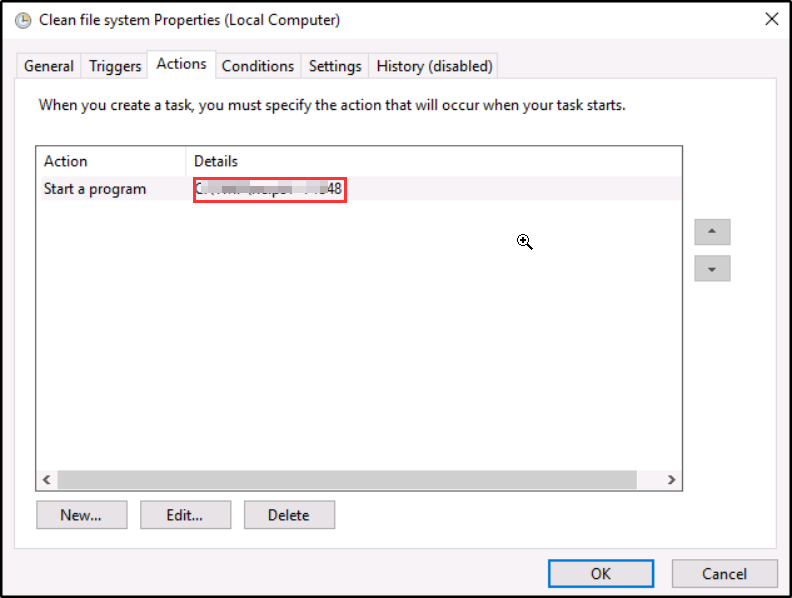
Q. What port did this file listen locally for?
A. Here the “-l” flag got set to listen for the entered port.
Q. When did Jenny last logon?
We can take a look at Jenny user,
net user Jenny

Q. At what date did the compromise take place? Answer format: MM/DD/YY
While exploring the system some more, I found a suspicious directory called “/TMP” on the “C:" location,

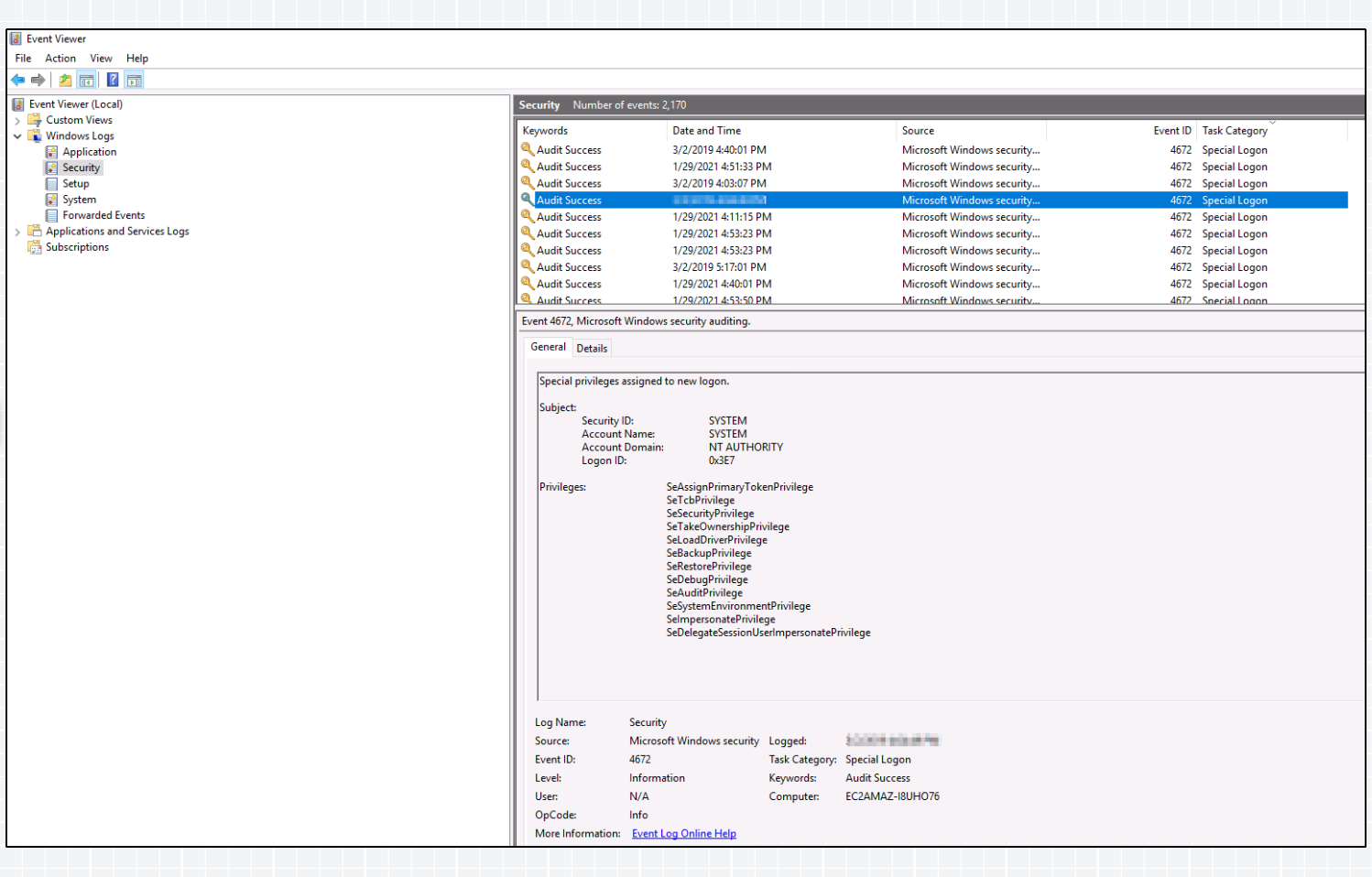
Q. At what time did Windows first assign special privileges to a new logon? Answer format: MM/DD/YYYY HH:MM:SS AM/PM
To get the answer to this question I opened the “Event Viewer” and inspected the “Security” logs. For this I have oriented myself according to the date of the compromise,
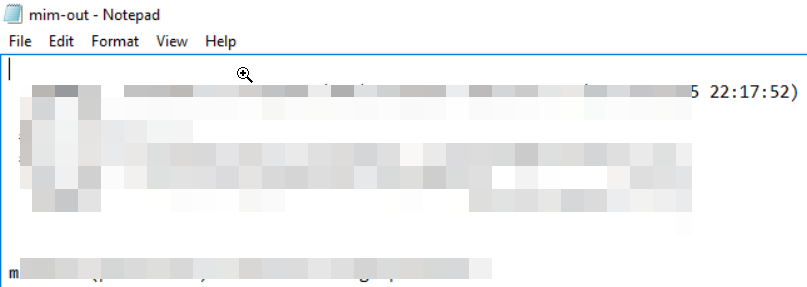
Q. What tool was used to get Windows passwords?
In the “/TMP” directory were some more files and one well-known tool with an output file,
Q. What was the attackers external control and command servers IP?
I got the answer for this question when I solved the last question of the room looking at the “hosts” file,

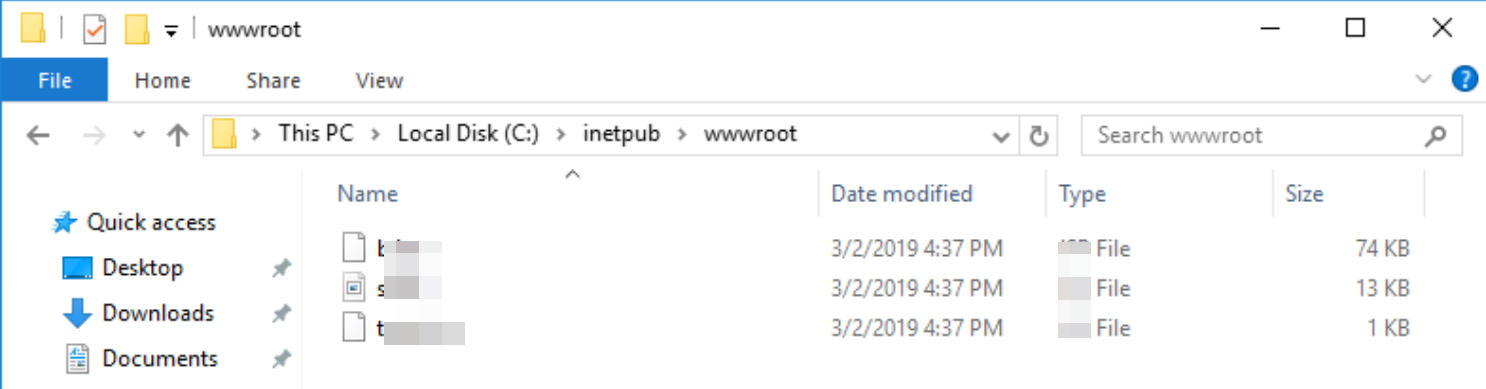
Q. What was the extension name of the shell uploaded via the servers website?
The website of the server was located at “C:\intetpub\wwwroot” and here I got the files,
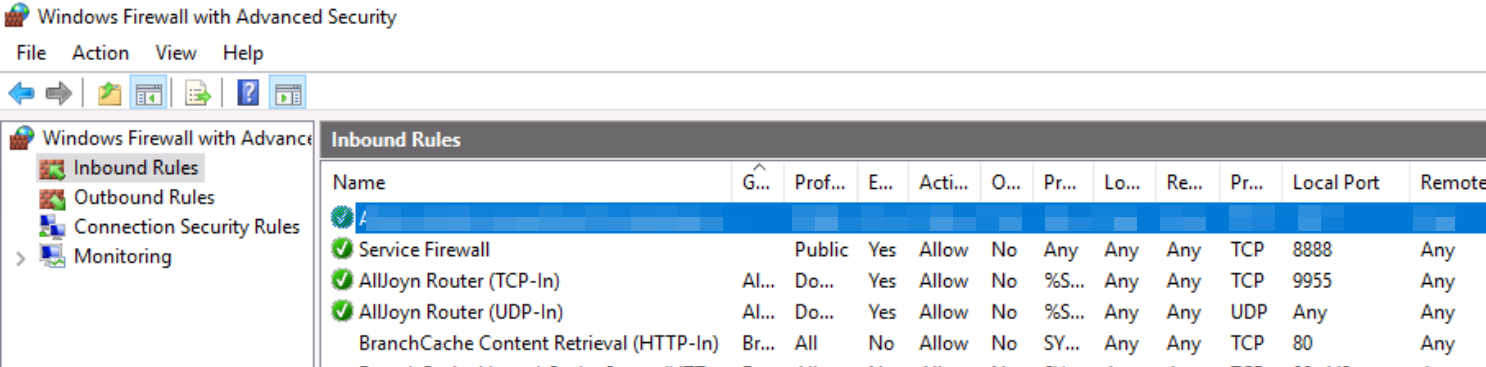
Q. What was the last port the attacker opened?
For this I had to take the hint and went to the Firewall options. The first Inbound Rule was to allow outside connections on the local port 1337,
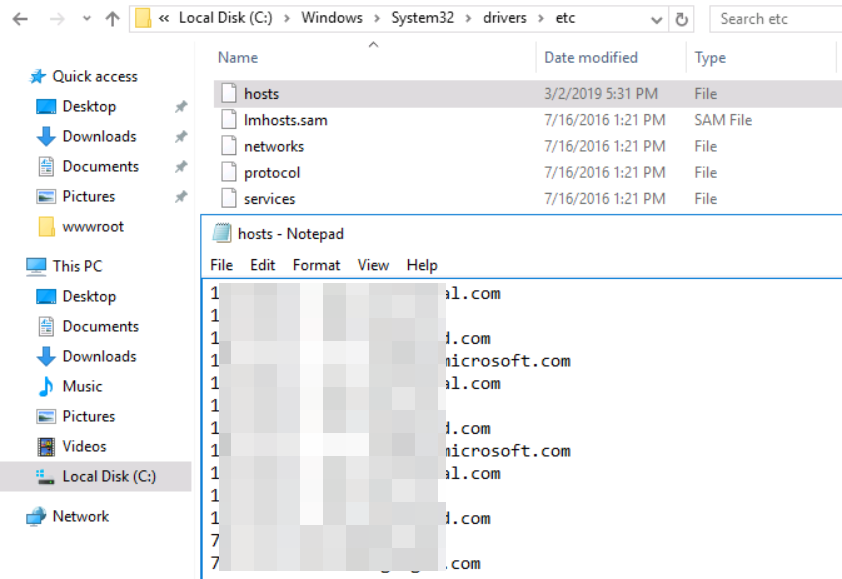
Q. Check for DNS poisoning, what site was targeted?
To get to the DNS record like Linux, I searched for the hosts file on Windows. I got the location of it from this site. In here I got the hostname and the IP address from the attacker for question 13,